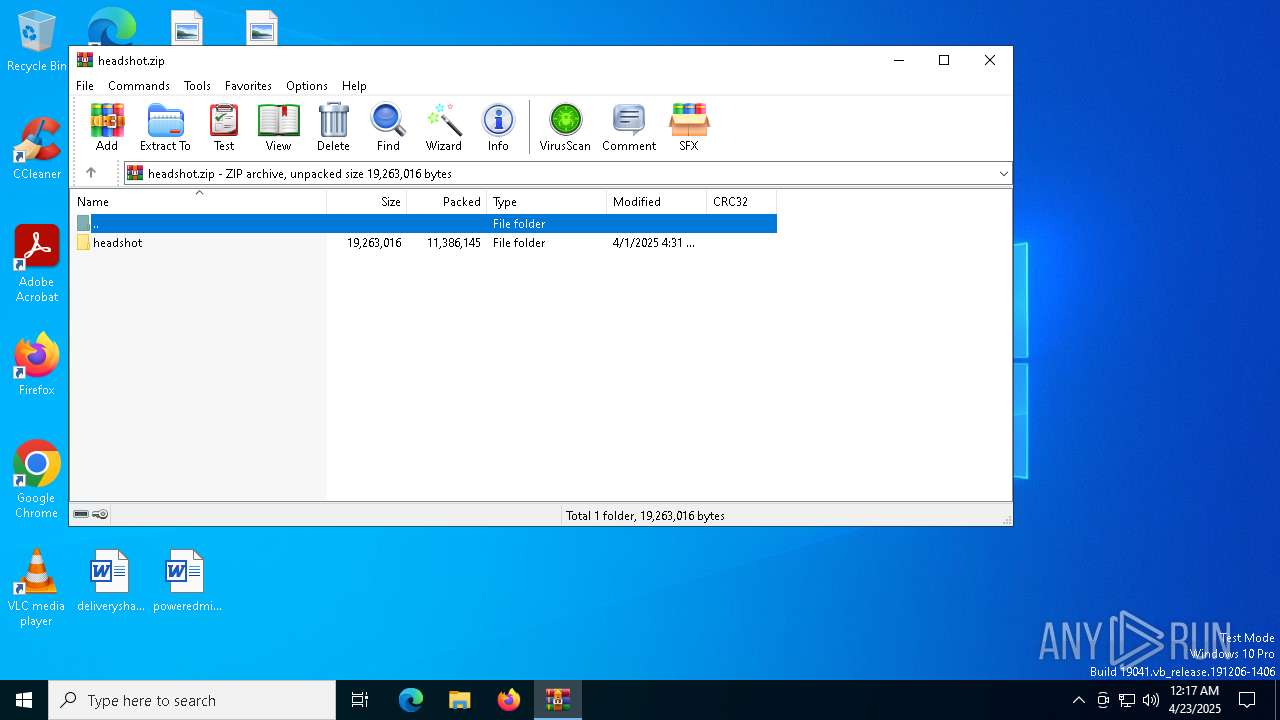
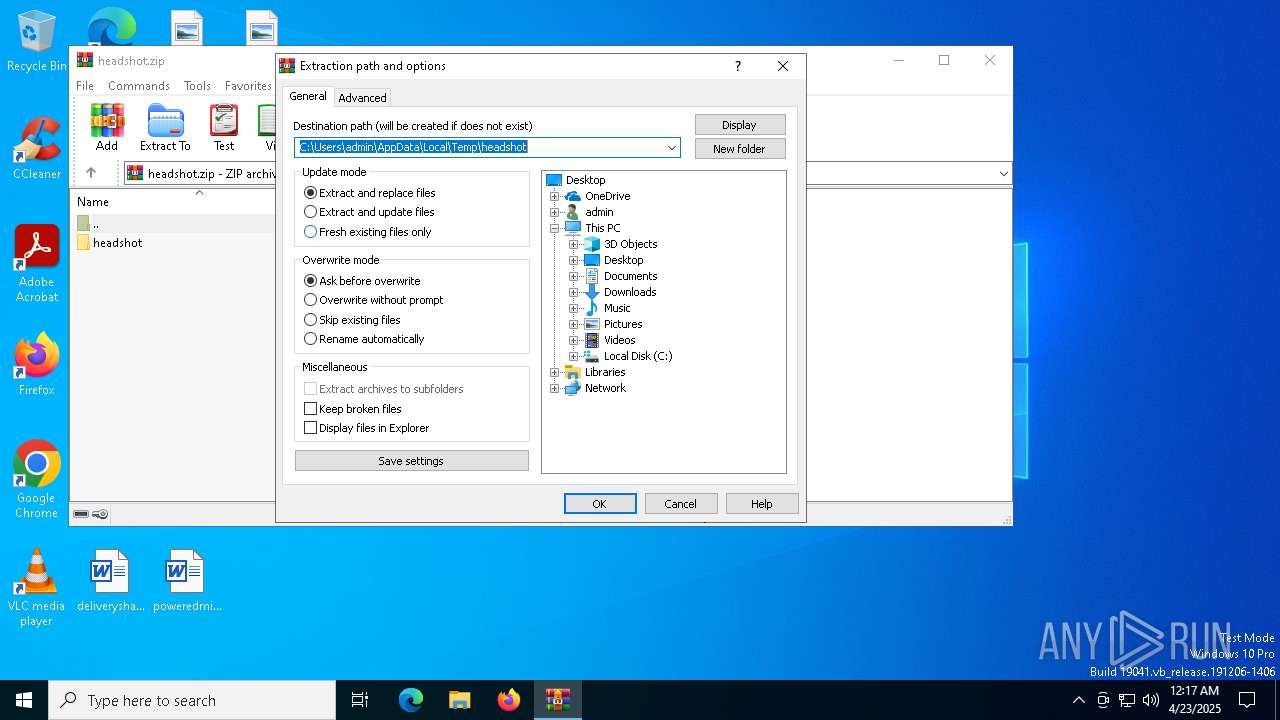
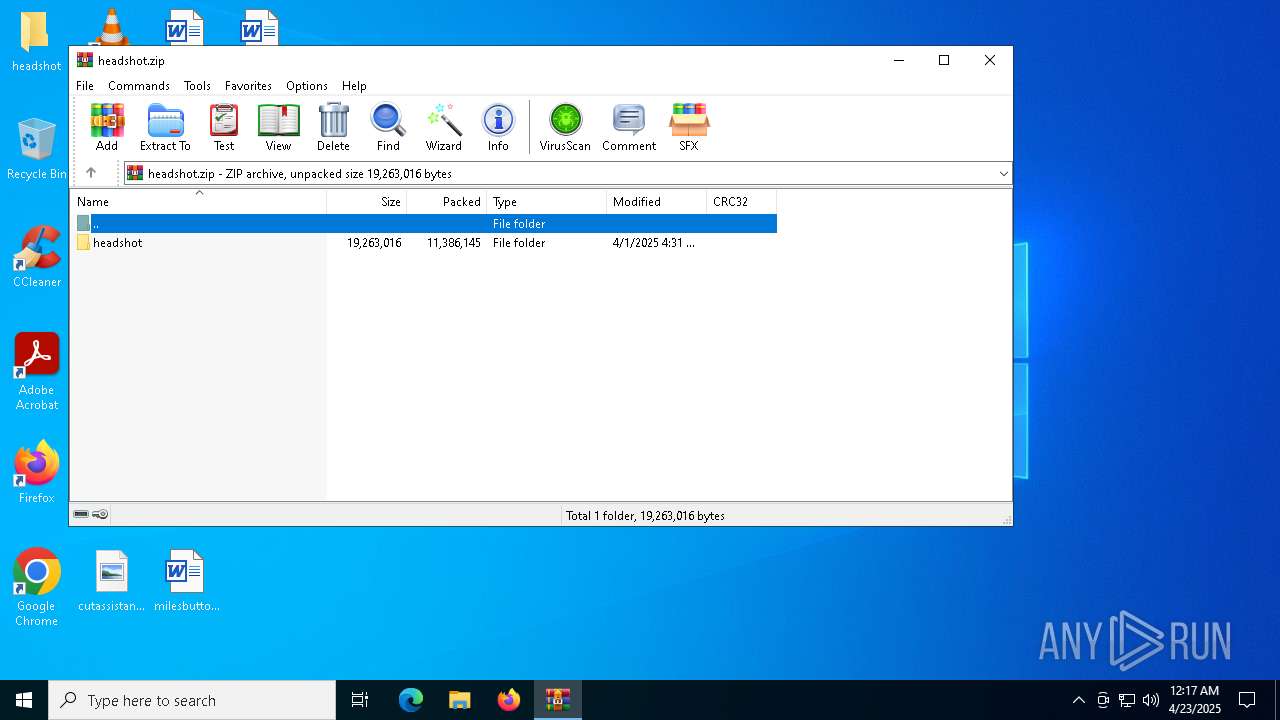
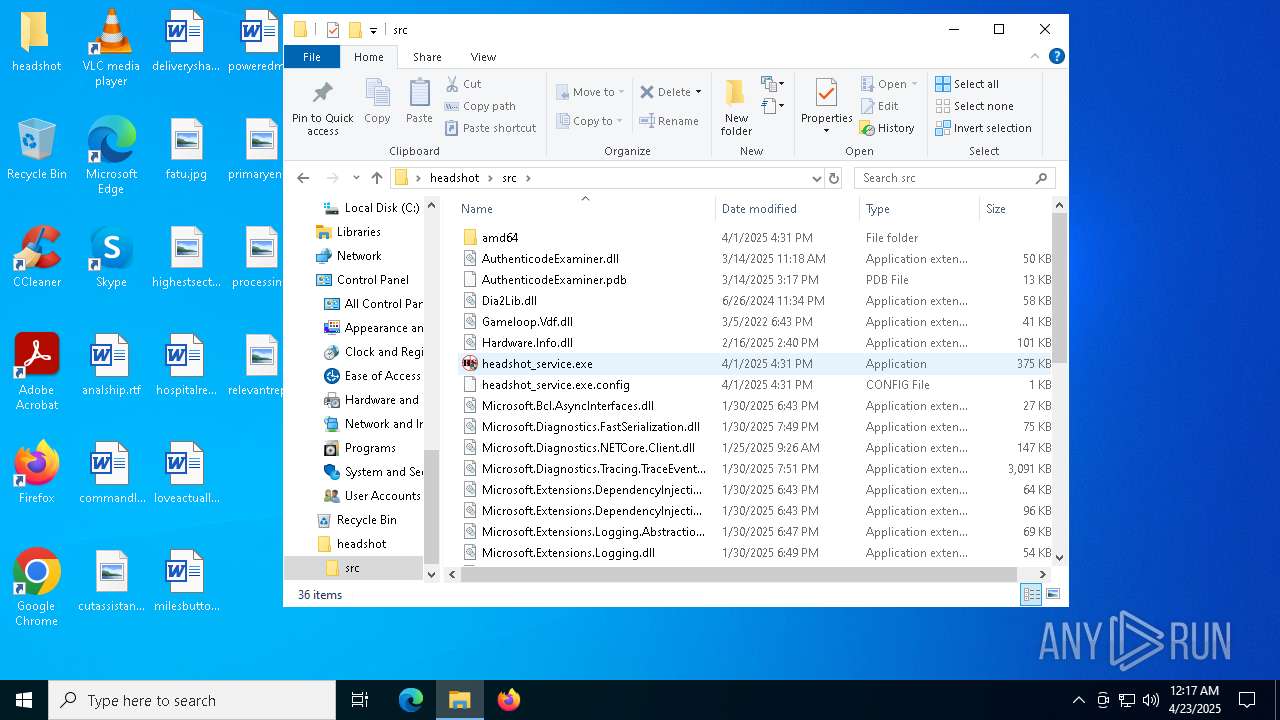
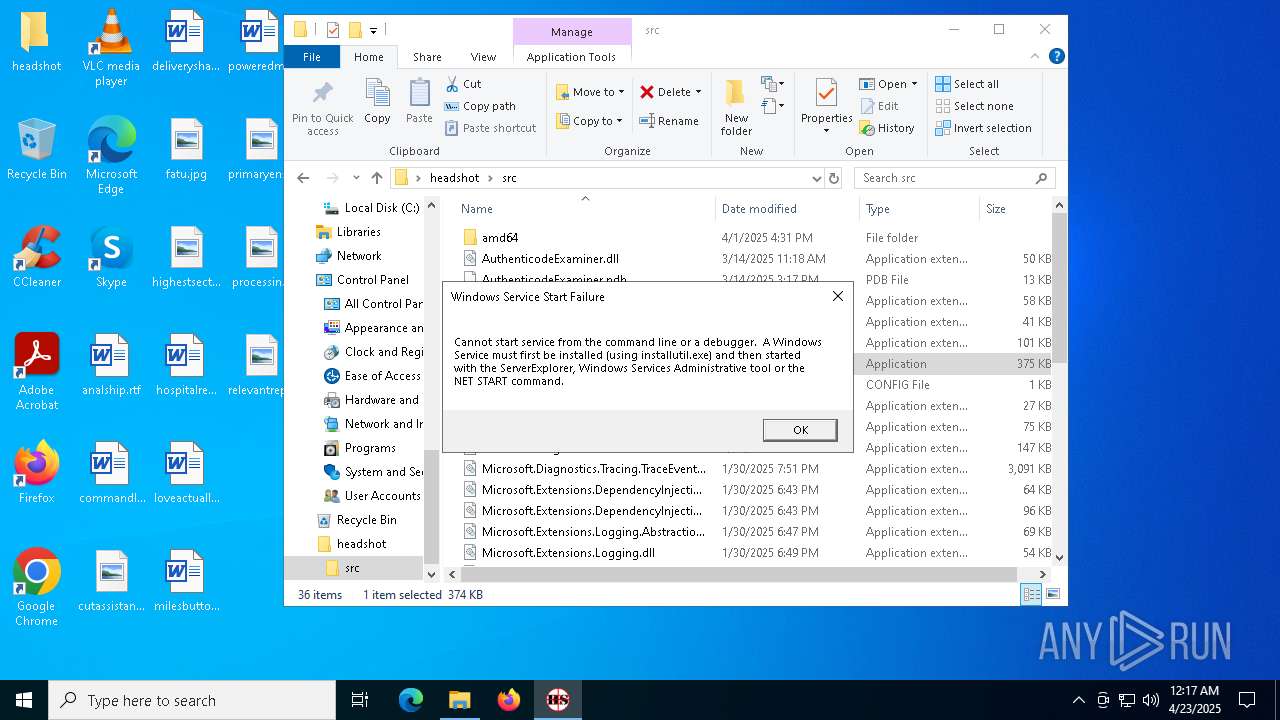
| File name: | headshot.zip |
| Full analysis: | https://app.any.run/tasks/3ee9dbe4-1991-4a3e-b1a0-0228ef8e3638 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2025, 00:17:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 9F13936875AFD92B2CE5C0B3C25C56B1 |
| SHA1: | 4720461E024CB05A4FB092F889DC8D6B3637B456 |
| SHA256: | 518E01399C5D91B2C9C5369435CB61A8368CECDE11AA0FCEEB58D1D284B699F5 |
| SSDEEP: | 98304:wiIVa3wrtRAtCq9a/0ciM2P2wiOnMXmdWEG0xIESaIBxNTb7tJ/34y8R9LhtjQOZ:qWtk2+VKbkpeL3evm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4776)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4776)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4776)
Manual execution by a user
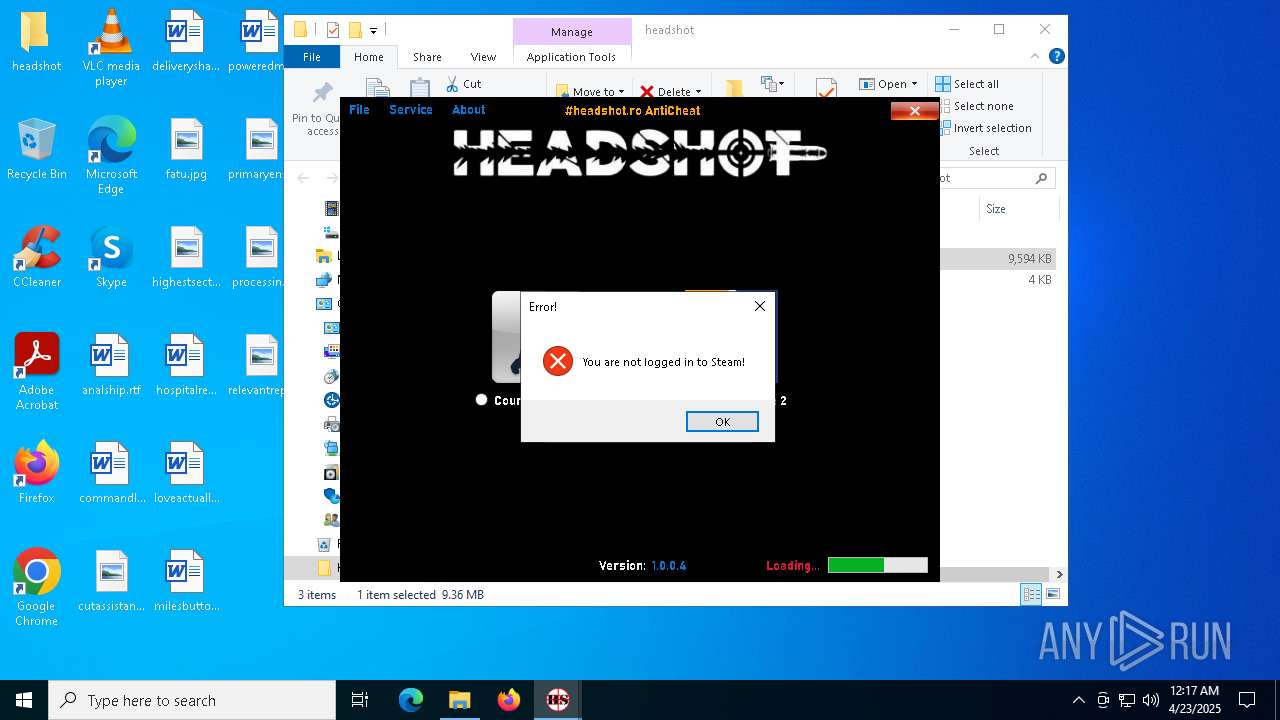
- headshot_anticheat.exe (PID: 4868)
- headshot_anticheat.exe (PID: 1184)
- headshot_service.exe (PID: 6480)
- headshot_service.exe (PID: 728)
Reads the machine GUID from the registry
- headshot_anticheat.exe (PID: 1184)
Disables trace logs
- headshot_anticheat.exe (PID: 1184)
Checks supported languages
- headshot_anticheat.exe (PID: 1184)
- headshot_service.exe (PID: 728)
Reads the computer name
- headshot_anticheat.exe (PID: 1184)
- headshot_service.exe (PID: 728)
Checks proxy server information
- headshot_anticheat.exe (PID: 1184)
Reads Environment values
- headshot_anticheat.exe (PID: 1184)
Reads the software policy settings
- headshot_anticheat.exe (PID: 1184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:01 19:31:20 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | headshot/ |
Total processes
132
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\Users\admin\Desktop\headshot\src\headshot_service.exe" | C:\Users\admin\Desktop\headshot\src\headshot_service.exe | explorer.exe | ||||||||||||
User: admin Company: www.headshot.ro / #headshot gather Integrity Level: HIGH Description: #headshot AntiCheat Service Version: 1.0.0.4 Modules
| |||||||||||||||
| 1184 | "C:\Users\admin\Desktop\headshot\headshot_anticheat.exe" | C:\Users\admin\Desktop\headshot\headshot_anticheat.exe | explorer.exe | ||||||||||||
User: admin Company: www.headshot.ro / #headshot gather Integrity Level: HIGH Description: #headshot AntiCheat Exit code: 1 Version: 1.0.0.4 Modules
| |||||||||||||||
| 2320 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\headshot.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4868 | "C:\Users\admin\Desktop\headshot\headshot_anticheat.exe" | C:\Users\admin\Desktop\headshot\headshot_anticheat.exe | — | explorer.exe | |||||||||||
User: admin Company: www.headshot.ro / #headshot gather Integrity Level: MEDIUM Description: #headshot AntiCheat Exit code: 3221226540 Version: 1.0.0.4 Modules
| |||||||||||||||
