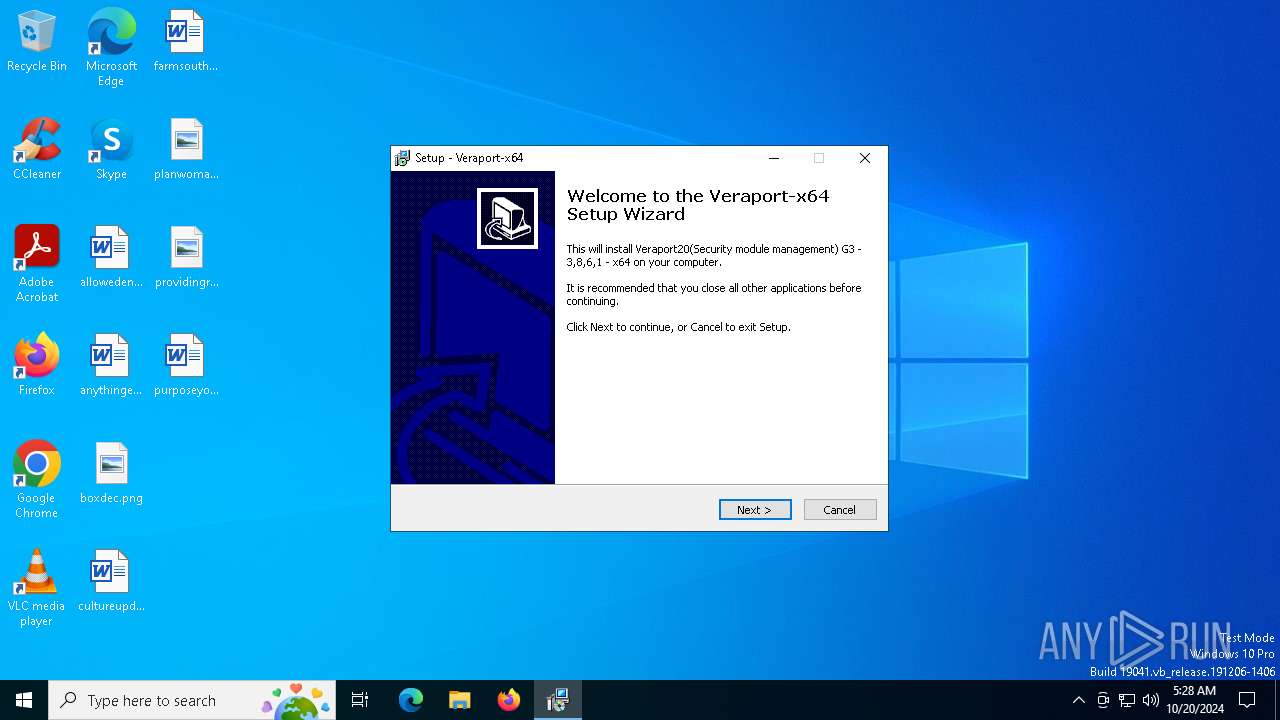
| File name: | veraport-g3-x64.exe |
| Full analysis: | https://app.any.run/tasks/c2e99ad0-f158-4afc-8f00-9c09d0918580 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2024, 05:28:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | FCA6017276F0FEEEE26A095A6509530D |
| SHA1: | BBCAB6D538BB641CC2F442D34962DE7F67DEFE7D |
| SHA256: | 52773760053A7D754C22E9741BDD38F29FD7EE366CA9C4F8B58ED428172CF567 |
| SSDEEP: | 98304:+HOSG0gEMfYUx8ahLChwu7mfqTmqAmutOA/yuOw1hz09qvJ0qeKnl51uZeTrPZt4:PbIpx8Jfas5pDIzJ |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- veraport-g3-x64.tmp (PID: 6648)
SUSPICIOUS
Reads security settings of Internet Explorer
- veraport-g3-x64.tmp (PID: 5172)
- veraport20unloader.exe (PID: 4556)
Executable content was dropped or overwritten
- veraport-g3-x64.exe (PID: 6436)
- veraport-g3-x64.exe (PID: 6508)
- veraport-g3-x64.tmp (PID: 6648)
- wpmsvcsetup.exe (PID: 540)
- wpmsvcsetup.tmp (PID: 6960)
Process drops legitimate windows executable
- veraport-g3-x64.tmp (PID: 6648)
- wpmsvcsetup.tmp (PID: 6960)
Reads the Windows owner or organization settings
- veraport-g3-x64.tmp (PID: 6648)
Starts SC.EXE for service management
- veraport-g3-x64.tmp (PID: 6648)
The process drops C-runtime libraries
- veraport-g3-x64.tmp (PID: 6648)
Reads the date of Windows installation
- veraport20unloader.exe (PID: 4556)
Executes as Windows Service
- wpmsvc.exe (PID: 7132)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 2648)
INFO
Create files in a temporary directory
- veraport-g3-x64.exe (PID: 6436)
- veraport-g3-x64.exe (PID: 6508)
- veraport-g3-x64.tmp (PID: 6648)
Checks supported languages
- veraport-g3-x64.tmp (PID: 5172)
- veraport-g3-x64.exe (PID: 6436)
- veraport-g3-x64.exe (PID: 6508)
- veraport-g3-x64.tmp (PID: 6648)
- veraport20unloader.exe (PID: 4556)
Reads the computer name
- veraport-g3-x64.tmp (PID: 5172)
- veraport-g3-x64.tmp (PID: 6648)
- veraport20unloader.exe (PID: 4556)
Process checks computer location settings
- veraport-g3-x64.tmp (PID: 5172)
- veraport20unloader.exe (PID: 4556)
The process uses the downloaded file
- veraport20unloader.exe (PID: 4556)
Manual execution by a user
- control.exe (PID: 2648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9c40 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.8.6.1 |
| ProductVersionNumber: | 3.8.6.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Wizvera |
| FileDescription: | Veraport |
| FileVersion: | 3.8.6.1 |
| LegalCopyright: | Wizvera |
| ProductName: | Veraport |
| ProductVersion: | 3,8,6,1 |
Total processes
197
Monitored processes
66
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\Users\admin\AppData\Local\Temp\is-A5IOP.tmp\wpmsvcsetup.exe" /VERYSILENT | C:\Users\admin\AppData\Local\Temp\is-A5IOP.tmp\wpmsvcsetup.exe | veraport-g3-x64.tmp | ||||||||||||
User: admin Company: WIZVERA Integrity Level: HIGH Description: Exit code: 0 Version: | |||||||||||||||
| 632 | "c:\users\admin\appdata\local\temp\is-a5iop.tmp\.\nss\certutil.exe" -A -n "WIZVERA-CA-SHA2" -t "TCu,Cuw,Tuw" -i c:\users\admin\appdata\local\temp\is-a5iop.tmp\wizvera_ca.crt -d "./" | C:\Users\admin\AppData\Local\Temp\is-A5IOP.tmp\nss\certutil.exe | — | wizcertutil.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 944 | "C:\WINDOWS\system32\sc.exe" start WizveraPMSvc | C:\Windows\System32\sc.exe | — | veraport-g3-x64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1056 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1172 | "c:\users\admin\appdata\local\temp\is-a5iop.tmp\.\nss_sql\certutil.exe" -A -n "WIZVERA-CA-SHA2" -t "TCu,Cuw,Tuw" -i c:\users\admin\appdata\local\temp\is-a5iop.tmp\wizvera_ca.crt -d sql:"./" | C:\Users\admin\AppData\Local\Temp\is-A5IOP.tmp\nss_sql\certutil.exe | — | wizcertutil.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 255 | |||||||||||||||
| 1252 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1576 | "c:\users\admin\appdata\local\temp\is-a5iop.tmp\.\nss\certutil.exe" -A -n "WIZVERA-CA-SHA2" -t "TCu,Cuw,Tuw" -i c:\users\admin\appdata\local\temp\is-a5iop.tmp\wizvera_ca.crt -d "./" | C:\Users\admin\AppData\Local\Temp\is-A5IOP.tmp\nss\certutil.exe | — | wizcertutil.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 1584 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CheckNetIsolation.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1584 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2312 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2312 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
655
Read events
655
Write events
0
Delete events
0
Modification events
Executable files
90
Suspicious files
47
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6648 | veraport-g3-x64.tmp | C:\Users\admin\AppData\Local\Temp\is-A5IOP.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 6648 | veraport-g3-x64.tmp | C:\Users\admin\AppData\Local\Temp\is-A5IOP.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 6508 | veraport-g3-x64.exe | C:\Users\admin\AppData\Local\Temp\is-TEMDJ.tmp\veraport-g3-x64.tmp | executable | |
MD5:67C5A4F36E1C91A3B85E440EDD7AD026 | SHA256:99C299D6565AB53D9AF66E0146737DC0ECFBC52ECF4740825B552DB0CC4210C6 | |||
| 6648 | veraport-g3-x64.tmp | C:\Program Files\Wizvera\Veraport20\is-H1AI1.tmp | executable | |
MD5:D61EF285731C8704F3B131A168DF08A4 | SHA256:DAF8F8F98E961CDE3DC0E8AB52E19CC66D2039E2FCC4681CD6A98E8642E794E6 | |||
| 6648 | veraport-g3-x64.tmp | C:\Program Files\Wizvera\Veraport20\is-F8GQ5.tmp | executable | |
MD5:AA4EF1C182A79F24B519167C41FAB32E | SHA256:5F196219171FB668B4022ACBE3E1D58A90D202D0622D6EBCD67D224AD9ED58DB | |||
| 6648 | veraport-g3-x64.tmp | C:\Program Files\Wizvera\Veraport20\is-G551K.tmp | executable | |
MD5:57709804AE9AEE4948827AD46291345E | SHA256:2C80C4FDD9246282A8A3DDA36BA2CF287B6F01D694B7D704FDCA48AC154E75CB | |||
| 6648 | veraport-g3-x64.tmp | C:\Program Files\Wizvera\Veraport20\is-89ULR.tmp | executable | |
MD5:0D1DCC7C7FCD03FAF31D13BD8AB10857 | SHA256:16D56C3DE5A9C252A0DE59489A1369D5993E4CBA8058B81446C053657206FA7A | |||
| 6648 | veraport-g3-x64.tmp | C:\Program Files\Wizvera\Veraport20\wizveraregsvr.exe | executable | |
MD5:AA4EF1C182A79F24B519167C41FAB32E | SHA256:5F196219171FB668B4022ACBE3E1D58A90D202D0622D6EBCD67D224AD9ED58DB | |||
| 6648 | veraport-g3-x64.tmp | C:\Program Files\Wizvera\Veraport20\npveraport20.dll | executable | |
MD5:0D1DCC7C7FCD03FAF31D13BD8AB10857 | SHA256:16D56C3DE5A9C252A0DE59489A1369D5993E4CBA8058B81446C053657206FA7A | |||
| 6648 | veraport-g3-x64.tmp | C:\Users\admin\AppData\Local\Temp\is-A5IOP.tmp\is-U9DBT.tmp | executable | |
MD5:AA8F3A80D78B19E1656E1E7C01605CC2 | SHA256:BB420F85C25137E65C63D0BD180C19D861DB366A3629C5E3F1BA13A82A4AA4DC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
56
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.136:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |