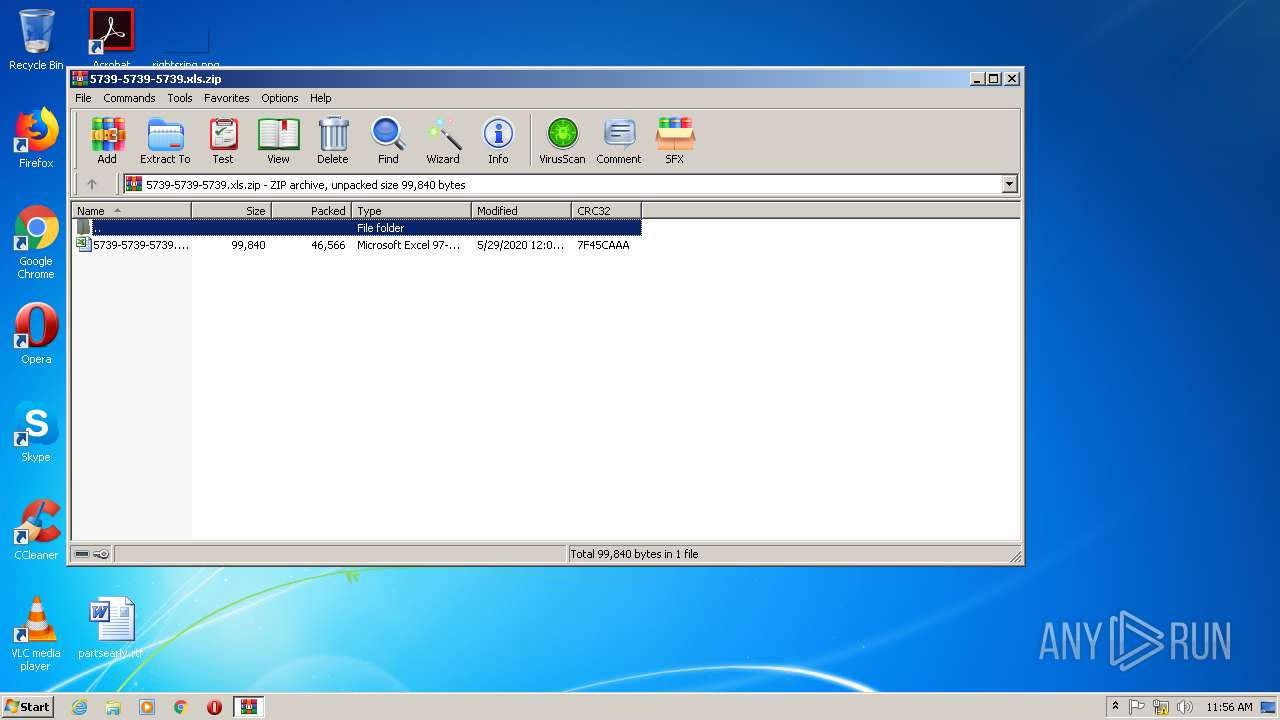
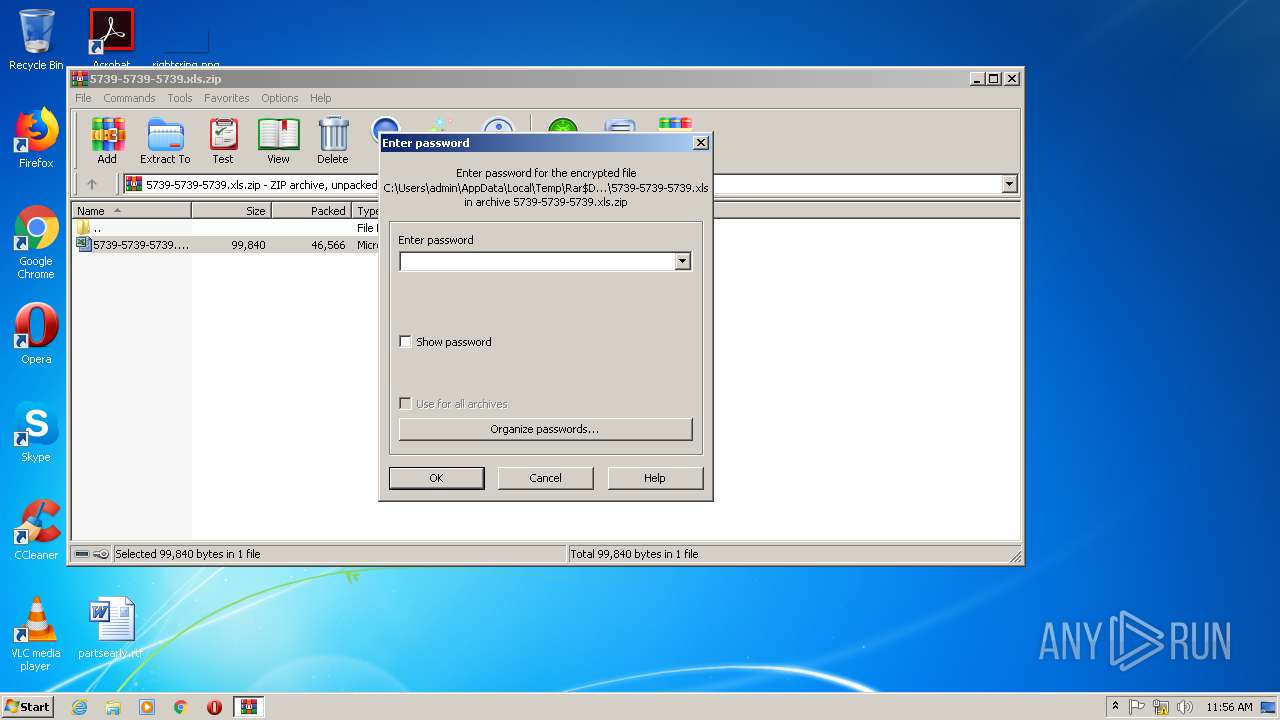
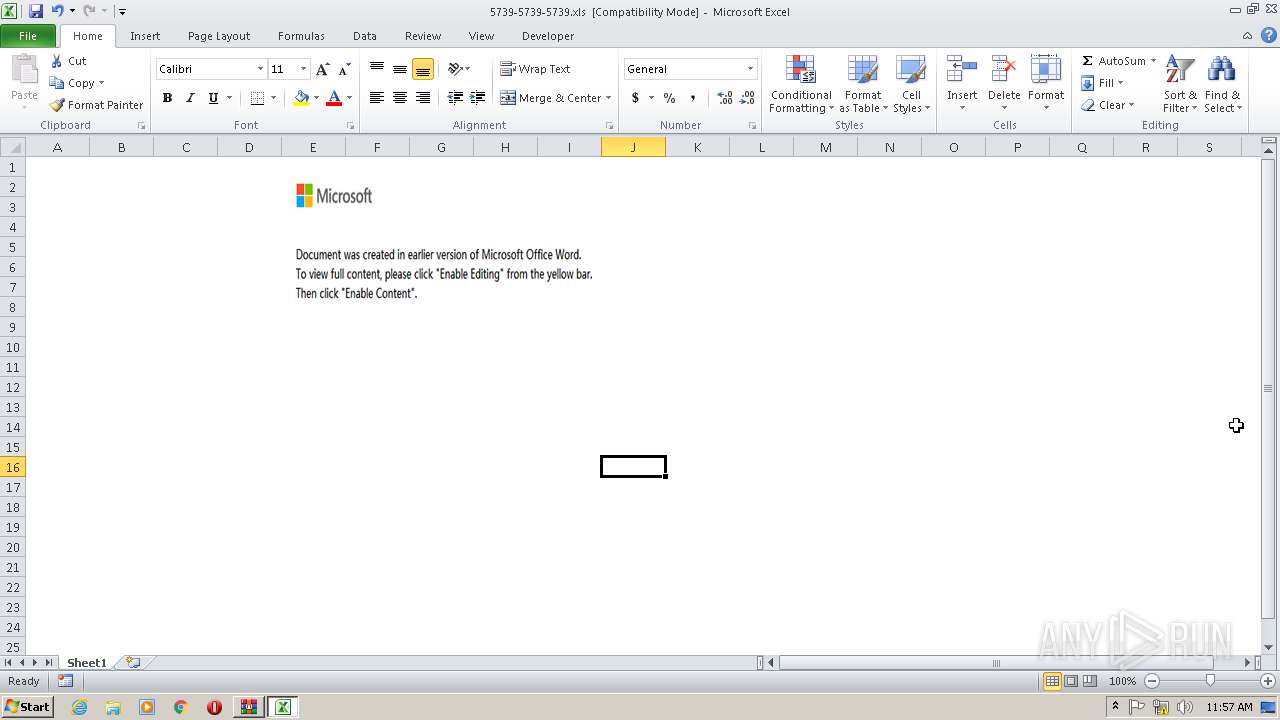
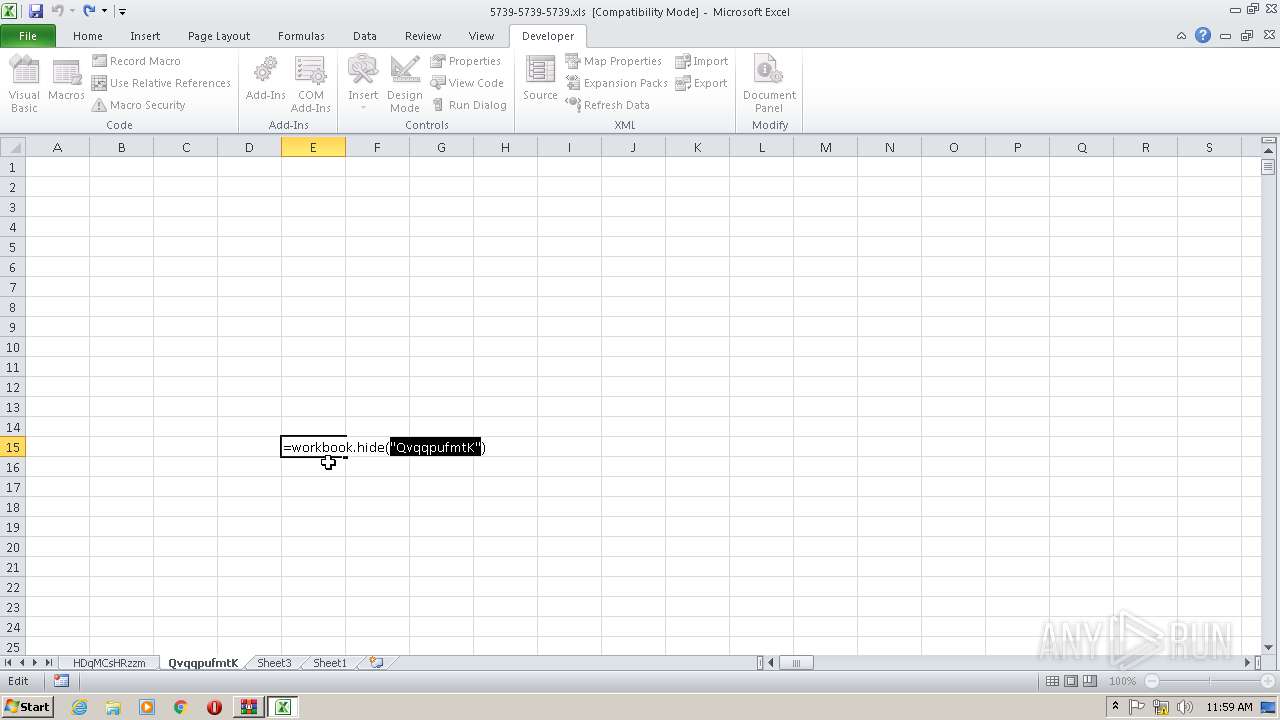
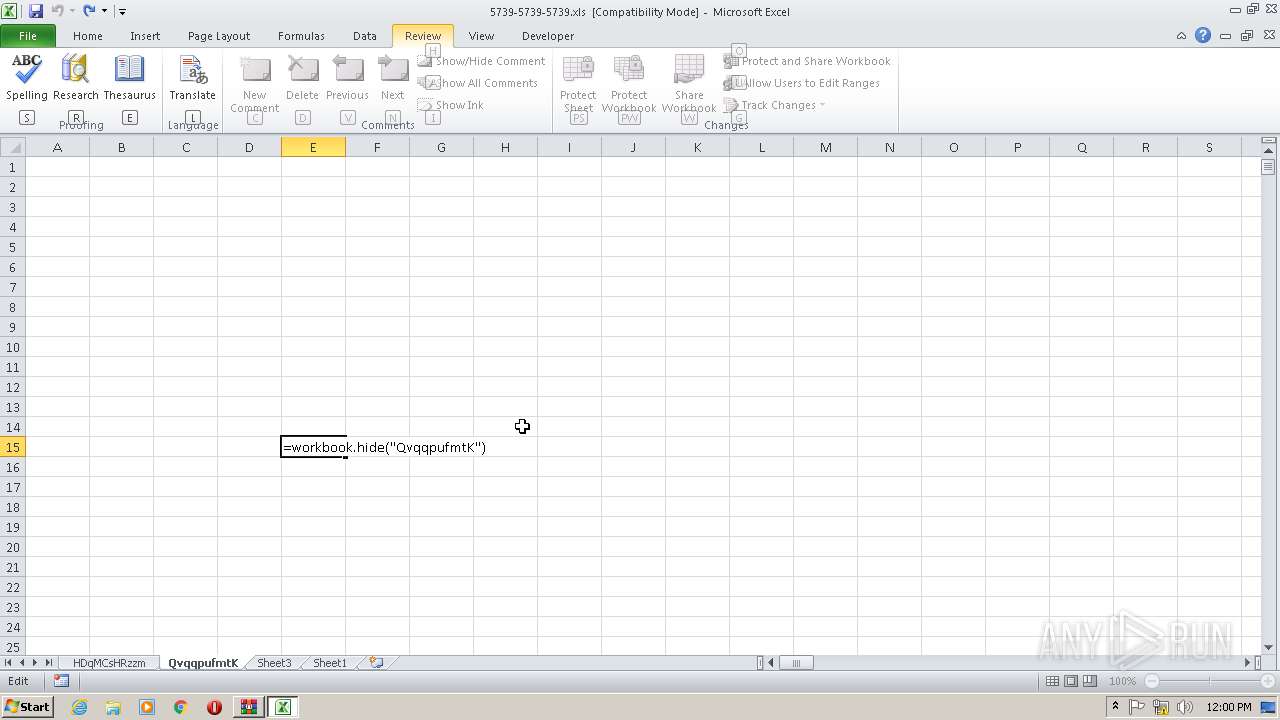
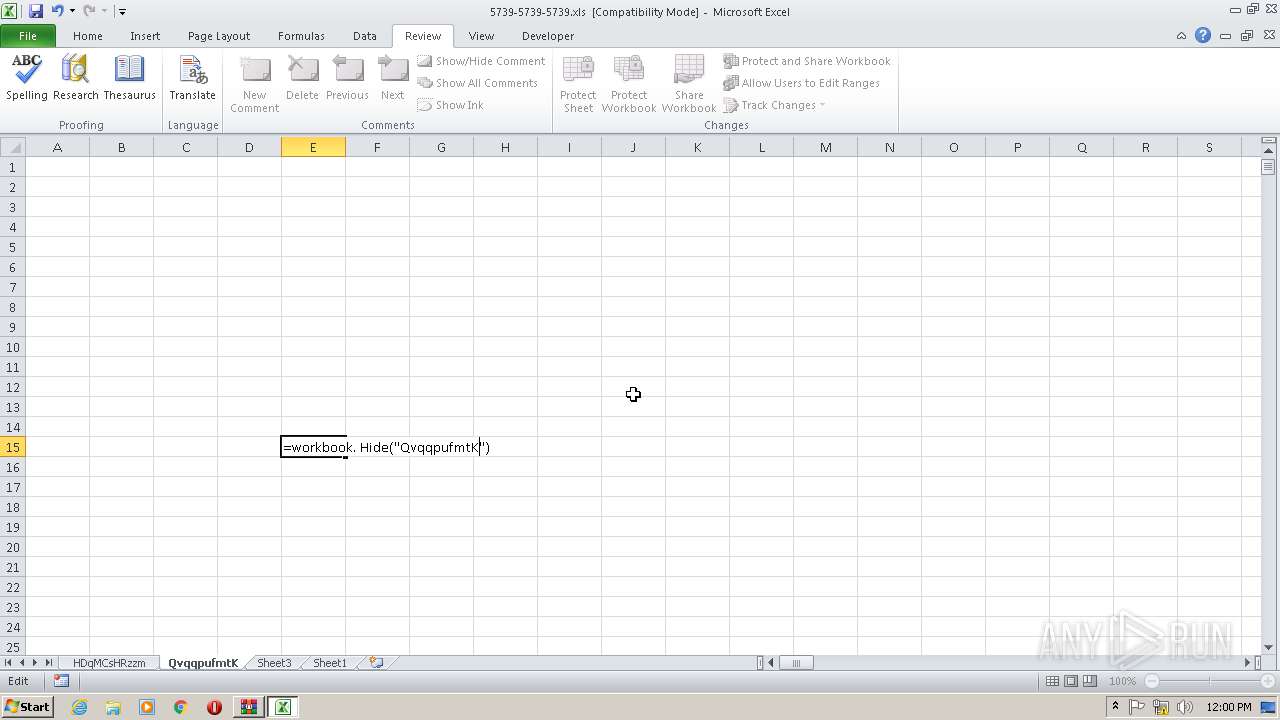
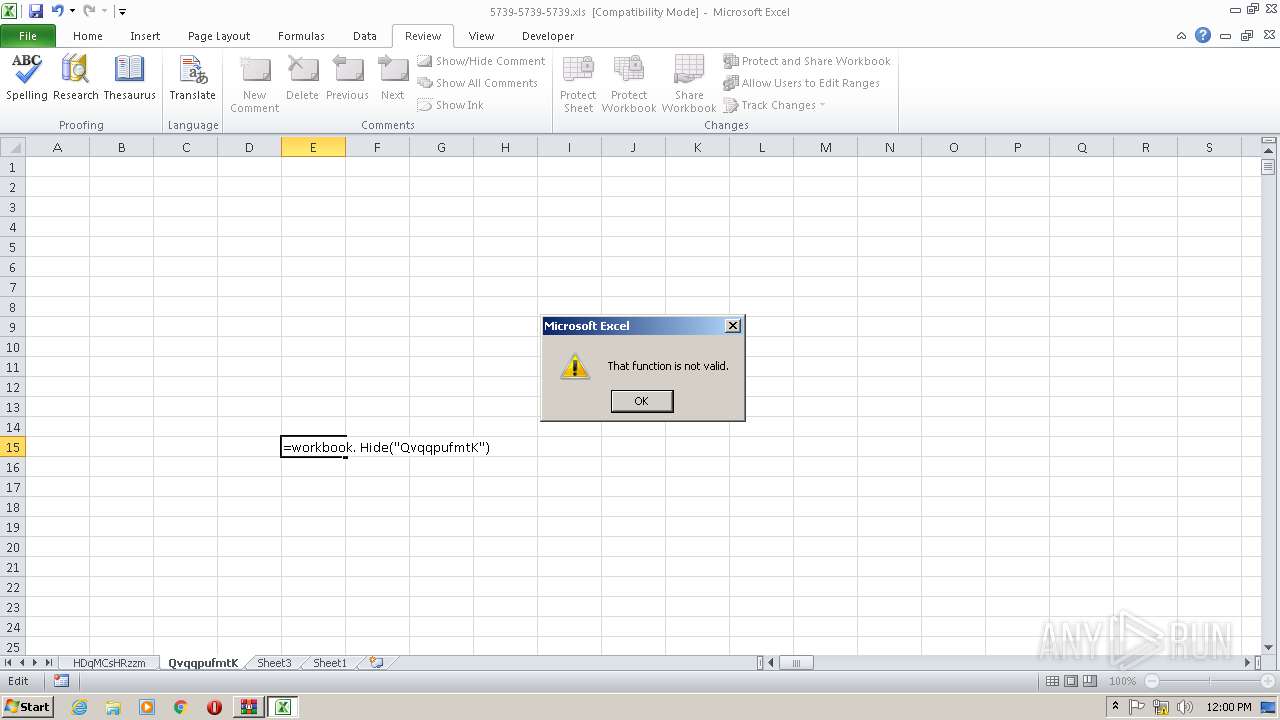
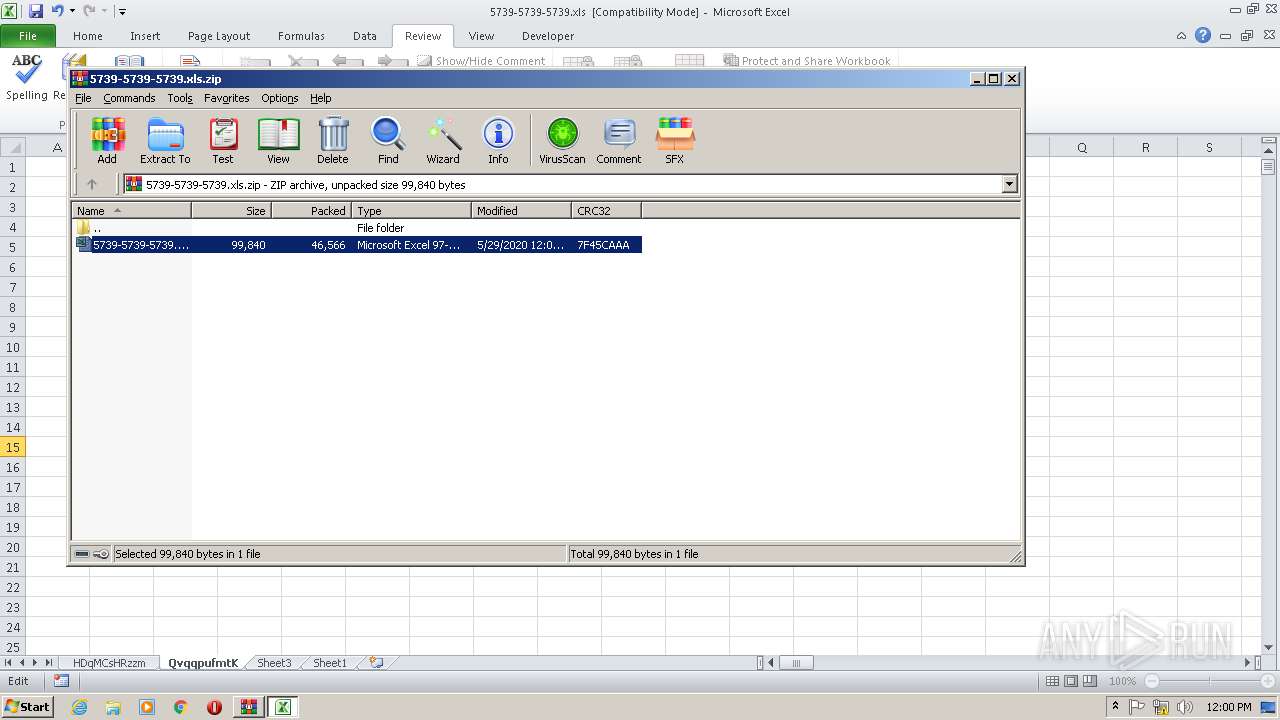
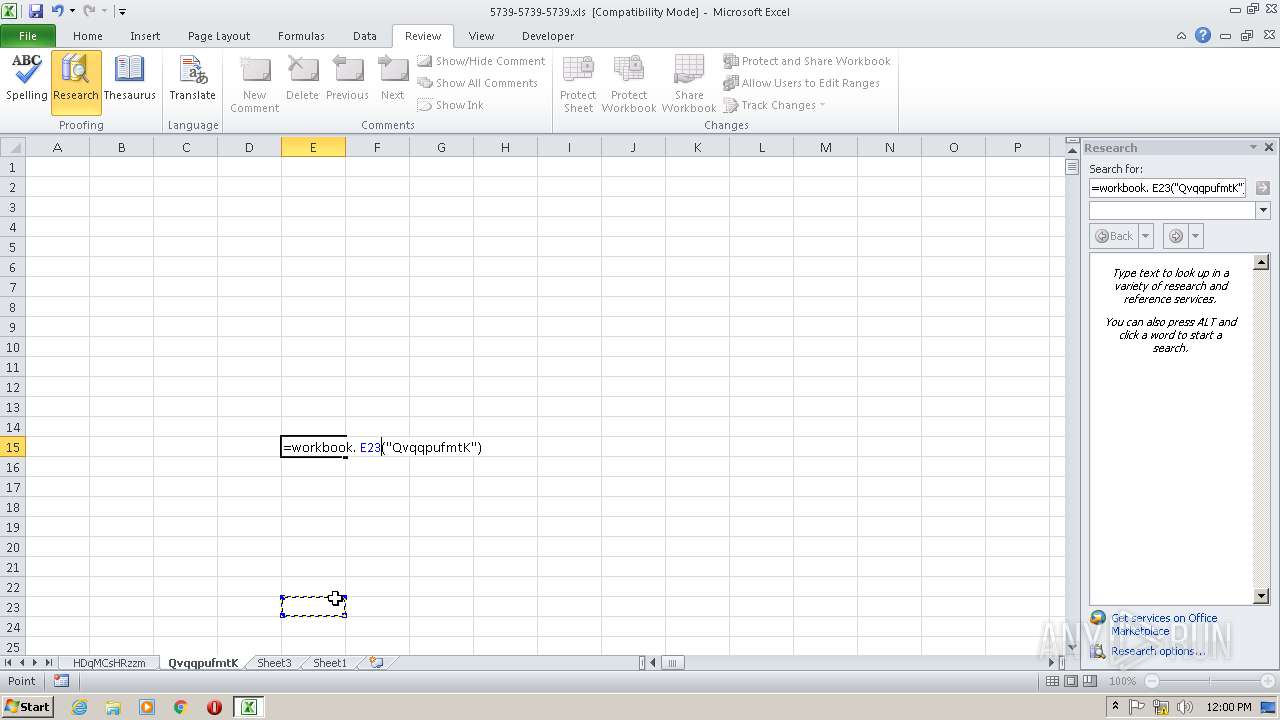
| File name: | 5739-5739-5739.xls.zip |
| Full analysis: | https://app.any.run/tasks/89d09250-05e5-4145-9c4f-fc8c288471d6 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 30, 2020, 10:56:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | EC7988488BAC99DA468307696B910BF7 |
| SHA1: | 7AF28481F30FA37BAEE5AAFBDED045D81EB8E1E5 |
| SHA256: | 51A0EF23467136D86F68FE60F45BEA54B69AB95C41B8D13A6B0B2FBEA6E6A53A |
| SSDEEP: | 768:bbIIuuCz4cIu9QO6zB2UWB4UafMidSGNEhYxf43ZFCRzgA1hWD5q:bbZpcImpkNMiMG0Yxf0Ez/1hR |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 4016)
Actions looks like stealing of personal data
- WinRAR.exe (PID: 1344)
SUSPICIOUS
Starts Microsoft Office Application
- WinRAR.exe (PID: 1344)
- dwwin.exe (PID: 2892)
INFO
Creates files in the user directory
- EXCEL.EXE (PID: 4016)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2768)
- EXCEL.EXE (PID: 4016)
Reads Internet Cache Settings
- EXCEL.EXE (PID: 4016)
Reads settings of System Certificates
- EXCEL.EXE (PID: 4016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:05:29 01:07:02 |
| ZipCRC: | 0x7f45caaa |
| ZipCompressedSize: | 46566 |
| ZipUncompressedSize: | 99840 |
| ZipFileName: | 5739-5739-5739.xls |
Total processes
38
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1344 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\5739-5739-5739.xls.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
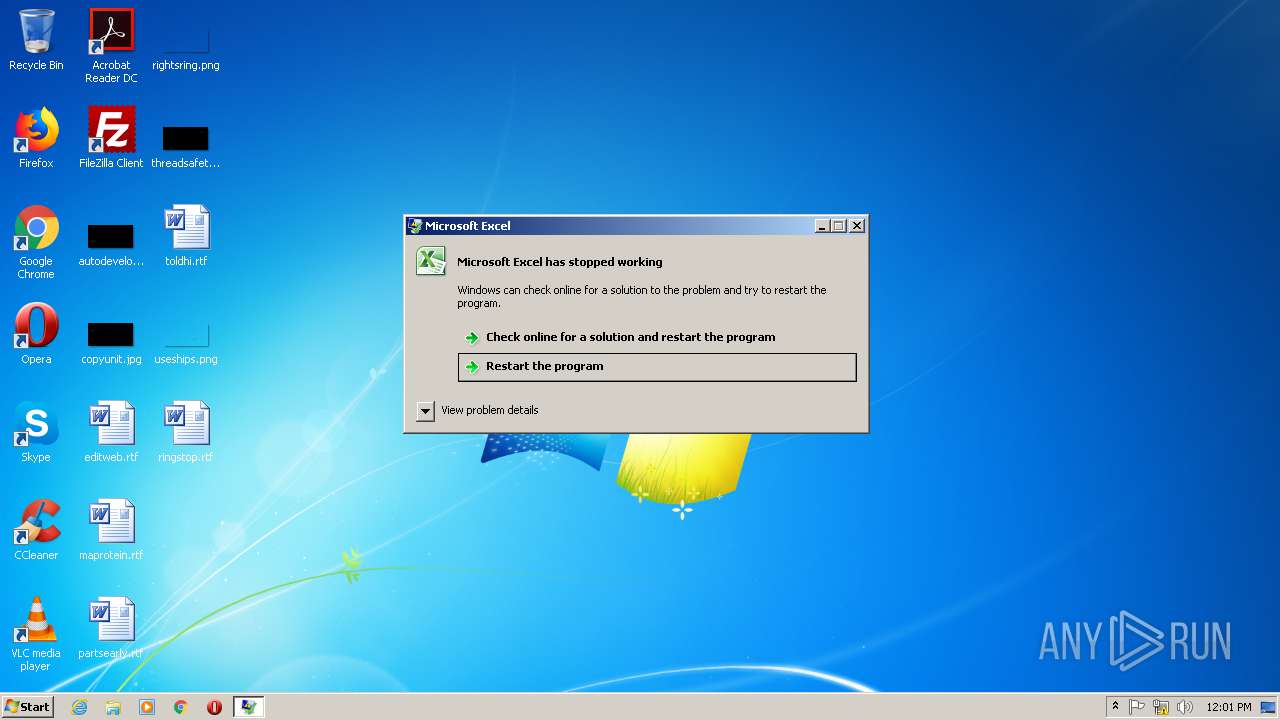
| 2436 | "C:\PROGRA~1\COMMON~1\MICROS~1\DW\DW20.EXE" -x -s 1608 | C:\PROGRA~1\COMMON~1\MICROS~1\DW\DW20.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Application Error Reporting Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
| 2768 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | dwwin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2892 | C:\Windows\system32\dwwin.exe -x -s 1608 | C:\Windows\system32\dwwin.exe | DW20.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Watson Client Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4016 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 2 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
24 143
Read events
8 655
Write events
15 441
Delete events
47
Modification events
| (PID) Process: | (1344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1344) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1344) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\5739-5739-5739.xls.zip | |||
| (PID) Process: | (1344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
0
Suspicious files
7
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4016 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRD1BB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 4016 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\config14[1].xml | — | |
MD5:— | SHA256:— | |||
| 4016 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CabAB69.tmp | — | |
MD5:— | SHA256:— | |||
| 4016 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\TarAB6A.tmp | — | |
MD5:— | SHA256:— | |||
| 4016 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF3651937B9BAB7022.TMP | — | |
MD5:— | SHA256:— | |||
| 4016 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb1344.4686\C7B42000 | — | |
MD5:— | SHA256:— | |||
| 4016 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF7E1BFEEA1F32DCE2.TMP | — | |
MD5:— | SHA256:— | |||
| 2768 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR125B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 4016 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\ONetConfig\786b7d3a5372048de949b5ce333fe46e.xml | xml | |
MD5:— | SHA256:— | |||
| 4016 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_C9FB72B5AE80778A08024D8B0FDECC6F | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
4
DNS requests
3
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4016 | EXCEL.EXE | GET | 200 | 52.109.88.8:80 | http://office14client.microsoft.com/config14?UILCID=1033&CLCID=1033&ILCID=1033&HelpLCID=1033&App={538F6C89-2AD5-4006-8154-C6670774E980}&build=14.0.6023 | NL | xml | 1.99 Kb | whitelisted |
4016 | EXCEL.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAtqs7A%2Bsan2xGCSaqjN%2FrM%3D | US | der | 1.47 Kb | whitelisted |
4016 | EXCEL.EXE | POST | — | 52.109.120.29:443 | http://rr.office.microsoft.com:443/Research/query.asmx | HK | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4016 | EXCEL.EXE | 52.109.88.8:80 | office14client.microsoft.com | Microsoft Corporation | NL | whitelisted |
4016 | EXCEL.EXE | 52.109.120.29:443 | rr.office.microsoft.com | Microsoft Corporation | HK | whitelisted |
4016 | EXCEL.EXE | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
office14client.microsoft.com |
| whitelisted |
rr.office.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4016 | EXCEL.EXE | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
Process | Message |
|---|---|
dwwin.exe | Error - |
dwwin.exe | ReadProcessMemory failed while trying to read PebBaseAddress |
dwwin.exe | |
dwwin.exe | Error - |
dwwin.exe | |
dwwin.exe |