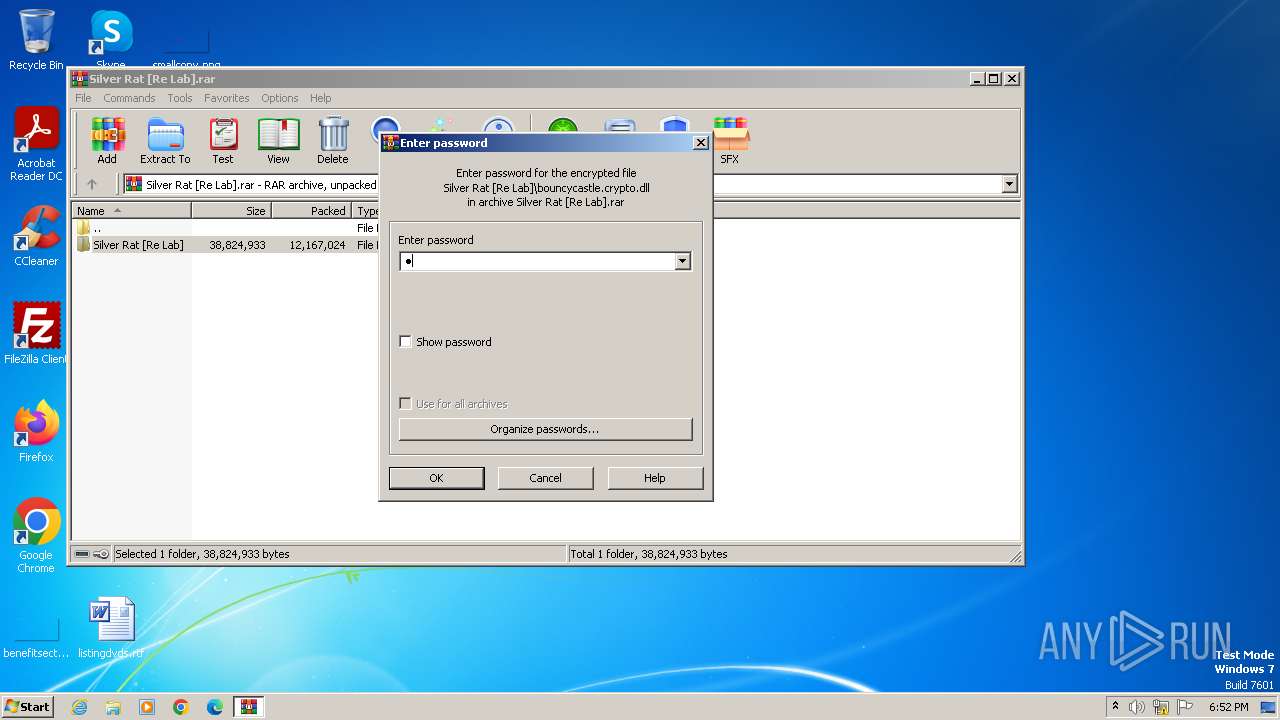
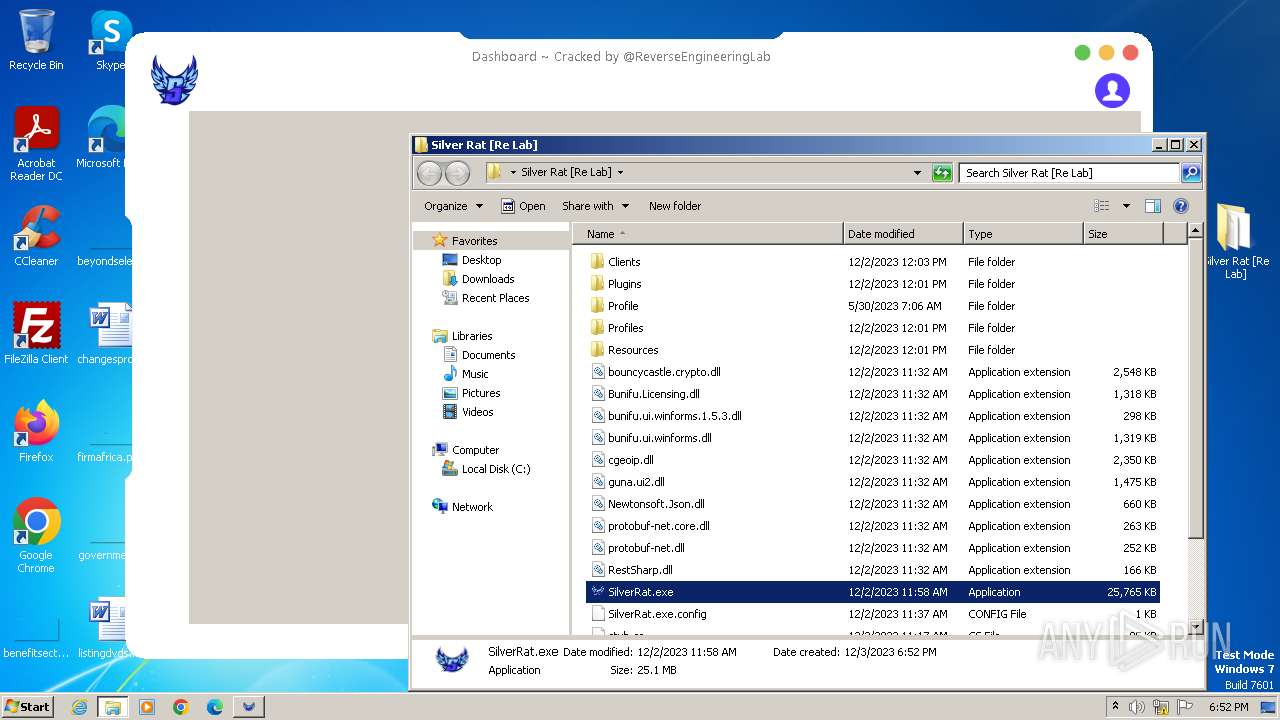
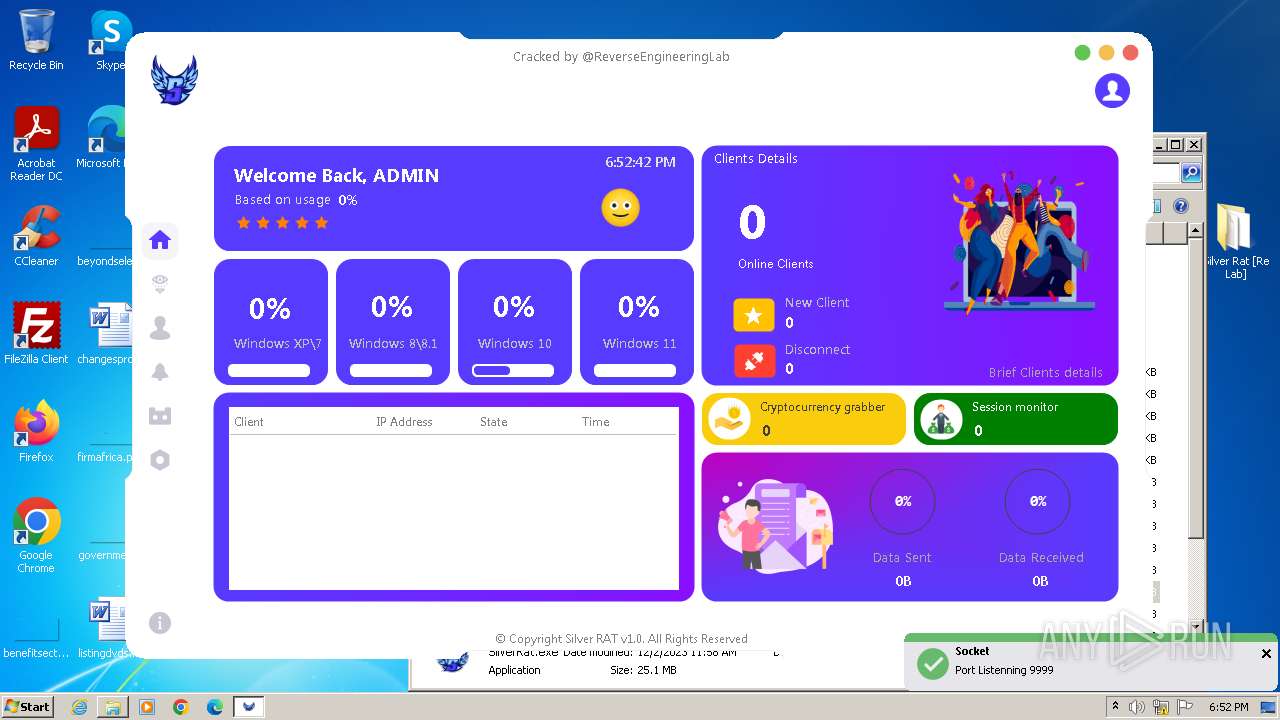
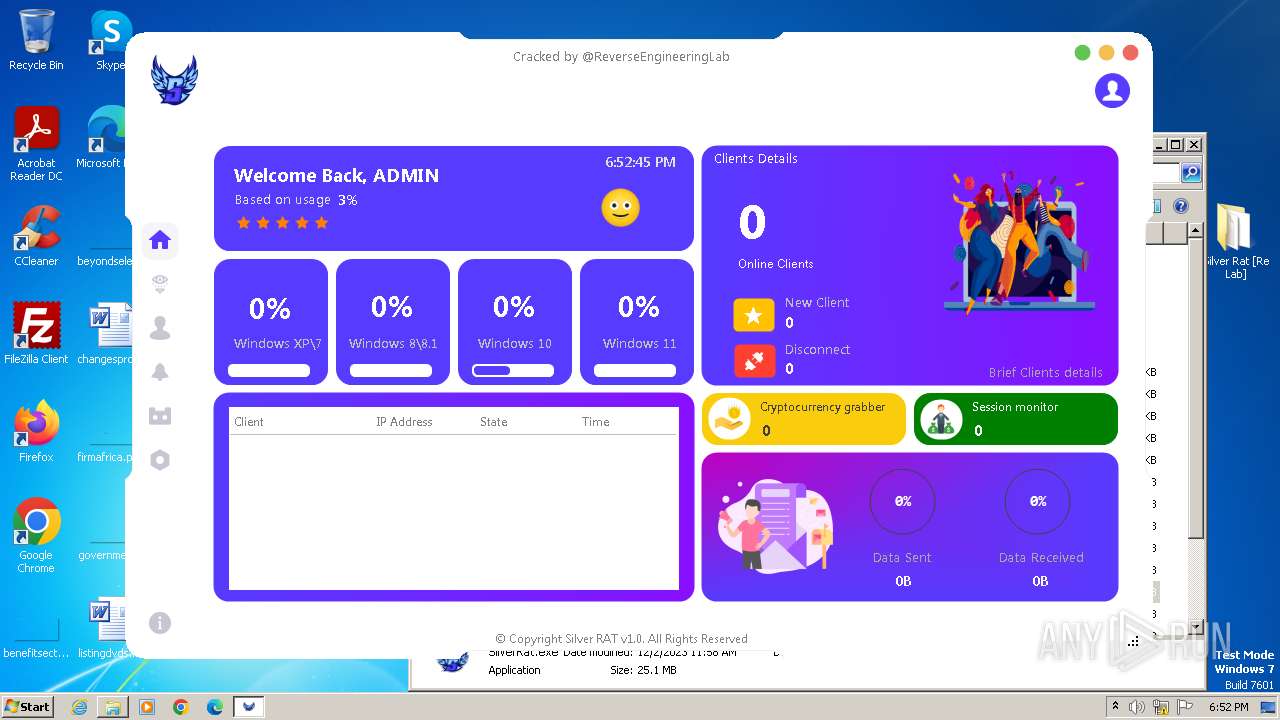
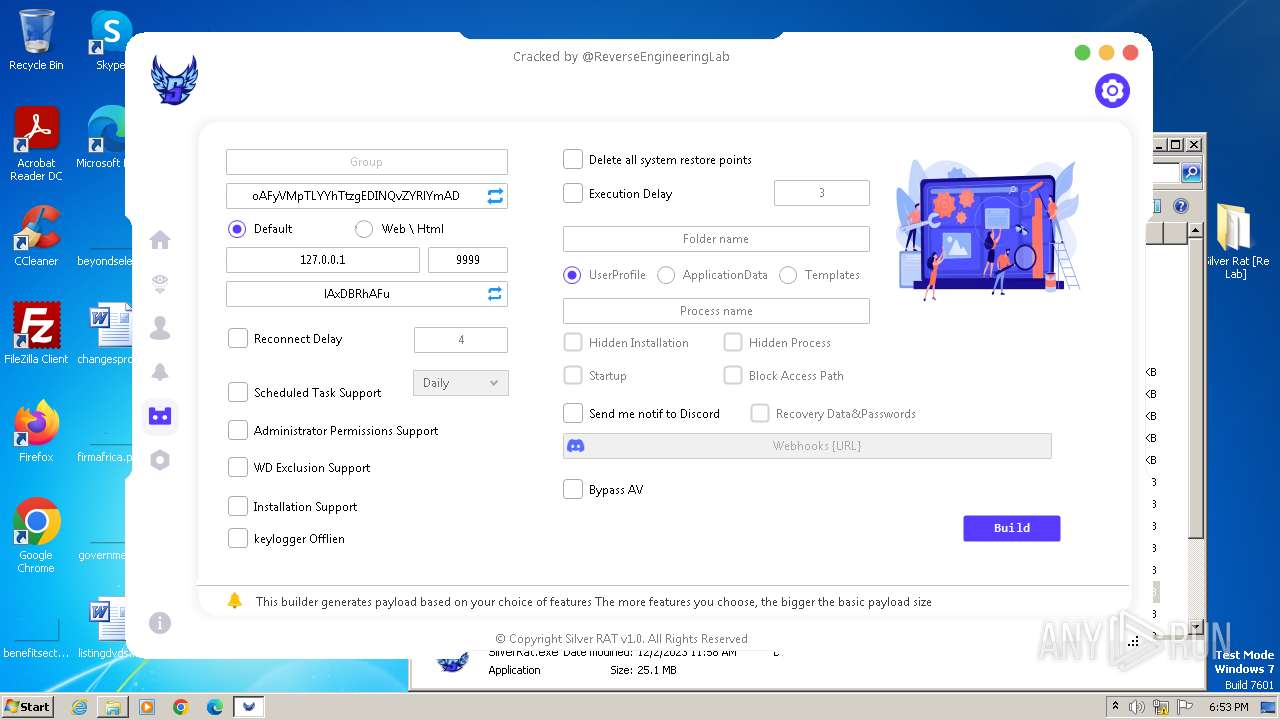
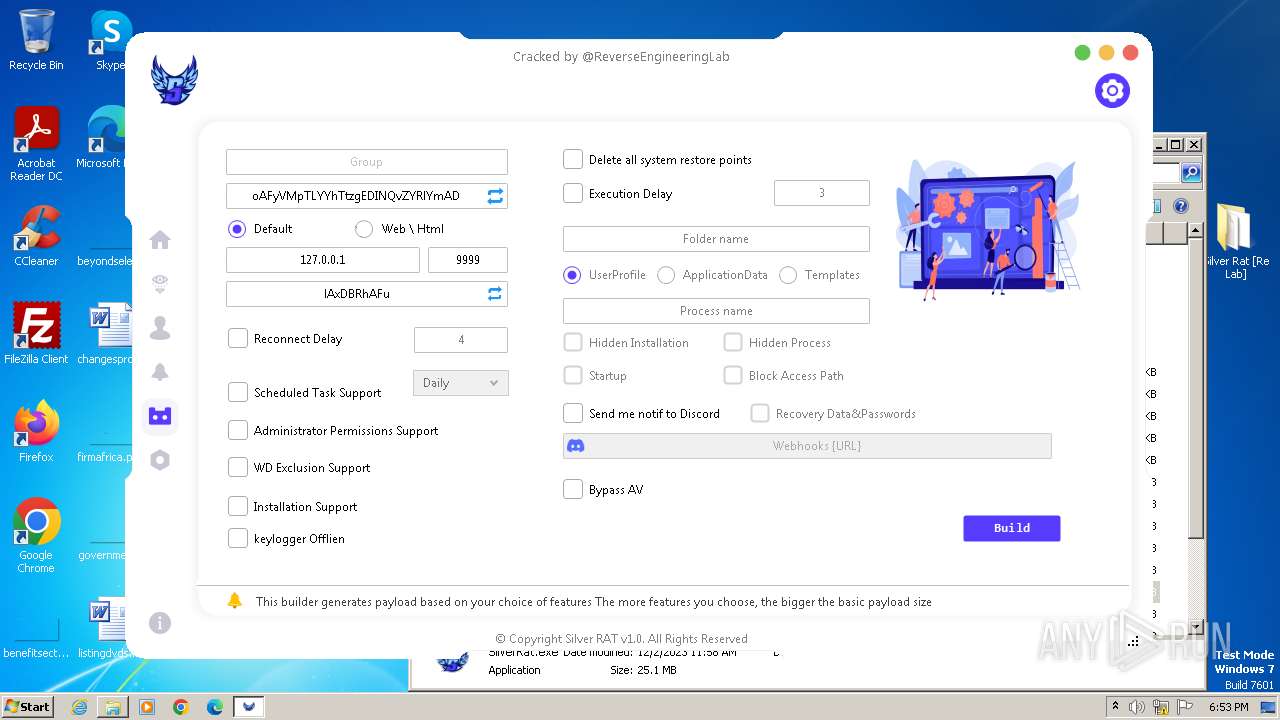
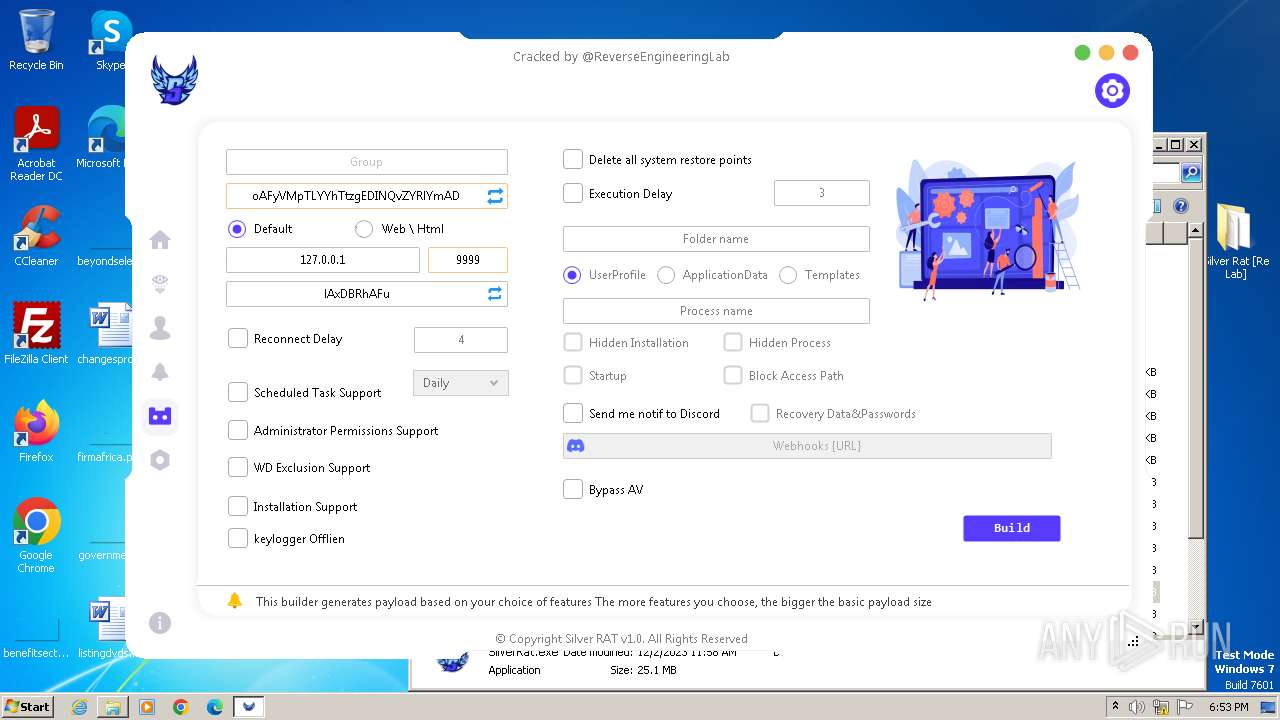
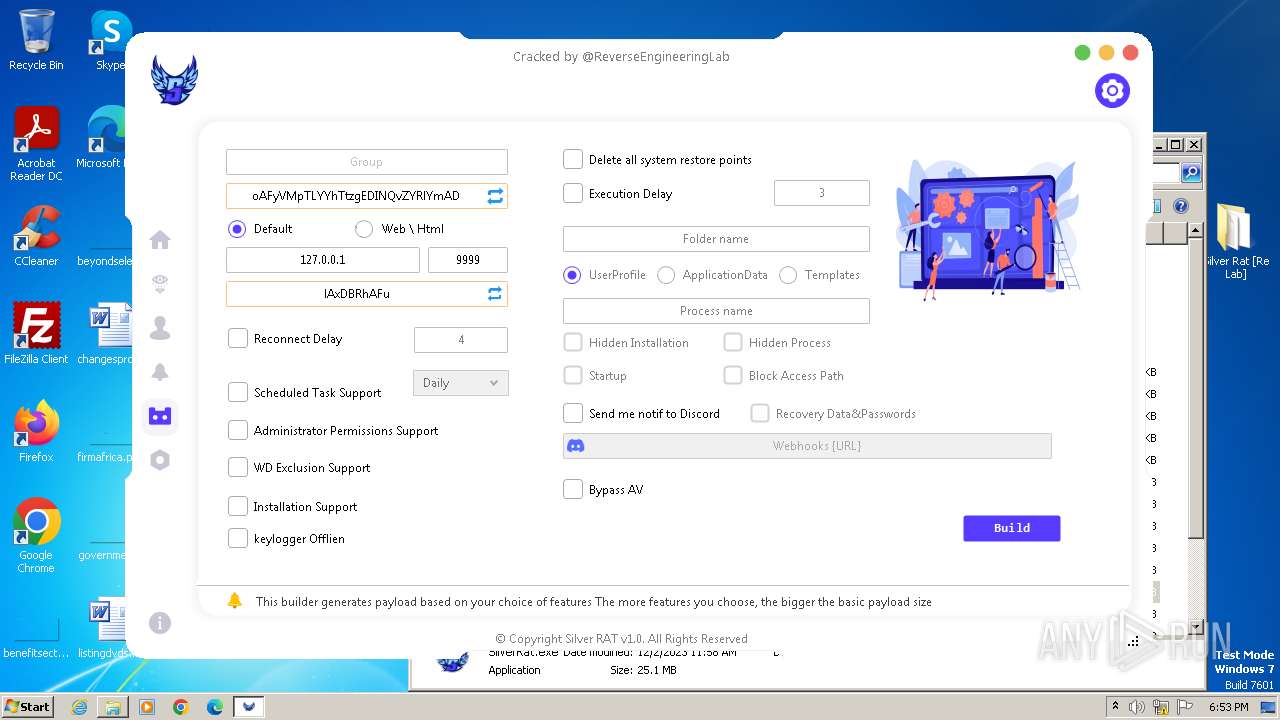
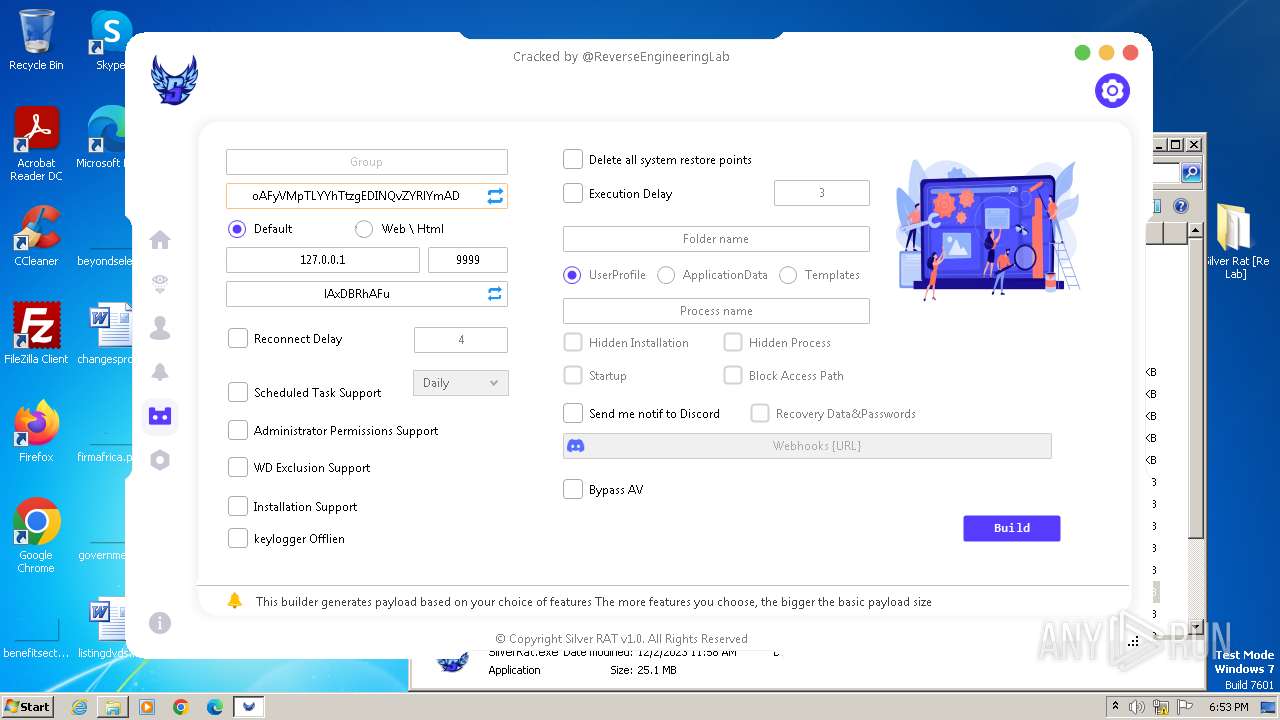
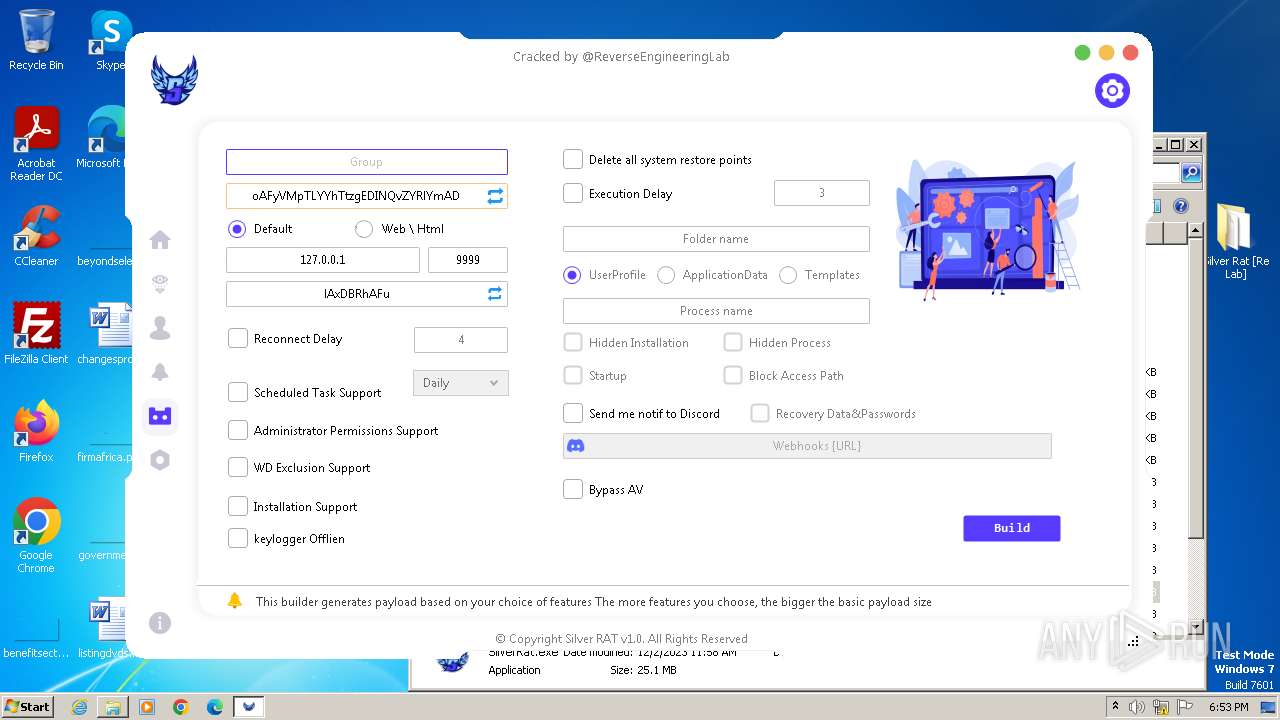
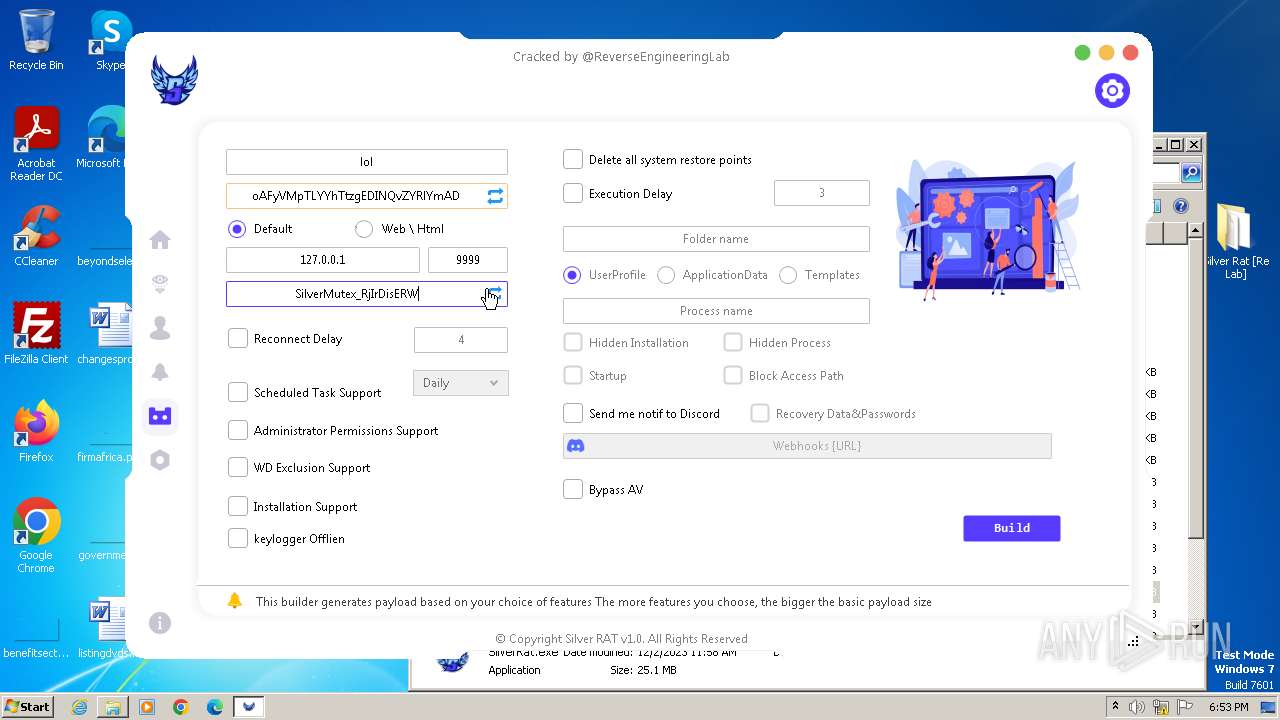
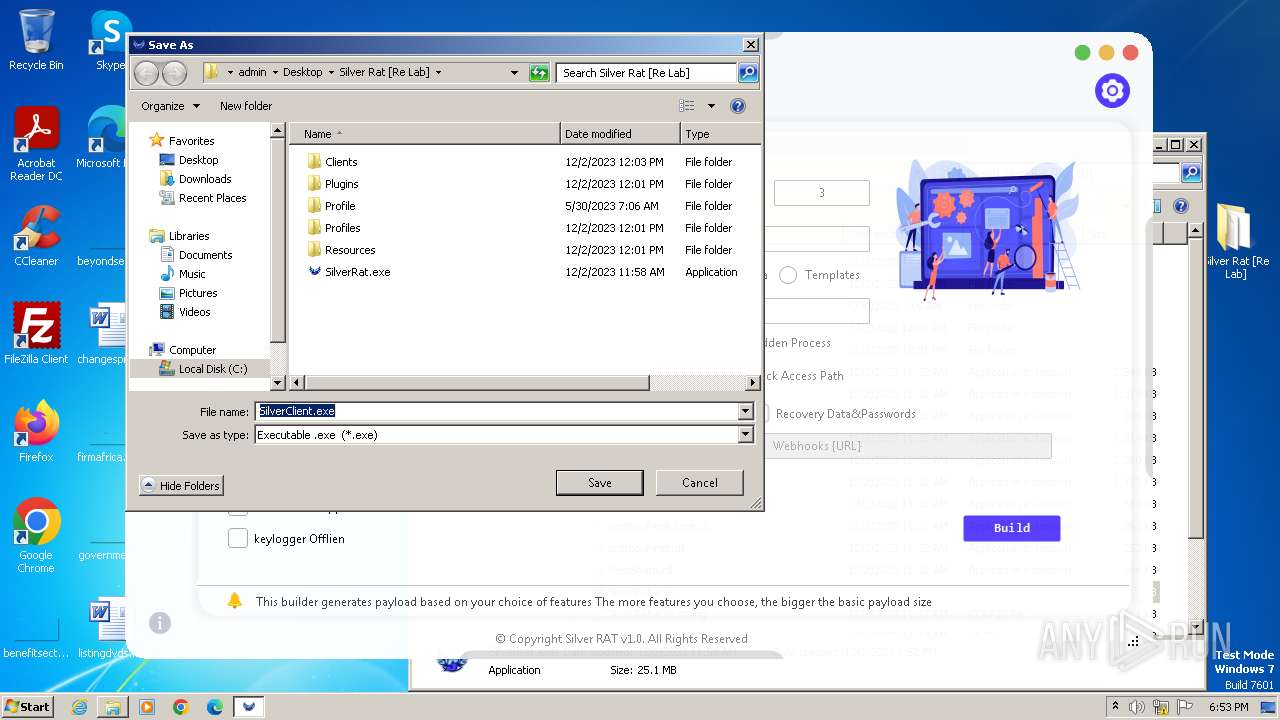
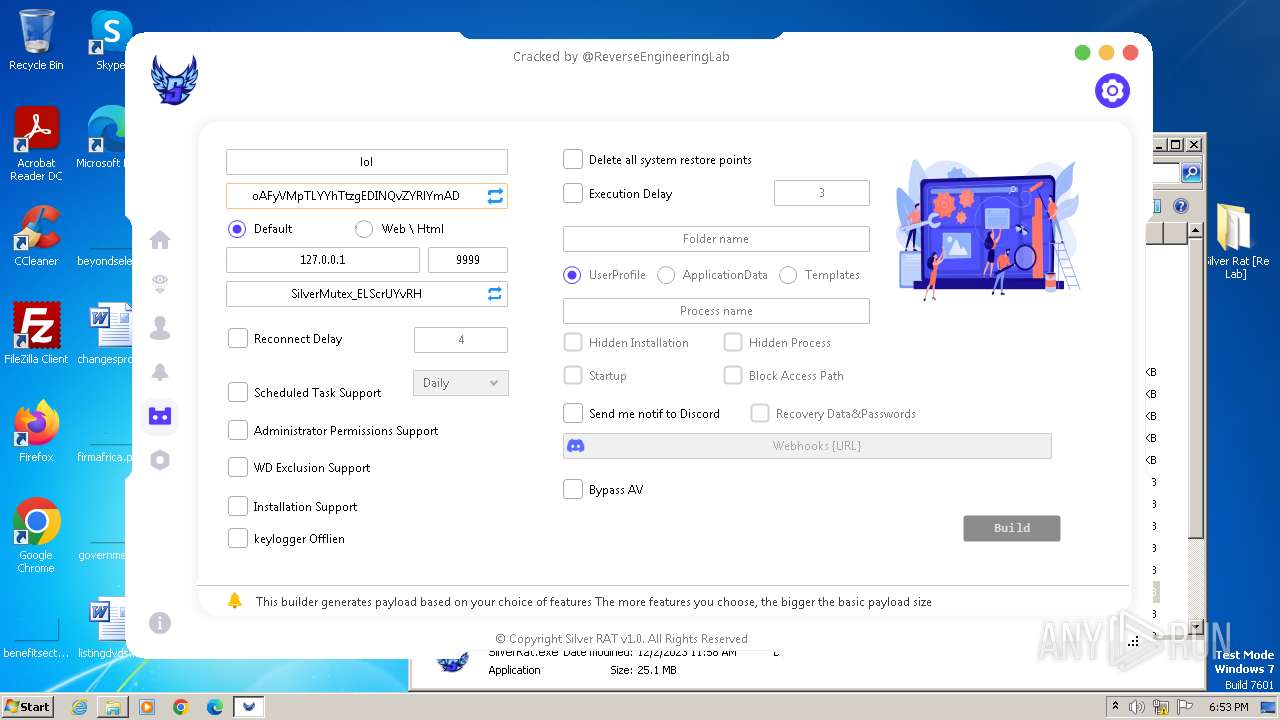
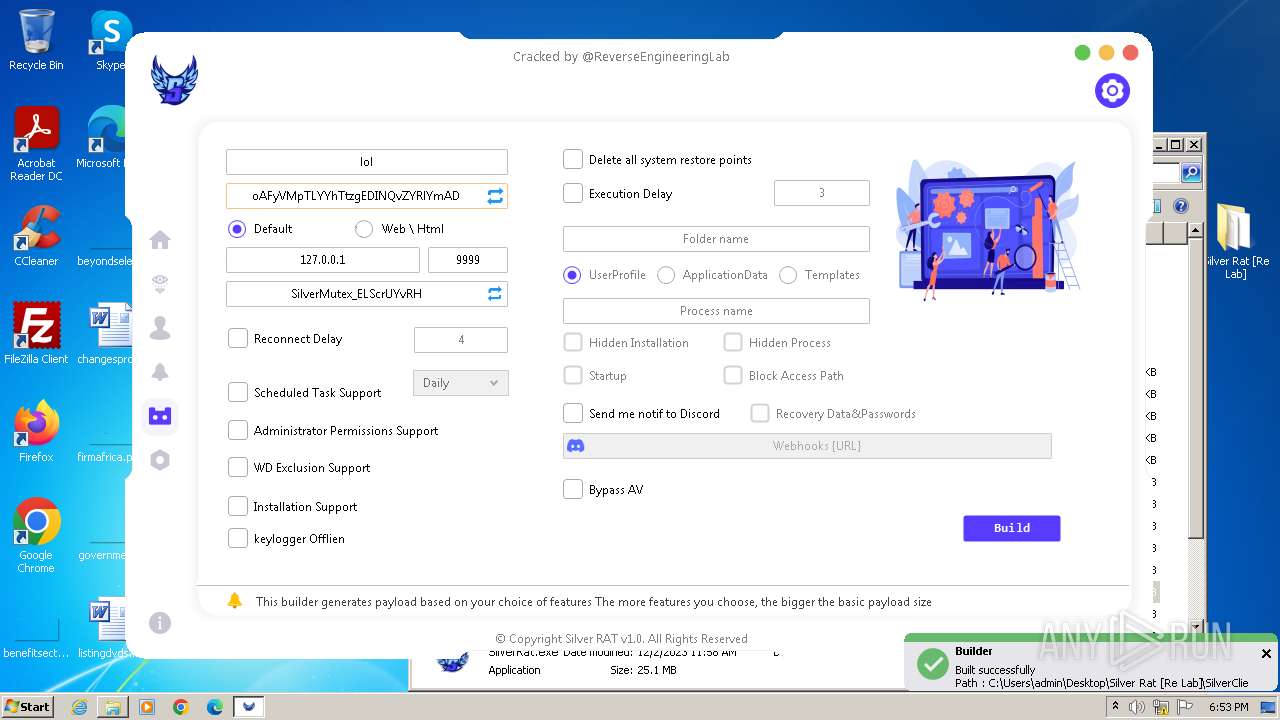
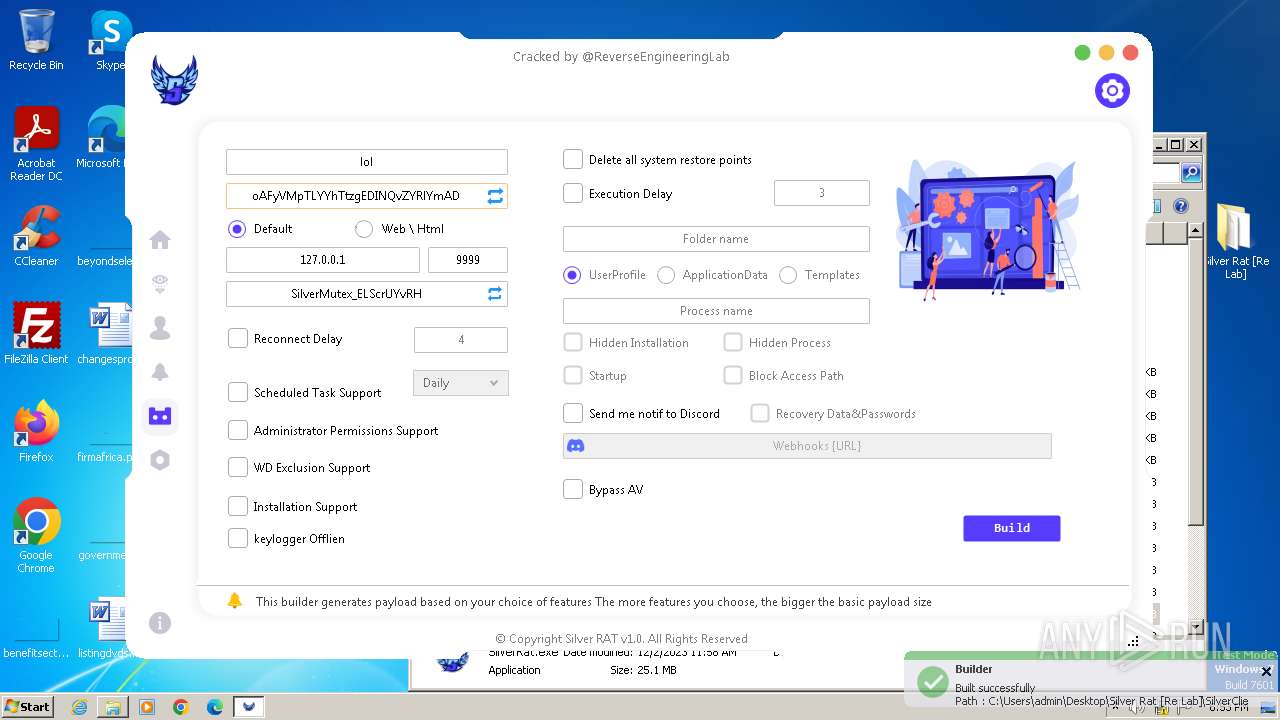
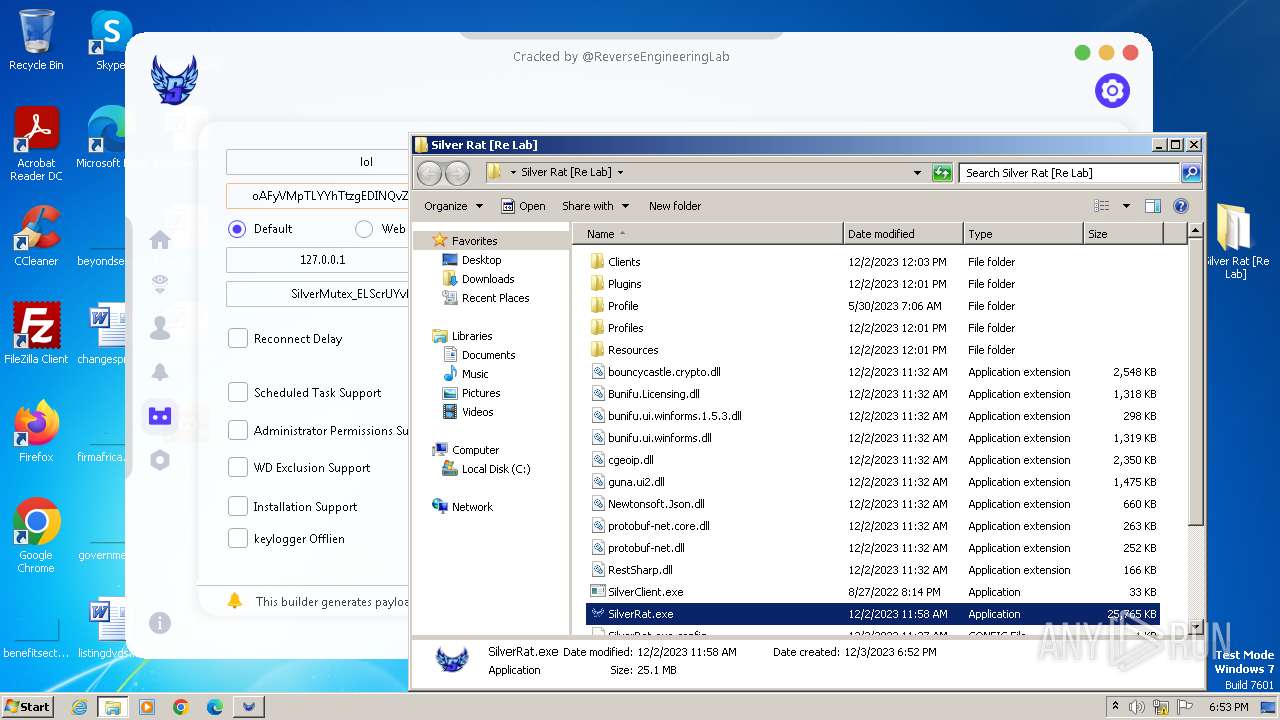
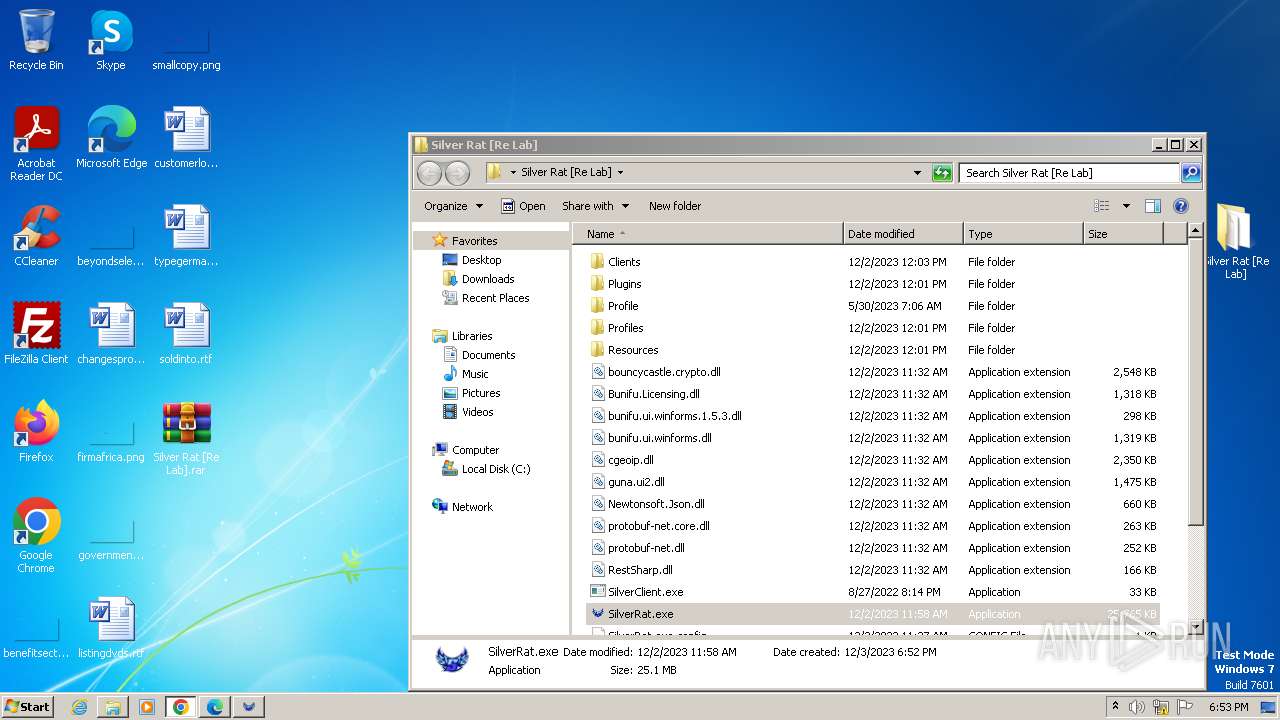
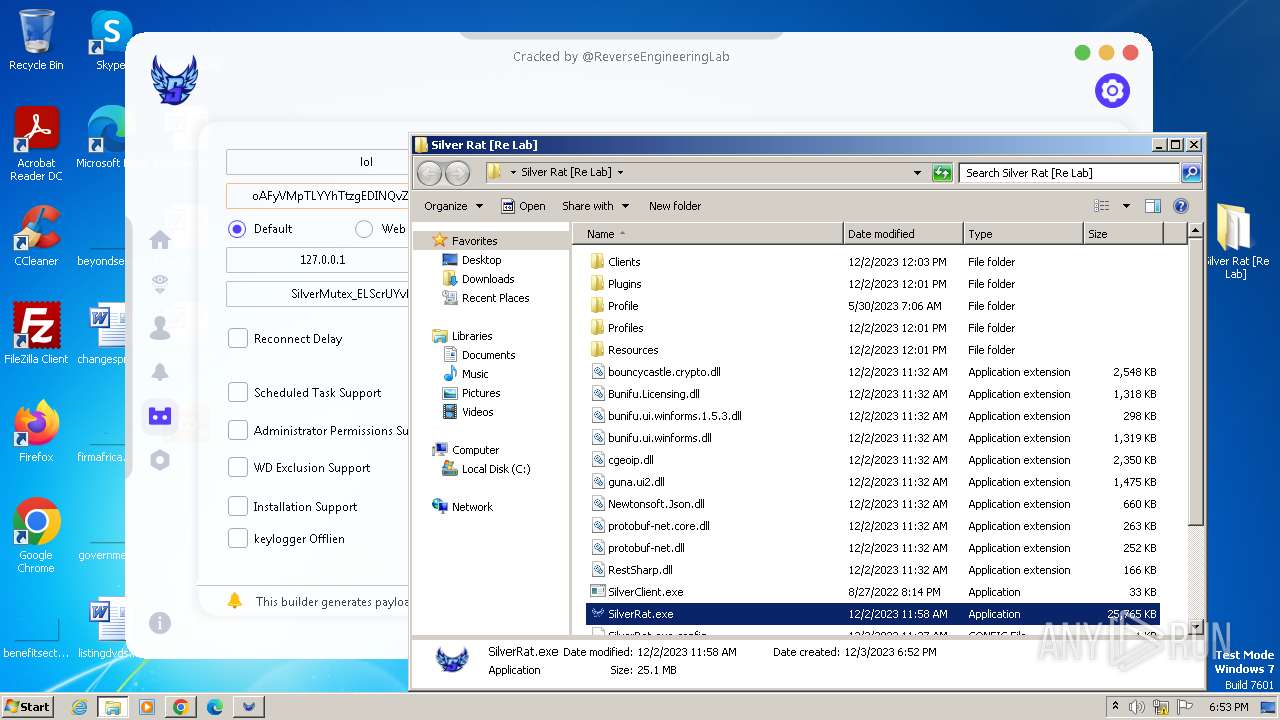
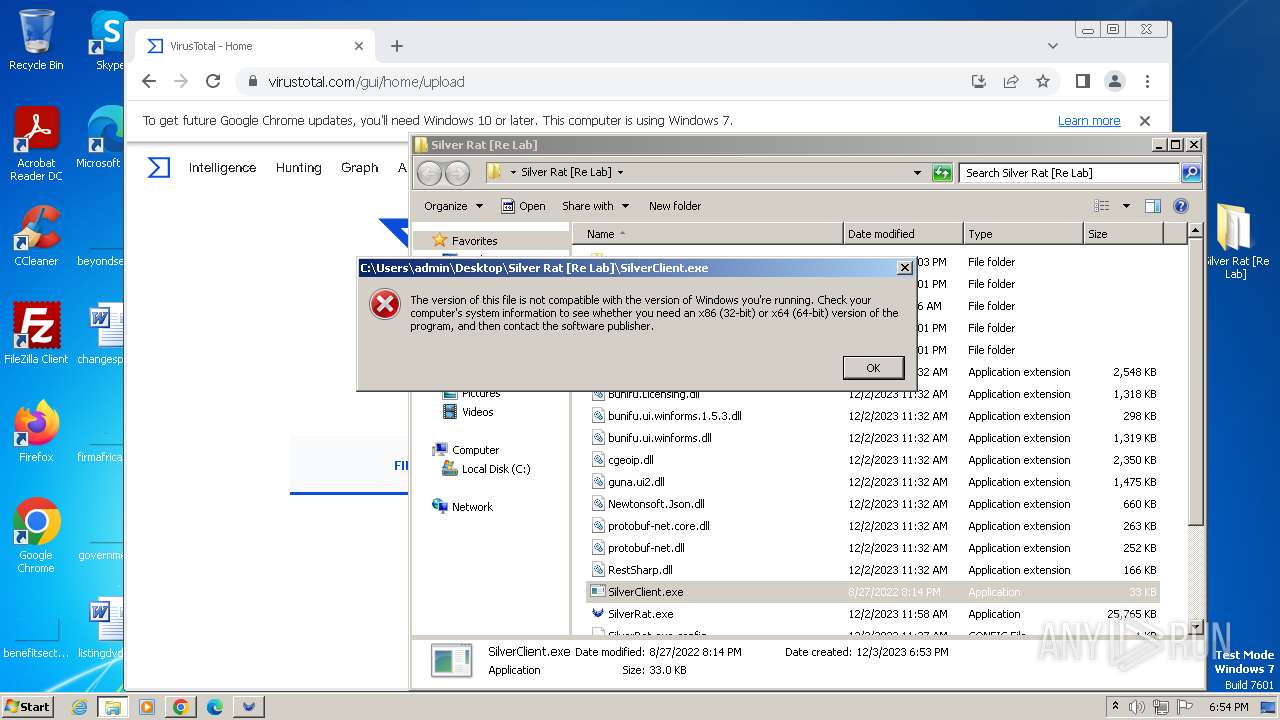
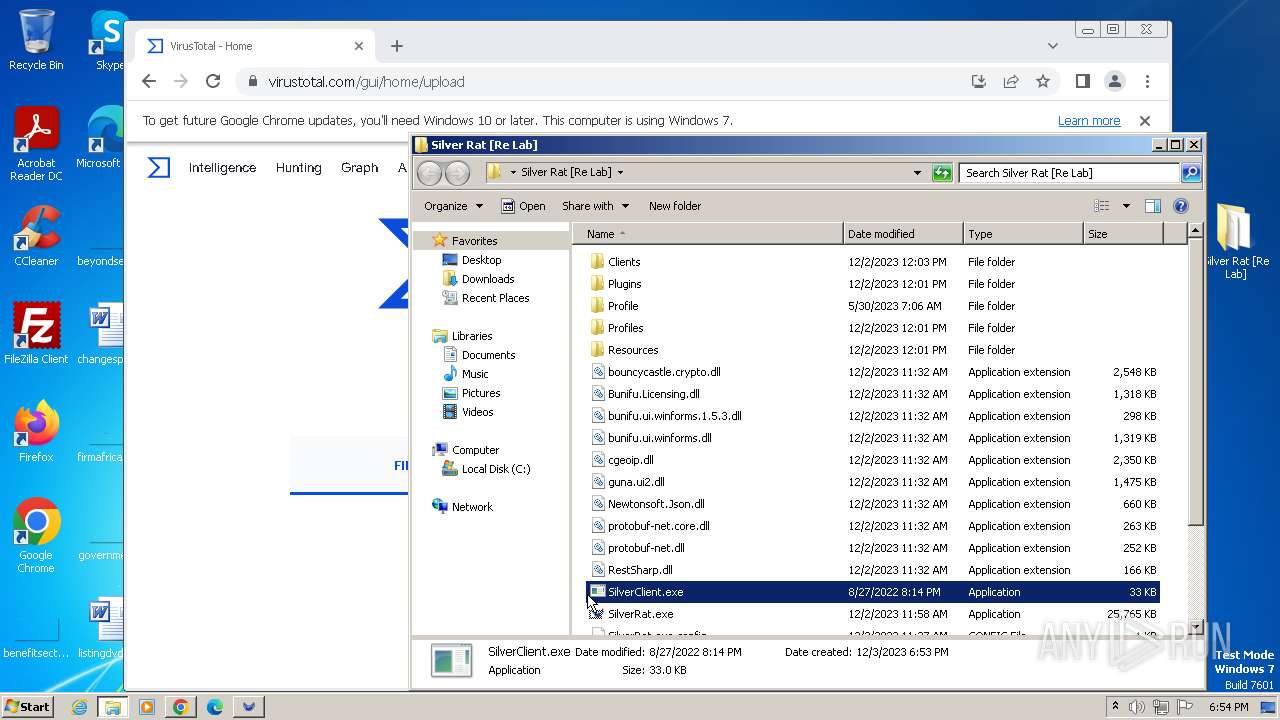
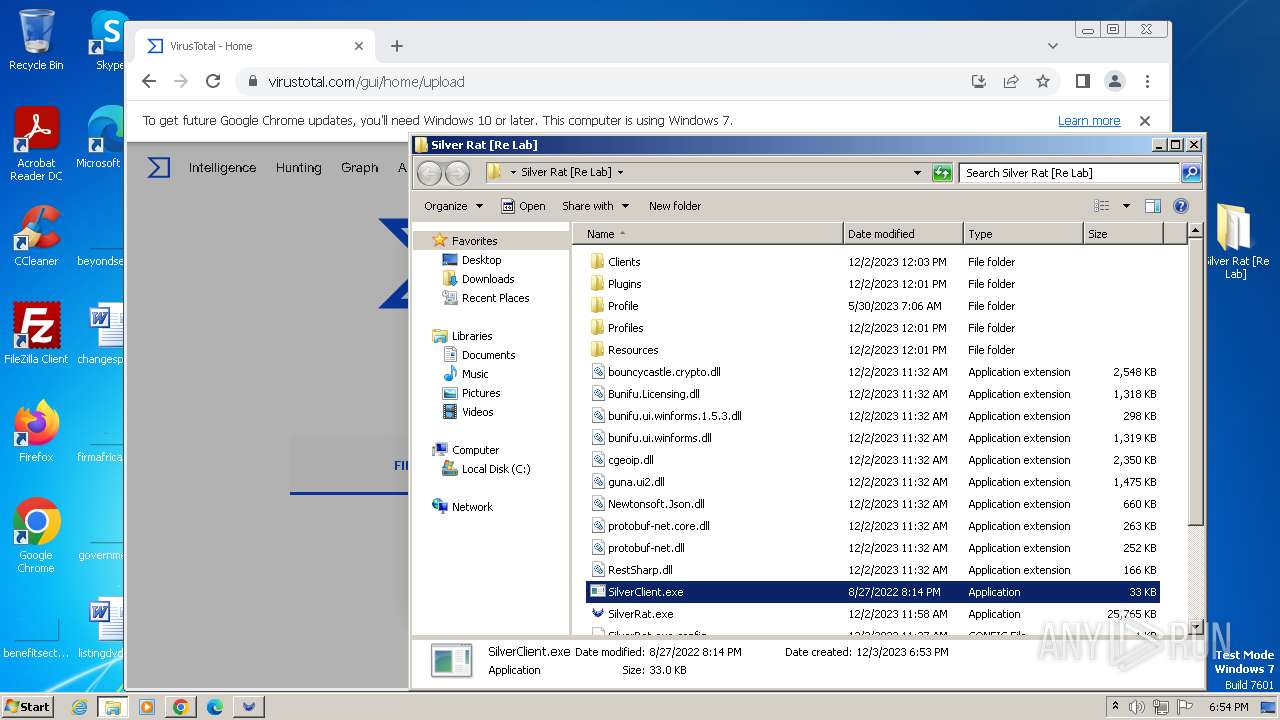
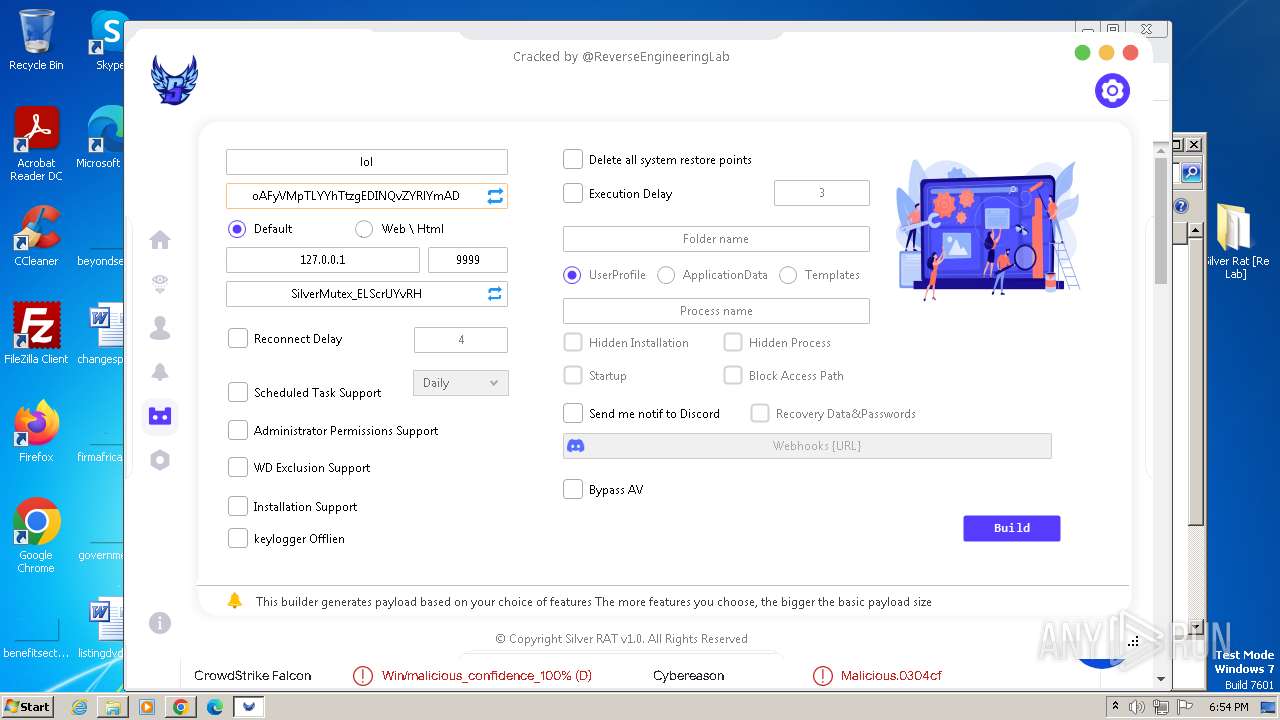
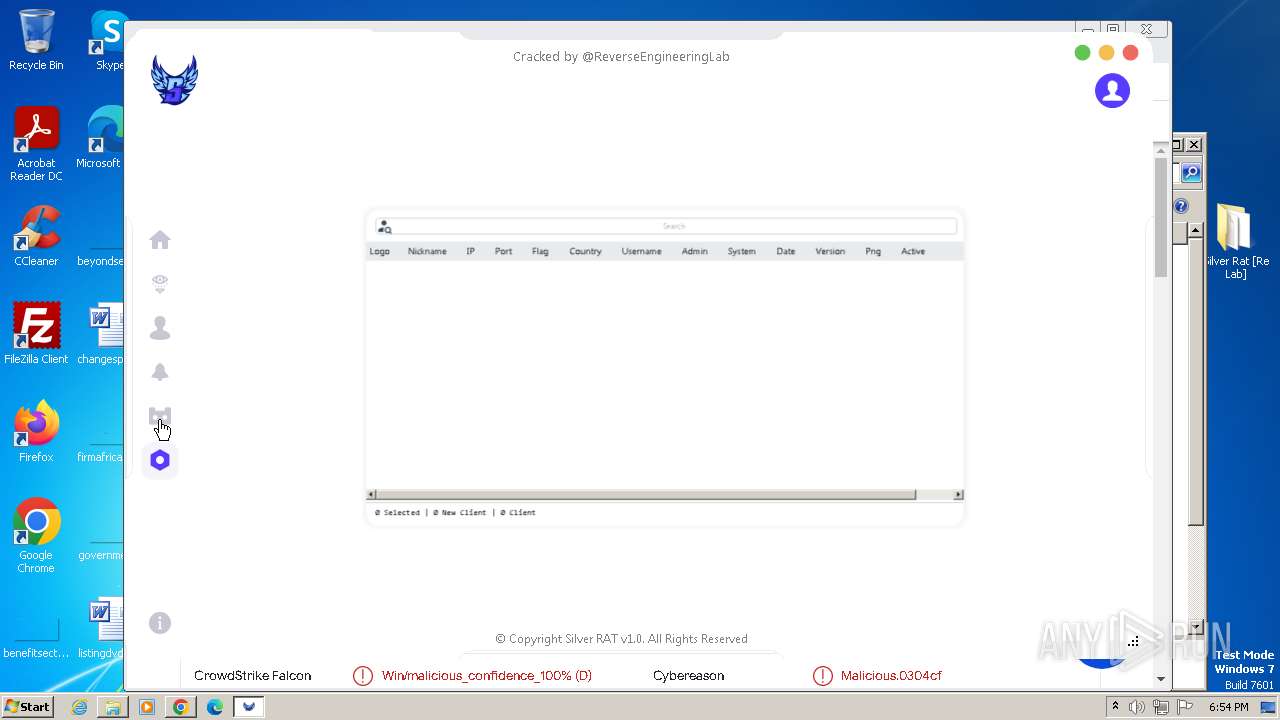
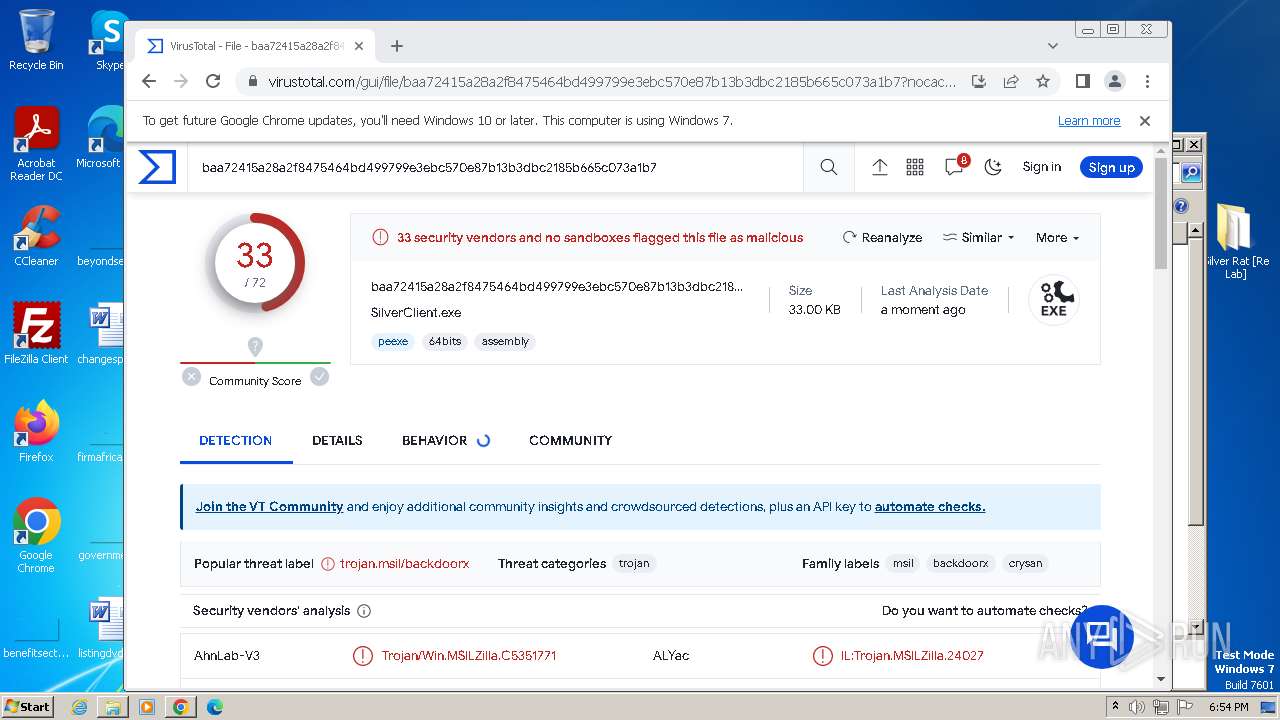
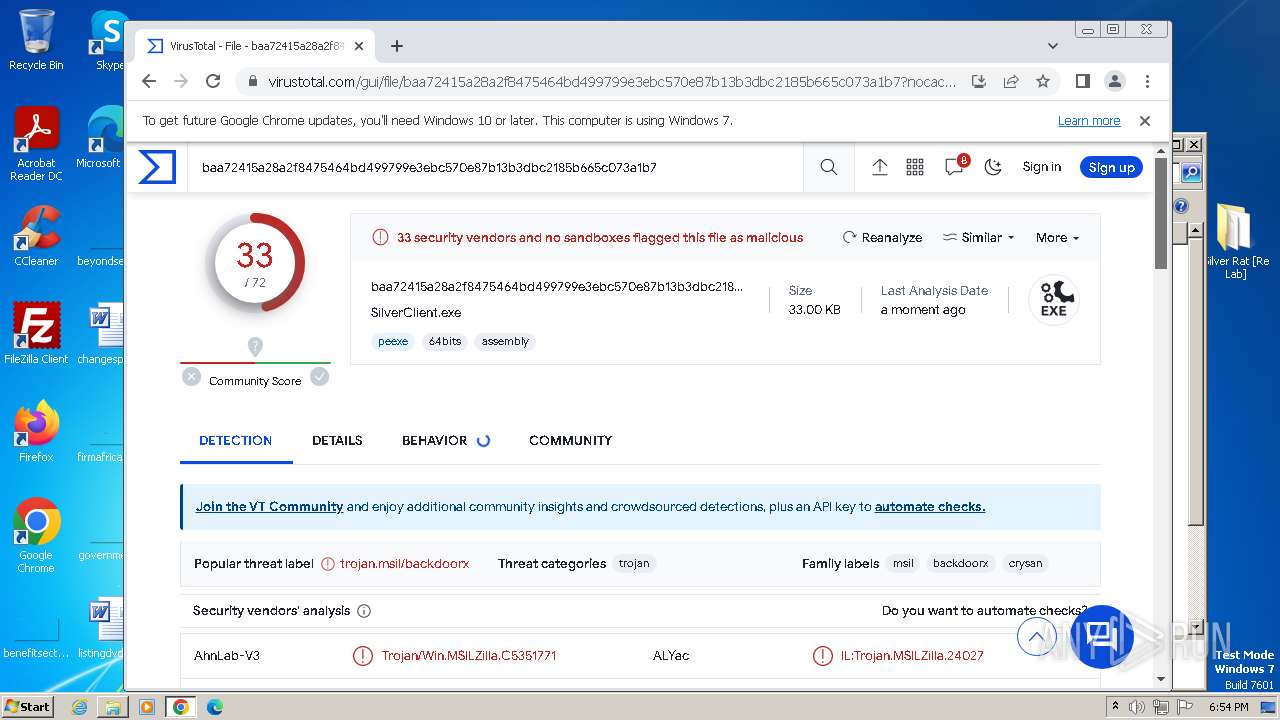
| File name: | Silver Rat [Re Lab].rar |
| Full analysis: | https://app.any.run/tasks/ca5a749a-6964-4399-9bba-5be78f848da5 |
| Verdict: | Malicious activity |
| Analysis date: | December 03, 2023, 18:52:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | BC071020AF8ADD654767B458CD0374E4 |
| SHA1: | F37E4A3B270CFB7A32577897ADF5538B5CFCD155 |
| SHA256: | 52322392520984112218F598836DBA6632AEB87494694E931C6EEC2DB576E493 |
| SSDEEP: | 98304:j+qIBOaHcJ1QyIy8ngNCEBdkNjr5i3wT1P2jbDhBicCPMwBUOXsvccjvfaM9lEpR:ecNg2DpCjXtaWJjS+ |
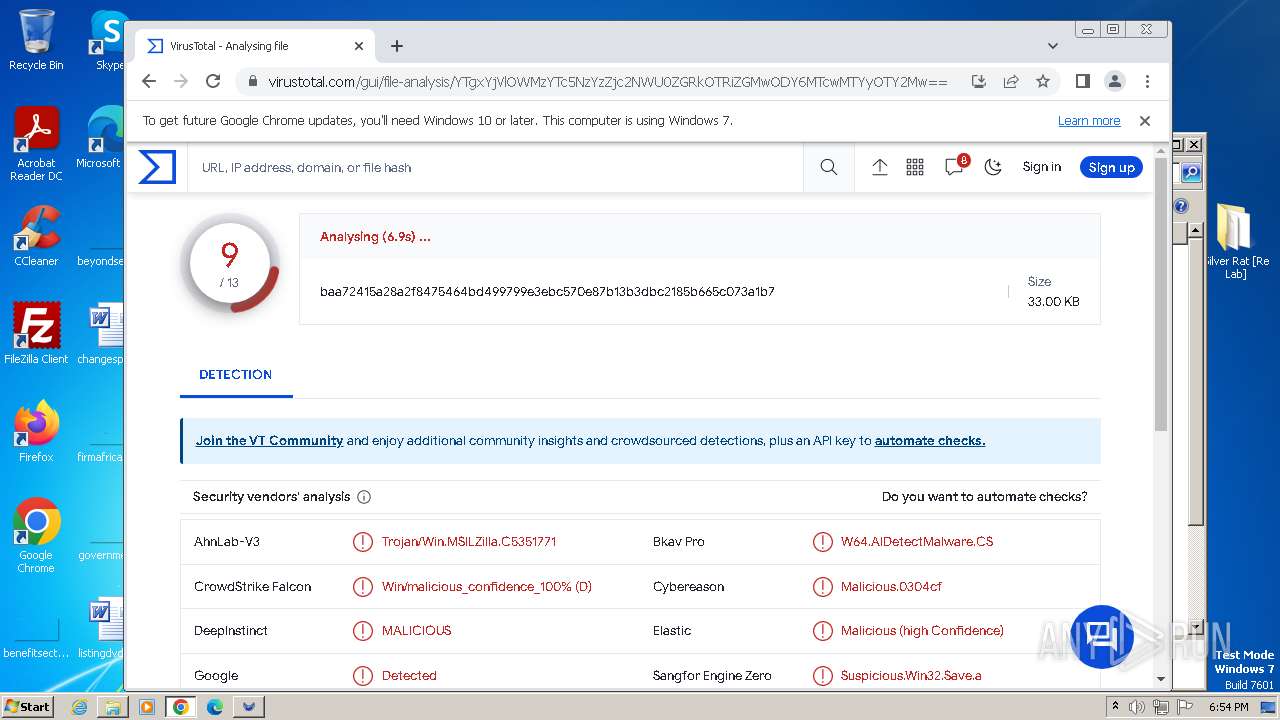
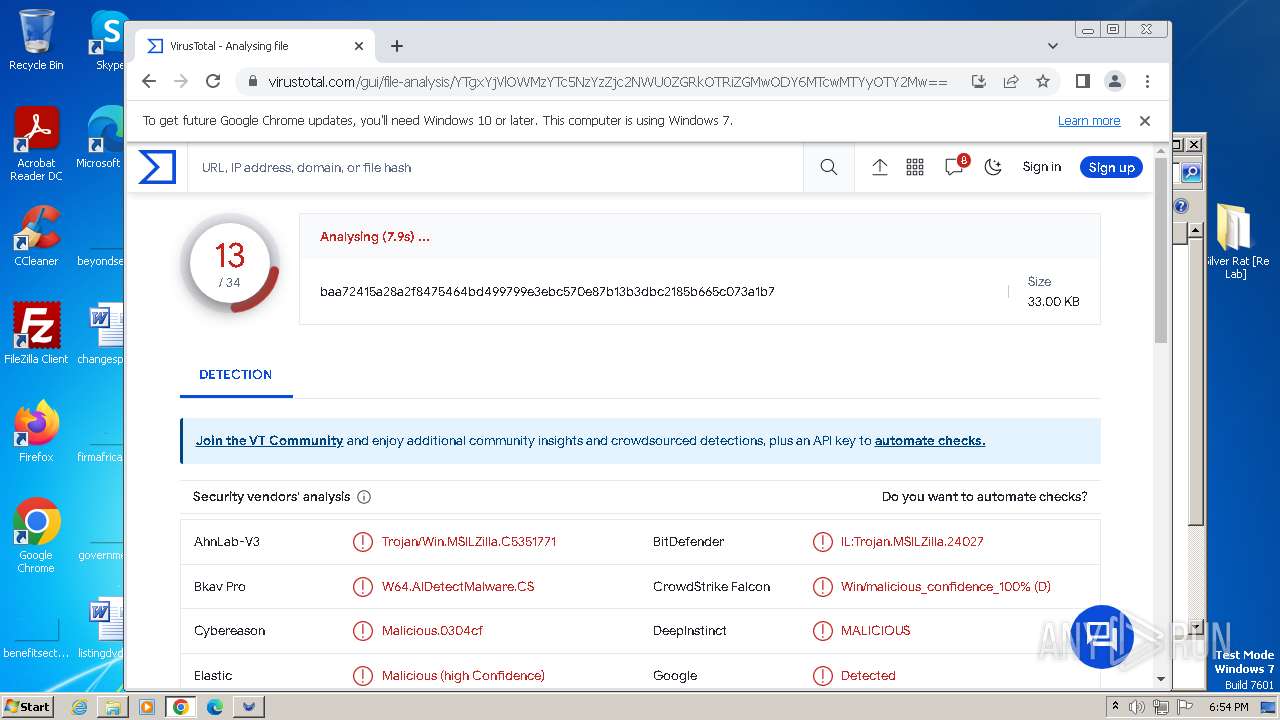
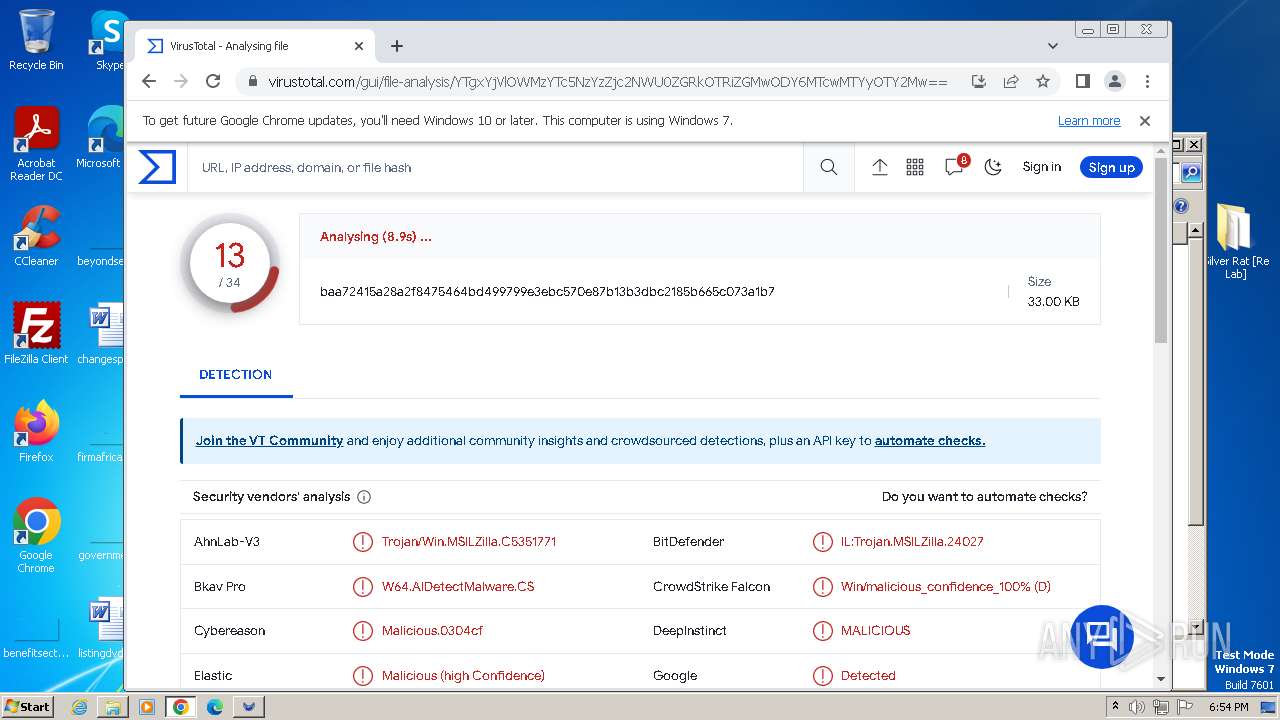
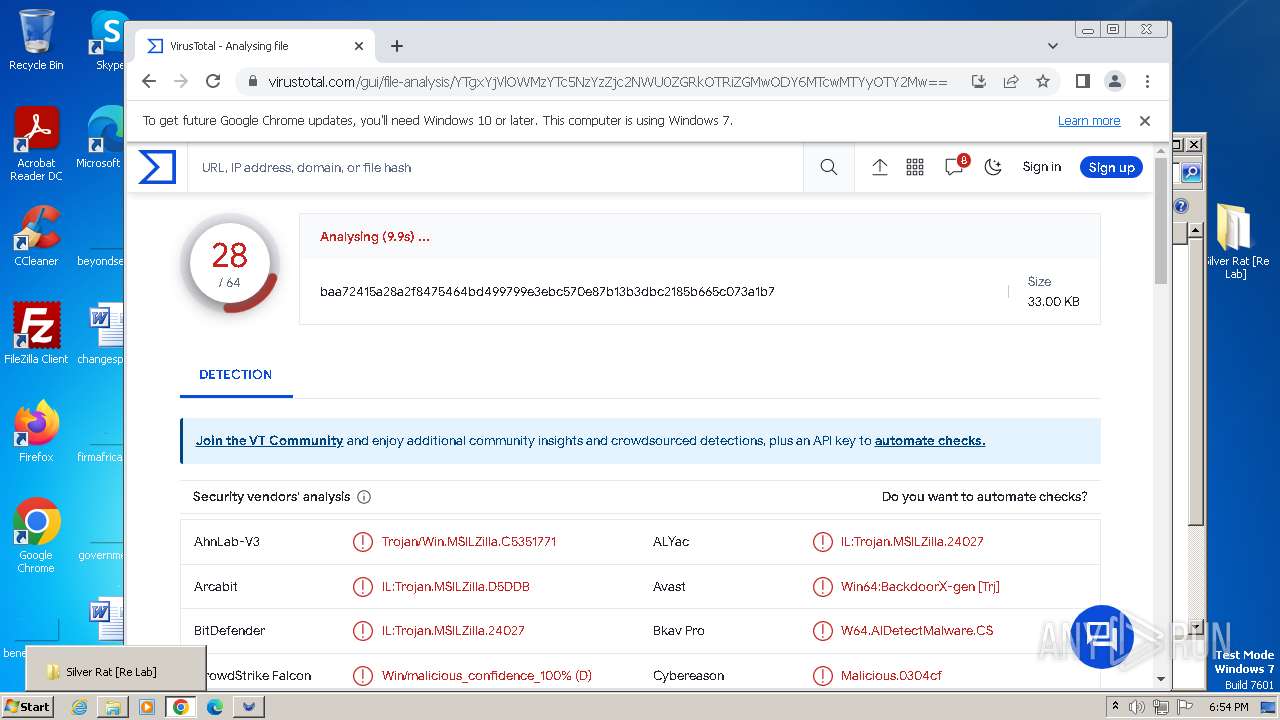
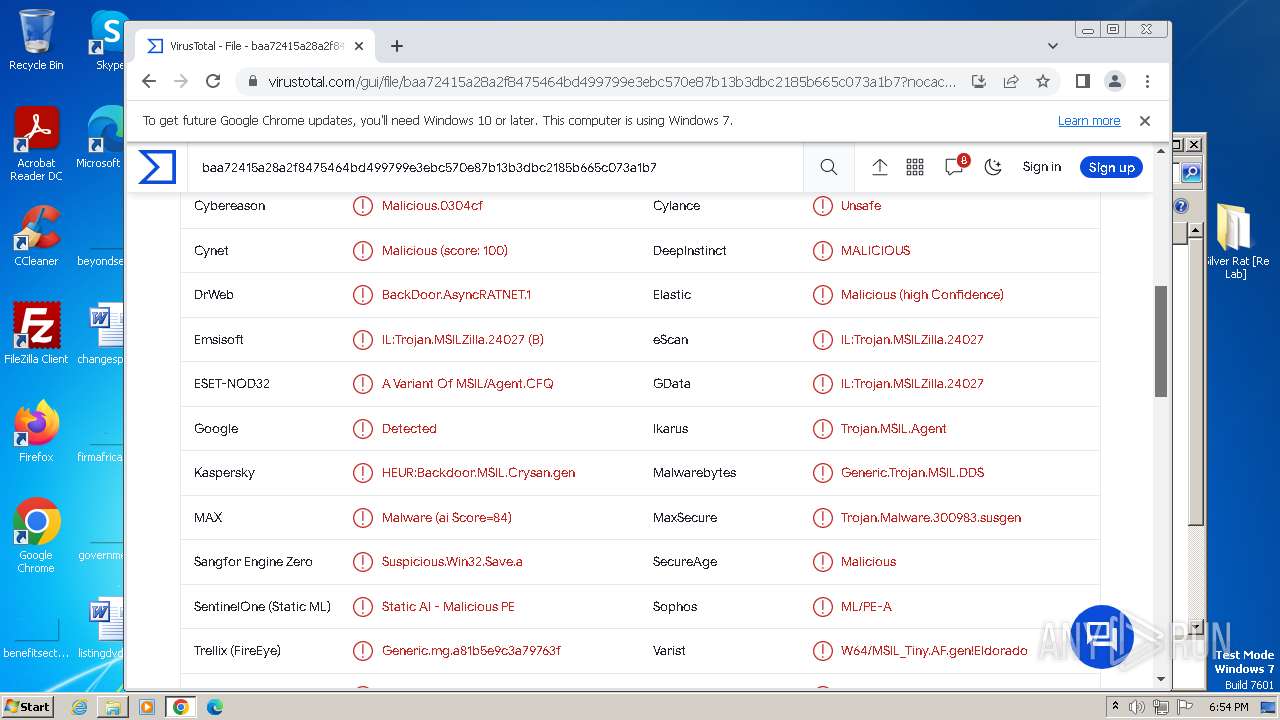
MALICIOUS
Starts Visual C# compiler
- SilverRat.exe (PID: 2920)
Drops the executable file immediately after the start
- csc.exe (PID: 3880)
SUSPICIOUS
Reads the Internet Settings
- SilverRat.exe (PID: 2920)
Uses .NET C# to load dll
- SilverRat.exe (PID: 2920)
Reads Internet Explorer settings
- SilverRat.exe (PID: 2920)
Process drops legitimate windows executable
- WinRAR.exe (PID: 564)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 564)
Reads the computer name
- SilverRat.exe (PID: 2920)
- wmpnscfg.exe (PID: 952)
Reads the machine GUID from the registry
- SilverRat.exe (PID: 2920)
- cvtres.exe (PID: 3388)
- csc.exe (PID: 3880)
Reads Environment values
- SilverRat.exe (PID: 2920)
Manual execution by a user
- SilverRat.exe (PID: 2920)
- wmpnscfg.exe (PID: 952)
- chrome.exe (PID: 2072)
Creates files or folders in the user directory
- SilverRat.exe (PID: 2920)
Checks supported languages
- csc.exe (PID: 3880)
- cvtres.exe (PID: 3388)
- wmpnscfg.exe (PID: 952)
- SilverRat.exe (PID: 2920)
Create files in a temporary directory
- cvtres.exe (PID: 3388)
- SilverRat.exe (PID: 2920)
Application launched itself
- chrome.exe (PID: 2072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
65
Monitored processes
25
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Silver Rat [Re Lab].rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=3516 --field-trial-handle=1220,i,2389276403844663328,2839971787345474502,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=784 --field-trial-handle=1220,i,2389276403844663328,2839971787345474502,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1248 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3556 --field-trial-handle=1220,i,2389276403844663328,2839971787345474502,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1416 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=2292 --field-trial-handle=1220,i,2389276403844663328,2839971787345474502,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3080 --field-trial-handle=1220,i,2389276403844663328,2839971787345474502,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2080 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1032 --field-trial-handle=1220,i,2389276403844663328,2839971787345474502,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=2236 --field-trial-handle=1220,i,2389276403844663328,2839971787345474502,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
7 167
Read events
7 053
Write events
111
Delete events
3
Modification events
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
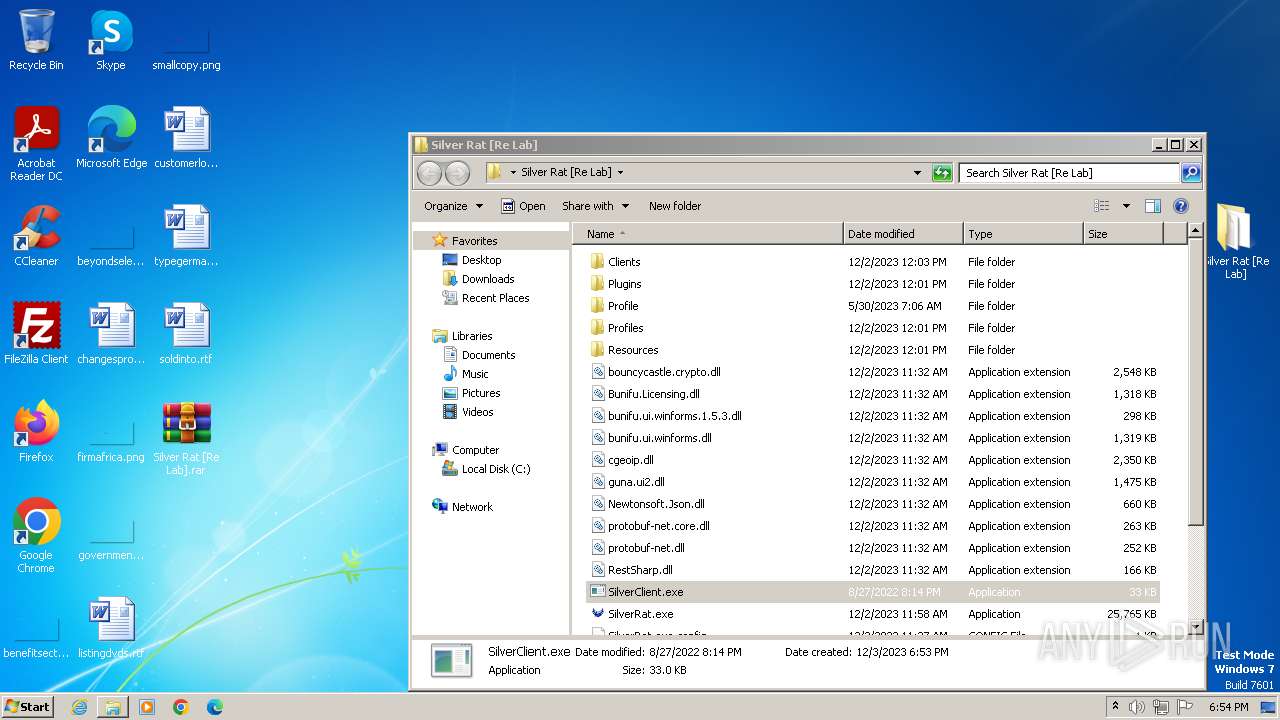
Executable files
19
Suspicious files
199
Text files
41
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb564.2462\Silver Rat [Re Lab]\Plugins\HBrowser.dll | binary | |
MD5:CE1D9F8C498CD8C5EE38FA94DF4B4907 | SHA256:55B5EFE0A09CB5CB79308874E2E5D25C895F995754BBF960CE9A403207CE3ABD | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb564.2462\Silver Rat [Re Lab]\bunifu.ui.winforms.1.5.3.dll | executable | |
MD5:C1D51A0E747C9D6156410CB3C5B97A60 | SHA256:6937052B86BC251BE510B110E08FC5089D3BD687CE2333A85EA6D5C2C09B437A | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb564.2462\Silver Rat [Re Lab]\Plugins\Options.dll | binary | |
MD5:FF88D61DC7ADC644D79B0F898059A7B1 | SHA256:3FD7B67E56B40CAF53AA9B2DF102967F7E2AAB0BB4BF90EA769EA725C0498657 | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb564.2462\Silver Rat [Re Lab]\Plugins\HVNC.dll | binary | |
MD5:3D07031E76978680240E80CC54451AD4 | SHA256:44CB17F3B048BA2C7653409B0DEC7C94EB86D2CF0322AC79CE6764D5B8DF1549 | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb564.2462\Silver Rat [Re Lab]\Plugins\Passwords.dll | binary | |
MD5:67DF2A509DF555BBBB04264D9177C4C9 | SHA256:31805C53DCD4DF47675401E2F286026492A4D2C9FFB13BF5293E8955D5EC96D1 | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb564.2462\Silver Rat [Re Lab]\guna.ui2.dll | executable | |
MD5:ACEC68D05E0B9B6C34A24DA530DC07B2 | SHA256:BF72939922AFA2CD17071F5170B4A82D05BCEB1FC33CE29CDFBC68DBB97F0277 | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb564.2462\Silver Rat [Re Lab]\Plugins\Chat.dll | binary | |
MD5:736292DD81AD93BFF84C28CE5DE02385 | SHA256:0C83898F29762A4E3650FC5F5A8A3C3114D06DA8F6A3FB2FA8B990A36716D6BD | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb564.2462\Silver Rat [Re Lab]\Plugins\HApps.dll | binary | |
MD5:A7C3B329AB9F4E20ED40C78B2AC36864 | SHA256:D922C1762640F37A503EB116627A732290AE38B52F9B33437FFEE608F7853A28 | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb564.2462\Silver Rat [Re Lab]\Plugins\OptionsForm.dll.config | xml | |
MD5:A78FA19B73BAA4B9BB1D29D22DFBEA83 | SHA256:C53F33A5C3A7DFA005F62BC9D81AE8D6E5EB019463BD2986C32CA00CE9404F1A | |||
| 564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb564.2462\Silver Rat [Re Lab]\Plugins\Ransom.dll | binary | |
MD5:47CED016511C0EDCA8AF7E371ED50136 | SHA256:D47F10F19FF148464747BF7E38F7FB44C1D99569D4A9B31EEE731ABACD540A2F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
39
DNS requests
47
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 5.83 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 10.3 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 8.83 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2072 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4040 | chrome.exe | 142.250.186.131:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
4040 | chrome.exe | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | unknown |
4040 | chrome.exe | 172.217.18.100:443 | www.google.com | GOOGLE | US | whitelisted |
4040 | chrome.exe | 172.217.23.110:443 | apis.google.com | GOOGLE | US | whitelisted |
4040 | chrome.exe | 142.250.185.227:443 | update.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
www.virustotal.com |
| whitelisted |
www.recaptcha.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
Process | Message |
|---|---|
SilverRat.exe | Animation started.
|
SilverRat.exe | Animation stopped.
|
SilverRat.exe | Wait timer started.
|
SilverRat.exe | Wait timer elapsed.
|
SilverRat.exe | Animation started.
|
SilverRat.exe | Animation stopped.
|
SilverRat.exe | Animation started.
|
SilverRat.exe | Wait timer started.
|
SilverRat.exe | Animation stopped.
|
SilverRat.exe | Animation started.
|