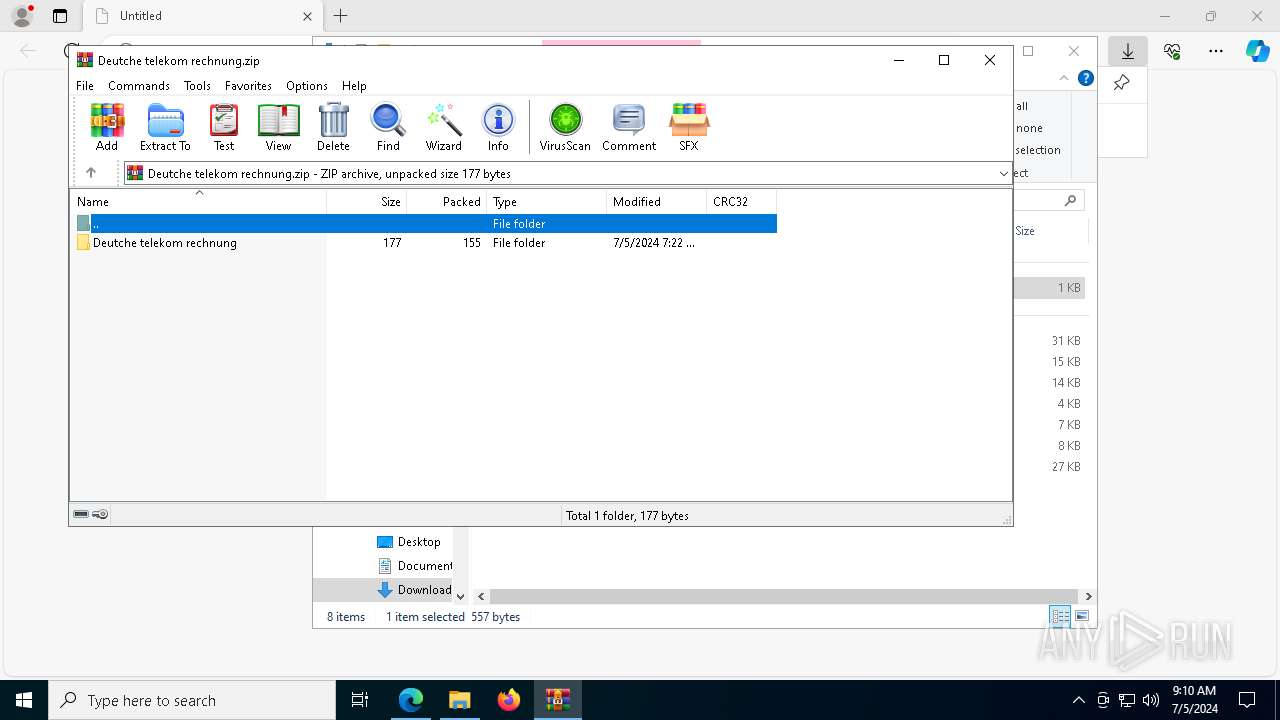
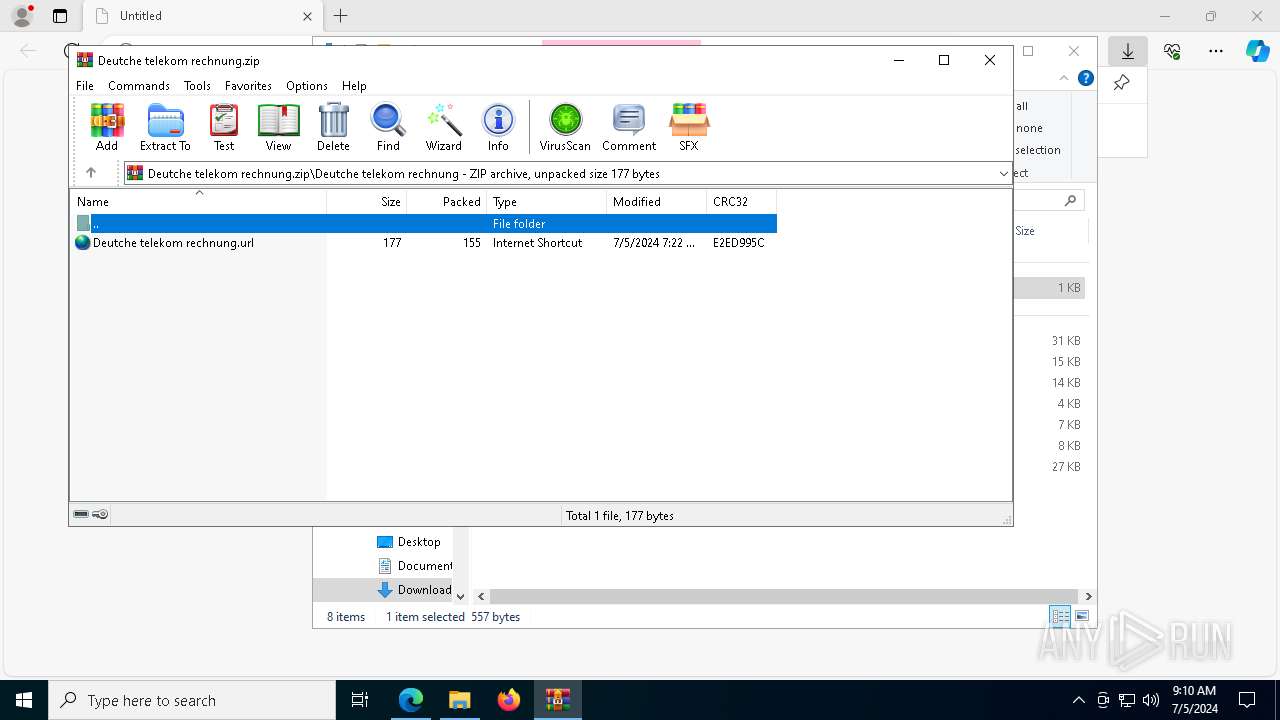
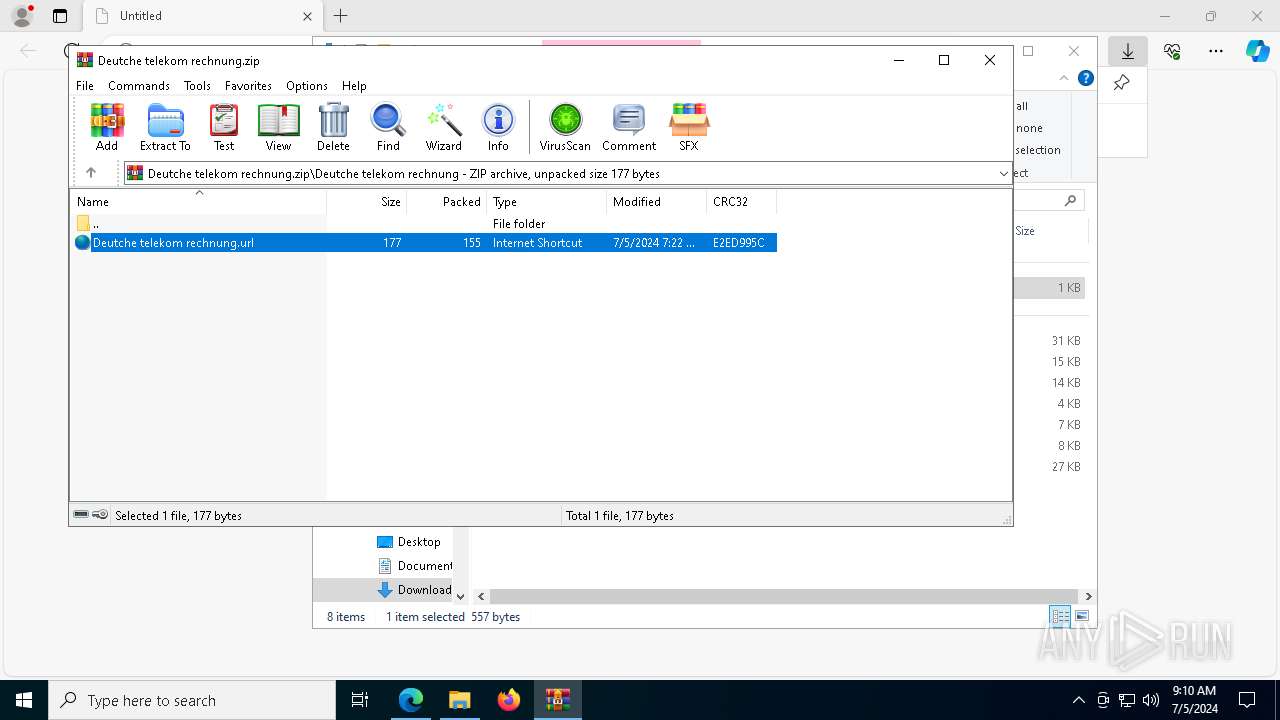
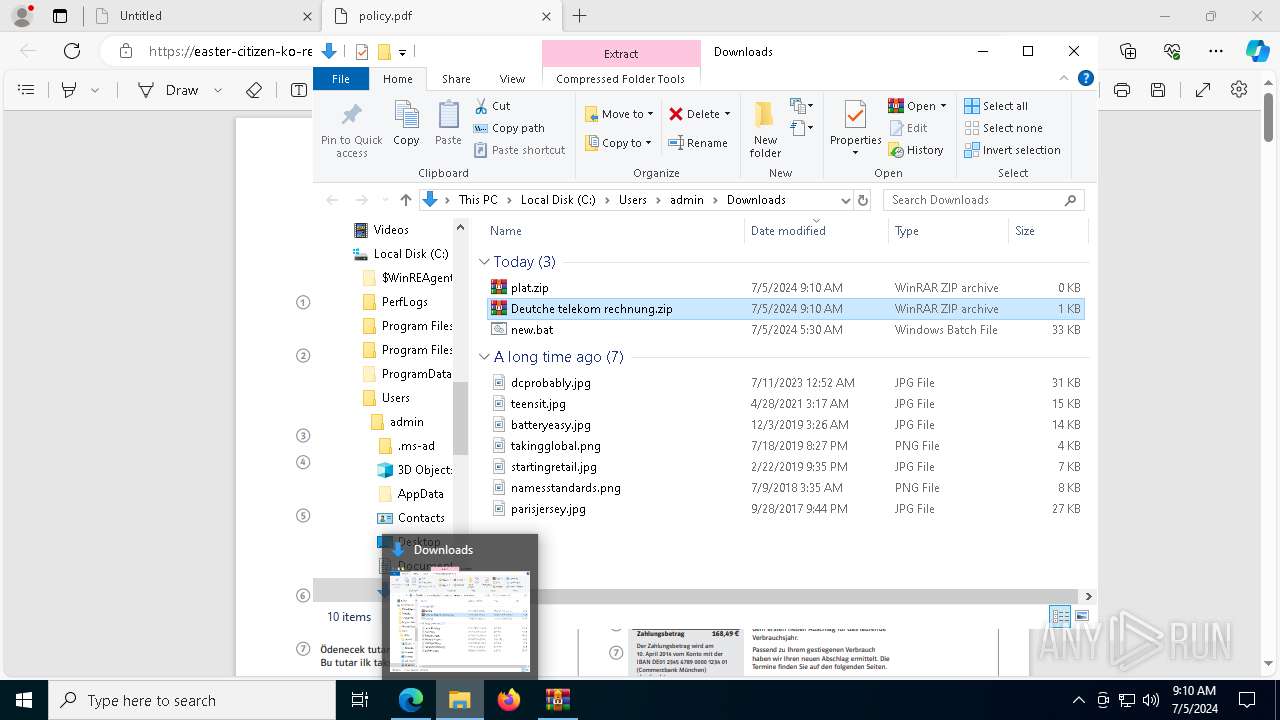
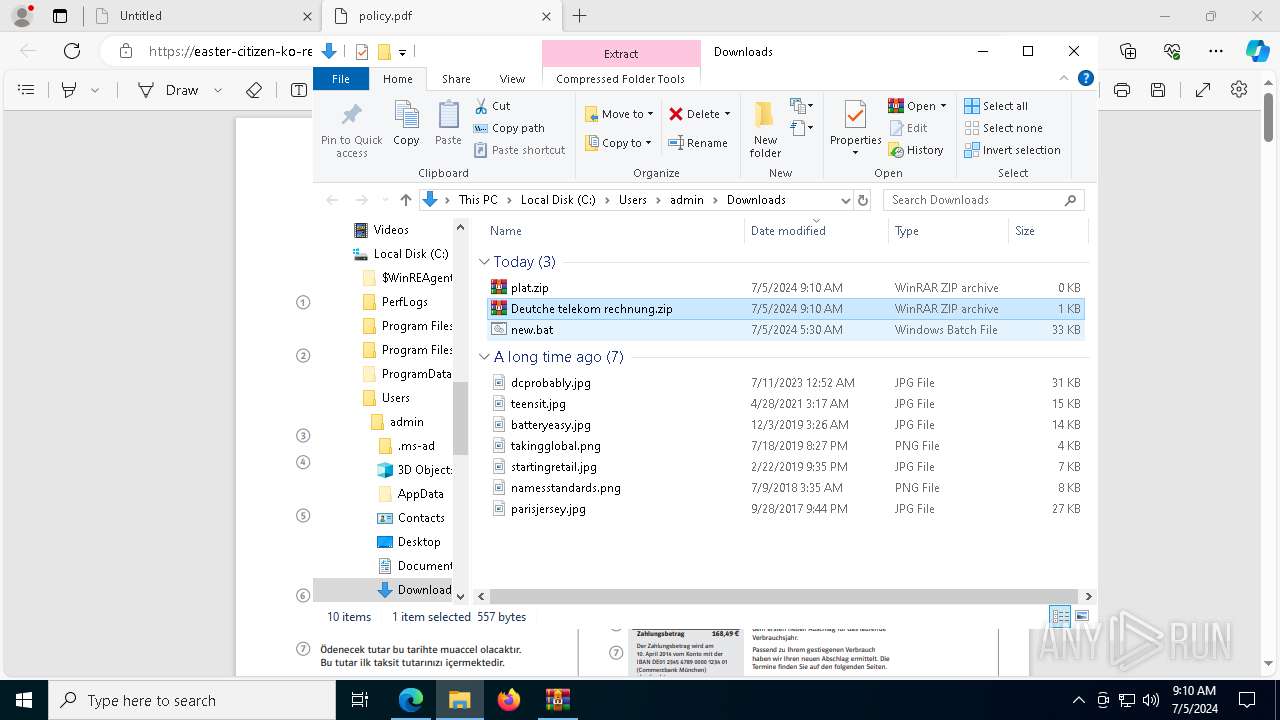
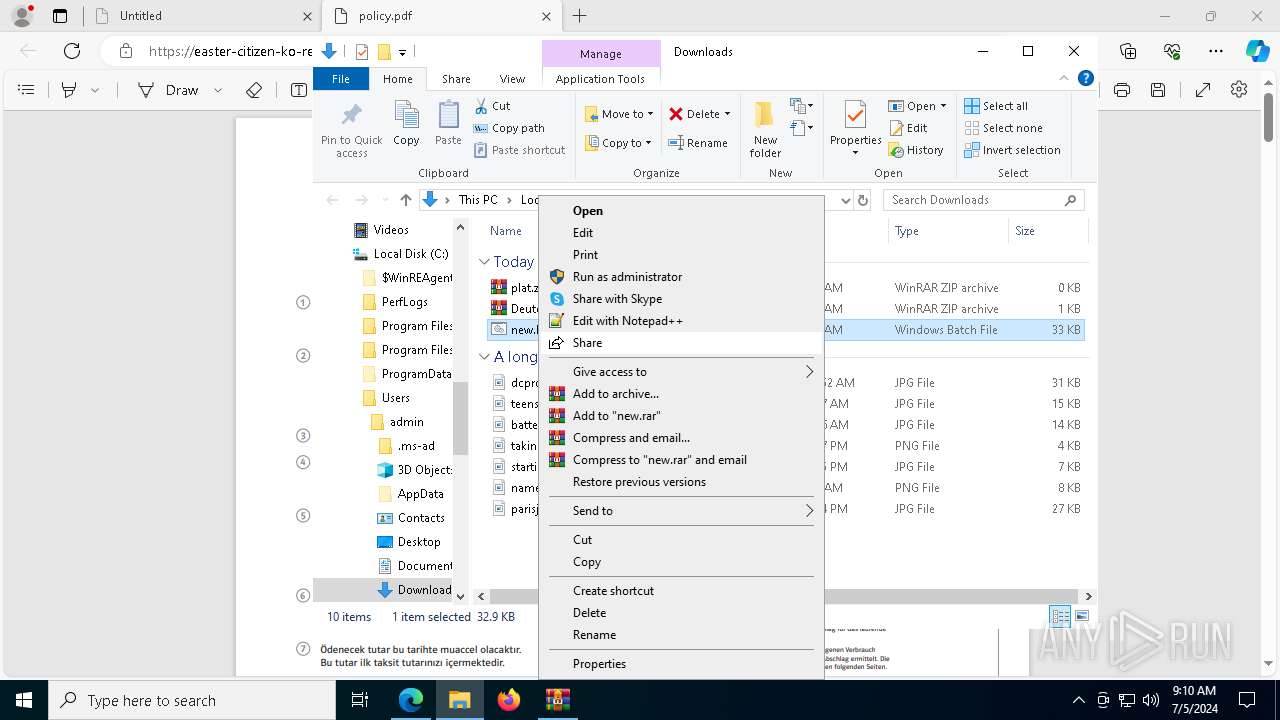
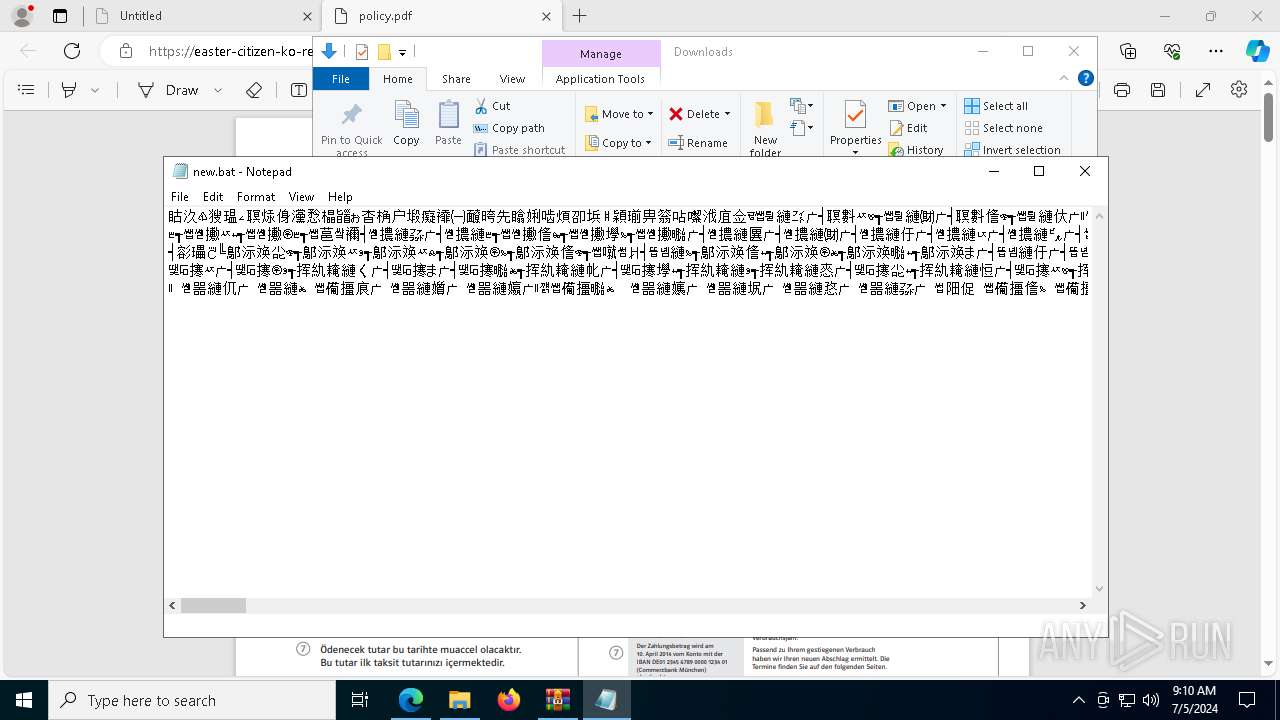
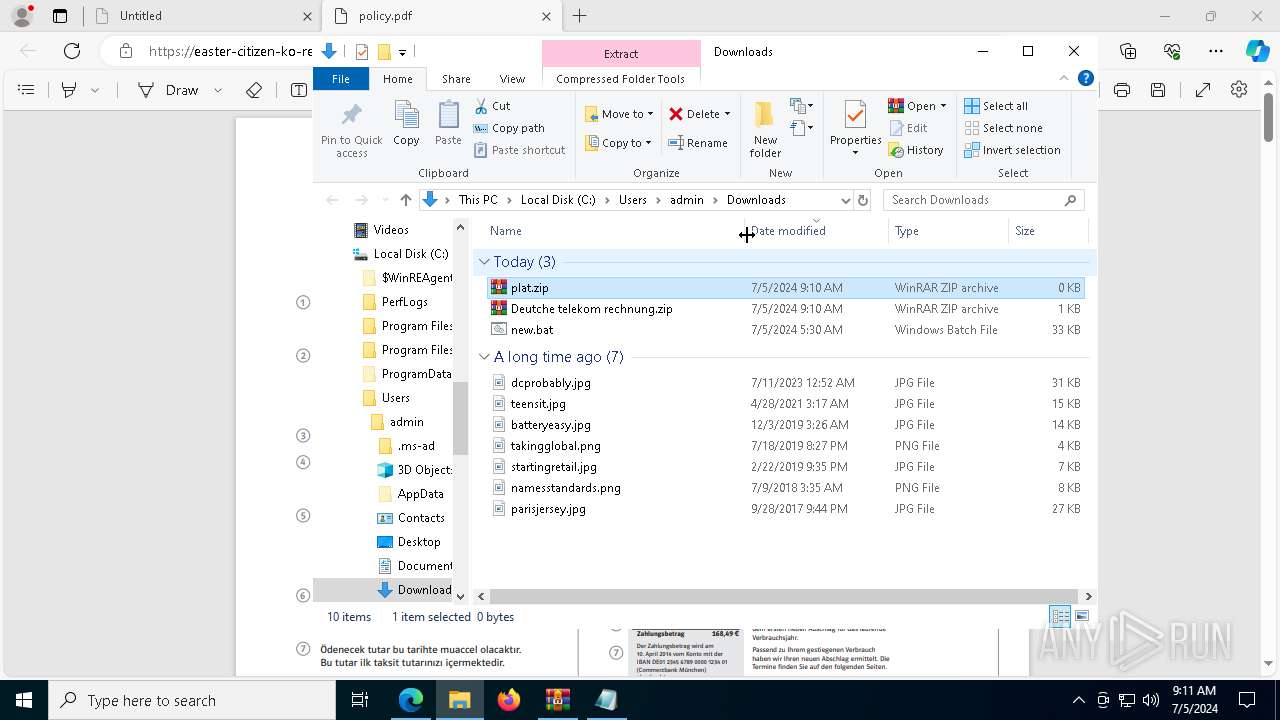
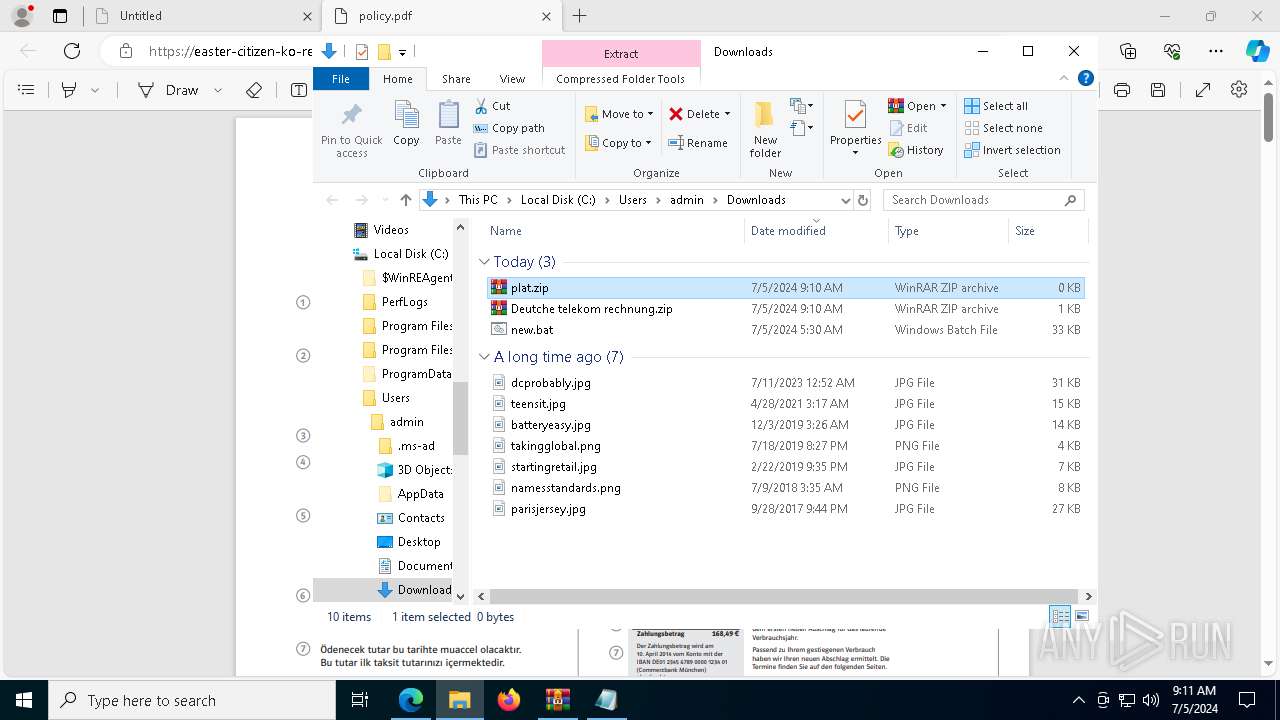
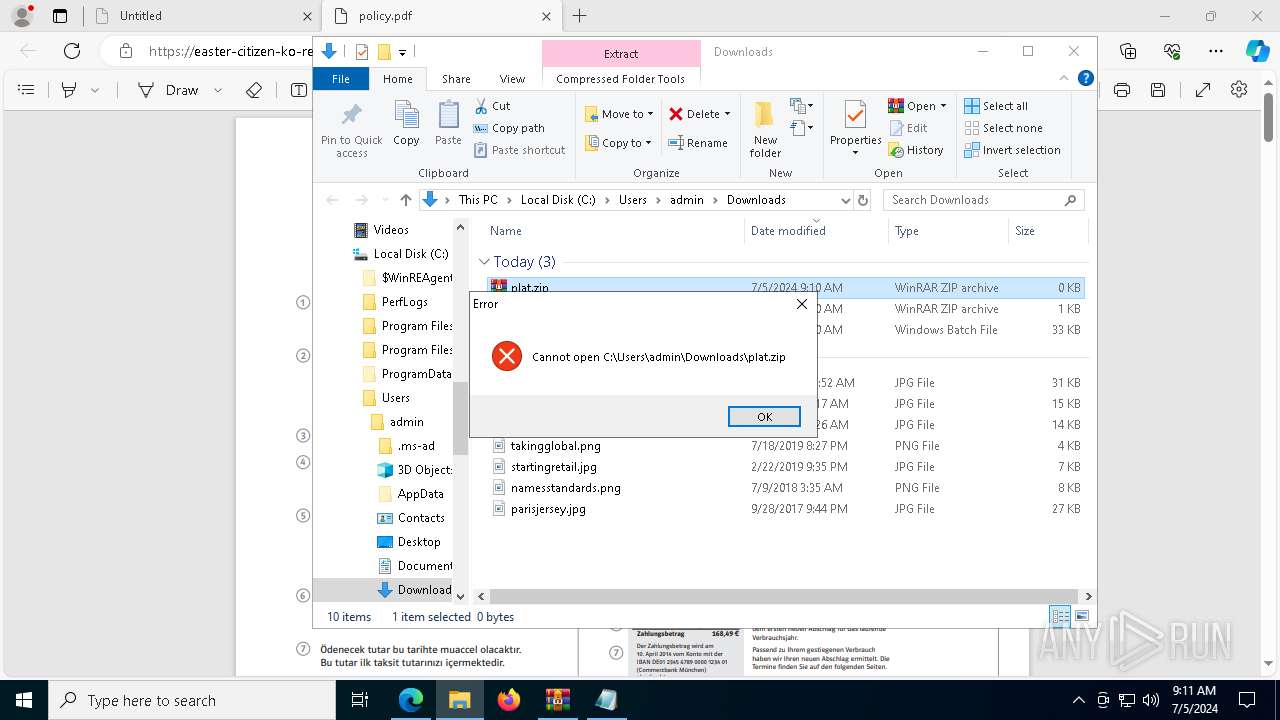
| URL: | https://dl.dropboxusercontent.com/scl/fi/adtf8tdt2awfvsxc7vm5b/Deutche-telekom-rechnung.zip?rlkey=j3mdg9qy4kpk2lblrj4c93bix&st=rgigszl2&dl=0 |
| Full analysis: | https://app.any.run/tasks/ed5d22aa-cb59-4530-9062-e49a57842f2d |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2024, 09:10:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 30C004A124D3B62ECD9C50F3D1E55DD2 |
| SHA1: | 21B8F9E308FA5E10BE39DC495A8E4A37E39F363B |
| SHA256: | 525E5D1B0C42F044DB535A38EB0372377E39D6ACF3773CD0F12FD1C95886BB06 |
| SSDEEP: | 3:N8RdNcvALtGTU6CLEhdYGJdCzwZOAcYuI0OX/ZAcK+z0:27NFGdsG/Q15Yuf41K/ |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 7984)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7356)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 7720)
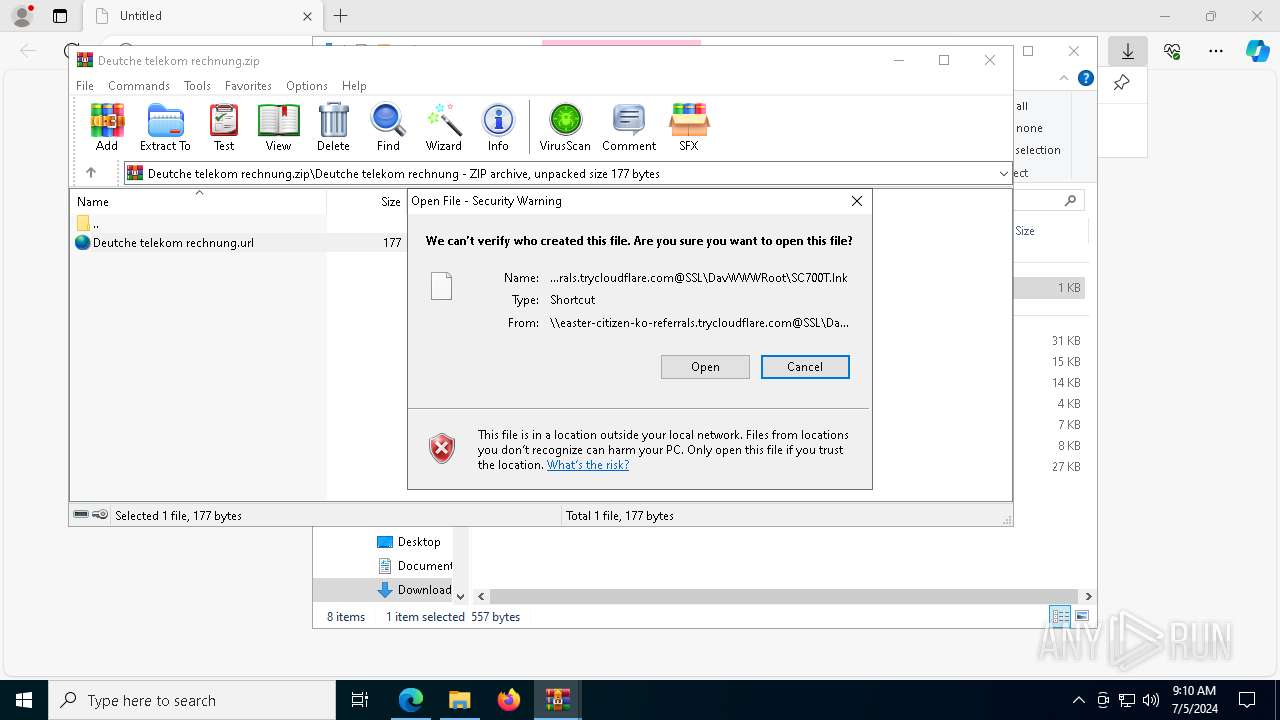
Abuses WebDav for code execution
- svchost.exe (PID: 7720)
Checks Windows Trust Settings
- WinRAR.exe (PID: 7356)
Starts POWERSHELL.EXE for commands execution
- WinRAR.exe (PID: 7356)
- cmd.exe (PID: 5532)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 7984)
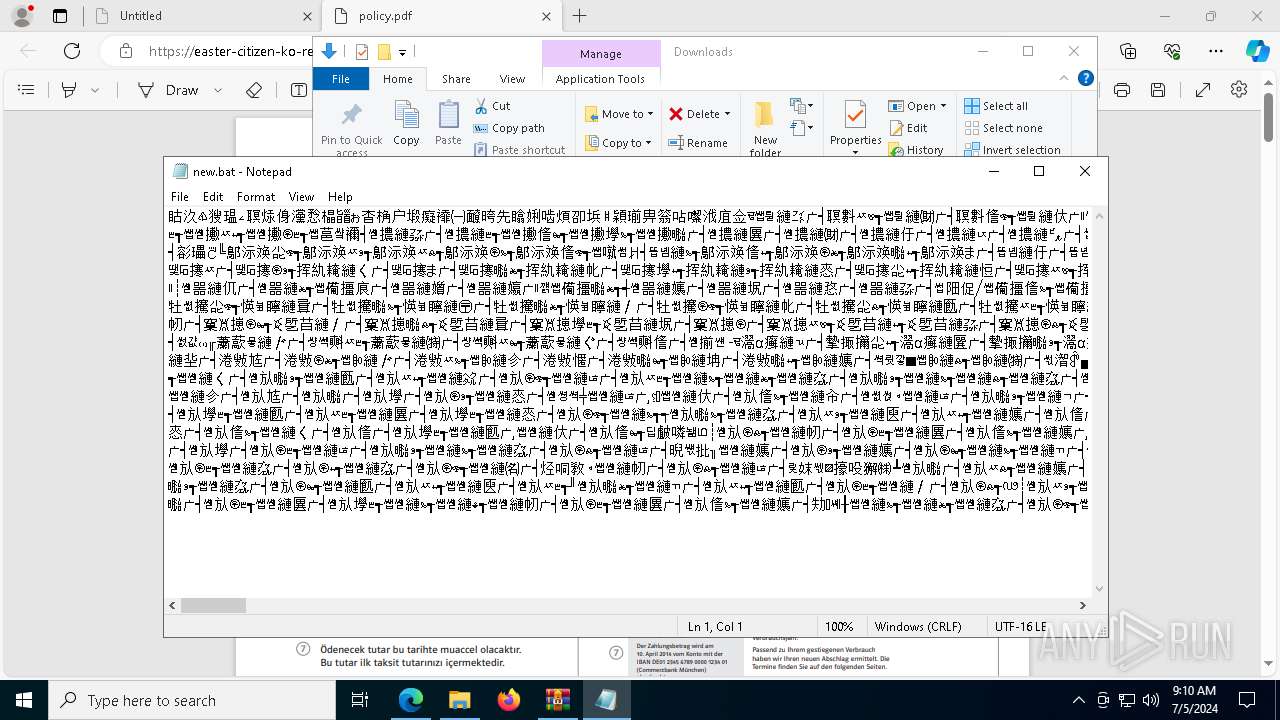
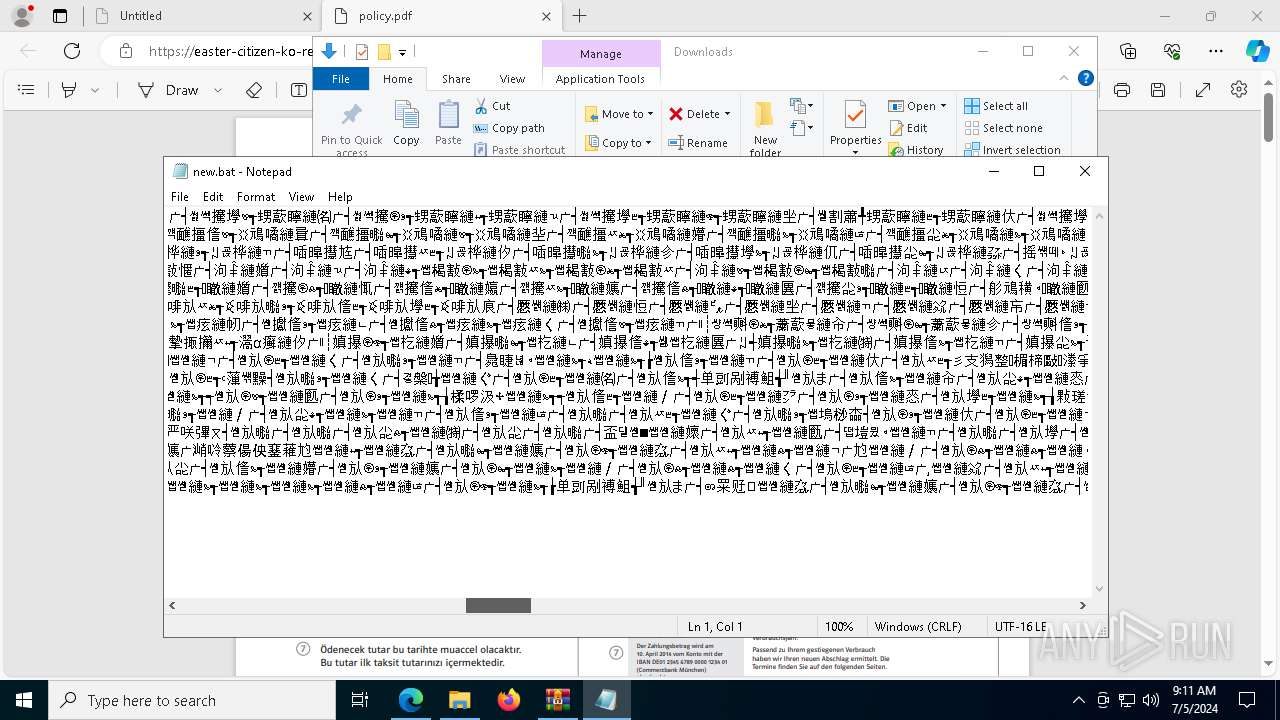
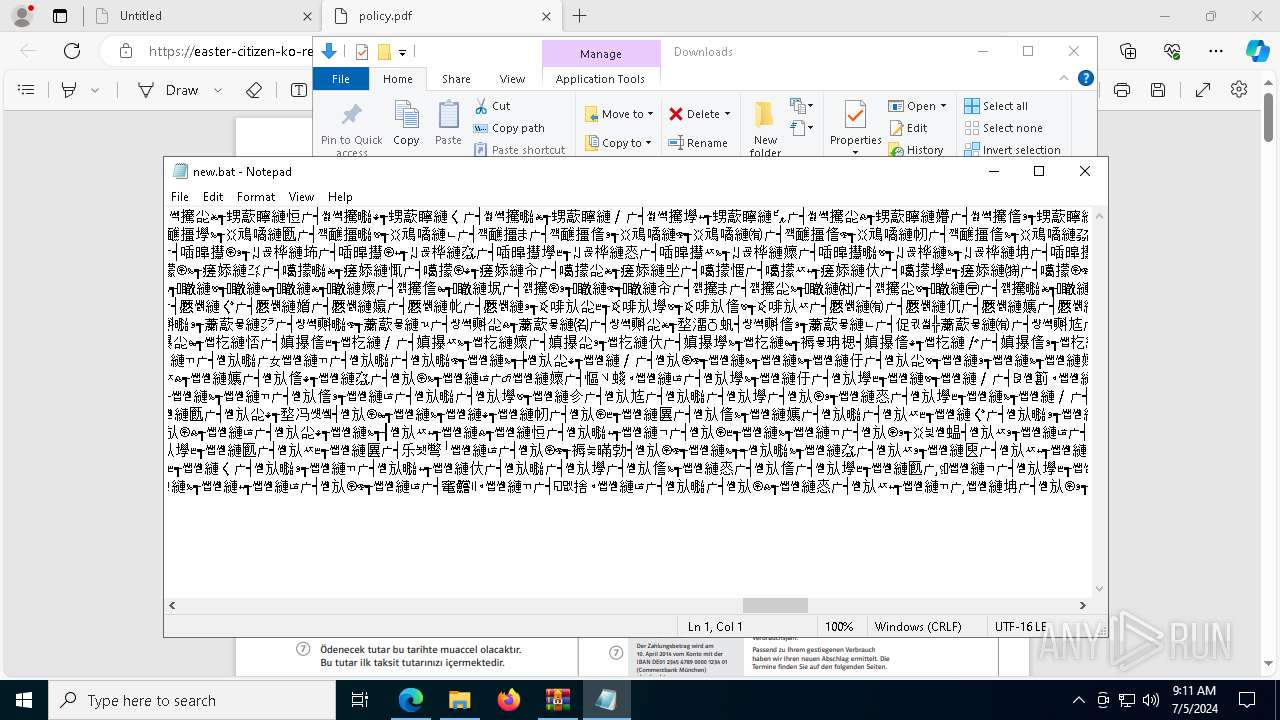
Executing commands from a ".bat" file
- powershell.exe (PID: 7984)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5532)
Downloads file from URI
- powershell.exe (PID: 7180)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 5532)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 7180)
INFO
Reads Microsoft Office registry keys
- msedge.exe (PID: 5884)
- WinRAR.exe (PID: 7356)
Checks supported languages
- identity_helper.exe (PID: 7384)
Reads the computer name
- identity_helper.exe (PID: 7384)
The process uses the downloaded file
- msedge.exe (PID: 6952)
- WinRAR.exe (PID: 7356)
Manual execution by a user
- WinRAR.exe (PID: 7356)
- WinRAR.exe (PID: 6064)
- notepad.exe (PID: 8128)
- WinRAR.exe (PID: 6948)
Application launched itself
- msedge.exe (PID: 5884)
Checks proxy server information
- WinRAR.exe (PID: 7356)
- conhost.exe (PID: 7972)
- powershell.exe (PID: 7984)
- powershell.exe (PID: 7180)
Reads the software policy settings
- WinRAR.exe (PID: 7356)
Reads security settings of Internet Explorer
- conhost.exe (PID: 7972)
- notepad.exe (PID: 8128)
Disables trace logs
- powershell.exe (PID: 7180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
180
Monitored processes
45
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3572 --field-trial-handle=2384,i,14290749231182484387,13222523905442347024,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2056 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2452 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2360 --field-trial-handle=2384,i,14290749231182484387,13222523905442347024,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2628 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x2ec,0x2f0,0x2f4,0x2e8,0x2fc,0x7ffd94725fd8,0x7ffd94725fe4,0x7ffd94725ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4152 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2740 --field-trial-handle=2384,i,14290749231182484387,13222523905442347024,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4264 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4536 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4556 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://easter-citizen-ko-referrals.trycloudflare.com/policy.pdf | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4784 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2232 --field-trial-handle=2384,i,14290749231182484387,13222523905442347024,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=7096 --field-trial-handle=2384,i,14290749231182484387,13222523905442347024,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
Total events
29 301
Read events
29 140
Write events
158
Delete events
3
Modification events
| (PID) Process: | (5884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (5884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (5884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (5884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5884) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (5884) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5884) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
0
Suspicious files
57
Text files
50
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1cf053.TMP | — | |
MD5:— | SHA256:— | |||
| 5884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1cf053.TMP | — | |
MD5:— | SHA256:— | |||
| 5884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1cf053.TMP | — | |
MD5:— | SHA256:— | |||
| 5884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1cf053.TMP | — | |
MD5:— | SHA256:— | |||
| 5884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1cf072.TMP | — | |
MD5:— | SHA256:— | |||
| 5884 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
76
DNS requests
42
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
6700 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6672 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
7804 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
7804 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4784 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4784 | msedge.exe | 162.125.66.15:443 | dl.dropboxusercontent.com | DROPBOX | DE | malicious |
5884 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4784 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4784 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4784 | msedge.exe | 13.107.246.42:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4784 | msedge.exe | 2.19.126.145:443 | bzib.nelreports.net | Akamai International B.V. | DE | unknown |
4004 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
dl.dropboxusercontent.com |
| shared |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| unknown |
bzib.nelreports.net |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4784 | msedge.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
2168 | svchost.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
4784 | msedge.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
4784 | msedge.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |