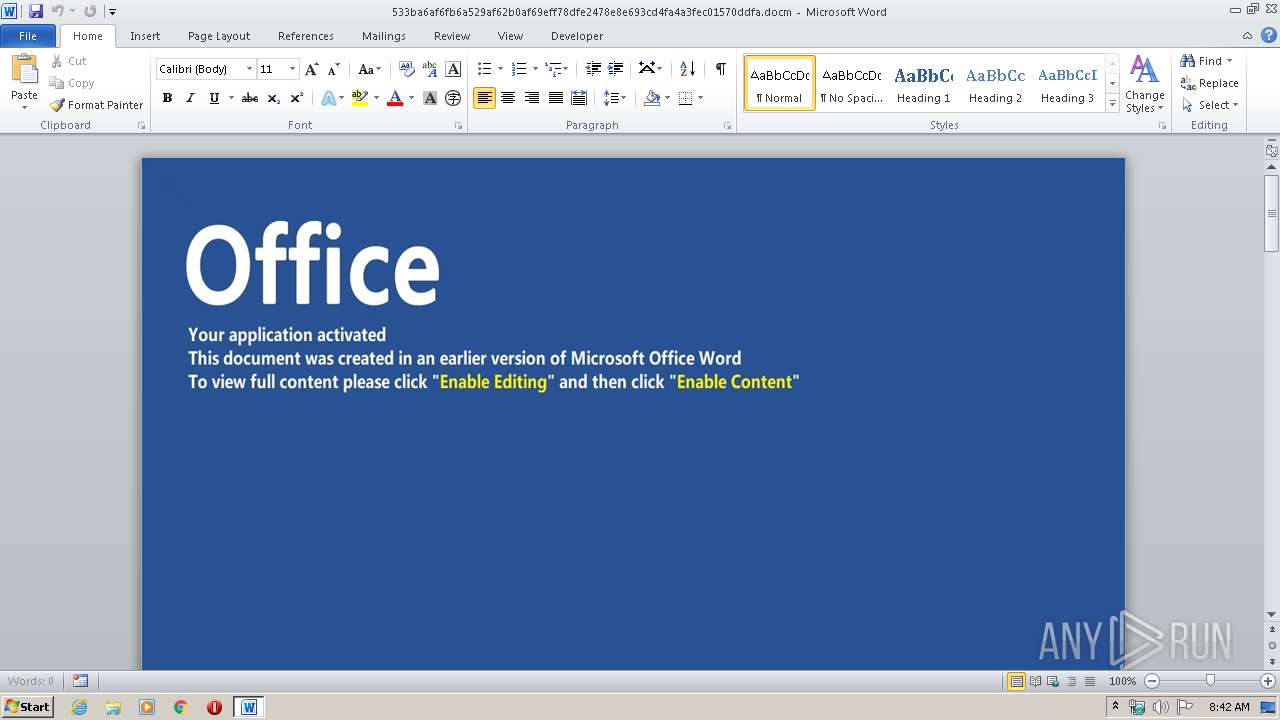
| File name: | 533ba6af6fb6a529af62b0af69eff78dfe2478e8e693cd4fa4a3fec01570ddfa |
| Full analysis: | https://app.any.run/tasks/c2e32273-98a8-4b87-b51a-17bb89074508 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 07:41:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 05B07832E9E004F72B0A599EDE0DBBCD |
| SHA1: | 0E4490C6A714C413C52CA25D7FCA47DA85C8E4E0 |
| SHA256: | 533BA6AF6FB6A529AF62B0AF69EFF78DFE2478E8E693CD4FA4A3FEC01570DDFA |
| SSDEEP: | 6144:b8GW+Yb57dvQAIWK7knpCdX/fbM5mboFg2xynDsXODCTb922fzuSsvtidEk/KCc:bUDdvfIp7XN/TqRxv++fYmyvti9KCc |
MALICIOUS
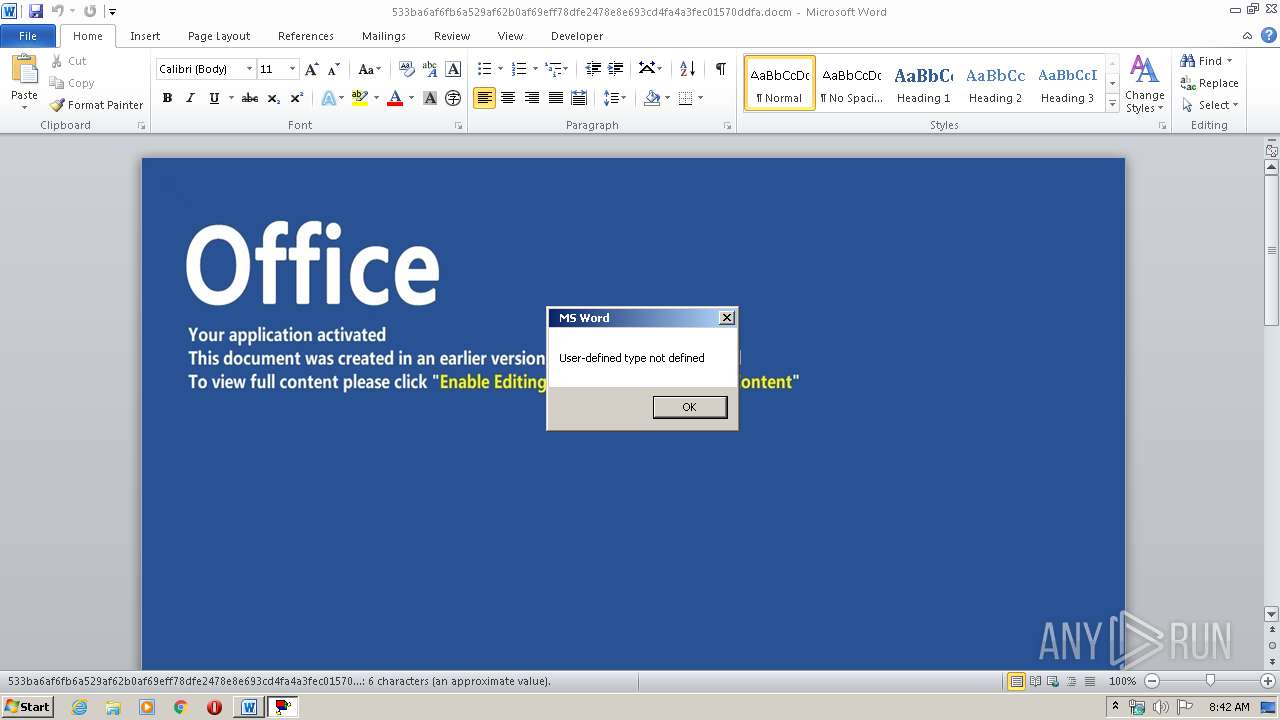
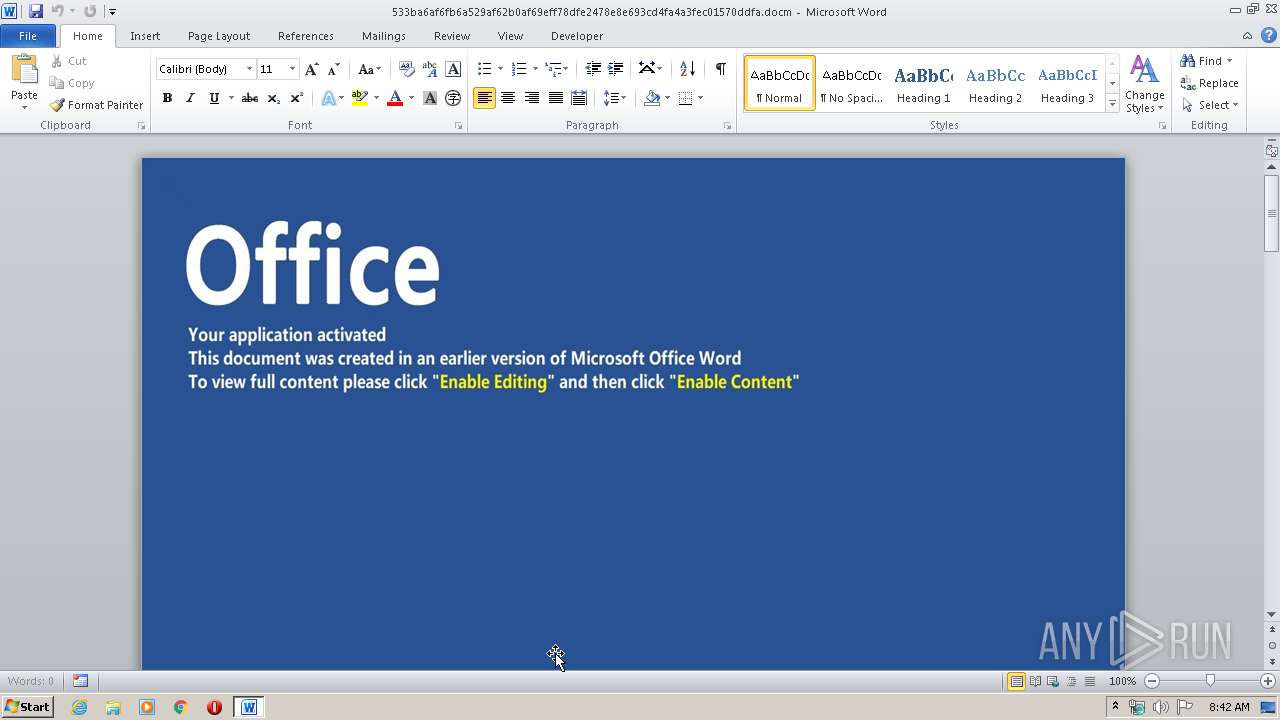
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2956)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2956)
SUSPICIOUS
Executes scripts
- cmd.exe (PID: 3824)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2956)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0xfefd9a9e |
| ZipCompressedSize: | 482 |
| ZipUncompressedSize: | 2010 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Creator: | - |
XML
| LastModifiedBy: | - |
|---|---|
| RevisionNumber: | 1 |
| CreateDate: | 2020:01:13 01:40:00Z |
| ModifyDate: | 2020:02:25 13:14:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | 1 |
| Characters: | 7 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 7 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 14 |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1444 | cscript //nologo C:\AprilReport\List1.jse | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2956 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\533ba6af6fb6a529af62b0af69eff78dfe2478e8e693cd4fa4a3fec01570ddfa.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3824 | cmd /c C:\AprilReport\LogsTsg\LogsTsg7\LogsTsg8\List1.bat | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 038
Read events
865
Write events
158
Delete events
15
Modification events
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | !$2 |
Value: 212432008C0B0000010000000000000000000000 | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6C01.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF78E2F419F48D7E9F.TMP | — | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFFEE8BF0E2B7D3FC4.TMP | — | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF43589D36E8CC7AC9.TMP | — | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\AprilReport\LogsTsg\LogsTsg7\LogsTsg8\List1.bat | text | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\AprilReport\List1.jse | text | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$3ba6af6fb6a529af62b0af69eff78dfe2478e8e693cd4fa4a3fec01570ddfa.docm | pgc | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report