| File name: | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader |
| Full analysis: | https://app.any.run/tasks/997f56bf-339f-4cf9-9118-dc45e4598a35 |
| Verdict: | Malicious activity |
| Analysis date: | April 18, 2025, 04:26:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 8C8BADF634F5C15D5AEBEA34D2233F50 |
| SHA1: | 8CF8EE9269D04BD5DBCDFA8A49024F25A46714AF |
| SHA256: | 5387A93FC5BD4D316D29DA5E3E05607EEC6C0D97BFA36E76BA1D4880F4DFA998 |
| SSDEEP: | 49152:dTdgMIISYUnUu4O3f/HAzruQfZt8lW3mUbzDJH38:RCMlSYUnUu4O3fSfZeW3VXd8 |
MALICIOUS
Executing a file with an untrusted certificate
- FileCoAuth.exe (PID: 7448)
SUSPICIOUS
Executable content was dropped or overwritten
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 1164)
- FileCoAuth.exe (PID: 7392)
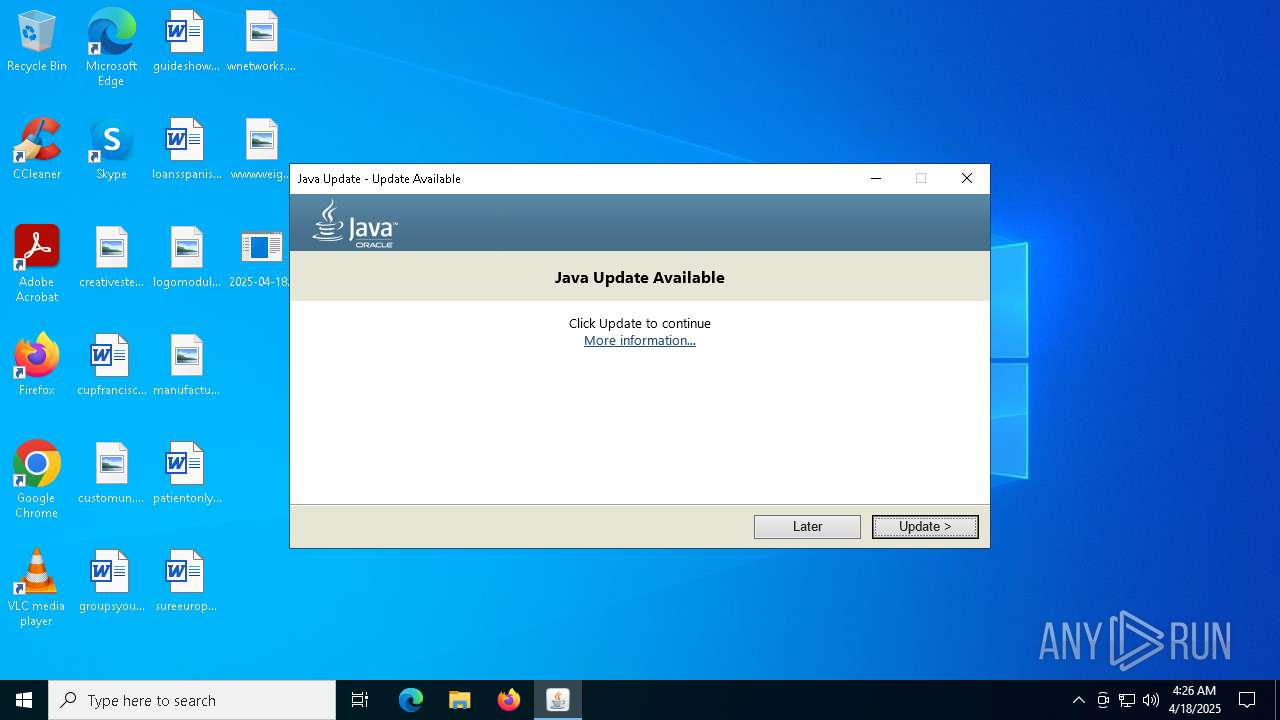
Checks for Java to be installed
- jp2launcher.exe (PID: 5728)
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
Reads security settings of Internet Explorer
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 1164)
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
- jp2launcher.exe (PID: 5728)
- FileCoAuth.exe (PID: 7392)
Reads Microsoft Outlook installation path
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
Reads Internet Explorer settings
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
There is functionality for taking screenshot (YARA)
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 1164)
Process drops legitimate windows executable
- FileCoAuth.exe (PID: 7392)
Starts a Microsoft application from unusual location
- FileCoAuth.exe (PID: 7448)
INFO
Checks supported languages
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 1164)
- javaws.exe (PID: 6712)
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
- jp2launcher.exe (PID: 5728)
- FileCoAuth.exe (PID: 7448)
Reads the computer name
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 1164)
- javaws.exe (PID: 6712)
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
- jp2launcher.exe (PID: 5728)
- FileCoAuth.exe (PID: 7448)
Process checks computer location settings
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 1164)
- FileCoAuth.exe (PID: 7392)
The sample compiled with english language support
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 1164)
- FileCoAuth.exe (PID: 7392)
Checks proxy server information
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
- jp2launcher.exe (PID: 5728)
- slui.exe (PID: 7540)
Create files in a temporary directory
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 1164)
- jp2launcher.exe (PID: 5728)
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
- FileCoAuth.exe (PID: 7448)
Reads the software policy settings
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
- slui.exe (PID: 7540)
Reads the machine GUID from the registry
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
- jp2launcher.exe (PID: 5728)
- FileCoAuth.exe (PID: 7448)
Creates files or folders in the user directory
- 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe (PID: 5892)
- jp2launcher.exe (PID: 5728)
- FileCoAuth.exe (PID: 7448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (49.2) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (16.2) |
| .scr | | | Windows screen saver (14.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 29696 |
| InitializedDataSize: | 29184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x80e4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
133
Monitored processes
7
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | "C:\Users\admin\Desktop\2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe" | C:\Users\admin\Desktop\2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5728 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxwbHVnaW4uamFyAC1EamRrLmRpc2FibGVMYXN0VXNhZ2VUcmFja2luZz10cnVlAC1Eam5scHguanZtPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcYmluXGphdmF3LmV4ZQAtRGpubHB4LnZtYXJncz1MVVJxWkdzdVpHbHpZV0pzWlV4aGMzUlZjMkZuWlZSeVlXTnJhVzVuUFhSeWRXVUE= -ma LVNTVkJhc2VsaW5lVXBkYXRlAC1ub3RXZWJKYXZh | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 5892 | "C:\Users\admin\AppData\Local\Temp\3582-490\2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Update Checker Version: 2.8.401.10 Modules
| |||||||||||||||
| 6712 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" -J-Djdk.disableLastUsageTracking=true -SSVBaselineUpdate | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 7392 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7448 | "C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe" -Embedding | C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe | — | FileCoAuth.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 7540 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 634
Read events
11 594
Write events
25
Delete events
15
Modification events
| (PID) Process: | (5892) 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | write | Name: | Method |
Value: jau-m | |||
| (PID) Process: | (5892) 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | write | Name: | LastUpdateBeginTime |
Value: Fri, 18 Apr 2025 04:26:54 GMT | |||
| (PID) Process: | (5892) 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | delete value | Name: | LocalFileName |
Value: | |||
| (PID) Process: | (5892) 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | delete value | Name: | InstallOptions |
Value: | |||
| (PID) Process: | (5892) 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | delete value | Name: | UpdateDescription |
Value: | |||
| (PID) Process: | (5892) 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | delete value | Name: | UpdateTitle1 |
Value: | |||
| (PID) Process: | (5892) 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | delete value | Name: | UpdateTitle2 |
Value: | |||
| (PID) Process: | (5892) 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | delete value | Name: | UpdateMoreInfoUrl |
Value: | |||
| (PID) Process: | (5892) 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | delete value | Name: | BalloonTitle |
Value: | |||
| (PID) Process: | (5892) 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | delete value | Name: | BalloonTip |
Value: | |||
Executable files
9
Suspicious files
3
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7448 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2025-04-18.0427.7448.1.aodl | binary | |
MD5:28DCA2FF4B34B5A52A2E59DF202A6ED3 | SHA256:33BACCB7296F1ED1F995FC77A23049F261CF391AC0388F9E8DD161F8C17B7F94 | |||
| 1164 | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | C:\Users\admin\AppData\Local\Temp\3582-490\2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | executable | |
MD5:00D43AFFB8E12569A341EC4E86FE07D7 | SHA256:2228007A6284EA84BBFFFCF3C31CA081771F14F4BB94B865D6C2F5DD0D1EF1C2 | |||
| 1164 | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | C:\ProgramData\Adobe\ARM\S\388\AdobeARMHelper.exe | executable | |
MD5:C2A0798C0FADF00C7A1F374A31012152 | SHA256:9D0BBD67B2CF12AD6B0C5A781377F8A858C71C6861D2C04E4D8DA5E48D0CCBE3 | |||
| 1164 | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileSyncConfig.exe | executable | |
MD5:0F27A0A9CD3BD9796B73BBB50E2590FF | SHA256:E0BD73EFACD6095FCC1D7DE8F97A71505879ADBEE626278D32510520B98C7D34 | |||
| 1164 | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\OneDrive.exe | executable | |
MD5:EA16990673CB3198617430BD8ED90960 | SHA256:17512B1DC73DDE13508659E68EF8463FACE5870FBC5FCF19790F7B452711BCCE | |||
| 1164 | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\OneDriveUpdaterService.exe | executable | |
MD5:32C1CFACE596E114A37E9A39CC678BDA | SHA256:724D6AF89AE852CF8E19E10E54B533F1304F42DF61B73E3BAE752AB1687AC0C9 | |||
| 1164 | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | executable | |
MD5:29B54FF4FC920FD25431198C67860AC7 | SHA256:012D3925C3210BFE2D2D3FF524D512BB7044D4B4F83CCB3C603F9F1B7BAC8B65 | |||
| 7392 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe | executable | |
MD5:394DEEEF3E5FFE6C77A9CDA1832361BB | SHA256:37DCEC7509B0803F2BBA453845ED67FDBAA15771F8A60FC11F9082FD2A64BD23 | |||
| 1164 | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | C:\Users\admin\AppData\Local\Temp\tmp5023.tmp | text | |
MD5:C7675DDA6121F931F9F9D208E122257A | SHA256:B6AB79C23B7FA907A178234309C2277E5B25340DBA277DC661FF68E5948782BC | |||
| 7448 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2025-04-18.0427.7448.1.odl | binary | |
MD5:7527CB19AB1EA1DCABD3FF268A253806 | SHA256:5FD73EDF1E51424FC2959FA5B143CF1AF7DEA2AC8A4E2448A0CAC99526079D95 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
24
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.197.134.132:443 | https://javadl-esd-secure.oracle.com/update/1.8.0/map-m-1.8.0.xml | unknown | — | — | unknown |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 23.197.134.132:443 | https://javadl-esd-secure.oracle.com/update/1.8.0/8a1589aa0fe24566b4337beee47c2d29/au-descriptor-1.8.0_451-b10.xml | unknown | xml | 6.67 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5892 | 2025-04-18_8c8badf634f5c15d5aebea34d2233f50_amadey_black-basta_elex_hijackloader_luca-stealer_neshta_remcos_smoke-loader.exe | 23.197.134.132:443 | javadl-esd-secure.oracle.com | Akamai International B.V. | US | whitelisted |
5728 | jp2launcher.exe | 23.197.134.132:443 | javadl-esd-secure.oracle.com | Akamai International B.V. | US | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4776 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7540 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
javadl-esd-secure.oracle.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |