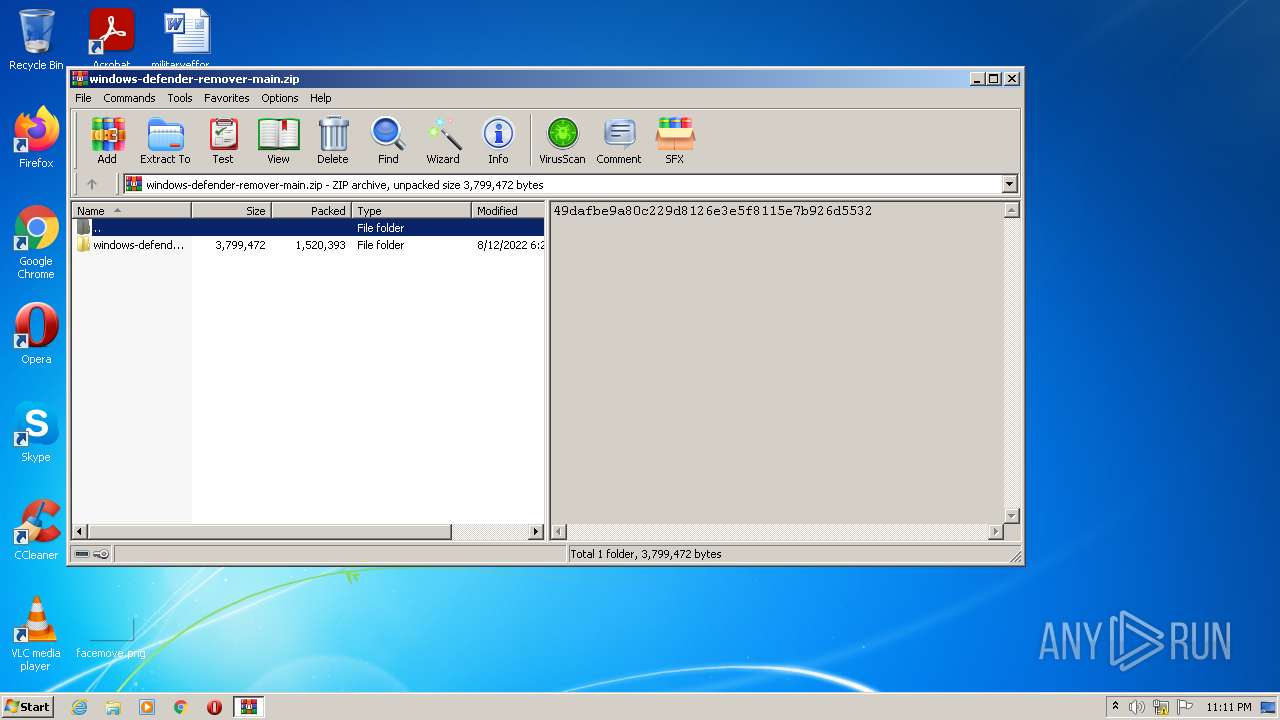
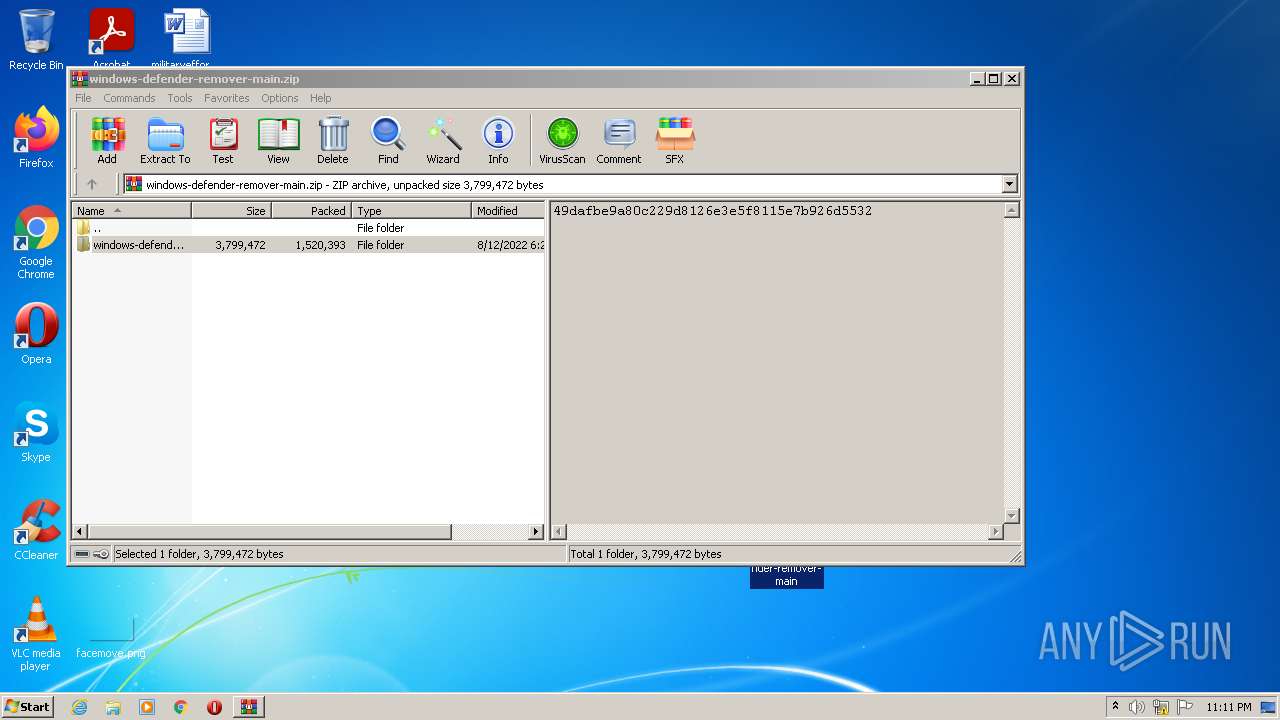
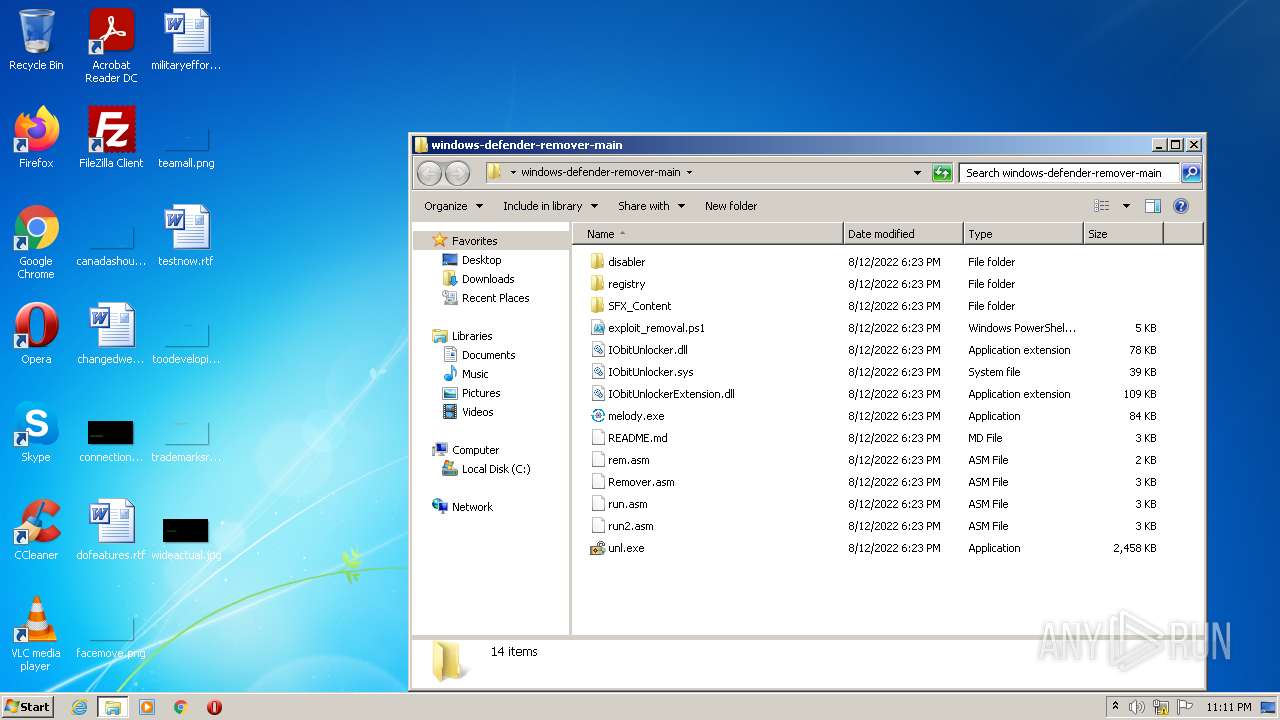
| File name: | windows-defender-remover-main.zip |
| Full analysis: | https://app.any.run/tasks/0cf89b8e-fdb6-4c1b-b861-471f9db560ce |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 22:11:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 30C49C1BBA1EF2A863CF09C4CB7191FA |
| SHA1: | 04F4E72C213C5600F8CB08269CCD882F9AE3FE65 |
| SHA256: | 521C72BBE40AC284D236B5CD8D8B68663797E8CC1421E8039440C28EFAE3A1A1 |
| SSDEEP: | 24576:972TDMMAr37TyY/Wb6aQBGWdddgAt6mRAABX0PRRrvJLckK7YYzrJPsimEn9J7fA:Z2TDde3qQaQeA0aTBX0pxNckK7x2BE9e |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3052)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3836)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3052)
Reads the computer name
- WinRAR.exe (PID: 3052)
Checks supported languages
- WinRAR.exe (PID: 3052)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3052)
Reads default file associations for system extensions
- SearchProtocolHost.exe (PID: 3836)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | windows-defender-remover-main/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2022:08:12 10:23:04 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
35
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3052 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\windows-defender-remover-main.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3836 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
1 723
Read events
1 697
Write events
26
Delete events
0
Modification events
| (PID) Process: | (3052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3052) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\windows-defender-remover-main.zip | |||
| (PID) Process: | (3052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
0
Text files
124
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3052.43315\windows-defender-remover-main\README.md | text | |
MD5:— | SHA256:— | |||
| 3052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3052.43315\windows-defender-remover-main\SFX_Content\Asm\x86\7zAsm.asm | text | |
MD5:— | SHA256:— | |||
| 3052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3052.43315\windows-defender-remover-main\Remover.asm | text | |
MD5:— | SHA256:— | |||
| 3052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3052.43315\windows-defender-remover-main\IObitUnlocker.dll | executable | |
MD5:5DD95FE265D754DA1DA874BB738B3E02 | SHA256:B3E02EEB8A6D9BA420DD4258929BFB5FB9DD25E0C80D913E3D082FCE64C65D5C | |||
| 3052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3052.43315\windows-defender-remover-main\IObitUnlocker.sys | executable | |
MD5:85DEF55323CFC4A04A270127A20F4D2C | SHA256:2BA404C50684D59B701959A1732617DEC6A6A25C8005294C0D2B3822B38479A4 | |||
| 3052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3052.43315\windows-defender-remover-main\SFX_Content\Asm\x86\7zCrcOpt.asm | text | |
MD5:412CCDDDF83FD5761AB1F68C2A82A3B4 | SHA256:9055ED868C506DE27D6E5D9B888C21E6596F37E230D9E4B5CD70B392B19EF870 | |||
| 3052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3052.43315\windows-defender-remover-main\SFX_Content\C\AesOpt.c | text | |
MD5:— | SHA256:— | |||
| 3052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3052.43315\windows-defender-remover-main\SFX_Content\C\7zTypes.h | text | |
MD5:— | SHA256:— | |||
| 3052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3052.43315\windows-defender-remover-main\SFX_Content\C\7zVersion.h | text | |
MD5:— | SHA256:— | |||
| 3052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3052.43315\windows-defender-remover-main\SFX_Content\C\Aes.c | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report