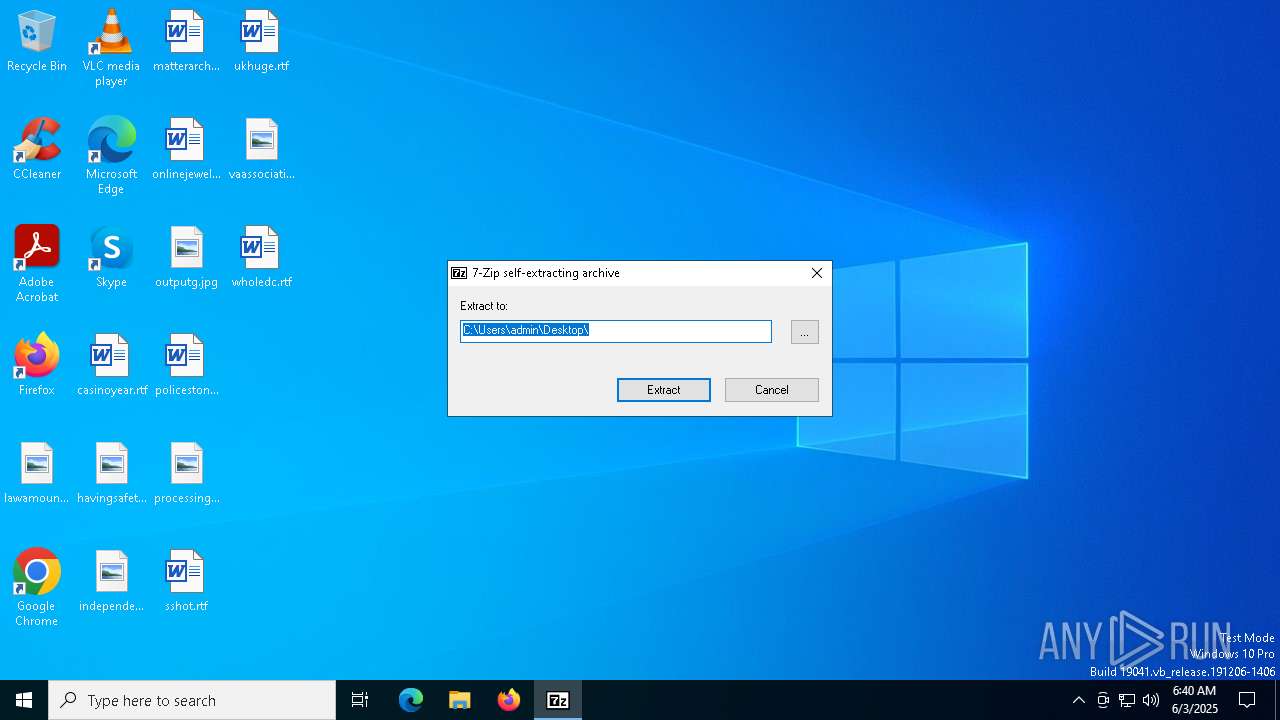
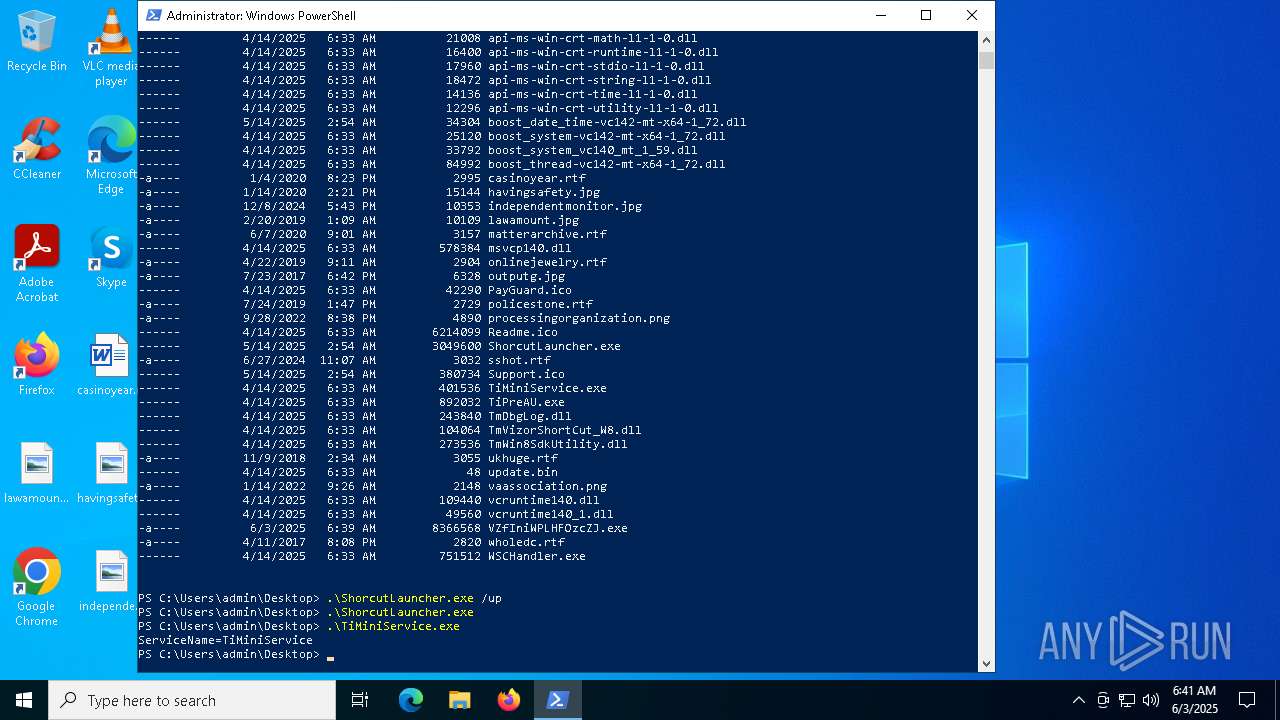
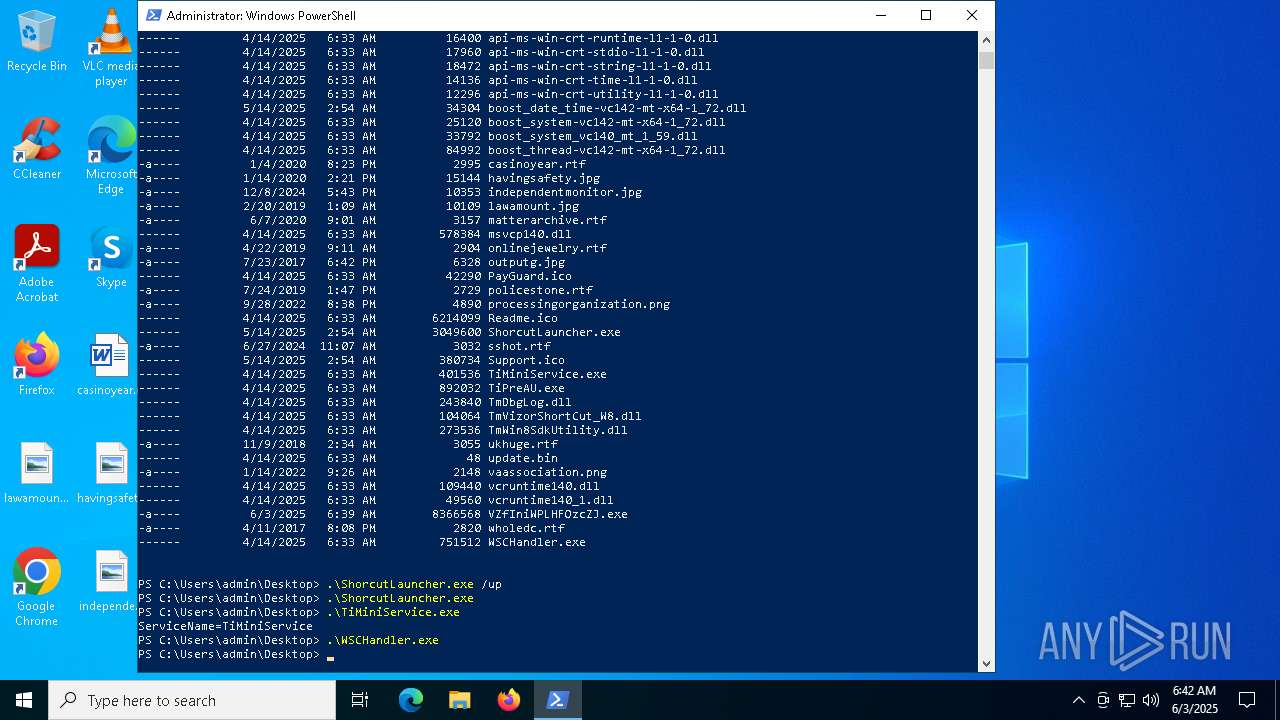
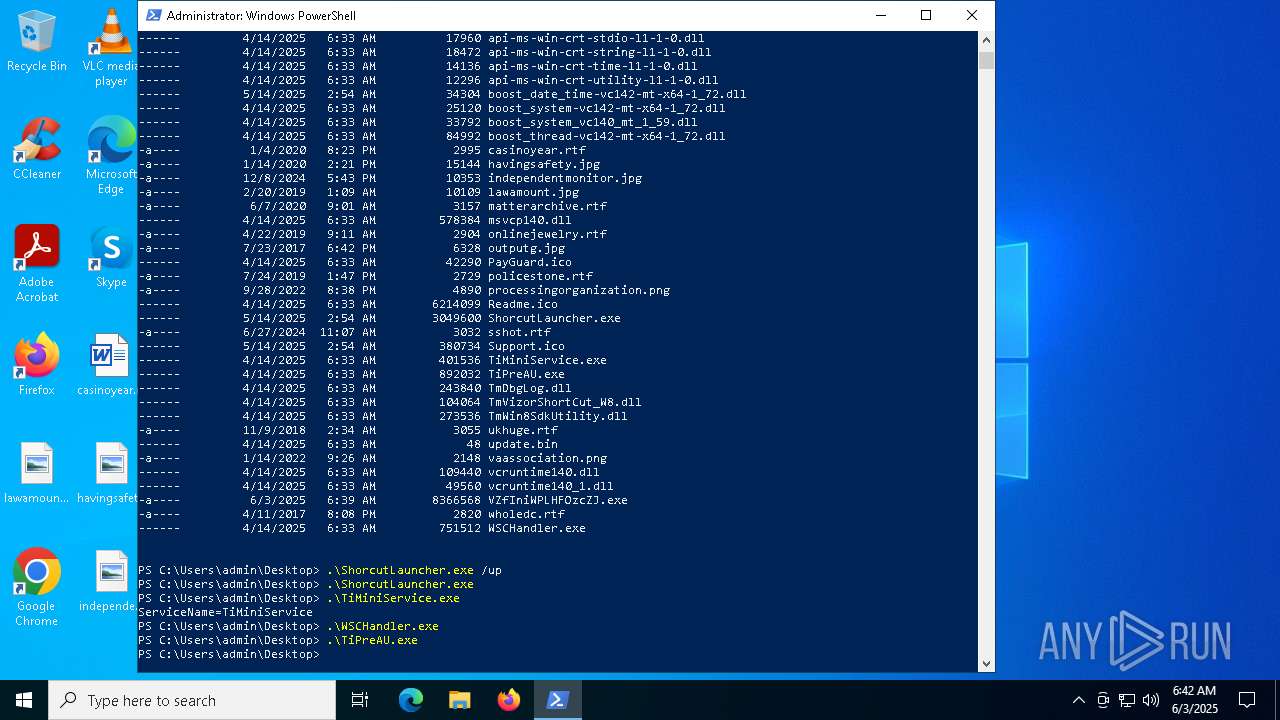
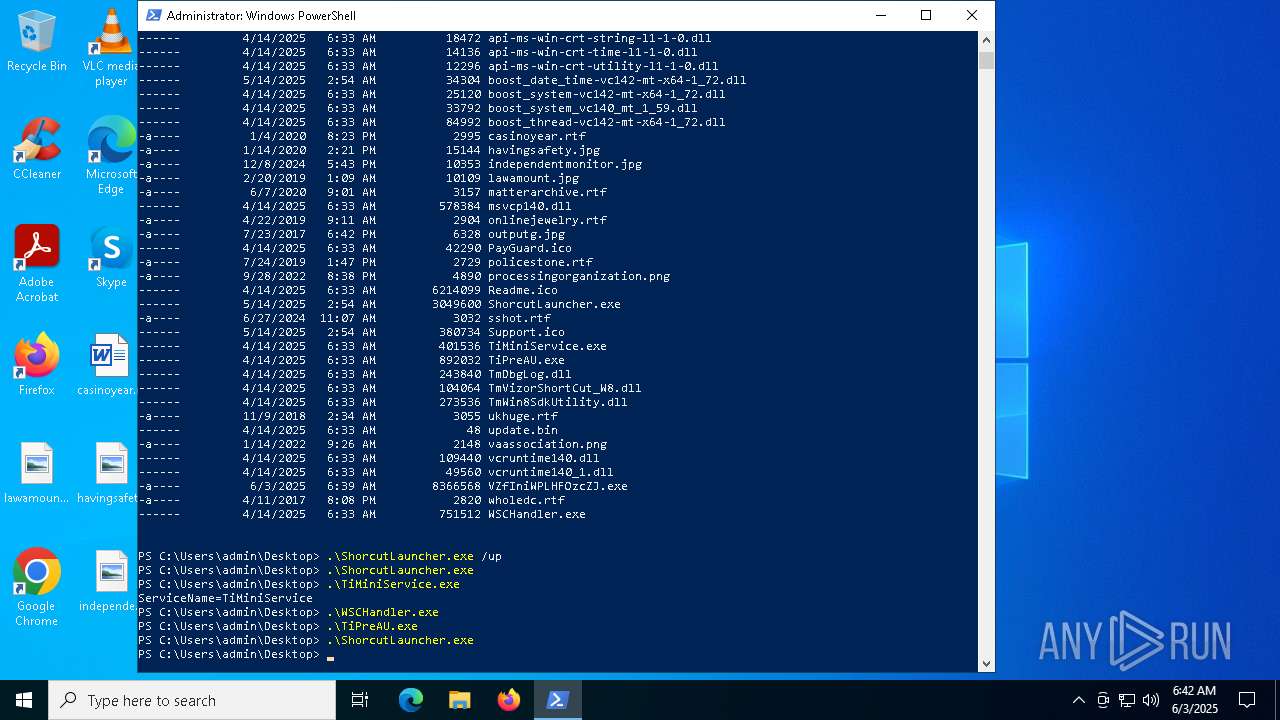
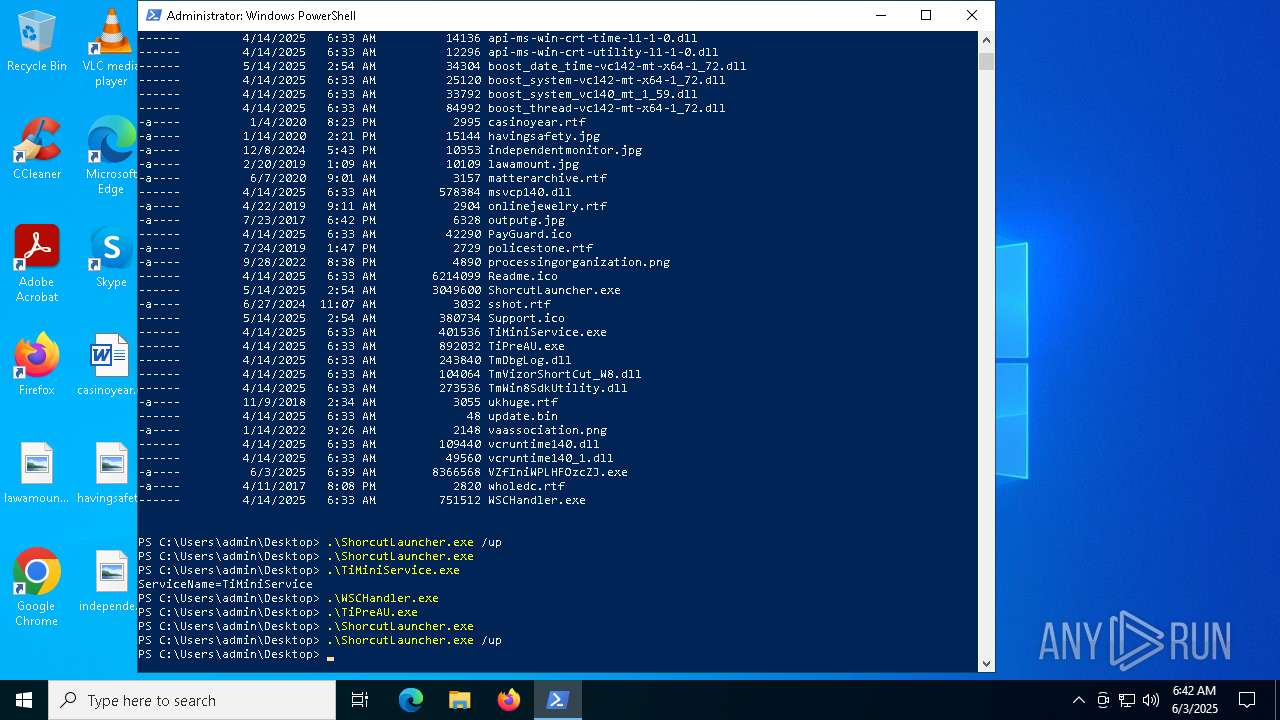
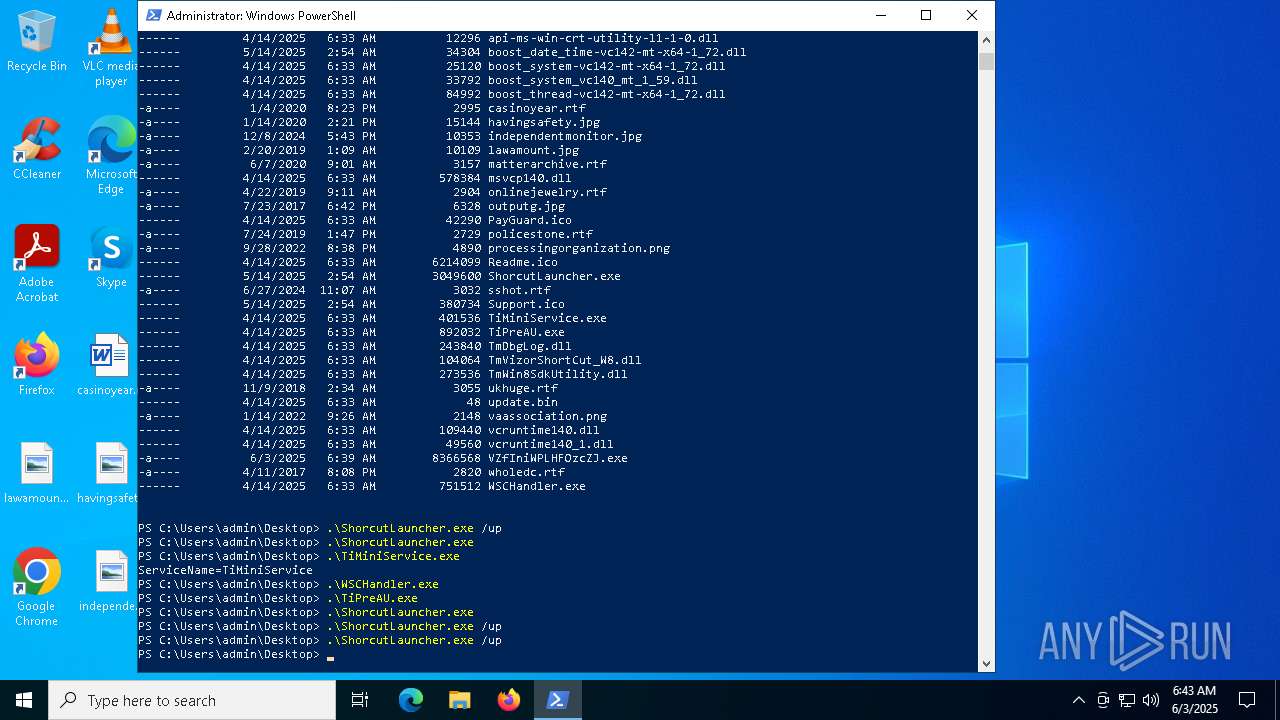
| File name: | VZfIniWPLHFOzcZJ.exe |
| Full analysis: | https://app.any.run/tasks/d59e7328-96ab-4179-ad33-81bb0a8f8163 |
| Verdict: | Malicious activity |
| Analysis date: | June 03, 2025, 06:39:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | CBDA073177BD7E400F4C456B8D159A73 |
| SHA1: | 0D8EDC3CD0492E80AC9DAF3A5CB7112CAC55F545 |
| SHA256: | 521513EFF6F612917CC606F34A7B2E2B735878911F19D666B6594F3C8FE36957 |
| SSDEEP: | 98304:RG+mP4RSYOgSVyF/ZalYw2ntih+Y/NITA75pvkbVwhtTeuqkB+Ng5iGus0mqhFDo:vBbwxpX+Ne9qOIVV+A6 |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- VZfIniWPLHFOzcZJ.exe (PID: 6584)
Executable content was dropped or overwritten
- VZfIniWPLHFOzcZJ.exe (PID: 6584)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 5064)
- WSCHandler.exe (PID: 7784)
Process drops legitimate windows executable
- VZfIniWPLHFOzcZJ.exe (PID: 6584)
Executes application which crashes
- ShorcutLauncher.exe (PID: 1660)
- ShorcutLauncher.exe (PID: 7556)
- WSCHandler.exe (PID: 7784)
- ShorcutLauncher.exe (PID: 5512)
- ShorcutLauncher.exe (PID: 2616)
