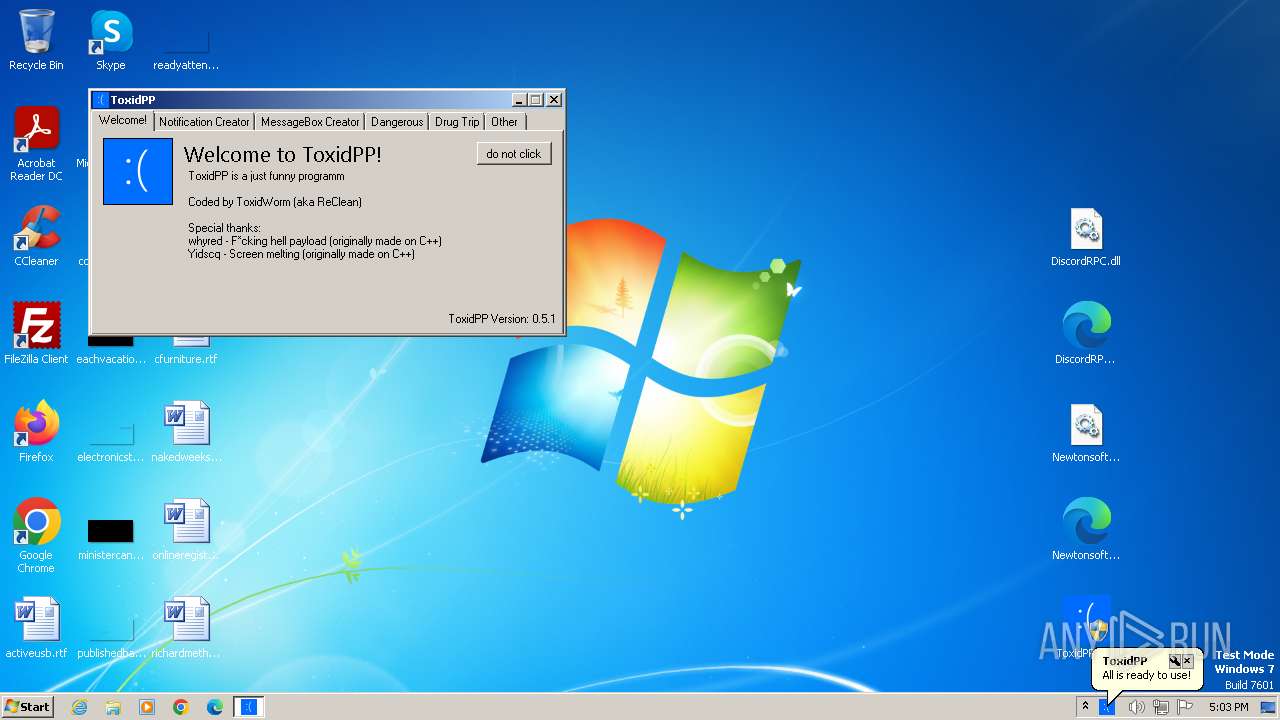
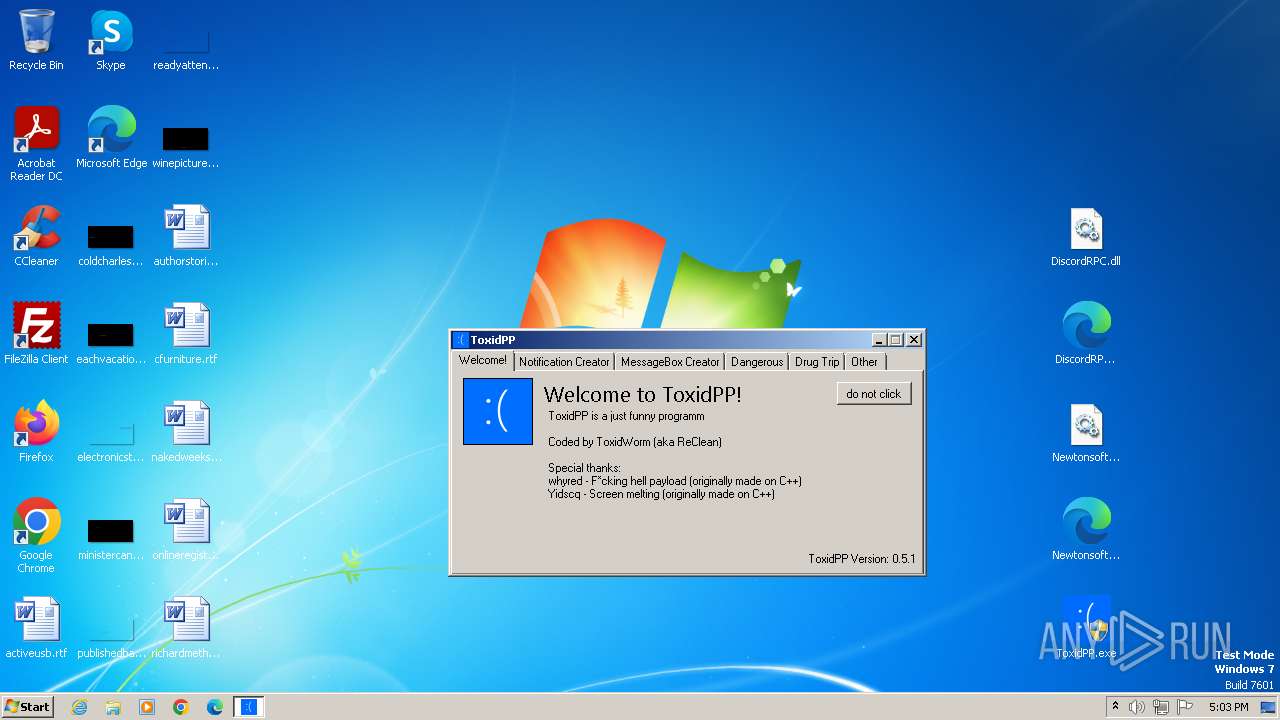
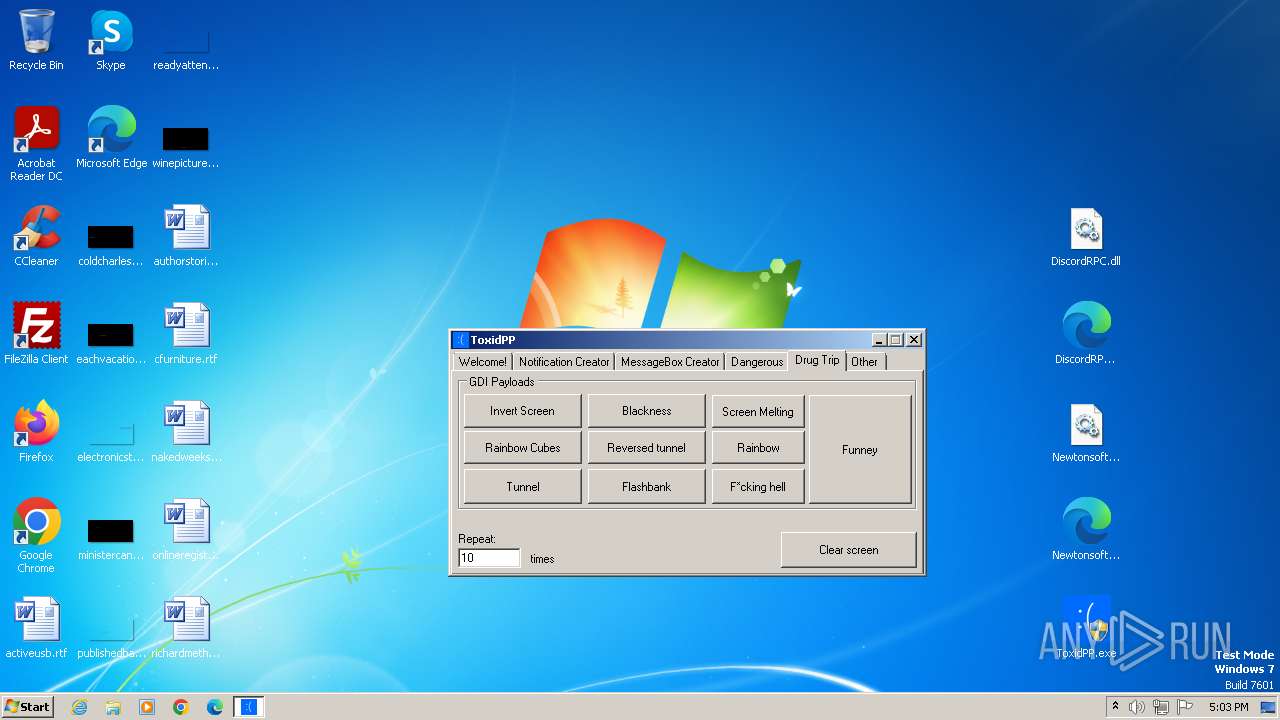
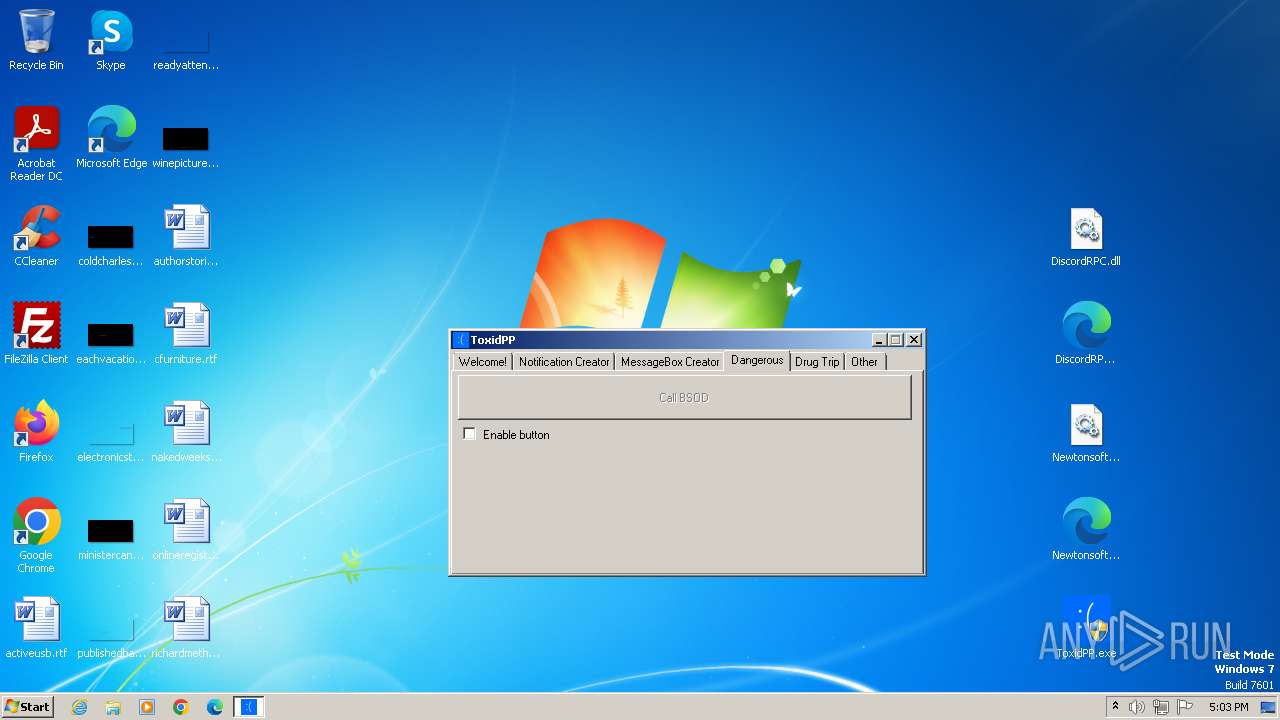
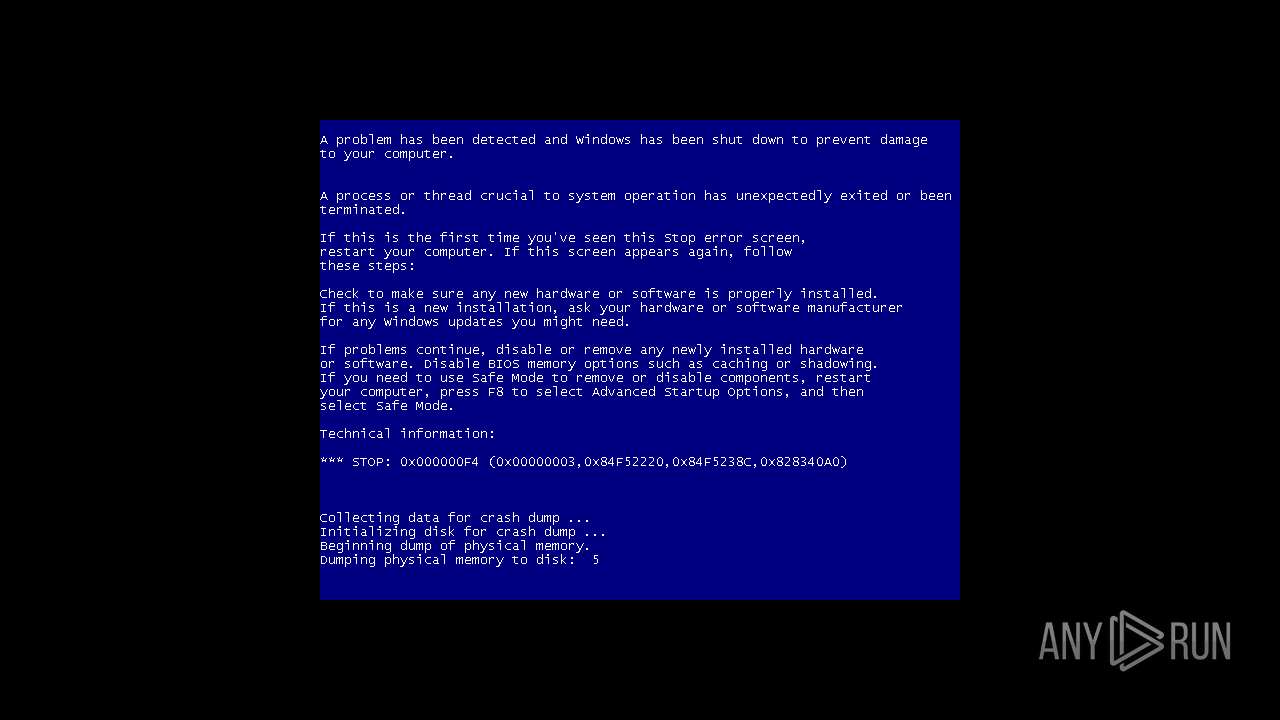
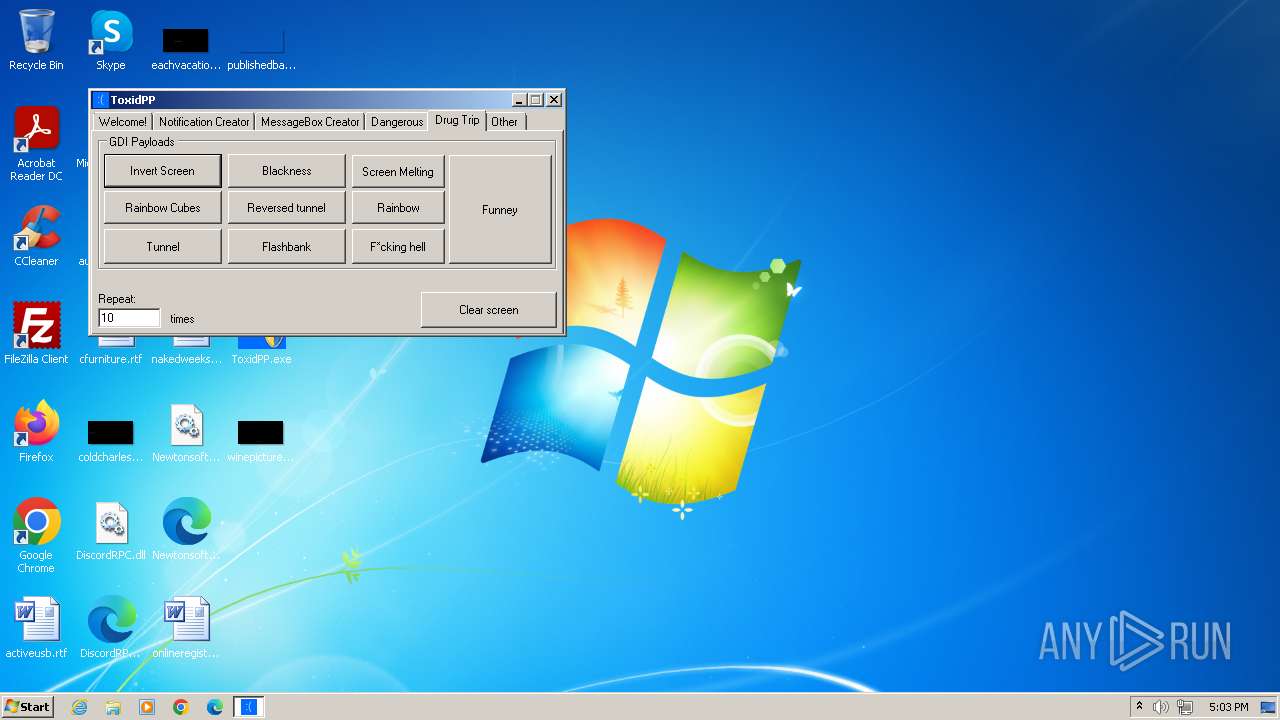
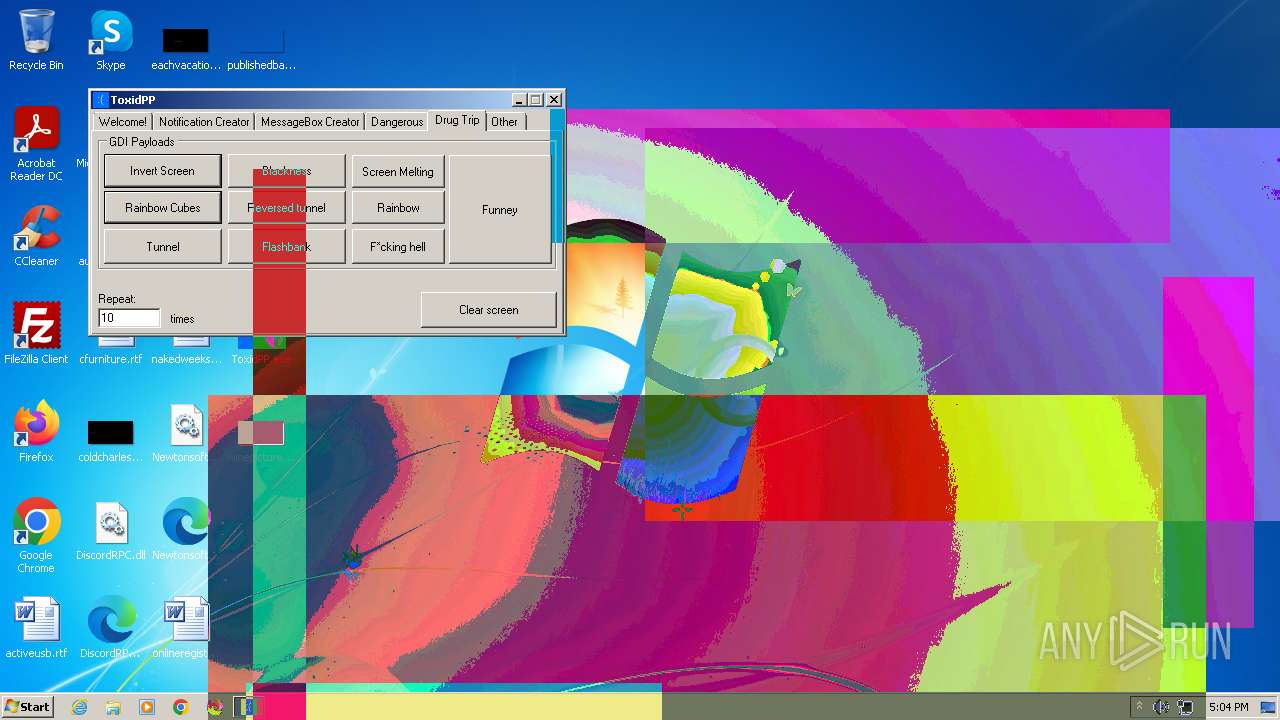
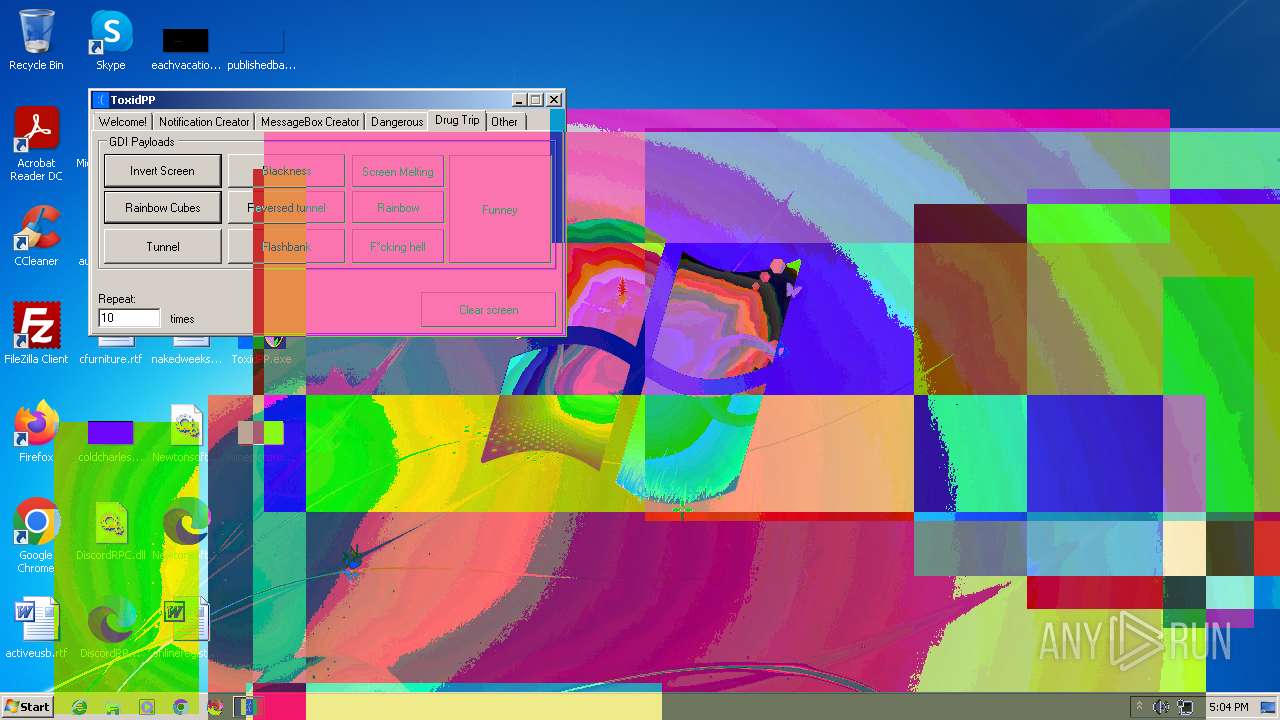
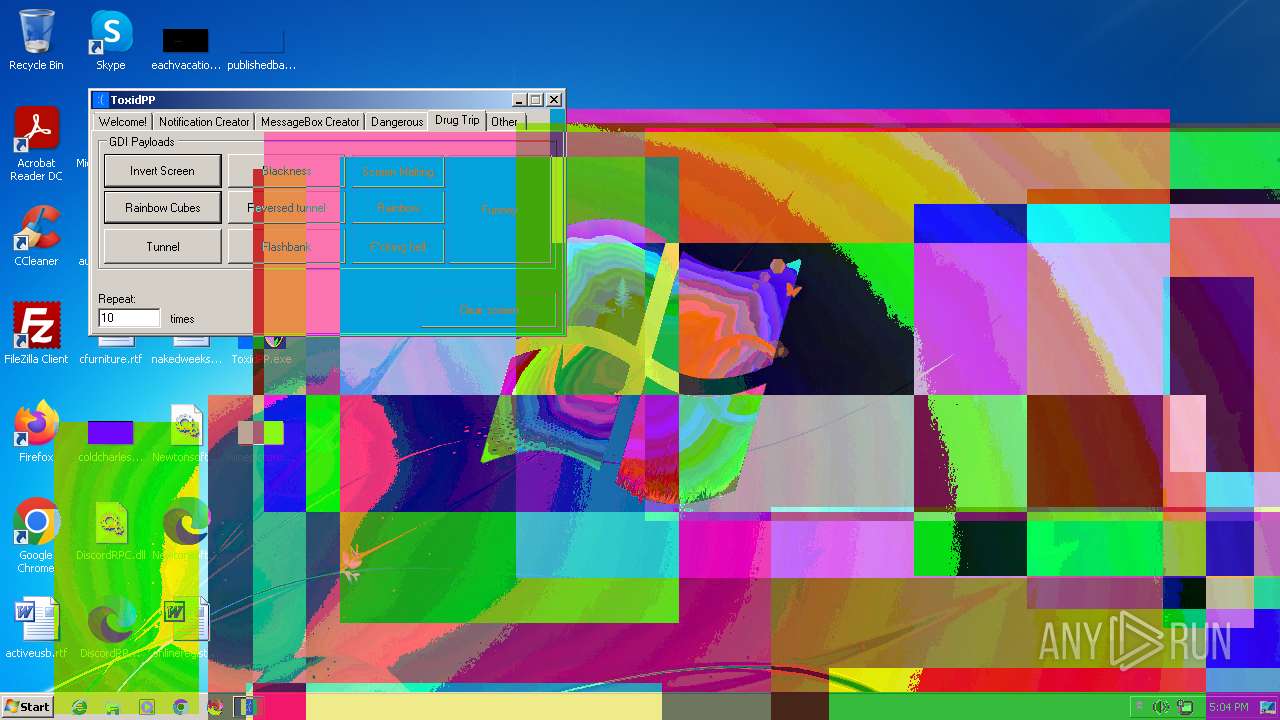
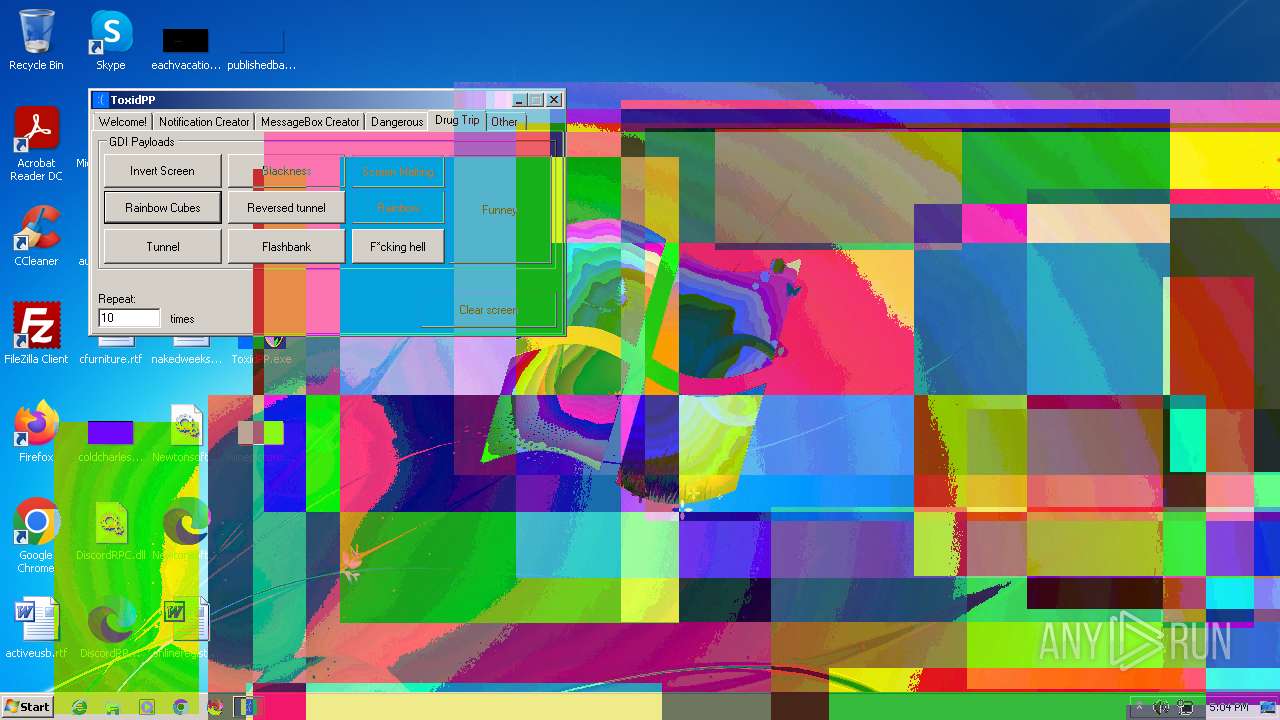
| File name: | ToxidPP.zip |
| Full analysis: | https://app.any.run/tasks/45d88ae9-7584-4371-b04e-6bc5144158e2 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2023, 16:02:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E4C9B38ACD1F5495364020B0B29249EC |
| SHA1: | 0CEE5B2671795C71C54BE216635D8F62E16F517B |
| SHA256: | 523C187C70D392ECB8B0129EF0303C0C5B7C163FFC55D2E3543A99406C806229 |
| SSDEEP: | 24576:8ILwY16wAcOpa1S+A21x2kVDOkFHk8bC1H76LGirtKWqmeYmCUg:8ILwY16wAcOpa18272kVDRFHk8bC1H7Q |
MALICIOUS
Application was dropped or rewritten from another process
- ToxidPP.exe (PID: 1824)
- ToxidPP.exe (PID: 3488)
- ToxidPP.exe (PID: 1604)
- ToxidPP.exe (PID: 432)
Loads dropped or rewritten executable
- ToxidPP.exe (PID: 1824)
- ToxidPP.exe (PID: 1604)
SUSPICIOUS
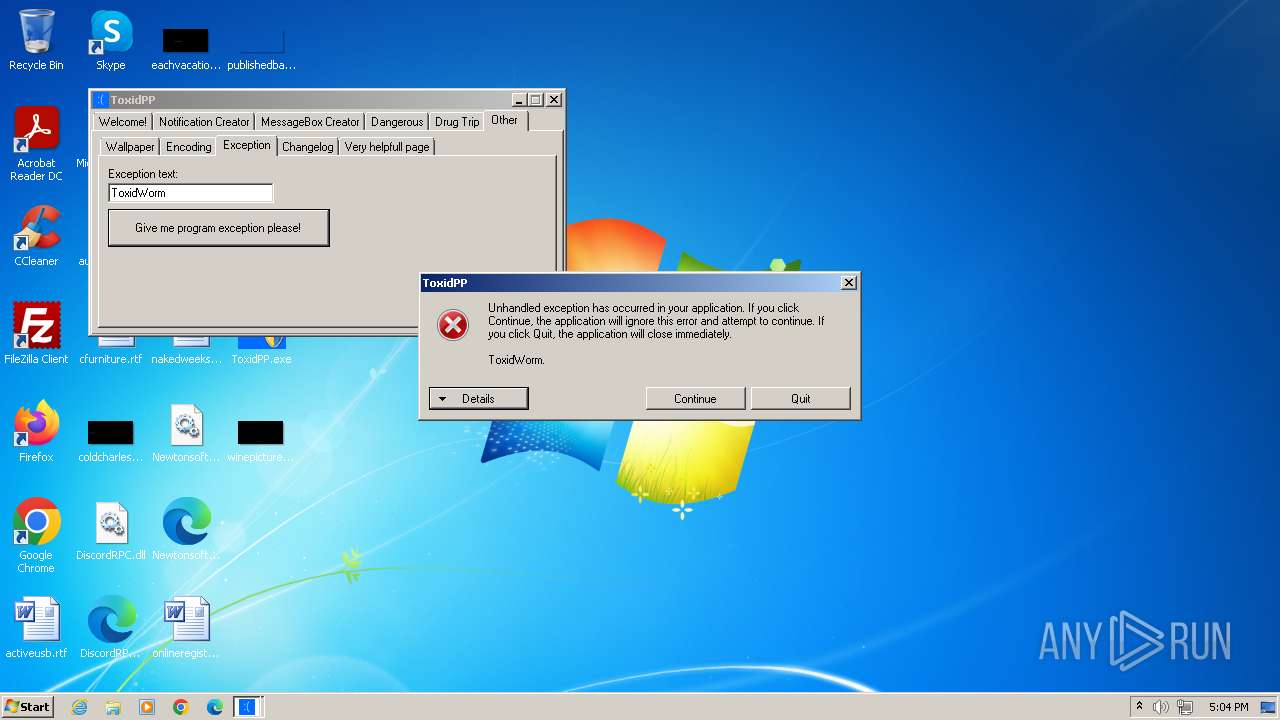
Application launched itself
- WerFault.exe (PID: 664)
Reads settings of System Certificates
- sipnotify.exe (PID: 1720)
Reads the Internet Settings
- runonce.exe (PID: 1240)
- sipnotify.exe (PID: 1720)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1720)
INFO
Checks supported languages
- ToxidPP.exe (PID: 1824)
- wmpnscfg.exe (PID: 2760)
- IMEKLMG.EXE (PID: 2652)
- IMEKLMG.EXE (PID: 2684)
- wmpnscfg.exe (PID: 2804)
- ToxidPP.exe (PID: 1604)
- wmpnscfg.exe (PID: 4084)
Manual execution by a user
- ToxidPP.exe (PID: 1824)
- ToxidPP.exe (PID: 3488)
- wmpnscfg.exe (PID: 2760)
- IMEKLMG.EXE (PID: 2652)
- wmpnscfg.exe (PID: 4084)
- runonce.exe (PID: 1240)
- IMEKLMG.EXE (PID: 2684)
- wmpnscfg.exe (PID: 2804)
- ToxidPP.exe (PID: 432)
- ToxidPP.exe (PID: 1604)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2760)
- ToxidPP.exe (PID: 1824)
- wmpnscfg.exe (PID: 2804)
- wmpnscfg.exe (PID: 4084)
- ToxidPP.exe (PID: 1604)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2980)
Reads the computer name
- ToxidPP.exe (PID: 1824)
- IMEKLMG.EXE (PID: 2684)
- IMEKLMG.EXE (PID: 2652)
- wmpnscfg.exe (PID: 2804)
- wmpnscfg.exe (PID: 4084)
- ToxidPP.exe (PID: 1604)
- wmpnscfg.exe (PID: 2760)
Reads the time zone
- runonce.exe (PID: 1240)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 2684)
- IMEKLMG.EXE (PID: 2652)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1720)
Create files in a temporary directory
- WerFault.exe (PID: 2100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:04:22 00:57:26 |
| ZipCRC: | 0xbd216e97 |
| ZipCompressedSize: | 49259 |
| ZipUncompressedSize: | 701978 |
| ZipFileName: | Newtonsoft.Json.xml |
Total processes
100
Monitored processes
15
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\Users\admin\Desktop\ToxidPP.exe" | C:\Users\admin\Desktop\ToxidPP.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: ToxidPP Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 664 | "C:\Windows\System32\WerFault.exe" -k -rq | C:\Windows\System32\WerFault.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1240 | runonce.exe /Explorer | C:\Windows\System32\runonce.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1604 | "C:\Users\admin\Desktop\ToxidPP.exe" | C:\Users\admin\Desktop\ToxidPP.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: ToxidPP Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1720 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1824 | "C:\Users\admin\Desktop\ToxidPP.exe" | C:\Users\admin\Desktop\ToxidPP.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: ToxidPP Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2100 | C:\Windows\System32\WerFault.exe -k -q | C:\Windows\System32\WerFault.exe | — | WerFault.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2132 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2652 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2684 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
Total events
5 598
Read events
5 539
Write events
44
Delete events
15
Modification events
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2760) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{85A8AA2E-2289-431B-915B-E20873E7BA20}\{7FCDC15D-7595-4D40-8625-11A4A734F080} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2760) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{85A8AA2E-2289-431B-915B-E20873E7BA20} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
3
Suspicious files
8
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2100 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\Kernel_0_0_cab_08343ba1\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.26301\Newtonsoft.Json.xml | xml | |
MD5:ED67AC96769018255050AC0829CA459A | SHA256:F32ED922FE5B22DD693E160AEE4F0DCAB753EBD740BED40490AE4179274B4B49 | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.26301\Newtonsoft.Json.dll | executable | |
MD5:4DF6C8781E70C3A4912B5BE796E6D337 | SHA256:3598CCCAD5B535FEA6F93662107A4183BFD6167BF1D0F80260436093EDC2E3AF | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2980.26301\ToxidPP.exe | executable | |
MD5:DFC559E2A5994DBCB4CCFE080FC28CAF | SHA256:9DBAB7AF2FC3FEB7CF356F055A67469212655ED65613FA854AF16BF4DAEDA244 | |||
| 1720 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\metadata.json | binary | |
MD5:E8A970BA6CE386EED9A5E724F26212A6 | SHA256:7E06107D585D8FC7870998F3856DCC3E35800AA97E4406AAB83BC8444B6CBDE3 | |||
| 2100 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER3B08.tmp.cab.tmp | binary | |
MD5:06903EC90307DDB423806220CB6D10DF | SHA256:A0026C5A2A90675B29EDE3A28CD6CDB9C81092FEF05ACCA0947D5EB351FD0E73 | |||
| 1720 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\styles.css | text | |
MD5:3383EEF350240253D7C2C2564381B3CB | SHA256:85443493D86D6D7FB0E07BC9705DFC9C858086FBA1B0E508092AB328D5F145E8 | |||
| 2100 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER3B09.tmp.cab.tmp | binary | |
MD5:40E071E83E2C3FA6E3B0D062B4F22789 | SHA256:8D93F898BB9D95512CAAB22A795204830095FFAB261CBDB1139D3DD81F51FE0A | |||
| 2100 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER3B06.tmp.cab.tmp | binary | |
MD5:B5AAE222E52C77A6FA6735D7C35D3E3F | SHA256:7658A79AAE58DF6C9DF9788DFE6F9E04B7FDED515813ADC4D2871A85B4EF9F22 | |||
| 2100 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER3B07.tmp.cab.tmp | binary | |
MD5:40E071E83E2C3FA6E3B0D062B4F22789 | SHA256:8D93F898BB9D95512CAAB22A795204830095FFAB261CBDB1139D3DD81F51FE0A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 88.221.61.151:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133422950263900000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 88.221.61.151:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |