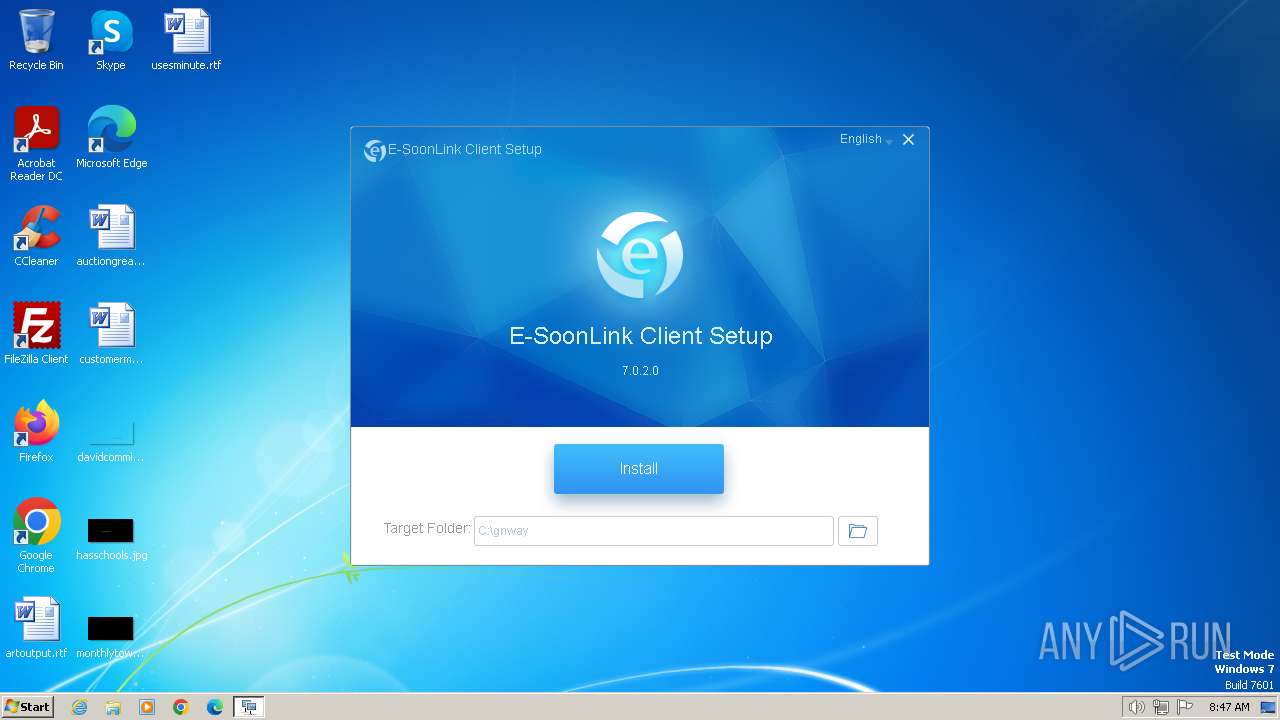
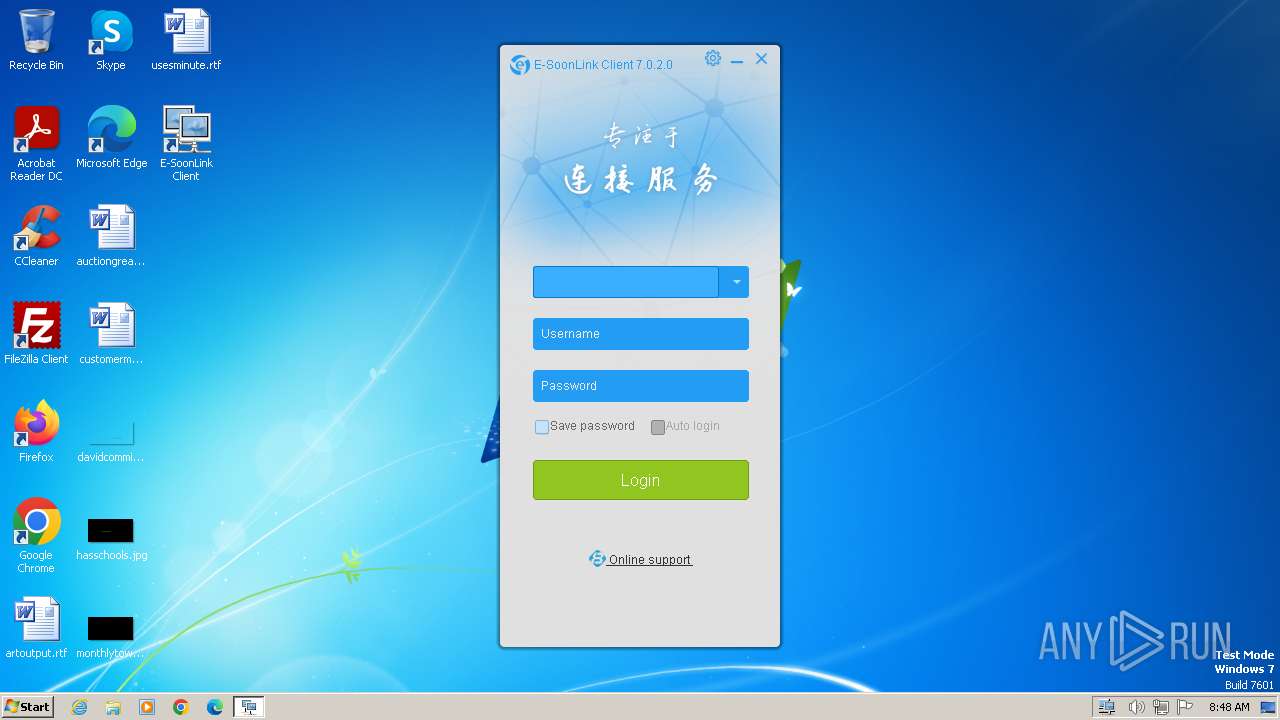
| File name: | setup_std_client.exe |
| Full analysis: | https://app.any.run/tasks/33d6b81e-8bbd-4692-9dac-b2b11d81c218 |
| Verdict: | Malicious activity |
| Analysis date: | December 20, 2023, 08:47:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | A0CEB79E6DE4D2A5EA46067BF07FDDB6 |
| SHA1: | 9A28532665B16E4B775535C8F1E1905CC79A0C6D |
| SHA256: | 52E3DC730ED4BE2ABB04169FAAC4B4D72ADE35DC5AA98621EF7E3BE0B06C41FB |
| SSDEEP: | 196608:ixV43PYUuOUvWS5eG6utpko7sMQWbRwuOLA:ixV4/YUuOUuSYGlqCYWqhLA |
MALICIOUS
Creates a writable file in the system directory
- setup_std_client.exe (PID: 2080)
Drops the executable file immediately after the start
- setup_std_client.exe (PID: 2080)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- setup_std_client.exe (PID: 2080)
Process drops legitimate windows executable
- setup_std_client.exe (PID: 2080)
The process creates files with name similar to system file names
- setup_std_client.exe (PID: 2080)
Drops a system driver (possible attempt to evade defenses)
- setup_std_client.exe (PID: 2080)
Drops 7-zip archiver for unpacking
- setup_std_client.exe (PID: 2080)
INFO
Checks supported languages
- setup_std_client.exe (PID: 2080)
- GNESLClient.exe (PID: 1840)
- ESLUSBServer.exe (PID: 1972)
Reads the computer name
- setup_std_client.exe (PID: 2080)
- ESLUSBServer.exe (PID: 1972)
- GNESLClient.exe (PID: 1840)
Create files in a temporary directory
- setup_std_client.exe (PID: 2080)
Creates files in the program directory
- setup_std_client.exe (PID: 2080)
Reads the machine GUID from the registry
- setup_std_client.exe (PID: 2080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 23:53:18+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25088 |
| InitializedDataSize: | 124928 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x36a0 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.0.2.81 |
| ProductVersionNumber: | 7.0.2.81 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| ProductName: | - |
Total processes
41
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1840 | C:\gnway\eSoonlink\GNESLClient.exe | C:\gnway\eSoonlink\GNESLClient.exe | — | setup_std_client.exe | |||||||||||
User: admin Integrity Level: HIGH Description: GNESLCli Application Exit code: 0 Version: 7.0.2.81 Modules
| |||||||||||||||
| 1972 | C:\gnway\eSoonlink\ESLUSBServer.exe install | C:\gnway\eSoonlink\ESLUSBServer.exe | — | GNESLClient.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2080 | "C:\Users\admin\AppData\Local\Temp\setup_std_client.exe" | C:\Users\admin\AppData\Local\Temp\setup_std_client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\AppData\Local\Temp\setup_std_client.exe" | C:\Users\admin\AppData\Local\Temp\setup_std_client.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
952
Read events
950
Write events
1
Delete events
1
Modification events
| (PID) Process: | (2080) setup_std_client.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2080) setup_std_client.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\gnway\esoonlink\Client\PrintSetup |
| Operation: | write | Name: | PrintQuality |
Value: ÖÐ | |||
Executable files
61
Suspicious files
11
Text files
74
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2080 | setup_std_client.exe | C:\Users\admin\AppData\Local\Temp\nsj55D.tmp\System.dll | executable | |
MD5:00A0194C20EE912257DF53BFE258EE4A | SHA256:DC4DA2CCADB11099076926B02764B2B44AD8F97CD32337421A4CC21A3F5448F3 | |||
| 2080 | setup_std_client.exe | C:\gnway\eSoonlink\ESLDriverAutoInstaller.dll | executable | |