- ShorcutLauncher.exe (PID: 240)
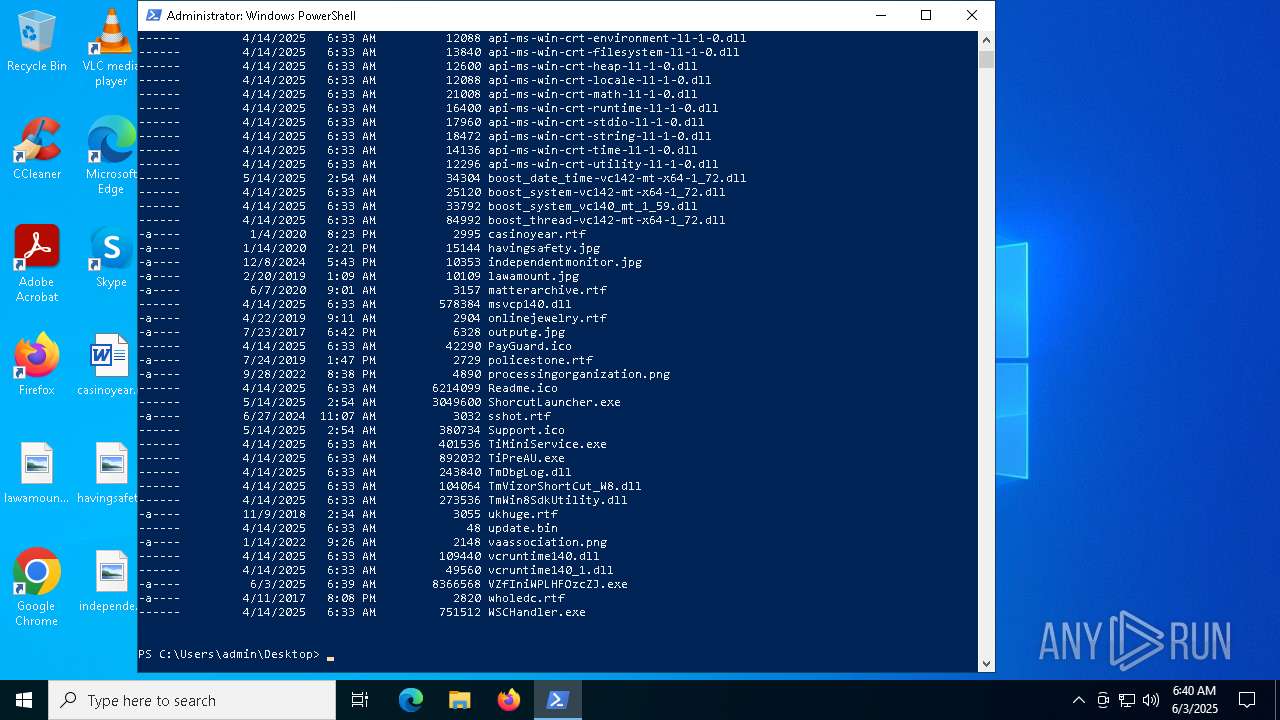
Drops 7-zip archiver for unpacking
- VZfIniWPLHFOzcZJ.exe (PID: 6584)
INFO
The sample compiled with english language support
- VZfIniWPLHFOzcZJ.exe (PID: 6584)
Checks supported languages
- VZfIniWPLHFOzcZJ.exe (PID: 6584)
- ShellExperienceHost.exe (PID: 5064)
- ShorcutLauncher.exe (PID: 1660)
- ShorcutLauncher.exe (PID: 7556)
- TiMiniService.exe (PID: 4724)
- WSCHandler.exe (PID: 7784)
- TiPreAU.exe (PID: 7316)
- ShorcutLauncher.exe (PID: 240)
- ShorcutLauncher.exe (PID: 5512)
- ShorcutLauncher.exe (PID: 2616)
Reads the computer name
- ShellExperienceHost.exe (PID: 5064)
- ShorcutLauncher.exe (PID: 1660)
- ShorcutLauncher.exe (PID: 7556)
- TiMiniService.exe (PID: 4724)
- WSCHandler.exe (PID: 7784)
- ShorcutLauncher.exe (PID: 2616)
- ShorcutLauncher.exe (PID: 5512)
- ShorcutLauncher.exe (PID: 240)
- VZfIniWPLHFOzcZJ.exe (PID: 6584)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 3140)
Manual execution by a user
- powershell.exe (PID: 3140)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3140)
Checks current location (POWERSHELL)
- powershell.exe (PID: 3140)
Creates files or folders in the user directory
- WerFault.exe (PID: 7820)
- WerFault.exe (PID: 7948)
- WerFault.exe (PID: 5772)
- WerFault.exe (PID: 3996)
- WerFault.exe (PID: 680)
- WerFault.exe (PID: 8000)
Reads Environment values
- TiMiniService.exe (PID: 4724)
- TiPreAU.exe (PID: 7316)
Reads the machine GUID from the registry
- WSCHandler.exe (PID: 7784)
Reads the software policy settings
- WSCHandler.exe (PID: 7784)
- slui.exe (PID: 6560)
Checks proxy server information
- slui.exe (PID: 6560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:11:29 18:00:00+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 174592 |
| InitializedDataSize: | 59904 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x284cc |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 24.9.0.0 |
| ProductVersionNumber: | 24.9.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov |
| FileDescription: | 7z SFX |
| FileVersion: | 24.09 |
| InternalName: | 7z.sfx |
| LegalCopyright: | Copyright (c) 1999-2024 Igor Pavlov |
| OriginalFileName: | 7z.sfx.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 24.09 |
Total processes
155
Monitored processes
19
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
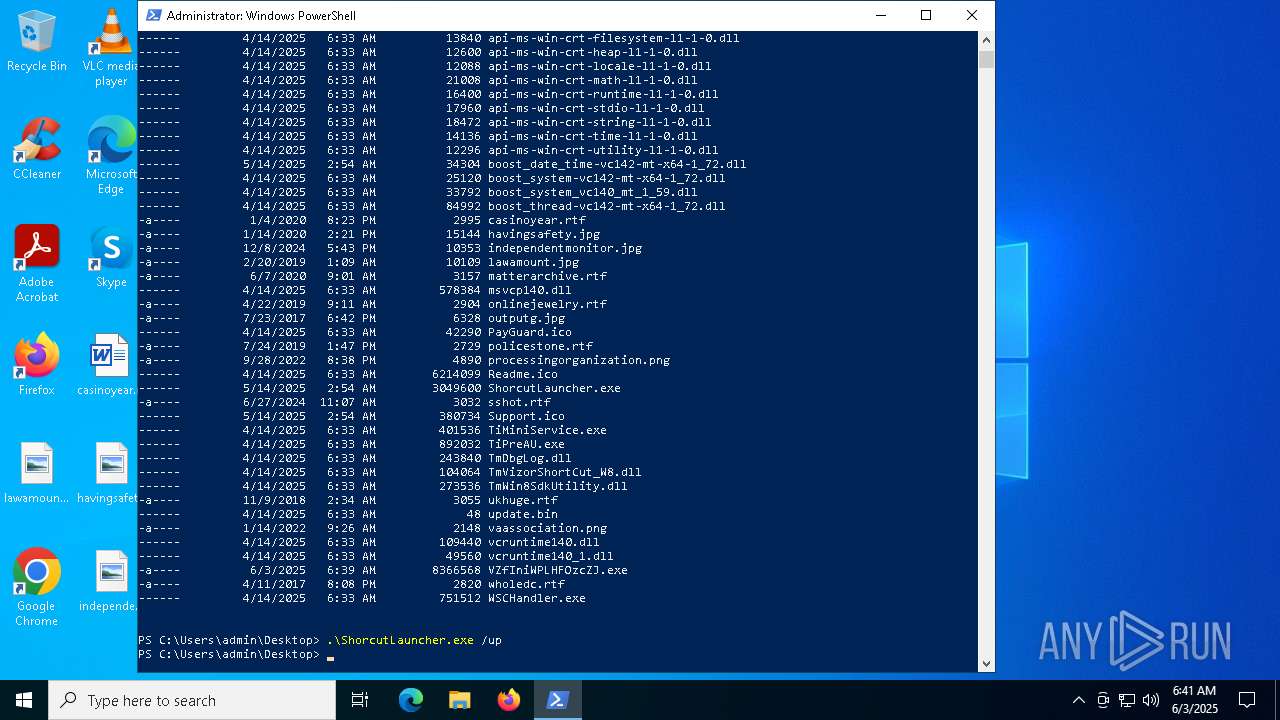
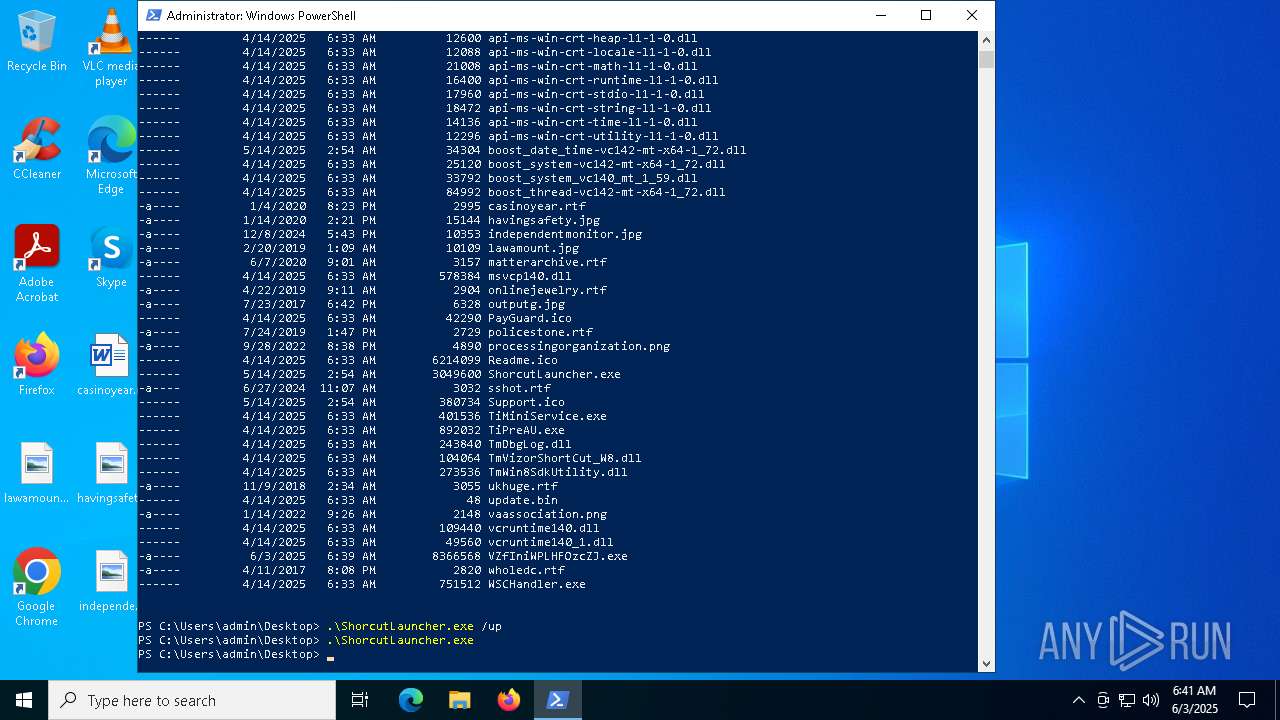
| 240 | "C:\Users\admin\Desktop\ShorcutLauncher.exe" /up | C:\Users\admin\Desktop\ShorcutLauncher.exe | powershell.exe | ||||||||||||
User: admin Company: Trend Micro Inc. Integrity Level: HIGH Description: Trend Micro Launcher Exit code: 3221225501 Version: 17.7.0.1903 Modules
