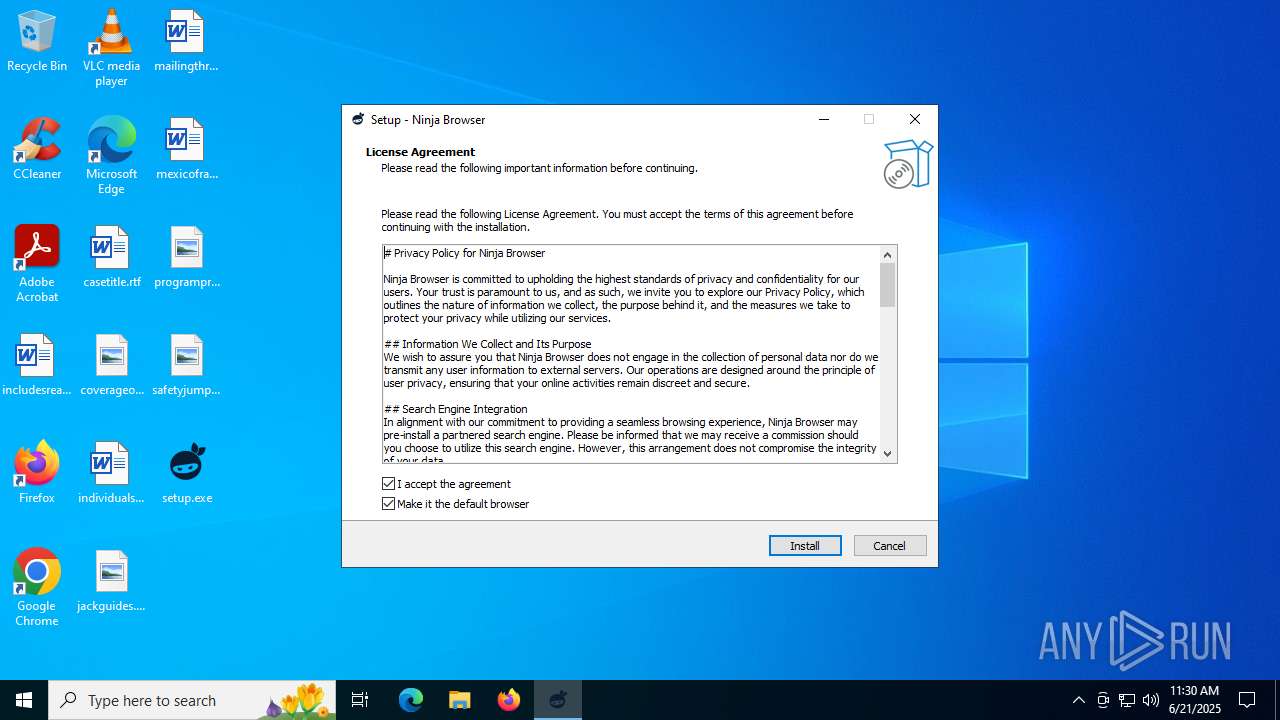
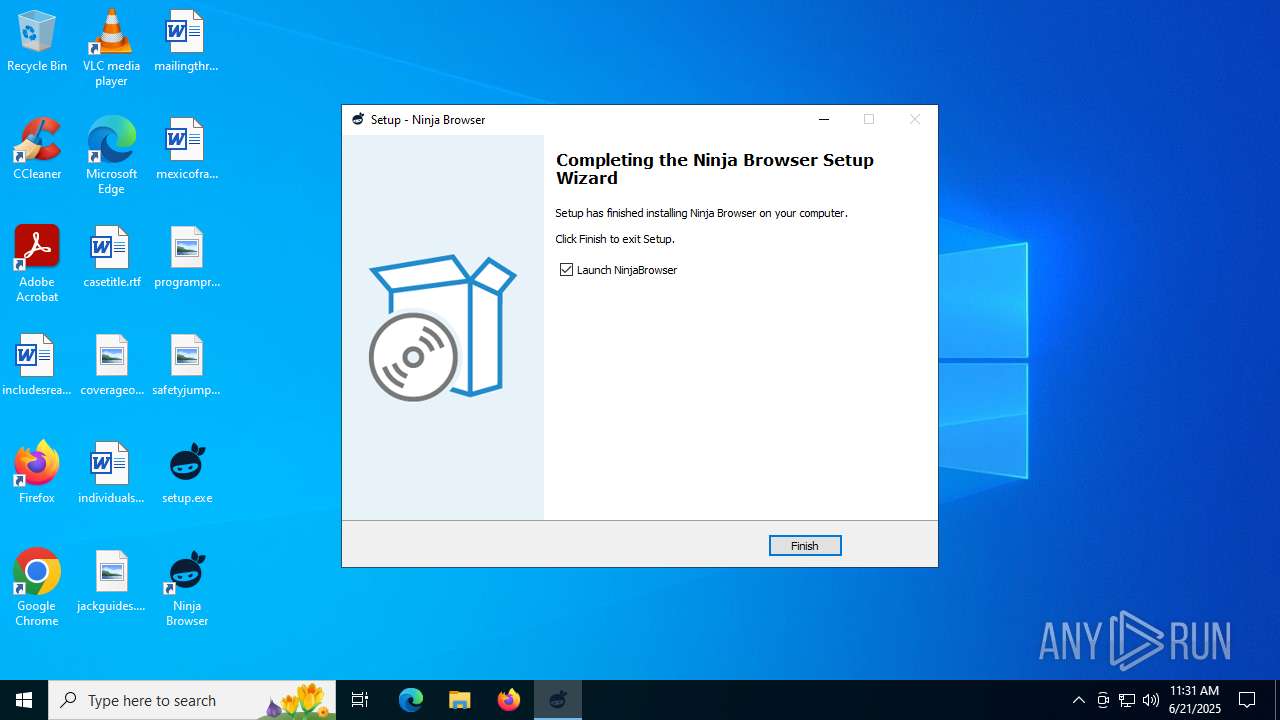
| File name: | setup.exe |
| Full analysis: | https://app.any.run/tasks/3d570e66-2a8e-4910-9c1d-51b0573d4d9f |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 11:30:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | BE9CD5055FB680B27F8B0F475B8A0A86 |
| SHA1: | 57D87D973243A0641394DDA7D0FB701C3FC0E25B |
| SHA256: | 5329D4B1D8AA6B3E90176927C2597F28C7173F9293304504F9C3A426C821C93D |
| SSDEEP: | 98304:f6GavilJWDoh5wkRK1QcuFLSrs4dWT5I90O6C/e0TSptR:Mh6 |
MALICIOUS
GENERIC has been found (auto)
- setup.exe (PID: 3888)
- setup.tmp (PID: 1720)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2200)
Changes the autorun value in the registry
- setup.exe (PID: 1180)
Uses Task Scheduler to run other applications
- setup.tmp (PID: 1720)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- mshta.exe (PID: 6460)
- mshta.exe (PID: 3964)
- mshta.exe (PID: 3836)
SUSPICIOUS
Reads security settings of Internet Explorer
- setup.tmp (PID: 516)
- chrmstp.exe (PID: 7724)
Executable content was dropped or overwritten
- setup.exe (PID: 3888)
- setup.exe (PID: 1296)
- setup.tmp (PID: 1720)
- chromium.exe (PID: 1100)
- chromium.exe (PID: 4312)
- setup.exe (PID: 1180)
- setup.exe (PID: 472)
Reads the Windows owner or organization settings
- setup.tmp (PID: 1720)
Creates file in the systems drive root
- chromium.exe (PID: 1100)
- setup.exe (PID: 1180)
- chromium.exe (PID: 4312)
Searches for installed software
- setup.exe (PID: 1180)
- setup.exe (PID: 4080)
- setup.exe (PID: 472)
- chrmstp.exe (PID: 6840)
- chrmstp.exe (PID: 7724)
Creates a software uninstall entry
- setup.exe (PID: 1180)
Application launched itself
- setup.exe (PID: 1180)
- NinjaBrowser.exe (PID: 3956)
- chrmstp.exe (PID: 6840)
INFO
Reads the computer name
- setup.tmp (PID: 516)
- setup.exe (PID: 1296)
- setup.tmp (PID: 1720)
- chromium.exe (PID: 1100)
- setup.exe (PID: 1180)
- chromium.exe (PID: 4312)
- setup.exe (PID: 4080)
- def.exe (PID: 6388)
- def.exe (PID: 1332)
- def.exe (PID: 4372)
- def.exe (PID: 4112)
- NinjaBrowser.exe (PID: 3956)
- def.exe (PID: 4804)
- NinjaBrowser.exe (PID: 5896)
- NinjaBrowser.exe (PID: 1528)
- NinjaBrowser.exe (PID: 3672)
- chrmstp.exe (PID: 7724)
Checks supported languages
- setup.tmp (PID: 516)
- setup.exe (PID: 3888)
- setup.exe (PID: 1296)
- setup.tmp (PID: 1720)
- chromium.exe (PID: 1100)
- setup.exe (PID: 4080)
- chromium.exe (PID: 4312)
- setup.exe (PID: 1180)
- setup.exe (PID: 472)
- def.exe (PID: 6388)
- def.exe (PID: 4804)
- def.exe (PID: 4112)
- def.exe (PID: 4372)
- NinjaBrowser.exe (PID: 3956)
- def.exe (PID: 1332)
- NinjaBrowser.exe (PID: 1528)
- NinjaBrowser.exe (PID: 5896)
- NinjaBrowser.exe (PID: 1208)
- NinjaBrowser.exe (PID: 304)
- NinjaBrowser.exe (PID: 2552)
- NinjaBrowser.exe (PID: 7032)
- NinjaBrowser.exe (PID: 7132)
- NinjaBrowser.exe (PID: 2064)
- NinjaBrowser.exe (PID: 6800)
- NinjaBrowser.exe (PID: 3396)
- NinjaBrowser.exe (PID: 5764)
- NinjaBrowser.exe (PID: 3748)
- NinjaBrowser.exe (PID: 6536)
- NinjaBrowser.exe (PID: 5772)
- NinjaBrowser.exe (PID: 6840)
- NinjaBrowser.exe (PID: 3864)
- NinjaBrowser.exe (PID: 4804)
- NinjaBrowser.exe (PID: 2680)
- NinjaBrowser.exe (PID: 2792)
- NinjaBrowser.exe (PID: 3656)
- NinjaBrowser.exe (PID: 768)
- NinjaBrowser.exe (PID: 1036)
- NinjaBrowser.exe (PID: 3820)
- NinjaBrowser.exe (PID: 1100)
- NinjaBrowser.exe (PID: 3740)
- NinjaBrowser.exe (PID: 1028)
- NinjaBrowser.exe (PID: 2320)
- NinjaBrowser.exe (PID: 3160)
- NinjaBrowser.exe (PID: 320)
- NinjaBrowser.exe (PID: 2664)
- NinjaBrowser.exe (PID: 4104)
- NinjaBrowser.exe (PID: 2120)
- NinjaBrowser.exe (PID: 6360)
- NinjaBrowser.exe (PID: 2804)
- NinjaBrowser.exe (PID: 592)
- NinjaBrowser.exe (PID: 6756)
- NinjaBrowser.exe (PID: 6344)
- NinjaBrowser.exe (PID: 5708)
- NinjaBrowser.exe (PID: 4372)
- NinjaBrowser.exe (PID: 7304)
- NinjaBrowser.exe (PID: 7276)
- NinjaBrowser.exe (PID: 7412)
- NinjaBrowser.exe (PID: 7396)
- NinjaBrowser.exe (PID: 7380)
- NinjaBrowser.exe (PID: 7552)
- NinjaBrowser.exe (PID: 7476)
- NinjaBrowser.exe (PID: 7512)
- NinjaBrowser.exe (PID: 7504)
- NinjaBrowser.exe (PID: 7688)
- NinjaBrowser.exe (PID: 7772)
- NinjaBrowser.exe (PID: 7792)
- NinjaBrowser.exe (PID: 7808)
- NinjaBrowser.exe (PID: 5168)
- NinjaBrowser.exe (PID: 6256)
- NinjaBrowser.exe (PID: 3624)
- NinjaBrowser.exe (PID: 7824)
- NinjaBrowser.exe (PID: 7800)
- NinjaBrowser.exe (PID: 7816)
- NinjaBrowser.exe (PID: 7832)
- NinjaBrowser.exe (PID: 8072)
- NinjaBrowser.exe (PID: 8088)
- NinjaBrowser.exe (PID: 8032)
- NinjaBrowser.exe (PID: 7840)
- NinjaBrowser.exe (PID: 7180)
- NinjaBrowser.exe (PID: 7744)
- NinjaBrowser.exe (PID: 7848)
- NinjaBrowser.exe (PID: 7784)
- NinjaBrowser.exe (PID: 7300)
- NinjaBrowser.exe (PID: 8180)
- NinjaBrowser.exe (PID: 7400)
- NinjaBrowser.exe (PID: 3672)
- chrmstp.exe (PID: 6840)
- chrmstp.exe (PID: 7724)
- NinjaBrowser.exe (PID: 5616)
- NinjaBrowser.exe (PID: 1356)
- NinjaBrowser.exe (PID: 1056)
Create files in a temporary directory
- setup.exe (PID: 3888)
- setup.exe (PID: 1296)
- setup.tmp (PID: 1720)
- chromium.exe (PID: 1100)
- chromium.exe (PID: 4312)
- def.exe (PID: 6388)
- def.exe (PID: 4112)
- def.exe (PID: 4804)
- NinjaBrowser.exe (PID: 3956)
Process checks computer location settings
- setup.tmp (PID: 516)
- NinjaBrowser.exe (PID: 3956)
- NinjaBrowser.exe (PID: 2552)
- NinjaBrowser.exe (PID: 304)
- NinjaBrowser.exe (PID: 7772)
- NinjaBrowser.exe (PID: 8088)
- NinjaBrowser.exe (PID: 7840)
- NinjaBrowser.exe (PID: 7400)
- NinjaBrowser.exe (PID: 8032)
- NinjaBrowser.exe (PID: 7744)
- NinjaBrowser.exe (PID: 7848)
- NinjaBrowser.exe (PID: 8072)
- NinjaBrowser.exe (PID: 8180)
- NinjaBrowser.exe (PID: 7180)
- NinjaBrowser.exe (PID: 1356)
- NinjaBrowser.exe (PID: 1056)
Reads the software policy settings
- setup.tmp (PID: 1720)
Checks proxy server information
- setup.tmp (PID: 1720)
- NinjaBrowser.exe (PID: 3956)
Detects InnoSetup installer (YARA)
- setup.exe (PID: 1296)
- setup.tmp (PID: 516)
- setup.tmp (PID: 1720)
- setup.exe (PID: 3888)
Compiled with Borland Delphi (YARA)
- setup.exe (PID: 3888)
- setup.exe (PID: 1296)
- setup.tmp (PID: 1720)
- setup.tmp (PID: 516)
Creates files in the program directory
- setup.tmp (PID: 1720)
- setup.exe (PID: 4080)
- setup.exe (PID: 1180)
- setup.exe (PID: 472)
The sample compiled with english language support
- setup.tmp (PID: 1720)
- chromium.exe (PID: 1100)
- setup.exe (PID: 1180)
- setup.exe (PID: 472)
- chromium.exe (PID: 4312)
Launching a file from a Registry key
- setup.exe (PID: 1180)
Creates files or folders in the user directory
- setup.exe (PID: 4080)
- NinjaBrowser.exe (PID: 3956)
- NinjaBrowser.exe (PID: 5896)
- chrmstp.exe (PID: 7724)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- setup.tmp (PID: 1720)
Launching a file from Task Scheduler
- setup.tmp (PID: 1720)
Reads Internet Explorer settings
- mshta.exe (PID: 6172)
- mshta.exe (PID: 6460)
- mshta.exe (PID: 3964)
- mshta.exe (PID: 6796)
- mshta.exe (PID: 3836)
- mshta.exe (PID: 6304)
Reads the machine GUID from the registry
- NinjaBrowser.exe (PID: 3956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:01:08 15:36:35+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 684032 |
| InitializedDataSize: | 211456 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa7f98 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.1 |
| ProductVersionNumber: | 3.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Ninja Browser |
| FileDescription: | Ninja Browser Setup |
| FileVersion: | 3.0.0.1 |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Ninja Browser |
| ProductVersion: | 128.0.0.0 |
Total processes
244
Monitored processes
108
Malicious processes
14
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=renderer --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3200,i,8056607956621841649,4755507602206769110,262144 --variations-seed-version --mojo-platform-channel-handle=3224 /prefetch:1 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Version: 137.0.6613.124 Modules
| |||||||||||||||
| 320 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --field-trial-handle=5184,i,8056607956621841649,4755507602206769110,262144 --variations-seed-version --mojo-platform-channel-handle=4504 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 137.0.6613.124 Modules
| |||||||||||||||
| 472 | "C:\Users\admin\AppData\Local\Temp\is-MQEAA.tmp\CR_10A5A.tmp\setup.exe" --install-archive="C:\Users\admin\AppData\Local\Temp\is-MQEAA.tmp\CR_10A5A.tmp\CHROME.PACKED.7Z" --system-level --rename-chrome-exe | C:\Users\admin\AppData\Local\Temp\is-MQEAA.tmp\CR_10A5A.tmp\setup.exe | chromium.exe | ||||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: HIGH Description: Ninja Browser Installer Exit code: 24 Version: 137.0.6613.124 Modules
| |||||||||||||||
| 516 | "C:\Users\admin\AppData\Local\Temp\is-0A4HR.tmp\setup.tmp" /SL5="$40302,932127,896512,C:\Users\admin\Desktop\setup.exe" | C:\Users\admin\AppData\Local\Temp\is-0A4HR.tmp\setup.tmp | — | setup.exe | |||||||||||
User: admin Company: Ninja Browser Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 592 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --field-trial-handle=9148,i,8056607956621841649,4755507602206769110,262144 --variations-seed-version --mojo-platform-channel-handle=9128 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 137.0.6613.124 Modules
| |||||||||||||||
| 768 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --field-trial-handle=4272,i,8056607956621841649,4755507602206769110,262144 --variations-seed-version --mojo-platform-channel-handle=7004 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 137.0.6613.124 Modules
| |||||||||||||||
| 984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --field-trial-handle=4124,i,8056607956621841649,4755507602206769110,262144 --variations-seed-version --mojo-platform-channel-handle=7392 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 137.0.6613.124 Modules
| |||||||||||||||
| 1036 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --field-trial-handle=3996,i,8056607956621841649,4755507602206769110,262144 --variations-seed-version --mojo-platform-channel-handle=4484 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 137.0.6613.124 Modules
| |||||||||||||||
| 1056 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=renderer --extension-process --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=75 --field-trial-handle=8764,i,8056607956621841649,4755507602206769110,262144 --variations-seed-version --mojo-platform-channel-handle=8844 /prefetch:2 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Version: 137.0.6613.124 Modules
| |||||||||||||||
Total events
7 827
Read events
7 658
Write events
163
Delete events
6
Modification events
| (PID) Process: | (1180) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\NinjaBrowser |
| Operation: | write | Name: | InstallerProgress |
Value: 19 | |||
| (PID) Process: | (1180) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\NinjaBrowser |
| Operation: | write | Name: | InstallerProgress |
Value: 25 | |||
| (PID) Process: | (1180) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\NinjaBrowser |
| Operation: | write | Name: | InstallerProgress |
Value: 39 | |||
| (PID) Process: | (1180) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{635EFA6F-08D6-4EC9-BD14-8A0FDE975159}\LocalServer32 |
| Operation: | write | Name: | ServerExecutable |
Value: C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\137.0.6613.124\notification_helper.exe | |||
| (PID) Process: | (1180) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{D133B120-6DB4-4D6B-8BFE-83BF8CA1B1B0} |
| Operation: | write | Name: | AppID |
Value: {D133B120-6DB4-4D6B-8BFE-83BF8CA1B1B0} | |||
| (PID) Process: | (1180) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\{D133B120-6DB4-4D6B-8BFE-83BF8CA1B1B0} |
| Operation: | write | Name: | LocalService |
Value: ChromiumElevationService | |||
| (PID) Process: | (1180) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{B88C45B9-8825-4629-B83E-77CC67D9CEED}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1180) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{B88C45B9-8825-4629-B83E-77CC67D9CEED}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1180) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\Windows Error Reporting\RuntimeExceptionHelperModules |
| Operation: | write | Name: | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\137.0.6613.124\chrome_wer.dll |
Value: 0 | |||
| (PID) Process: | (1180) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\NinjaBrowser |
| Operation: | write | Name: | DowngradeCleanupCommand |
Value: "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\137.0.6613.124\Installer\setup.exe" --cleanup-for-downgrade-version=$1 --cleanup-for-downgrade-operation=$2 --system-level | |||
Executable files
19
Suspicious files
775
Text files
924
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1720 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-MQEAA.tmp\is-KGMCO.tmp | — | |
MD5:— | SHA256:— | |||
| 1720 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-MQEAA.tmp\chromium.exe | — | |
MD5:— | SHA256:— | |||
| 1100 | chromium.exe | C:\Users\admin\AppData\Local\Temp\is-MQEAA.tmp\CR_2C443.tmp\CHROME.PACKED.7Z | — | |
MD5:— | SHA256:— | |||
| 1180 | setup.exe | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\137.0.6613.124\Installer\chrome.7z | — | |
MD5:— | SHA256:— | |||
| 3888 | setup.exe | C:\Users\admin\AppData\Local\Temp\is-0A4HR.tmp\setup.tmp | executable | |
MD5:B972C2931B82E429DE66DC64D4C67D07 | SHA256:18621988A50F23905F9C8BBF5D90693C02D97EC4A6CBE3F47316CD898A9F0D74 | |||
| 1720 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-MQEAA.tmp\is-FJ667.tmp | executable | |
MD5:BE9CD5055FB680B27F8B0F475B8A0A86 | SHA256:5329D4B1D8AA6B3E90176927C2597F28C7173F9293304504F9C3A426C821C93D | |||
| 1296 | setup.exe | C:\Users\admin\AppData\Local\Temp\is-JGVCN.tmp\setup.tmp | executable | |
MD5:B972C2931B82E429DE66DC64D4C67D07 | SHA256:18621988A50F23905F9C8BBF5D90693C02D97EC4A6CBE3F47316CD898A9F0D74 | |||
| 1720 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-MQEAA.tmp\_isetup\_isdecmp.dll | executable | |
MD5:C6AE924AD02500284F7E4EFA11FA7CFC | SHA256:31D04C1E4BFDFA34704C142FA98F80C0A3076E4B312D6ADA57C4BE9D9C7DCF26 | |||
| 1720 | setup.tmp | C:\Users\admin\AppData\Local\Temp\is-MQEAA.tmp\updater.exe | executable | |
MD5:BE9CD5055FB680B27F8B0F475B8A0A86 | SHA256:5329D4B1D8AA6B3E90176927C2597F28C7173F9293304504F9C3A426C821C93D | |||
| 4312 | chromium.exe | C:\Users\admin\AppData\Local\Temp\is-MQEAA.tmp\CR_10A5A.tmp\CHROME.PACKED.7Z | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
27
DNS requests
24
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2292 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5744 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5744 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2140 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
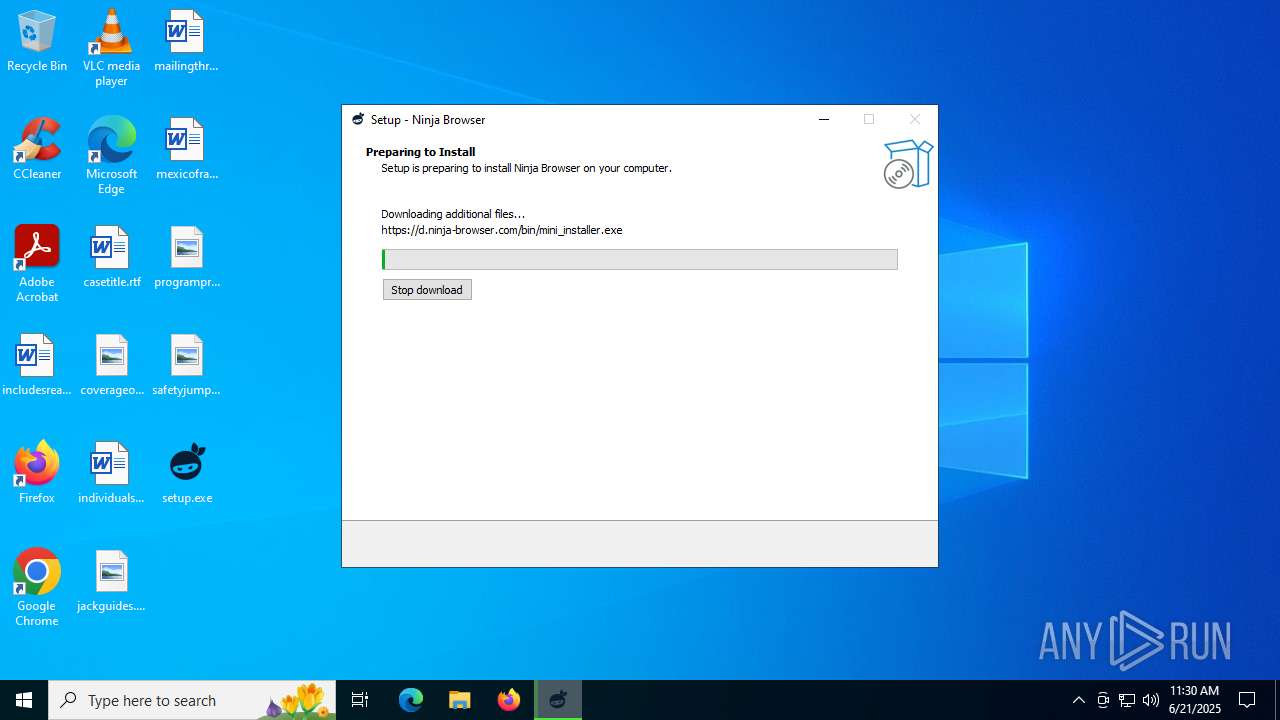
1720 | setup.tmp | 89.111.170.193:443 | d.ninja-browser.com | Jsc ru-center | RU | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2292 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2292 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
d.ninja-browser.com |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .ninja-browser .com) |