MD5:DEB250523C38D00BA151740165822959 | SHA256:0AF367ED69680CD5CA6F3705F0D68B20030273E1A82A2704B9BE1A0A22752ABB | |||
| 2080 | setup_std_client.exe | C:\gnway\eSoonlink\VCClient.dll | executable | |
MD5:0FC8D6172BE1053828DBA866B7254828 | SHA256:F09E3169B070AF84C417A757EC27C4CD7B3FEEBA352EDD8726941E2D2341D22E | |||
| 2080 | setup_std_client.exe | C:\gnway\eSoonlink\GNLink_e.exe | executable | |
MD5:1D786C4F775ED5043321B5C57A05D061 | SHA256:4B0CE49CD3172B6E80E30E15FF342AD33AA955ACC3CBF56680A609A06443C6A8 | |||
| 2080 | setup_std_client.exe | C:\gnway\eSoonlink\GNClientPro.exe | executable | |
MD5:090FAC82656923A1860C9EC4916A8C06 | SHA256:92121DAD896CD6C60841116E49C9BFB728E55848FBADC083F7536FA81FAC4197 | |||
| 2080 | setup_std_client.exe | C:\Users\admin\AppData\Local\Temp\Language_sc.ini | text | |
MD5:B32D22CD78158F6F39F70FE65B888B76 | SHA256:C6C750A8173A00D0F05A8749F270F3D25CD2D6041B2E8D4201AC94FA8022BB3C | |||
| 2080 | setup_std_client.exe | C:\gnway\eSoonlink\GNESLClient.exe | executable | |
MD5:0411D0047B0FB6B92B90AAED78FBA848 | SHA256:4F080220C6170DBAD76C2E0D56B99415A1E029186BFF688D1231511A630A2DCC | |||
| 2080 | setup_std_client.exe | C:\gnway\eSoonlink\FileType.bat | text | |
MD5:684D39A99066F5E641D06DE9E930150D | SHA256:BF99ECE581EE8C07C2F2D306C1C3E308D7C4362896416602DF9D17DD9E74B908 | |||
| 2080 | setup_std_client.exe | C:\Users\admin\AppData\Local\Temp\skin\Language_en.ini | text | |
MD5:7FF8A48B8B86FB67E11FFEC659209F47 | SHA256:9E9DA9F85D8A4900D451132B0845758C92A90F71FD3FE410AE9A4A35FBD593EA | |||
| 2080 | setup_std_client.exe | C:\gnway\eSoonlink\ESLUSBServer.exe | executable | |
MD5:25F6F07E5BAFD68118CA1585F8DB5036 | SHA256:616E2FA71828A807B2BF2EBECBB3EDC0C66573F3DFF226B87C065094827DA246 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |