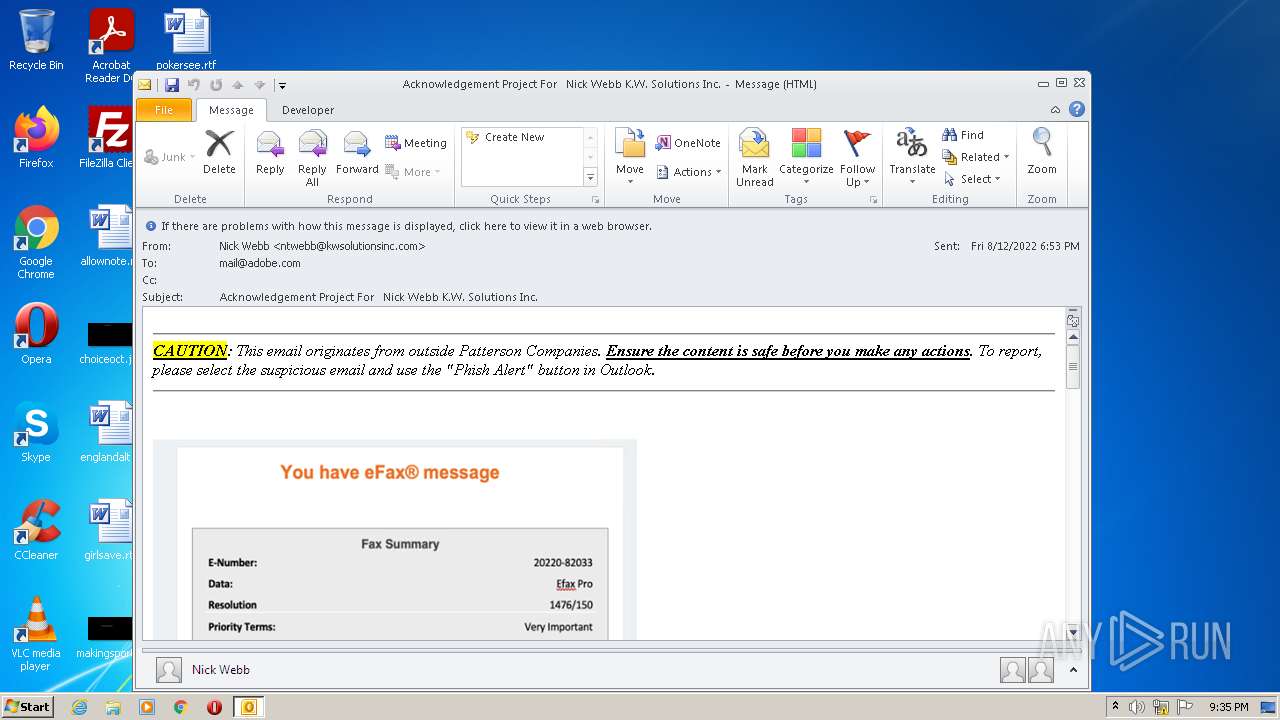
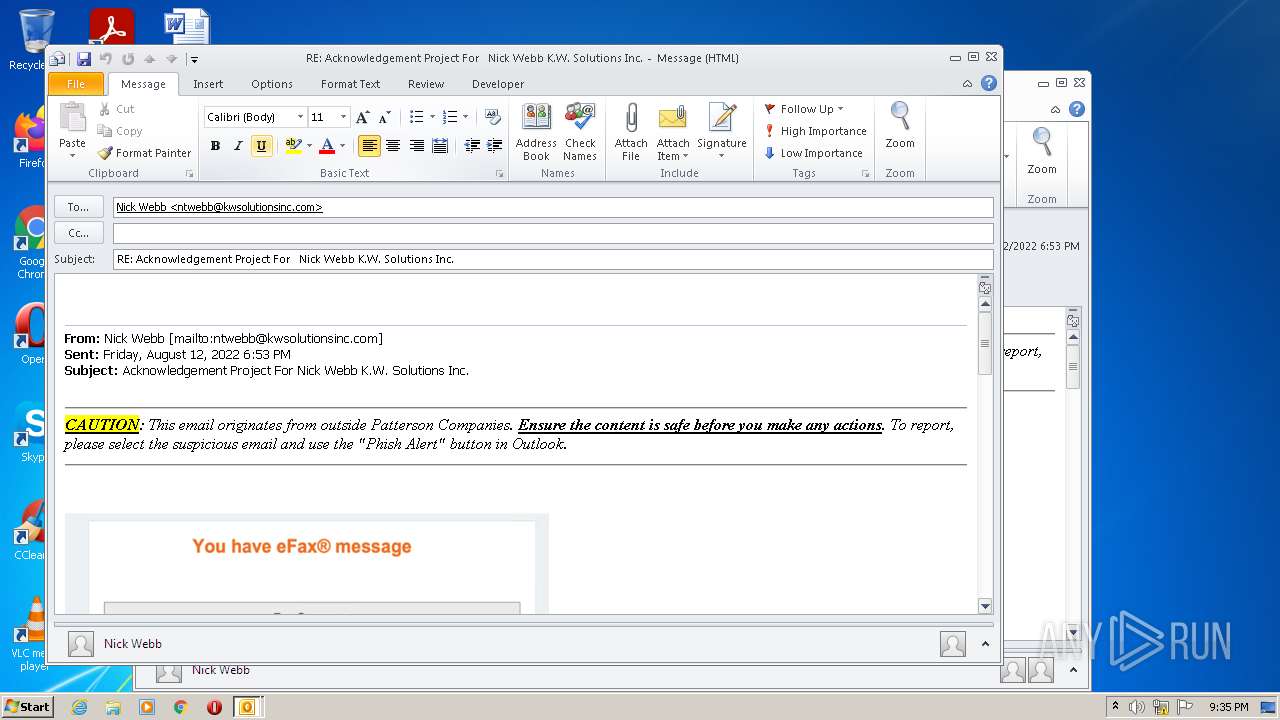
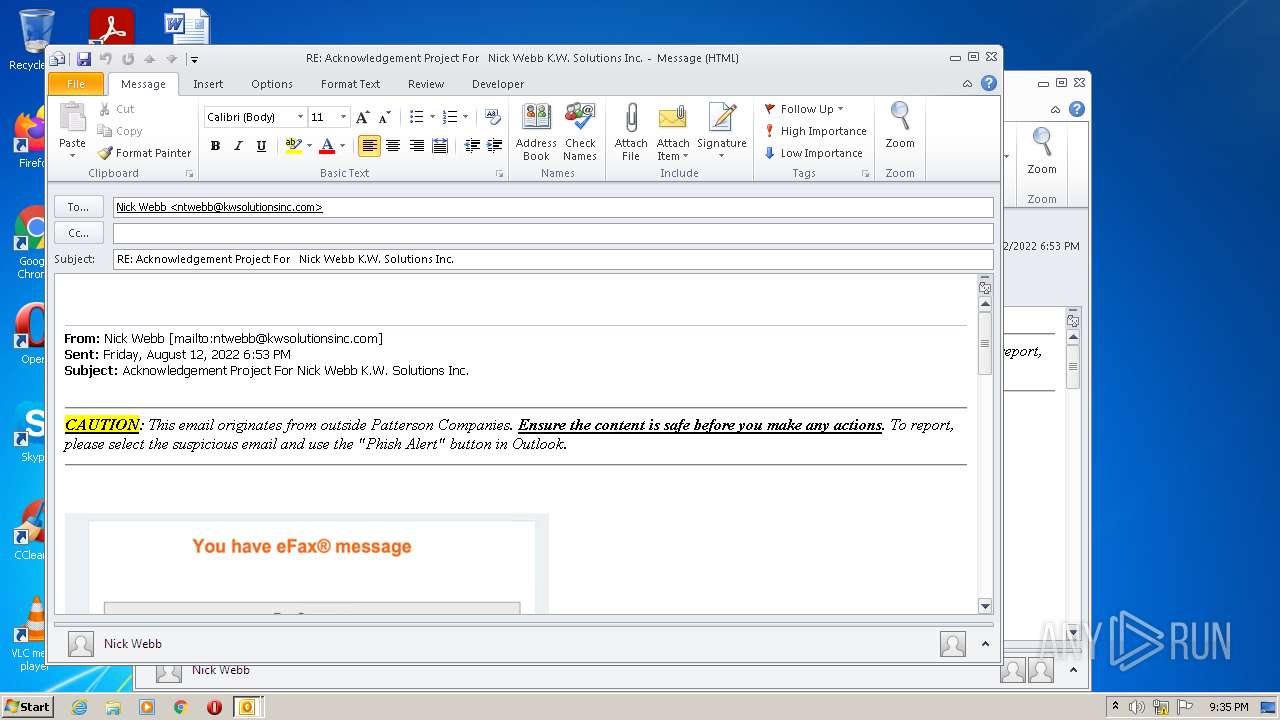
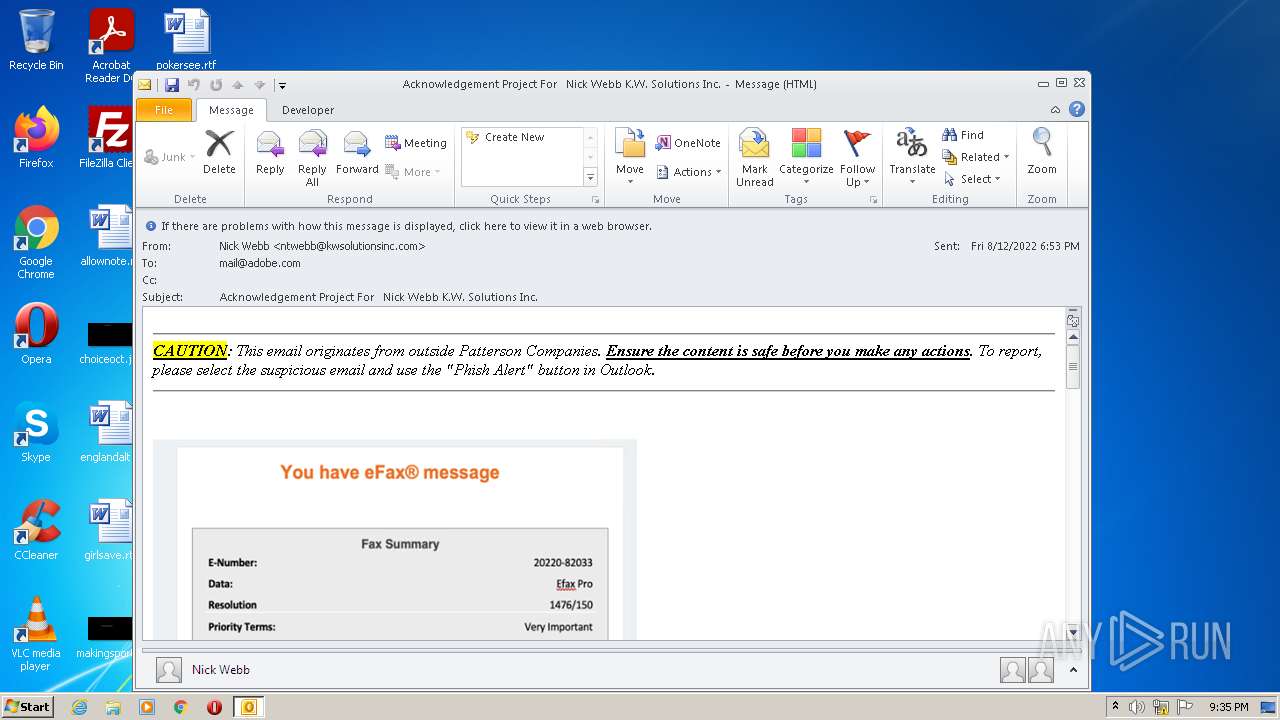
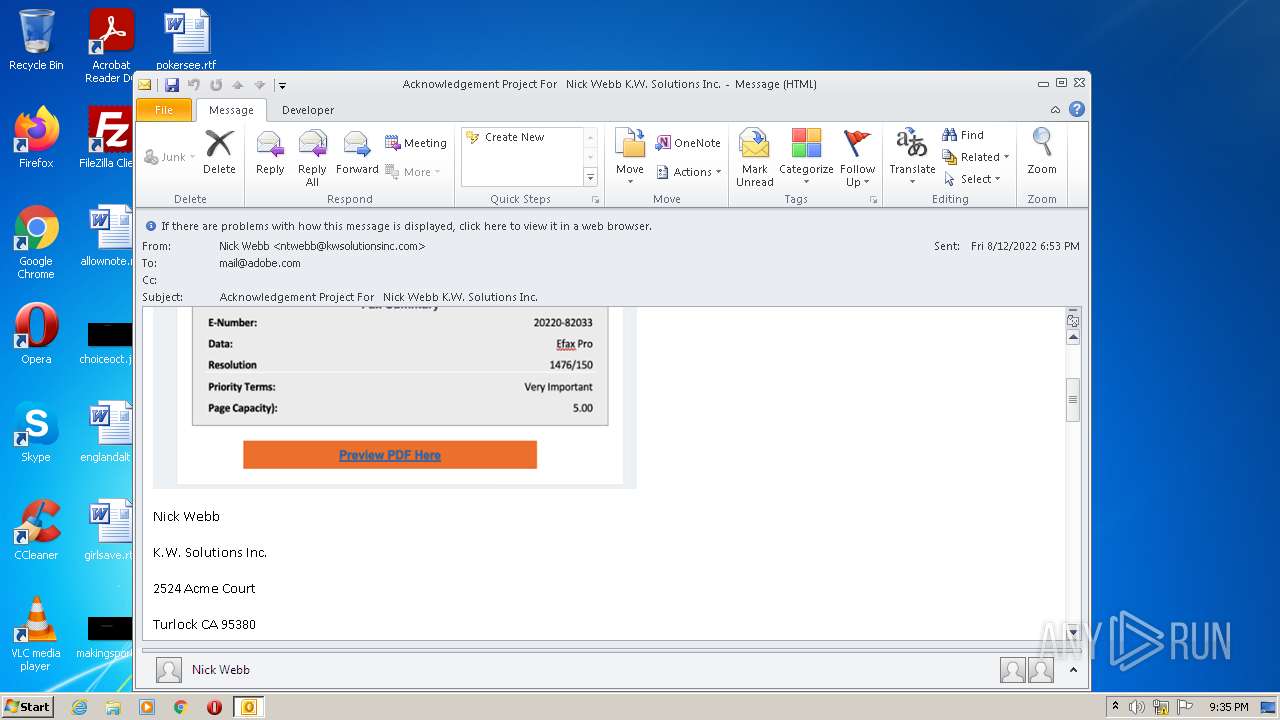
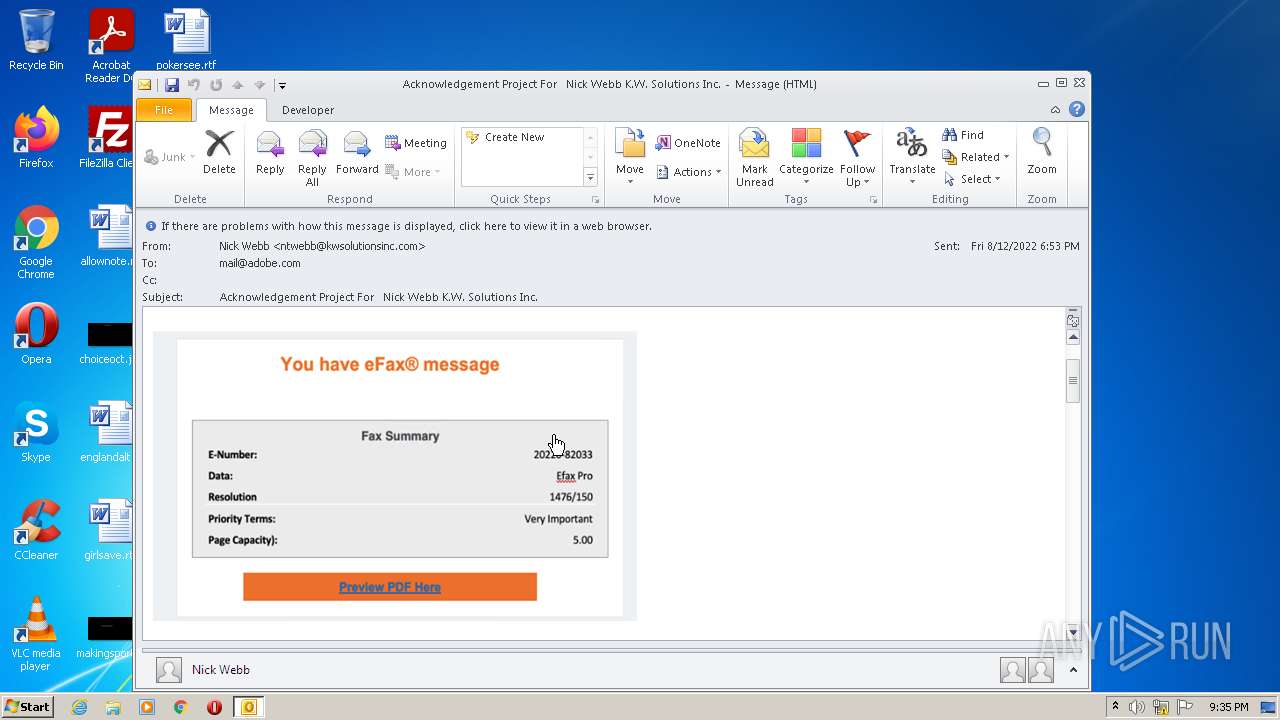
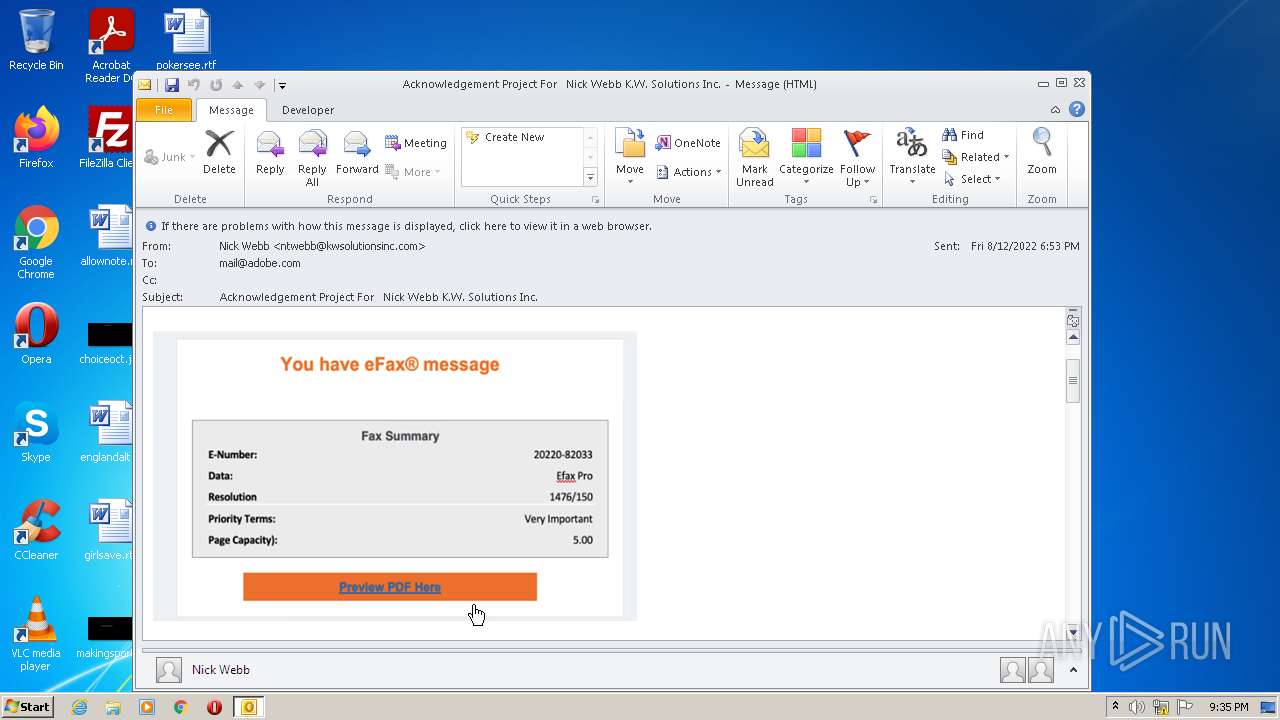
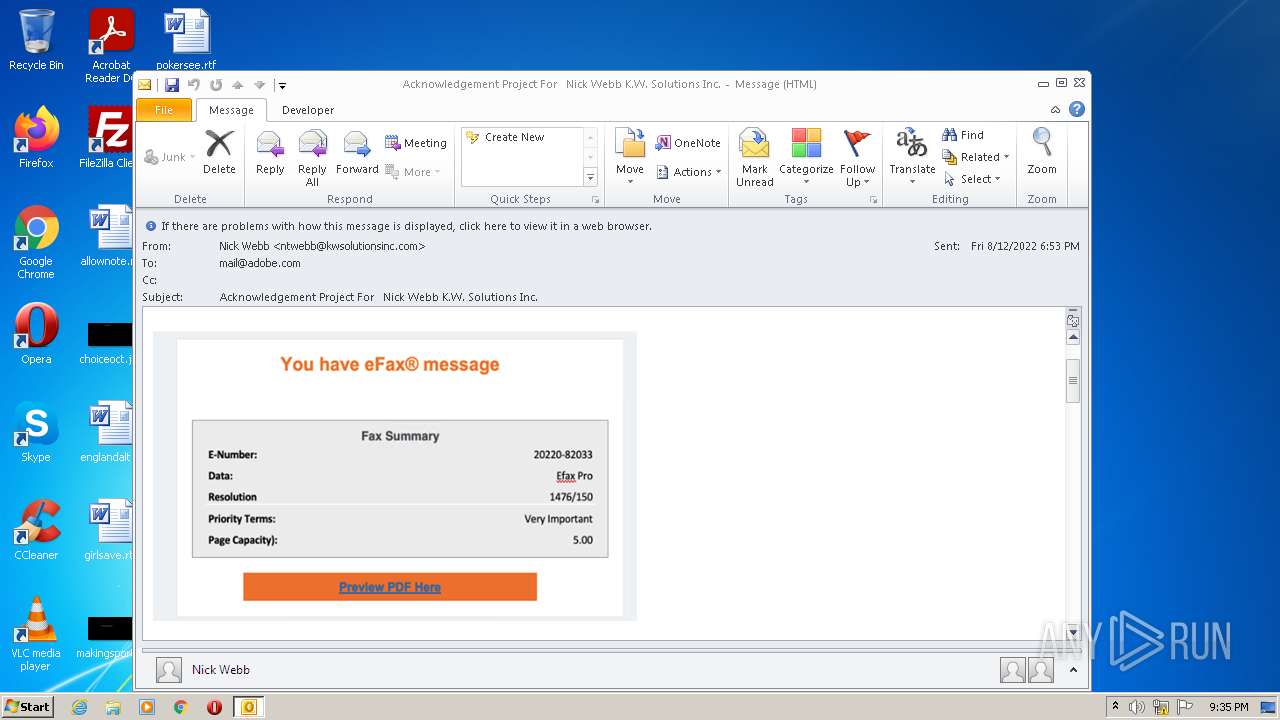
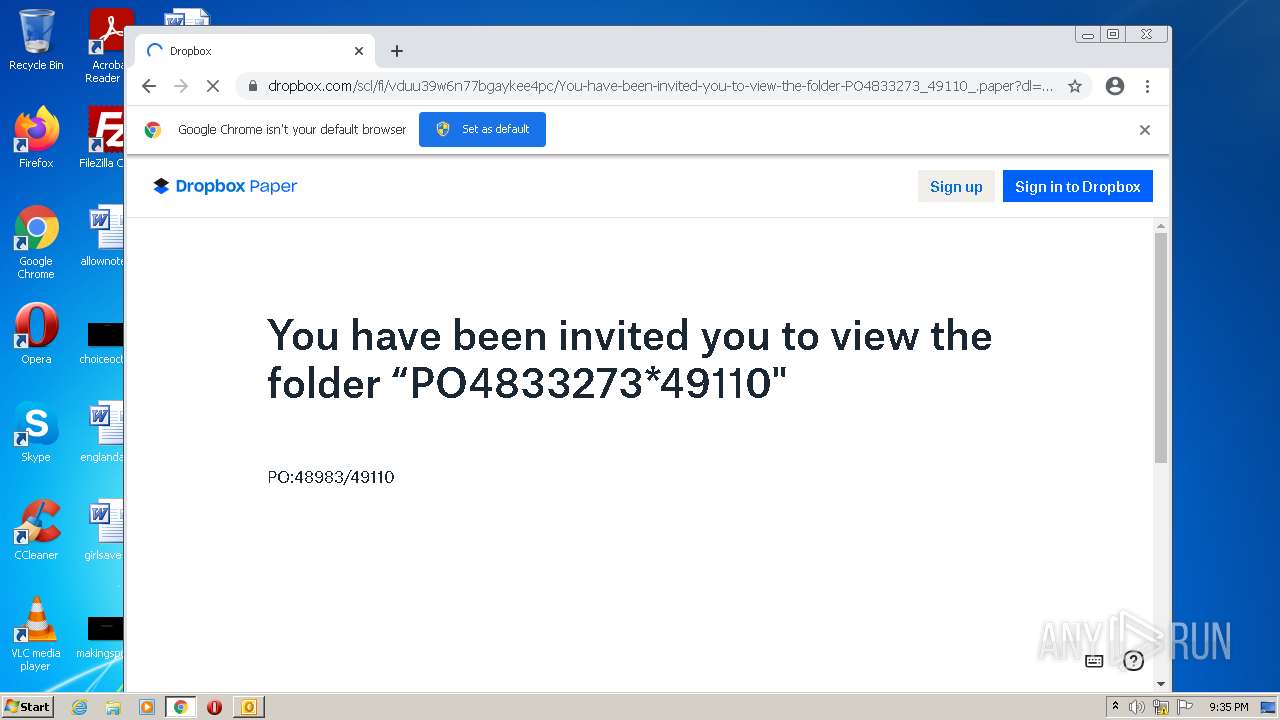
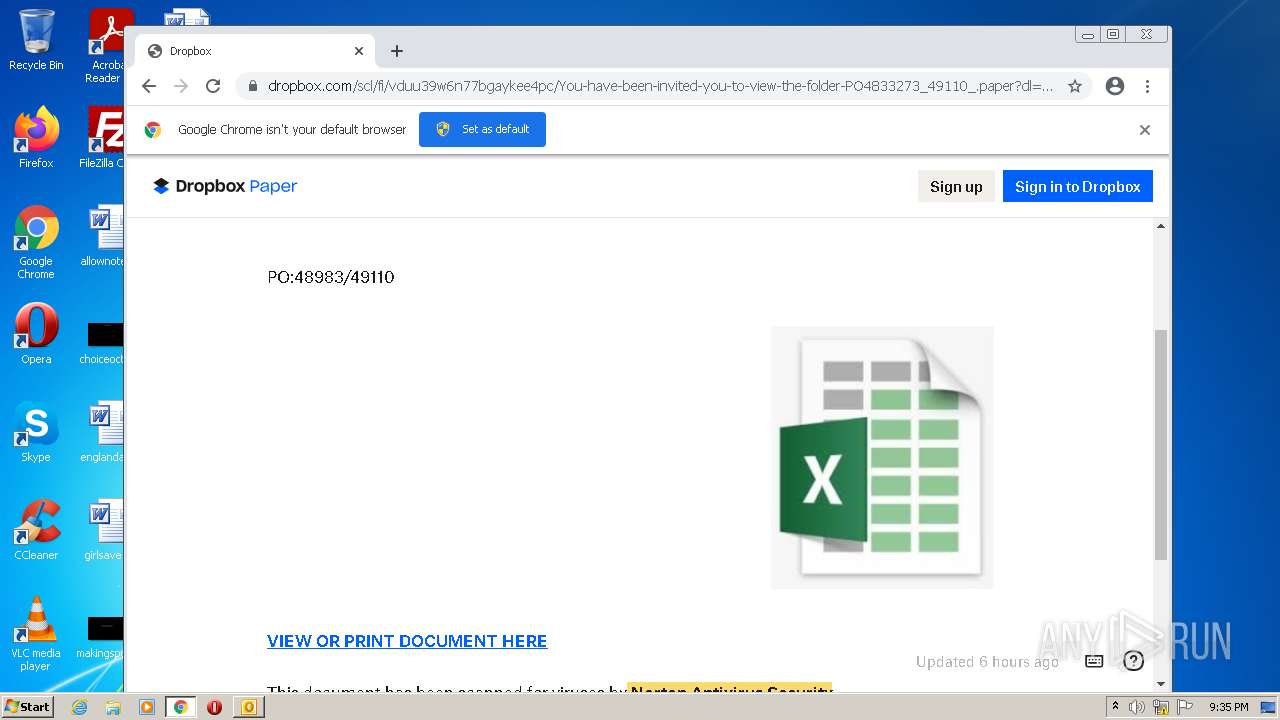
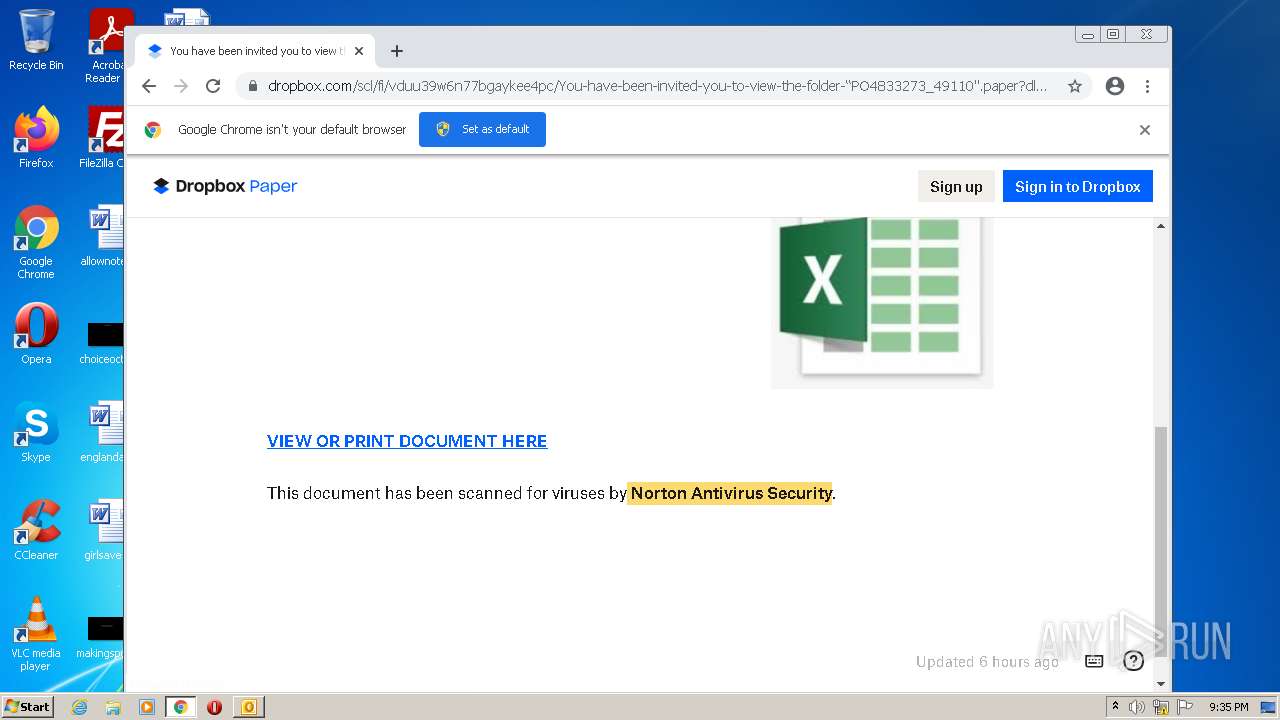
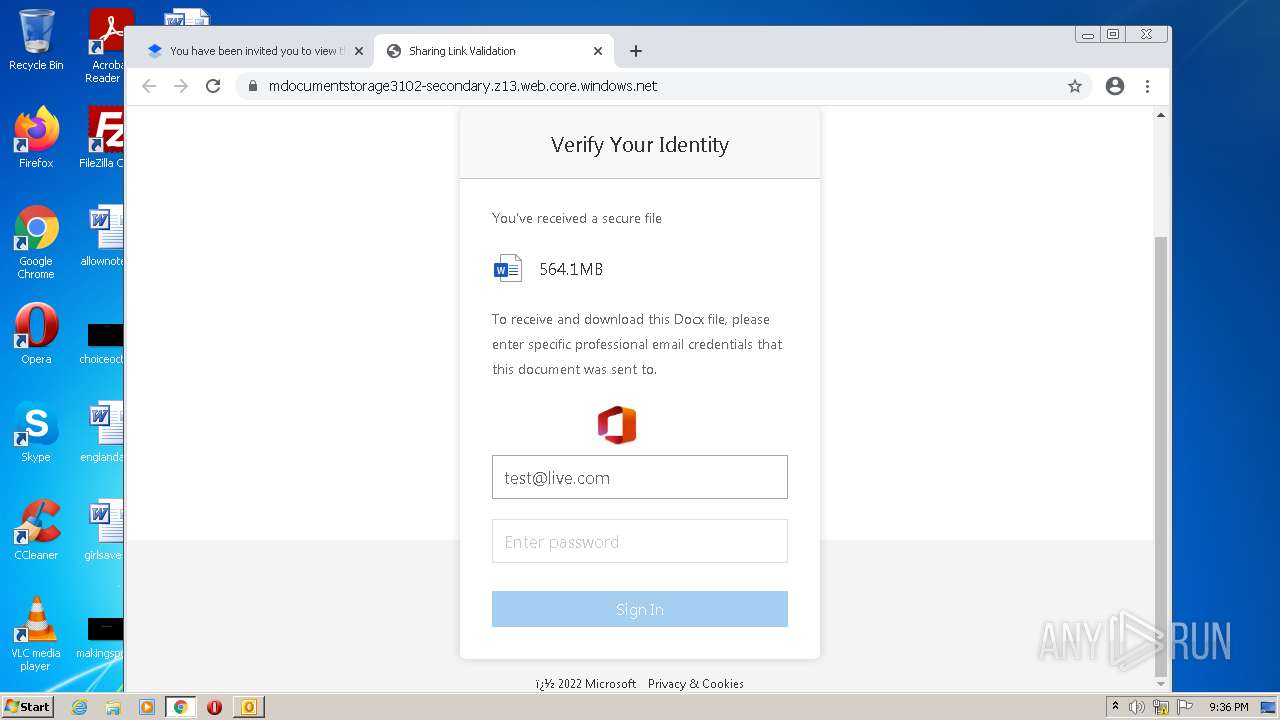
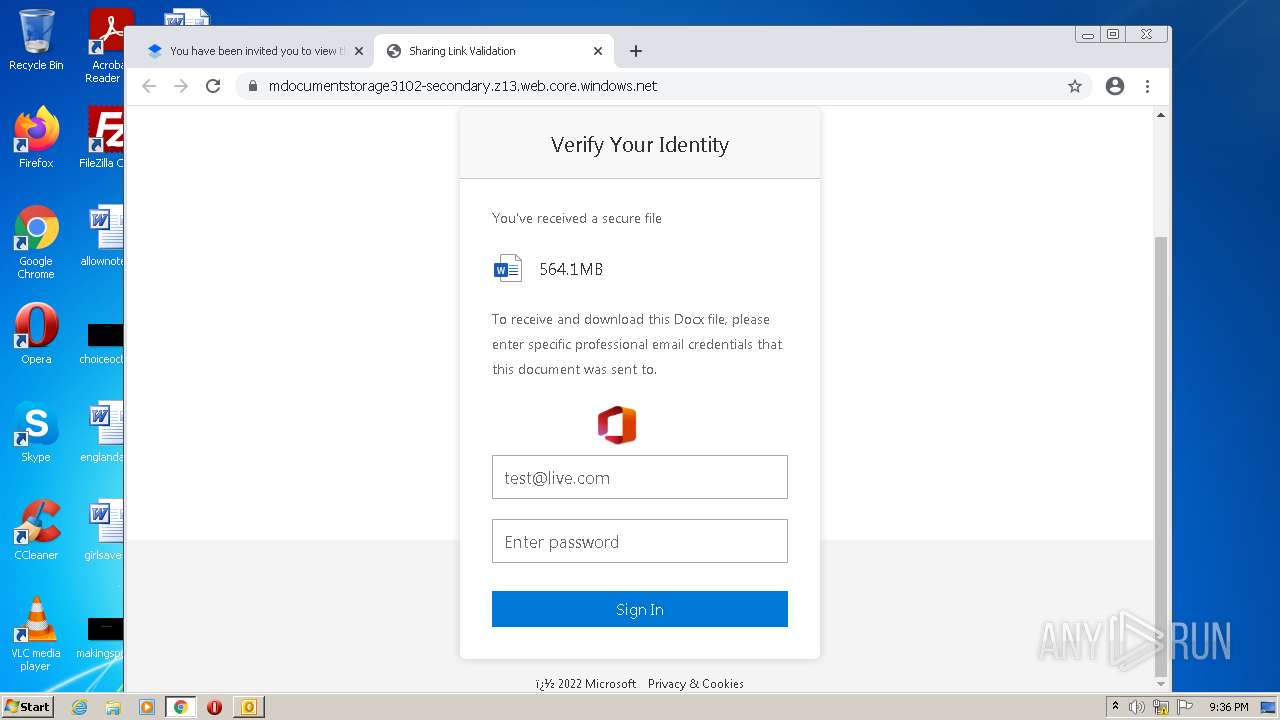
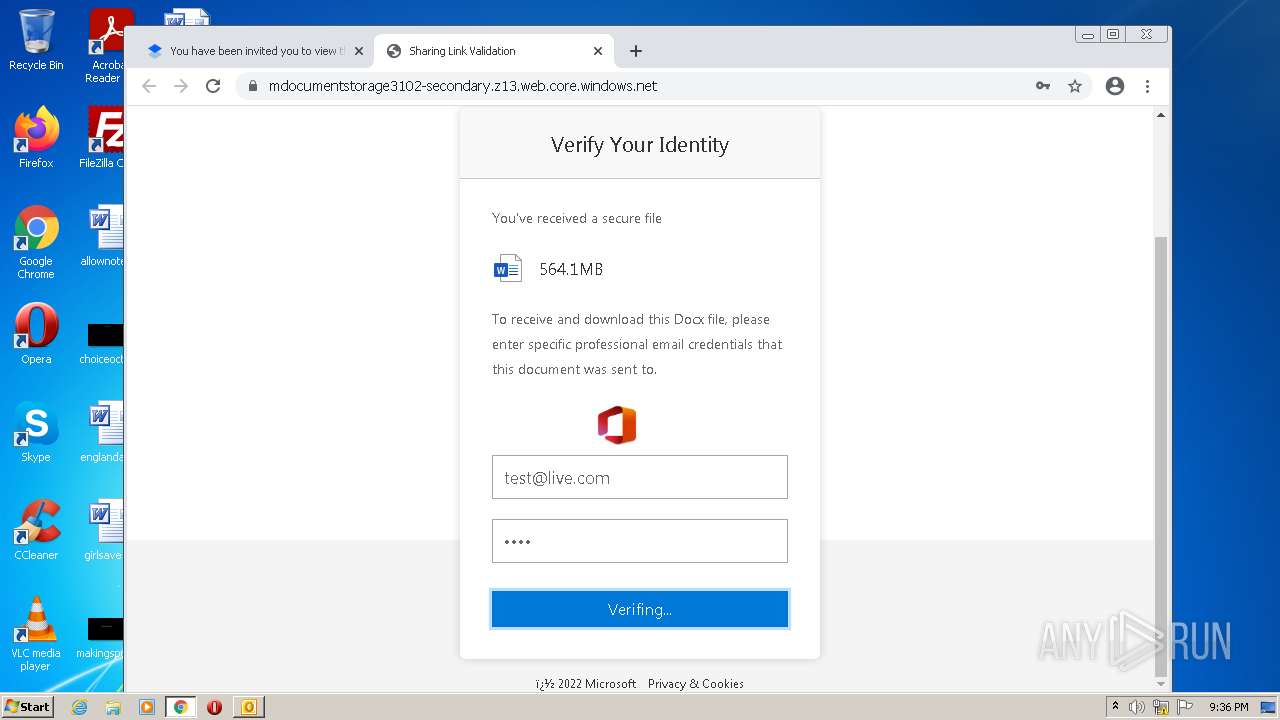
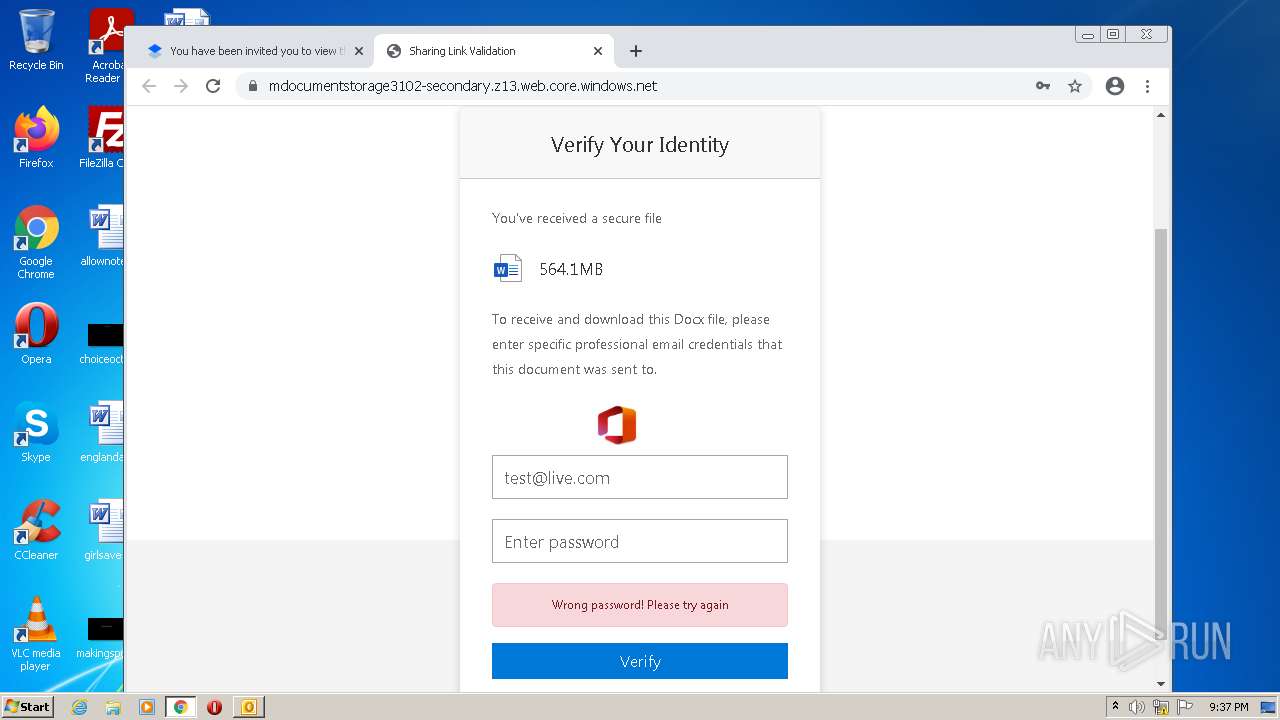
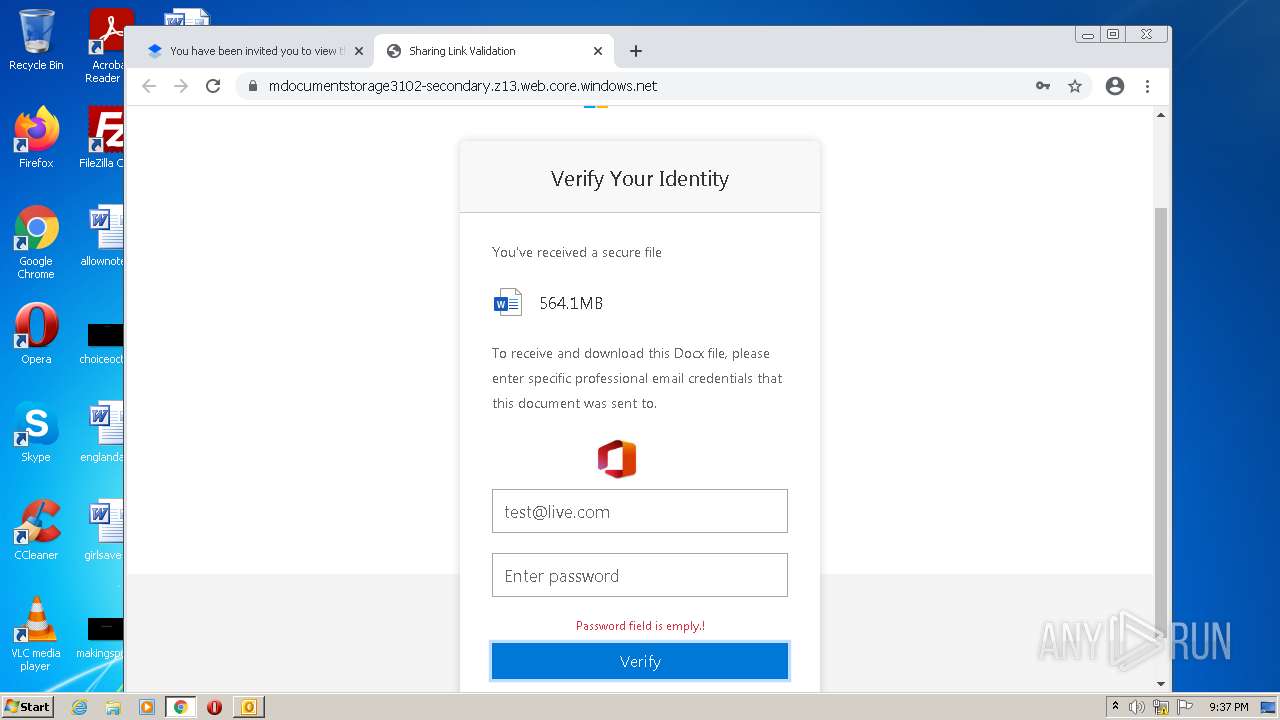
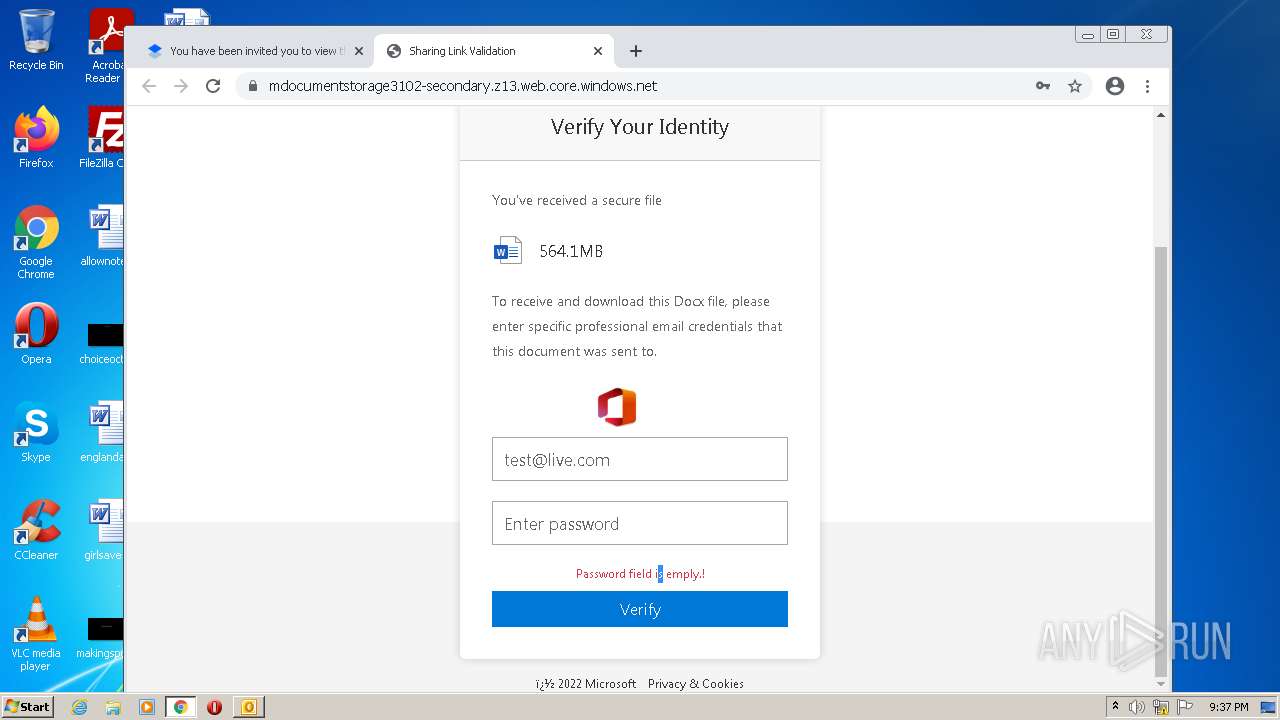
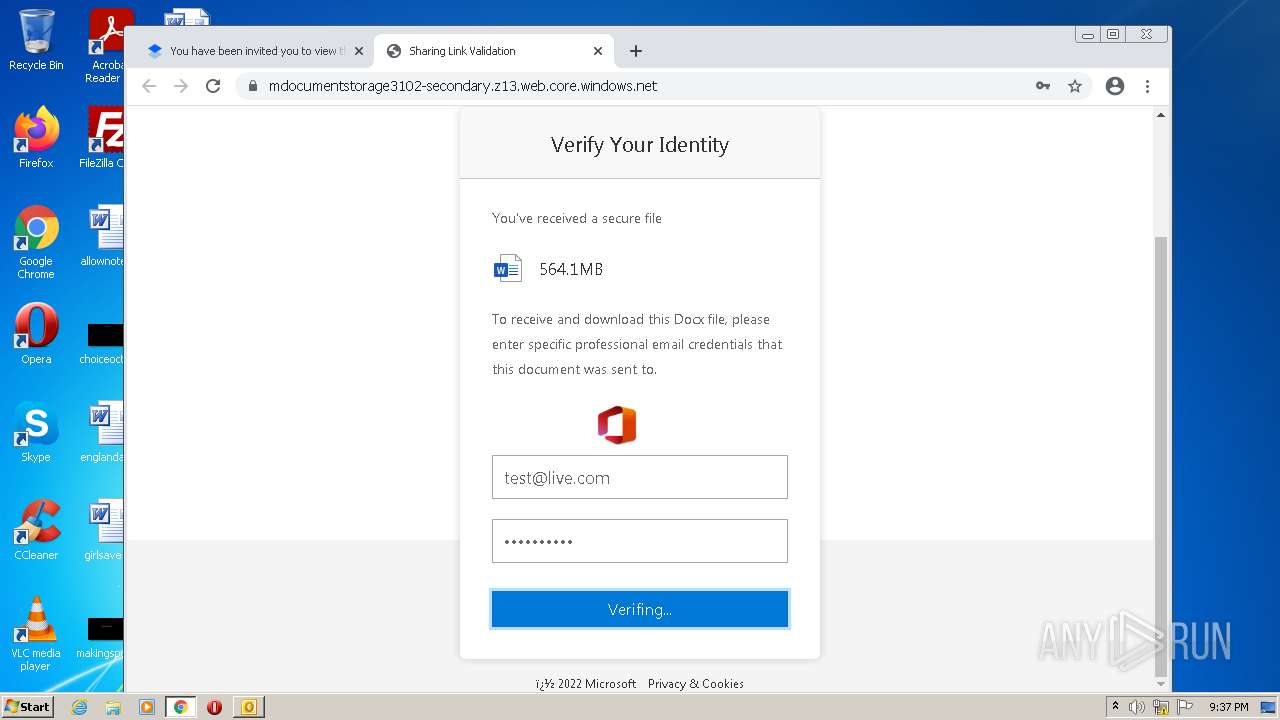
| File name: | phish_alert_sp2_2.0.0.0.eml |
| Full analysis: | https://app.any.run/tasks/8d909a92-1864-4d46-a78d-b940138ef710 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 20:34:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 3F458ECF8663387D4070CDA3B83BEA2C |
| SHA1: | 59E858BC2D4FDCC646D3F83D5A73D40829A977EC |
| SHA256: | 52F000B20602144EE6BC493AEABE9F5D4C7A5AA01BFFE77863A3EFEC493ABA48 |
| SSDEEP: | 6144:NfAwMxqbLzA1rNPktp7Jrv/U543TbcjNjn:NfAwb8RqtpNrvrQjxn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- OUTLOOK.EXE (PID: 2948)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1180)
Reads the computer name
- OUTLOOK.EXE (PID: 2948)
Searches for installed software
- OUTLOOK.EXE (PID: 2948)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1392)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3412)
Application launched itself
- iexplore.exe (PID: 3412)
- chrome.exe (PID: 1392)
Reads the computer name
- iexplore.exe (PID: 3412)
- iexplore.exe (PID: 1180)
- chrome.exe (PID: 1392)
- chrome.exe (PID: 2908)
- chrome.exe (PID: 1756)
- chrome.exe (PID: 4008)
- chrome.exe (PID: 4072)
- chrome.exe (PID: 724)
- chrome.exe (PID: 1288)
- chrome.exe (PID: 2084)
- chrome.exe (PID: 3288)
Checks supported languages
- iexplore.exe (PID: 3412)
- iexplore.exe (PID: 1180)
- chrome.exe (PID: 1392)
- chrome.exe (PID: 3480)
- chrome.exe (PID: 2908)
- chrome.exe (PID: 3416)
- chrome.exe (PID: 1852)
- chrome.exe (PID: 1756)
- chrome.exe (PID: 4020)
- chrome.exe (PID: 1712)
- chrome.exe (PID: 4072)
- chrome.exe (PID: 1880)
- chrome.exe (PID: 3076)
- chrome.exe (PID: 3684)
- chrome.exe (PID: 4008)
- chrome.exe (PID: 1656)
- chrome.exe (PID: 2880)
- chrome.exe (PID: 3700)
- chrome.exe (PID: 2156)
- chrome.exe (PID: 3028)
- chrome.exe (PID: 1288)
- chrome.exe (PID: 1396)
- chrome.exe (PID: 724)
- chrome.exe (PID: 2084)
- chrome.exe (PID: 2972)
- chrome.exe (PID: 3288)
Reads internet explorer settings
- iexplore.exe (PID: 1180)
Manual execution by user
- chrome.exe (PID: 1392)
Checks Windows Trust Settings
- iexplore.exe (PID: 1180)
- iexplore.exe (PID: 3412)
Reads settings of System Certificates
- iexplore.exe (PID: 1180)
- iexplore.exe (PID: 3412)
- chrome.exe (PID: 1756)
Reads the date of Windows installation
- iexplore.exe (PID: 3412)
- chrome.exe (PID: 2084)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
67
Monitored processes
27
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 724 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,9610895756291864258,14090402080685074688,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4124 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1180 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3412 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,9610895756291864258,14090402080685074688,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2424 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,9610895756291864258,14090402080685074688,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=536 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,9610895756291864258,14090402080685074688,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3752 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1712 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,9610895756291864258,14090402080685074688,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2168 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1032,9610895756291864258,14090402080685074688,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1344 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1852 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,9610895756291864258,14090402080685074688,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1936 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,9610895756291864258,14090402080685074688,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2676 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
34 008
Read events
33 150
Write events
821
Delete events
37
Modification events
| (PID) Process: | (2948) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2948) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2948) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2948) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2948) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2948) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2948) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2948) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2948) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2948) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
327
Text files
153
Unknown types
43
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2948 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9E34.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2948 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2948 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1180 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1180 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | der | |
MD5:— | SHA256:— | |||
| 1180 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:— | SHA256:— | |||
| 1180 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:— | SHA256:— | |||
| 1180 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:— | SHA256:— | |||
| 1180 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\35DDEDF268117918D1D277A171D8DF7B_72E9B602DBBE8F382B48D98F49AE6328 | der | |
MD5:— | SHA256:— | |||
| 1180 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\35DDEDF268117918D1D277A171D8DF7B_72E9B602DBBE8F382B48D98F49AE6328 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
109
DNS requests
49
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2948 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
1180 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEARjCJDaop17YcNTR%2BYV%2F24%3D | US | der | 471 b | whitelisted |
1180 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEA8SS204AU0V7RwfjlLyRTc%3D | US | der | 471 b | whitelisted |
1180 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
3412 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 10.9 Kb | whitelisted |
3412 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
1180 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 5.64 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2948 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
1180 | iexplore.exe | 162.125.66.18:443 | www.dropbox.com | Dropbox, Inc. | DE | suspicious |
1180 | iexplore.exe | 23.216.77.44:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
1180 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1180 | iexplore.exe | 104.16.100.29:443 | cfl.dropboxstatic.com | Cloudflare Inc | US | shared |
3412 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1180 | iexplore.exe | 13.224.189.42:443 | assets.dropbox.com | — | US | suspicious |
1756 | chrome.exe | 142.250.181.228:443 | www.google.com | Google Inc. | US | whitelisted |
1756 | chrome.exe | 142.250.186.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1756 | chrome.exe | 142.250.74.206:443 | clients2.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.dropbox.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cfl.dropboxstatic.com |
| shared |
assets.dropbox.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1180 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
1756 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
— | — | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ga Domain |
1756 | chrome.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.ga) in TLS SNI |