| 5256 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6244 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6480 | "C:\Users\admin\Desktop\headshot\src\headshot_service.exe" | C:\Users\admin\Desktop\headshot\src\headshot_service.exe | — | explorer.exe | |||||||||||
User: admin Company: www.headshot.ro / #headshot gather Integrity Level: MEDIUM Description: #headshot AntiCheat Service Exit code: 3221226540 Version: 1.0.0.4 Modules
| |||||||||||||||
Total events
3 238
Read events
3 188
Write events
37
Delete events
13
Modification events
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\headshot.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
36
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4776 | WinRAR.exe | C:\Users\admin\Desktop\headshot\src\Hardware.Info.dll | executable | |
MD5:A815D487985608CF7165AE1B47EE1940 | SHA256:0EFE34682450AEBB23B3CE017DC4B6644A370F776E293D0E628567914F6793DA | |||
| 4776 | WinRAR.exe | C:\Users\admin\Desktop\headshot\src\headshot_service.exe | executable | |
MD5:E4F4405400D9C86B52F4EE191948D9EC | SHA256:EB5DB7C7B7F91908665996B8DD7CBFE65747F185BB6CB75BC99BE29798E8505E | |||
| 4776 | WinRAR.exe | C:\Users\admin\Desktop\headshot\src\amd64\msdia140.dll | executable | |
MD5:38CE537CF506EBD0A13565EC4A496DE8 | SHA256:52B87B5CACBAD5A32362EF467693DD559F380B626AF310D3875B05CB5ED81A98 | |||
| 4776 | WinRAR.exe | C:\Users\admin\Desktop\headshot\src\Dia2Lib.dll | executable | |
MD5:BE6474B726207994DECDC22E84936A3C | SHA256:6C4CAC68010FE032218EFE5E9FCF46EEF9F77BFAA5F3BD33F03C5FF77D5A8FAC | |||
| 4776 | WinRAR.exe | C:\Users\admin\Desktop\headshot\src\headshot_service.exe.config | xml | |
MD5:3A7D9295FC78E521222AFA1DE6B6A950 | SHA256:B70CD6C2CE2A4FB5DFB4C59AAC97E2DCC4C7D3D4041EBBCF096C7FEE461042C8 | |||
| 4776 | WinRAR.exe | C:\Users\admin\Desktop\headshot\src\amd64\KernelTraceControl.dll | executable | |
MD5:B1C75BF2B5095AC3299403E34D462C4C | SHA256:98DE2F1DE4FB1711688C04E2CB0187BF8C47E627771E8F51329671F296BFC688 | |||
| 4776 | WinRAR.exe | C:\Users\admin\Desktop\headshot\src\Gameloop.Vdf.dll | executable | |
MD5:C3D74A26D3AC858CA827546FB6A993CF | SHA256:325DE2B398089F136E23E623CF1658B03C51A821A9271069B74CC4187D3482E0 | |||
| 4776 | WinRAR.exe | C:\Users\admin\Desktop\headshot\src\AuthenticodeExaminer.dll | executable | |
MD5:1FC478AF95BA9A5860F7F694879159B8 | SHA256:9043F097BC9D529830BF6E9BE69558DDC2BF891D696D926A0B4321B77CF155FE | |||
| 4776 | WinRAR.exe | C:\Users\admin\Desktop\headshot\src\Microsoft.Diagnostics.FastSerialization.dll | executable | |
MD5:DE8FF4540D0C3FB4DEA14C10D08138AA | SHA256:B00B2C0DFCB7FB51E547CC929CBD6F004ECEAB62E2B832045E856F1F3A49B1C3 | |||
| 4776 | WinRAR.exe | C:\Users\admin\Desktop\headshot\headshot_anticheat.exe | executable | |
MD5:5C292BA0B6D088D76EDEFF92C855BAE3 | SHA256:4010E81A767148A1C8F406A57BFBDC287A243F4F3381F0D38F219B3FCC00F150 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
13
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1184 | headshot_anticheat.exe | 104.21.80.1:443 | api.headshot.ro | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
api.headshot.ro |
| unknown |