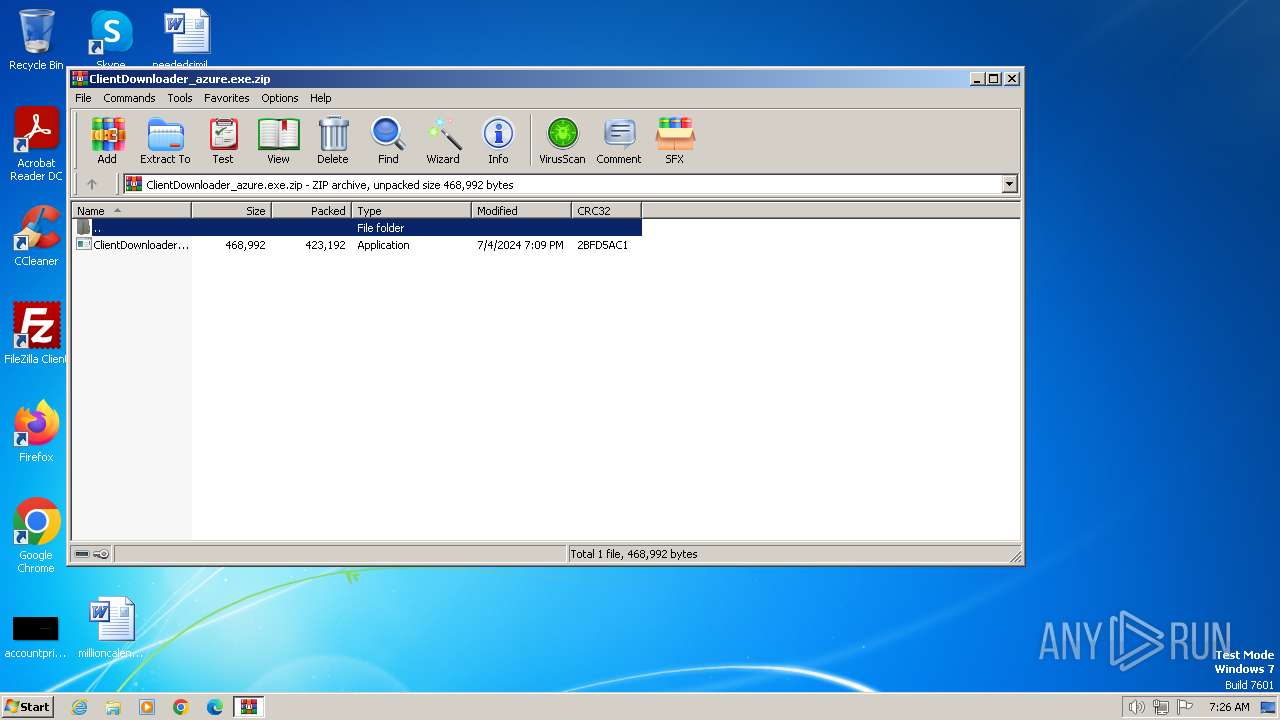
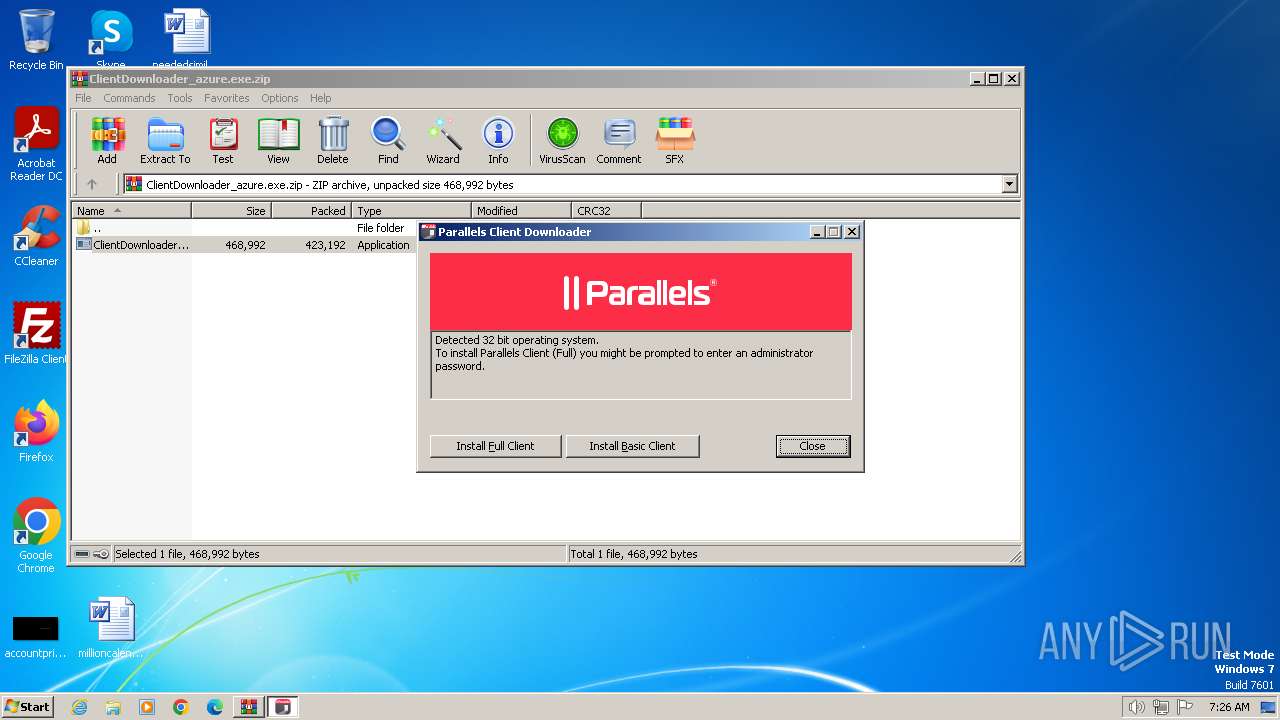
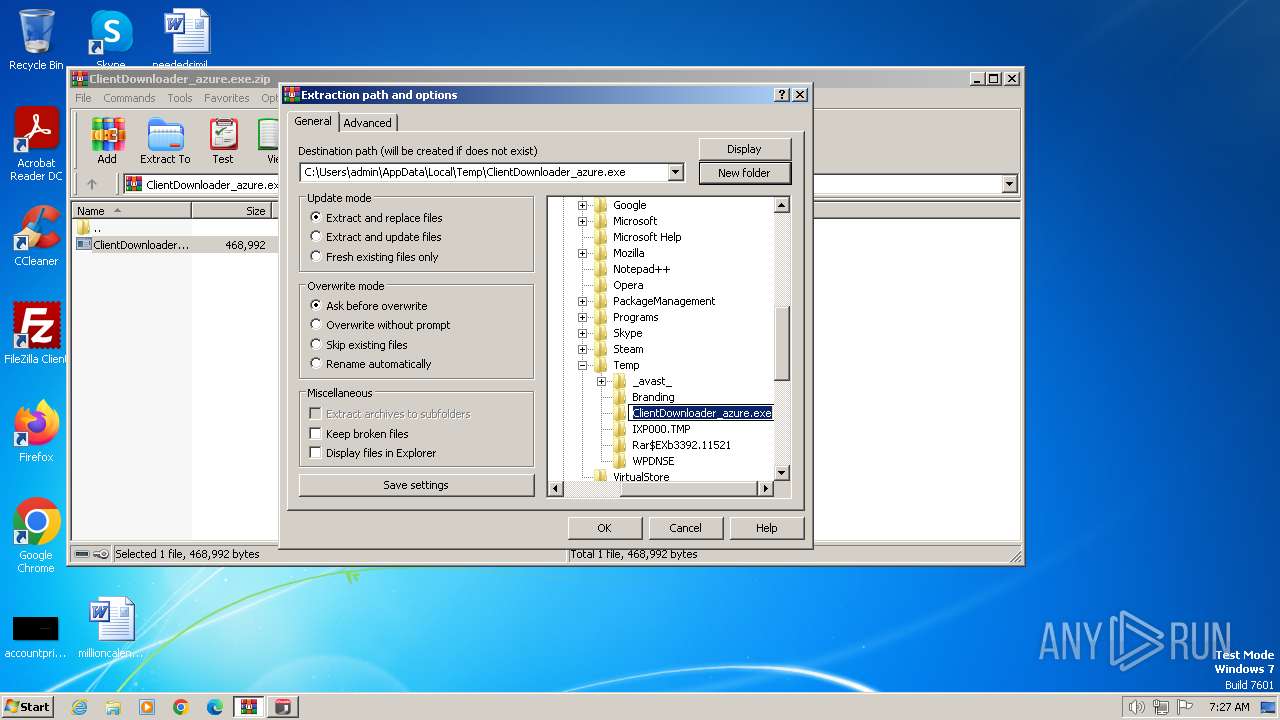
| File name: | ClientDownloader_azure.exe.zip |
| Full analysis: | https://app.any.run/tasks/000cc863-3bb1-4b28-8666-68f44625d9c5 |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2024, 06:26:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 7CA6993950746A2B319DBDA239C00131 |
| SHA1: | EA5C9AD2A5EC6EC566E168BE294F9EFDB82890E7 |
| SHA256: | 52FAF417AC90851072DD58C43BBDF3492DE631C709E051749E1213D005D1622E |
| SSDEEP: | 12288:Nl++Pe4eWAbUStboFkPvFQE8M25GzCFUfcTa01B0r/f:Nl1ZeWAbUSts+PvFQE8M25GzsUfcTa0m |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3392)
- ClientDownloader_azure.exe (PID: 3432)
- CLIENT~1.EXE (PID: 3252)
SUSPICIOUS
Starts a Microsoft application from unusual location
- ClientDownloader_azure.exe (PID: 3432)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3392)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3392)
- CLIENT~1.EXE (PID: 3252)
Executable content was dropped or overwritten
- ClientDownloader_azure.exe (PID: 3432)
- CLIENT~1.EXE (PID: 3252)
Reads the Internet Settings
- CLIENT~1.EXE (PID: 3252)
Reads settings of System Certificates
- CLIENT~1.EXE (PID: 3252)
Creates file in the systems drive root
- WinRAR.exe (PID: 3392)
Checks Windows Trust Settings
- CLIENT~1.EXE (PID: 3252)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3392)
Checks supported languages
- ClientDownloader_azure.exe (PID: 3432)
- CLIENT~1.EXE (PID: 3252)
Create files in a temporary directory
- ClientDownloader_azure.exe (PID: 3432)
- CLIENT~1.EXE (PID: 3252)
Reads the computer name
- CLIENT~1.EXE (PID: 3252)
Checks proxy server information
- CLIENT~1.EXE (PID: 3252)
Reads the machine GUID from the registry
- CLIENT~1.EXE (PID: 3252)
Creates files or folders in the user directory
- CLIENT~1.EXE (PID: 3252)
Reads the software policy settings
- CLIENT~1.EXE (PID: 3252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:04 19:09:46 |
| ZipCRC: | 0x2bfd5ac1 |
| ZipCompressedSize: | 423192 |
| ZipUncompressedSize: | 468992 |
| ZipFileName: | ClientDownloader_azure.exe |
Total processes
41
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3252 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\CLIENT~1.EXE | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\CLIENT~1.EXE | ClientDownloader_azure.exe | ||||||||||||
User: admin Company: Parallels International GmbH. Integrity Level: MEDIUM Description: ClientDownloader Version: 19.2 (build 23975) Modules
| |||||||||||||||
| 3392 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\ClientDownloader_azure.exe.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3432 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3392.11521\ClientDownloader_azure.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3392.11521\ClientDownloader_azure.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Version: 11.00.17763.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 817
Read events
7 750
Write events
61
Delete events
6
Modification events
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ClientDownloader_azure.exe.zip | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3392) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
4
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3392.11521\ClientDownloader_azure.exe | executable | |
MD5:1860AD93ADECF0277B63EFEA4861EB22 | SHA256:6F6EFCC0963CFEAAB823CC119444A87AE8CB22BBFC39198ACA2C8FF9EE7F5A9B | |||
| 3432 | ClientDownloader_azure.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Brand.ico | image | |
MD5:30CFE051D6960678093F425E3C4860C5 | SHA256:8162F24745FB61E949EA6302D615F2925474EFB0FF64A8C106CF97293DA46297 | |||
| 3252 | CLIENT~1.EXE | C:\Users\admin\AppData\Local\Temp\Branding\Brand.ico | image | |
MD5:30CFE051D6960678093F425E3C4860C5 | SHA256:8162F24745FB61E949EA6302D615F2925474EFB0FF64A8C106CF97293DA46297 | |||
| 3252 | CLIENT~1.EXE | C:\Users\admin\AppData\Local\Temp\Branding\Brand.ini | text | |
MD5:7E25C8DC756B9278B2AD8B7DF1D478B0 | SHA256:1AB91F08955825178D10AA8EA740188D4538EFEBC417E13CFB0630BB88270414 | |||
| 3252 | CLIENT~1.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:2365869258DF7A66A2121B802CA4AFD9 | SHA256:D6B1932822BBD72A8E78C771717D992142348F67D625A42393719FEFBE59B0ED | |||
| 3252 | CLIENT~1.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:1BFE0A81DB078EA084FF82FE545176FE | SHA256:5BA8817F13EEE00E75158BAD93076AB474A068C6B52686579E0F728FDA68499F | |||
| 3252 | CLIENT~1.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:44F5564D0BEFD0D63763C9FD406DD33B | SHA256:06CE540B58FBD60370AFD47014BCEBDD829898292A4D15A2C26703DFFA3956C4 | |||
| 3432 | ClientDownloader_azure.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Brand.ini | text | |
MD5:7E25C8DC756B9278B2AD8B7DF1D478B0 | SHA256:1AB91F08955825178D10AA8EA740188D4538EFEBC417E13CFB0630BB88270414 | |||
| 3252 | CLIENT~1.EXE | C:\Users\admin\AppData\Local\Temp\Branding\Brand.bmp | image | |
MD5:E591837CB8D3B780C325A1122A3EA792 | SHA256:E365D7B12777E7E73A6A6A69A131B7C1A1A8E079589AA0C67F5E6C6C837DF7E0 | |||
| 3432 | ClientDownloader_azure.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Brand.bmp | image | |
MD5:E591837CB8D3B780C325A1122A3EA792 | SHA256:E365D7B12777E7E73A6A6A69A131B7C1A1A8E079589AA0C67F5E6C6C837DF7E0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
12
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.216.77.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3252 | CLIENT~1.EXE | GET | 200 | 216.58.212.131:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | unknown |
3252 | CLIENT~1.EXE | GET | 200 | 216.58.212.131:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67a3611ec3c0260d | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.216.77.10:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
3252 | CLIENT~1.EXE | 104.18.171.3:443 | download.parallels.com | CLOUDFLARENET | — | unknown |
3252 | CLIENT~1.EXE | 216.58.212.131:80 | c.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
download.parallels.com |
| whitelisted |
c.pki.goog |
| unknown |