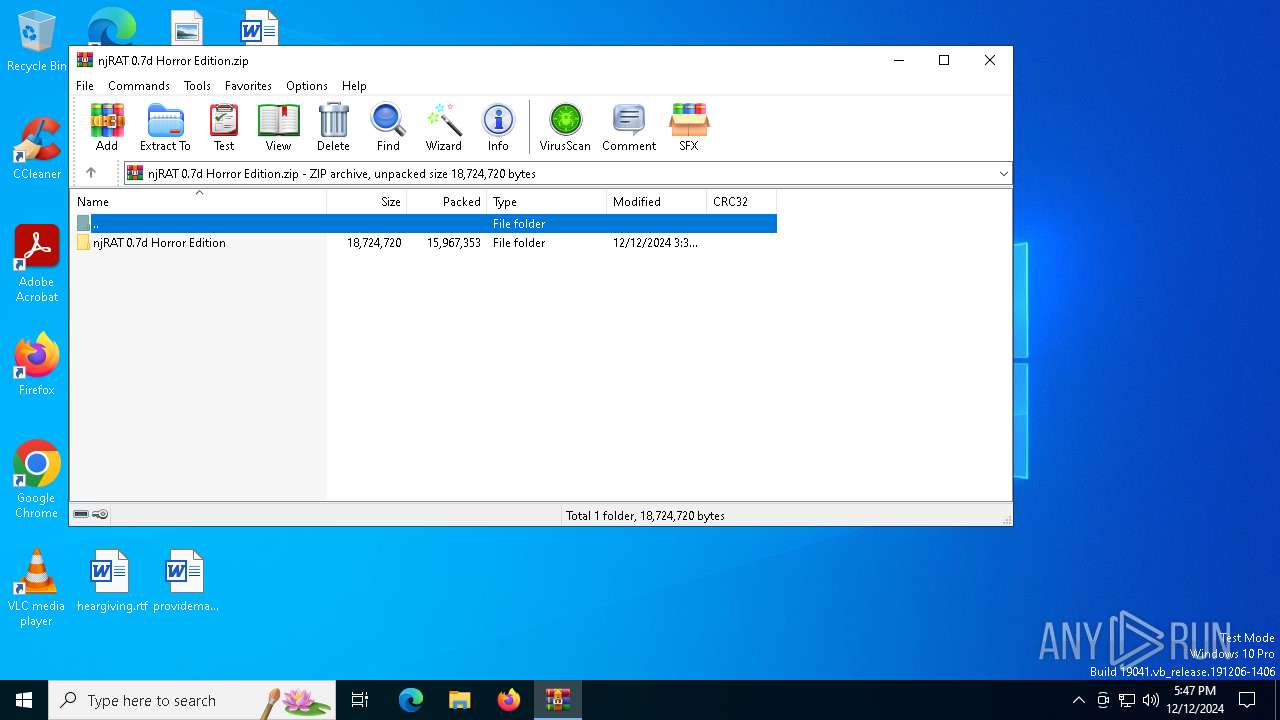
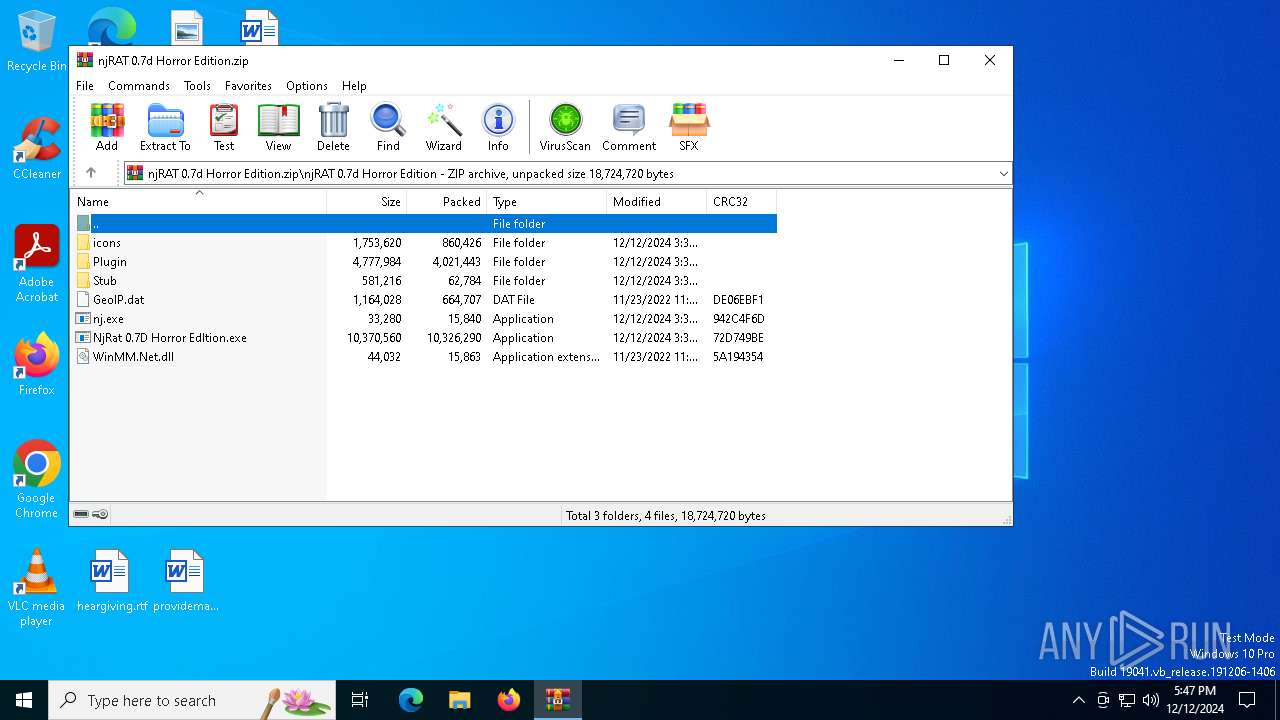
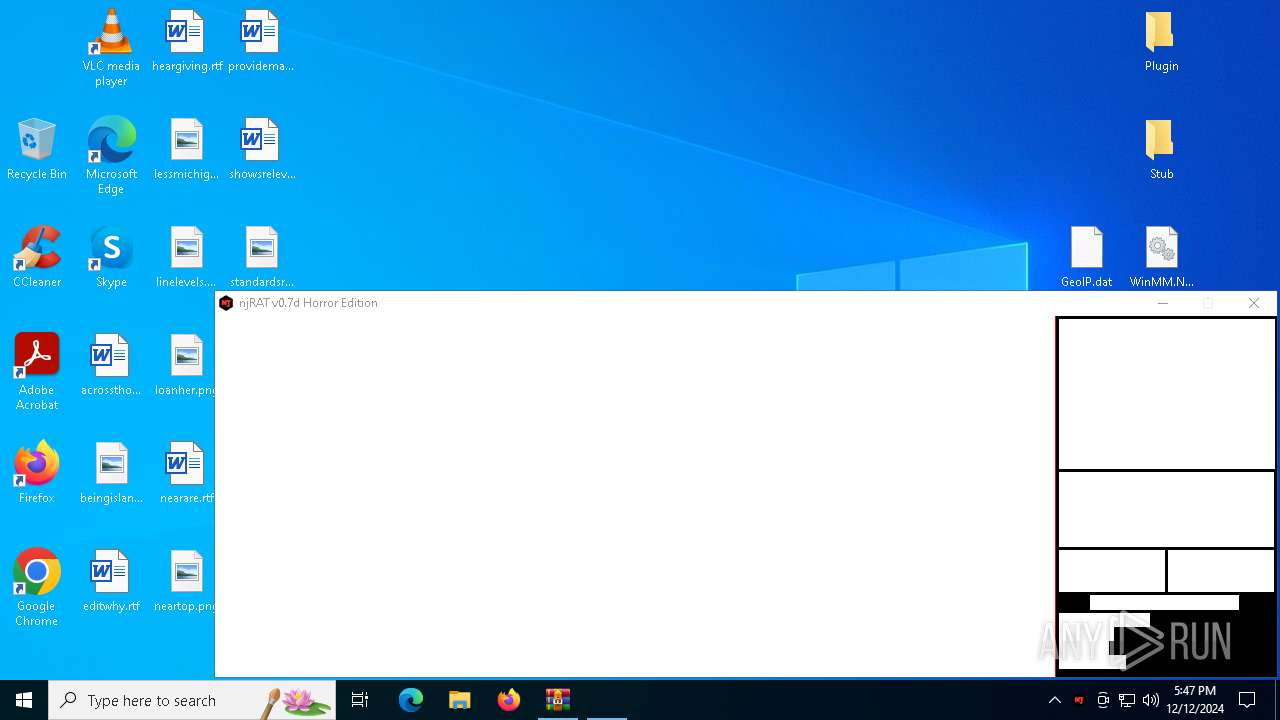
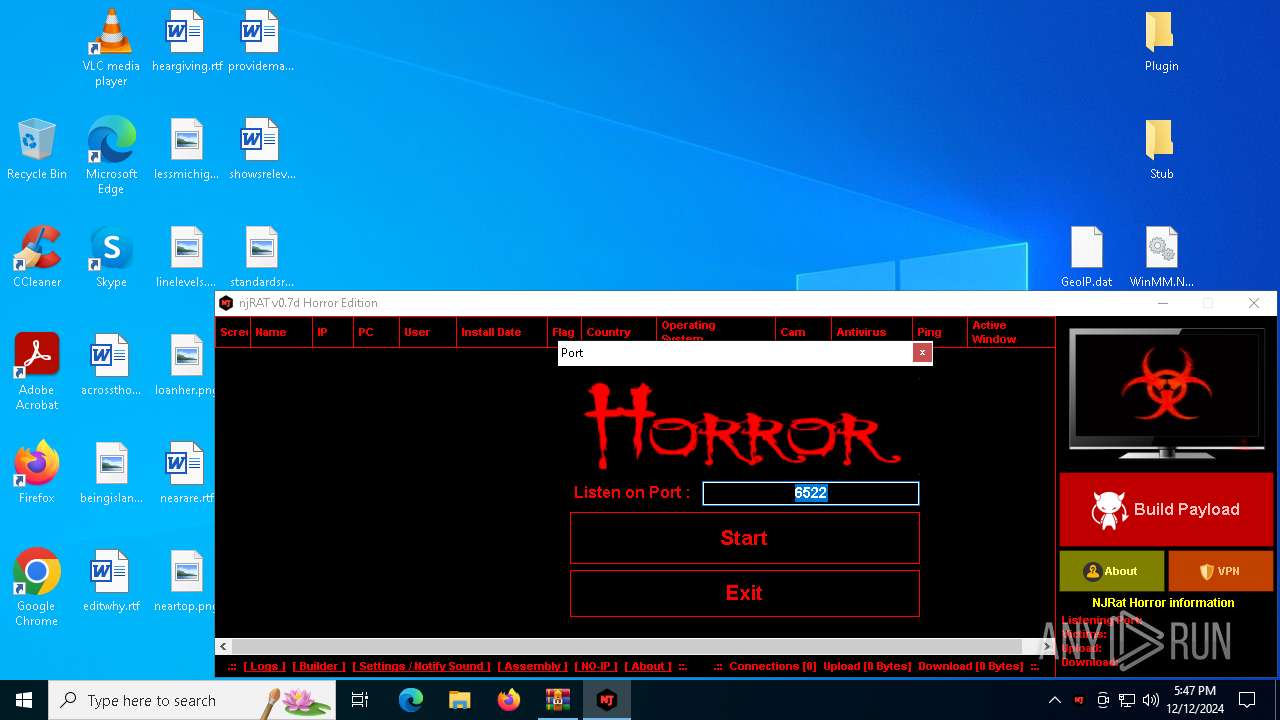
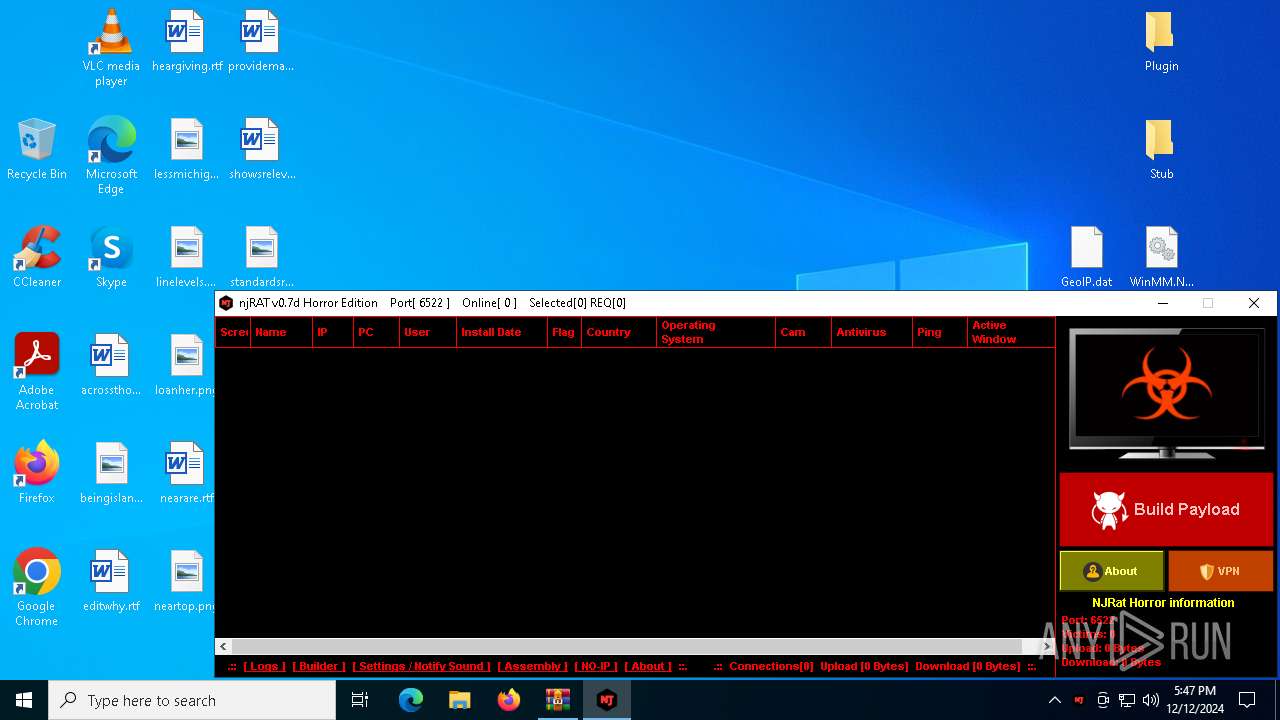
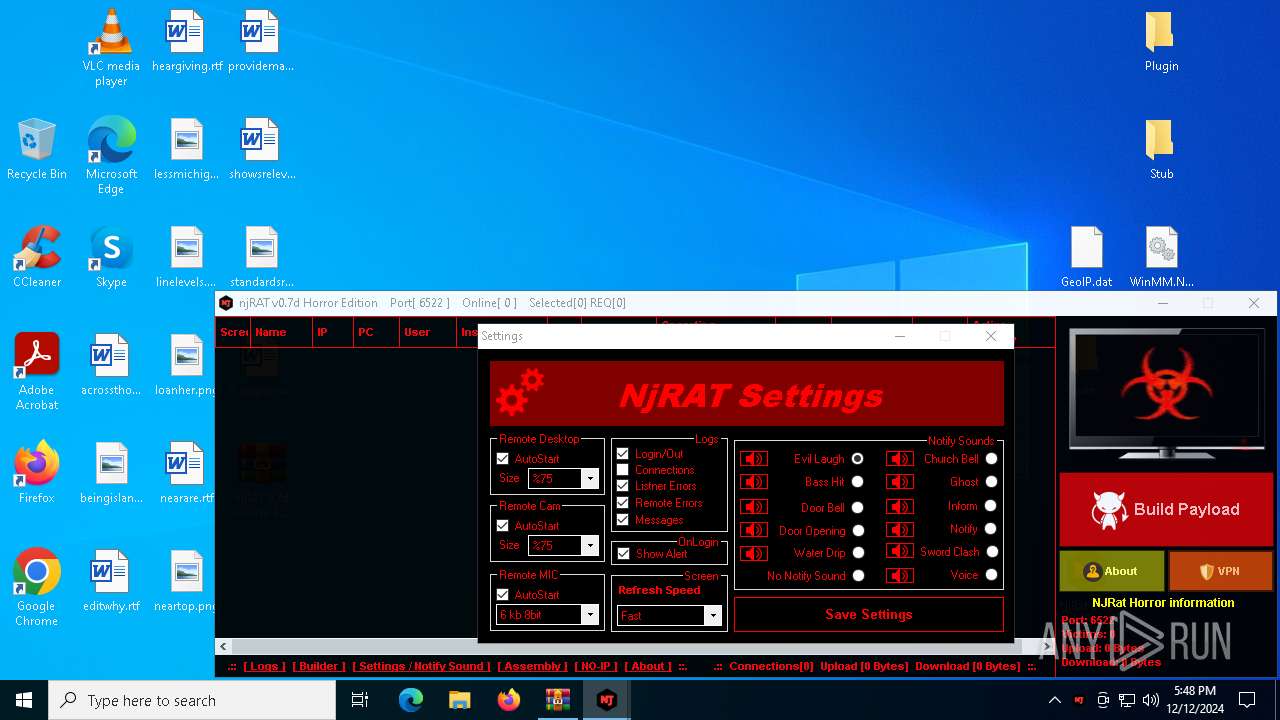
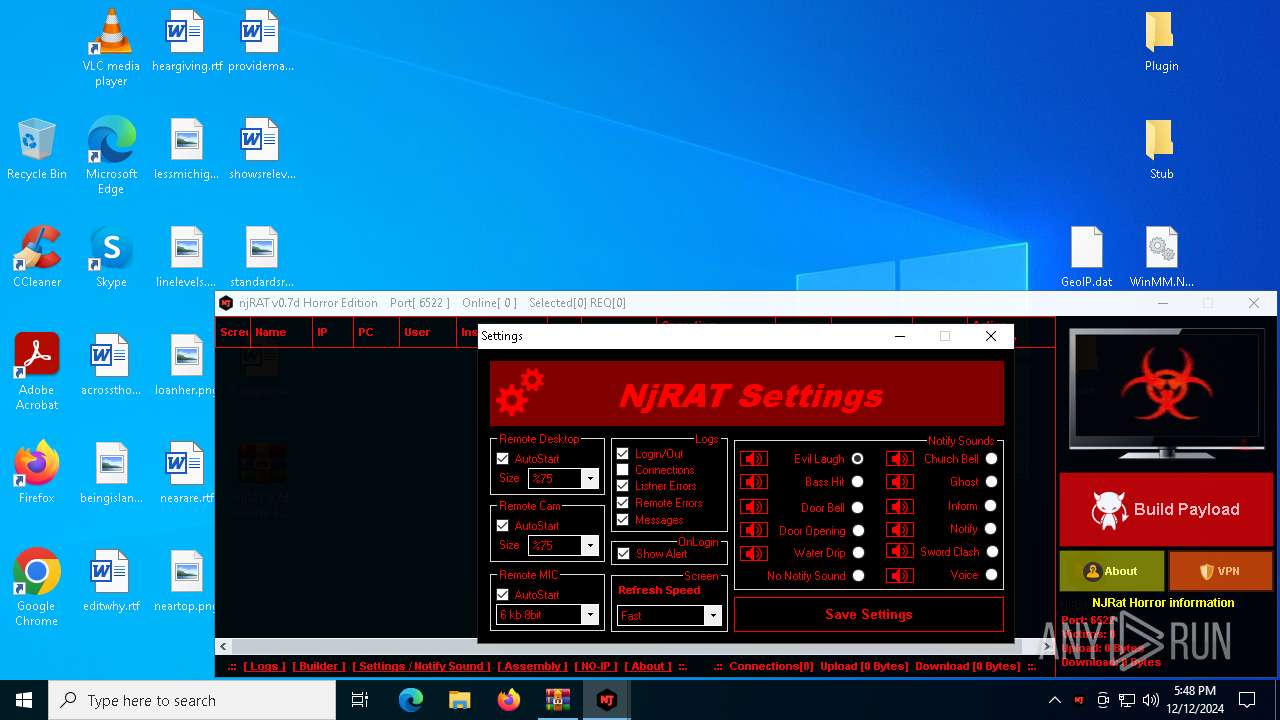
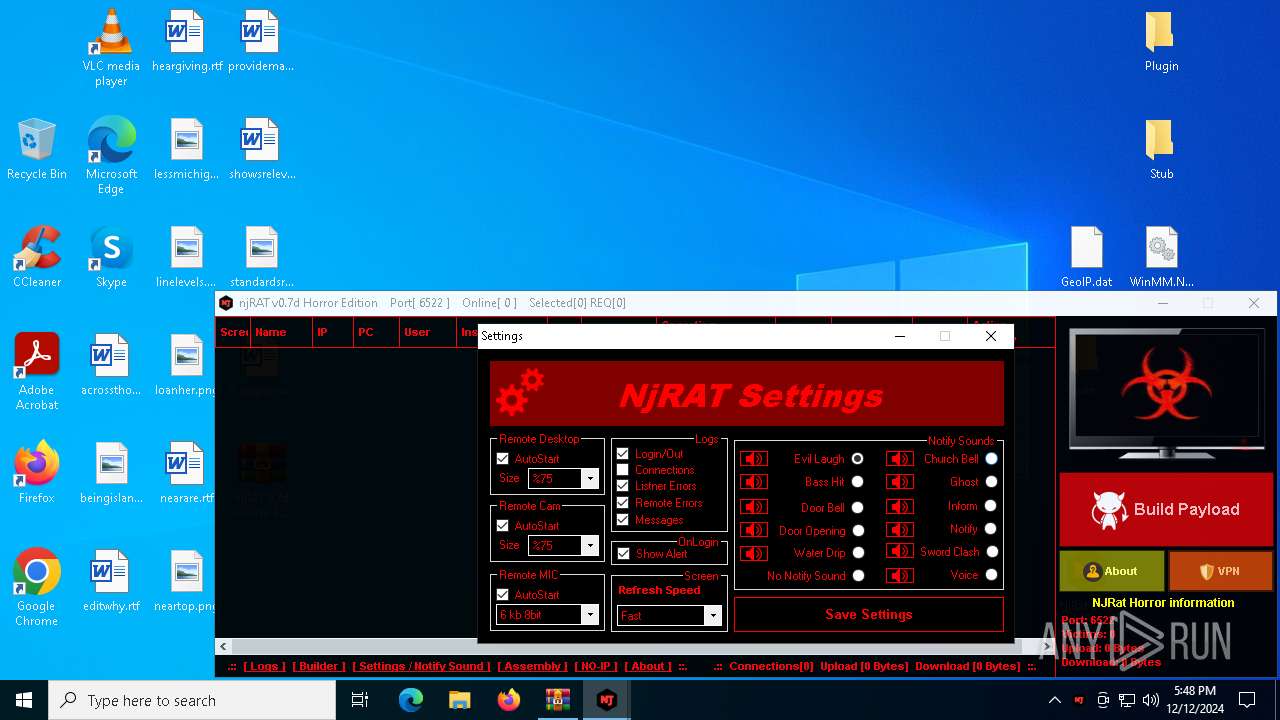
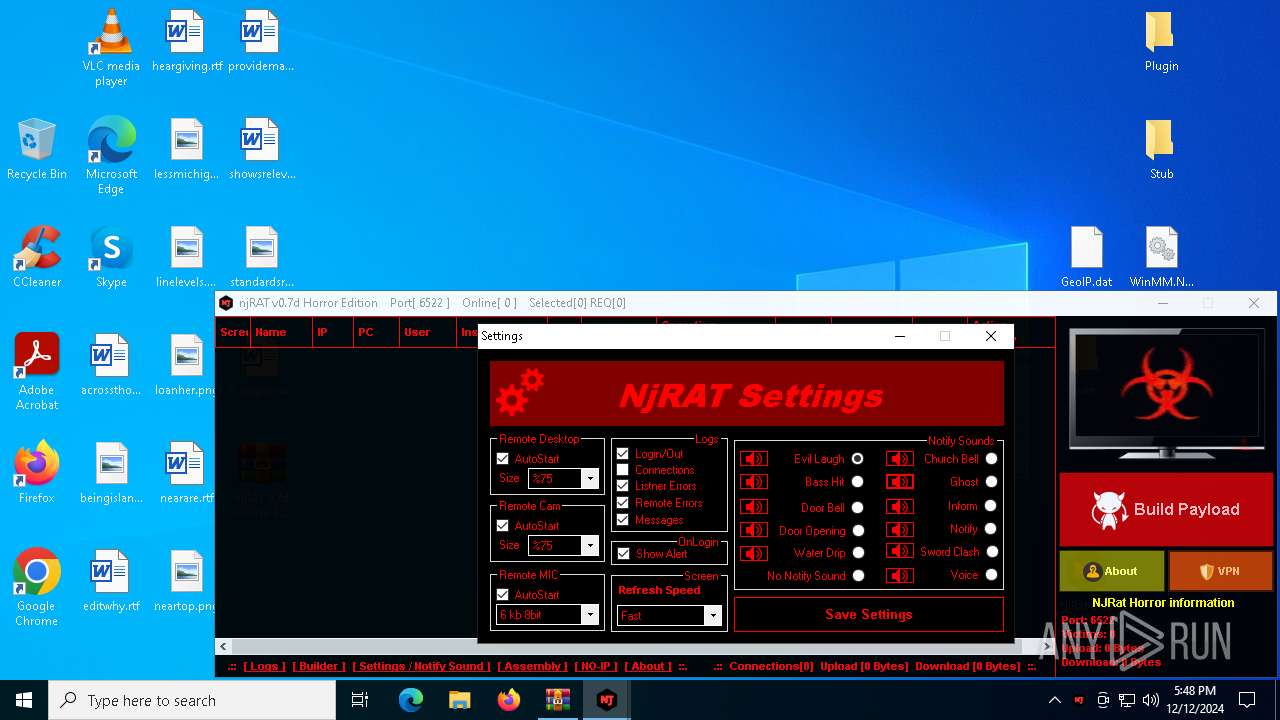
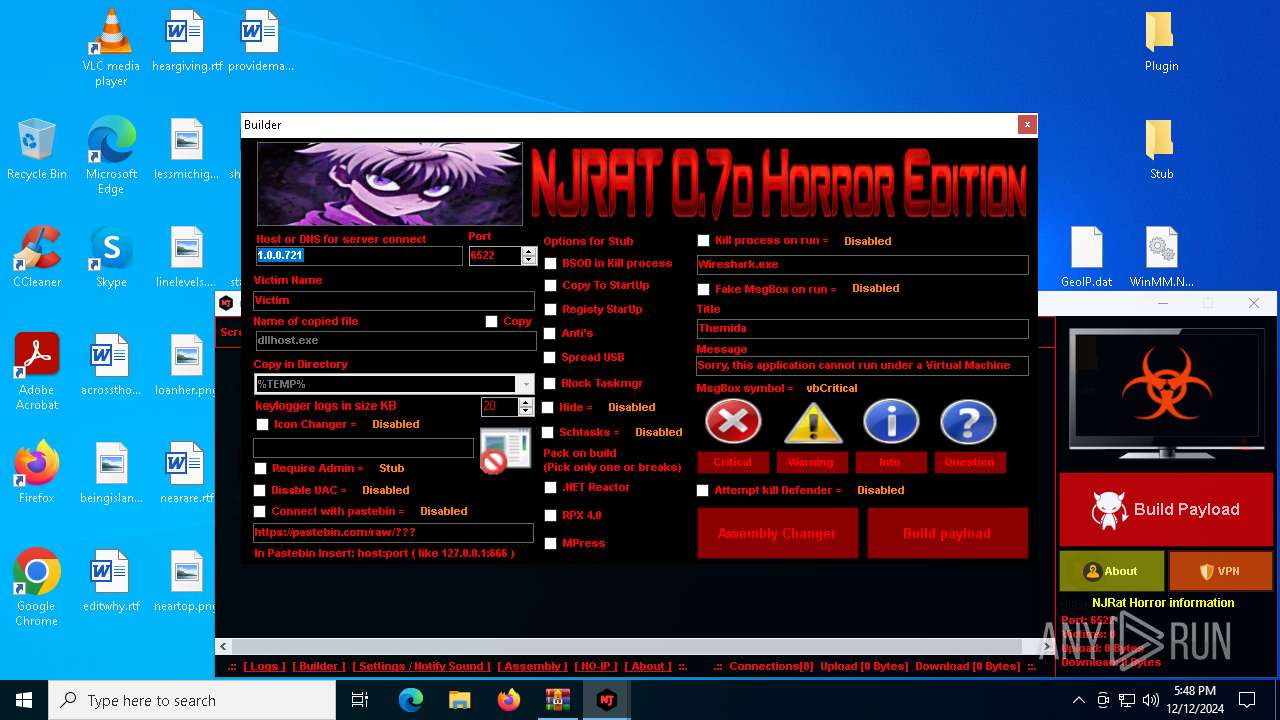
| File name: | njRAT 0.7d Horror Edition.zip |
| Full analysis: | https://app.any.run/tasks/6f4b6d17-5318-4ae2-9586-35e4c3c1b854 |
| Verdict: | Malicious activity |
| Analysis date: | December 12, 2024, 17:46:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | B7D702006B94E691396A02932152083D |
| SHA1: | E02A6836F287627BE59CB3FFEBAE7BA02BE1847A |
| SHA256: | 52084A6110C29BD4C44A8549467F94AA139CCF5920069A50427280BDEF79D3B8 |
| SSDEEP: | 98304:B8jwJPLBhH8jfbYD81Pj14LRj4XAS2IGn9ZGvxJNXjd17uPKyDGkqG2wwQj/y74O:Vca0JGIitJFdnXZ6jOQXFJZ8A+pf2+m |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2212)
XWORM has been detected (YARA)
- nj.exe (PID: 6872)
SUSPICIOUS
Reads the date of Windows installation
- NjRat 0.7D Horror Edltion.exe (PID: 6812)
Executable content was dropped or overwritten
- NjRat 0.7D Horror Edltion.exe (PID: 6812)
- nj.exe (PID: 6872)
Reads security settings of Internet Explorer
- NjRat 0.7D Horror Edltion.exe (PID: 6812)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- nj.exe (PID: 6872)
Connects to unusual port
- nj.exe (PID: 6872)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2212)
Manual execution by a user
- NjRat 0.7D Horror Edltion.exe (PID: 6812)
Checks supported languages
- NjRat 0.7D Horror Edltion.exe (PID: 6812)
- nj.exe (PID: 6872)
- NjRat 0.7D Horror Edition.exe (PID: 6904)
Reads the computer name
- nj.exe (PID: 6872)
- NjRat 0.7D Horror Edltion.exe (PID: 6812)
- NjRat 0.7D Horror Edition.exe (PID: 6904)
Reads the machine GUID from the registry
- NjRat 0.7D Horror Edltion.exe (PID: 6812)
- nj.exe (PID: 6872)
- NjRat 0.7D Horror Edition.exe (PID: 6904)
The process uses the downloaded file
- NjRat 0.7D Horror Edltion.exe (PID: 6812)
Process checks computer location settings
- NjRat 0.7D Horror Edltion.exe (PID: 6812)
Checks proxy server information
- nj.exe (PID: 6872)
Disables trace logs
- nj.exe (PID: 6872)
Reads the software policy settings
- nj.exe (PID: 6872)
Reads Environment values
- NjRat 0.7D Horror Edition.exe (PID: 6904)
- nj.exe (PID: 6872)
Attempting to use instant messaging service
- svchost.exe (PID: 2192)
Creates files or folders in the user directory
- nj.exe (PID: 6872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
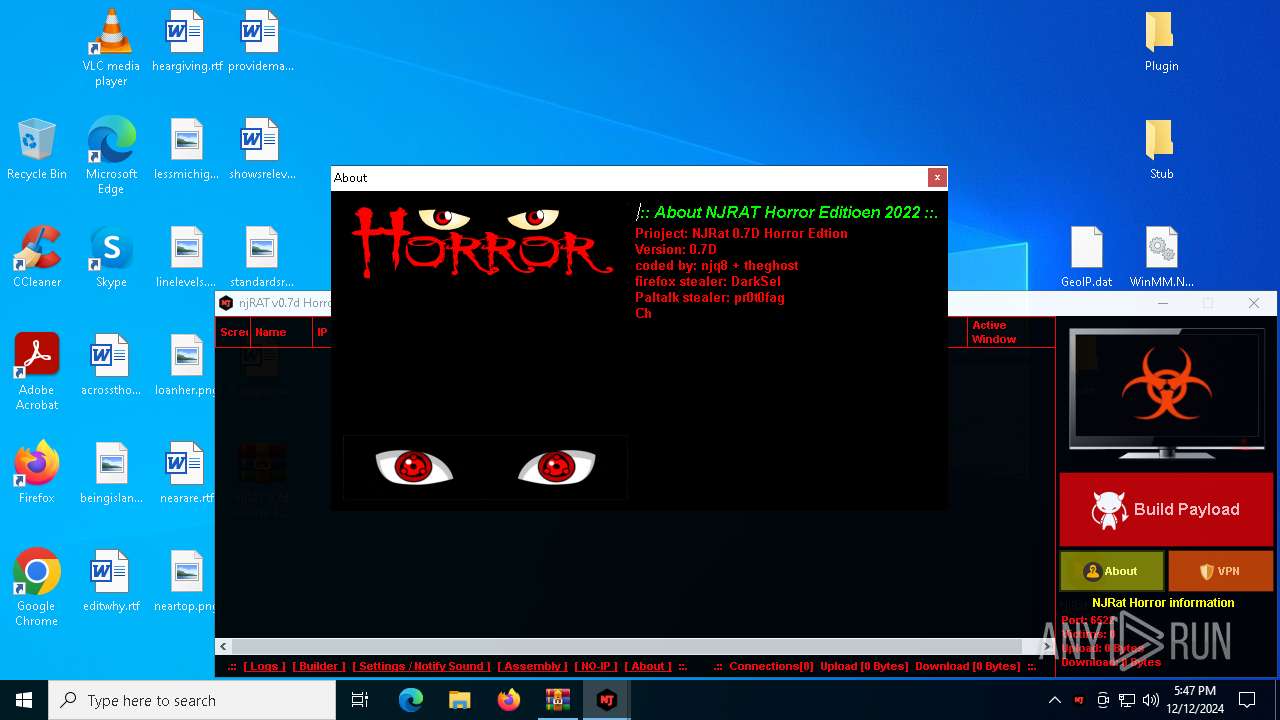
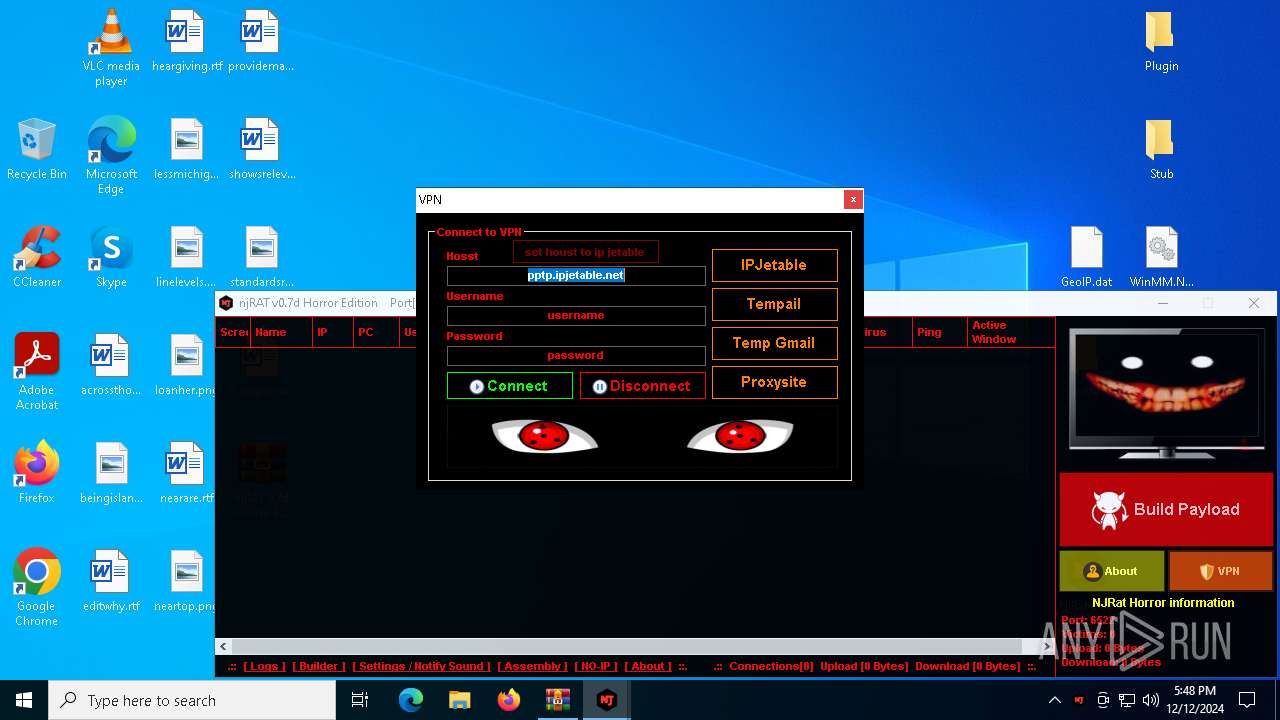
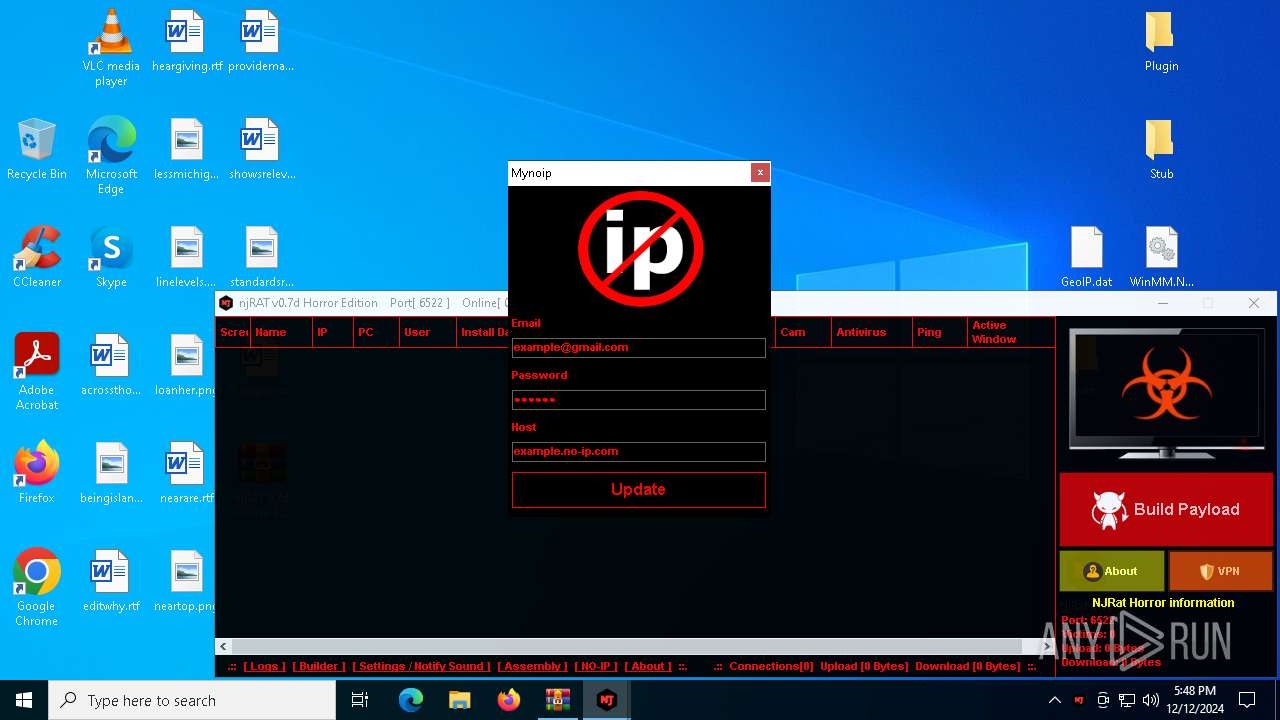
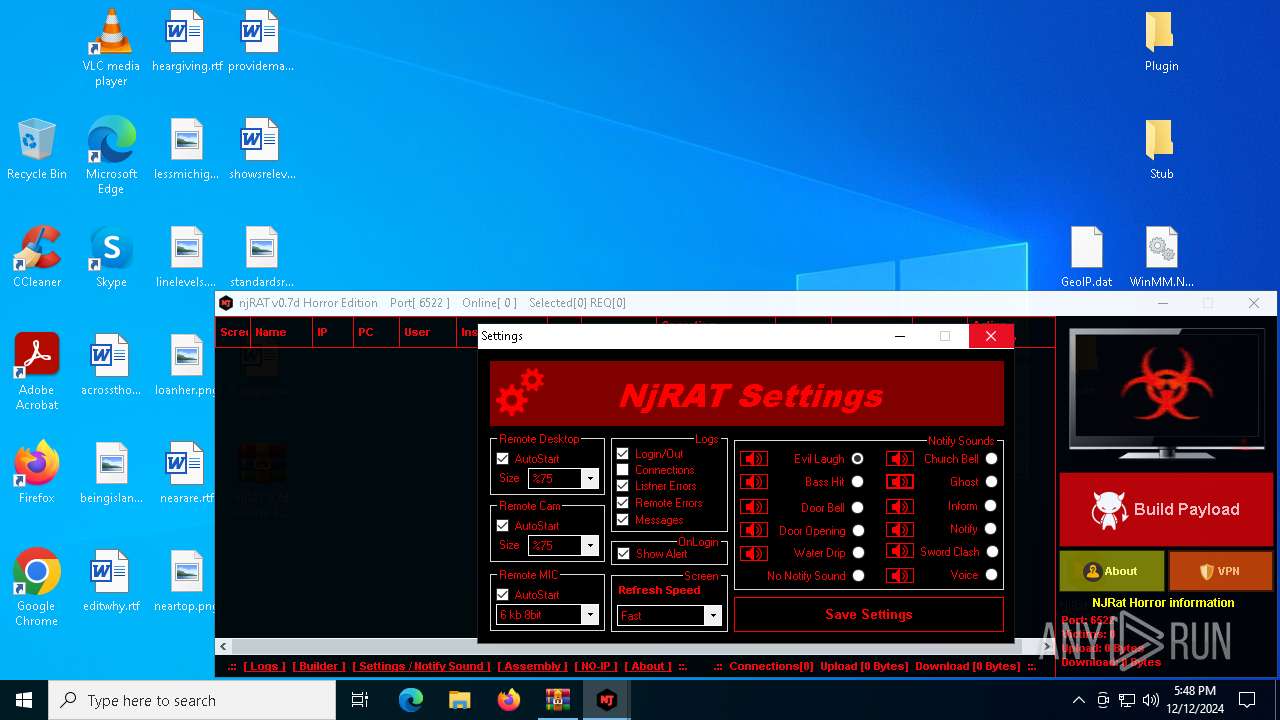
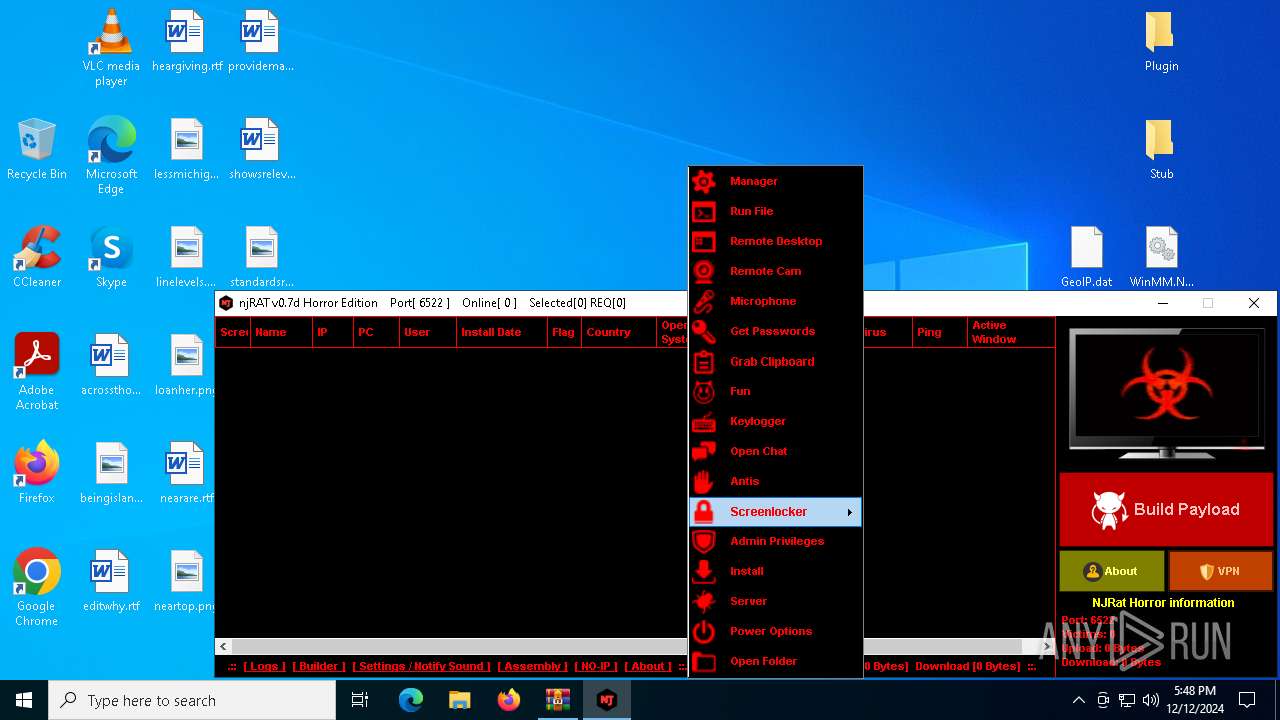
XWorm
(PID) Process(6872) nj.exe
C224.ip.gl.ply.gg:27322
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameUSB.exe
MutexzrtVrQsPKMWPaU1b
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:12 07:37:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | njRAT 0.7d Horror Edition/ |
Total processes
126
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2212 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\njRAT 0.7d Horror Edition.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6812 | "C:\Users\admin\Desktop\NjRat 0.7D Horror Edltion.exe" | C:\Users\admin\Desktop\NjRat 0.7D Horror Edltion.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.7 Modules
| |||||||||||||||
| 6872 | "C:\Users\admin\Desktop\nj.exe" | C:\Users\admin\Desktop\nj.exe | NjRat 0.7D Horror Edltion.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 1.0.0.0 Modules
XWorm(PID) Process(6872) nj.exe C224.ip.gl.ply.gg:27322 Keys AES<123456789> Options Splitter<Xwormmm> Sleep time3 USB drop nameUSB.exe MutexzrtVrQsPKMWPaU1b | |||||||||||||||
| 6904 | "C:\Users\admin\Desktop\NjRat 0.7D Horror Edition.exe" | C:\Users\admin\Desktop\NjRat 0.7D Horror Edition.exe | — | NjRat 0.7D Horror Edltion.exe | |||||||||||
User: admin Integrity Level: MEDIUM Version: 0.0.0.7 Modules
| |||||||||||||||
Total events
3 742
Read events
3 718
Write events
24
Delete events
0
Modification events
| (PID) Process: | (2212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\njRAT 0.7d Horror Edition.zip | |||
| (PID) Process: | (2212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2212) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6812) NjRat 0.7D Horror Edltion.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6872) nj.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\nj_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
20
Suspicious files
2
Text files
37
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2212.44860\njRAT 0.7d Horror Edition\icons\222.ico | image | |
MD5:4F5C162D6C6A8102E72FAD0822E0D1B2 | SHA256:F7C66D34840BAD867C64809D1EBA416832422D8230C7BFC55A1EC066E5FBD77A | |||
| 2212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2212.44860\njRAT 0.7d Horror Edition\icons\33.ico | image | |
MD5:2A28ECEBE11028B280549CA7BEA462DC | SHA256:04BA6BF89FD52C3D3C93EF77045B0CA6A6087C964841C8FBBD989E6370D655FA | |||
| 2212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2212.44860\njRAT 0.7d Horror Edition\icons\10.ico | image | |
MD5:1CB45CB1FC481E43D11F518A12C007BE | SHA256:B5C9954FE4F300E11226301E4FDEFD35A180A9DFD38385AD8448DDFE07447EB0 | |||
| 2212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2212.44860\njRAT 0.7d Horror Edition\icons\11.ico | image | |
MD5:A999BD85D73B4B4581350FF5F6C28D84 | SHA256:6418F9A87C22029F8BBD6690D30BF845E5852D3A2FF2CF7B72ED3E34DEF8B25A | |||
| 2212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2212.44860\njRAT 0.7d Horror Edition\icons\5.ico | image | |
MD5:CDEE018E88B7A515827C9B7C0AFE9C3F | SHA256:B8EEDD84108576669B3EBE1AF006A39DBE7B932A5CFDCB4EED8E1028464DA24D | |||
| 2212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2212.44860\njRAT 0.7d Horror Edition\icons\60.ico | image | |
MD5:1E2F8337310ABEC7E1697B11FA5B5C45 | SHA256:6E7BC8640EB3C9ABE2812315CE0856B25C92867DB899E402034190BA276D7C40 | |||
| 2212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2212.44860\njRAT 0.7d Horror Edition\GeoIP.dat | binary | |
MD5:A0A228C187329AD148F33C81DDB430BB | SHA256:B4BFD1EBC50F0EAAB3D3F4C2152FEAE7AA8EFAD380B85064153A6BFD006C6210 | |||
| 2212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2212.44860\njRAT 0.7d Horror Edition\icons\Luma - Yellow.ico | image | |
MD5:372573FB768C0AC6A5A467BECD74271D | SHA256:90C3A8EC41F20C19011BFFF58C4B437394121828A093BC3C9F0D2D4CDB23D824 | |||
| 2212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2212.44860\njRAT 0.7d Horror Edition\icons\jpeg.ico | image | |
MD5:9A7AE63DC67B2F1EE401F9F24FEFFB90 | SHA256:ECB5ACFE689DE564248BE488A29C798E5186E801C4BE455BC2712FF4E8CDFE3F | |||
| 2212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2212.44860\njRAT 0.7d Horror Edition\icons\Luma - Blue.ico | image | |
MD5:47C3CA39C929688E84558438E1142E10 | SHA256:0B5B1FA5030A11EAAFA818B8D4EA41AB7D69B97E9EC46A7494B8E5495A182807 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
18
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1760 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1760 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6312 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 184.86.251.21:443 | — | Akamai International B.V. | DE | unknown |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6872 | nj.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.telegram.org |
| shared |
slscr.update.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
— | — | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
— | — | Misc activity | ET HUNTING Telegram API Certificate Observed |
— | — | Misc activity | ET INFO Tunneling Service in DNS Lookup (* .ply .gg) |