| URL: | http://31.168.230.11/flix/buffer/thumbs/flix.gif |
| Full analysis: | https://app.any.run/tasks/937089df-2af4-44b7-bec6-d376260ddf65 |
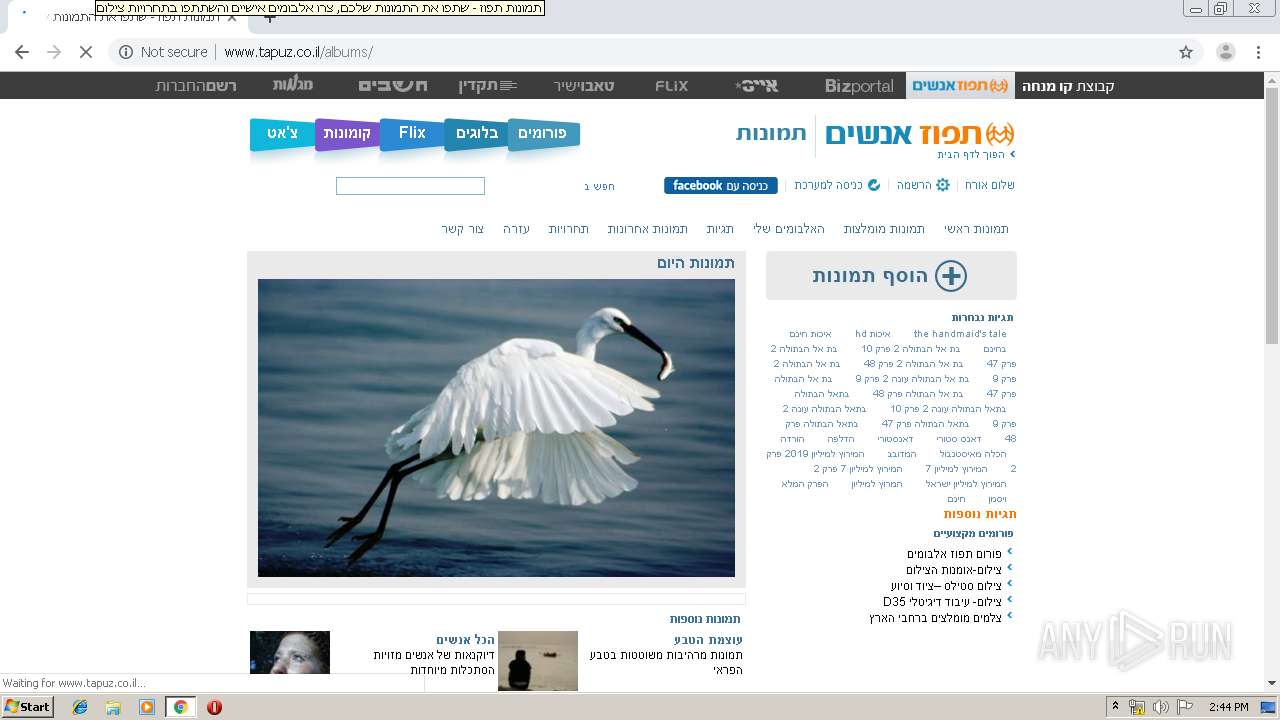
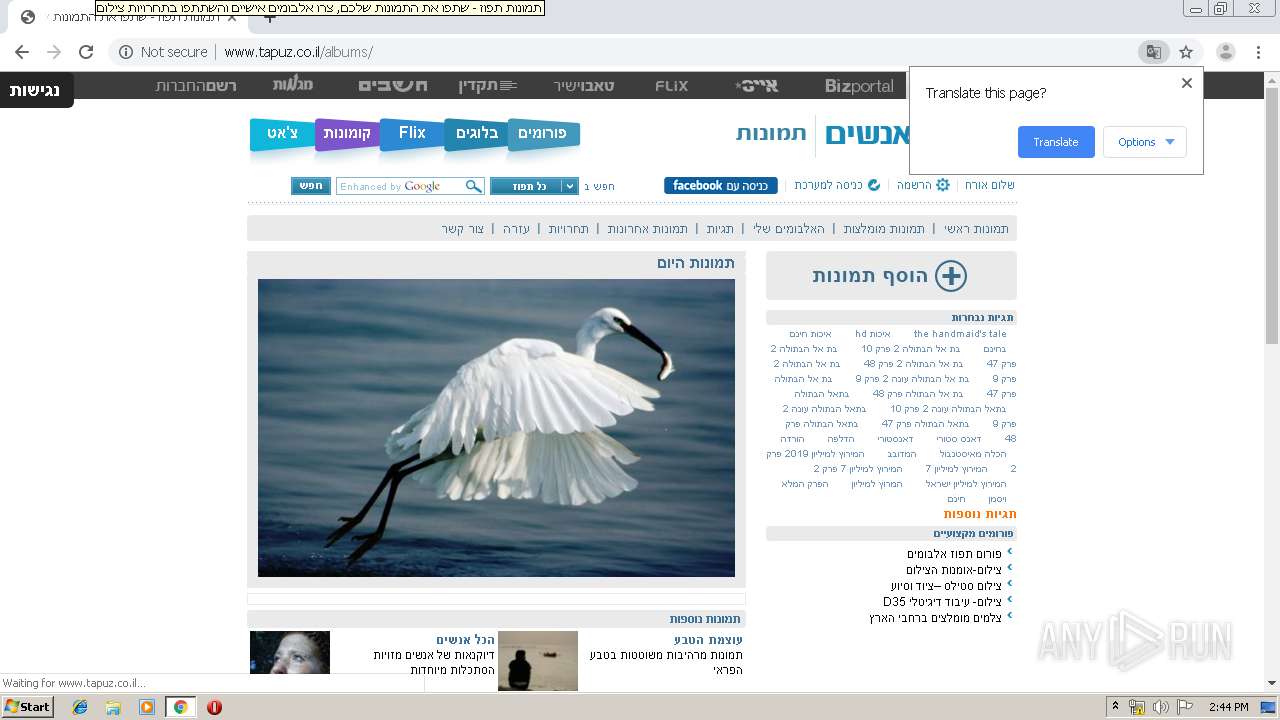
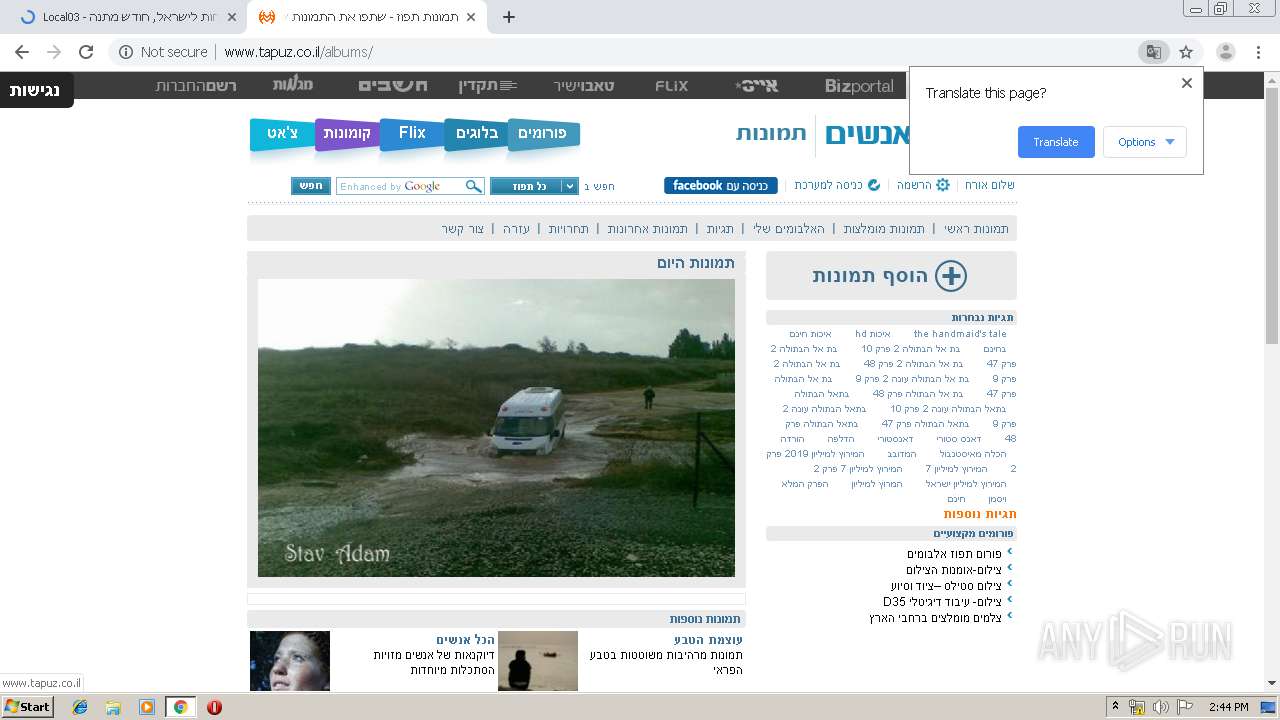
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 13:43:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 488B81B459EAB23C96582407AD18D842 |
| SHA1: | 18C6B7552B611DB3A6175175F8C3FD1436A6EAD7 |
| SHA256: | 52A0AACFE93CD9D4FEBC45BC3A263F7ADC7B28676A3DC2AA5FC695033C6F629E |
| SSDEEP: | 3:N1KGyWhuJ7wf69YbMD:CGCMyV |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3880)
INFO
Application launched itself
- chrome.exe (PID: 3880)
Changes settings of System certificates
- chrome.exe (PID: 3128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
62
Monitored processes
27
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,5461602649931781349,1546450854198267236,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16476636992069560490 --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1288 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,5461602649931781349,1546450854198267236,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1336530929484735201 --renderer-client-id=17 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2940 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,5461602649931781349,1546450854198267236,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14079423773804253475 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2484 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,5461602649931781349,1546450854198267236,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13091248058857079504 --mojo-platform-channel-handle=3404 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,5461602649931781349,1546450854198267236,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11322913261564880382 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2228 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,5461602649931781349,1546450854198267236,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8612016954792380140 --mojo-platform-channel-handle=3492 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6fafa9d0,0x6fafa9e0,0x6fafa9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2264 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,5461602649931781349,1546450854198267236,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6846975878262513865 --mojo-platform-channel-handle=3516 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,5461602649931781349,1546450854198267236,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=140369072335914443 --renderer-client-id=21 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2672 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,5461602649931781349,1546450854198267236,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16830711759601558151 --mojo-platform-channel-handle=3432 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
626
Read events
529
Write events
92
Delete events
5
Modification events
| (PID) Process: | (3880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (3880) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3880-13207844633242125 |
Value: 259 | |||
Executable files
0
Suspicious files
89
Text files
136
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\1728f7c1-3f7f-47a7-a357-10125a7f9177.tmp | — | |
MD5:— | SHA256:— | |||
| 3880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFdf57c.TMP | text | |
MD5:— | SHA256:— | |||
| 3880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RFdf5da.TMP | text | |
MD5:— | SHA256:— | |||
| 3880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFdf58c.TMP | text | |
MD5:— | SHA256:— | |||
| 3880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RFdf59b.TMP | text | |
MD5:— | SHA256:— | |||
| 3880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
90
TCP/UDP connections
64
DNS requests
54
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
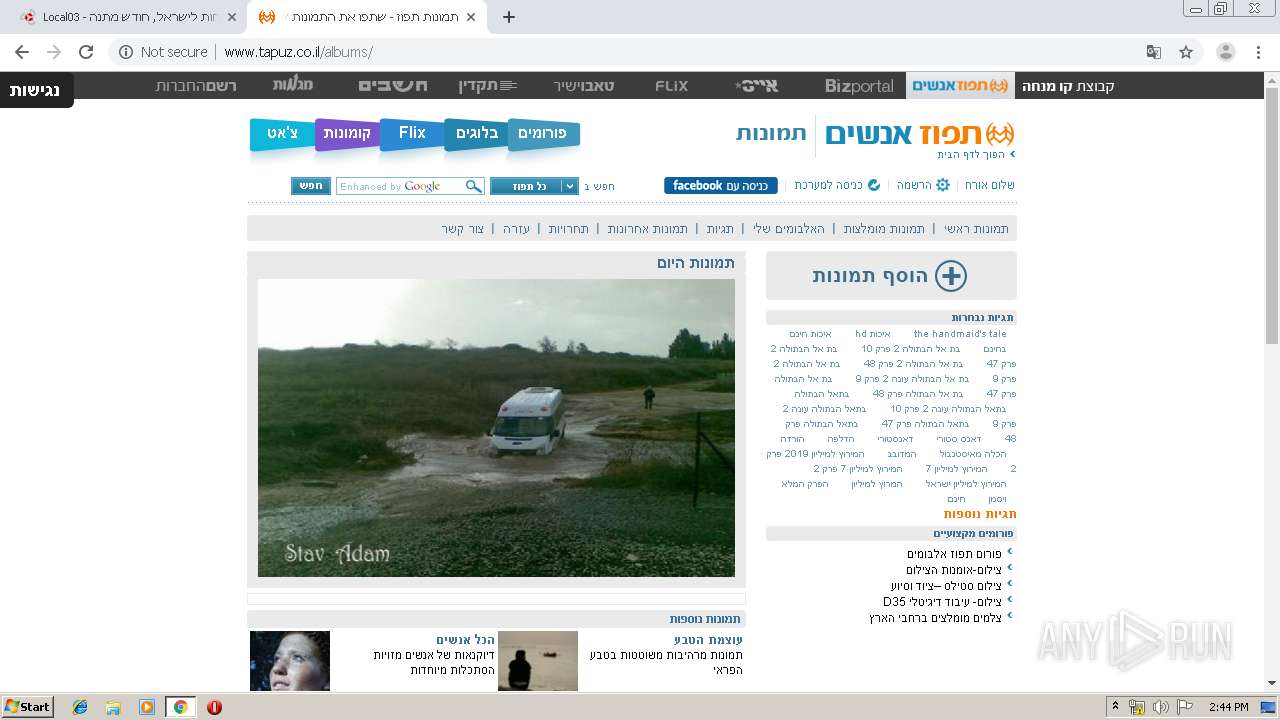
3128 | chrome.exe | GET | 200 | 31.168.230.10:80 | http://www.tapuz.co.il/tapuzGlobals/Common/Styles/headerDefault.css | IL | text | 3.15 Kb | suspicious |
3128 | chrome.exe | GET | 200 | 31.168.230.11:80 | http://31.168.230.11/flix/buffer/thumbs/flix.gif | IL | image | 2.11 Kb | unknown |
3128 | chrome.exe | GET | 200 | 31.168.230.10:80 | http://www.tapuz.co.il/Common/JS/userLogin.js | IL | text | 511 b | suspicious |
3128 | chrome.exe | GET | 200 | 31.168.230.10:80 | http://www.tapuz.co.il/tapuzGlobals/Common/Styles/footerDefault.css | IL | text | 849 b | suspicious |
3128 | chrome.exe | GET | 200 | 31.168.230.10:80 | http://www.tapuz.co.il/albums/style/albums.css | IL | text | 5.23 Kb | suspicious |
3128 | chrome.exe | GET | 200 | 31.168.230.10:80 | http://www.tapuz.co.il/tapuzGlobals/Common/styles/kavManhe.css | IL | text | 767 b | suspicious |
3128 | chrome.exe | GET | 302 | 31.168.230.11:80 | http://31.168.230.11/ | IL | html | 150 b | unknown |
3128 | chrome.exe | GET | 200 | 31.168.230.10:80 | http://www.tapuz.co.il/hit/cooperation/defaultHitStyle.css | IL | text | 1.10 Kb | suspicious |
3128 | chrome.exe | GET | 200 | 31.168.230.10:80 | http://www.tapuz.co.il/common/style/colorbox.css | IL | text | 1.74 Kb | suspicious |
3128 | chrome.exe | GET | 301 | 31.168.230.10:80 | http://www.tapuz.co.il/albums | IL | html | 153 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3128 | chrome.exe | 172.217.22.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3128 | chrome.exe | 216.58.206.14:443 | clients2.google.com | Google Inc. | US | whitelisted |
3128 | chrome.exe | 172.217.21.196:443 | www.google.com | Google Inc. | US | whitelisted |
3128 | chrome.exe | 172.217.22.97:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
3128 | chrome.exe | 172.217.22.99:443 | www.google.no | Google Inc. | US | whitelisted |
3128 | chrome.exe | 172.217.18.174:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
3128 | chrome.exe | 172.217.23.131:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3128 | chrome.exe | 188.121.36.237:80 | certificates.godaddy.com | GoDaddy.com, LLC | NL | suspicious |
3128 | chrome.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3128 | chrome.exe | 46.166.134.22:80 | live.sekindo.com | NForce Entertainment B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
www.google.no |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |
r4---sn-5hne6nsr.gvt1.com |
| whitelisted |
www.tapuz.co.il |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3128 | chrome.exe | A Network Trojan was detected | MALWARE [PTsecurity] Inbox.Toolbar Install xml Server Response |