| |||||||||||||||
| 680 | C:\WINDOWS\system32\WerFault.exe -u -p 240 -s 460 | C:\Windows\System32\WerFault.exe | — | ShorcutLauncher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\Desktop\ShorcutLauncher.exe" /up | C:\Users\admin\Desktop\ShorcutLauncher.exe | powershell.exe | ||||||||||||
User: admin Company: Trend Micro Inc. Integrity Level: HIGH Description: Trend Micro Launcher Exit code: 3221225501 Version: 17.7.0.1903 Modules
| |||||||||||||||
| 1680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | "C:\Users\admin\Desktop\ShorcutLauncher.exe" | C:\Users\admin\Desktop\ShorcutLauncher.exe | powershell.exe | ||||||||||||
User: admin Company: Trend Micro Inc. Integrity Level: HIGH Description: Trend Micro Launcher Exit code: 3221225501 Version: 17.7.0.1903 Modules
| |||||||||||||||
| 3140 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3996 | C:\WINDOWS\system32\WerFault.exe -u -p 5512 -s 464 | C:\Windows\System32\WerFault.exe | — | ShorcutLauncher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | "C:\Users\admin\Desktop\TiMiniService.exe" | C:\Users\admin\Desktop\TiMiniService.exe | — | powershell.exe | |||||||||||
User: admin Company: Trend Micro Inc. Integrity Level: HIGH Description: Trend Micro Internet Security mini-service Exit code: 0 Version: 17.7.0.1827 Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5512 | "C:\Users\admin\Desktop\ShorcutLauncher.exe" /up | C:\Users\admin\Desktop\ShorcutLauncher.exe | powershell.exe | ||||||||||||
User: admin Company: Trend Micro Inc. Integrity Level: HIGH Description: Trend Micro Launcher Exit code: 3221225501 Version: 17.7.0.1903 Modules
| |||||||||||||||
Total events
21 560
Read events
21 486
Write events
56
Delete events
18
Modification events
| (PID) Process: | (7820) WerFault.exe | Key: | \REGISTRY\A\{60451e81-65e1-c640-4262-692977751e4c}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (7820) WerFault.exe | Key: | \REGISTRY\A\{60451e81-65e1-c640-4262-692977751e4c}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7820) WerFault.exe | Key: | \REGISTRY\A\{60451e81-65e1-c640-4262-692977751e4c}\Root\InventoryApplicationFile\shorcutlauncher.|546dbd93c2cc9e59 |
| Operation: | write | Name: | ProgramId |
Value: 00065527cb76c23aadddf76f9d58a5141e6f00000904 | |||
| (PID) Process: | (7820) WerFault.exe | Key: | \REGISTRY\A\{60451e81-65e1-c640-4262-692977751e4c}\Root\InventoryApplicationFile\shorcutlauncher.|546dbd93c2cc9e59 |
| Operation: | write | Name: | FileId |
Value: 0000f3332a0afcb4ab08e59b9ba6b8765a222f45029a | |||
| (PID) Process: | (7820) WerFault.exe | Key: | \REGISTRY\A\{60451e81-65e1-c640-4262-692977751e4c}\Root\InventoryApplicationFile\shorcutlauncher.|546dbd93c2cc9e59 |
| Operation: | write | Name: | LowerCaseLongPath |
Value: c:\users\admin\desktop\shorcutlauncher.exe | |||
| (PID) Process: | (7820) WerFault.exe | Key: | \REGISTRY\A\{60451e81-65e1-c640-4262-692977751e4c}\Root\InventoryApplicationFile\shorcutlauncher.|546dbd93c2cc9e59 |
| Operation: | write | Name: | LongPathHash |
Value: shorcutlauncher.|546dbd93c2cc9e59 | |||
| (PID) Process: | (7820) WerFault.exe | Key: | \REGISTRY\A\{60451e81-65e1-c640-4262-692977751e4c}\Root\InventoryApplicationFile\shorcutlauncher.|546dbd93c2cc9e59 |
| Operation: | write | Name: | Name |
Value: ShorcutLauncher.exe | |||
| (PID) Process: | (7820) WerFault.exe | Key: | \REGISTRY\A\{60451e81-65e1-c640-4262-692977751e4c}\Root\InventoryApplicationFile\shorcutlauncher.|546dbd93c2cc9e59 |
| Operation: | write | Name: | OriginalFileName |
Value: shorcutlauncher.exe | |||
| (PID) Process: | (7820) WerFault.exe | Key: | \REGISTRY\A\{60451e81-65e1-c640-4262-692977751e4c}\Root\InventoryApplicationFile\shorcutlauncher.|546dbd93c2cc9e59 |
| Operation: | write | Name: | Publisher |
Value: trend micro inc. | |||
| (PID) Process: | (7820) WerFault.exe | Key: | \REGISTRY\A\{60451e81-65e1-c640-4262-692977751e4c}\Root\InventoryApplicationFile\shorcutlauncher.|546dbd93c2cc9e59 |
| Operation: | write | Name: | Version |
Value: 17.7.0.1903 | |||
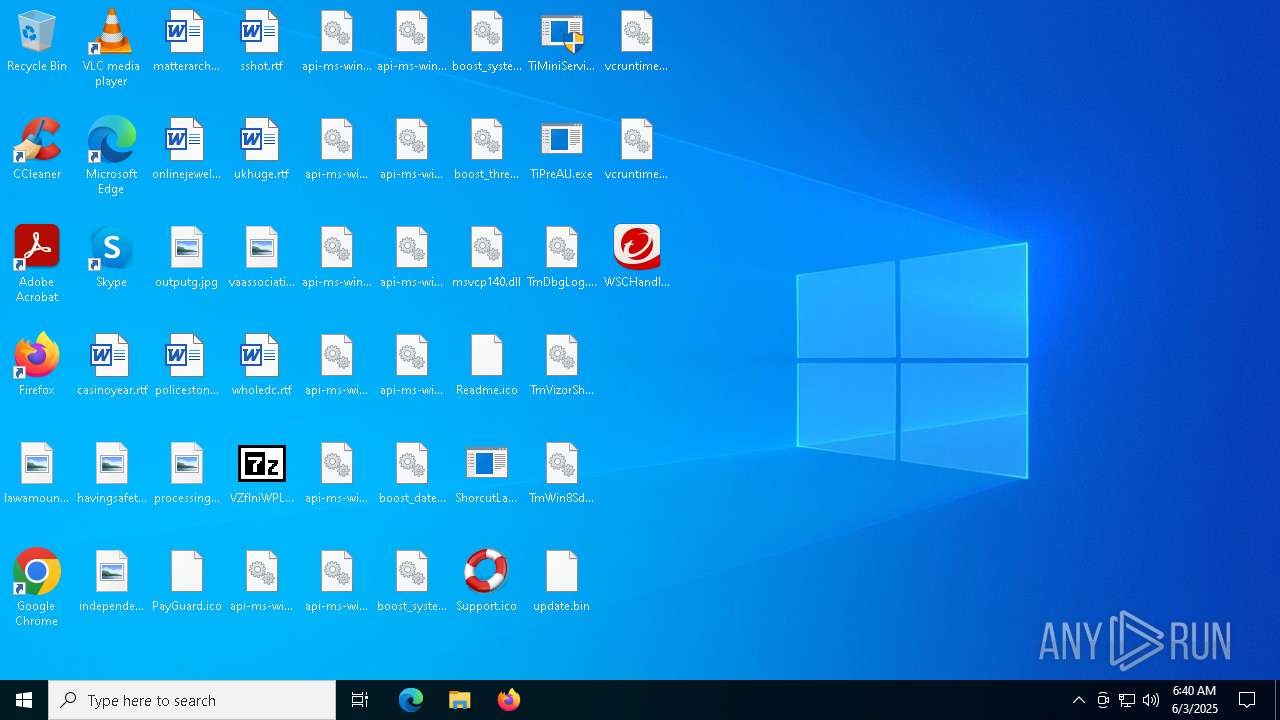
Executable files
25
Suspicious files
14
Text files
18
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6584 | VZfIniWPLHFOzcZJ.exe | C:\Users\admin\Desktop\Readme.ico | — | |
MD5:— | SHA256:— | |||
| 6584 | VZfIniWPLHFOzcZJ.exe | C:\Users\admin\Desktop\update.bin | binary | |
MD5:B5F3AFCCA181AEE002217B21DF625CB8 | SHA256:3BAD035FC26BA3FD9BE3D736F477B2993E94851CB41DF7EBB7DBA5B907D53AD1 | |||
| 6584 | VZfIniWPLHFOzcZJ.exe | C:\Users\admin\Desktop\api-ms-win-crt-locale-l1-1-0.dll | executable | |
MD5:FF48B107B2449A647C64BAABD49408A1 | SHA256:7BB8644E565AD4BCFD890F9044BCCB4D99953A740E9A500B1F820B2FDC3FC240 | |||
| 6584 | VZfIniWPLHFOzcZJ.exe | C:\Users\admin\Desktop\PayGuard.ico | binary | |
MD5:955BCA8FF155E135ACA347877FB70FFA | SHA256:2921A570030993DEA4197A17710D6A05B2B43820D415DAC42A817FABE3F80349 | |||
| 6584 | VZfIniWPLHFOzcZJ.exe | C:\Users\admin\Desktop\api-ms-win-crt-environment-l1-1-0.dll | executable | |
MD5:9653409A06CF90AEAE4491EE6A66125C | SHA256:5833BF2D9A301ED80514E6133B0DFF7C9BA152B4631FA6BC0153FDD696C0757F | |||
| 6584 | VZfIniWPLHFOzcZJ.exe | C:\Users\admin\Desktop\api-ms-win-crt-runtime-l1-1-0.dll | executable | |
MD5:F91E1FF896B5616919AC97C7095C513E | SHA256:07382C0D91DAD2BB6BA8BD06EA02F12C57ABF7C4E5A70672E9F2954D09A4FFD4 | |||
| 6584 | VZfIniWPLHFOzcZJ.exe | C:\Users\admin\Desktop\api-ms-win-crt-string-l1-1-0.dll | executable | |
MD5:0F593E50BE4715AA8E1F6EB39434EDD5 | SHA256:BF4EA10BE1B64C442AC0CCF4BDF69F6703467176A27E9E14A488D26448A6E179 | |||
| 6584 | VZfIniWPLHFOzcZJ.exe | C:\Users\admin\Desktop\api-ms-win-crt-filesystem-l1-1-0.dll | executable | |
MD5:42A2A95F1BB940D01F55EB1674A81FE2 | SHA256:51541EC6684B43157A85EA46A42EBED4555BE06BED0D0D07FF3EA6377301318D | |||
| 6584 | VZfIniWPLHFOzcZJ.exe | C:\Users\admin\Desktop\api-ms-win-crt-stdio-l1-1-0.dll | executable | |
MD5:429C26ED27A026442F89C95FF16CE8C2 | SHA256:2A466648AFFD3D51B944F563BB65046A3DA91006A0D90FB2C0B123487A1FC1B3 | |||
| 6584 | VZfIniWPLHFOzcZJ.exe | C:\Users\admin\Desktop\api-ms-win-crt-heap-l1-1-0.dll | executable | |
MD5:98DA186FD7D7873C164A51C5D7B77F1A | SHA256:80139E4CAA379D87B1D1DAFC23ACE71D2B330368115F6314140D4AE59C2A78E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
21
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7560 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2800 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2800 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
7560 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
7252 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
7560 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |