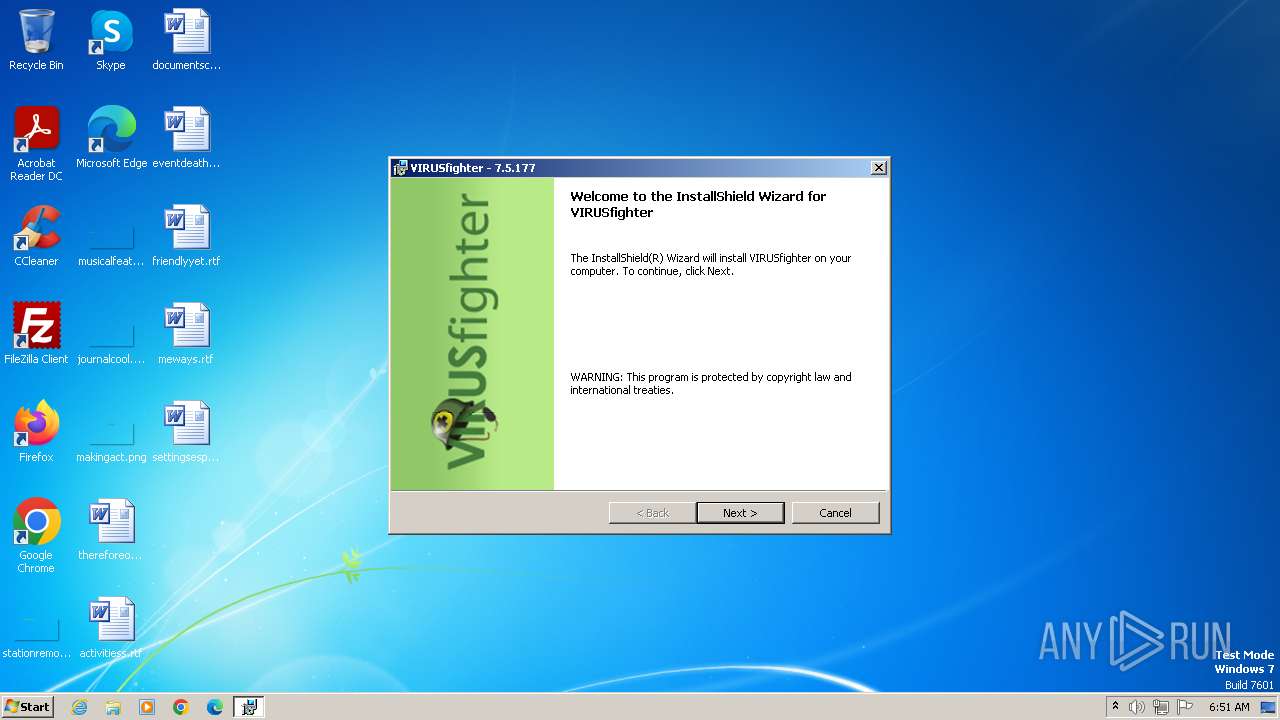
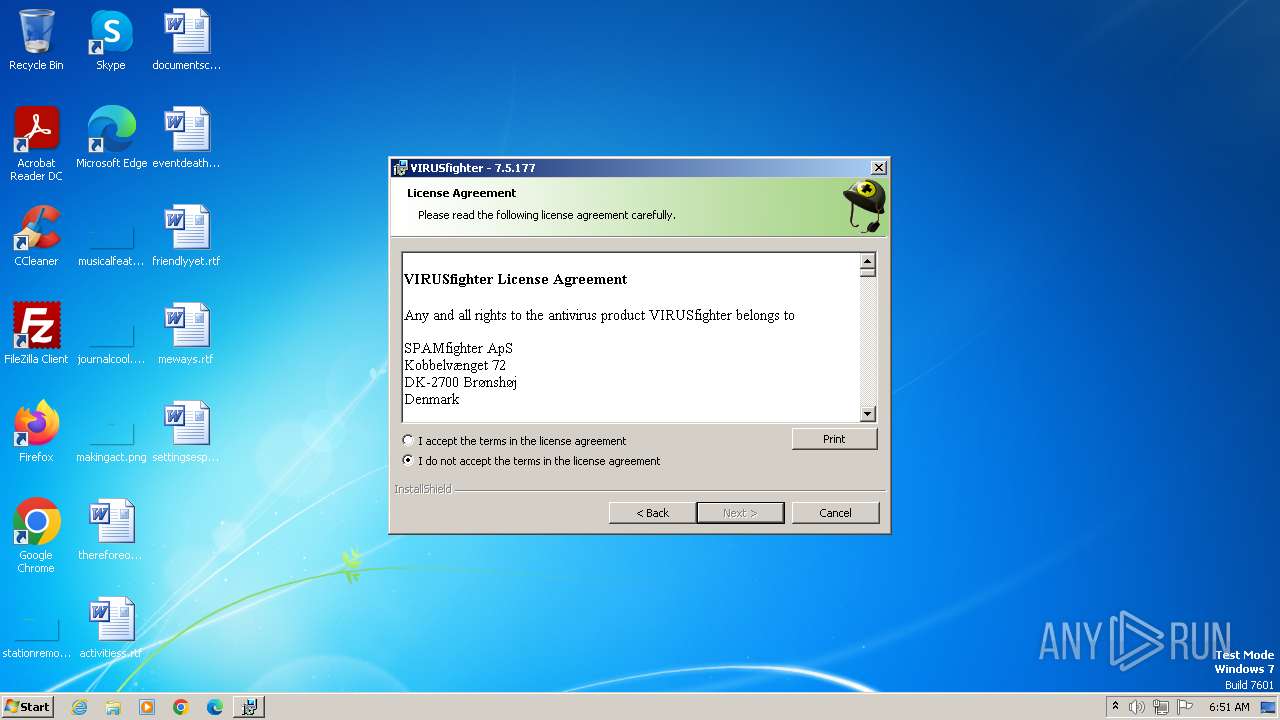
| File name: | VIRUSfighter_web.exe |
| Full analysis: | https://app.any.run/tasks/5adef739-ac2e-4afe-ab59-604865e9c015 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | October 21, 2023, 05:51:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A8AB6EC46B1845AA4C8339A5056451A8 |
| SHA1: | 415AC6711B9C398AD74FEA13E51E0A3901A8224D |
| SHA256: | 523224E0C00FCB65F324C2914758F9CEC84EED87337EAF9CC0F9661E526DD6CB |
| SSDEEP: | 98304:wJFkNi9IkTLlI8njk7jweIL+Pvm0gdNkQ1QCZ3psUqC5VFgMPFKu:LU/ |
MALICIOUS
Drops the executable file immediately after the start
- VIRUSfighter_web.exe (PID: 2732)
- msiexec.exe (PID: 576)
- msiexec.exe (PID: 3516)
- FightersTray.exe (PID: 1044)
- AVScanningService.exe (PID: 2896)
Application was dropped or rewritten from another process
- SWVFSetup_x32.exe (PID: 2960)
- FighterSuiteService.exe (PID: 2380)
- avdriversetup_x86.exe (PID: 3276)
- AVScanningService.exe (PID: 3840)
- AVWatchService.exe (PID: 4060)
- FighterSuiteService.exe (PID: 2608)
- machineid.exe (PID: 2564)
- AVScanningService.exe (PID: 1808)
- AVScanningService.exe (PID: 2896)
- AVWatchService.exe (PID: 2920)
- AVWatchService.exe (PID: 3600)
- FighterLauncher.exe (PID: 4068)
- FightersTray.exe (PID: 1044)
- vfproTray.exe (PID: 3288)
- FighterLauncher.exe (PID: 3380)
- FighterLauncher.exe (PID: 3004)
- vfproTray.exe (PID: 2468)
- FighterSuiteService.exe (PID: 2780)
Loads dropped or rewritten executable
- msiexec.exe (PID: 576)
- FighterSuiteService.exe (PID: 2380)
- msiexec.exe (PID: 3180)
- AVScanningService.exe (PID: 3840)
- FighterSuiteService.exe (PID: 2608)
- FighterSuiteService.exe (PID: 2780)
- AVWatchService.exe (PID: 4060)
- AVScanningService.exe (PID: 1808)
- AVScanningService.exe (PID: 2896)
- AVWatchService.exe (PID: 2920)
- AVWatchService.exe (PID: 3600)
- FighterLauncher.exe (PID: 4068)
- FightersTray.exe (PID: 1044)
- vfproTray.exe (PID: 3288)
- FighterLauncher.exe (PID: 3380)
- FighterLauncher.exe (PID: 3004)
- vfproTray.exe (PID: 2468)
Creates a writable file the system directory
- rundll32.exe (PID: 2856)
- machineid.exe (PID: 2564)
Connects to the CnC server
- FightersTray.exe (PID: 1044)
Registers / Runs the DLL via REGSVR32.EXE
- AVScanningService.exe (PID: 2896)
SUSPICIOUS
Reads the Internet Settings
- VIRUSfighter_web.exe (PID: 2732)
- msiexec.exe (PID: 2232)
- msiexec.exe (PID: 3180)
- runonce.exe (PID: 1592)
- FightersTray.exe (PID: 1044)
Executes as Windows Service
- VSSVC.exe (PID: 3652)
- FighterSuiteService.exe (PID: 2780)
- AVScanningService.exe (PID: 2896)
- AVWatchService.exe (PID: 3600)
Process drops legitimate windows executable
- msiexec.exe (PID: 3516)
The process drops C-runtime libraries
- msiexec.exe (PID: 3516)
Uses RUNDLL32.EXE to load library
- avdriversetup_x86.exe (PID: 3276)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 3516)
- rundll32.exe (PID: 2856)
Reads settings of System Certificates
- rundll32.exe (PID: 2856)
Process requests binary or script from the Internet
- FightersTray.exe (PID: 1044)
- AVScanningService.exe (PID: 2896)
Application launched itself
- FighterLauncher.exe (PID: 3380)
INFO
Reads the computer name
- VIRUSfighter_web.exe (PID: 2732)
- SWVFSetup_x32.exe (PID: 2960)
- msiexec.exe (PID: 3180)
- msiexec.exe (PID: 3516)
- msiexec.exe (PID: 576)
- avdriversetup_x86.exe (PID: 3276)
- FighterSuiteService.exe (PID: 2380)
- AVScanningService.exe (PID: 3840)
- FighterSuiteService.exe (PID: 2608)
- FighterSuiteService.exe (PID: 2780)
- machineid.exe (PID: 2564)
- AVScanningService.exe (PID: 1808)
- AVScanningService.exe (PID: 2896)
- AVWatchService.exe (PID: 2920)
- AVWatchService.exe (PID: 3600)
- FighterLauncher.exe (PID: 4068)
- FightersTray.exe (PID: 1044)
- vfproTray.exe (PID: 3288)
- FighterLauncher.exe (PID: 3380)
- FighterLauncher.exe (PID: 3004)
- vfproTray.exe (PID: 2468)
- AVWatchService.exe (PID: 4060)
Checks supported languages
- VIRUSfighter_web.exe (PID: 2732)
- SWVFSetup_x32.exe (PID: 2960)
- msiexec.exe (PID: 3516)
- msiexec.exe (PID: 3180)
- msiexec.exe (PID: 576)
- FighterSuiteService.exe (PID: 2380)
- avdriversetup_x86.exe (PID: 3276)
- AVScanningService.exe (PID: 3840)
- AVWatchService.exe (PID: 4060)
- FighterSuiteService.exe (PID: 2608)
- FighterSuiteService.exe (PID: 2780)
- machineid.exe (PID: 2564)
- AVScanningService.exe (PID: 1808)
- AVScanningService.exe (PID: 2896)
- AVWatchService.exe (PID: 2920)
- FighterLauncher.exe (PID: 4068)
- AVWatchService.exe (PID: 3600)
- FightersTray.exe (PID: 1044)
- vfproTray.exe (PID: 3288)
- FighterLauncher.exe (PID: 3380)
- vfproTray.exe (PID: 2468)
- FighterLauncher.exe (PID: 3004)
Create files in a temporary directory
- VIRUSfighter_web.exe (PID: 2732)
- SWVFSetup_x32.exe (PID: 2960)
- msiexec.exe (PID: 2232)
- msiexec.exe (PID: 576)
- msiexec.exe (PID: 3516)
- rundll32.exe (PID: 2856)
Checks proxy server information
- msiexec.exe (PID: 2232)
Drops the executable file immediately after the start
- msiexec.exe (PID: 2232)
- rundll32.exe (PID: 2856)
Reads Microsoft Office registry keys
- msiexec.exe (PID: 576)
- msiexec.exe (PID: 3180)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3516)
- msiexec.exe (PID: 576)
- machineid.exe (PID: 2564)
- FighterSuiteService.exe (PID: 2780)
- AVWatchService.exe (PID: 3600)
- msiexec.exe (PID: 3180)
- AVScanningService.exe (PID: 2896)
Application launched itself
- msiexec.exe (PID: 3516)
- msedge.exe (PID: 3908)
Creates files in the program directory
- FighterSuiteService.exe (PID: 2380)
- rundll32.exe (PID: 2856)
- AVScanningService.exe (PID: 3840)
- AVWatchService.exe (PID: 4060)
- FighterSuiteService.exe (PID: 2780)
- AVScanningService.exe (PID: 2896)
- AVWatchService.exe (PID: 3600)
Creates files in the driver directory
- rundll32.exe (PID: 2856)
Reads the time zone
- runonce.exe (PID: 1592)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 2856)
Reads product name
- FighterSuiteService.exe (PID: 2780)
Reads Environment values
- FighterSuiteService.exe (PID: 2780)
- AVScanningService.exe (PID: 2896)
Creates a software uninstall entry
- msiexec.exe (PID: 3180)
Manual execution by a user
- vfproTray.exe (PID: 3288)
- FightersTray.exe (PID: 1044)
- msedge.exe (PID: 3908)
Creates files or folders in the user directory
- FighterLauncher.exe (PID: 4068)
- FightersTray.exe (PID: 1044)
- vfproTray.exe (PID: 3288)
- FighterLauncher.exe (PID: 3380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (54.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (34.8) |
| .exe | | | Win32 Executable (generic) (5.6) |
| .exe | | | Generic Win/DOS Executable (2.5) |
| .exe | | | DOS Executable Generic (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:01:06 16:06:51+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 283136 |
| InitializedDataSize: | 235520 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x240d3 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.5.177.0 |
| ProductVersionNumber: | 7.5.177.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | SPAMfighter ApS |
| LegalCopyright: | Copyright (C) 2011 SPAMfighter ApS |
| FileVersion: | 7.5.177.0 |
| ProductVersion: | 7.5.177.0 |
| ProductName: | VIRUSfighter |
| InternalName: | VIRUSfighter Setup |
| OriginalFileName: | Setup.exe |
| FileDescription: | VIRUSfighter Installation Package |
Total processes
96
Monitored processes
49
Malicious processes
17
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2616 --field-trial-handle=1220,i,4983424556548969632,12441256761396335992,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 576 | C:\Windows\system32\MsiExec.exe -Embedding B6ADFCC0C0B2762E4E425EF1CE0303DC C | C:\Windows\System32\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Fighters\Tray\FightersTray.exe" | C:\Program Files\Fighters\Tray\FightersTray.exe | explorer.exe | ||||||||||||
User: admin Company: SPAMfighter ApS Integrity Level: MEDIUM Description: FIGHTERtools Update Manager Exit code: 0 Version: 4.0.282.0 Modules
| |||||||||||||||
| 1176 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=2472 --field-trial-handle=1220,i,4983424556548969632,12441256761396335992,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1592 | "C:\Windows\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1808 | "C:\Program Files\Common Files\Common Toolkit Suite\AVEngine\\AVScanningService.exe" /s | C:\Program Files\Common Files\Common Toolkit Suite\AVEngine\AVScanningService.exe | — | msiexec.exe | |||||||||||
User: admin Company: Security Software Limited Integrity Level: HIGH Description: Preventon AV Scanning Service Exit code: 0 Version: 3.2.2 Modules
| |||||||||||||||
| 1908 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1564 --field-trial-handle=1220,i,4983424556548969632,12441256761396335992,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1912 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2284 --field-trial-handle=1220,i,4983424556548969632,12441256761396335992,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1928 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4424 --field-trial-handle=1220,i,4983424556548969632,12441256761396335992,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1940 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1260 --field-trial-handle=1220,i,4983424556548969632,12441256761396335992,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
15 189
Read events
15 035
Write events
140
Delete events
14
Modification events
| (PID) Process: | (2732) VIRUSfighter_web.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2732) VIRUSfighter_web.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2732) VIRUSfighter_web.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2732) VIRUSfighter_web.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2232) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2232) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2232) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2232) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2232) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2232) msiexec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000056010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
118
Suspicious files
1 258
Text files
694
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2960 | SWVFSetup_x32.exe | C:\Users\admin\AppData\Local\Temp\{06C86627-2D91-4EDA-9132-602C4B0523DD}\0x0406.ini | text | |
MD5:2934637BF3CCCDC7097C72044DE19F98 | SHA256:47BF75B72EA1581B567F4517B9FD4E6F718E39FBB4C751E5213E94B5312942BB | |||
| 2960 | SWVFSetup_x32.exe | C:\Users\admin\AppData\Local\Temp\{06C86627-2D91-4EDA-9132-602C4B0523DD}\Setup.INI | text | |
MD5:F9BDDEC4DF254B791B408A36EA007043 | SHA256:10E8FCD93716209AF114D2EAC8991618AEFA3311F17C2A658C004F8C675D0BF5 | |||
| 2960 | SWVFSetup_x32.exe | C:\Users\admin\AppData\Local\Temp\{06C86627-2D91-4EDA-9132-602C4B0523DD}\0x0405.ini | text | |
MD5:E66F855502B409A2EAA50EF9BC66ACBD | SHA256:BBE50A141BB622513C4117EF72DABBBBD152F83393490A6B61173025BCBED188 | |||
| 2960 | SWVFSetup_x32.exe | C:\Users\admin\AppData\Local\Temp\{06C86627-2D91-4EDA-9132-602C4B0523DD}\_ISMSIDEL.INI | text | |
MD5:2AB39784DC5C543DA3CCFF96FFC3CF6F | SHA256:3CFC957D0361A379817E9DB75DBA2ED48F328412F2D1F6CD3FCC831E9D7C2944 | |||
| 2732 | VIRUSfighter_web.exe | C:\Users\admin\AppData\Local\Temp\VFSW1697867492\SWVFSetup_x32.exe | executable | |
MD5:B4BE99340B5461423FF830F871A2C1DA | SHA256:CB7AEFEE1D31B3CFABC8650CCC01AA4C383C9B2761CC2594FB989095A833BCF8 | |||
| 2960 | SWVFSetup_x32.exe | C:\Users\admin\AppData\Local\Temp\{06C86627-2D91-4EDA-9132-602C4B0523DD}\0x0409.ini | text | |
MD5:FB2887DF5A359468851A7080B9140311 | SHA256:A9CF5B5A4303CA758BDEFF308CBD59FC98CF918C3D51CD62913E2FC75D2E4339 | |||
| 2960 | SWVFSetup_x32.exe | C:\Users\admin\AppData\Local\Temp\{06C86627-2D91-4EDA-9132-602C4B0523DD}\0x040a.ini | text | |
MD5:4AF55AE1A38156139694B8A772E2661D | SHA256:5CBC55BF53B318A7C95865FDF161D9405EAECDC4047A0F23E4E9A6D1E6857021 | |||
| 2232 | msiexec.exe | C:\Windows\Installer\MSIEB29.tmp | — | |
MD5:— | SHA256:— | |||
| 2960 | SWVFSetup_x32.exe | C:\Users\admin\AppData\Local\Temp\{06C86627-2D91-4EDA-9132-602C4B0523DD}\0x0412.ini | text | |
MD5:EA1FE197FF8838CDF76D5EDF01772521 | SHA256:26345F5CA9CD84F01847DFF88EA3C0E95114DE8F5E747C48FA98D95AD07B9DB3 | |||
| 2960 | SWVFSetup_x32.exe | C:\Users\admin\AppData\Local\Temp\{06C86627-2D91-4EDA-9132-602C4B0523DD}\0x0414.ini | text | |
MD5:4BEFFE334C0F3A99E166EB0875448100 | SHA256:56C712FA85FCFBE2065370AFAF89741D634480EE2B542F1D902C0D79E040495B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
610
TCP/UDP connections
69
DNS requests
71
Threats
39
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
576 | msiexec.exe | GET | 200 | 51.144.56.51:80 | http://login.spamfighter.com/Loginsystem/EmailValidate/?Email= | unknown | text | 129 b | unknown |
3516 | msiexec.exe | GET | 200 | 13.107.246.64:80 | http://redir.download.spamfighter.com/spywarefighter/web/4.5.177/VF.cab | unknown | compressed | 3.90 Mb | unknown |
576 | msiexec.exe | GET | 302 | 51.144.56.51:80 | http://login.spamfighter.com/ | unknown | html | 147 b | unknown |
2232 | msiexec.exe | GET | 200 | 13.107.246.64:80 | http://redir.download.spamfighter.com/spywarefighter/web/4.5.177/Fighters.msi | unknown | executable | 10.9 Mb | unknown |
576 | msiexec.exe | GET | 200 | 51.144.56.51:80 | http://login.spamfighter.com/Loginsystem/EmailValidate/?Email=jsdnvbhd@gmail.com | unknown | text | 147 b | unknown |
3516 | msiexec.exe | GET | 200 | 13.107.246.64:80 | http://redir.download.spamfighter.com/spywarefighter/web/4.5.177/Toolkit.cab | unknown | compressed | 3.87 Mb | unknown |
3516 | msiexec.exe | GET | 200 | 13.107.246.64:80 | http://redir.download.spamfighter.com/spywarefighter/web/4.5.177/Common.cab | unknown | compressed | 2.51 Mb | unknown |
2780 | FighterSuiteService.exe | POST | 200 | 51.144.56.51:80 | http://update.spamfighter.com/Toolkit/Service.asmx | unknown | xml | 393 b | unknown |
2780 | FighterSuiteService.exe | POST | 200 | 51.144.56.51:80 | http://update.spamfighter.com/Toolkit/Service.asmx | unknown | xml | 4.91 Kb | unknown |
2780 | FighterSuiteService.exe | POST | 200 | 51.144.56.51:80 | http://update.spamfighter.com/Toolkit/Service.asmx | unknown | xml | 413 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2232 | msiexec.exe | 13.107.246.64:80 | redir.download.spamfighter.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
576 | msiexec.exe | 51.144.56.51:80 | login.spamfighter.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3516 | msiexec.exe | 13.107.246.64:80 | redir.download.spamfighter.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2780 | FighterSuiteService.exe | 51.144.56.51:80 | login.spamfighter.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2780 | FighterSuiteService.exe | 51.124.128.217:80 | download.dk.spamfighter.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2896 | AVScanningService.exe | 3.64.163.50:80 | sfxbvf8n.preventon.net | AMAZON-02 | DE | unknown |
2896 | AVScanningService.exe | 20.38.109.132:80 | blobsfavdownload.blob.core.windows.net | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
1044 | FightersTray.exe | 51.144.56.51:80 | login.spamfighter.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
redir.download.spamfighter.com |
| unknown |
login.spamfighter.com |
| unknown |
update.spamfighter.com |
| unknown |
download.dk.spamfighter.com |
| unknown |
sfxbvf8n.preventon.net |
| unknown |
blobsfavdownload.blob.core.windows.net |
| unknown |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.spamfighter.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2232 | msiexec.exe | Potential Corporate Privacy Violation | ET POLICY Observed MSI Download |
3516 | msiexec.exe | Potential Corporate Privacy Violation | ET HUNTING Suspicious Windows Installer UA for non-MSI |
3516 | msiexec.exe | Potential Corporate Privacy Violation | ET HUNTING Suspicious Windows Installer UA for non-MSI |
3516 | msiexec.exe | Potential Corporate Privacy Violation | ET HUNTING Suspicious Windows Installer UA for non-MSI |
1044 | FightersTray.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP PUP/SpamFighter CnC Request |
1044 | FightersTray.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP PUP/SpamFighter CnC Request |
1044 | FightersTray.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP PUP/SpamFighter CnC Request |
1044 | FightersTray.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP PUP/SpamFighter CnC Request |
1044 | FightersTray.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP PUP/SpamFighter CnC Request |
1044 | FightersTray.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP PUP/SpamFighter CnC Request |
Process | Message |
|---|---|
AVWatchService.exe | QObject: Cannot create children for a parent that is in a different thread.
(Parent is QCoreApplication(0x22f74c), parent's thread is QThread(0x6be0b8), current thread is QThread(0x6be1a8)
|
AVWatchService.exe | QObject: Cannot create children for a parent that is in a different thread.
(Parent is QCoreApplication(0x22f74c), parent's thread is QThread(0x6be0b8), current thread is QThread(0x6be1a8)
|