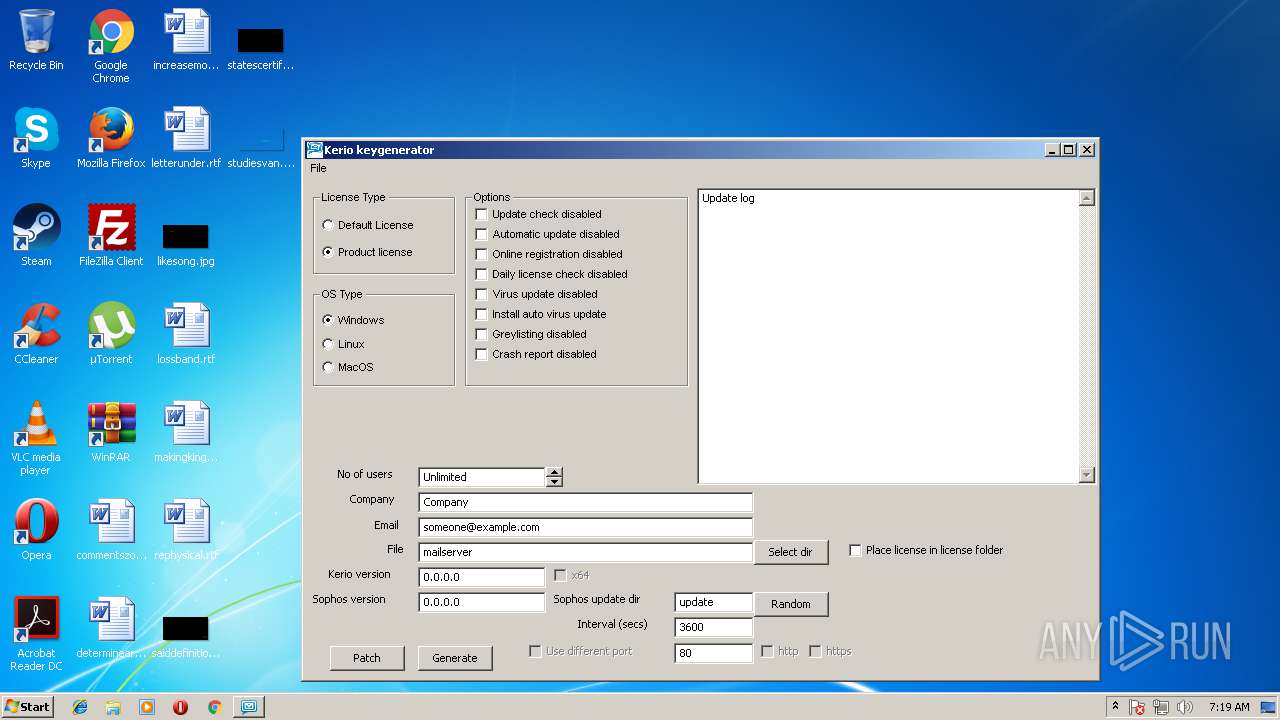
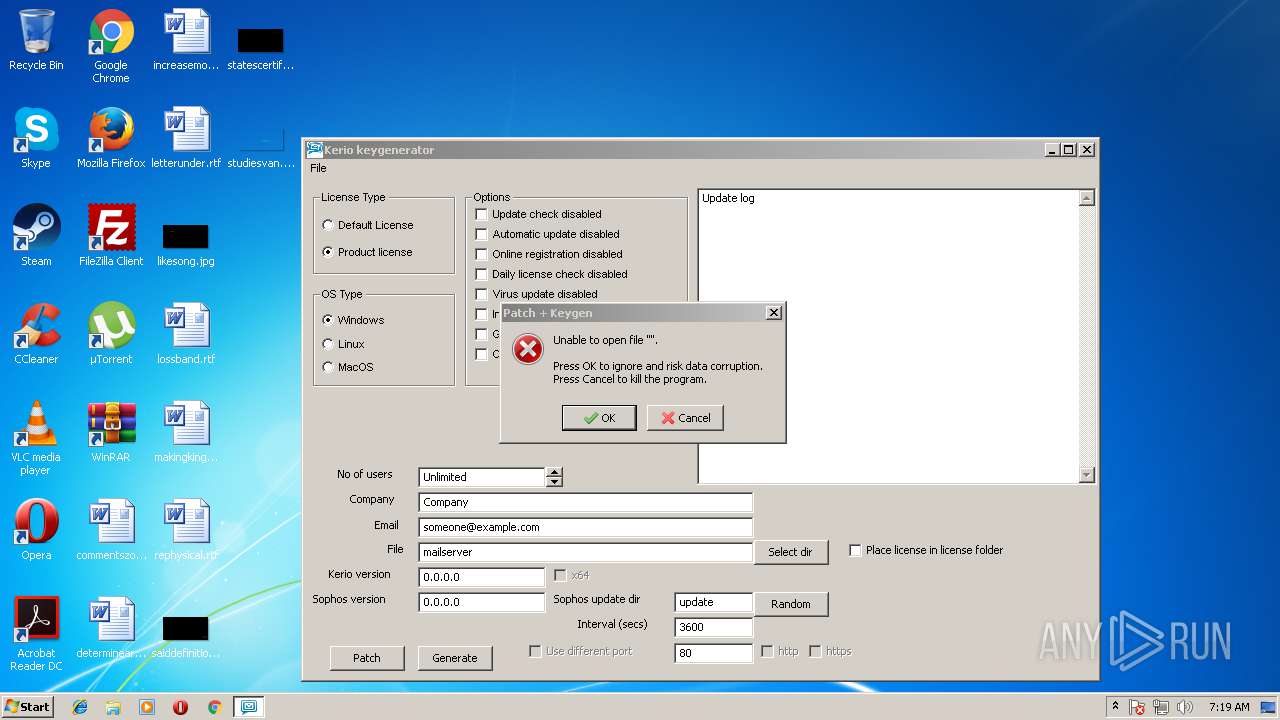
| File name: | Patch + Keygen.exe |
| Full analysis: | https://app.any.run/tasks/e7c39dbe-7380-4d1a-ad9b-7820d13b8815 |
| Verdict: | Malicious activity |
| Analysis date: | August 30, 2018, 06:18:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | A145B5FB32C2BC4BC9FE78F10910957C |
| SHA1: | 76E19ED9FE2F796842D5B0D70B07E0FE374E5B95 |
| SHA256: | 533A3324C5A87E050F32E136BF7EC996D57A6A5BF9CD474C1E7D3FC0D6E9D3AD |
| SSDEEP: | 49152:FvVxD7avJ9SrK5OkXESczHLCfAnwvxRIS4gJ3gO9W4VRtN:dVxPalZXyDLCfAwF4a3nW4xN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates a software uninstall entry
- 3.5.3_44494.exe (PID: 4020)
Creates files in the user directory
- 3.5.3_44494.exe (PID: 4020)
- uTorrent.exe (PID: 2684)
- uTorrent.exe (PID: 2348)
Starts Internet Explorer
- uTorrent.exe (PID: 2348)
Starts itself from another location
- 3.5.3_44494.exe (PID: 4020)
Reads Internet Cache Settings
- uTorrent.exe (PID: 2348)
- utorrentie.exe (PID: 1892)
Changes IE settings (feature browser emulation)
- uTorrent.exe (PID: 2348)
Executable content was dropped or overwritten
- 3.5.3_44494.exe (PID: 4020)
INFO
Dropped object may contain URL's
- uTorrent.exe (PID: 2684)
- 3.5.3_44494.exe (PID: 4020)
- uTorrent.exe (PID: 2348)
Creates files in the user directory
- WINWORD.EXE (PID: 2616)
Reads Internet Cache Settings
- iexplore.exe (PID: 2732)
Changes internet zones settings
- iexplore.exe (PID: 2860)
Reads internet explorer settings
- iexplore.exe (PID: 2732)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ 5.0 (34) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (23.3) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (17.5) |
| .exe | | | Win64 Executable (generic) (15.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.62 |
| CodeSize: | 1480112 |
| InitializedDataSize: | 359036 |
| UninitializedDataSize: | 20500 |
| EntryPoint: | 0x16a580 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.0.58 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
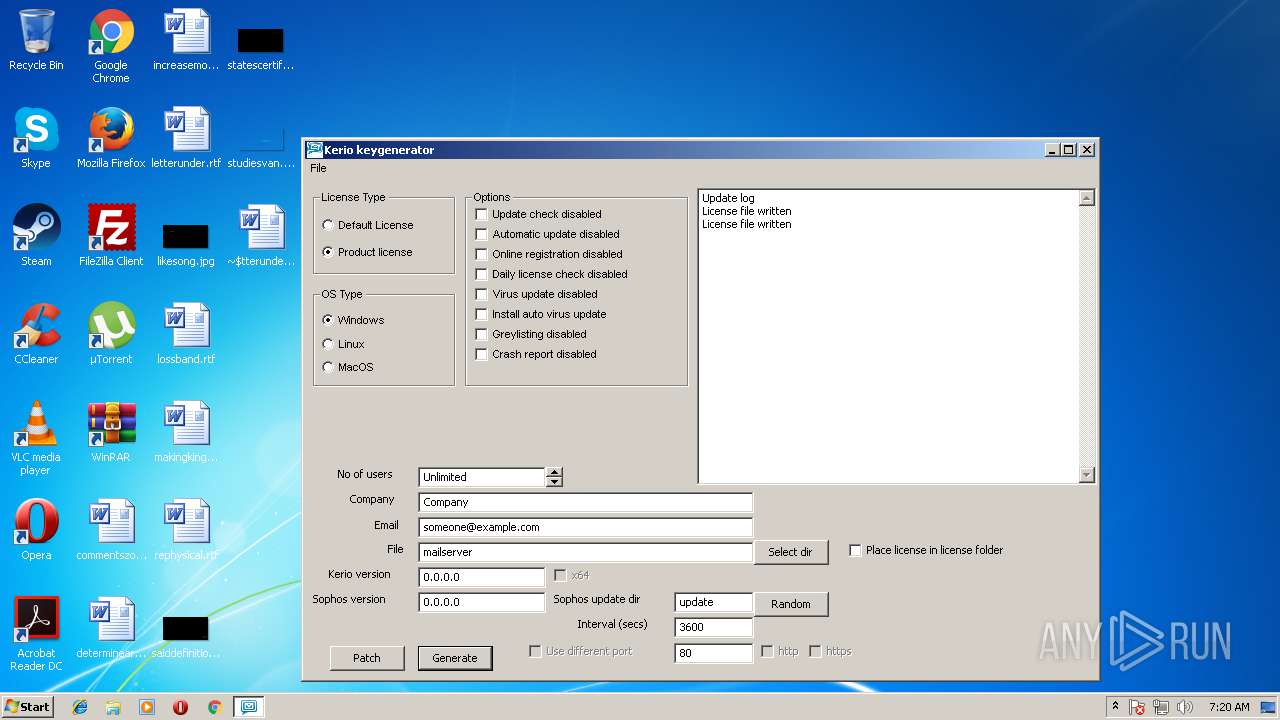
| Comments: | Kerio Keygenerator |
| CompanyName: | Kerio Rulez |
| FileDescription: | Kerio Keygenerator |
| InternalName: | KerioKeyGen |
| LegalCopyright: | None |
| ProductVersion: | - |
| FileVersion: | 1.1.0.58 |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | - |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Jan-1970 00:00:00 |
| Detected languages: |
|
| Comments: | Kerio Keygenerator |
| CompanyName: | Kerio Rulez |
| FileDescription: | Kerio Keygenerator |
| InternalName: | KerioKeyGen |
| LegalCopyright: | None |
| ProductVersion: | - |
| FileVersion: | 1.1.0.58 |
| LegalTrademarks: | - |
| OriginalFilename: | - |
| ProductName: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 01-Jan-1970 00:00:00 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x001695B0 | 0x00169600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.99607 |
.data | 0x0016B000 | 0x00057A7C | 0x00057C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.60042 |
.bss | 0x001C3000 | 0x00005014 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.CRT | 0x001C9000 | 0x00000004 | 0x00000200 | IMAGE_SCN_MEM_DISCARDABLE | 0 |
.idata | 0x001CA000 | 0x000030A0 | 0x00003200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.97521 |
.rsrc | 0x001CE000 | 0x000D5868 | 0x000D5A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.2715 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.20197 | 740 | UNKNOWN | UNKNOWN | RT_VERSION |
2 | 3.51492 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 3.47072 | 1736 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 2.94365 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 4.14746 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 4.54727 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 4.627 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
8 | 3.72109 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
LAZ_PIC_DIALOG_TEMPLATE | 1.96928 | 50 | UNKNOWN | UNKNOWN | RT_DIALOG |
AVUPSERV | 6.28503 | 813056 | UNKNOWN | English - United States | RT_RCDATA |
Imports
advapi32.dll |
comctl32.dll |
comdlg32.dll |
gdi32.dll |
kernel32.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
user32.dll |
version.dll |
Total processes
46
Monitored processes
10
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1276 | "C:\Users\admin\AppData\Roaming\uTorrent\updates\3.5.3_44494\utorrentie.exe" uTorrent_2348_00BD1D30_705423973 µTorrent4823DF041B09 uTorrent | C:\Users\admin\AppData\Roaming\uTorrent\updates\3.5.3_44494\utorrentie.exe | — | uTorrent.exe | |||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: LOW Description: WebHelper Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 1468 | "C:\Users\admin\AppData\Local\Temp\Patch + Keygen.exe" | C:\Users\admin\AppData\Local\Temp\Patch + Keygen.exe | — | explorer.exe | |||||||||||
User: admin Company: Kerio Rulez Integrity Level: MEDIUM Description: Kerio Keygenerator Exit code: 3221226540 Version: 1.1.0.58 Modules
| |||||||||||||||
| 1892 | "C:\Users\admin\AppData\Roaming\uTorrent\updates\3.5.3_44494\utorrentie.exe" uTorrent_2348_00BD1C00_912563215 µTorrent4823DF041B09 uTorrent | C:\Users\admin\AppData\Roaming\uTorrent\updates\3.5.3_44494\utorrentie.exe | — | uTorrent.exe | |||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: LOW Description: WebHelper Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
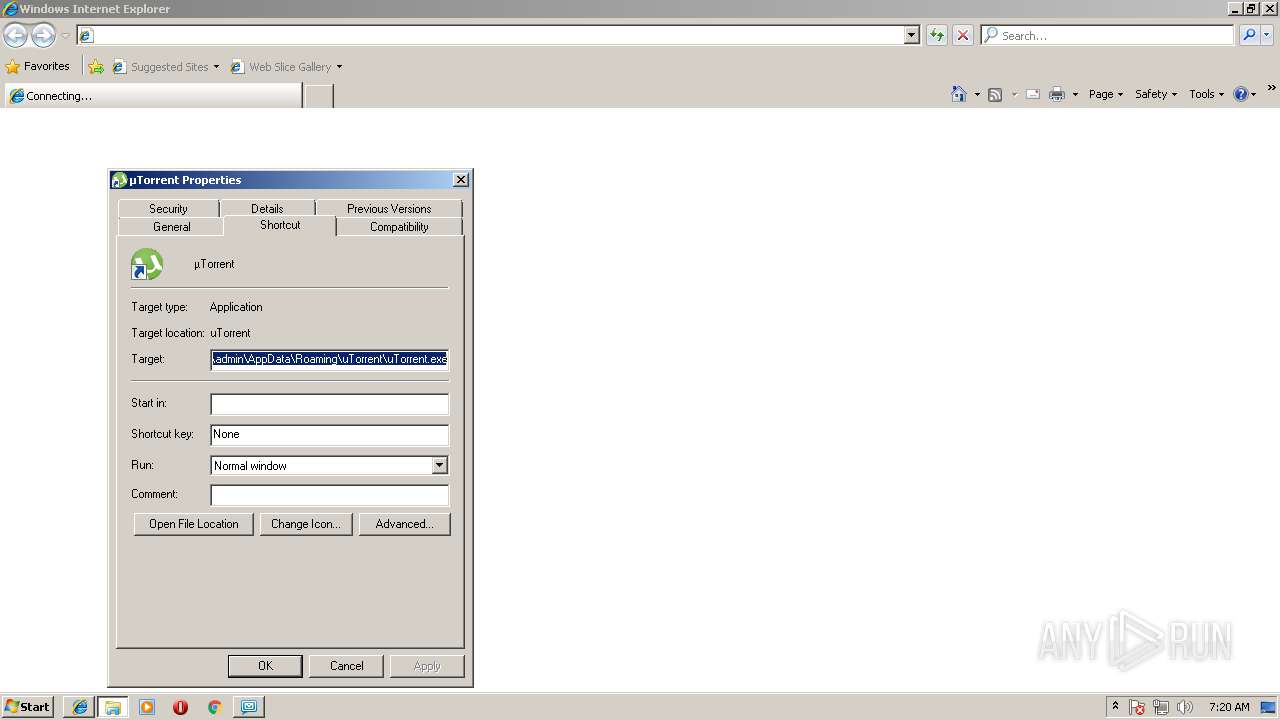
| 2348 | "C:\Users\admin\AppData\Roaming\uTorrent\uTorrent.exe" /RELOCATED | C:\Users\admin\AppData\Roaming\uTorrent\uTorrent.exe | 3.5.3_44494.exe | ||||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: MEDIUM Description: µTorrent Exit code: 0 Version: 3.5.3.44494 Modules
| |||||||||||||||
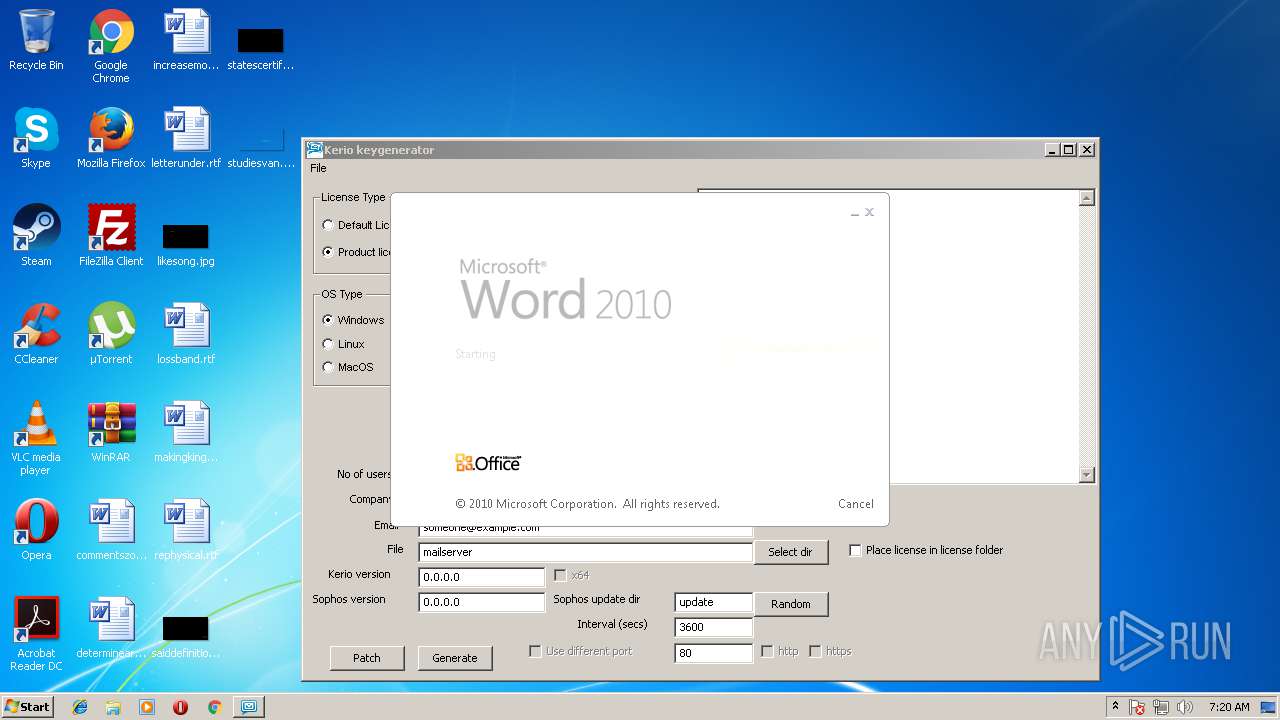
| 2616 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\letterunder.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2684 | "C:\Users\admin\AppData\Roaming\uTorrent\uTorrent.exe" | C:\Users\admin\AppData\Roaming\uTorrent\uTorrent.exe | explorer.exe | ||||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: MEDIUM Description: µTorrent Exit code: 0 Version: 3.5.1.44332 Modules
| |||||||||||||||
| 2732 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2860 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2860 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | — | uTorrent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3864 | "C:\Users\admin\AppData\Local\Temp\Patch + Keygen.exe" | C:\Users\admin\AppData\Local\Temp\Patch + Keygen.exe | explorer.exe | ||||||||||||
User: admin Company: Kerio Rulez Integrity Level: HIGH Description: Kerio Keygenerator Exit code: 0 Version: 1.1.0.58 Modules
| |||||||||||||||
| 4020 | "C:\Users\admin\AppData\Roaming\uTorrent\updates\3.5.3_44494.exe" /LAUNCHED | C:\Users\admin\AppData\Roaming\uTorrent\updates\3.5.3_44494.exe | uTorrent.exe | ||||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: MEDIUM Description: µTorrent Exit code: 0 Version: 3.5.3.44494 Modules
| |||||||||||||||
Total events
1 834
Read events
1 708
Write events
115
Delete events
11
Modification events
| (PID) Process: | (2616) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | w7v |
Value: 77377600380A0000010000000000000000000000 | |||
| (PID) Process: | (2616) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2616) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2616) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1293811734 | |||
| (PID) Process: | (2616) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1293811816 | |||
| (PID) Process: | (2616) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1293811817 | |||
| (PID) Process: | (2616) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | FontInfoCacheW |
Value: 6000000060000000F5FFFFFF000000000000000000000000BC02000000000000004000225400610068006F006D006100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000D0000000B000000020000000200000000000000060000001A000000BC0200000000000060000000600000002000FDFF1F0020000000002700000000FF2E00E15B6000C0290000000000000001000000000028200700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000D0000000B0000000200000002000000000000000500000017000000900100000000000060000000600000002000FDFF1F0020000000002700000000FF2E00E15B6000C02900000000000000010000000000282006000000F7FFFFFF0000000000000000000000009001000000000000004000225400610068006F006D006100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000B000000090000000200000002000000000000000400000013000000900100000000000060000000600000002000FDFF1F0020000000002700000000FF2E00E15B6000C02900000000000000010000000000282005000000 | |||
| (PID) Process: | (2616) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 380A00009409D17E2940D40100000000 | |||
| (PID) Process: | (2616) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | `8v |
Value: 60387600380A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2616) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | `8v |
Value: 60387600380A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
Executable files
1
Suspicious files
16
Text files
8
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2616 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR17D7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2616 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{92CBBC77-A285-4AA0-9E42-9CA198713885}.tmp | — | |
MD5:— | SHA256:— | |||
| 2616 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{8E5E5FF9-17CE-4ABF-8925-E0F3D242B217}.tmp | — | |
MD5:— | SHA256:— | |||
| 2684 | uTorrent.exe | C:\Users\admin\AppData\Local\Temp\utt41D5.tmp | — | |
MD5:— | SHA256:— | |||
| 2684 | uTorrent.exe | C:\Users\admin\AppData\Local\Temp\Cab4233.tmp | — | |
MD5:— | SHA256:— | |||
| 2684 | uTorrent.exe | C:\Users\admin\AppData\Local\Temp\Tar4234.tmp | — | |
MD5:— | SHA256:— | |||
| 2684 | uTorrent.exe | C:\Users\admin\AppData\Local\Temp\Cab4235.tmp | — | |
MD5:— | SHA256:— | |||
| 2684 | uTorrent.exe | C:\Users\admin\AppData\Local\Temp\Tar4236.tmp | — | |
MD5:— | SHA256:— | |||
| 2684 | uTorrent.exe | C:\Users\admin\AppData\Local\Temp\Cab42F3.tmp | — | |
MD5:— | SHA256:— | |||
| 2684 | uTorrent.exe | C:\Users\admin\AppData\Local\Temp\Tar42F4.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
41
DNS requests
15
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2348 | uTorrent.exe | GET | — | 69.164.0.0:80 | http://cdn.ap.bittorrent.com/control/tags/ut.json | US | — | — | shared |
2732 | iexplore.exe | GET | — | 178.79.251.129:80 | http://cdn.bitmedianetwork.com/network/5682.js | GB | — | — | suspicious |
2348 | uTorrent.exe | GET | — | 173.254.195.58:80 | http://update.bittorrent.com/time.php | US | — | — | whitelisted |
— | — | GET | — | 178.79.251.129:80 | http://cdn.bitmedianetwork.com/favicon.ico | GB | — | — | suspicious |
— | — | GET | — | 87.248.214.163:80 | http://www.bt.co/assets/js/3p/ie8.js | IT | — | — | whitelisted |
2684 | uTorrent.exe | POST | — | 174.129.255.167:80 | http://i-31.b-44332.ut.bench.utorrent.com/e?i=31 | US | — | — | malicious |
2348 | uTorrent.exe | POST | — | 54.235.208.27:80 | http://i-29.b-44494.ut.bench.utorrent.com/e?i=29 | US | — | — | malicious |
2732 | iexplore.exe | GET | 200 | 178.79.251.129:80 | http://cdn.bitmedianetwork.com/network/r.html?u=ue1-8427979be7984a8ea13ffc1e9a9fcded&next=http://utorrent.com/prodnews&osv=1DB10106&iev=8&geo=US&lang=en&ver=3%2e5%2e3%2e1%2e44494 | GB | html | 1.20 Kb | suspicious |
— | — | GET | 200 | 69.164.0.0:80 | http://cdn.ap.bittorrent.com/control/feature/tags/ut.json | US | text | 2.11 Kb | shared |
2860 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2348 | uTorrent.exe | 54.230.44.15:443 | now.bt.co | Amazon.com, Inc. | US | unknown |
— | — | 67.215.246.10:6881 | router.bittorrent.com | QuadraNet, Inc | US | suspicious |
2348 | uTorrent.exe | 82.221.103.244:6881 | router.utorrent.com | Thor Data Center ehf | IS | suspicious |
2684 | uTorrent.exe | 13.107.4.50:80 | www.download.windowsupdate.com | Microsoft Corporation | US | whitelisted |
2684 | uTorrent.exe | 174.129.255.167:80 | i-31.b-44332.ut.bench.utorrent.com | Amazon.com, Inc. | US | whitelisted |
2348 | uTorrent.exe | 54.230.44.219:80 | now.bt.co | Amazon.com, Inc. | US | unknown |
— | — | 167.99.128.141:25555 | — | — | US | unknown |
2860 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2732 | iexplore.exe | 178.79.251.129:80 | cdn.bitmedianetwork.com | Limelight Networks, Inc. | GB | malicious |
2348 | uTorrent.exe | 54.235.208.27:80 | i-31.b-44332.ut.bench.utorrent.com | Amazon.com, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.download.windowsupdate.com |
| whitelisted |
router.utorrent.com |
| whitelisted |
router.bittorrent.com |
| shared |
i-31.b-44332.ut.bench.utorrent.com |
| malicious |
apps.bittorrent.com |
| whitelisted |
now.bt.co |
| whitelisted |
utclient.utorrent.com |
| shared |
www.bing.com |
| whitelisted |
cdn.bitmedianetwork.com |
| suspicious |
update.bittorrent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2348 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
2348 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
2348 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
2348 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
2348 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
2348 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
— | — | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |