| File name: | 52341adb87a5e79d06901a64002c494e3f431c378193982c30225eab3b136688.msi |
| Full analysis: | https://app.any.run/tasks/2adaee21-599e-4eeb-86d0-3f1e6976609d |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2025, 18:12:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
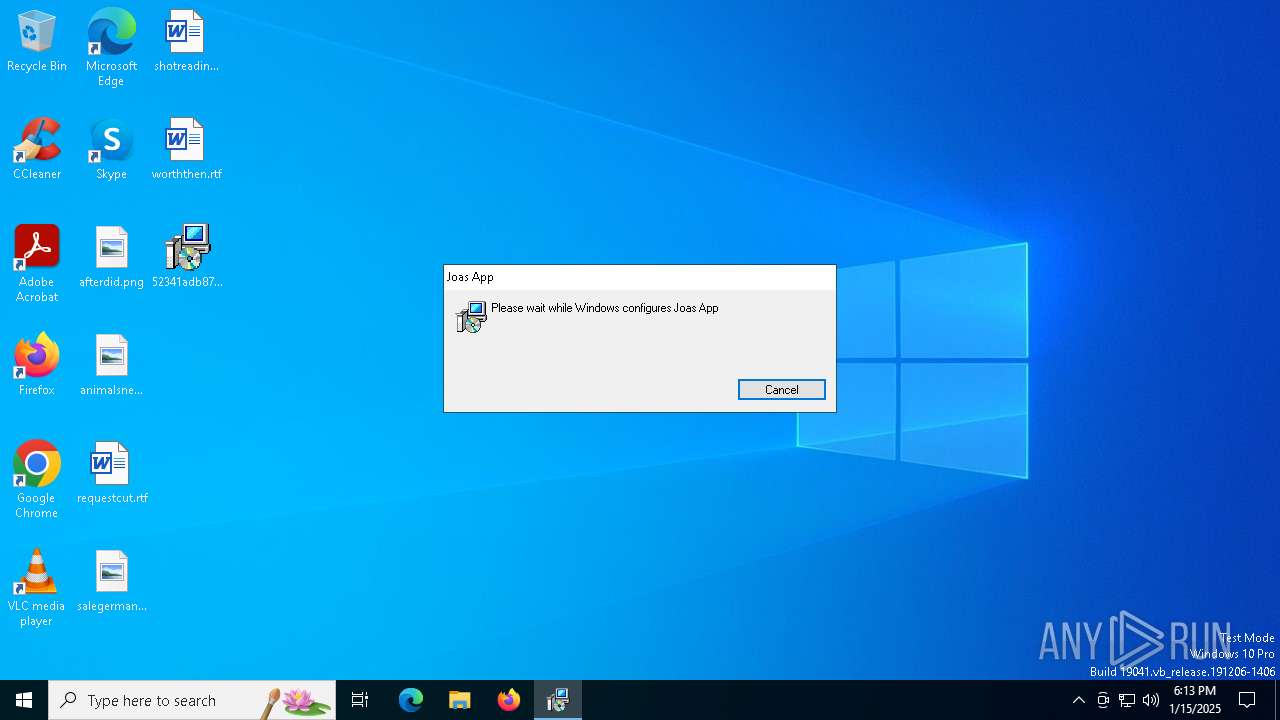
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {B33EC93A-7963-48BA-BFFE-FA8E09A16C9E}, Number of Words: 10, Subject: Joas App, Author: Barsoc Quite Sols, Name of Creating Application: Joas App, Template: x64;2057, Comments: This installer database contains the logic and data required to install Joas App., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Wed Jan 15 12:32:58 2025, Last Saved Time/Date: Wed Jan 15 12:32:58 2025, Last Printed: Wed Jan 15 12:32:58 2025, Number of Pages: 450 |
| MD5: | FC2FCA2711E9FF2C2D5919F4C27CD1A1 |
| SHA1: | 1D0A411878F9EBC1C5C7DA1B2FE812C295A37CBD |
| SHA256: | 52341ADB87A5E79D06901A64002C494E3F431C378193982C30225EAB3B136688 |
| SSDEEP: | 196608:mrFVNBAlwKwiV+PR9U+nv8LcngwlDXB7b421If9:6PIOhianXEdwlDtb4P |
MALICIOUS
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 6632)
Bypass execution policy to execute commands
- powershell.exe (PID: 6772)
SUSPICIOUS
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6632)
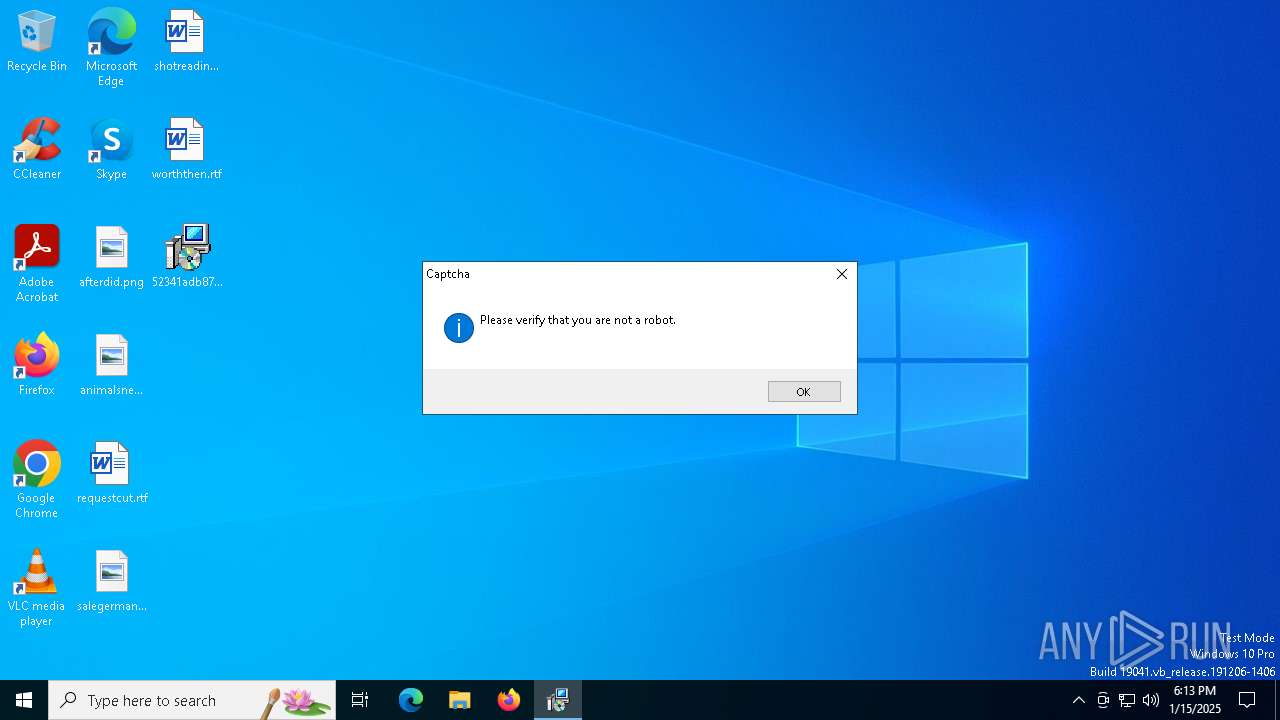
The process hide an interactive prompt from the user
- msiexec.exe (PID: 6632)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 6632)
Checks Windows Trust Settings
- msiexec.exe (PID: 6632)
The process executes Powershell scripts
- msiexec.exe (PID: 6632)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 6632)
The process drops C-runtime libraries
- msiexec.exe (PID: 6580)
Reverses array data (POWERSHELL)
- powershell.exe (PID: 6772)
Process drops legitimate windows executable
- msiexec.exe (PID: 6580)
INFO
Reads the computer name
- msiexec.exe (PID: 6580)
- msiexec.exe (PID: 6632)
An automatically generated document
- msiexec.exe (PID: 6468)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6580)
The sample compiled with english language support
- msiexec.exe (PID: 6580)
Checks proxy server information
- msiexec.exe (PID: 6632)
Checks supported languages
- msiexec.exe (PID: 6632)
- msiexec.exe (PID: 6580)
- createdump.exe (PID: 6932)
Reads Environment values
- msiexec.exe (PID: 6632)
Create files in a temporary directory
- msiexec.exe (PID: 6632)
- powershell.exe (PID: 6772)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6632)
Reads the software policy settings
- msiexec.exe (PID: 6632)
- powershell.exe (PID: 6772)
Reads security settings of Internet Explorer
- powershell.exe (PID: 6772)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6772)
Creates files or folders in the user directory
- msiexec.exe (PID: 6580)
Creates a software uninstall entry
- msiexec.exe (PID: 6580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {B33EC93A-7963-48BA-BFFE-FA8E09A16C9E} |
| Words: | 10 |
| Subject: | Joas App |
| Author: | Barsoc Quite Sols |
| LastModifiedBy: | - |
| Software: | Joas App |
| Template: | x64;2057 |
| Comments: | This installer database contains the logic and data required to install Joas App. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2025:01:15 12:32:58 |
| ModifyDate: | 2025:01:15 12:32:58 |
| LastPrinted: | 2025:01:15 12:32:58 |
| Pages: | 450 |
Total processes
119
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6468 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\52341adb87a5e79d06901a64002c494e3f431c378193982c30225eab3b136688.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6580 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6632 | C:\Windows\syswow64\MsiExec.exe -Embedding 92579458F0AB37376F94C38DFA7874D0 | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6772 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pssC181.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msiC17E.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scrC17F.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scrC180.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6924 | "C:\Users\admin\AppData\Roaming\Barsoc Quite Sols\Joas App\obs-ffmpeg-mux.exe" | C:\Users\admin\AppData\Roaming\Barsoc Quite Sols\Joas App\obs-ffmpeg-mux.exe | — | msiexec.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 6932 | "C:\Users\admin\AppData\Roaming\Barsoc Quite Sols\Joas App\createdump.exe" | C:\Users\admin\AppData\Roaming\Barsoc Quite Sols\Joas App\createdump.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Runtime Crash Dump Generator Exit code: 4294967295 Version: 6,0,2223,42425 @Commit: 4bb6dc195c0a3bc4c7e24ff54a8925b98db Modules
| |||||||||||||||
| 6940 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | obs-ffmpeg-mux.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6948 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | createdump.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 470
Read events
9 325
Write events
136
Delete events
9
Modification events
| (PID) Process: | (6580) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: B4190000FF9D8A1C7967DB01 | |||
| (PID) Process: | (6580) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: CD2B15C58EBADE4A8582117A295A888219DDF11F9ABBAC8DD1CBCB50FEA530CD | |||
| (PID) Process: | (6580) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6580) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Users\admin\AppData\Roaming\Microsoft\Installer\ |
Value: | |||
| (PID) Process: | (6580) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\E443C93FE38A0674D88A2F672090B5F4 |
| Operation: | write | Name: | F77D37381FFFF4549ACB50E784EDD908 |
Value: C:\Users\admin\AppData\Roaming\Barsoc Quite Sols\Joas App\ | |||
| (PID) Process: | (6580) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\187E38CB2ED78A74793CE2C69CCBDA28 |
| Operation: | write | Name: | F77D37381FFFF4549ACB50E784EDD908 |
Value: 21:\Software\Barsoc Quite Sols\Joas App\Version | |||
| (PID) Process: | (6580) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\3E23C972A00A3154A9B83D89A4146ABF |
| Operation: | write | Name: | F77D37381FFFF4549ACB50E784EDD908 |
Value: C:\Users\admin\AppData\Roaming\Barsoc Quite Sols\Joas App\utest.dll | |||
| (PID) Process: | (6580) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\4E53B16B1EB817146BB92E24C39E71F9 |
| Operation: | write | Name: | F77D37381FFFF4549ACB50E784EDD908 |
Value: C:\Users\admin\AppData\Roaming\Barsoc Quite Sols\Joas App\vcruntime140.dll | |||
| (PID) Process: | (6580) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\EE69BDDFD74852B4581B566E26FC368A |
| Operation: | write | Name: | F77D37381FFFF4549ACB50E784EDD908 |
Value: C:\Users\admin\AppData\Roaming\Barsoc Quite Sols\Joas App\vcruntime140_1.dll | |||
| (PID) Process: | (6580) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\DE8D80696CE804542B23A42863608F26 |
| Operation: | write | Name: | F77D37381FFFF4549ACB50E784EDD908 |
Value: C:\Users\admin\AppData\Roaming\Barsoc Quite Sols\Joas App\msvcp140.dll | |||
Executable files
53
Suspicious files
16
Text files
7
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6580 | msiexec.exe | C:\Windows\Installer\13aa9b.msi | — | |
MD5:— | SHA256:— | |||
| 6632 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msiC17E.txt | — | |
MD5:— | SHA256:— | |||
| 6632 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scrC17F.ps1 | — | |
MD5:— | SHA256:— | |||
| 6632 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scrC180.txt | — | |
MD5:— | SHA256:— | |||
| 6632 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pssC181.ps1 | — | |
MD5:— | SHA256:— | |||
| 6580 | msiexec.exe | C:\Windows\Installer\MSIAD3C.tmp | executable | |
MD5:EE09D6A1BB908B42C05FD0BEEB67DFD2 | SHA256:7BBF611F5E2A16439DC8CD11936F6364F6D5CC0044545C92775DA5646AFC7752 | |||
| 6580 | msiexec.exe | C:\Windows\Installer\MSIAC02.tmp | executable | |
MD5:EE09D6A1BB908B42C05FD0BEEB67DFD2 | SHA256:7BBF611F5E2A16439DC8CD11936F6364F6D5CC0044545C92775DA5646AFC7752 | |||
| 6580 | msiexec.exe | C:\Windows\Installer\MSIC00F.tmp | binary | |
MD5:274F395DD6526409A1218A34AAC05B7A | SHA256:7B354CB16D6894BA5F6B7BAAAE98B3BEE4C082655762AC98241C734EB7D0E7B4 | |||
| 6772 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lmgjjrwl.0ys.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6772 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2nkmjomd.hnu.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
19
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 403 | 188.114.97.3:443 | https://staticmaxepress.com/updater2.php | unknown | html | 4.42 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6632 | msiexec.exe | 188.114.96.3:443 | staticmaxepress.com | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
staticmaxepress.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |