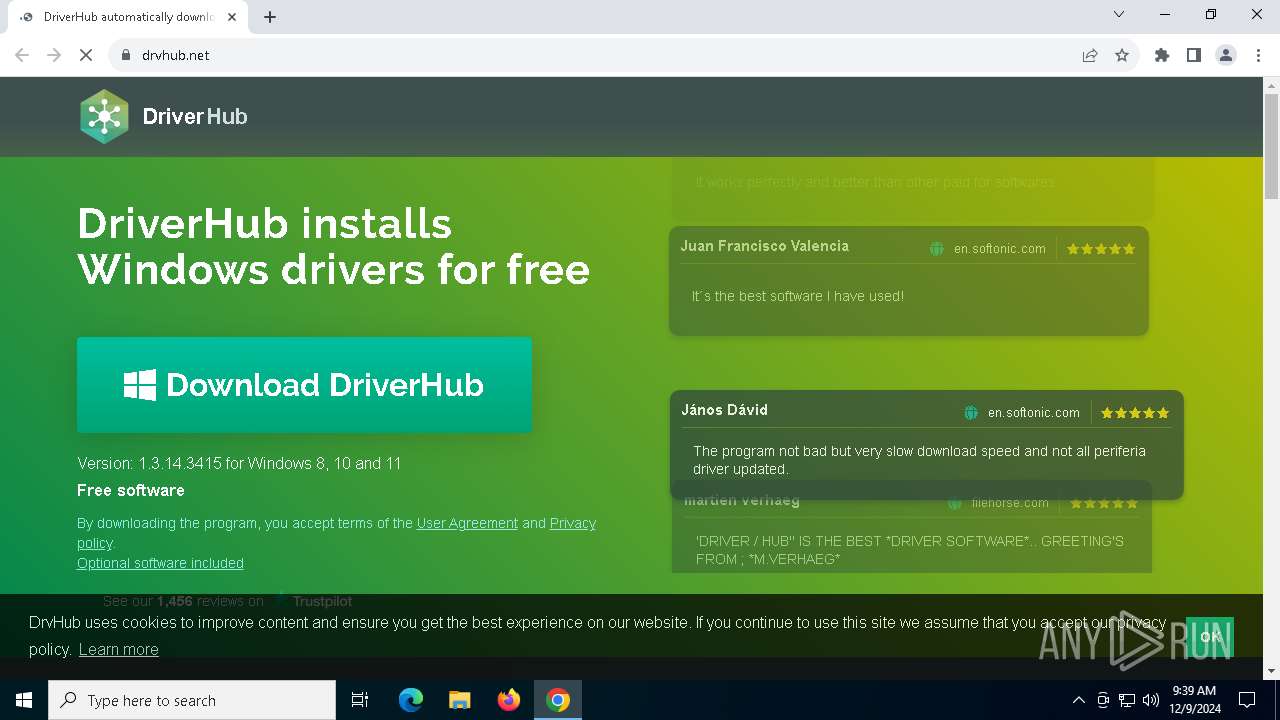
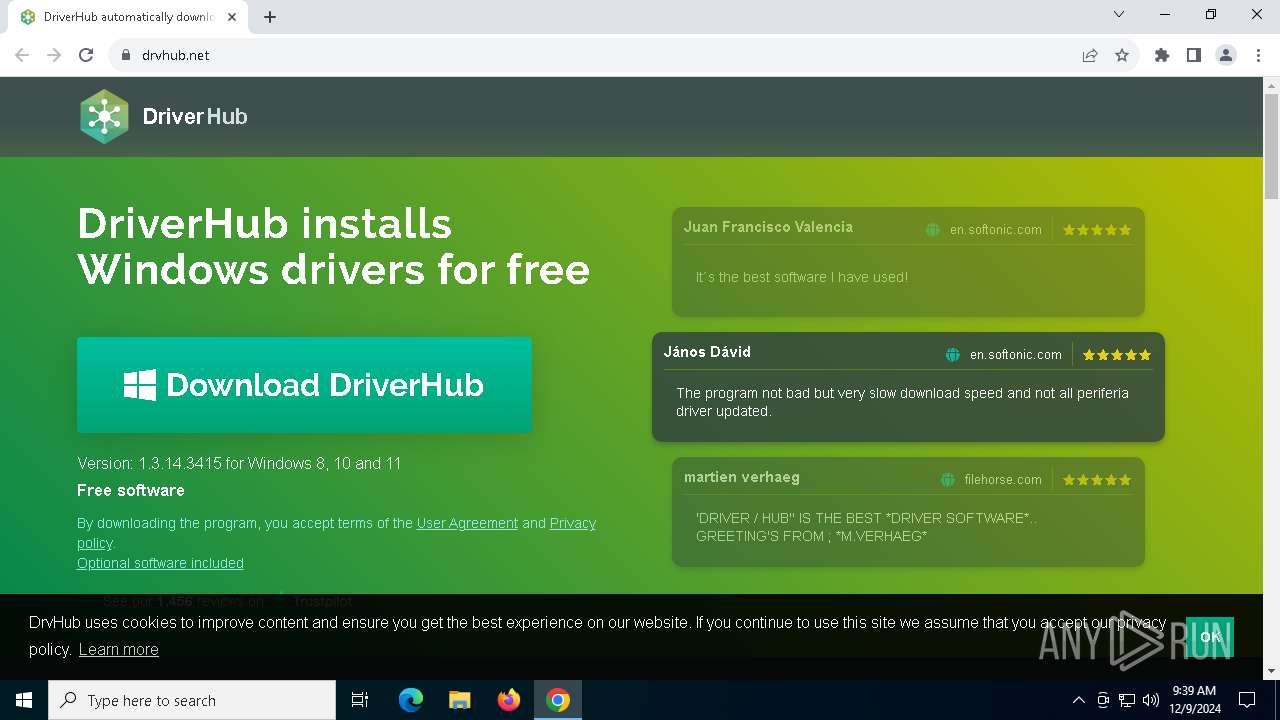
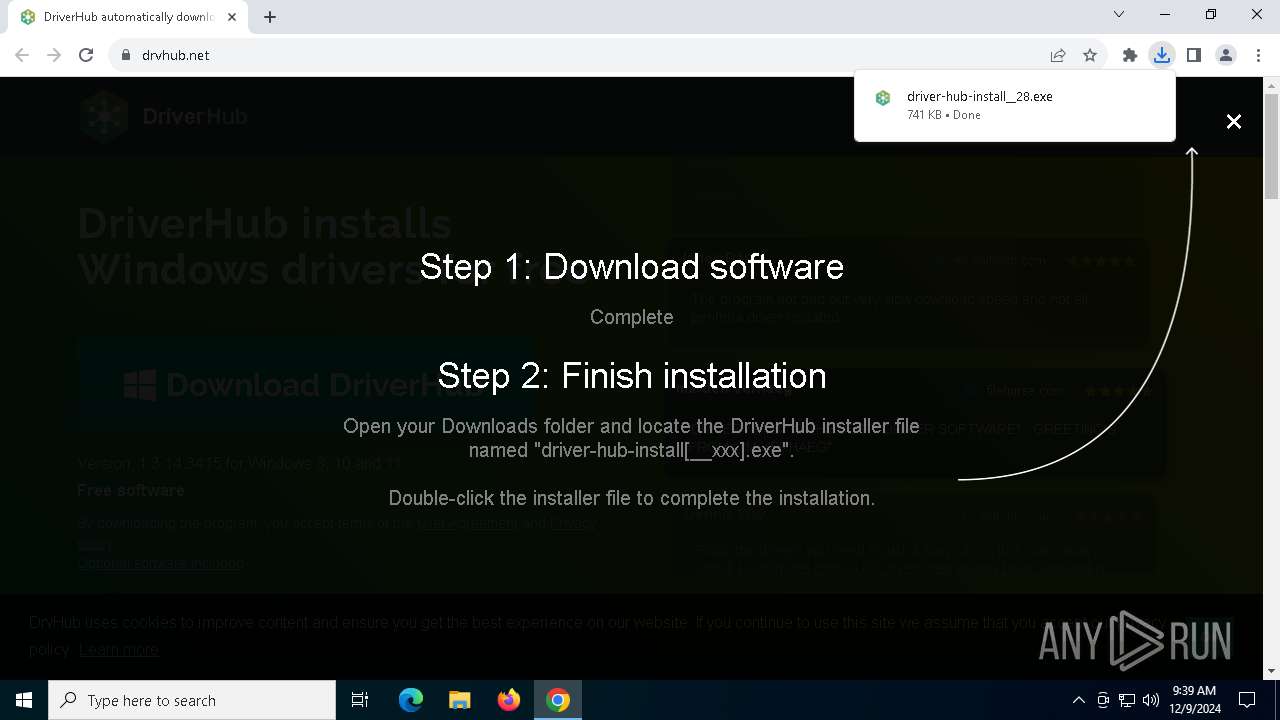
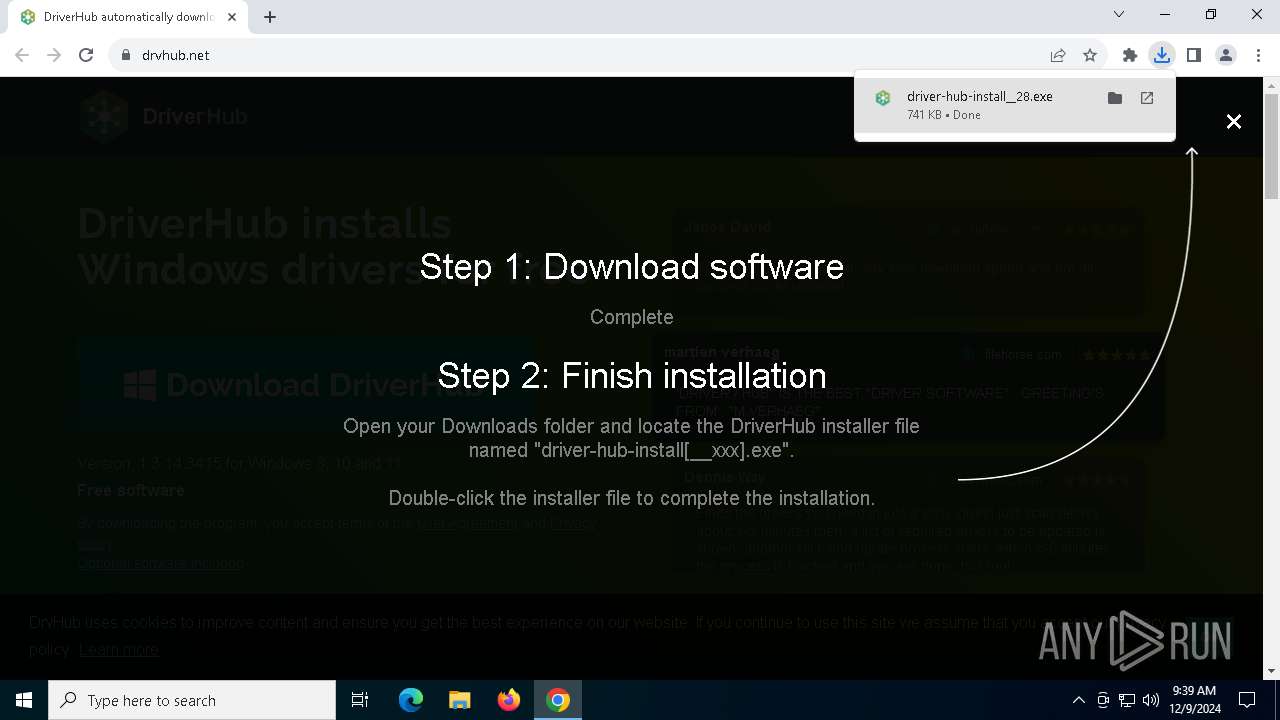
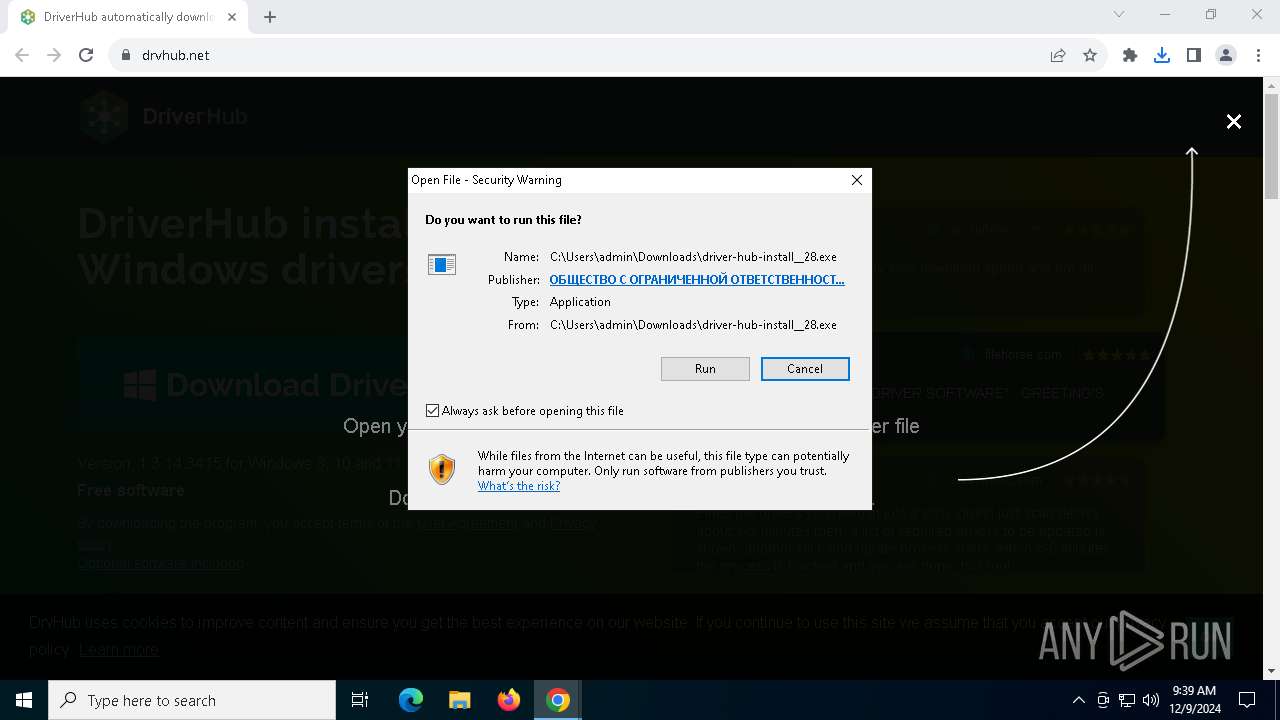
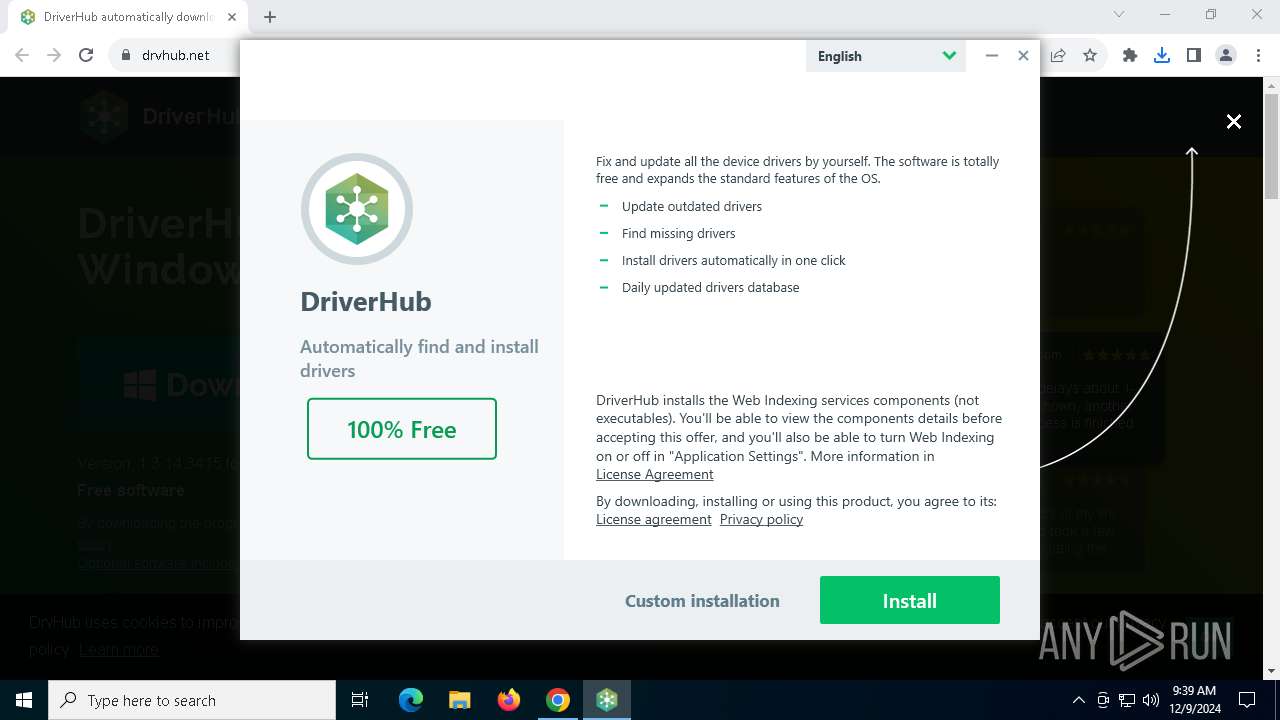
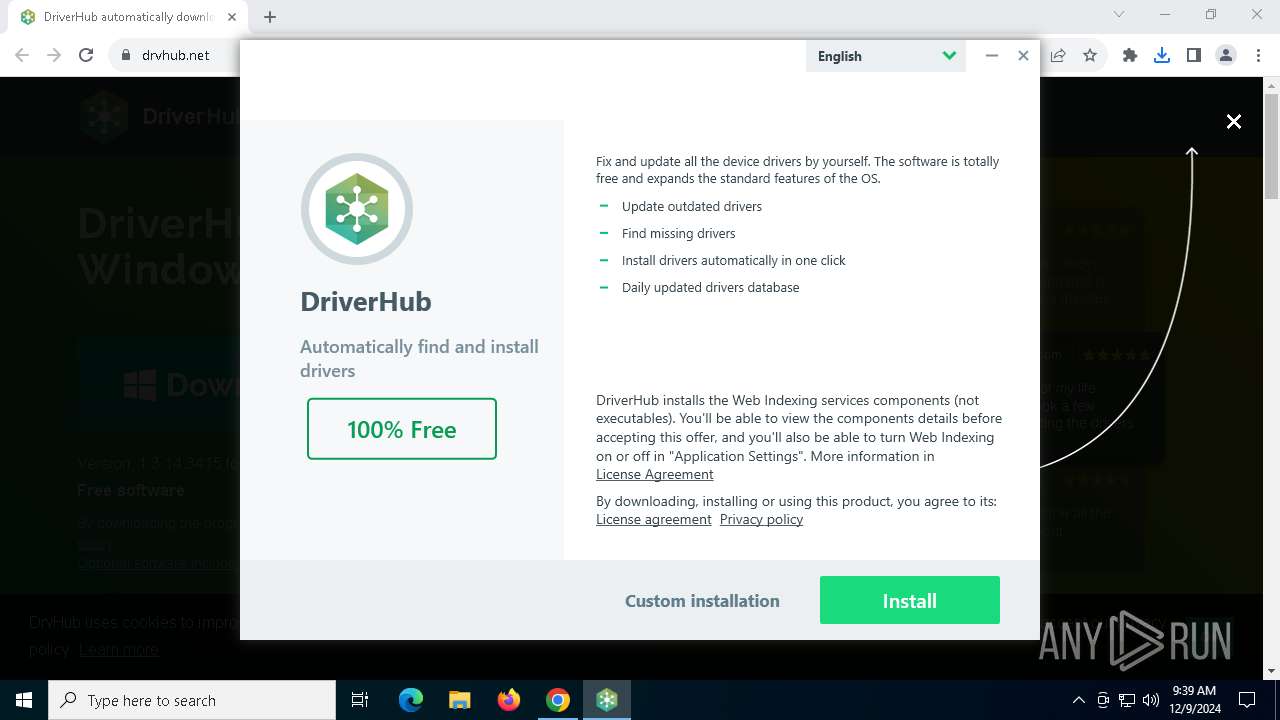
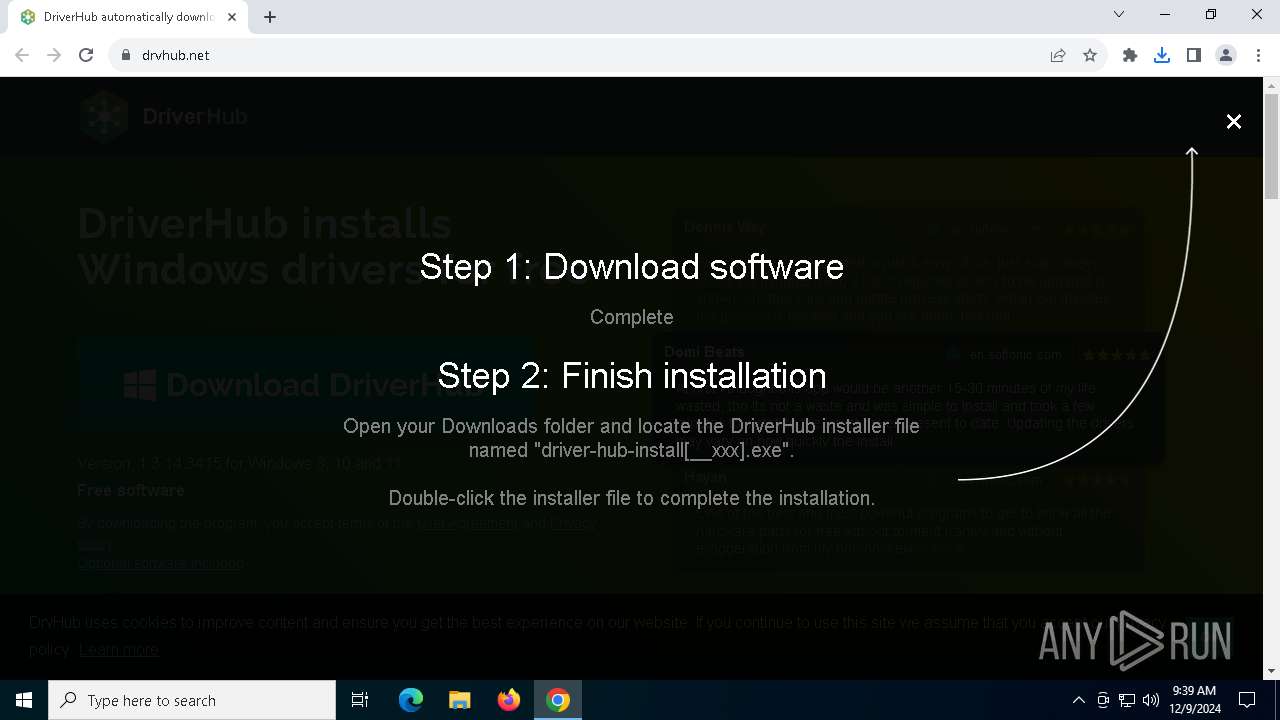
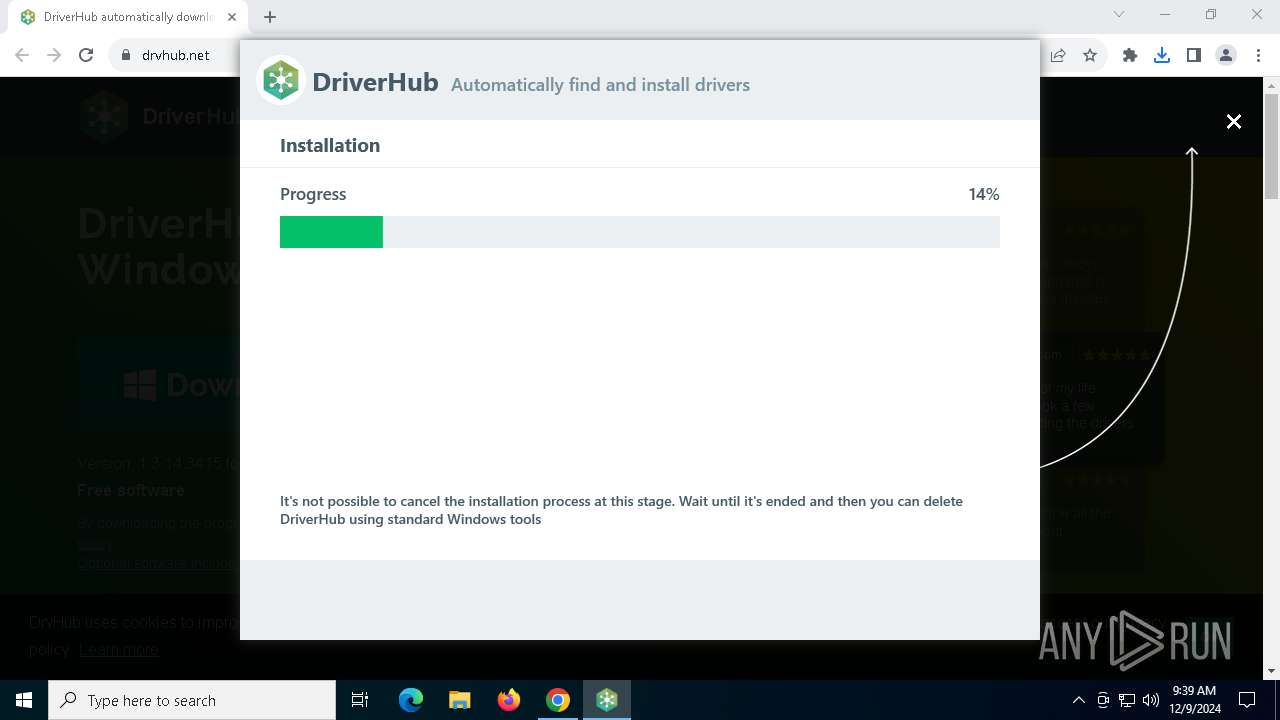
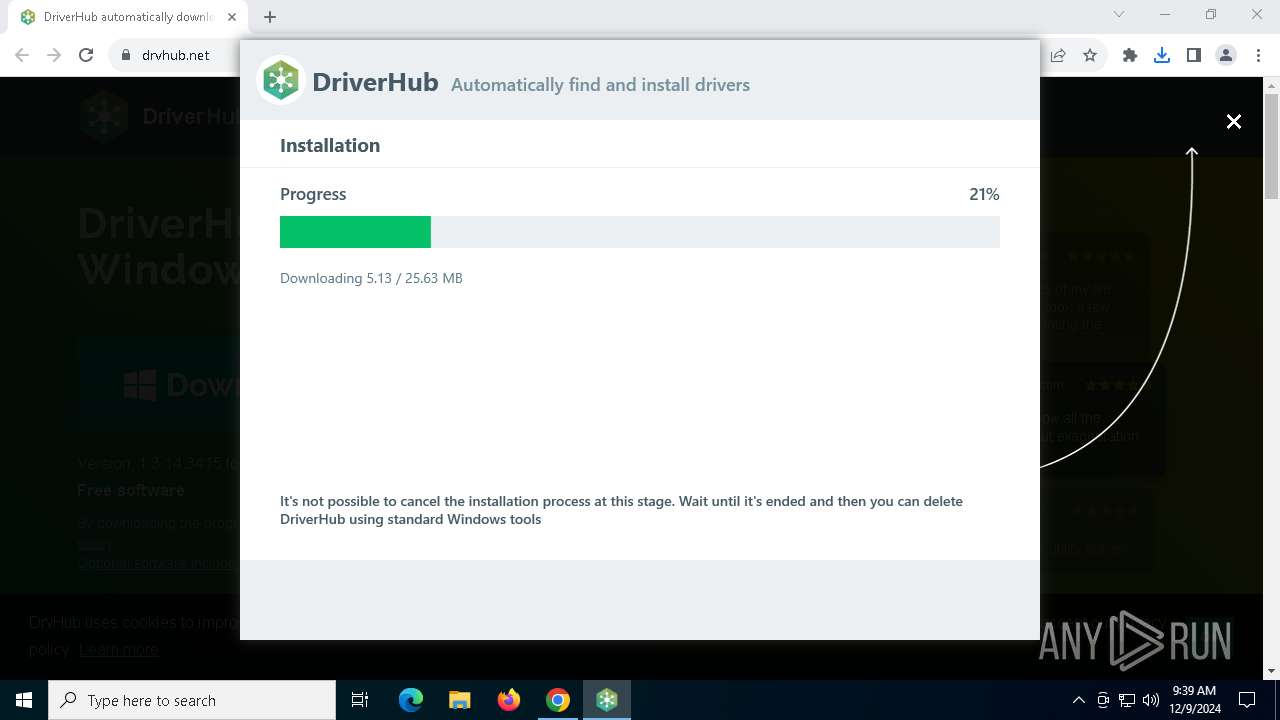
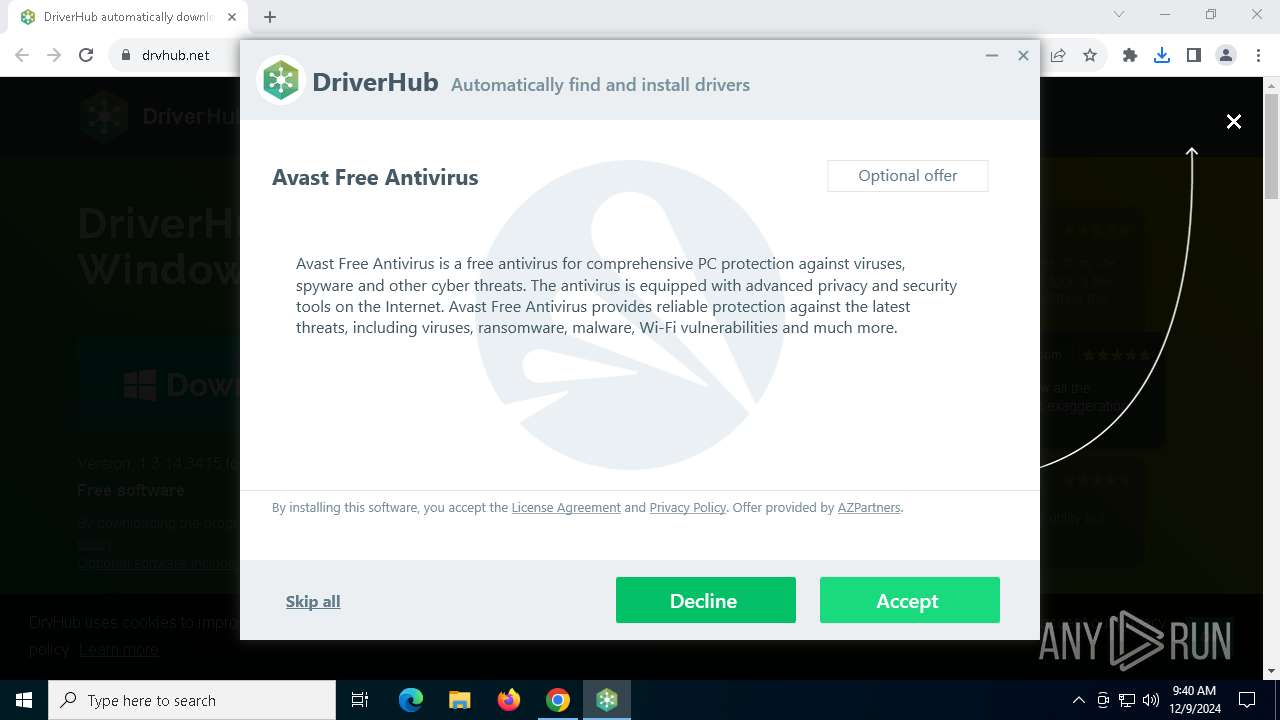
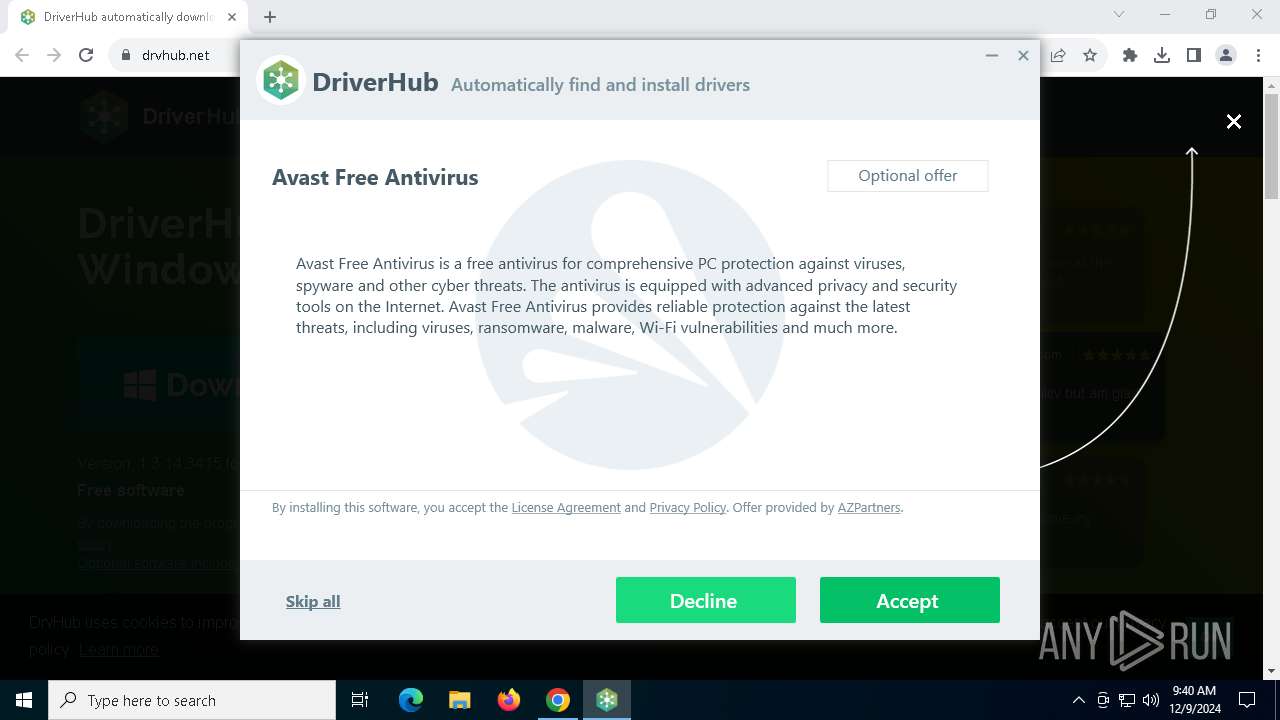
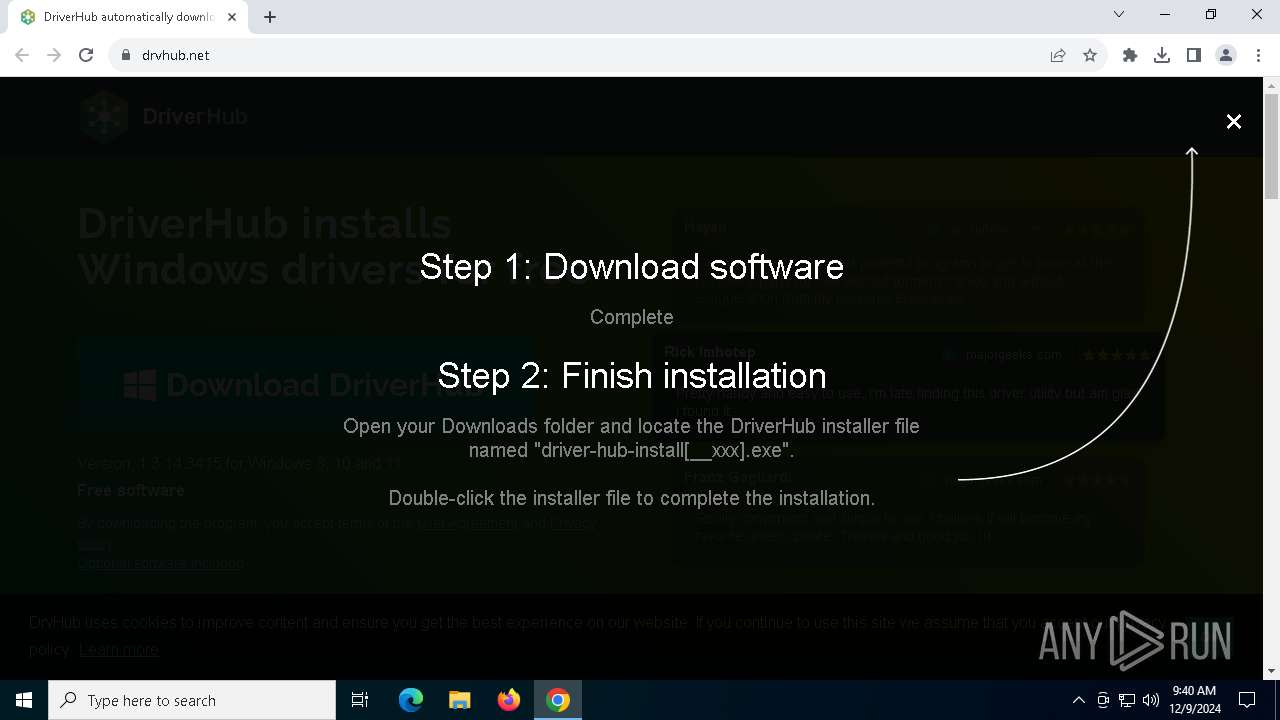
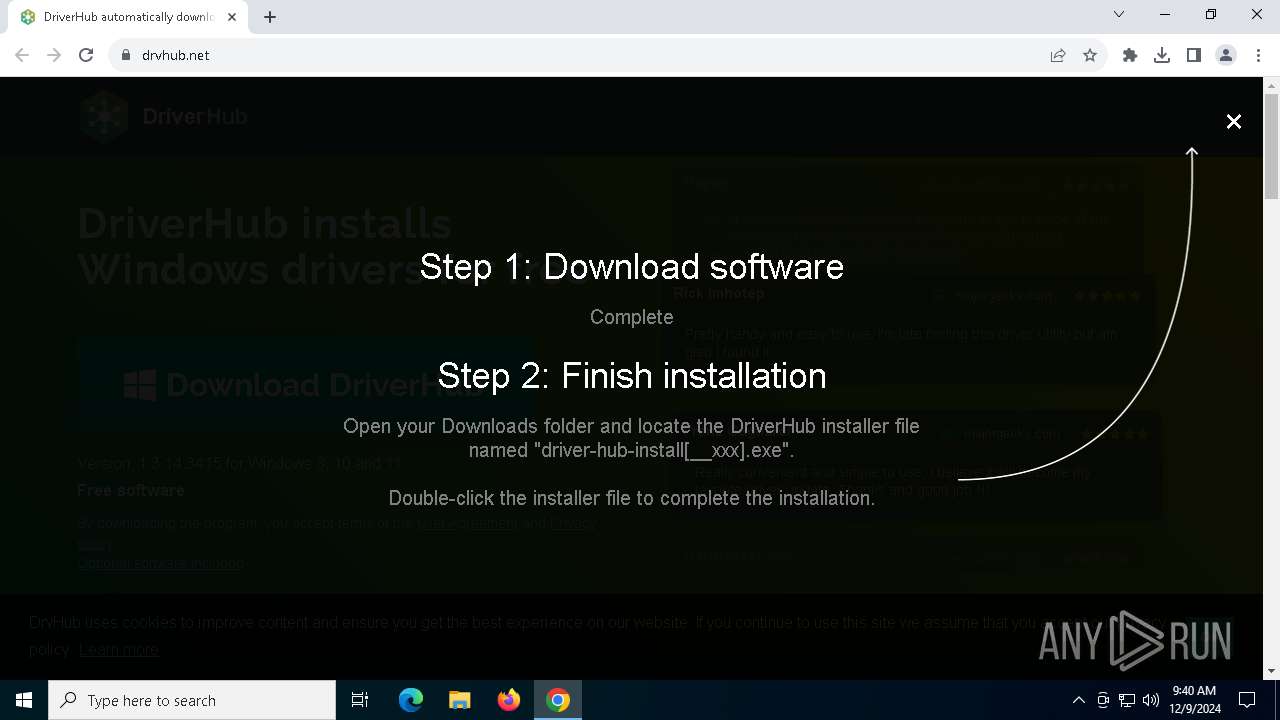
| URL: | https://www.drvhub.net |
| Full analysis: | https://app.any.run/tasks/77c789f9-a084-425b-b1cb-dafbf00fd471 |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2024, 09:39:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 735FB1C697778A6E4737882ABBAAED1B |
| SHA1: | 398F702078EB55C873FAB220DA0EFA88FF0375BB |
| SHA256: | 51D5FCF6F754EE5B821E50D42A2E47B121CFE5AA746A871AA712CB3CC3222BAF |
| SSDEEP: | 3:N8DSLFCoR:2OLFCoR |
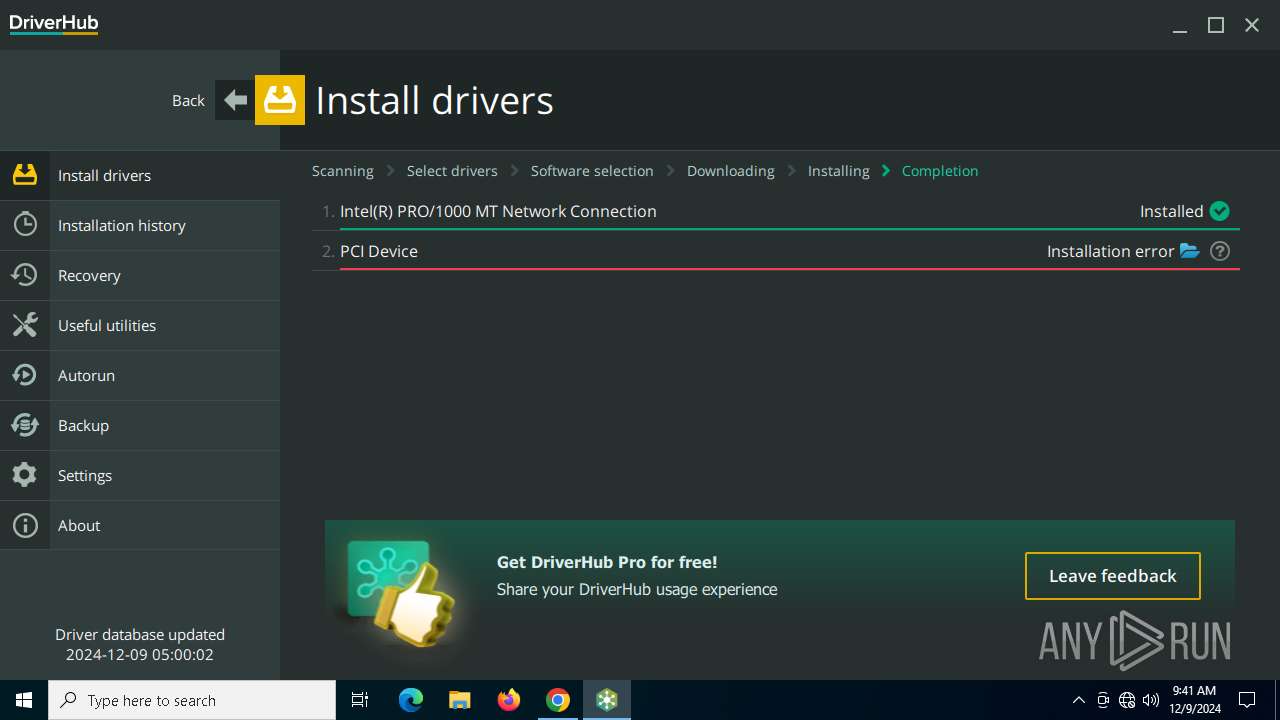
MALICIOUS
Changes the autorun value in the registry
- VC_redist.x86.exe (PID: 5340)
SUSPICIOUS
Reads security settings of Internet Explorer
- driver-hub-install__28.exe (PID: 5472)
- driver-hub-install__28.exe (PID: 5240)
- vcredist.exe (PID: 5268)
- VC_redist.x86.exe (PID: 5680)
- setup.exe (PID: 6172)
- DriverHub.exe (PID: 2280)
Searches for installed software
- driver-hub-install__28.exe (PID: 5472)
- VC_redist.x86.exe (PID: 5680)
- VC_redist.x86.exe (PID: 3052)
Process drops legitimate windows executable
- driver-hub-install__28.exe (PID: 5472)
- vcredist.exe (PID: 5320)
- vcredist.exe (PID: 5268)
- msiexec.exe (PID: 5036)
- VC_redist.x86.exe (PID: 3052)
- DriverHub.exe (PID: 2280)
- icarus.exe (PID: 1228)
- VC_redist.x86.exe (PID: 5340)
Application launched itself
- driver-hub-install__28.exe (PID: 5240)
- VC_redist.x86.exe (PID: 6960)
- VC_redist.x86.exe (PID: 5680)
- setup.exe (PID: 6172)
- setup.exe (PID: 1544)
Creates a software uninstall entry
- driver-hub-install__28.exe (PID: 5472)
- VC_redist.x86.exe (PID: 5340)
Executable content was dropped or overwritten
- driver-hub-install__28.exe (PID: 5472)
- vcredist.exe (PID: 5320)
- vcredist.exe (PID: 5268)
- VC_redist.x86.exe (PID: 5340)
- VC_redist.x86.exe (PID: 5680)
- VC_redist.x86.exe (PID: 3052)
- setup.exe (PID: 6340)
- OperaGXSetup.exe (PID: 1292)
- setup.exe (PID: 6172)
- setup.exe (PID: 4500)
- setup.exe (PID: 1544)
- avast_free_antivirus_setup_online.exe (PID: 6252)
- setup.exe (PID: 5972)
- avast_free_antivirus_online_setup.exe (PID: 1304)
- icarus.exe (PID: 6400)
- icarus.exe (PID: 1228)
- DriverHub.exe (PID: 2280)
- Installer.exe (PID: 7952)
- drvinst.exe (PID: 8024)
- drvinst.exe (PID: 8076)
- PDClient.exe (PID: 7552)
Starts a Microsoft application from unusual location
- vcredist.exe (PID: 5320)
- vcredist.exe (PID: 5268)
- VC_redist.x86.exe (PID: 5340)
Starts itself from another location
- vcredist.exe (PID: 5268)
- setup.exe (PID: 6172)
- icarus.exe (PID: 6400)
Executes as Windows Service
- VSSVC.exe (PID: 4308)
Checks Windows Trust Settings
- msiexec.exe (PID: 5036)
- setup.exe (PID: 6172)
- DriverHub.exe (PID: 2280)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5036)
The process drops C-runtime libraries
- msiexec.exe (PID: 5036)
- icarus.exe (PID: 1228)
Checks for external IP
- avast_free_antivirus_setup_online.exe (PID: 6252)
Connects to unusual port
- IndexingManager.exe (PID: 7656)
Drops a system driver (possible attempt to evade defenses)
- DriverHub.exe (PID: 2280)
- Installer.exe (PID: 7952)
- drvinst.exe (PID: 8024)
- drvinst.exe (PID: 8076)
Creates or modifies Windows services
- drvinst.exe (PID: 8076)
INFO
Reads the computer name
- driver-hub-install__28.exe (PID: 5240)
- driver-hub-install__28.exe (PID: 5472)
- VC_redist.x86.exe (PID: 3052)
- DriverHub.exe (PID: 2280)
- setup.exe (PID: 1544)
- icarus.exe (PID: 6400)
- icarus.exe (PID: 2392)
- icarus.exe (PID: 1228)
- PDClient.exe (PID: 7552)
Creates files in the program directory
- driver-hub-install__28.exe (PID: 5472)
- VC_redist.x86.exe (PID: 5340)
Checks supported languages
- driver-hub-install__28.exe (PID: 5472)
- driver-hub-install__28.exe (PID: 5240)
- vcredist.exe (PID: 5320)
- VC_redist.x86.exe (PID: 5340)
- VC_redist.x86.exe (PID: 5680)
- msiexec.exe (PID: 5036)
- VC_redist.x86.exe (PID: 3052)
- DriverHub.exe (PID: 2280)
- OperaGXSetup.exe (PID: 1292)
- setup.exe (PID: 6340)
- setup.exe (PID: 1544)
- avast_free_antivirus_online_setup.exe (PID: 1304)
- setup.exe (PID: 5972)
- icarus.exe (PID: 6400)
- icarus.exe (PID: 2392)
- icarus.exe (PID: 1228)
- PDClient.exe (PID: 7448)
- PDClient.exe (PID: 7552)
- Installer.exe (PID: 7952)
- drvinst.exe (PID: 8024)
- drvinst.exe (PID: 8076)
Executable content was dropped or overwritten
- chrome.exe (PID: 5488)
- msiexec.exe (PID: 5036)
Reads the machine GUID from the registry
- driver-hub-install__28.exe (PID: 5240)
- VC_redist.x86.exe (PID: 5340)
- msiexec.exe (PID: 5036)
- driver-hub-install__28.exe (PID: 5472)
- setup.exe (PID: 6172)
- avast_free_antivirus_setup_online.exe (PID: 6252)
- DriverHub.exe (PID: 2280)
- icarus.exe (PID: 6400)
- icarus.exe (PID: 2392)
- icarus.exe (PID: 1228)
- PDClient.exe (PID: 7448)
- PDClient.exe (PID: 7552)
Process checks computer location settings
- driver-hub-install__28.exe (PID: 5240)
- DriverHub.exe (PID: 2280)
Checks proxy server information
- driver-hub-install__28.exe (PID: 5472)
- avast_free_antivirus_online_setup.exe (PID: 1304)
- setup.exe (PID: 6172)
- DriverHub.exe (PID: 2280)
- icarus.exe (PID: 6400)
The process uses the downloaded file
- chrome.exe (PID: 5488)
- chrome.exe (PID: 2144)
Application launched itself
- chrome.exe (PID: 5488)
Reads the software policy settings
- driver-hub-install__28.exe (PID: 5472)
- msiexec.exe (PID: 5036)
- avast_free_antivirus_online_setup.exe (PID: 1304)
- setup.exe (PID: 6172)
- DriverHub.exe (PID: 2280)
- PDClient.exe (PID: 7552)
- Installer.exe (PID: 7952)
Manages system restore points
- SrTasks.exe (PID: 4264)
Create files in a temporary directory
- driver-hub-install__28.exe (PID: 5472)
- VC_redist.x86.exe (PID: 5680)
- OperaGXSetup.exe (PID: 1292)
- setup.exe (PID: 6340)
Sends debugging messages
- DriverHub.exe (PID: 2280)
- icarus.exe (PID: 1228)
- icarus.exe (PID: 6400)
Creates files or folders in the user directory
- DriverHub.exe (PID: 2280)
- setup.exe (PID: 6340)
Reads CPU info
- icarus.exe (PID: 2392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
189
Monitored processes
49
Malicious processes
16
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1228 | C:\WINDOWS\Temp\asw-6ae35a9c-a4af-4006-a83e-3db97334e9e5\avast-av\icarus.exe /silent /WS /cookie:mmm_mrk_ppi_004_408_v /edat_dir:C:\WINDOWS\Temp\asw.11bbc9cbd8e1947a /geo:DE /track-guid:f6d1cf22-9e54-4865-a968-85deab9ad08e /er_master:master_ep_4c612e54-f48a-43c6-be40-647190632acf /er_ui:ui_ep_1089cbf4-4d06-4b5c-92a4-2a879a86c44b /er_slave:avast-av_slave_ep_74bd7d9f-3ebc-4e2a-9fcf-6259cb0df405 /slave:avast-av | C:\Windows\Temp\asw-6ae35a9c-a4af-4006-a83e-3db97334e9e5\avast-av\icarus.exe | icarus.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: Avast Installer Exit code: 45003 Version: 24.11.8270.0 Modules
| |||||||||||||||
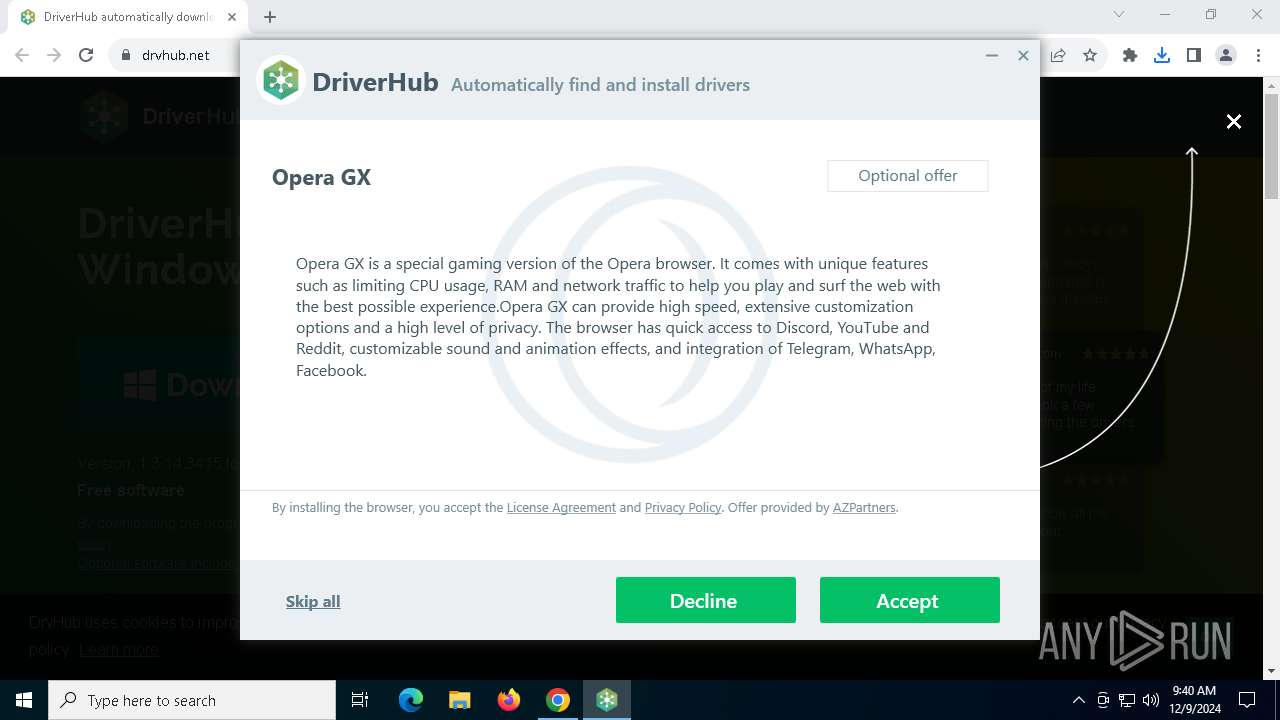
| 1292 | "C:\Users\admin\AppData\Local\Temp\DriverHub\OperaGXSetup.exe" --silent --allusers=0 | C:\Users\admin\AppData\Local\Temp\DriverHub\OperaGXSetup.exe | driver-hub-install__28.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Opera installer SFX Version: 114.0.5282.248 Modules
| |||||||||||||||
| 1304 | "C:\WINDOWS\Temp\asw.11bbc9cbd8e1947a\avast_free_antivirus_online_setup.exe" /silent /WS /cookie:mmm_mrk_ppi_004_408_v /ga_clientid:f6d1cf22-9e54-4865-a968-85deab9ad08e /edat_dir:C:\WINDOWS\Temp\asw.11bbc9cbd8e1947a /geo:DE | C:\Windows\Temp\asw.11bbc9cbd8e1947a\avast_free_antivirus_online_setup.exe | avast_free_antivirus_setup_online.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: Avast Self-Extract Package Exit code: 45003 Version: 24.11.8270.0 Modules
| |||||||||||||||
| 1400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | "C:\Users\admin\AppData\Local\Temp\7zSC0553D14\setup.exe" --backend --install --import-browser-data=0 --enable-stats=1 --enable-installer-stats=1 --consent-given=0 --general-interests=0 --general-location=0 --personalized-content=0 --personalized-ads=0 --vought_browser=0 --launchopera=1 --installfolder="C:\Users\admin\AppData\Local\Programs\Opera GX" --profile-folder --language=en --singleprofile=0 --copyonly=0 --allusers=0 --setdefaultbrowser=1 --pintotaskbar=1 --pintostartmenu=1 --run-at-startup=1 --server-tracking-data=server_tracking_data --initial-pid=6172 --package-dir-prefix="C:\Users\admin\AppData\Local\Temp\.opera\Opera GX Installer Temp\opera_package_20241209094023" --session-guid=be74ce96-5ae2-4a2e-9446-a08f17c522dc --server-tracking-blob=NzRkYTYxOWRhMjgxMjMzOWQ4Zjg5ZjczYmE1Y2U3ZjRmMmY5NTI4MDE1M2NmMjczNjczZGU2ZjJlYTU3YjI0Yzp7ImNvdW50cnkiOiJVUyIsImVkaXRpb24iOiJzdGQtMiIsImluc3RhbGxlcl9uYW1lIjoiT3BlcmFHWFNldHVwLmV4ZSIsInByb2R1Y3QiOnsibmFtZSI6Im9wZXJhX2d4In0sInF1ZXJ5IjoiL29wZXJhX2d4L3N0YWJsZS9lZGl0aW9uL3N0ZC0yP3V0bV9zb3VyY2U9UFdOZ2FtZXMmdXRtX21lZGl1bT1wYSZ1dG1fY2FtcGFpZ249UFdOX0RFX1BCNV8zODQ5JnV0bV9pZD1jM2M0NjU2NjI0MDY0MTk5YWE5YjIxNWQ0ZjRjMzkwOSZ1dG1fY29udGVudD0zODQ5X29wZ3g1Iiwic3lzdGVtIjp7InBsYXRmb3JtIjp7ImFyY2giOiJ4ODZfNjQiLCJvcHN5cyI6IldpbmRvd3MiLCJvcHN5cy12ZXJzaW9uIjoiMTAiLCJwYWNrYWdlIjoiRVhFIn19LCJ0aW1lc3RhbXAiOiIxNzMzNzM3MjIxLjE5NTMiLCJ1c2VyYWdlbnQiOiJEcml2ZXJIdWJJbnN0YWxsZXIvNC4wLjciLCJ1dG0iOnsiY2FtcGFpZ24iOiJQV05fREVfUEI1XzM4NDkiLCJjb250ZW50IjoiMzg0OV9vcGd4NSIsImlkIjoiYzNjNDY1NjYyNDA2NDE5OWFhOWIyMTVkNGY0YzM5MDkiLCJtZWRpdW0iOiJwYSIsInNvdXJjZSI6IlBXTmdhbWVzIn0sInV1aWQiOiI0Mzk2NjRhNy1mM2MyLTQwMjctOGI5MC1hNGI1MzQwMWZkZjcifQ== --silent --desktopshortcut=1 --wait-for-package --initial-proc-handle=0806000000000000 | C:\Users\admin\AppData\Local\Temp\7zSC0553D14\setup.exe | setup.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera GX Installer Version: 114.0.5282.248 Modules
| |||||||||||||||
| 2144 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5060 --field-trial-handle=1848,i,3534136398208161544,12392145471890641840,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2280 | "C:\Program Files (x86)\DriverHub\DriverHub.exe" | C:\Program Files (x86)\DriverHub\DriverHub.exe | driver-hub-install__28.exe | ||||||||||||
User: admin Company: ROSTPAY LTD Integrity Level: HIGH Description: DriverHub Version: 1.3.14.3415 Modules
| |||||||||||||||
| 2392 | C:\WINDOWS\Temp\asw-6ae35a9c-a4af-4006-a83e-3db97334e9e5\avast-av-vps\icarus.exe /silent /WS /cookie:mmm_mrk_ppi_004_408_v /edat_dir:C:\WINDOWS\Temp\asw.11bbc9cbd8e1947a /geo:DE /track-guid:f6d1cf22-9e54-4865-a968-85deab9ad08e /er_master:master_ep_4c612e54-f48a-43c6-be40-647190632acf /er_ui:ui_ep_1089cbf4-4d06-4b5c-92a4-2a879a86c44b /er_slave:avast-av-vps_slave_ep_391a96da-96c4-4e70-b6c1-34e6a8d1be3e /slave:avast-av-vps | C:\Windows\Temp\asw-6ae35a9c-a4af-4006-a83e-3db97334e9e5\avast-av-vps\icarus.exe | — | icarus.exe | |||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: Avast Installer Exit code: 44100 Version: 24.11.8270.0 Modules
| |||||||||||||||
| 3052 | "C:\ProgramData\Package Cache\{410c0ee1-00bb-41b6-9772-e12c2828b02f}\VC_redist.x86.exe" -q -burn.elevated BurnPipe.{B0CD2592-13F2-4A88-891B-F7CC2AAB2196} {8DF0A275-DF85-49E7-AF9C-85951DE65E05} 5680 | C:\ProgramData\Package Cache\{410c0ee1-00bb-41b6-9772-e12c2828b02f}\VC_redist.x86.exe | VC_redist.x86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x86) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 Modules
| |||||||||||||||
| 3420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5048 --field-trial-handle=1848,i,3534136398208161544,12392145471890641840,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
52 825
Read events
51 514
Write events
1 028
Delete events
283
Modification events
| (PID) Process: | (5488) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5488) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5488) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5488) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5488) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2144) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000E6D869361E4ADB01 | |||
| (PID) Process: | (5240) driver-hub-install__28.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\CTF\CUAS\DefaultCompositionWindow |
| Operation: | write | Name: | Left |
Value: 0 | |||
| (PID) Process: | (5240) driver-hub-install__28.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\CTF\CUAS\DefaultCompositionWindow |
| Operation: | write | Name: | Top |
Value: 0 | |||
| (PID) Process: | (5472) driver-hub-install__28.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\driver-hub-install__28_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5472) driver-hub-install__28.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\driver-hub-install__28_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
429
Suspicious files
833
Text files
739
Unknown types
163
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF13610f.TMP | — | |
MD5:— | SHA256:— | |||
| 5488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF13610f.TMP | — | |
MD5:— | SHA256:— | |||
| 5488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF13611e.TMP | — | |
MD5:— | SHA256:— | |||
| 5488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF13611e.TMP | — | |
MD5:— | SHA256:— | |||
| 5488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF13611e.TMP | — | |
MD5:— | SHA256:— | |||
| 5488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
142
DNS requests
130
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3884 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3884 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | chrome.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
5488 | chrome.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDBZjZSSeLnNdLOOoGg%3D%3D | unknown | — | — | whitelisted |
6348 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2148 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1684 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
3884 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3884 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.166:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1076 | svchost.exe | 23.32.186.57:443 | go.microsoft.com | AKAMAI-AS | BR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.drvhub.net |
| whitelisted |
accounts.google.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6572 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6572 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6572 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6572 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
6252 | avast_free_antivirus_setup_online.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
DriverHub.exe | qrc:/main.qml:655:13: QML Connections: Implicitly defined onFoo properties in Connections are deprecated. Use this syntax instead: function onFoo(<arguments>) { ... }
|
DriverHub.exe | qrc:/UpdateProgressDialog.qml:11:5: QML Connections: Implicitly defined onFoo properties in Connections are deprecated. Use this syntax instead: function onFoo(<arguments>) { ... }
|
DriverHub.exe | qrc:/main.qml:453:31: QML ItemDelegate: Binding loop detected for property "height"
|
DriverHub.exe | file:///C:/Program Files (x86)/DriverHub/QtQuick/Dialogs/DefaultFileDialog.qml:102:33: QML Settings: The following application identifiers have not been set: QVector("organizationName", "organizationDomain")
|
DriverHub.exe | file:///C:/Program Files (x86)/DriverHub/QtQuick/Dialogs/DefaultFileDialog.qml:102:33: QML Settings: Failed to initialize QSettings instance. Status code is: 1
|
DriverHub.exe | qrc:/SettingsPage.qml:47:9: QML MyCheckBox: Binding loop detected for property "width"
|
DriverHub.exe | qrc:/SettingsPage.qml:47:9: QML MyCheckBox: Binding loop detected for property "width"
|
DriverHub.exe | qrc:/SettingsPage.qml:29:9: QML MyCheckBox: Binding loop detected for property "width"
|
DriverHub.exe | qrc:/SettingsPage.qml:47:9: QML MyCheckBox: Binding loop detected for property "width"
|
DriverHub.exe | qrc:/SettingsPage.qml:29:9: QML MyCheckBox: Binding loop detected for property "width"
|