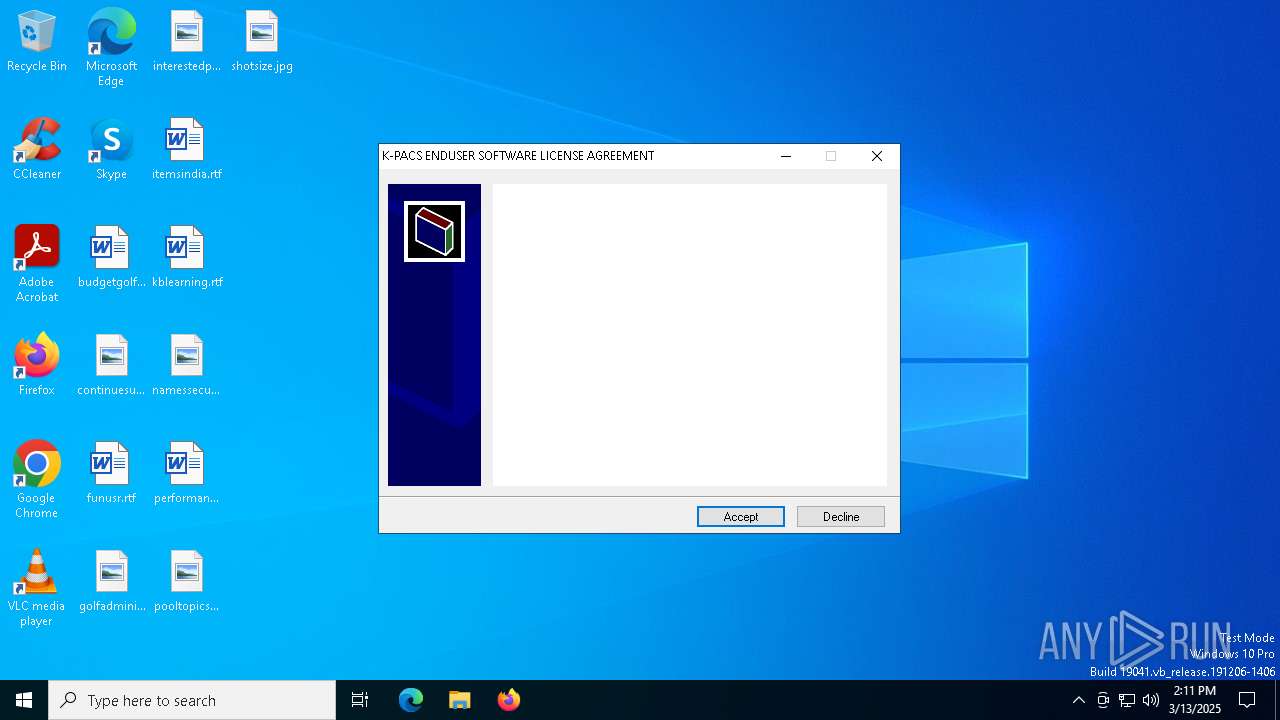
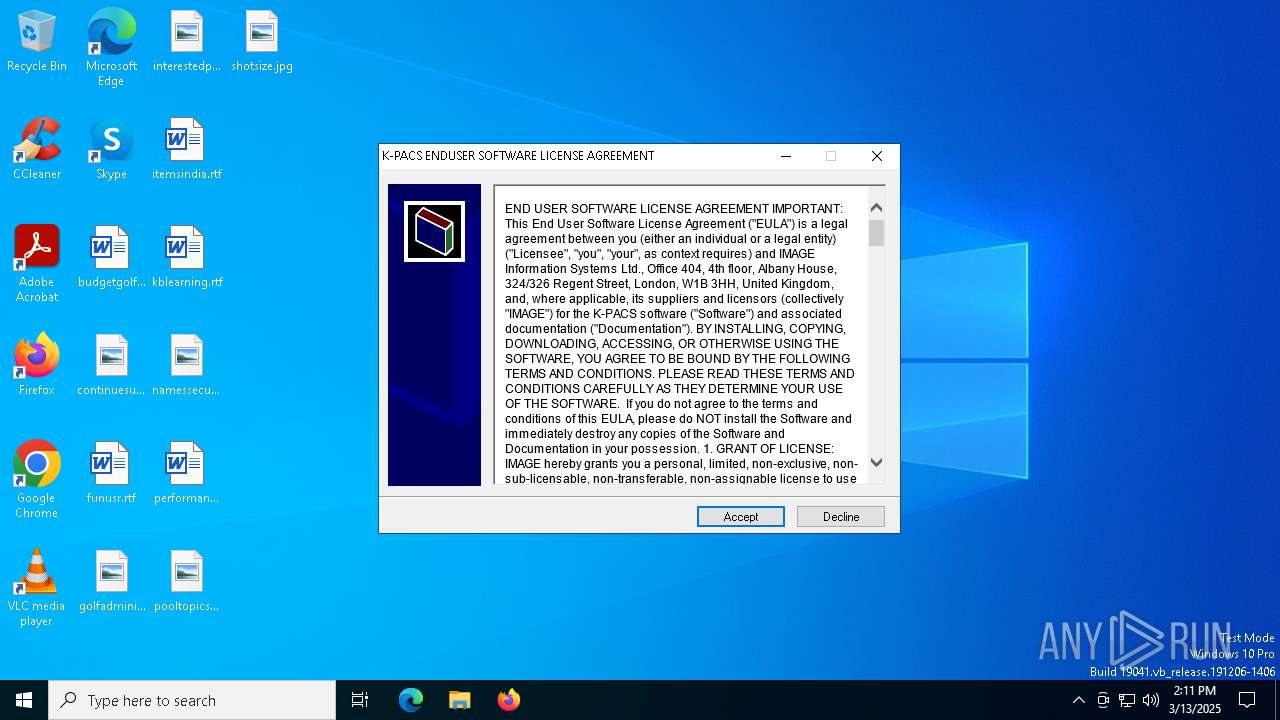
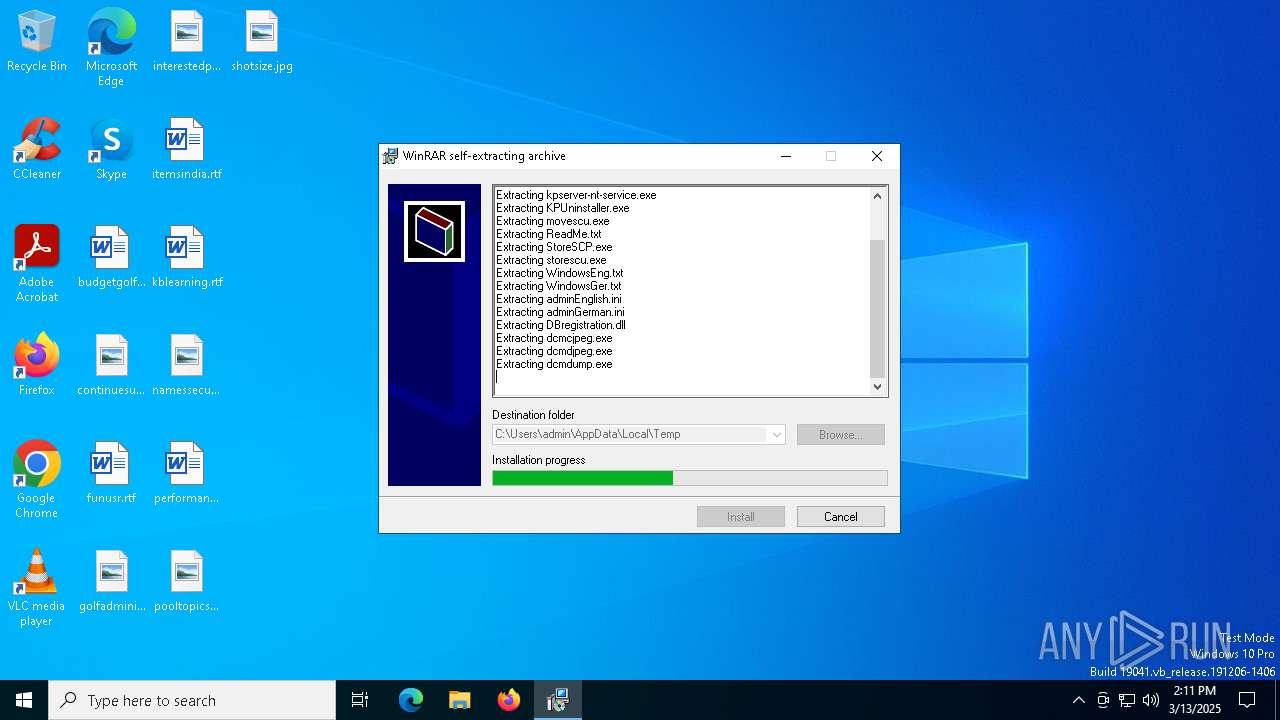
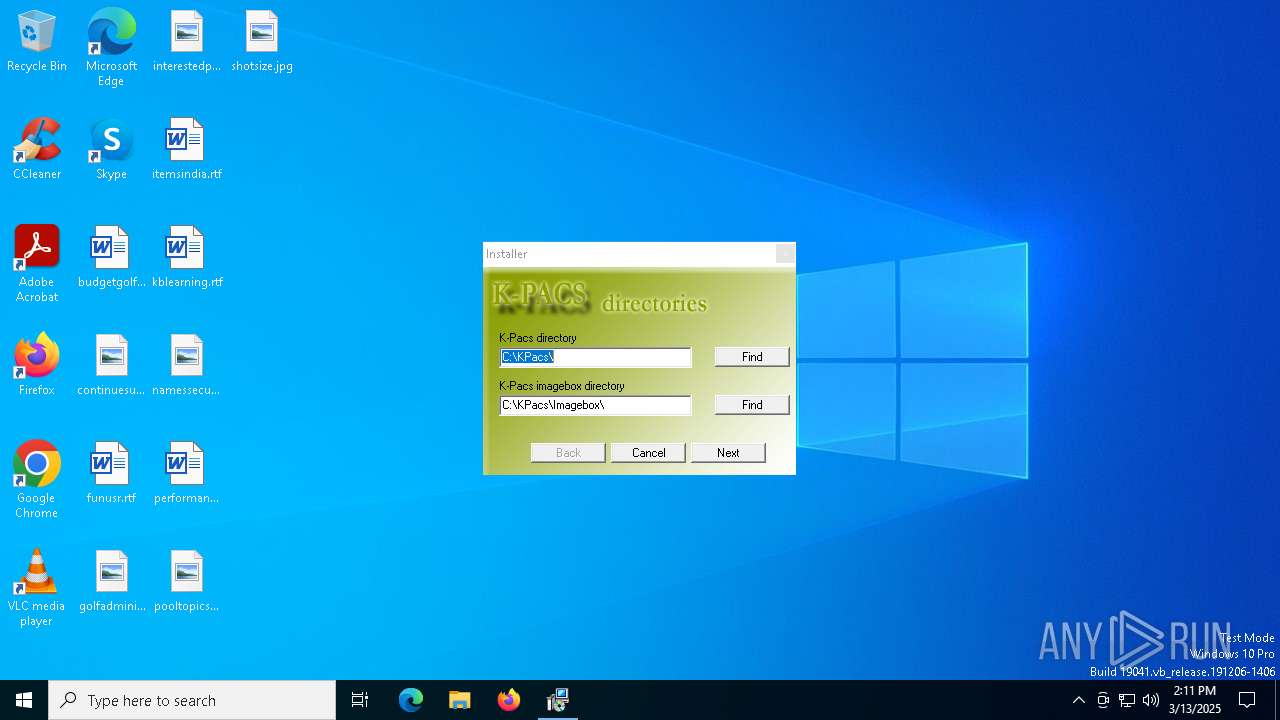
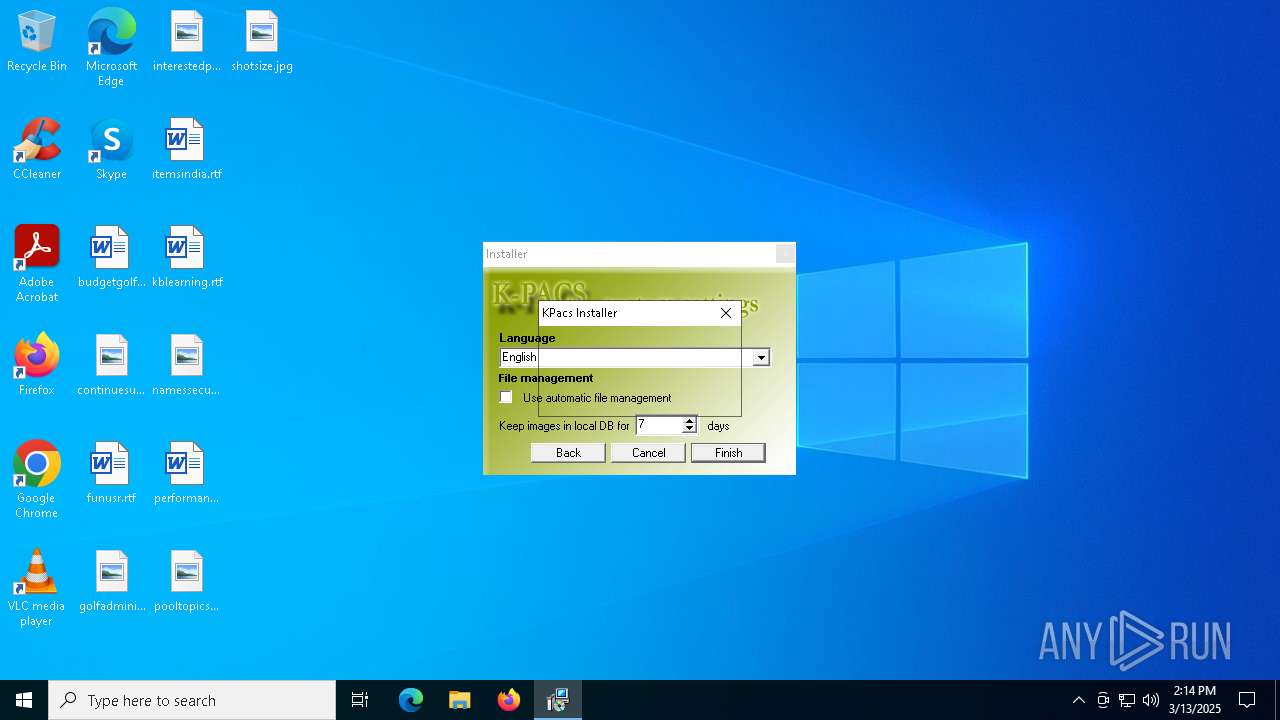
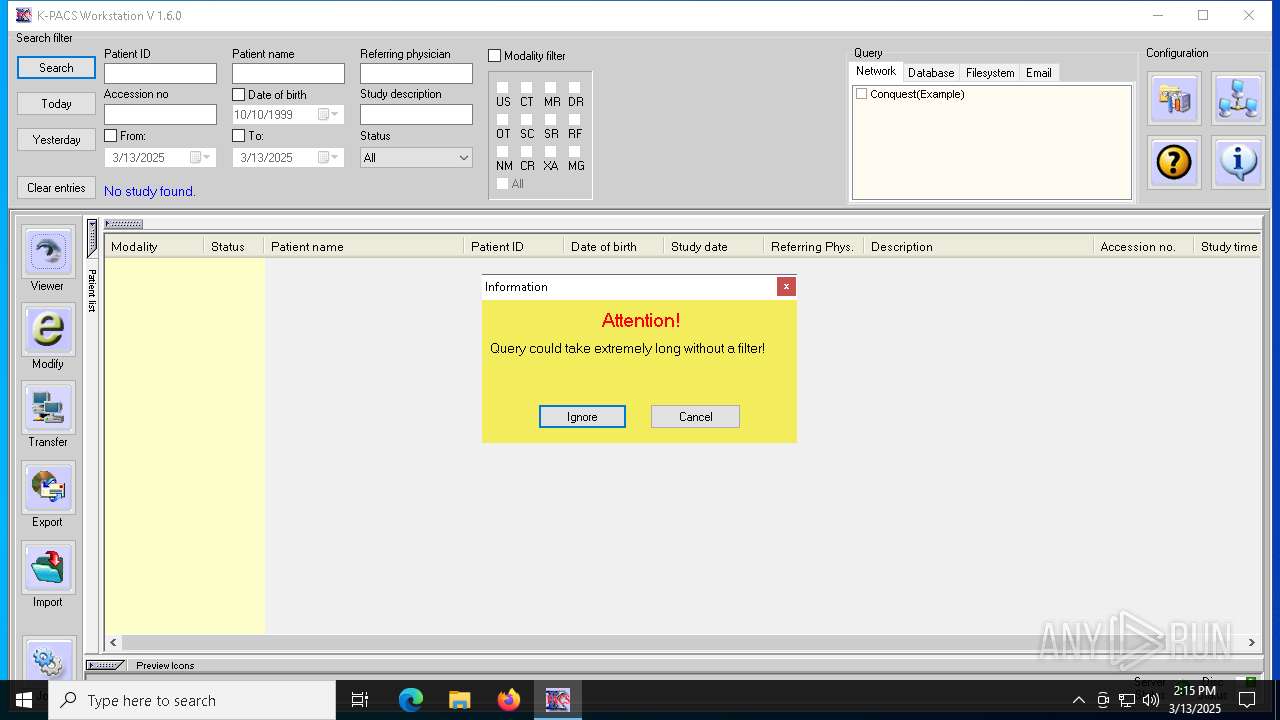
| File name: | K-Pacs Installer V1.6.0 English.exe |
| Full analysis: | https://app.any.run/tasks/6c4a9f39-1720-404f-8d3a-21fb82c653bf |
| Verdict: | Malicious activity |
| Analysis date: | March 13, 2025, 14:11:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive, 4 sections |
| MD5: | 4ACD7DF0A52701F962C5B799504DEDD4 |
| SHA1: | B3BDF037F657F3D8BD8C26735707D4C9EEA7021A |
| SHA256: | 5342831C0B2B50D93F558B167B5962E3E422FC43EE93E8A03DE0B2BF2CD324D9 |
| SSDEEP: | 98304:pjXPcdpTu9NqynZUz3GGysmLd/MusPLUHhYvo6kaM9ibRHcjNCJknx3VhhxTIlwv:nlmug7sRG/SJF |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
Reads security settings of Internet Explorer
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
Reads Internet Explorer settings
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
Executable content was dropped or overwritten
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
- Install-Eng.exe (PID: 8052)
There is functionality for taking screenshot (YARA)
- Install-Eng.exe (PID: 8052)
- k-pacs.exe (PID: 7996)
- kpserver.exe (PID: 5452)
Starts CMD.EXE for commands execution
- Install-Eng.exe (PID: 8052)
Executing commands from a ".bat" file
- Install-Eng.exe (PID: 8052)
INFO
Reads the computer name
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
- Install-Eng.exe (PID: 8052)
Checks supported languages
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
- k-pacs.exe (PID: 7996)
- Install-Eng.exe (PID: 8052)
The sample compiled with german language support
- Install-Eng.exe (PID: 8052)
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
Checks proxy server information
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
The sample compiled with english language support
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
- Install-Eng.exe (PID: 8052)
Process checks computer location settings
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
- k-pacs.exe (PID: 7996)
Create files in a temporary directory
- K-Pacs Installer V1.6.0 English.exe (PID: 7428)
- Install-Eng.exe (PID: 8052)
Compiled with Borland Delphi (YARA)
- Install-Eng.exe (PID: 8052)
- k-pacs.exe (PID: 7996)
- conhost.exe (PID: 6640)
- kpserver.exe (PID: 5452)
- slui.exe (PID: 2088)
Reads the software policy settings
- slui.exe (PID: 2088)
Creates files or folders in the user directory
- Install-Eng.exe (PID: 8052)
Manual execution by a user
- k-pacs.exe (PID: 7996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.3) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.1) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Win32 Executable Watcom C++ (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2005:06:26 09:05:32+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 77824 |
| InitializedDataSize: | 22016 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
149
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2088 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5452 | "C:\KPacs\K-PACS-Server\KPServer.exe" +x= -dw -od "C:\KPacs\Imagebox" -aet KPServer 104 | C:\KPacs\K-Pacs-Server\kpserver.exe | — | k-pacs.exe | |||||||||||
User: admin Company: IMAGE Information Systems Ltd. Integrity Level: MEDIUM Description: StoreSCP Application Version: 2, 5, 0, 1 Modules
| |||||||||||||||
| 6640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | kpserver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7344 | "C:\Users\admin\AppData\Local\Temp\K-Pacs Installer V1.6.0 English.exe" | C:\Users\admin\AppData\Local\Temp\K-Pacs Installer V1.6.0 English.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7428 | "C:\Users\admin\AppData\Local\Temp\K-Pacs Installer V1.6.0 English.exe" | C:\Users\admin\AppData\Local\Temp\K-Pacs Installer V1.6.0 English.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7688 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7752 | C:\WINDOWS\system32\cmd.exe /c C:\Users\admin\AppData\Local\Temp\uisF6AC.bat | C:\Windows\SysWOW64\cmd.exe | — | Install-Eng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7996 | "C:\KPacs\k-pacs.exe" | C:\KPacs\k-pacs.exe | — | explorer.exe | |||||||||||
User: admin Company: IMAGE Information Systems Ltd. Integrity Level: MEDIUM Description: Free DICOM Workstation Version: 1.6.0.3 Modules
| |||||||||||||||
| 8052 | "C:\Users\admin\AppData\Local\Temp\Install-Eng.exe" | C:\Users\admin\AppData\Local\Temp\Install-Eng.exe | K-Pacs Installer V1.6.0 English.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 876
Read events
2 852
Write events
22
Delete events
2
Modification events
| (PID) Process: | (7428) K-Pacs Installer V1.6.0 English.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7428) K-Pacs Installer V1.6.0 English.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7428) K-Pacs Installer V1.6.0 English.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7428) K-Pacs Installer V1.6.0 English.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (7428) K-Pacs Installer V1.6.0 English.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (8052) Install-Eng.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\dicom-tools\qrscp |
| Operation: | write | Name: | checkstate |
Value: 0\ | |||
| (PID) Process: | (8052) Install-Eng.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\dicom-tools\qrscp\compress |
| Operation: | write | Name: | comp |
Value: 1 | |||
| (PID) Process: | (8052) Install-Eng.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\dicom-tools\qrscp\compress |
| Operation: | write | Name: | jpeg |
Value: ja | |||
| (PID) Process: | (8052) Install-Eng.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\dicom-tools\qrscp\crypt |
| Operation: | write | Name: | anonym |
Value: nein | |||
| (PID) Process: | (8052) Install-Eng.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\dicom-tools\qrscp\crypt |
| Operation: | write | Name: | crypt |
Value: nein | |||
Executable files
40
Suspicious files
1
Text files
20
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7428 | K-Pacs Installer V1.6.0 English.exe | C:\Users\admin\AppData\Local\Temp\findscu.exe | executable | |
MD5:A0BA3355014DF8E21FF69BFAAB175328 | SHA256:031310F25949A8D90159AB5F050FFD0CADF6EFC65F892FAAB27586EE9819E263 | |||
| 7428 | K-Pacs Installer V1.6.0 English.exe | C:\Users\admin\AppData\Local\Temp\English.ini | text | |
MD5:5B690614D497DE2FB9B6F9BC67011B9B | SHA256:B7CF03CBACDBC635D7F7B6F459C6CD1F4AF0C27C235FBA59D6301D8F65C70C1F | |||
| 7428 | K-Pacs Installer V1.6.0 English.exe | C:\Users\admin\AppData\Local\Temp\German.ini | text | |
MD5:F3003E90E4F2D56C1ED1897AC355A232 | SHA256:638A0280F490BA3D965F7B494219A337A5469F5DBD3E80B5FE1E06DAA65F3564 | |||
| 7428 | K-Pacs Installer V1.6.0 English.exe | C:\Users\admin\AppData\Local\Temp\WindowsGer.txt | text | |
MD5:C25576F273217A39C2A2285AB4E748B6 | SHA256:593E11A375B4FFB8D3FA30F0BC996CD8BA9C3D3F10454E6D2F131EB0E3E2BDC0 | |||
| 7428 | K-Pacs Installer V1.6.0 English.exe | C:\Users\admin\AppData\Local\Temp\WindowsEng.txt | text | |
MD5:E26CB06775234B104EEF2CB5D1C139D5 | SHA256:CE265761E3AC073EAE1561FF6F23B52F9E6EFF80D921257E4328C64E8390FA2B | |||
| 7428 | K-Pacs Installer V1.6.0 English.exe | C:\Users\admin\AppData\Local\Temp\dcmcjpeg.exe | executable | |
MD5:1D100A47B9206B75E432874B741E55E5 | SHA256:E0902AB66534B0C8B00BEFF76739379BD094FD81A9A7CA10B8463A500CBE8D43 | |||
| 7428 | K-Pacs Installer V1.6.0 English.exe | C:\Users\admin\AppData\Local\Temp\adminEnglish.ini | text | |
MD5:7730CA15DCCA99931A62D9B7C6F070B4 | SHA256:48997971DCB2E3DA0EB759E41817981754333A6D240F8025024FC5D9F3A56C92 | |||
| 7428 | K-Pacs Installer V1.6.0 English.exe | C:\Users\admin\AppData\Local\Temp\DBregistration.dll | executable | |
MD5:004D7F139945736A0DFB040245D8E65A | SHA256:135F09A08478ACB9A7F2FC779853B1A95A17BBCB5B1140FF0B2EFB96A18CC96C | |||
| 7428 | K-Pacs Installer V1.6.0 English.exe | C:\Users\admin\AppData\Local\Temp\dcmdump.exe | executable | |
MD5:8E950C83752DA090388D066A11D738FC | SHA256:5F1C2EF779E043E3F7549A80208F8C45C9151A17C9AD1D5C079993EA20F366E1 | |||
| 7428 | K-Pacs Installer V1.6.0 English.exe | C:\Users\admin\AppData\Local\Temp\movescu.exe | executable | |
MD5:4E9493851869B0CFEEC407845D38DE57 | SHA256:DE3274B134D4316BAB677B1BE0190E02F5871C713FCA88E122470E4D93E3C585 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
26
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.164.40:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.40:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4944 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7596 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4944 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.40:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.40:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.16.164.40:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.40:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |