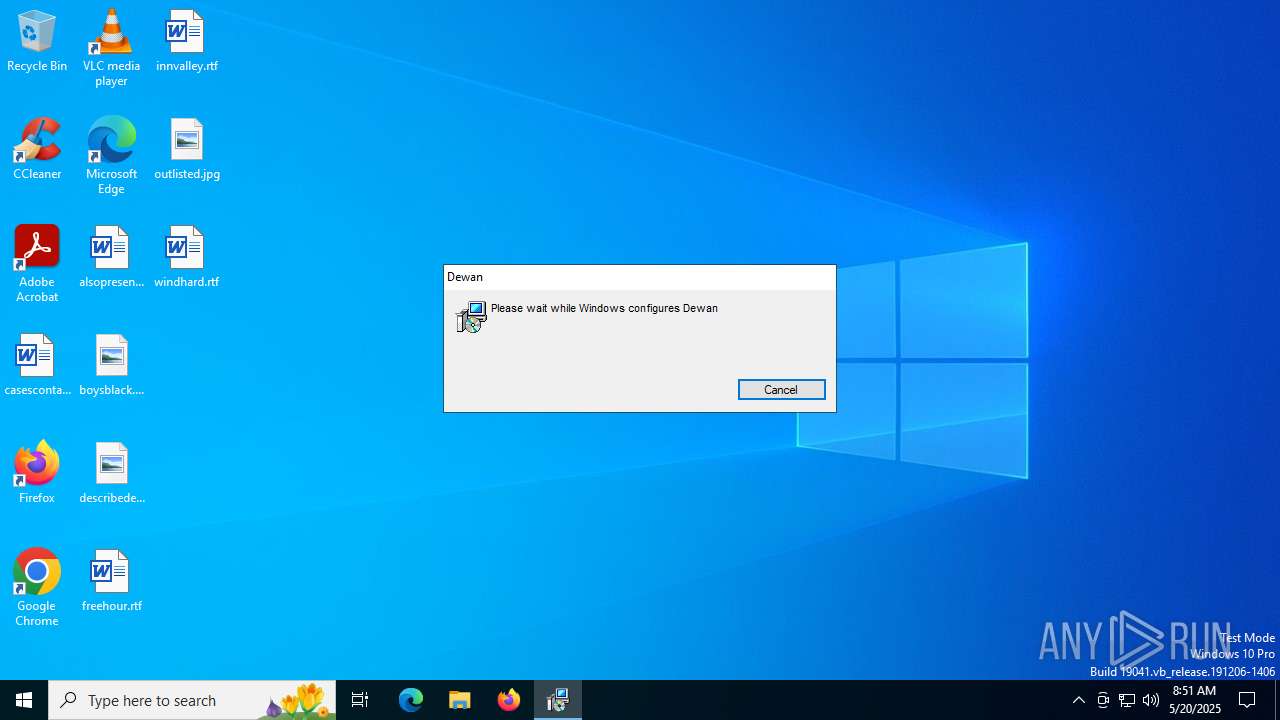
| File name: | ZNQJNQSS.msi |
| Full analysis: | https://app.any.run/tasks/db2d0d0a-5192-408f-b491-2136fbcb926a |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2025, 08:51:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Dewan, Author: Marrowfat Chlorpromazine, Keywords: Installer, Comments: This installer database contains the logic and data required to install Dewan., Template: Intel;1033, Revision Number: {5574507B-485D-4BCF-9635-4305F4DF4A11}, Create Time/Date: Fri May 16 09:37:28 2025, Last Saved Time/Date: Fri May 16 09:37:28 2025, Number of Pages: 500, Number of Words: 10, Name of Creating Application: WiX Toolset (4.0.0.0), Security: 2 |
| MD5: | A9CB4681A3A86D3A0EF536A6AB985B56 |
| SHA1: | 5DD1BAFB503B2CB74A5F7BC5260CF281839BF3DB |
| SHA256: | 526ACAF0B2536D05312C999FF4BEB5BB2F2BCBFDA4BF48FCA2AFD00AD4391B16 |
| SSDEEP: | 98304:L9OAXUMfbuWqbMUYWZKg4AKPwyeyBf+TsFp2qL14HLo31LuPbsT2b2mao2KeTeeH:VjJgG |
MALICIOUS
Executing a file with an untrusted certificate
- Hub_F.exe (PID: 2228)
- Hub_F.exe (PID: 6732)
SUSPICIOUS
Executable content was dropped or overwritten
- Hub_F.exe (PID: 2228)
- Hub_F.exe (PID: 6732)
Process drops legitimate windows executable
- msiexec.exe (PID: 3488)
- msiexec.exe (PID: 6548)
- Hub_F.exe (PID: 2228)
The process drops C-runtime libraries
- msiexec.exe (PID: 3488)
- msiexec.exe (PID: 6548)
- Hub_F.exe (PID: 2228)
Executes as Windows Service
- VSSVC.exe (PID: 472)
Starts itself from another location
- Hub_F.exe (PID: 2228)
INFO
The sample compiled with english language support
- msiexec.exe (PID: 6548)
- Hub_F.exe (PID: 2228)
- msiexec.exe (PID: 3488)
- Hub_F.exe (PID: 6732)
Manages system restore points
- SrTasks.exe (PID: 6404)
Checks supported languages
- msiexec.exe (PID: 6548)
Reads the computer name
- msiexec.exe (PID: 6548)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6548)
Application launched itself
- chrome.exe (PID: 4856)
- msedge.exe (PID: 1056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Dewan |
| Author: | Marrowfat Chlorpromazine |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Dewan. |
| Template: | Intel;1033 |
| RevisionNumber: | {5574507B-485D-4BCF-9635-4305F4DF4A11} |
| CreateDate: | 2025:05:16 09:37:28 |
| ModifyDate: | 2025:05:16 09:37:28 |
| Pages: | 500 |
| Words: | 10 |
| Software: | WiX Toolset (4.0.0.0) |
| Security: | Read-only recommended |
Total processes
187
Monitored processes
46
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --profile-directory="Default" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | DaemonUpdate_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1652 | "C:\Users\admin\AppData\Roaming\Zep_Client_test\tcpvcon.exe" "C:\Users\admin\AppData\Roaming\Zep_Client_test\tcpvcon.exe" /accepteula | C:\Users\admin\AppData\Roaming\Zep_Client_test\tcpvcon.exe | — | Hub_F.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Sysinternals TcpVcon Version: 4.18 | |||||||||||||||
| 2228 | "C:\Users\admin\AppData\Local\Anorak\Hub_F.exe" | C:\Users\admin\AppData\Local\Anorak\Hub_F.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Live Call Exit code: 0 Version: 1.5.188.0 Modules
| |||||||||||||||
| 3488 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\ZNQJNQSS.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=133.0.6943.127 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc4460fff8,0x7ffc44610004,0x7ffc44610010 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 4856 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | DaemonUpdate_x64.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 5172 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=2012,i,161685168480779398,2402065112861349857,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=1980 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 5244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=4724,i,161685168480779398,2402065112861349857,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5020 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
19 049
Read events
18 771
Write events
260
Delete events
18
Modification events
| (PID) Process: | (6548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000CFFF655E64C9DB0194190000880A0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000000364685E64C9DB0194190000880A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000E48BAD5E64C9DB0194190000880A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000E48BAD5E64C9DB0194190000880A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000E3DCAF5E64C9DB0194190000880A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000099D1B45E64C9DB0194190000880A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000CD75295F64C9DB0194190000880A0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000001CDA2B5F64C9DB0194190000CC0A0000E8030000010000000000000000000000976B04C8D0027343B91424C794DB2B8000000000000000000000000000000000 | |||
| (PID) Process: | (472) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
21
Suspicious files
174
Text files
85
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6548 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6548 | msiexec.exe | C:\Windows\Installer\17c592.msi | — | |
MD5:— | SHA256:— | |||
| 6548 | msiexec.exe | C:\Users\admin\AppData\Local\Anorak\La.rv | — | |
MD5:— | SHA256:— | |||
| 6548 | msiexec.exe | C:\Windows\Installer\17c594.msi | — | |
MD5:— | SHA256:— | |||
| 6548 | msiexec.exe | C:\Windows\Installer\MSIC786.tmp | binary | |
MD5:B8B5AD487087DCC8281923DE6C8A2485 | SHA256:9D829CFB1E3699D96F8F37C14438062F2998A05F80E7C3DE3713322EC14B3D8A | |||
| 6548 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{c8046b97-02d0-4373-b914-24c794db2b80}_OnDiskSnapshotProp | binary | |
MD5:18FE451A5E9363D4223777DA38FB7847 | SHA256:E5565D21535D8906E09D4FCD651AB75B5A79A051FAB4FD7D02A807F7D05DB5D8 | |||
| 6548 | msiexec.exe | C:\Windows\Temp\~DF422A42C8BA4C94DF.TMP | binary | |
MD5:B58CEC70649C1EFED80FCB1375B8ECC1 | SHA256:A1BE099082D159EDFC29E23E0F431C9632912D845EA04C1900E965C3EF28AD02 | |||
| 6548 | msiexec.exe | C:\Users\admin\AppData\Local\Anorak\msidcrl40.dll | executable | |
MD5:1A04EEF6D419840FC79C523FF71F4D7A | SHA256:C39CC298BB9ABC3D1D116F2AD634A9A52E04ECA40025CD3AF0F94BF482B18D49 | |||
| 6548 | msiexec.exe | C:\Windows\Temp\~DF23B2B38276E5B412.TMP | binary | |
MD5:F3E3A16EFBB17768304194FB2F71B02B | SHA256:E595A9CC980EB23F36353190AEE6544732754589EAC7EE8F67ECA1A83331BBBD | |||
| 6548 | msiexec.exe | C:\Users\admin\AppData\Local\Anorak\msvcr80.dll | executable | |
MD5:43143ABB001D4211FAB627C136124A44 | SHA256:CB8928FF2FAF2921B1EDDC267DCE1BB64E6FEE4D15B68CD32588E0F3BE116B03 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
94
DNS requests
82
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3656 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3656 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4020 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5708 | chrome.exe | GET | 200 | 142.250.185.78:80 | http://clients2.google.com/time/1/current?cup2key=8:CC9q0FFQuTOdKZCP5gEBrfmwIcxmJqRJg19o9tM_N7w&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7176 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:WTRH8cXr5XX3Ie2fF88CLWo3WZKrc8yu-ESM1t2X-7s&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4984 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6268 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
3656 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3656 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |