| download: | 64.exe |
| Full analysis: | https://app.any.run/tasks/5290873f-5811-4571-9db6-c510114e9e55 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | May 11, 2020, 18:33:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7979220890E32DFF3F13246176430601 |
| SHA1: | A72EB0E301DFFF293AAB908912269E59FA914C5D |
| SHA256: | 536C8111C7702589AA90108EFBBDACC2798F3CC44FAD8480401C8EBA3A6306D0 |
| SSDEEP: | 1536:vqEA70HzLJksPEOajozLElnqiO2cdJ/tHi:vXTLJkQ7zAV3+tC |
MALICIOUS
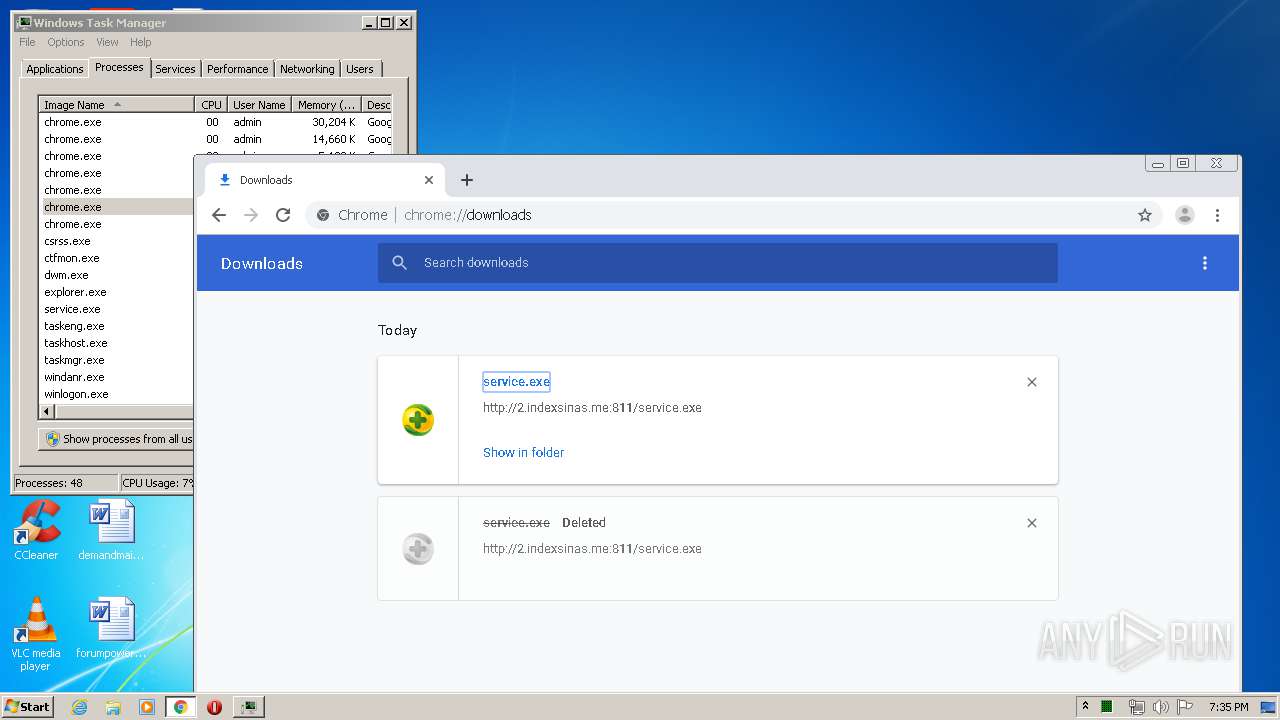
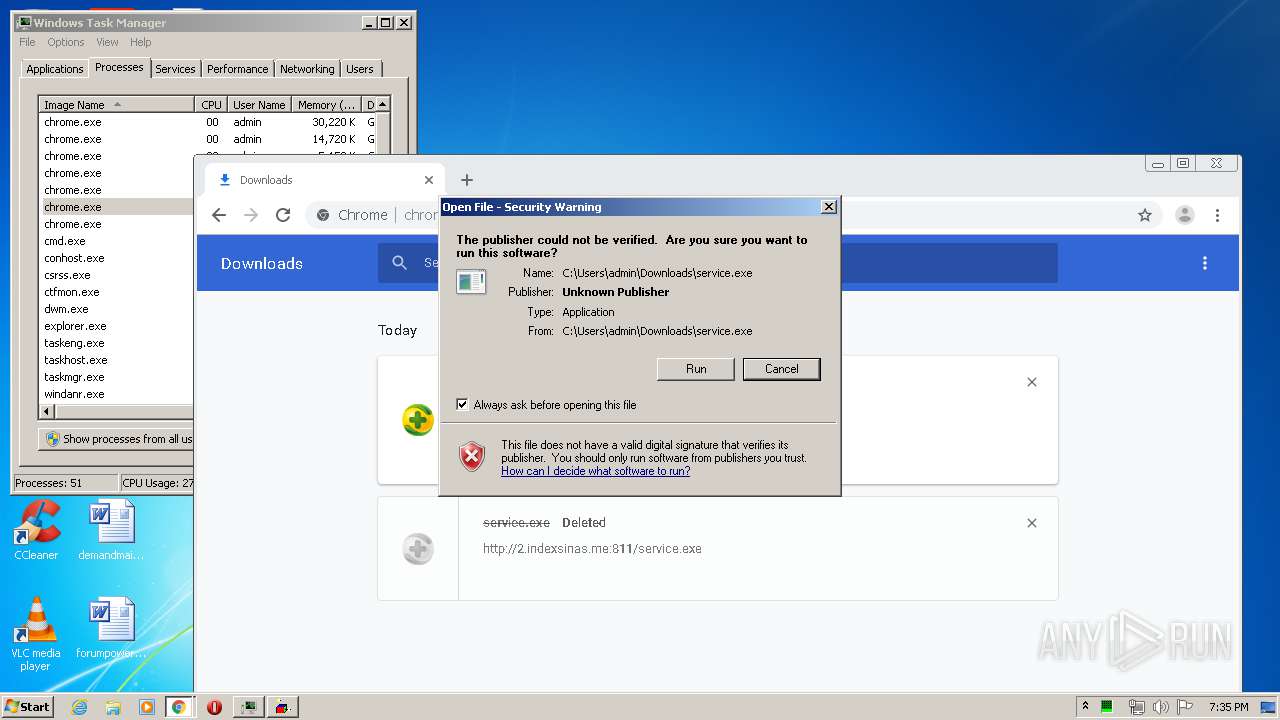
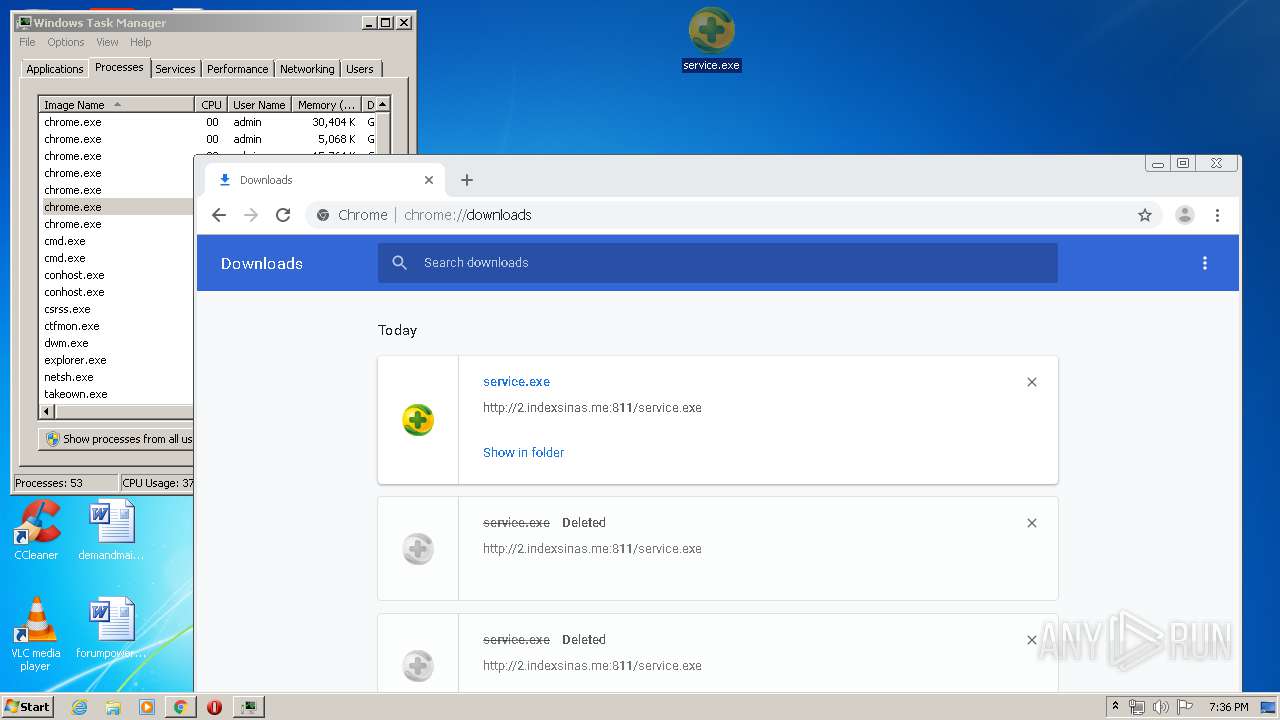
Downloads executable files from the Internet
- chrome.exe (PID: 3876)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 2700)
Application was dropped or rewritten from another process
- service.exe (PID: 1452)
- service.exe (PID: 4036)
- service.exe (PID: 676)
- service.exe (PID: 5560)
- d1lhots.exe (PID: 5116)
Starts NET.EXE for service management
- service.exe (PID: 1452)
- service.exe (PID: 4036)
- service.exe (PID: 676)
- service.exe (PID: 5560)
- conhost.exe (PID: 4420)
Uses TASKKILL.EXE to kill security tools
- cmd.exe (PID: 5536)
- cmd.exe (PID: 5520)
Looks like application has launched a miner
- conhost.exe (PID: 4420)
- svchost.exe (PID: 4700)
Tries to delete the host file
- cmd.exe (PID: 4632)
Writes to the hosts file
- cmd.exe (PID: 4632)
MINER was detected
- d1lhots.exe (PID: 5116)
Connects to CnC server
- d1lhots.exe (PID: 5116)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 1876)
Executable content was dropped or overwritten
- chrome.exe (PID: 3876)
- chrome.exe (PID: 1876)
- service.exe (PID: 5560)
- conhost.exe (PID: 4420)
Starts CMD.EXE for self-deleting
- 64.exe (PID: 2428)
Starts CMD.EXE for commands execution
- 64.exe (PID: 2428)
- service.exe (PID: 1452)
- cmd.exe (PID: 3292)
- service.exe (PID: 4036)
- cmd.exe (PID: 3848)
- service.exe (PID: 676)
- cmd.exe (PID: 2784)
- service.exe (PID: 5560)
- conhost.exe (PID: 4420)
- cmd.exe (PID: 4632)
Creates files in the Windows directory
- service.exe (PID: 1452)
- service.exe (PID: 4036)
- service.exe (PID: 5560)
- conhost.exe (PID: 4420)
- cmd.exe (PID: 4632)
Starts SC.EXE for service management
- service.exe (PID: 1452)
- cmd.exe (PID: 3848)
- service.exe (PID: 4036)
- cmd.exe (PID: 3292)
- service.exe (PID: 676)
- cmd.exe (PID: 2784)
- service.exe (PID: 5560)
- cmd.exe (PID: 4632)
- conhost.exe (PID: 4420)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 772)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 2548)
- cmd.exe (PID: 3148)
- cmd.exe (PID: 3292)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 4364)
- cmd.exe (PID: 5912)
- cmd.exe (PID: 1008)
- cmd.exe (PID: 4612)
- cmd.exe (PID: 5808)
- cmd.exe (PID: 5348)
- cmd.exe (PID: 4392)
- cmd.exe (PID: 4764)
- cmd.exe (PID: 4668)
- cmd.exe (PID: 4728)
- cmd.exe (PID: 4732)
- cmd.exe (PID: 4664)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 5960)
- cmd.exe (PID: 4496)
- cmd.exe (PID: 5320)
- cmd.exe (PID: 4472)
- cmd.exe (PID: 5672)
- cmd.exe (PID: 2216)
- cmd.exe (PID: 5332)
- cmd.exe (PID: 4116)
- cmd.exe (PID: 4272)
- cmd.exe (PID: 6132)
- cmd.exe (PID: 4380)
- cmd.exe (PID: 3652)
- cmd.exe (PID: 3304)
- cmd.exe (PID: 4936)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 2400)
- cmd.exe (PID: 5432)
- cmd.exe (PID: 4604)
- cmd.exe (PID: 5072)
- cmd.exe (PID: 5312)
- cmd.exe (PID: 3368)
- cmd.exe (PID: 4624)
- cmd.exe (PID: 1388)
- cmd.exe (PID: 5696)
- cmd.exe (PID: 5532)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 4736)
- cmd.exe (PID: 3228)
- cmd.exe (PID: 2708)
- cmd.exe (PID: 3112)
- cmd.exe (PID: 5792)
- cmd.exe (PID: 5884)
- cmd.exe (PID: 6024)
- cmd.exe (PID: 4944)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 1648)
- cmd.exe (PID: 5380)
- cmd.exe (PID: 5964)
- cmd.exe (PID: 5916)
- cmd.exe (PID: 4748)
- cmd.exe (PID: 5232)
- cmd.exe (PID: 4232)
- cmd.exe (PID: 5196)
- cmd.exe (PID: 3644)
- cmd.exe (PID: 6084)
- cmd.exe (PID: 4632)
- cmd.exe (PID: 5212)
- cmd.exe (PID: 5916)
- cmd.exe (PID: 5148)
- cmd.exe (PID: 3604)
- cmd.exe (PID: 4132)
- cmd.exe (PID: 4280)
- cmd.exe (PID: 6076)
- cmd.exe (PID: 924)
- cmd.exe (PID: 1872)
- cmd.exe (PID: 4412)
- cmd.exe (PID: 5252)
- cmd.exe (PID: 1848)
- cmd.exe (PID: 3828)
- cmd.exe (PID: 3184)
- cmd.exe (PID: 3096)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 4200)
- cmd.exe (PID: 5524)
- cmd.exe (PID: 4824)
- cmd.exe (PID: 2552)
- cmd.exe (PID: 4572)
- cmd.exe (PID: 2772)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3848)
- cmd.exe (PID: 3292)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 4632)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3848)
- cmd.exe (PID: 3292)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 4632)
- conhost.exe (PID: 4420)
- cmd.exe (PID: 5572)
- cmd.exe (PID: 5968)
- cmd.exe (PID: 5612)
- cmd.exe (PID: 5764)
Application launched itself
- cmd.exe (PID: 3848)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 3292)
- cmd.exe (PID: 4632)
Executes scripts
- service.exe (PID: 1452)
- service.exe (PID: 4036)
- service.exe (PID: 676)
- service.exe (PID: 5560)
Uses IPCONFIG.EXE to discover IP address
- cmd.exe (PID: 3848)
- cmd.exe (PID: 3292)
- cmd.exe (PID: 4632)
Removes files from Windows directory
- cmd.exe (PID: 3848)
- cmd.exe (PID: 3292)
- cmd.exe (PID: 4632)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3848)
- cmd.exe (PID: 3292)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 4632)
Creates executable files which already exist in Windows
- service.exe (PID: 5560)
Executed as Windows Service
- svchost.exe (PID: 5184)
- svchost.exe (PID: 4700)
Creates or modifies windows services
- netsh.exe (PID: 4780)
Creates files in the driver directory
- cmd.exe (PID: 4632)
INFO
Reads the hosts file
- chrome.exe (PID: 3876)
- chrome.exe (PID: 1876)
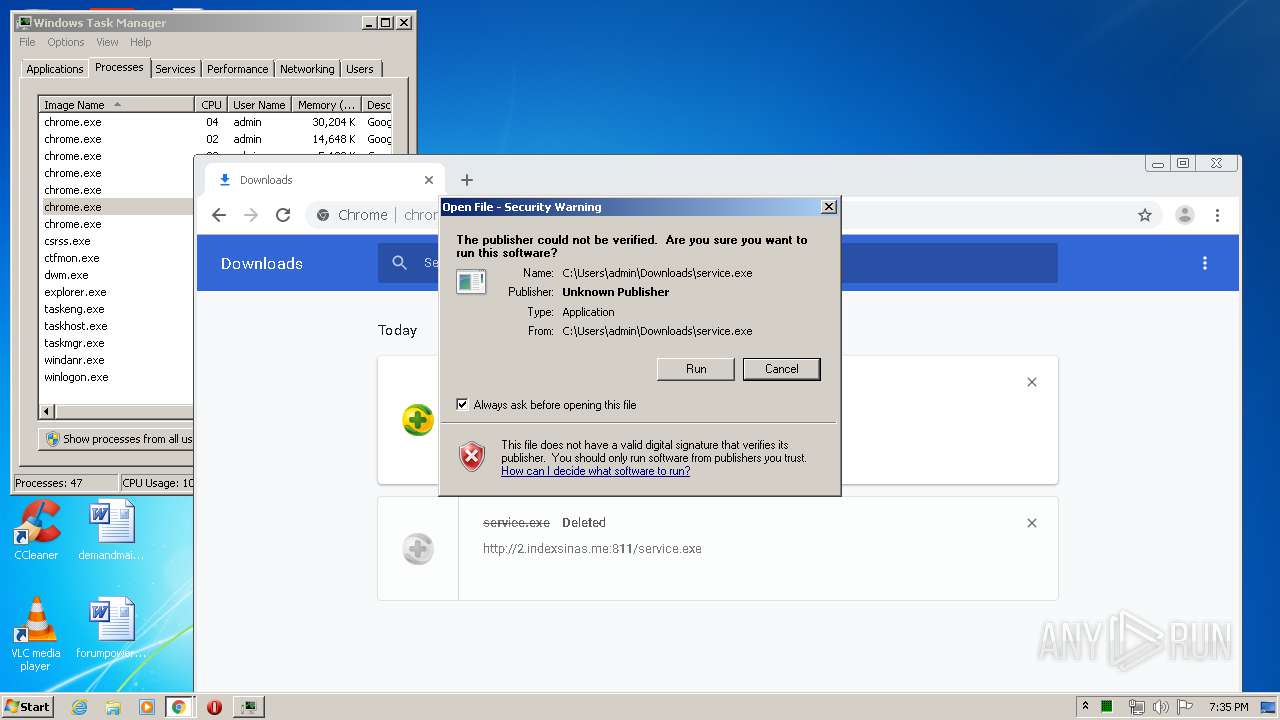
Manual execution by user
- chrome.exe (PID: 1876)
- taskmgr.exe (PID: 3676)
- service.exe (PID: 5560)
Application launched itself
- chrome.exe (PID: 1876)
Reads Internet Cache Settings
- chrome.exe (PID: 1876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:04:09 04:40:35+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 20480 |
| InitializedDataSize: | 94208 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3178 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | French |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | Application MFC MFC KING 2017 |
| FileVersion: | 1, 0, 0, 1 |
| InternalName: | MFC KING 2017 |
| LegalCopyright: | Copyright (C) 2017 |
| LegalTrademarks: | - |
| OriginalFileName: | MFC KING 2017.EXE |
| ProductName: | Application MFC KING 2017 |
| ProductVersion: | 1, 0, 0, 1 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 09-Apr-2017 02:40:35 |
| Detected languages: |
|
| CompanyName: | - |
| FileDescription: | Application MFC MFC KING 2017 |
| FileVersion: | 1, 0, 0, 1 |
| InternalName: | MFC KING 2017 |
| LegalCopyright: | Copyright (C) 2017 |
| LegalTrademarks: | - |
| OriginalFilename: | MFC KING 2017.EXE |
| ProductName: | Application MFC KING 2017 |
| ProductVersion: | 1, 0, 0, 1 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 09-Apr-2017 02:40:35 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000475E | 0x00005000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 3.53265 |
.rdata | 0x00006000 | 0x0000132A | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.26881 |
.data | 0x00008000 | 0x0000C01C | 0x0000C000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.19623 |
.idata | 0x00015000 | 0x000012EF | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.9713 |
.rsrc | 0x00017000 | 0x000045D6 | 0x00005000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.99703 |
.reloc | 0x0001C000 | 0x00000B6F | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.51583 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.42132 | 804 | UNKNOWN | French - France | RT_VERSION |
2 | 2.68898 | 296 | UNKNOWN | French - Switzerland | RT_ICON |
4 | 2.86383 | 18 | UNKNOWN | French - France | UNKNOWN |
5 | 2.94747 | 112 | UNKNOWN | French - France | RT_ACCELERATOR |
7 | 2.971 | 306 | UNKNOWN | French - France | RT_STRING |
9 | 2.7961 | 164 | UNKNOWN | French - France | RT_STRING |
100 | 3.40962 | 302 | UNKNOWN | French - France | RT_DIALOG |
128 | 2.77177 | 30 | UNKNOWN | French - France | UNKNOWN |
129 | 2.37086 | 34 | UNKNOWN | French - Switzerland | RT_GROUP_ICON |
3585 | 2.05855 | 66 | UNKNOWN | French - France | RT_STRING |
Imports
KERNEL32.dll |
MFC42.DLL |
MSVCRT.dll |
USER32.dll |
Total processes
1 054
Monitored processes
812
Malicious processes
13
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | C:\Windows\system32\cmd.exe /S /D /c" echo y" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 180 | cacls "C:\Program Files (x86)\Restorgj\ch\Clean.exe" /d everyone | C:\Windows\system32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 256 | sc delete csrss | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 256 | c:\windows\Fonts\svchost.exe set MicrosotMais DisplayName WMI Performance Services | c:\windows\Fonts\svchost.exe | — | conhost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Tasks Exit code: 0 Version: 6.1.7601.23403 (win7sp1_ldr.160325-0600) Modules
| |||||||||||||||
| 272 | C:\Windows\system32\cmd.exe /S /D /c" echo y" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 272 | wmic process where "name='explorer.exe' and ExecutablePath='c:\\windows\\debug\\nat\\explorer.exe'" call Terminate | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | cacls "C:\Windows\data\service.exe" /d everyone | C:\Windows\system32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | sc stop smtpsvrZy | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=135 | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=137 | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 289
Read events
4 059
Write events
2 223
Delete events
7
Modification events
| (PID) Process: | (2428) 64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2428) 64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3956) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 1876-13233695675868875 |
Value: 259 | |||
| (PID) Process: | (1876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
Executable files
9
Suspicious files
43
Text files
280
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5EB99ABC-754.pma | — | |
MD5:— | SHA256:— | |||
| 1876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\3c7619d2-fa7a-4a33-9214-87be37ae8198.tmp | — | |
MD5:— | SHA256:— | |||
| 1876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFa8eee3.TMP | text | |
MD5:— | SHA256:— | |||
| 1876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RFa8ef40.TMP | text | |
MD5:— | SHA256:— | |||
| 1876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFa8f079.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
39
DNS requests
25
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3876 | chrome.exe | GET | 302 | 216.58.212.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 524 b | whitelisted |
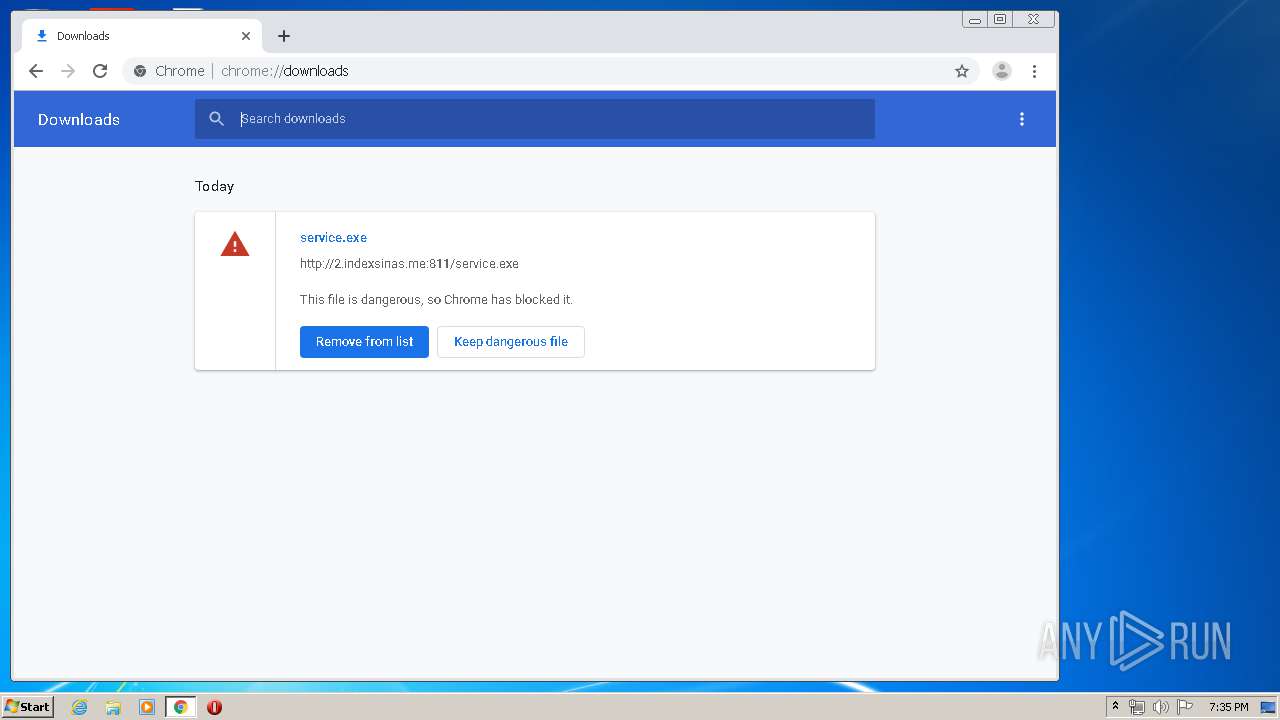
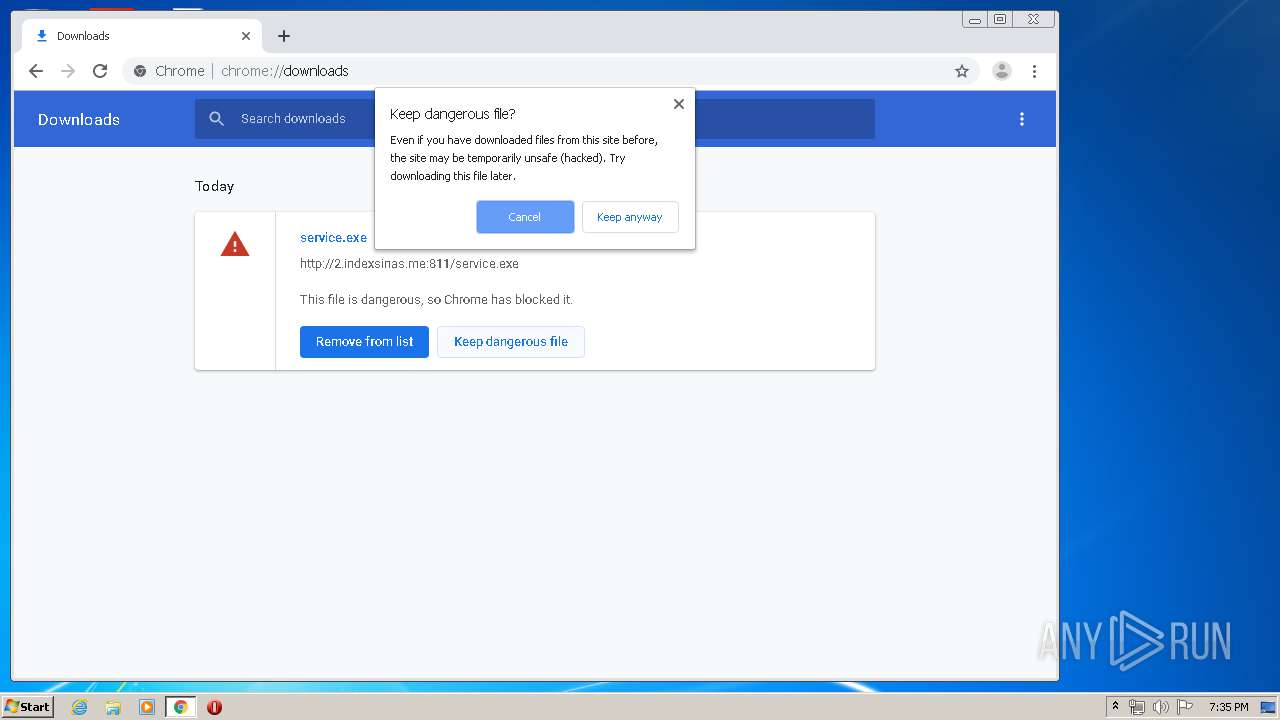
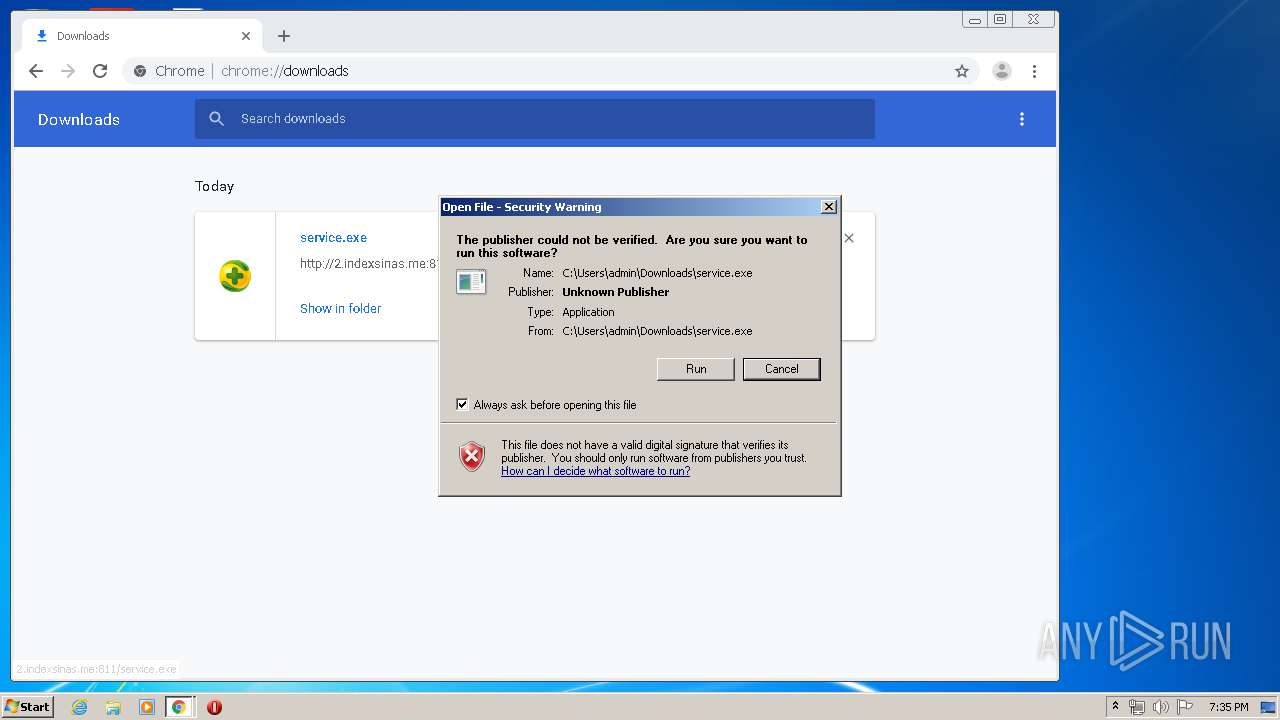
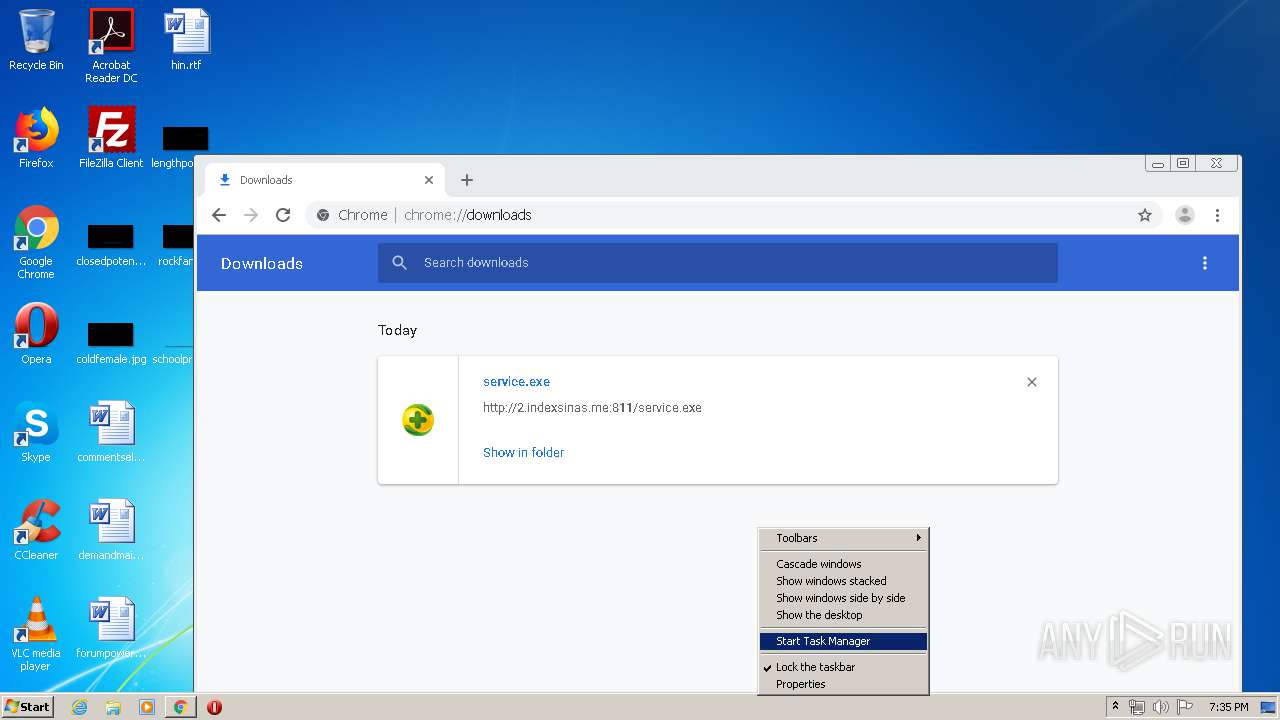
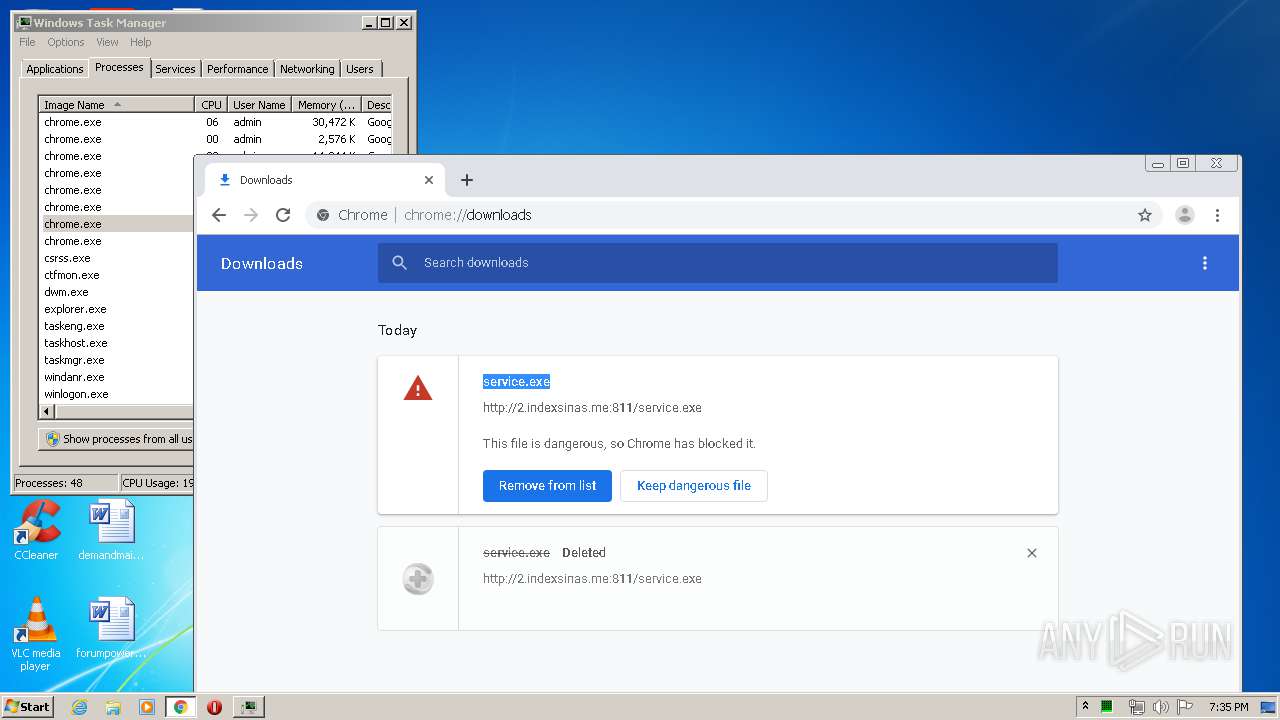
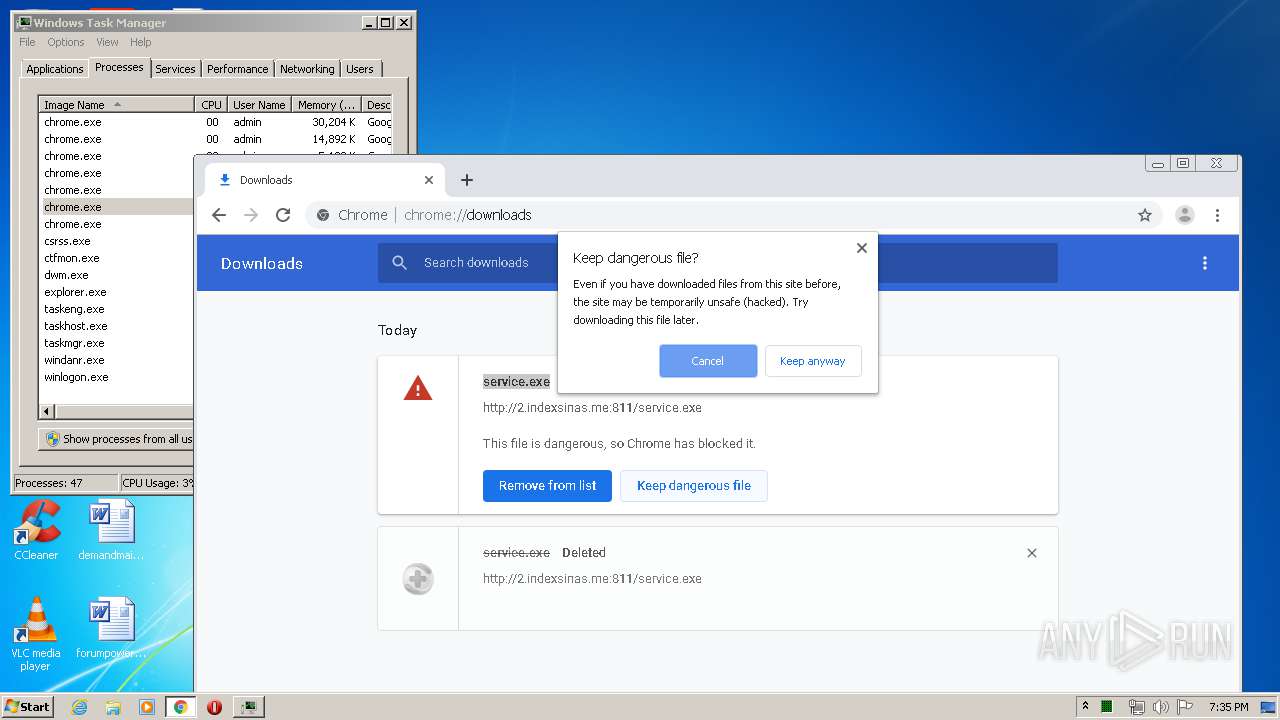
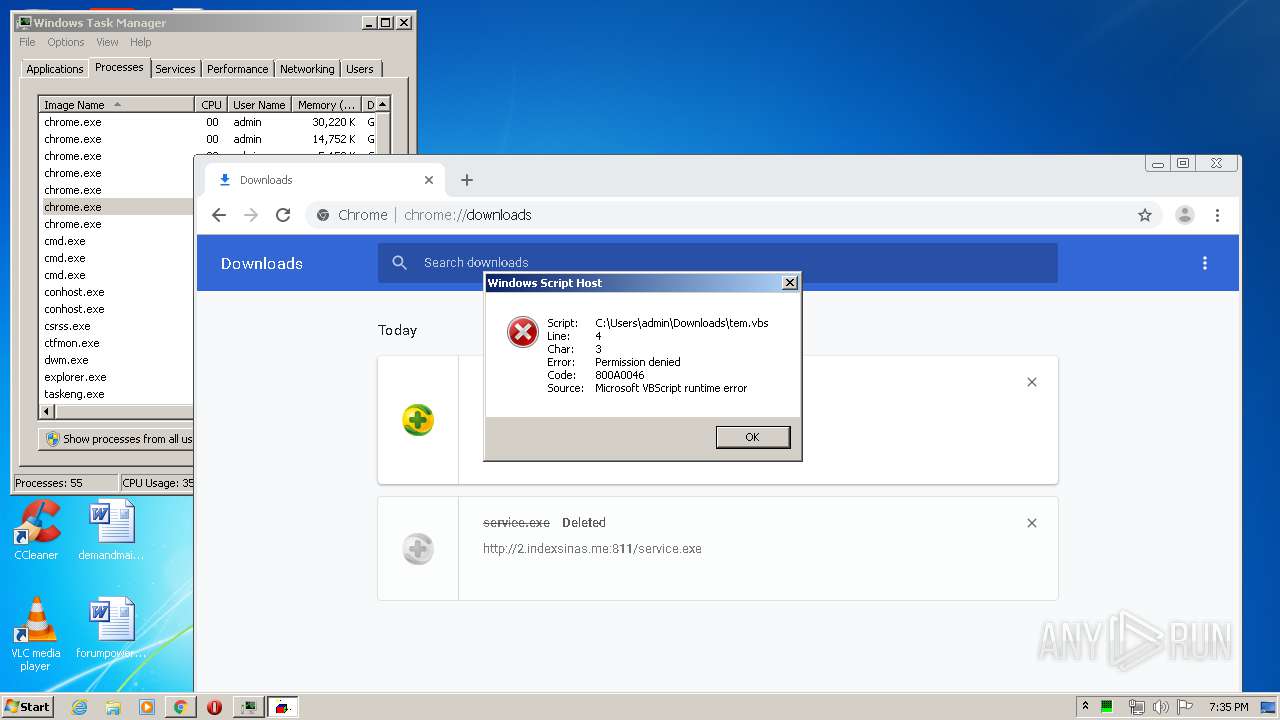
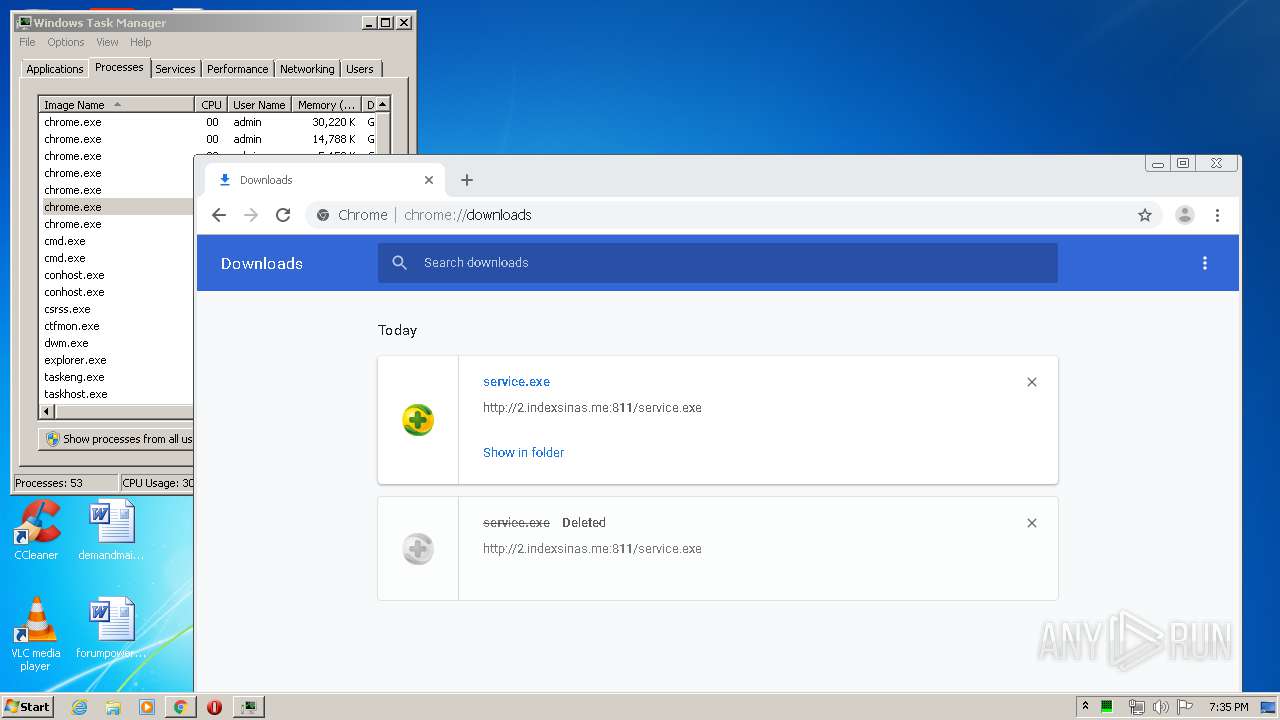
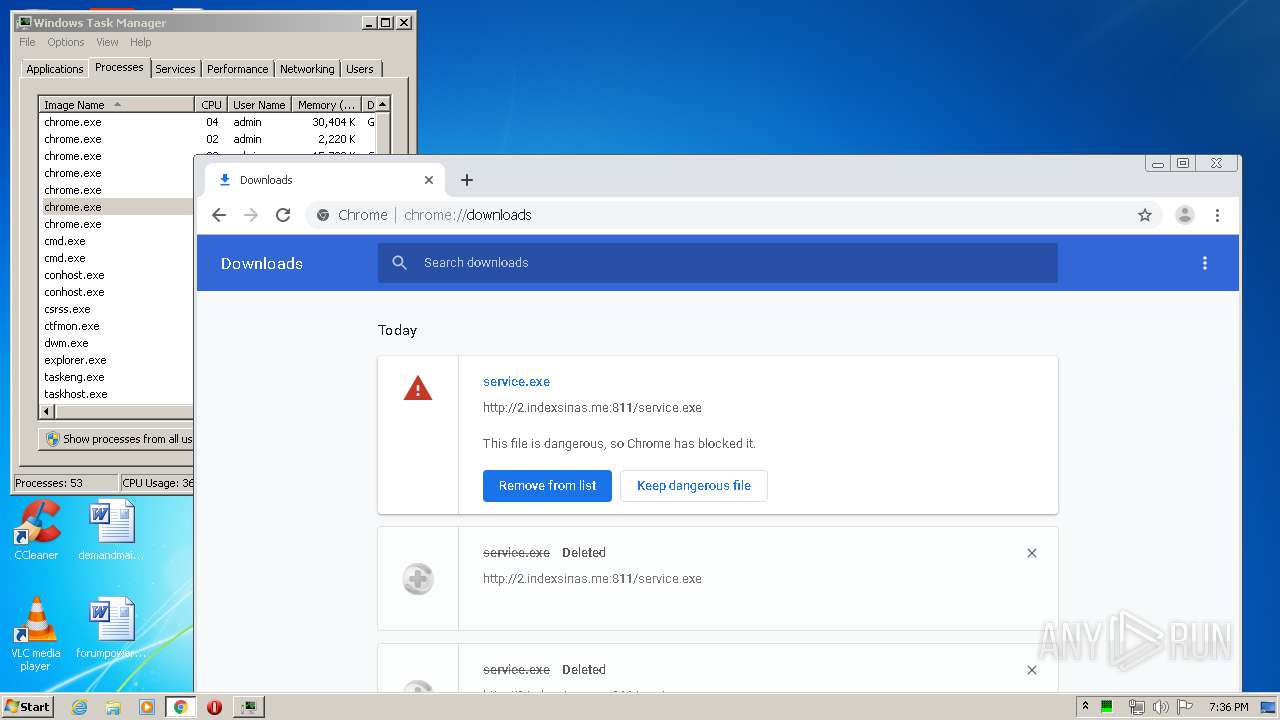
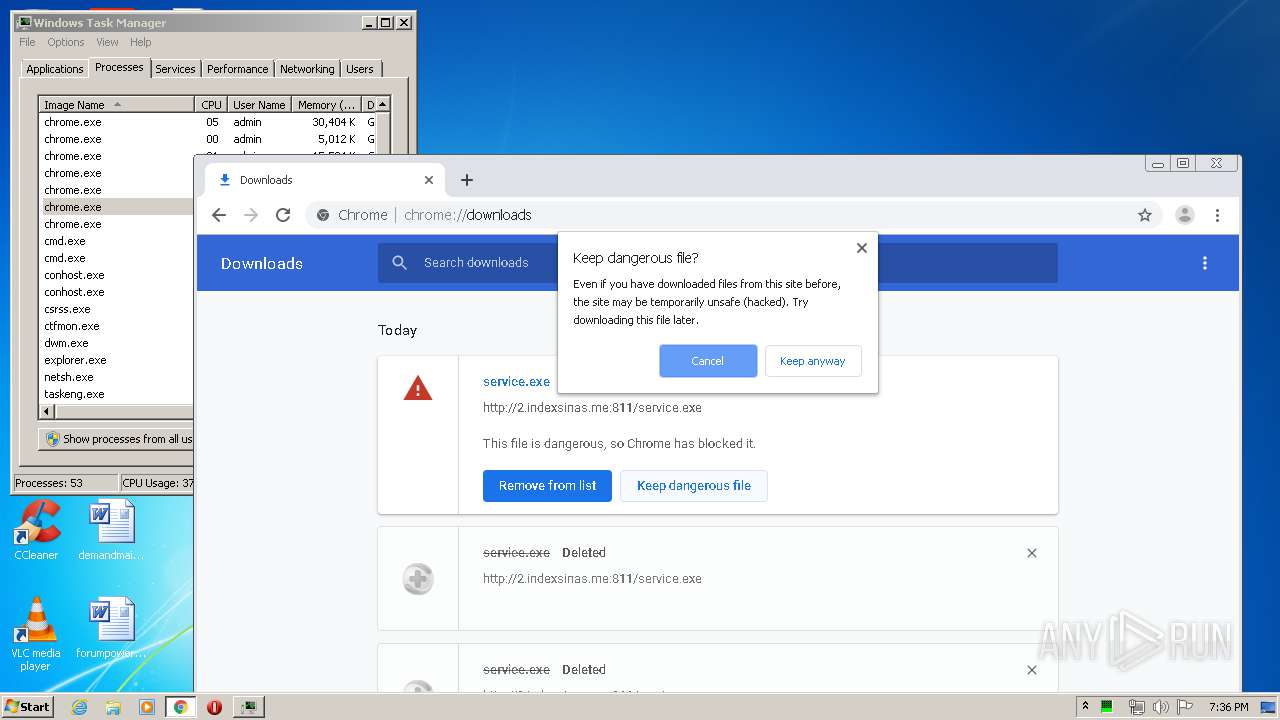
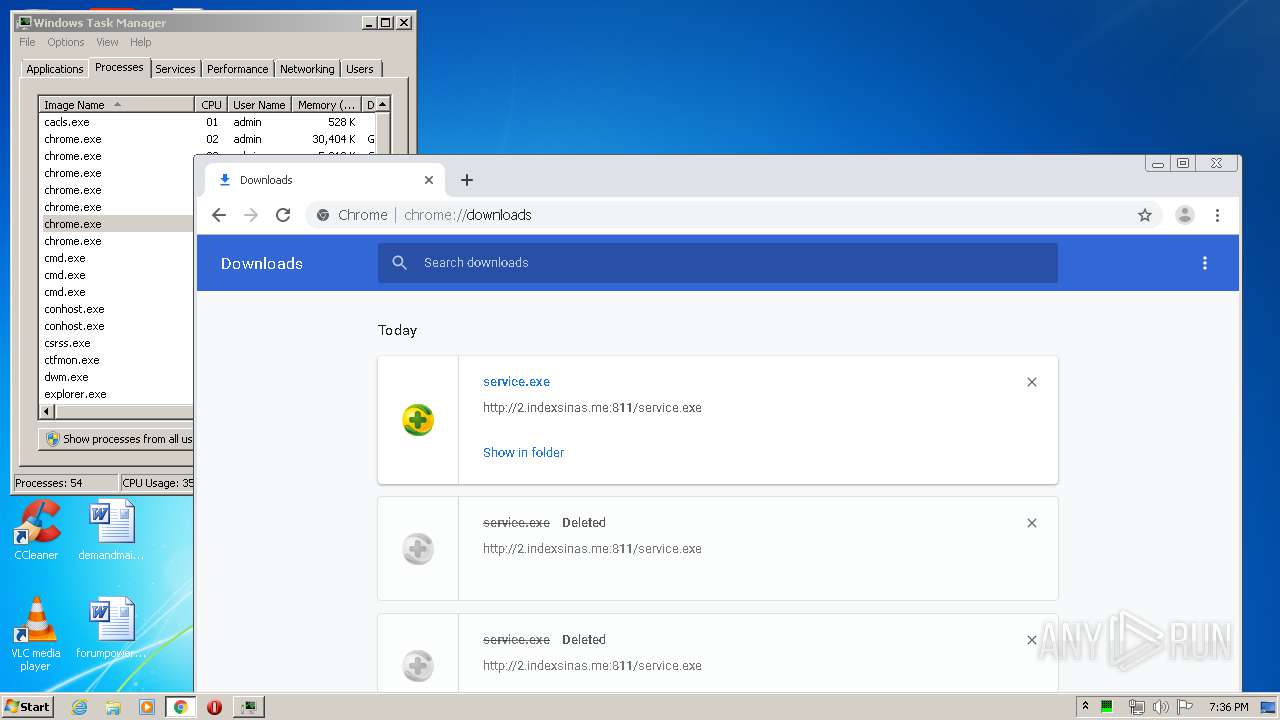
3876 | chrome.exe | GET | 200 | 103.132.180.227:811 | http://2.indexsinas.me:811/service.exe | unknown | executable | 2.16 Mb | suspicious |
3876 | chrome.exe | GET | 200 | 176.126.58.207:80 | http://r4---sn-x2pm-3ufk.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=Qx&mip=84.17.55.74&mm=28&mn=sn-x2pm-3ufk&ms=nvh&mt=1589221930&mv=u&mvi=3&pl=23&shardbypass=yes | PL | crx | 816 Kb | whitelisted |
3876 | chrome.exe | GET | 302 | 216.58.212.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 535 b | whitelisted |
3876 | chrome.exe | GET | 200 | 176.126.58.204:80 | http://r1---sn-x2pm-3ufk.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=QJ&mip=84.17.55.74&mm=28&mn=sn-x2pm-3ufk&ms=nvh&mt=1589221930&mv=u&mvi=0&pcm2cms=yes&pl=23&shardbypass=yes | PL | crx | 293 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3876 | chrome.exe | 176.126.58.204:80 | r1---sn-x2pm-3ufk.gvt1.com | Stowarzyszenie Na Rzecz Rozwoju Spoleczenstwa Informacyjnego e-Poludnie | PL | whitelisted |
3876 | chrome.exe | 216.58.212.142:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
3876 | chrome.exe | 216.58.212.129:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
3876 | chrome.exe | 176.126.58.207:80 | r4---sn-x2pm-3ufk.gvt1.com | Stowarzyszenie Na Rzecz Rozwoju Spoleczenstwa Informacyjnego e-Poludnie | PL | whitelisted |
3876 | chrome.exe | 103.132.180.227:811 | 2.indexsinas.me | — | — | suspicious |
3876 | chrome.exe | 172.217.18.110:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
— | — | 216.58.206.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3876 | chrome.exe | 172.217.23.99:443 | — | Google Inc. | US | whitelisted |
3876 | chrome.exe | 172.217.16.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3876 | chrome.exe | 216.58.206.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com.ua |
| whitelisted |
www.google.com |
| malicious |
www.google.pl |
| whitelisted |
clients2.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3876 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3876 | chrome.exe | A Network Trojan was detected | ET CURRENT_EVENTS DRIVEBY Likely Evil EXE with no referer from HFS webserver (used by Unknown EK) |
3876 | chrome.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
5116 | d1lhots.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
5116 | d1lhots.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight XMRig JSON_RPC Client Login |
5116 | d1lhots.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
5116 | d1lhots.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
5116 | d1lhots.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight XMRig JSON_RPC Client Login |
5116 | d1lhots.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
— | — | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
2 ETPRO signatures available at the full report