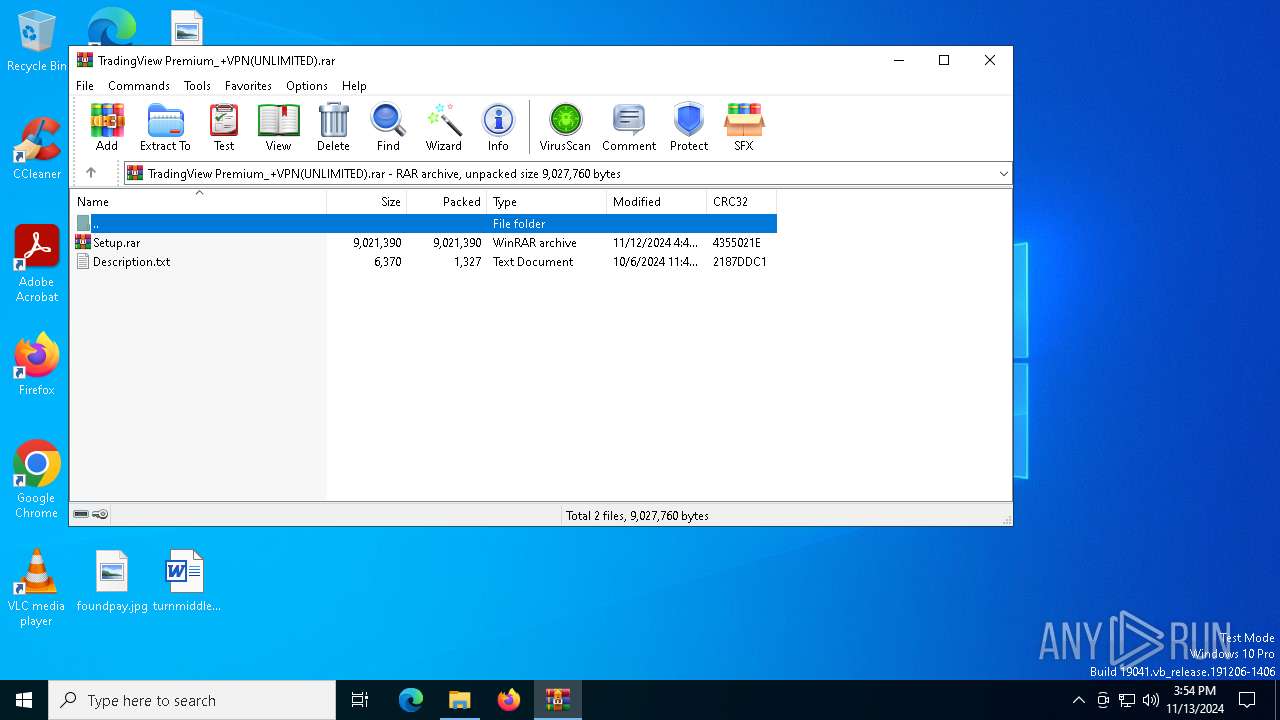
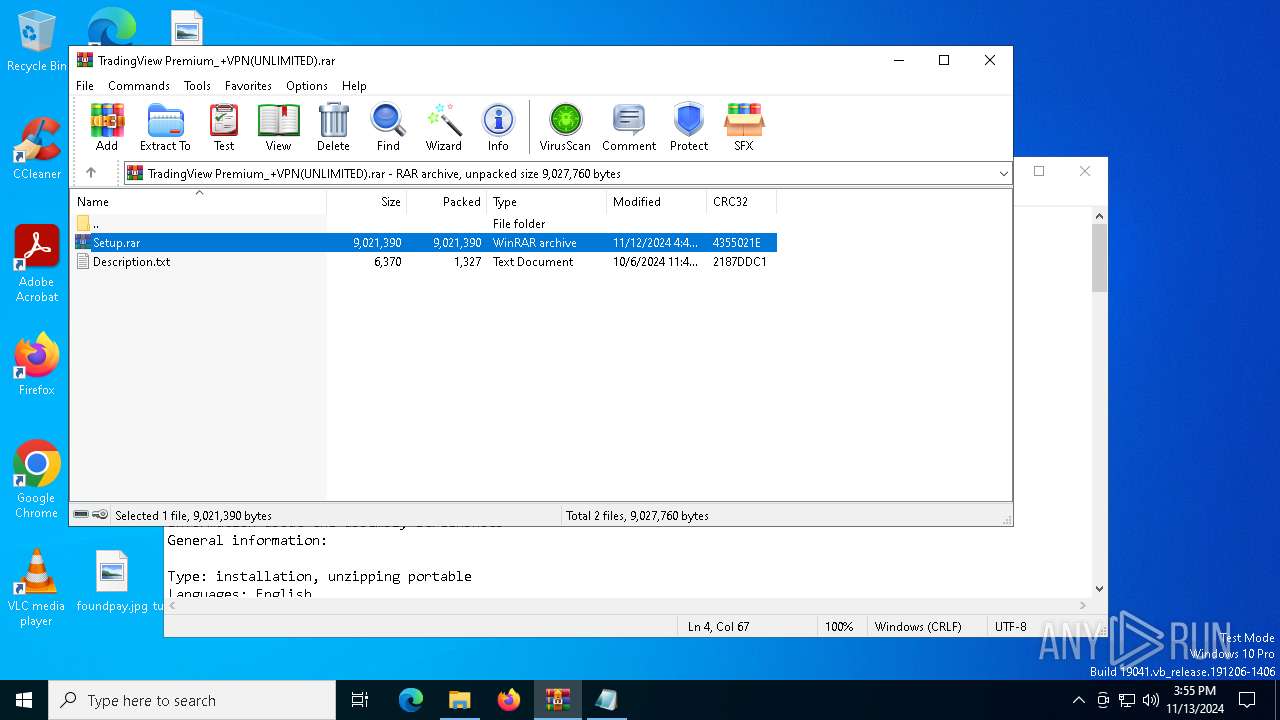
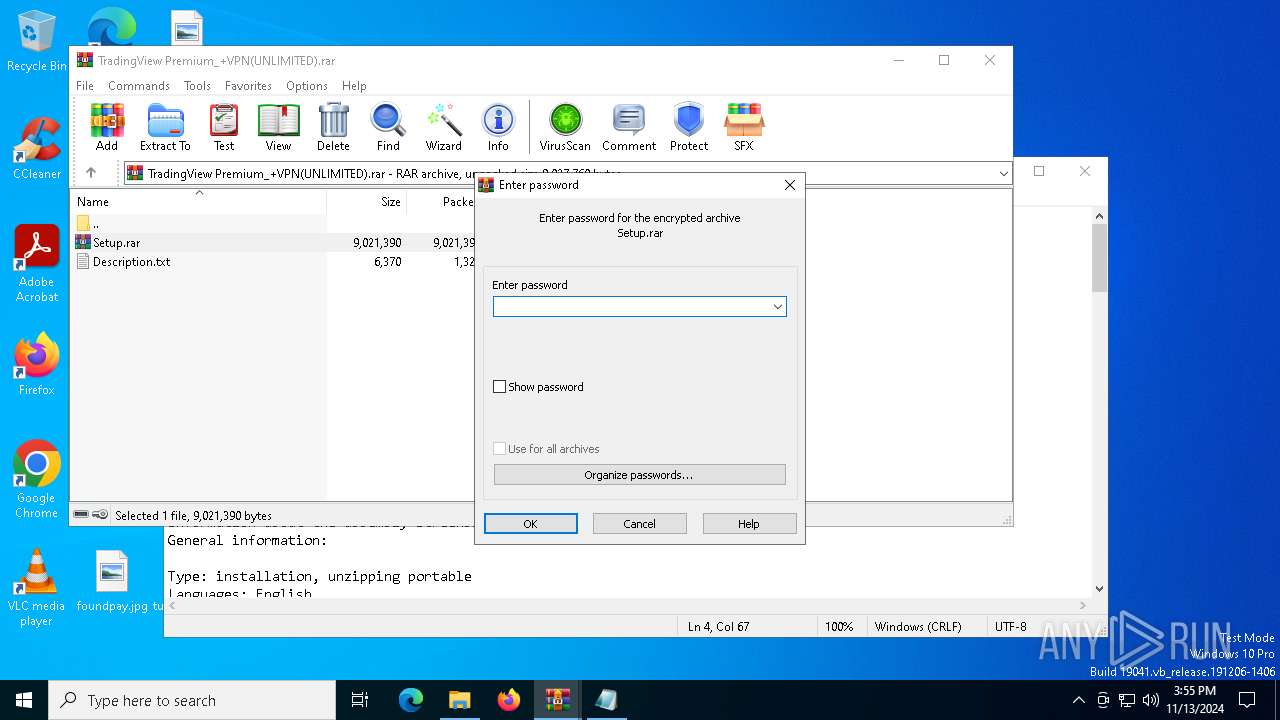
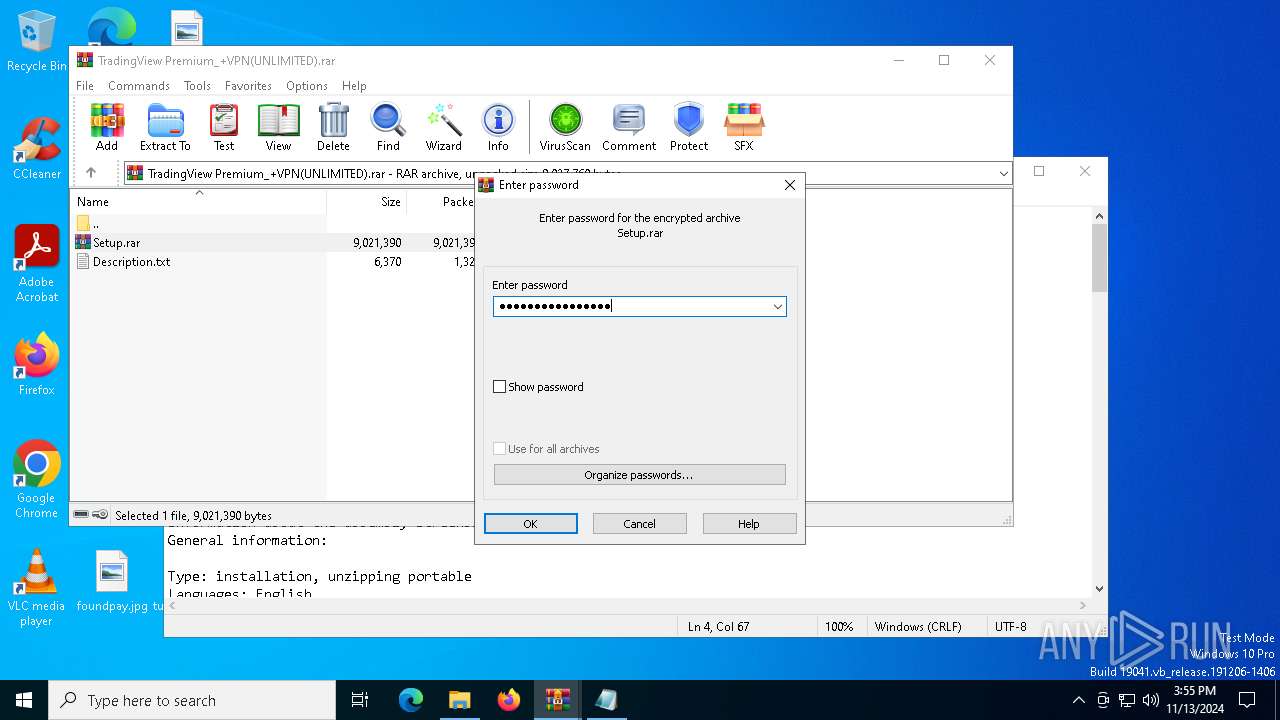
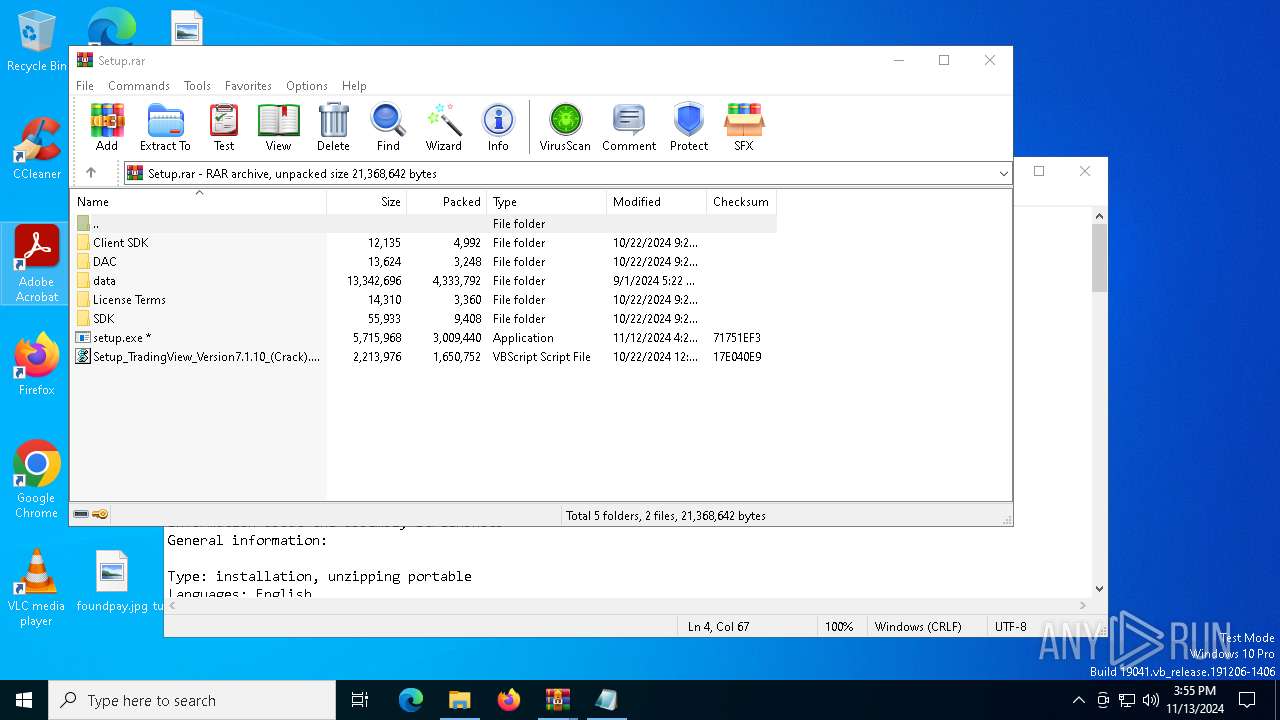
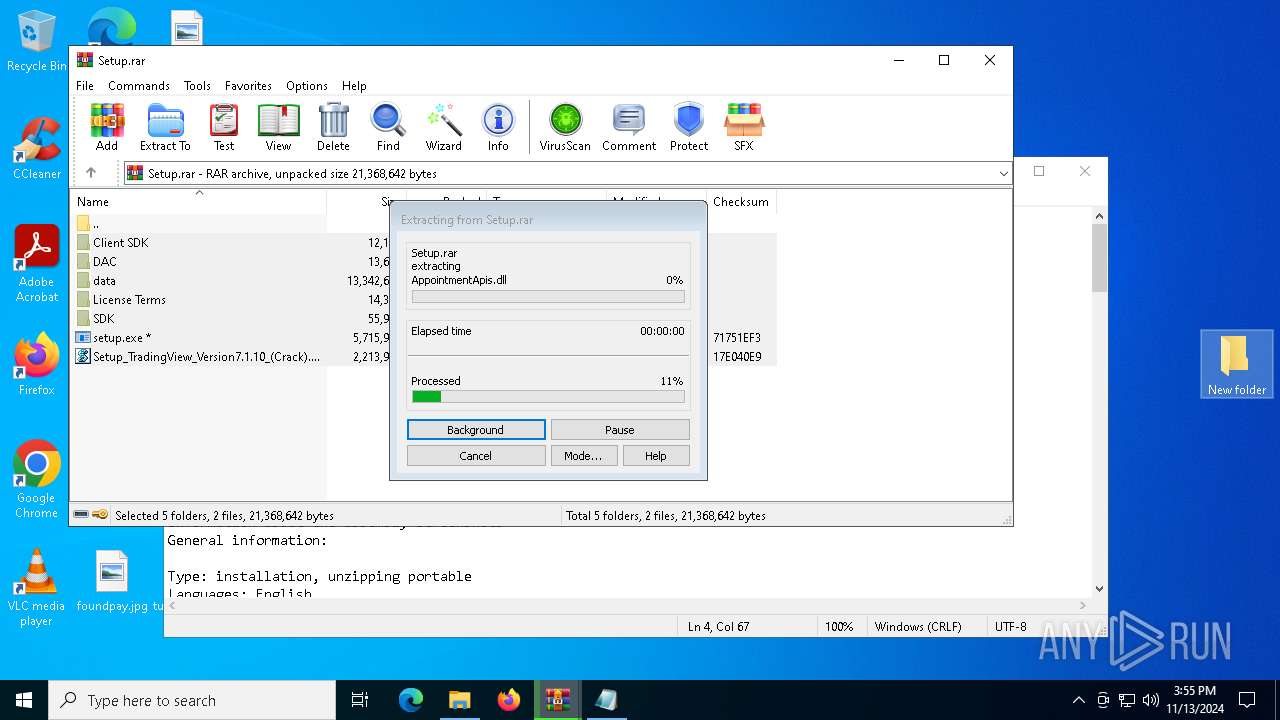
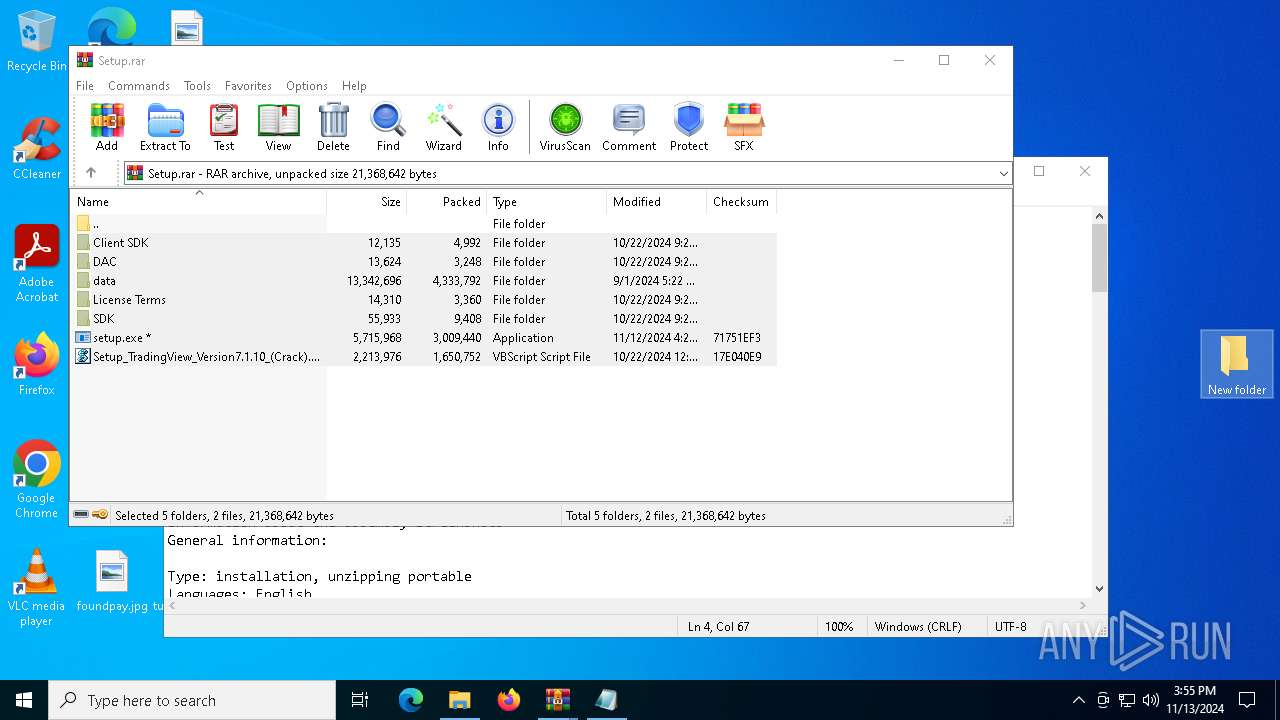
| File name: | TradingView Premium_+VPN(UNLIMITED).rar |
| Full analysis: | https://app.any.run/tasks/682440c8-9576-492a-9f2b-1aa865e2d66b |
| Verdict: | Malicious activity |
| Analysis date: | November 13, 2024, 15:53:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F01BB7FFBF88C697A380AF7D5FC11903 |
| SHA1: | A1CFC75246B8C14820330D317DD0618ECA42CD1C |
| SHA256: | 52103F6383E269A93965A0C2E40B0661BD1D02A0280FBFA9AEA54CBE481E1C2F |
| SSDEEP: | 98304:sWvqAos4yplEpZJU0dwcG8Xet6E9gC5xi0hJqfEne/NMUqIkcIWUWXwKaAn03Sc5:jsEpb5psRoIZT2VPVP |
MALICIOUS
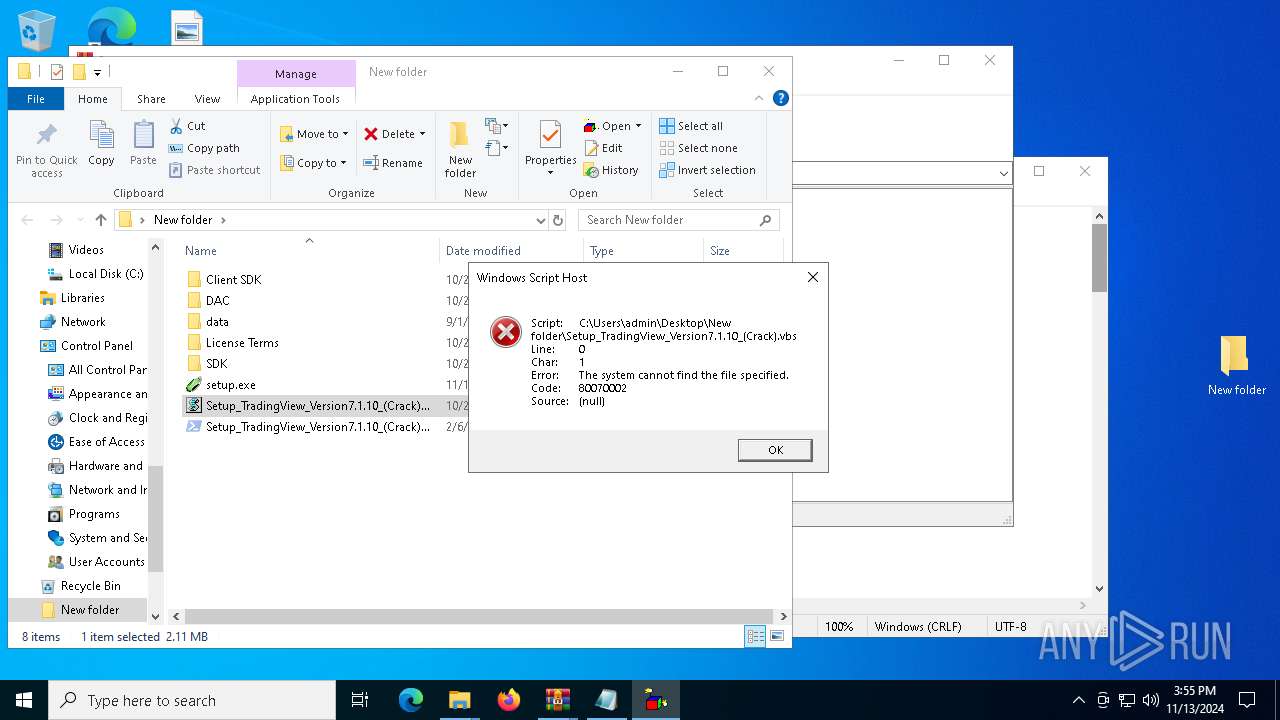
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 1452)
SUSPICIOUS
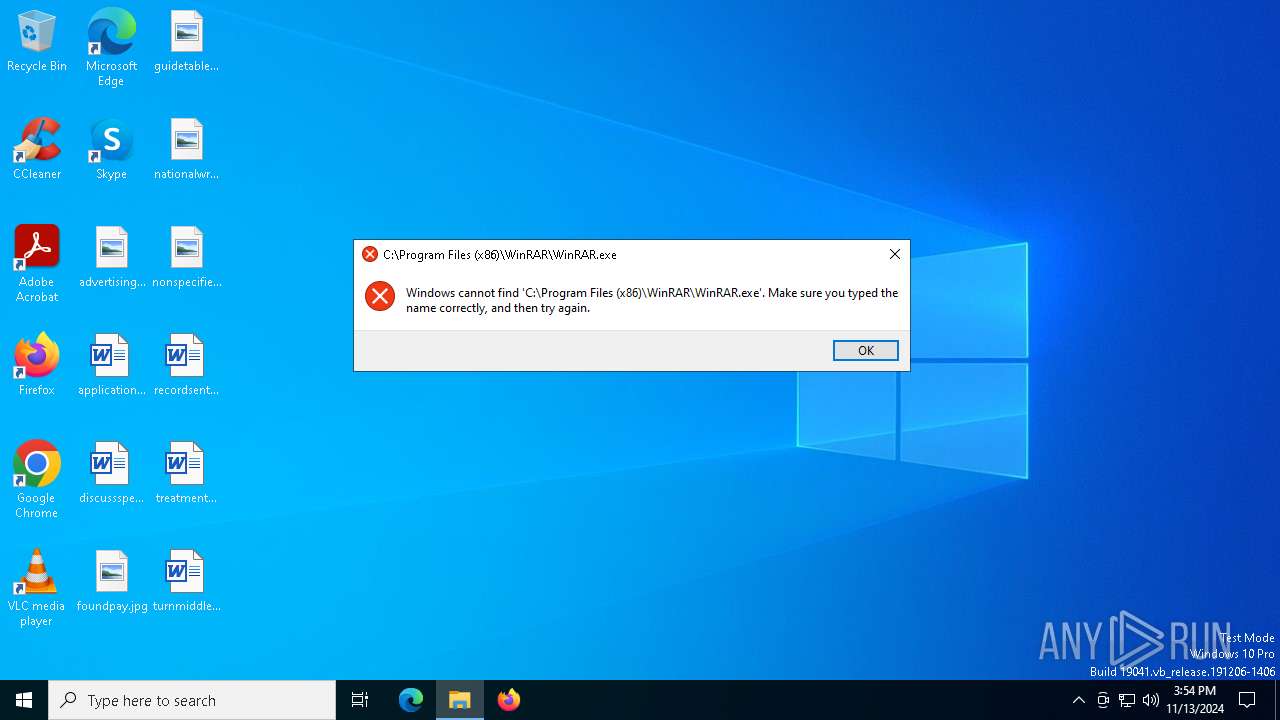
Application launched itself
- WinRAR.exe (PID: 2980)
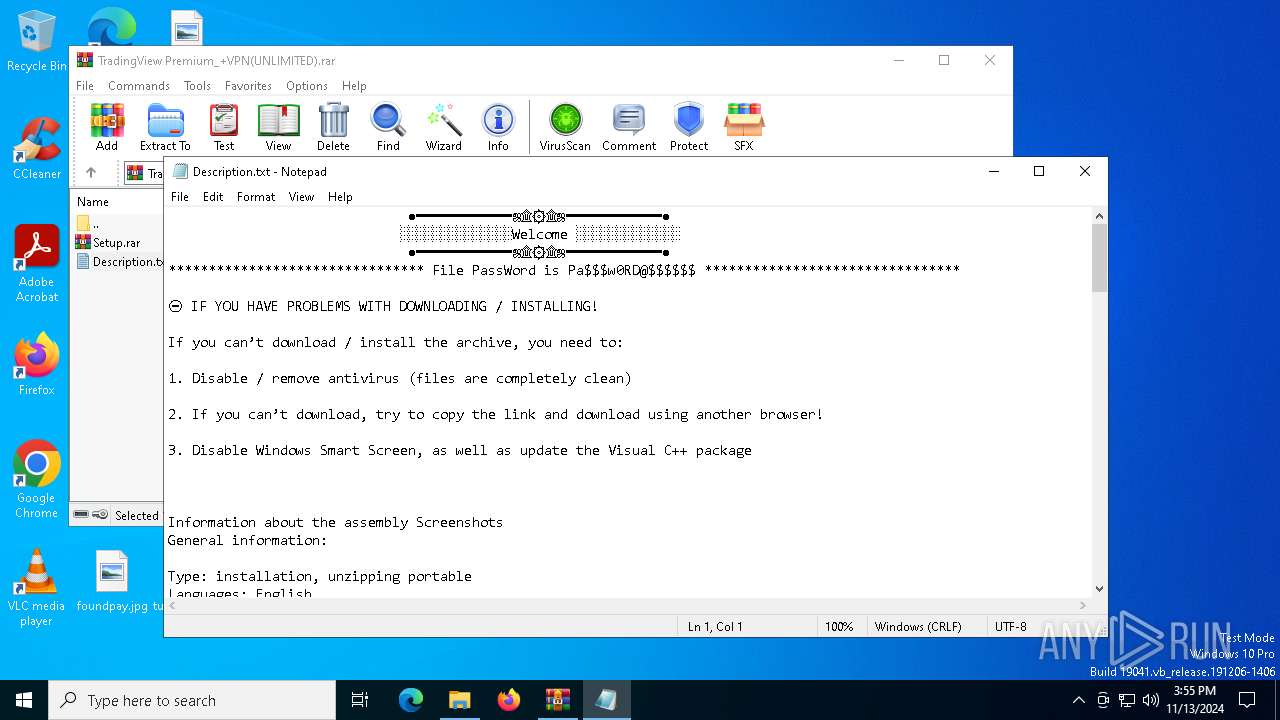
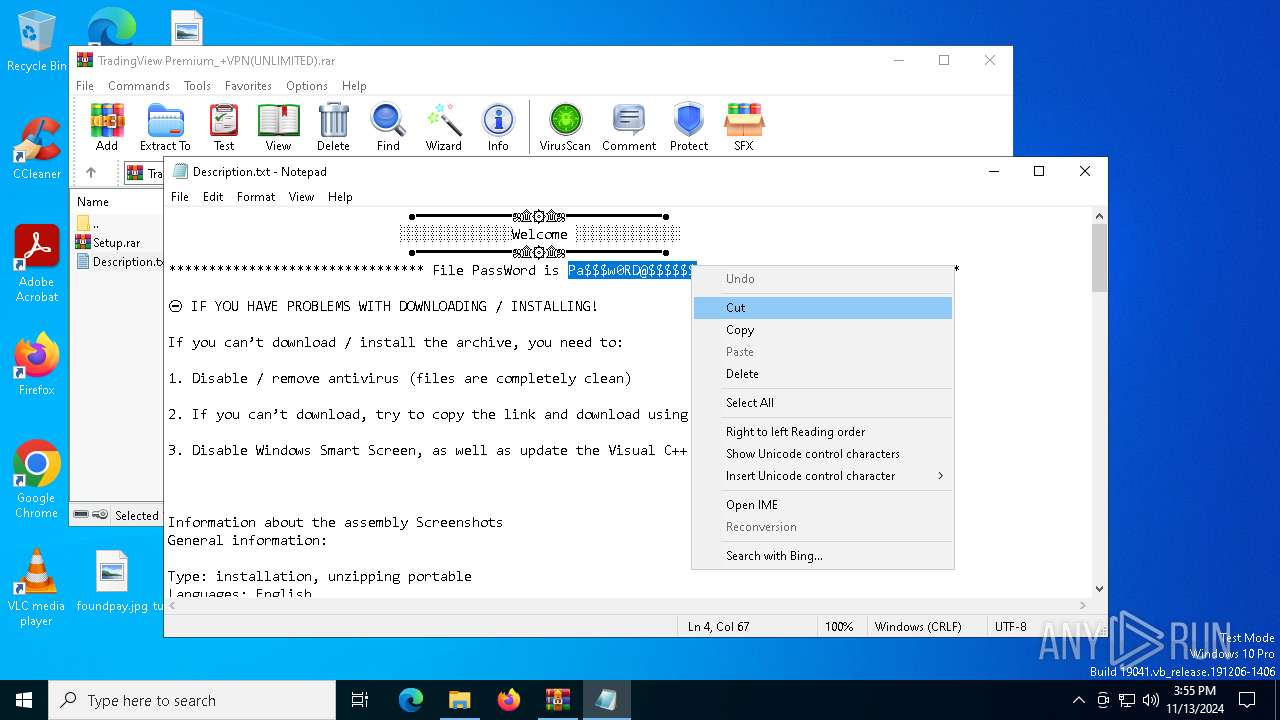
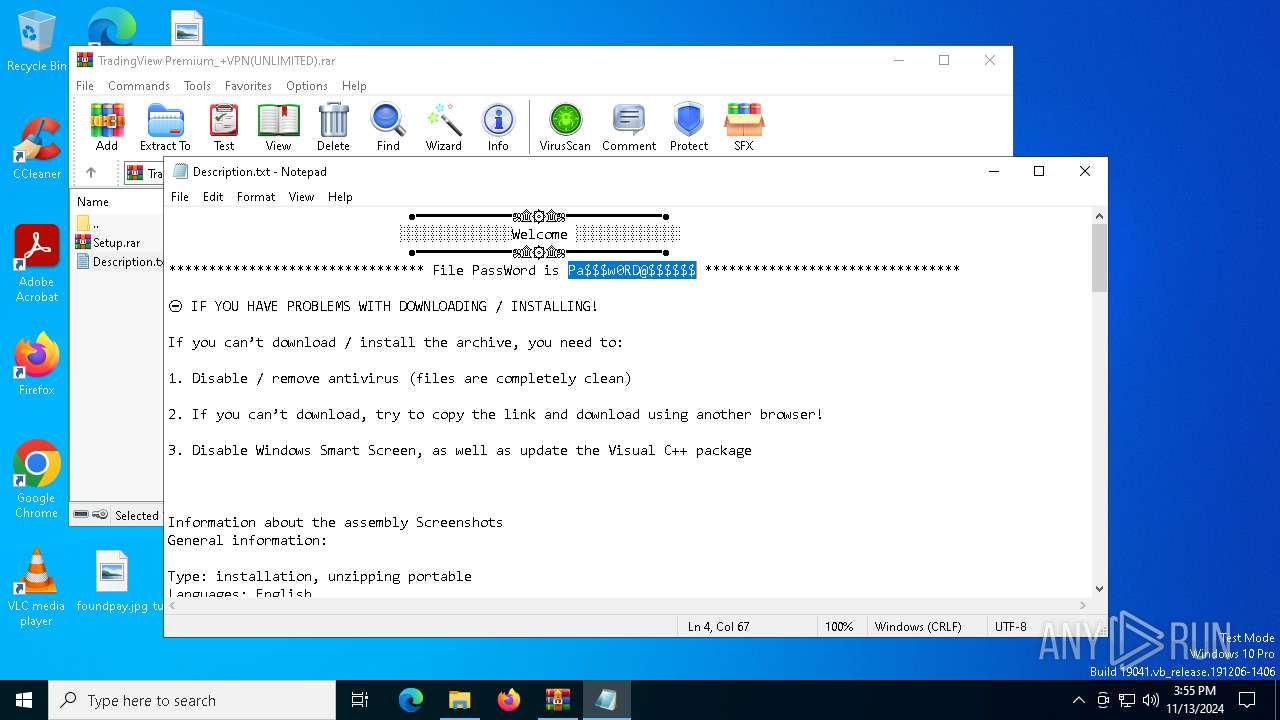
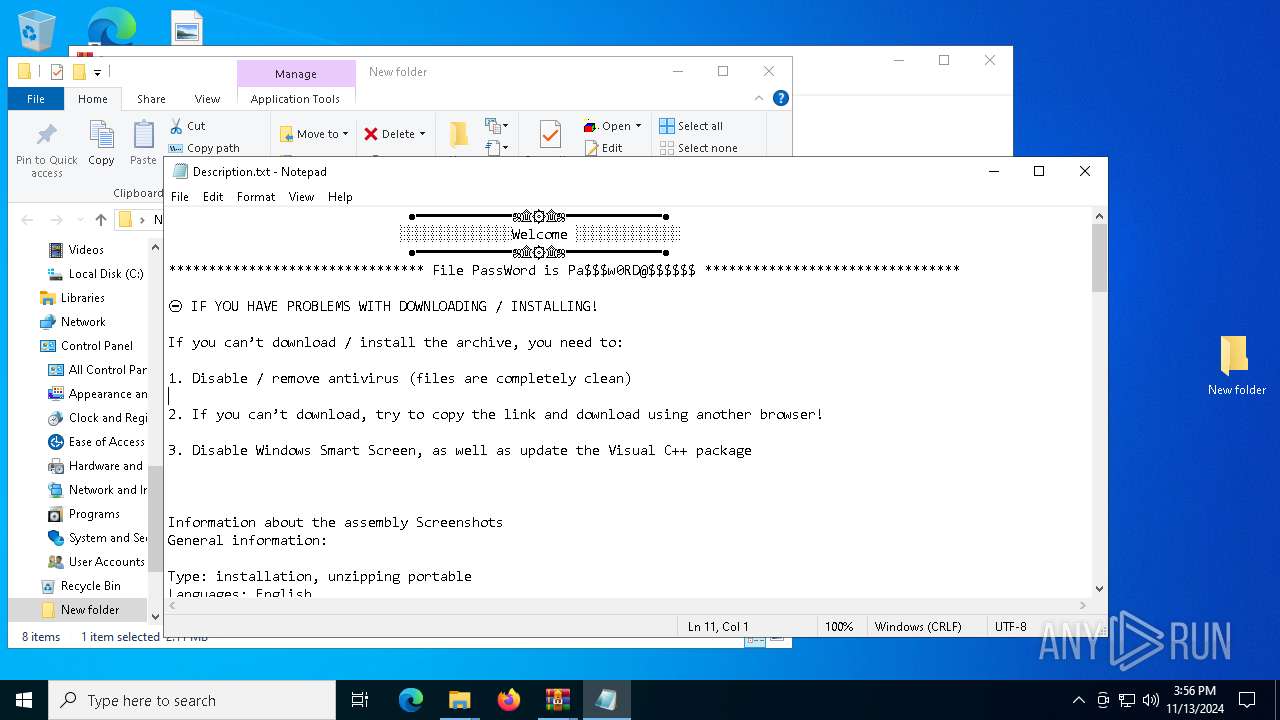
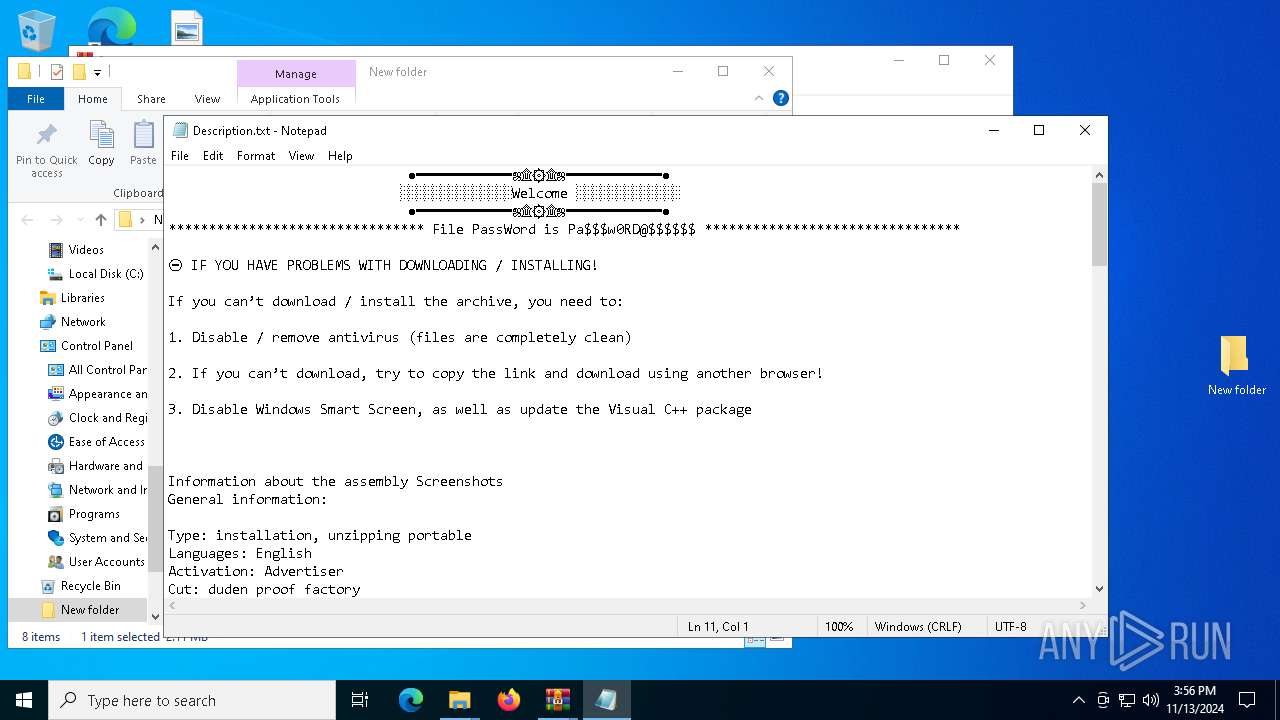
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 2980)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 1452)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 1452)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1452)
Creates an object to access WMI (SCRIPT)
- wscript.exe (PID: 1452)
Executed via WMI
- cmd.exe (PID: 3696)
Process drops legitimate windows executable
- cmd.exe (PID: 3696)
- WinRAR.exe (PID: 7040)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 1452)
Executable content was dropped or overwritten
- cmd.exe (PID: 3696)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2980)
- WinRAR.exe (PID: 7040)
Manual execution by a user
- wscript.exe (PID: 1452)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 9021390 |
| UncompressedSize: | 9021390 |
| OperatingSystem: | Win32 |
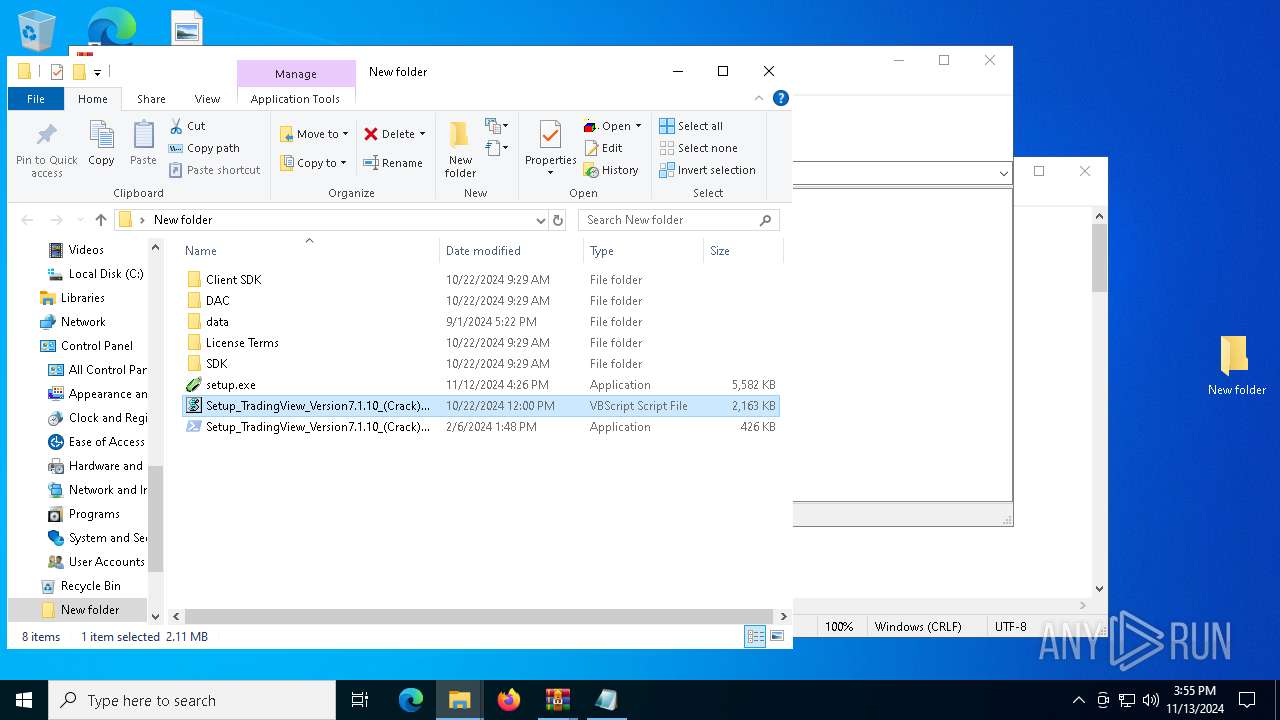
| ArchivedFileName: | Setup.rar |
Total processes
143
Monitored processes
10
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 916 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2980.11820\Description.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
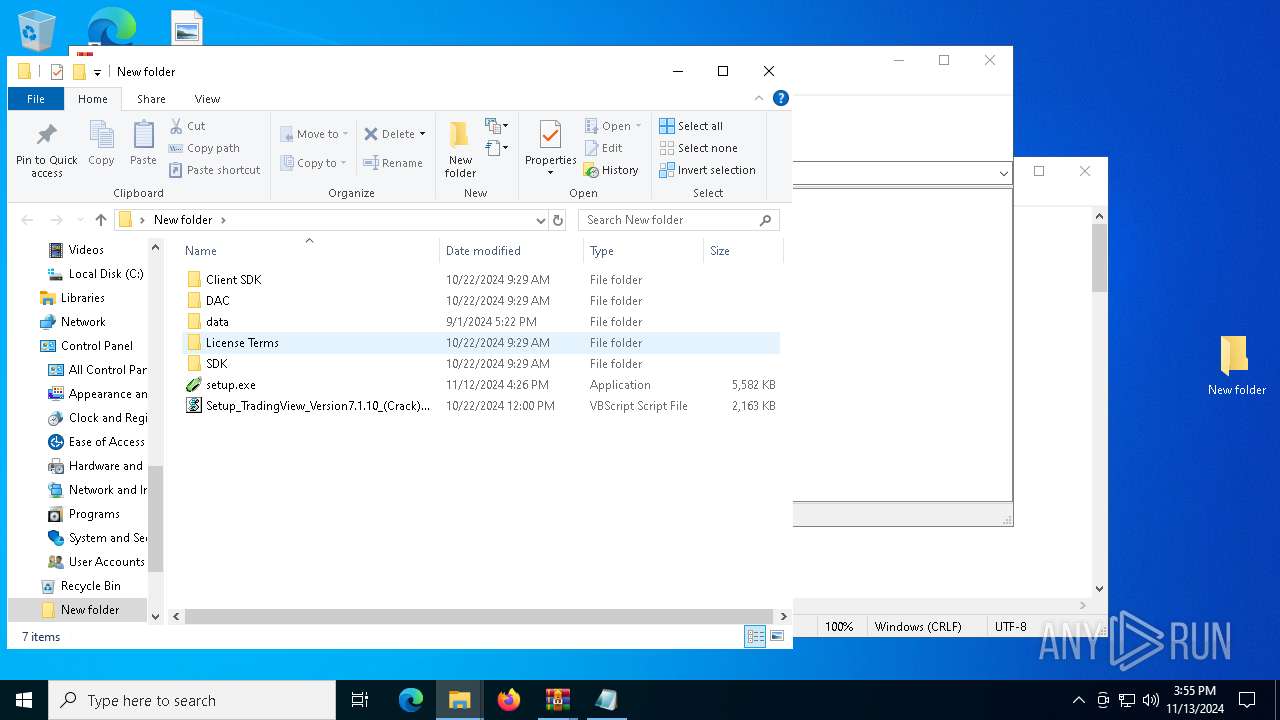
| 1452 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\New folder\Setup_TradingView_Version7.1.10_(Crack).vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2420 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
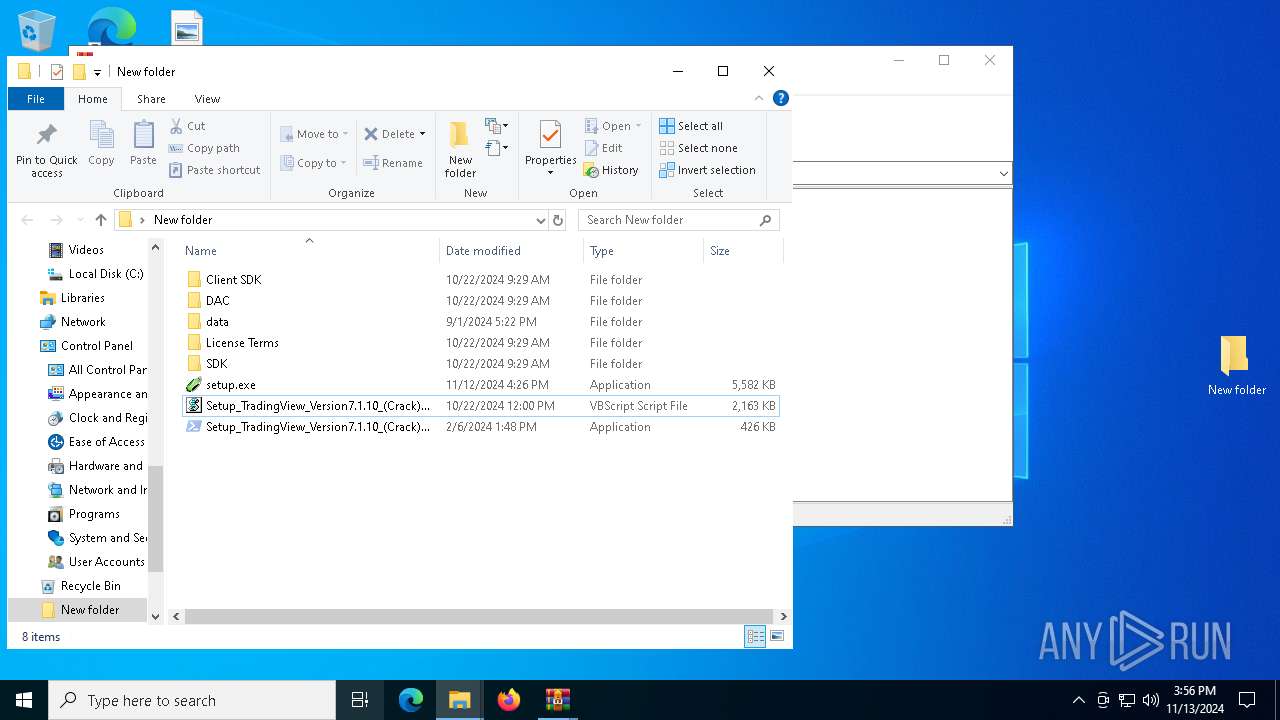
| 2980 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\TradingView Premium_+VPN(UNLIMITED).rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3696 | cmd /c copy "C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\Desktop\New folder\Setup_TradingView_Version7.1.10_(Crack).vbs.exe" /Y | C:\Windows\System32\cmd.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6416 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7040 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa2980.13009\Setup.rar | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7132 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 360
Read events
5 341
Write events
19
Delete events
0
Modification events
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TradingView Premium_+VPN(UNLIMITED).rar | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
| (PID) Process: | (7040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\AppData\Local\Temp\TradingView Premium_+VPN(UNLIMITED).rar | |||
Executable files
14
Suspicious files
0
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2980.13009\Setup.rar | — | |
MD5:— | SHA256:— | |||
| 7040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7040.14291\data\29216adb9440d701bb5600002011ec0a.msdelta.dll | executable | |
MD5:4268CC1FBDD2947725521853602E3351 | SHA256:A72E8D1C111616CE5F3B9E8C45EA5B7EBE5D89D4EC830078820F0D1DCBD9A922 | |||
| 7040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7040.14291\data\AppManMigrationPlugin.dll | executable | |
MD5:8AB1A94788FC84D590962B1C9A9C8EBC | SHA256:28C5EF2A8E3F67E190AE9B3B26B7615248A6F2A207267CAE749669AC04173F78 | |||
| 2980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2980.11820\Description.txt | text | |
MD5:0C02F4C49C21DA59FBED0061CB3A93DE | SHA256:214B43BEFA15CE49B83948403F039CA81626B6826C91CE81C5BE1266A9583B46 | |||
| 7040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7040.14291\data\appraiser.dll | executable | |
MD5:E3018A6A909084BF19168E20A0BC0A21 | SHA256:6E42452574B556821D273B78B6461A31C7C3AD4110D0F73D1E5545998BA61F74 | |||
| 7040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7040.14291\data\AppointmentApis.dll | executable | |
MD5:455BF9DB1F38409648F3F4FB37210B4A | SHA256:6858B0B0EE9748A117534FC21D2C1A36F639B77B3147ACC8D1DB3887DE62DC9F | |||
| 7040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7040.14291\SDK\Assemblies\ru\License_SMO.txt | text | |
MD5:839CDFA87B30840FAAA1D05F3F0014B6 | SHA256:C53071322A5D6E161EF5105FBB5EE4129A848E0BCB1ECB0DBBA11D351AD1CF13 | |||
| 7040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7040.14291\data\WMADMOE.DLL | executable | |
MD5:1B6C344E33BF0CDA03790CF68B3819E9 | SHA256:59F139C45F7734DDCB60F940E02D95013EDD0900ECE36F1581B3E0EA5378E934 | |||
| 7040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7040.14291\Client SDK\ODBC\170\License Terms\License_msodbcsql_ENU.txt | text | |
MD5:07CF3E505B9C844DE73D54D0159E55EC | SHA256:C80B4A4BCC21FE489E877D8CC7B3F3CFE4943801C4BC899A0F3C82244FA0F28A | |||
| 7040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7040.14291\Setup_TradingView_Version7.1.10_(Crack).vbs | text | |
MD5:9581A1C5428A3C95ED6804D800526CFC | SHA256:877B6EEA7B20282D3977B9AD512B62E5C614A57C8353971C76D3DD1416CEDEC1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
37
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4164 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2360 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2360 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6476 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.110.195:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 2.16.110.195:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |