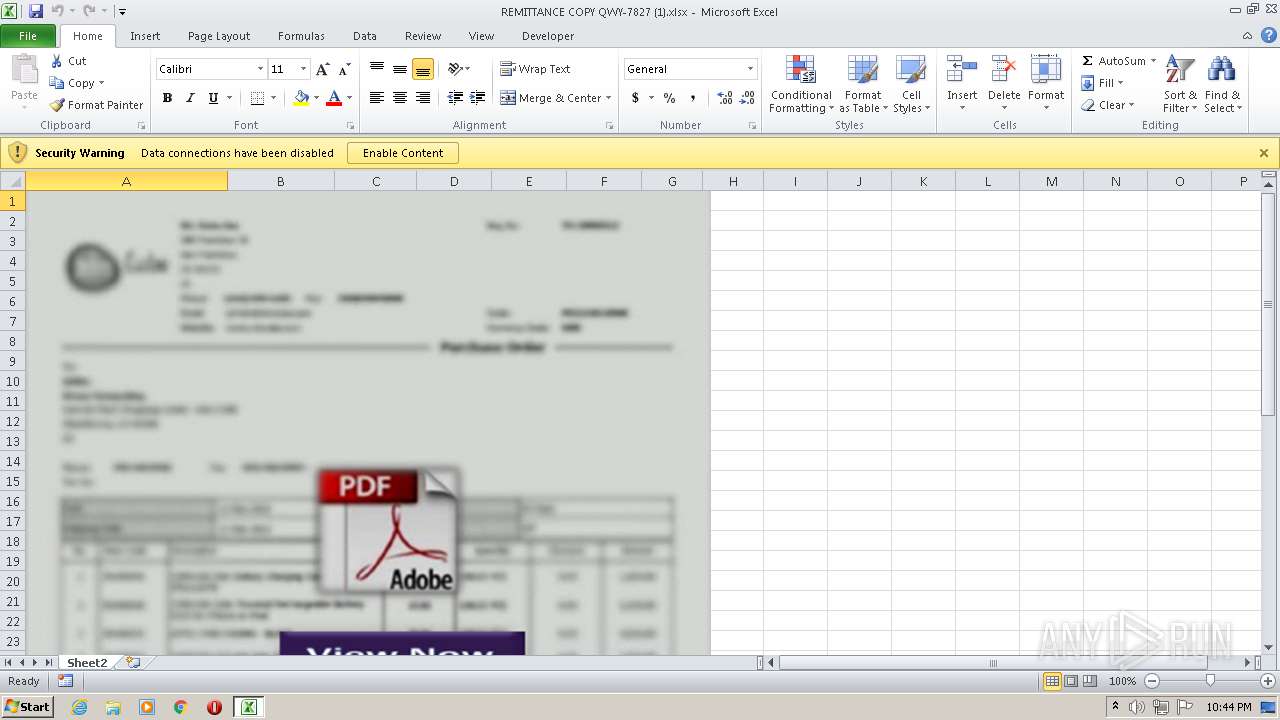
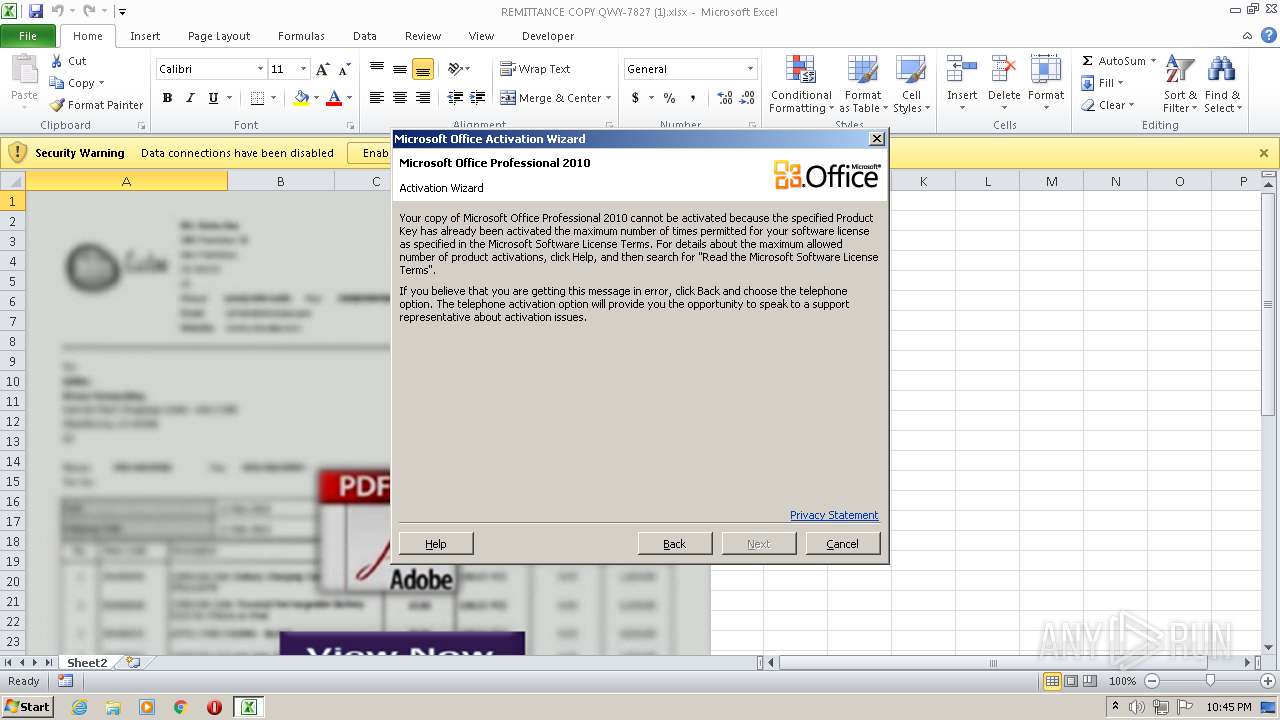
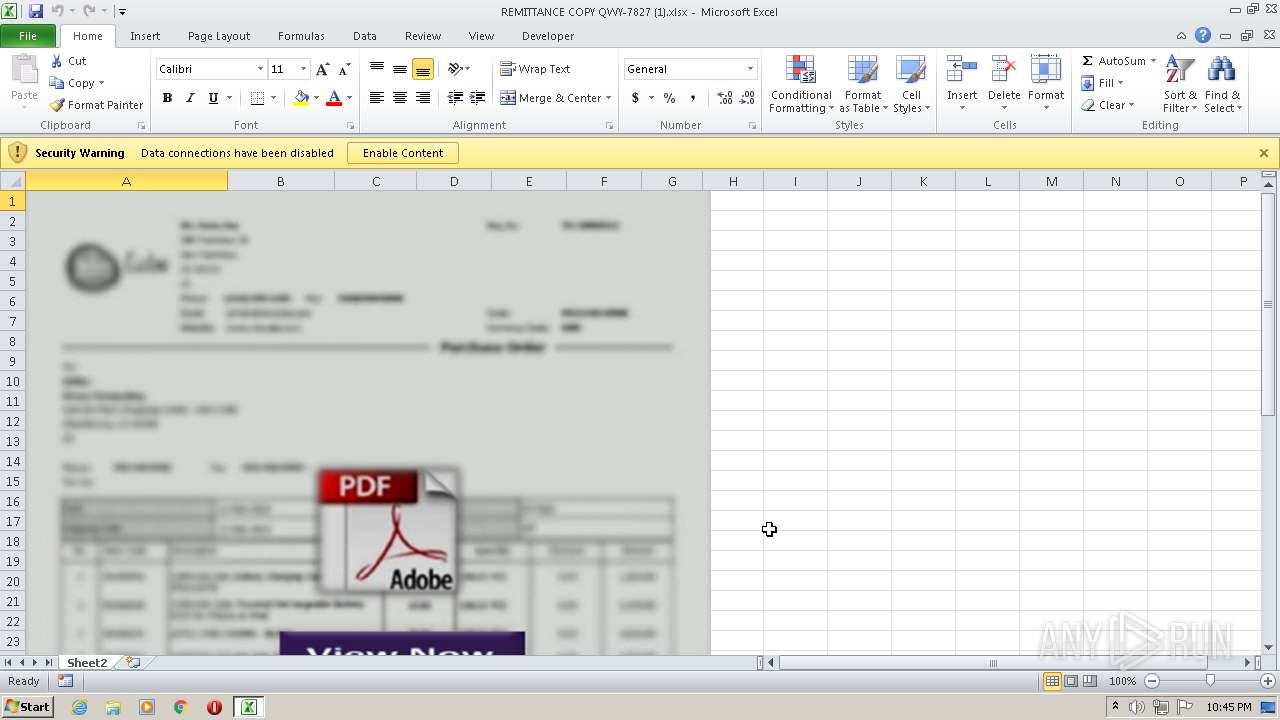
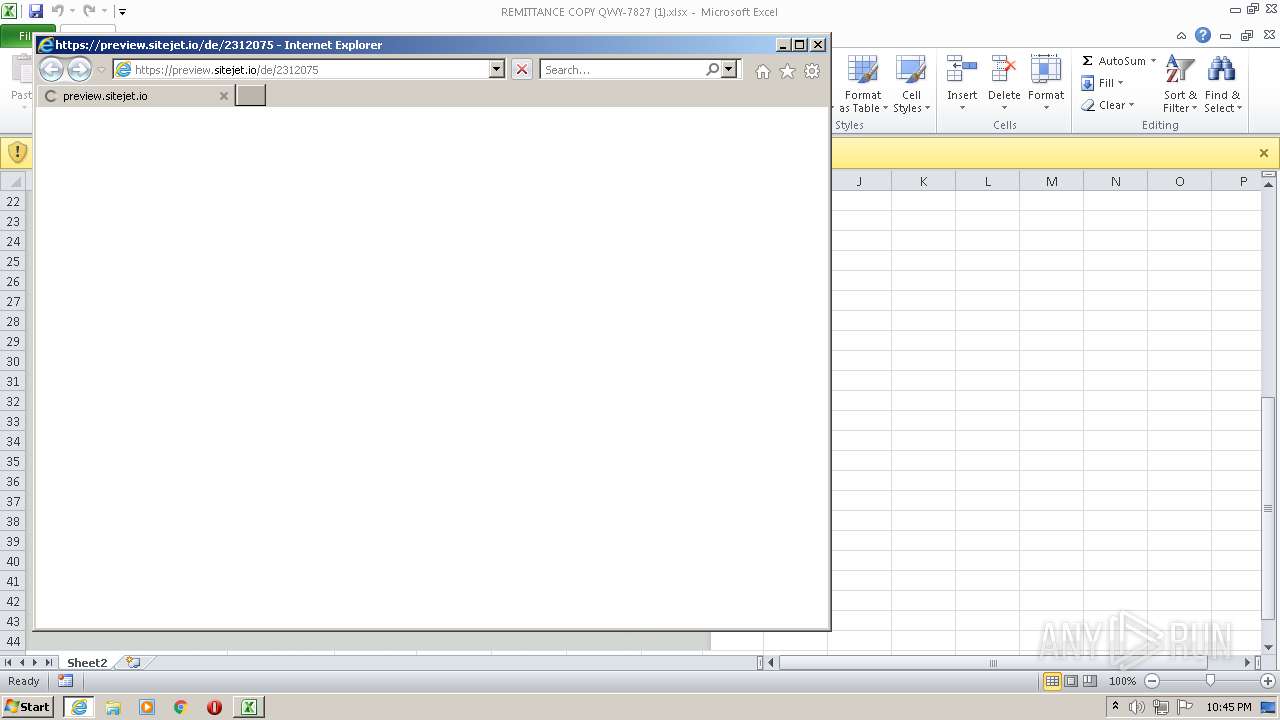
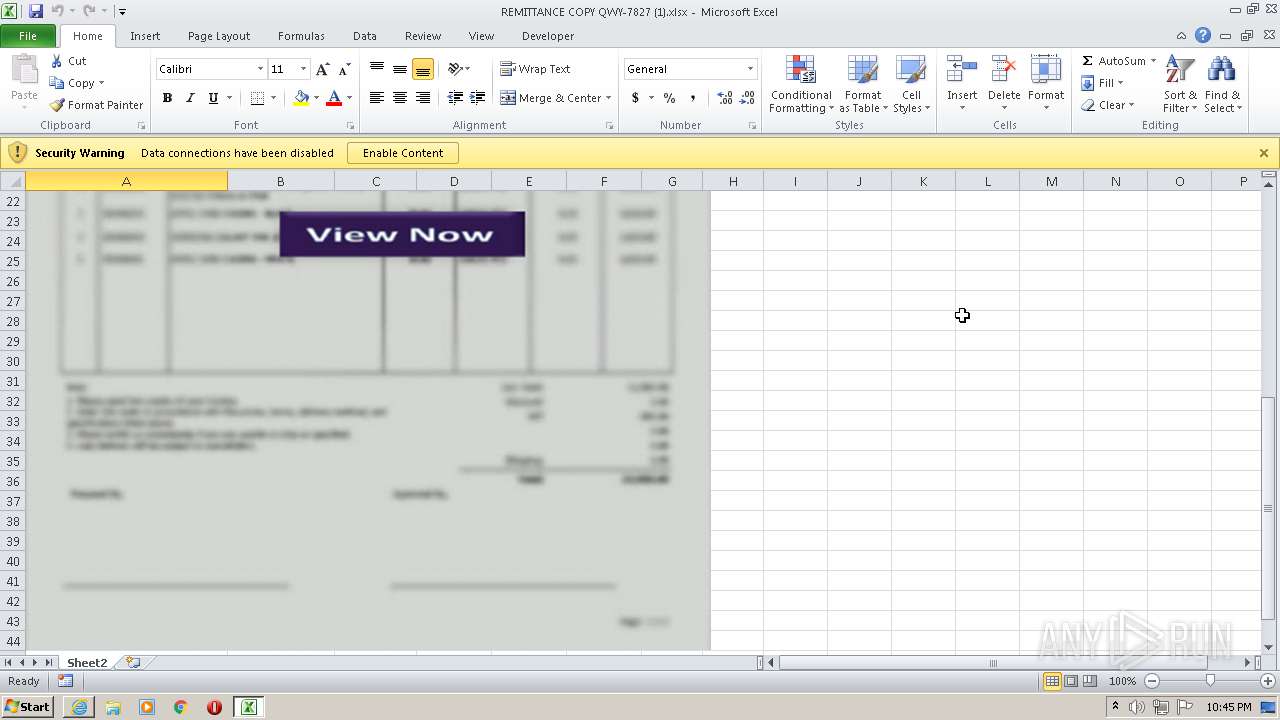
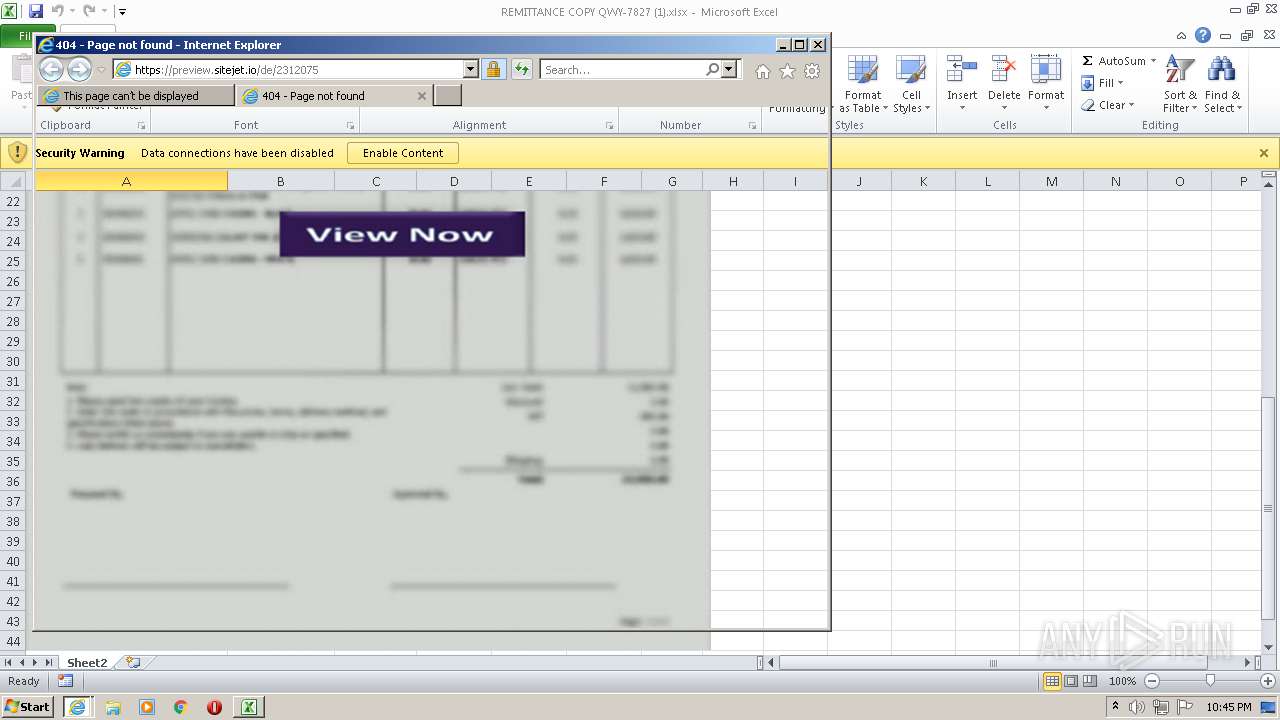
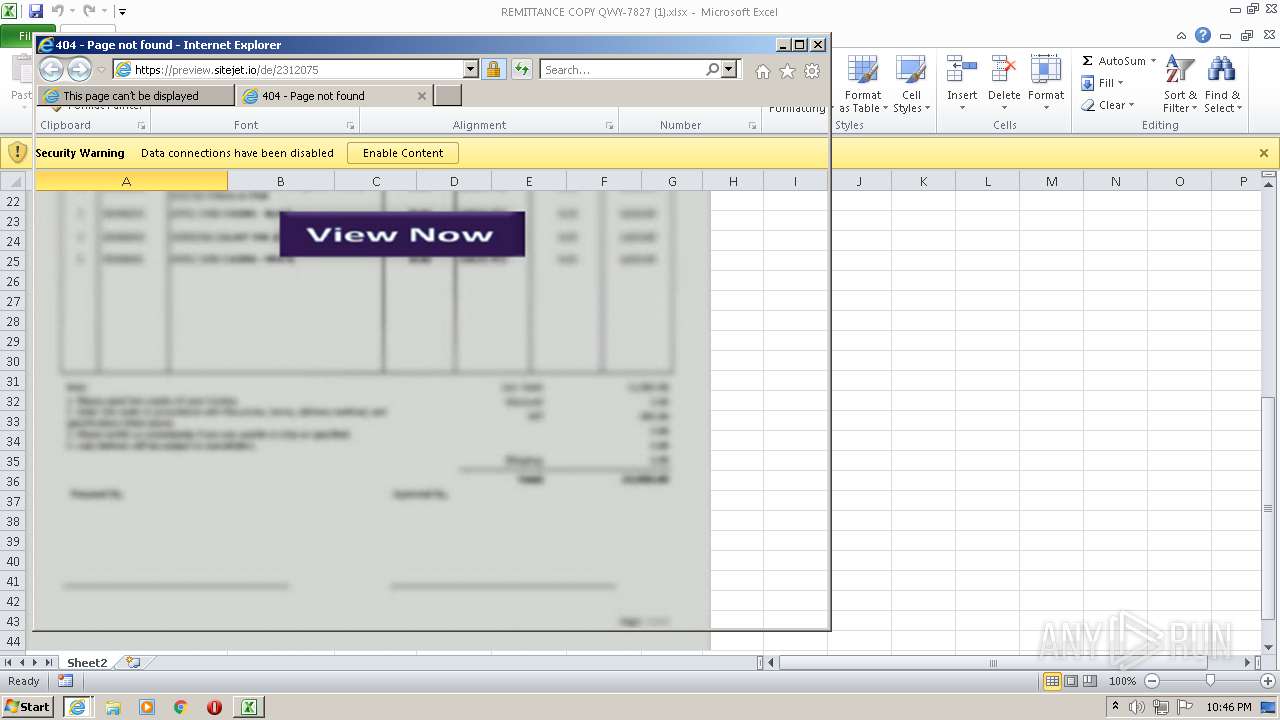
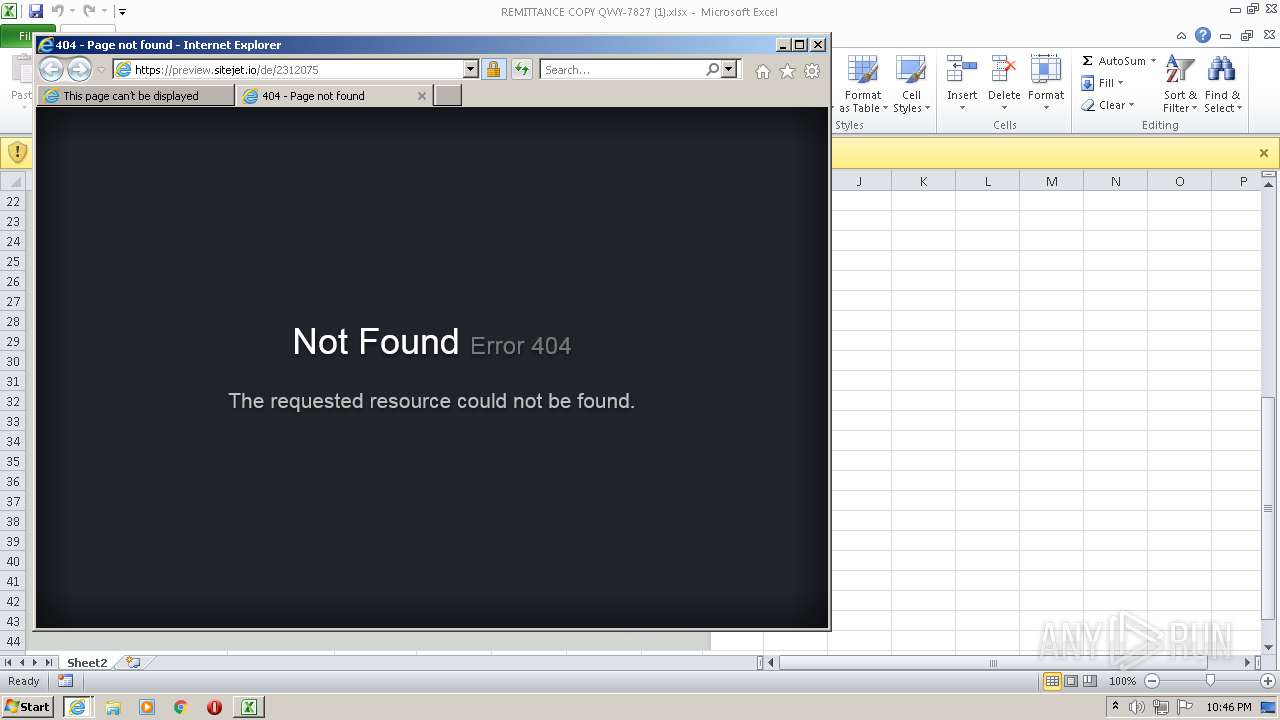
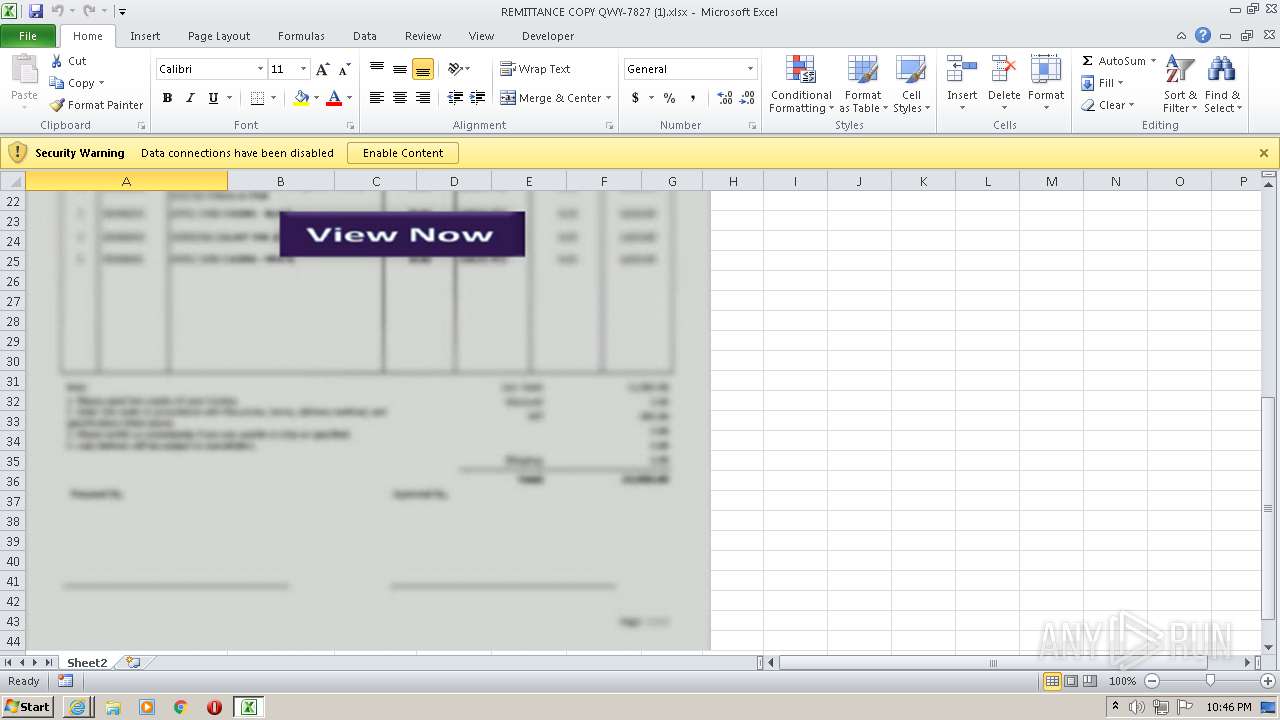
| File name: | REMITTANCE COPY QWY-7827 (1).xlsx |
| Full analysis: | https://app.any.run/tasks/aa5a8958-dd79-4b88-a0eb-c582d57169f1 |
| Verdict: | Malicious activity |
| Analysis date: | August 24, 2021, 21:44:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 68198B33DEFE80F4DA2E05EE884835B1 |
| SHA1: | 20969920C4B9B1786654EEA284FDD6D88E070E56 |
| SHA256: | 528CDFC78A271E9294573B70AB21D5832A4839BF2EE21BAB44F6C8C387D066A6 |
| SSDEEP: | 6144:s8x1X+6uuU/hvvANiuOepw0JfJJ3/Bfdkjt36DtPQL6ltGK:bnudHhvvANiuOepw0Jf73ZfEt36GWloK |
MALICIOUS
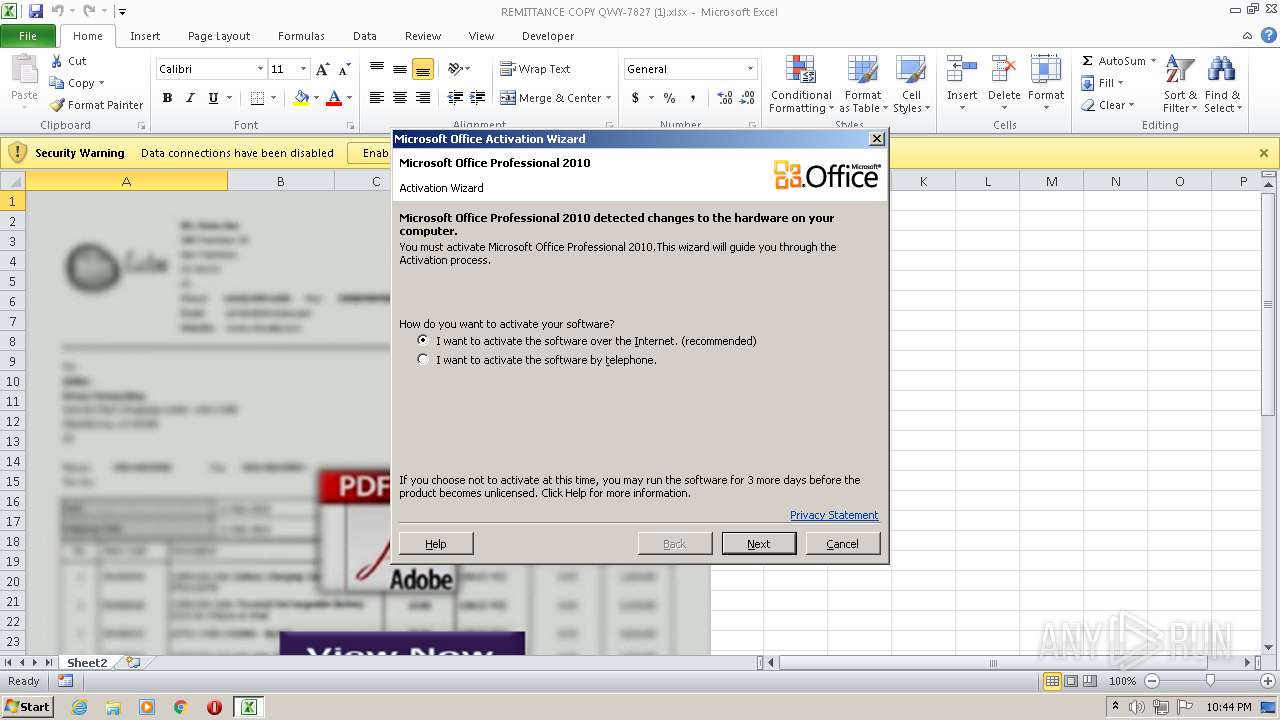
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2616)
SUSPICIOUS
Reads Microsoft Outlook installation path
- hh.exe (PID: 1236)
- iexplore.exe (PID: 3220)
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 3520)
Reads internet explorer settings
- hh.exe (PID: 1236)
Executed via COM
- iexplore.exe (PID: 3520)
INFO
Reads settings of System Certificates
- EXCEL.EXE (PID: 2616)
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 3220)
Reads the computer name
- hh.exe (PID: 1236)
- iexplore.exe (PID: 3520)
- EXCEL.EXE (PID: 2616)
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 3220)
Reads internet explorer settings
- EXCEL.EXE (PID: 2616)
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 3220)
Checks supported languages
- iexplore.exe (PID: 3220)
- EXCEL.EXE (PID: 2616)
- hh.exe (PID: 1236)
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 2924)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2616)
Checks Windows Trust Settings
- EXCEL.EXE (PID: 2616)
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 3220)
Reads Microsoft Outlook installation path
- EXCEL.EXE (PID: 2616)
Creates files in the user directory
- EXCEL.EXE (PID: 2616)
- iexplore.exe (PID: 3520)
Changes internet zones settings
- iexplore.exe (PID: 3520)
Application launched itself
- iexplore.exe (PID: 3520)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3520)
Changes settings of System certificates
- iexplore.exe (PID: 3520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsx | | | Excel Microsoft Office Open XML Format document (61.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (31.5) |
| .zip | | | ZIP compressed archive (7.2) |
EXIF
XML
| AppVersion: | 16.03 |
|---|---|
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| Company: | - |
| TitlesOfParts: | Sheet2 |
| HeadingPairs: |
|
| ScaleCrop: | No |
| DocSecurity: | None |
| Application: | Microsoft Excel |
| TotalEditTime: | - |
| ModifyDate: | 2021:08:24 17:26:00Z |
| CreateDate: | 2021:06:07 17:47:41Z |
| LastModifiedBy: | sammy |
XMP
| Creator: | Jaquez, Christian |
|---|
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 1799 |
| ZipCompressedSize: | 429 |
| ZipCRC: | 0x369c446e |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0006 |
| ZipRequiredVersion: | 20 |
Total processes
41
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1236 | "C:\Windows\hh.exe" -mapid 183675 "mk:@MSITStore:C:\Program Files\Common Files\Microsoft Shared\OFFICE14\Office Setup Controller\Office.en-us\SETUP.CHM" | C:\Windows\hh.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft� HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2616 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2924 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3520 CREDAT:333058 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3220 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3520 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3520 | "C:\Program Files\Internet Explorer\iexplore.exe" -startmediumtab -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
21 240
Read events
20 955
Write events
275
Delete events
10
Modification events
| (PID) Process: | (2616) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | 5}( |
Value: 357D2800380A0000010000000000000000000000 | |||
| (PID) Process: | (2616) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2616) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2616) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2616) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2616) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2616) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2616) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2616) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2616) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
16
Text files
25
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2616 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR8D15.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2616 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\644B8874112055B5E195ECB0E8F243A4 | der | |
MD5:— | SHA256:— | |||
| 2616 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9B676269C415D75C618072F0E0597ECE | binary | |
MD5:— | SHA256:— | |||
| 2616 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\my_website_presentation[1].htm | html | |
MD5:— | SHA256:— | |||
| 2616 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 2616 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\644B8874112055B5E195ECB0E8F243A4 | binary | |
MD5:— | SHA256:— | |||
| 2616 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\2312075[1].htm | html | |
MD5:— | SHA256:— | |||
| 1236 | hh.exe | C:\Users\admin\AppData\Local\Temp\IMT28D8.tmp | binary | |
MD5:5D0E5693027A0E5ADF1D49847779B65C | SHA256:AC0710AABAAEAAC65507050647FA9D97A82639DA0D1D6B436800B177478C6D6B | |||
| 2616 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\presentation[1].htm | html | |
MD5:— | SHA256:— | |||
| 3520 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
28
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2616 | EXCEL.EXE | POST | 302 | 104.92.93.19:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | NL | — | — | whitelisted |
2616 | EXCEL.EXE | POST | 302 | 104.92.93.19:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | NL | — | — | whitelisted |
1672 | svchost.exe | GET | 304 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?bdc4c6ff4d6f9b36 | US | — | — | whitelisted |
2616 | EXCEL.EXE | POST | 302 | 104.92.93.19:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | NL | — | — | whitelisted |
1672 | svchost.exe | GET | 304 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?908895d5f30f3f10 | US | — | — | whitelisted |
2616 | EXCEL.EXE | GET | 200 | 195.138.255.17:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgSmhFoDGYgXk%2FF%2FaCEmOGDtQA%3D%3D | DE | der | 503 b | shared |
2616 | EXCEL.EXE | GET | 200 | 195.138.255.9:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | DE | der | 1.16 Kb | whitelisted |
3520 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3520 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2616 | EXCEL.EXE | GET | 200 | 23.220.213.213:80 | http://x1.c.lencr.org/ | US | der | 717 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2616 | EXCEL.EXE | 104.92.93.19:80 | go.microsoft.com | Akamai Technologies, Inc. | NL | unknown |
2616 | EXCEL.EXE | 40.91.76.224:443 | activation.sls.microsoft.com | Microsoft Corporation | US | whitelisted |
2616 | EXCEL.EXE | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2616 | EXCEL.EXE | 195.138.255.17:80 | r3.o.lencr.org | AS33891 Netzbetrieb GmbH | DE | whitelisted |
2616 | EXCEL.EXE | 23.220.213.213:80 | x1.c.lencr.org | Akamai International B.V. | US | unknown |
3520 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1672 | svchost.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2924 | iexplore.exe | 136.243.5.208:443 | my.sitejet.io | Hetzner Online GmbH | DE | malicious |
3520 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3220 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
my.sitejet.io |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
cms.sitejet.io |
| unknown |
preview.sitejet.io |
| unknown |
api.bing.com |
| whitelisted |