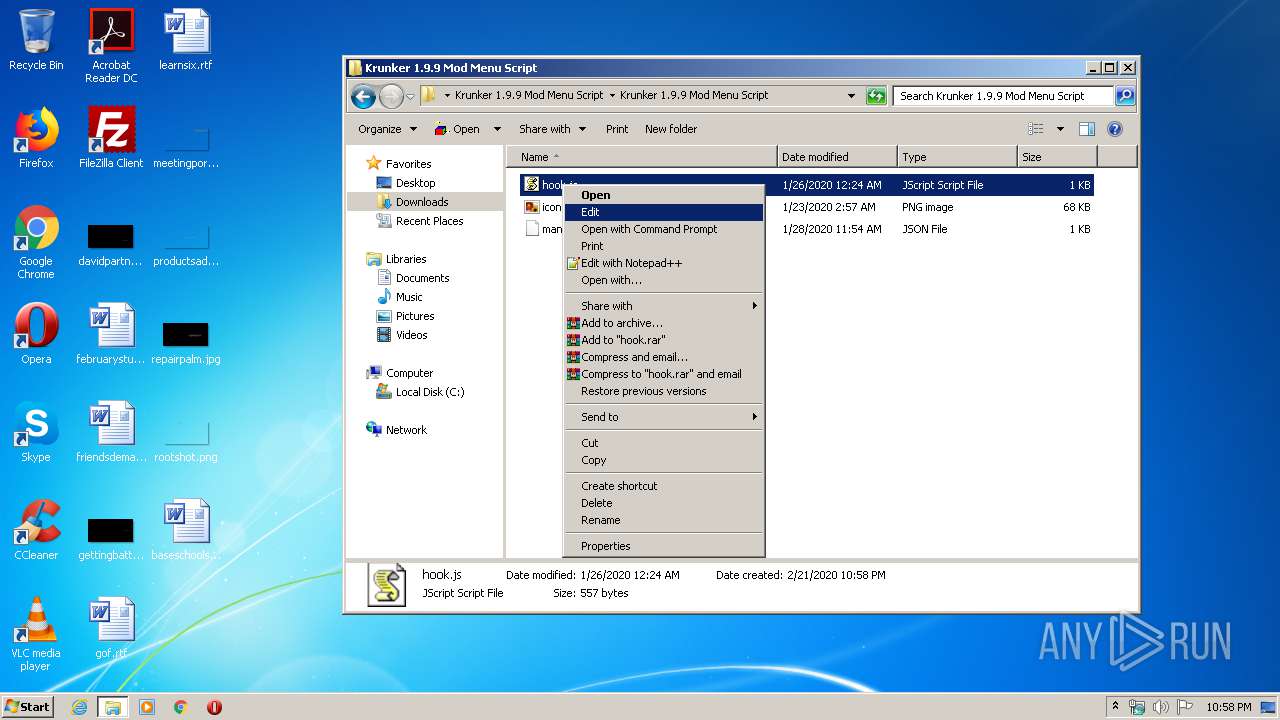
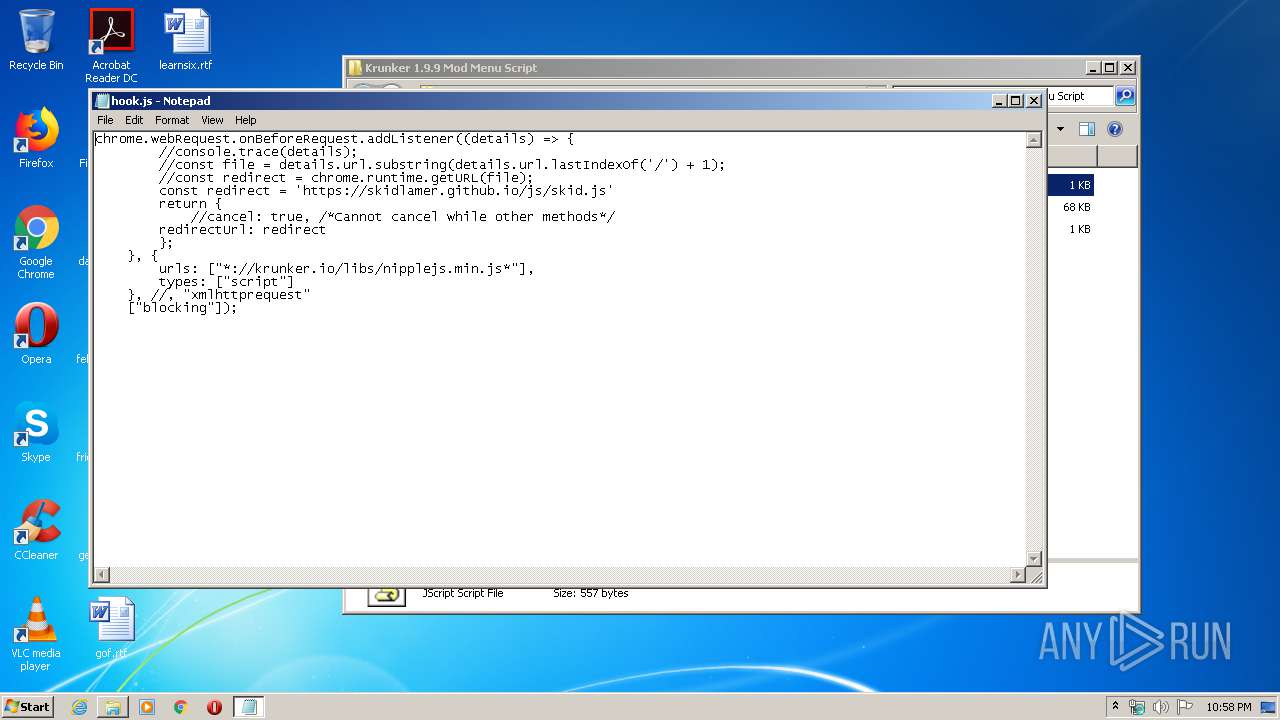
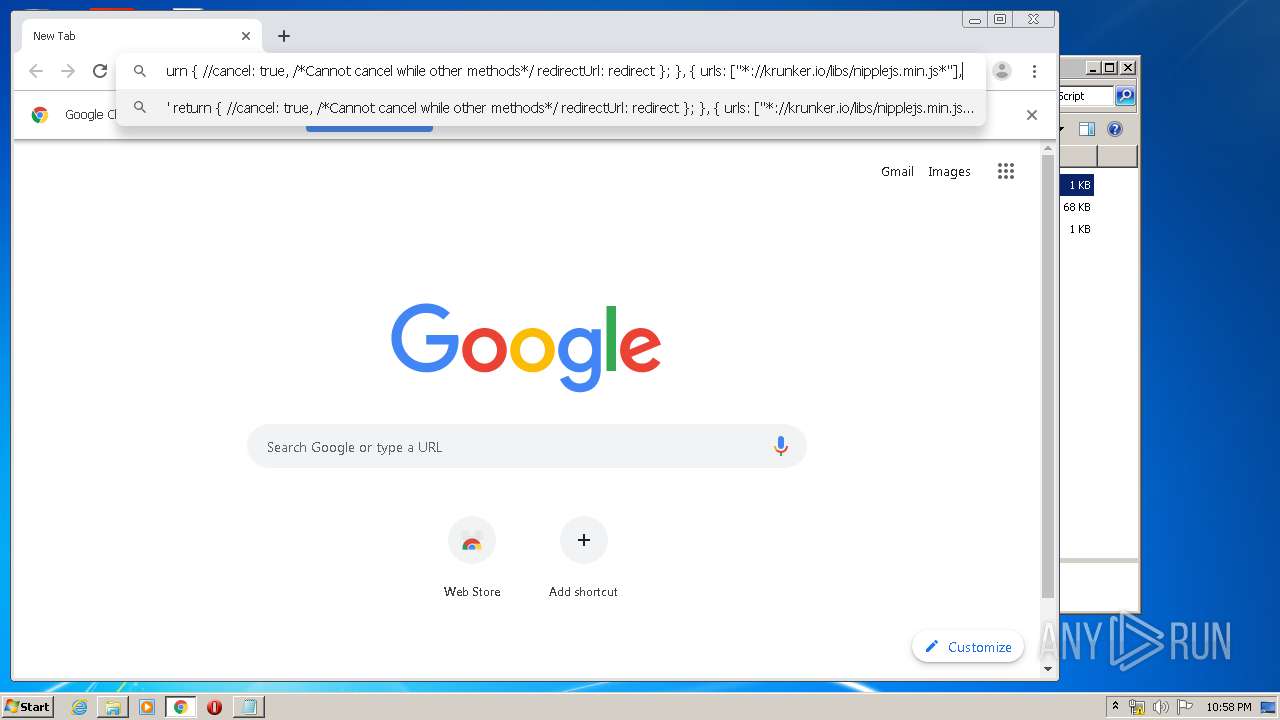
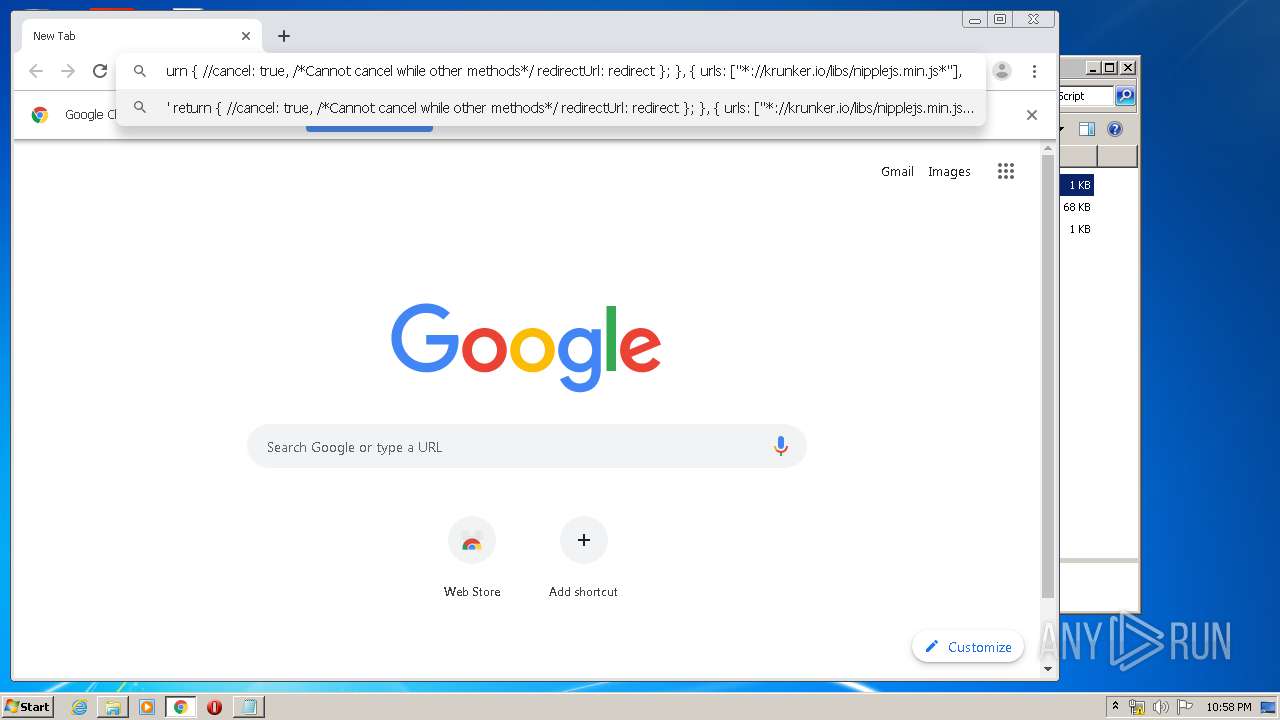
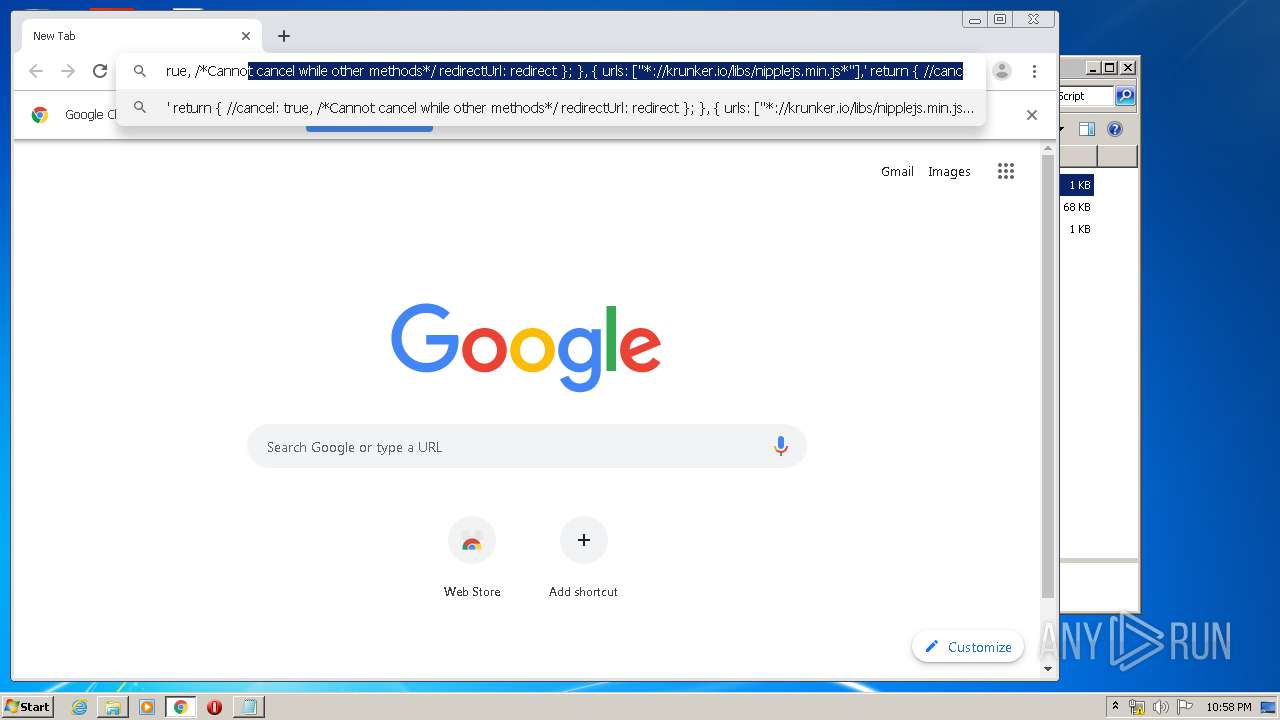
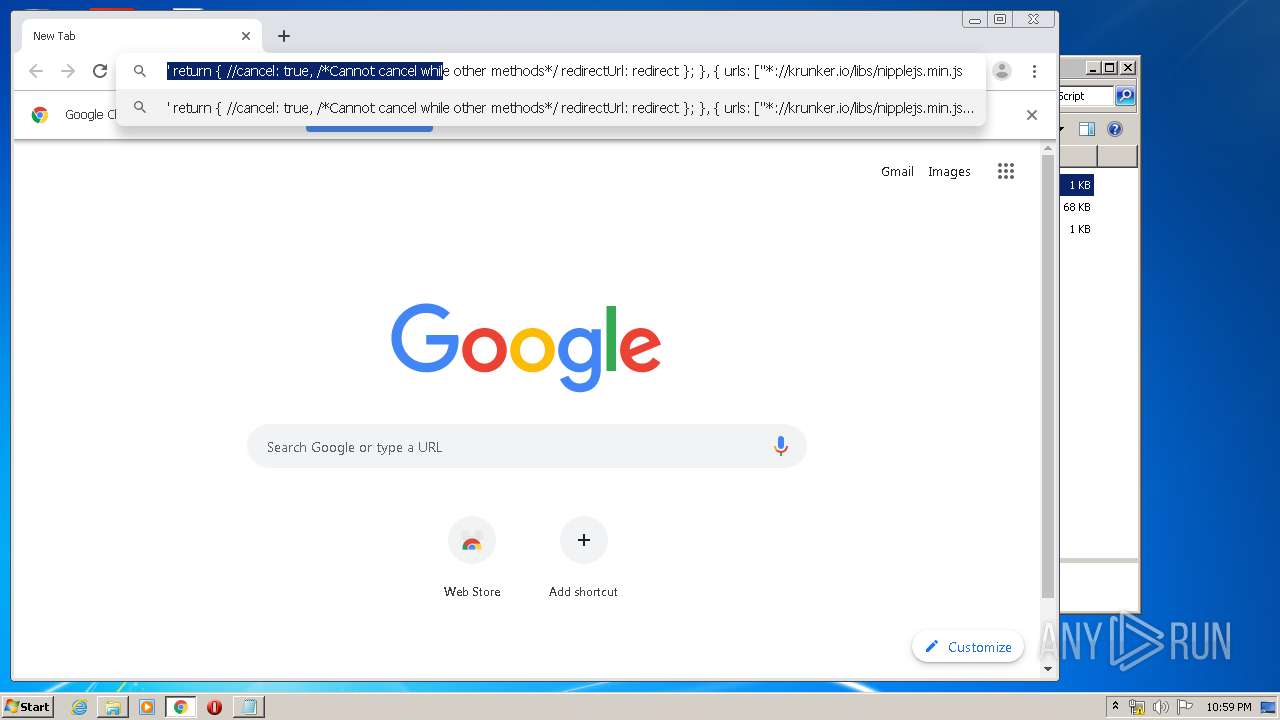
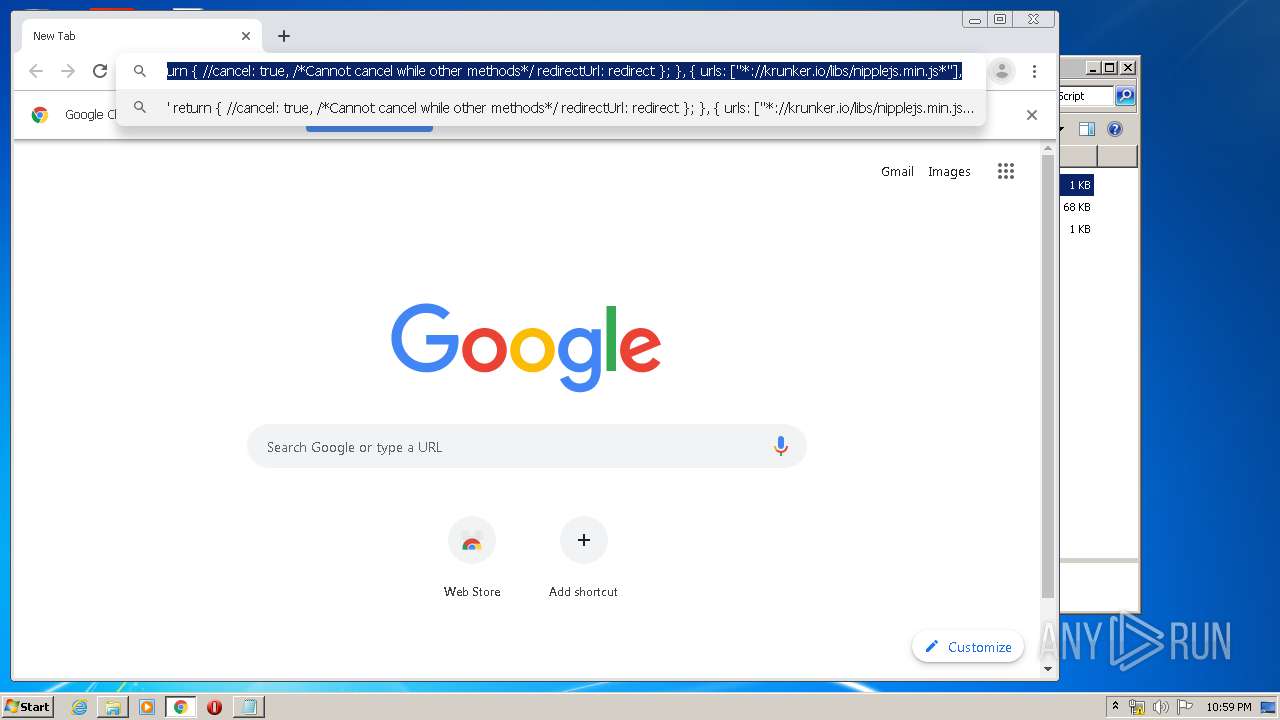
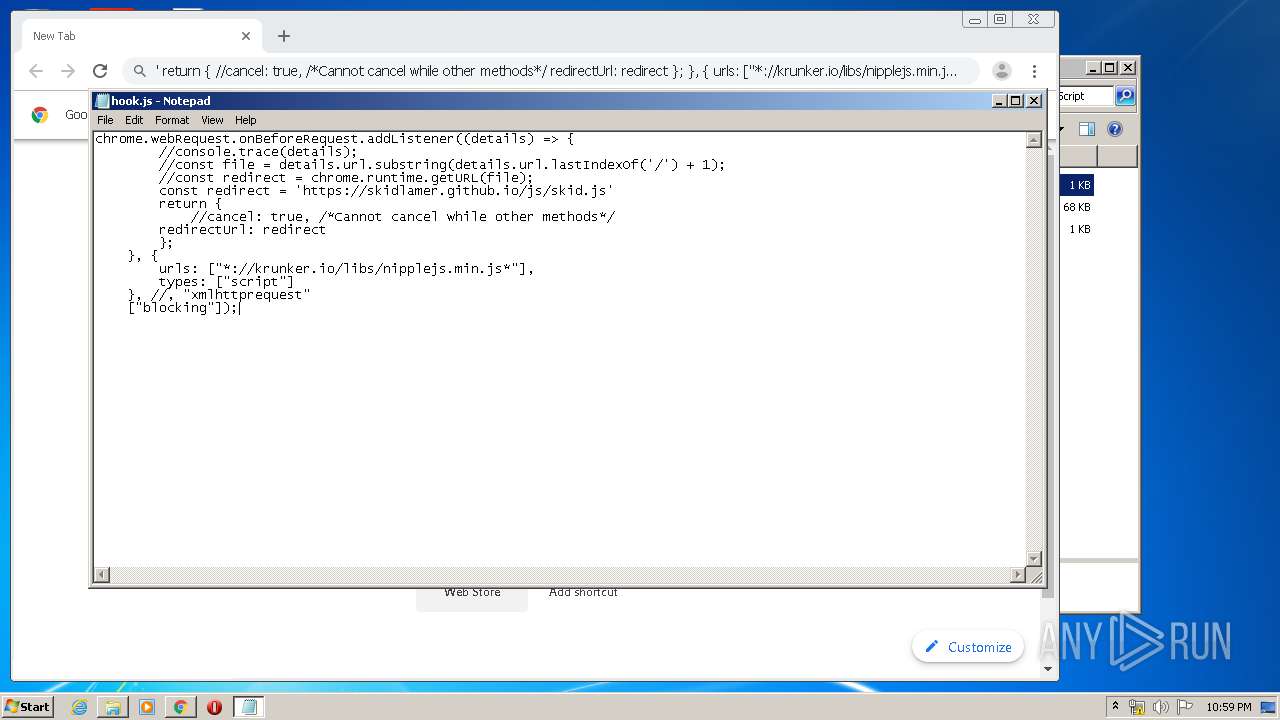
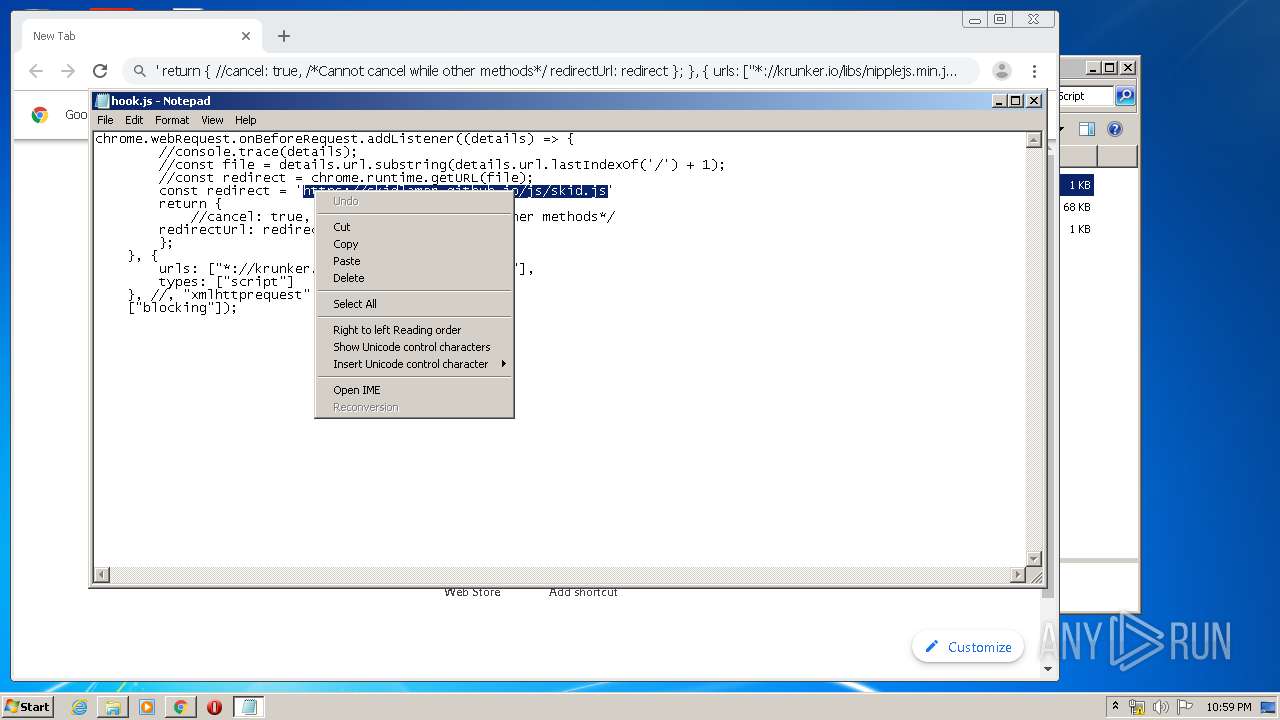
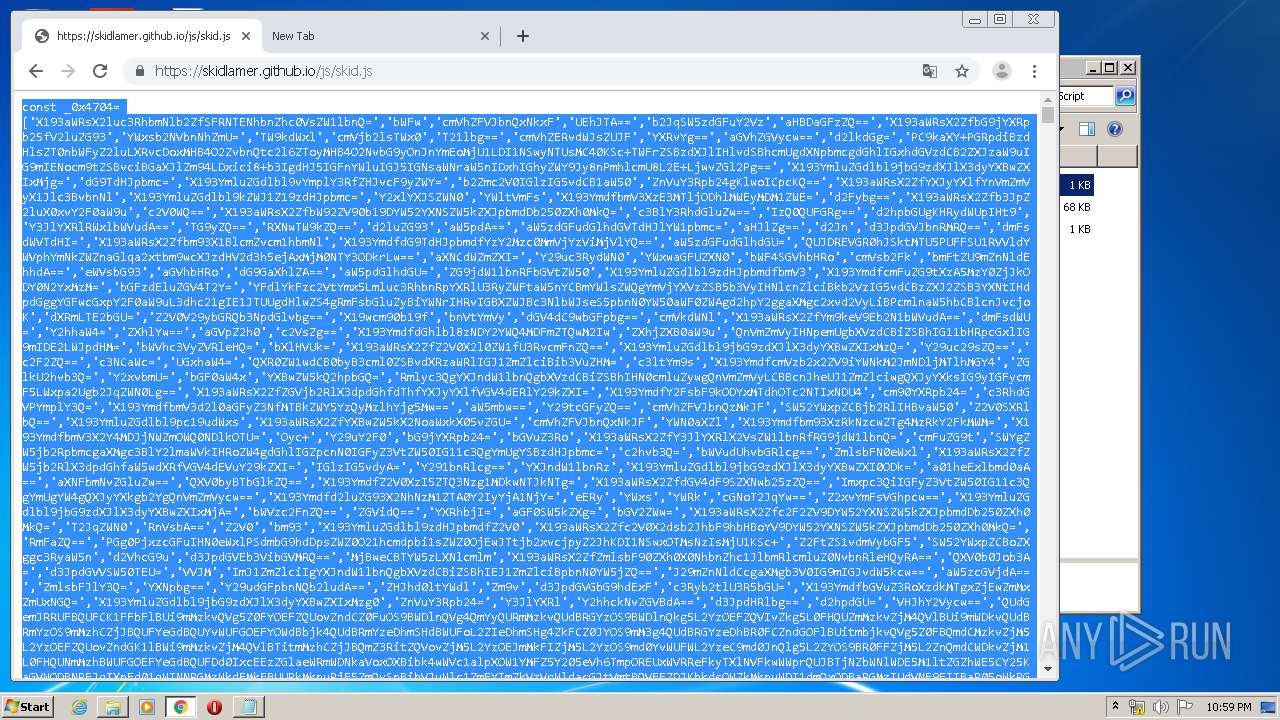
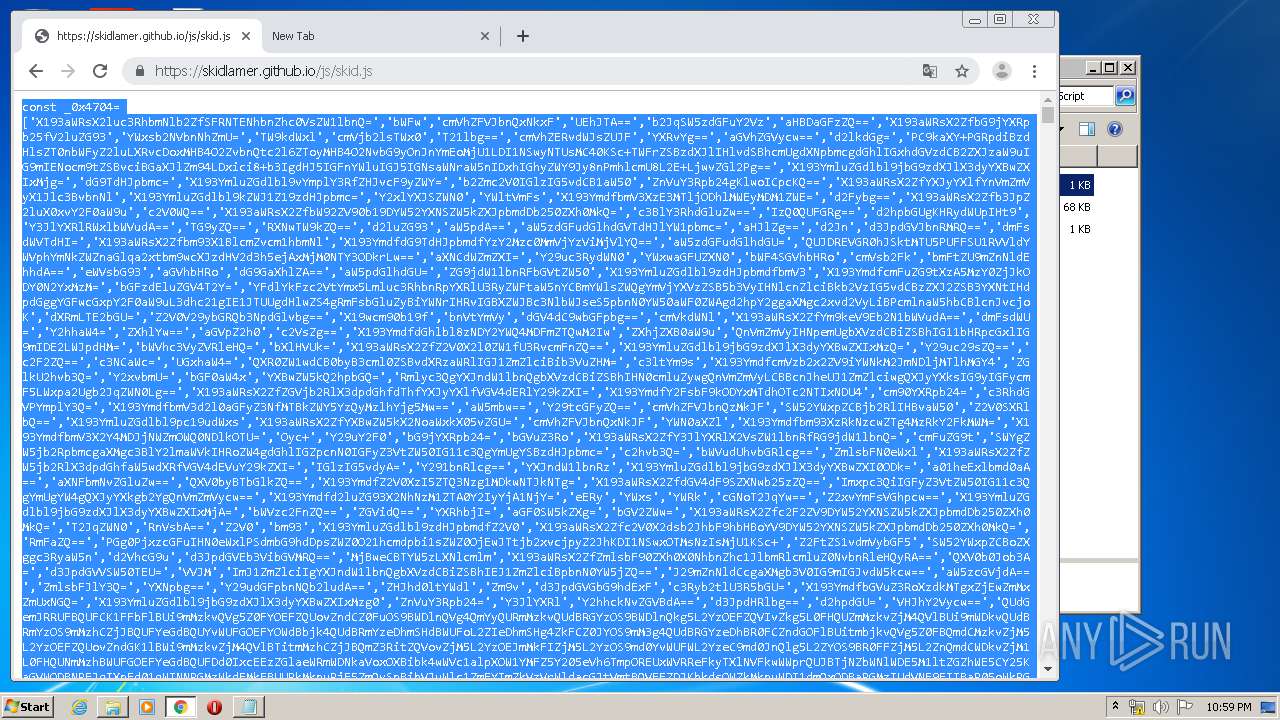
| URL: | https://anonfiles.com/L6v0BcS8n1/Krunker_1.9.9_Mod_Menu_Script_rar |
| Full analysis: | https://app.any.run/tasks/1de4f7d8-4588-439d-a6d9-46967a9f162f |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2020, 22:57:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 57290B57B0664320792F287E39F21011 |
| SHA1: | 888AD0CCC5CC4993B68E0E0CF67377A55632729B |
| SHA256: | 53196DE46DD599B803375303652491FEF9FB5E73ECA101D5DAB1D4B7BAFA8A1C |
| SSDEEP: | 3:N8M22vdWXevTKXMl6Vm+n:2M2iWuRcVm+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2208)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3576)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2436)
- iexplore.exe (PID: 3376)
- iexplore.exe (PID: 3744)
Creates files in the user directory
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2208)
- iexplore.exe (PID: 2436)
- iexplore.exe (PID: 3376)
Changes internet zones settings
- iexplore.exe (PID: 3376)
Reads internet explorer settings
- iexplore.exe (PID: 2436)
- iexplore.exe (PID: 3744)
Application launched itself
- iexplore.exe (PID: 3376)
- chrome.exe (PID: 3576)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3376)
Manual execution by user
- Notepad.exe (PID: 2952)
- explorer.exe (PID: 2728)
- chrome.exe (PID: 3576)
Reads the hosts file
- chrome.exe (PID: 3576)
- chrome.exe (PID: 2344)
Reads settings of System Certificates
- iexplore.exe (PID: 2436)
- chrome.exe (PID: 2344)
- iexplore.exe (PID: 3744)
- iexplore.exe (PID: 3376)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3376)
Changes settings of System certificates
- iexplore.exe (PID: 3376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
80
Monitored processes
42
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 940 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Krunker 1.9.9 Mod Menu Script.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,12950155662489575883,8963458926162918223,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1193754367468539879 --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2840 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1636 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,12950155662489575883,8963458926162918223,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8859103609422754402 --mojo-platform-channel-handle=3408 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,12950155662489575883,8963458926162918223,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12959588588797737271 --mojo-platform-channel-handle=3672 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2208 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 2344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,12950155662489575883,8963458926162918223,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=8970837820019121802 --mojo-platform-channel-handle=1576 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2424 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,12950155662489575883,8963458926162918223,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7228814164405373828 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2508 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2436 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3376 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,12950155662489575883,8963458926162918223,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15736623397525270123 --mojo-platform-channel-handle=3992 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2580 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1032,12950155662489575883,8963458926162918223,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=17977374167399708173 --mojo-platform-channel-handle=3092 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
7 723
Read events
2 507
Write events
3 556
Delete events
1 660
Modification events
| (PID) Process: | (3376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1687698818 | |||
| (PID) Process: | (3376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30796042 | |||
| (PID) Process: | (3376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3376) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
92
Text files
258
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab7D66.tmp | — | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar7D67.tmp | — | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | der | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\PGXAICWX.txt | text | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | binary | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\Krunker_1.9[1].htm | html | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\sw_anonfiles[1].js | text | |
MD5:3ADAB942A2AB6C02C549DAAF694F58FA | SHA256:9091B2493E77EAC744B42F7634AB2BBD51F693CC036926C9A91EFBEEF482D167 | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\de[1].png | image | |
MD5:9F8CC07C258BCD2DE0C7900861E20FFC | SHA256:07CD5A4CAD20604F77DCED9C7D8A92CA9AE3321718E5A1935296E4D75F921A19 | |||
| 3376 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ru[1].png | image | |
MD5:D8DF89B036E6AFB48F72D2440831BAD0 | SHA256:2DB4B55326C0EF7CD3CAF53E835AE1F38629DA1D1C2F5A127E0785165B16078C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
85
DNS requests
50
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2436 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
2436 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
2436 | iexplore.exe | GET | 200 | 172.217.23.163:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 172.217.23.163:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDx9it%2Fyk0DxwgAAAAALC4g | US | der | 472 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
2436 | iexplore.exe | GET | 200 | 172.217.23.163:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
2436 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAyO4MkNaokViAQGHuJB%2Ba8%3D | US | der | 471 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 172.217.23.163:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCgdZM8AVzzKAgAAAAALnDU | US | der | 472 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 172.217.23.163:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDx9it%2Fyk0DxwgAAAAALC4g | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2436 | iexplore.exe | 104.18.38.170:443 | anonfiles.com | Cloudflare Inc | US | unknown |
2436 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2436 | iexplore.exe | 151.101.2.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
2436 | iexplore.exe | 216.58.208.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
3376 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2436 | iexplore.exe | 151.101.2.133:80 | ocsp.globalsign.com | Fastly | US | malicious |
2436 | iexplore.exe | 143.204.208.120:443 | djv99sxoqpv11.cloudfront.net | — | US | whitelisted |
2436 | iexplore.exe | 23.37.43.27:80 | s.symcd.com | Akamai Technologies, Inc. | NL | whitelisted |
2436 | iexplore.exe | 172.217.23.163:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2436 | iexplore.exe | 172.217.22.14:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
anonfiles.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
vjs.zencdn.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
djv99sxoqpv11.cloudfront.net |
| shared |
ocsp.pki.goog |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
s.symcd.com |
| shared |