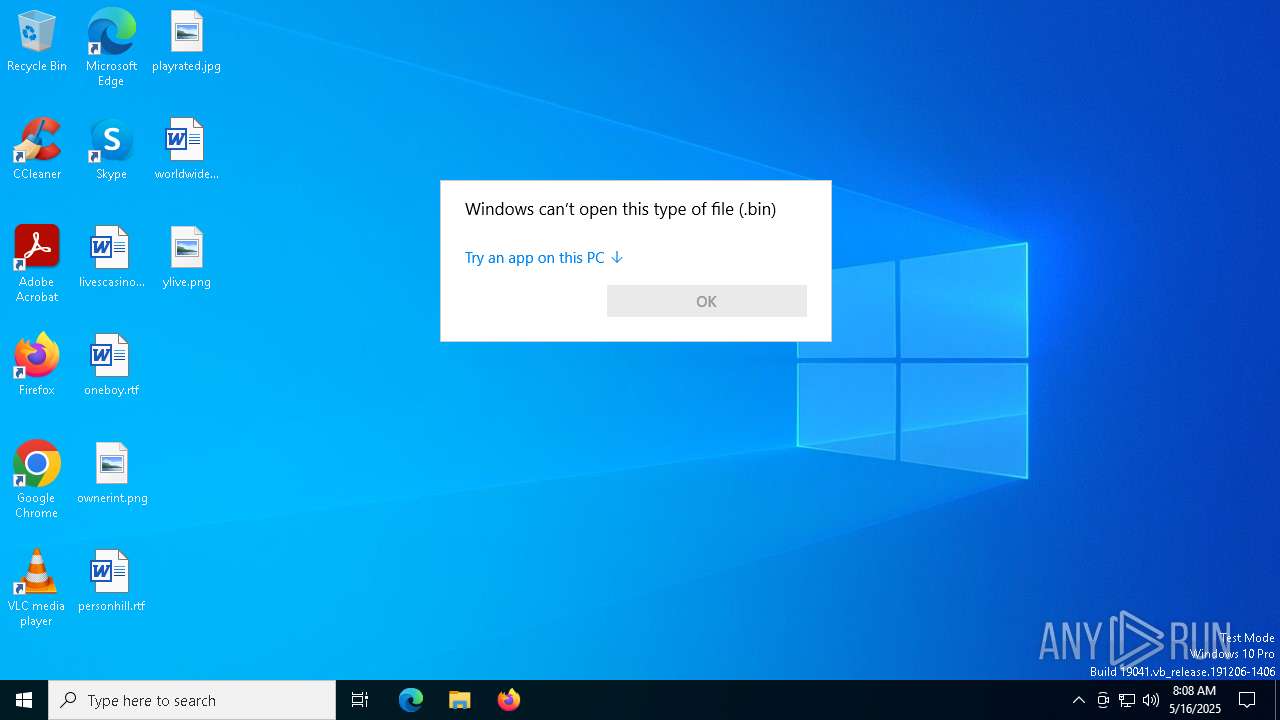
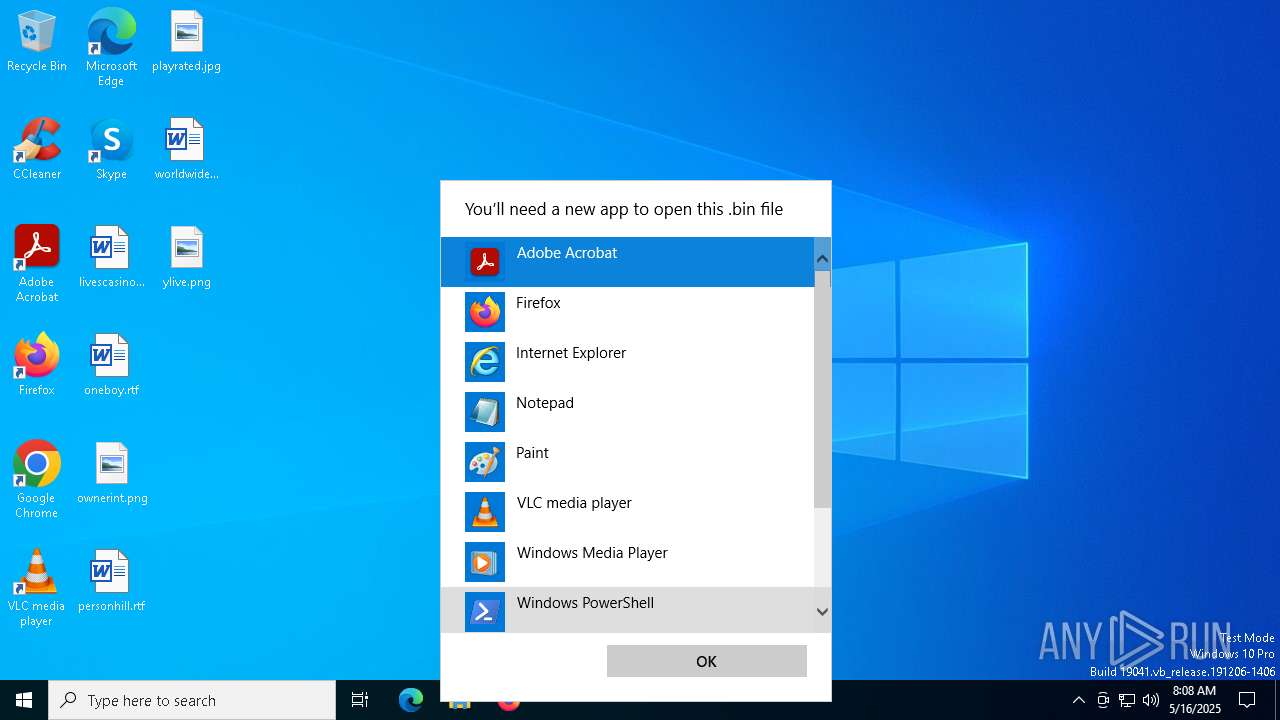
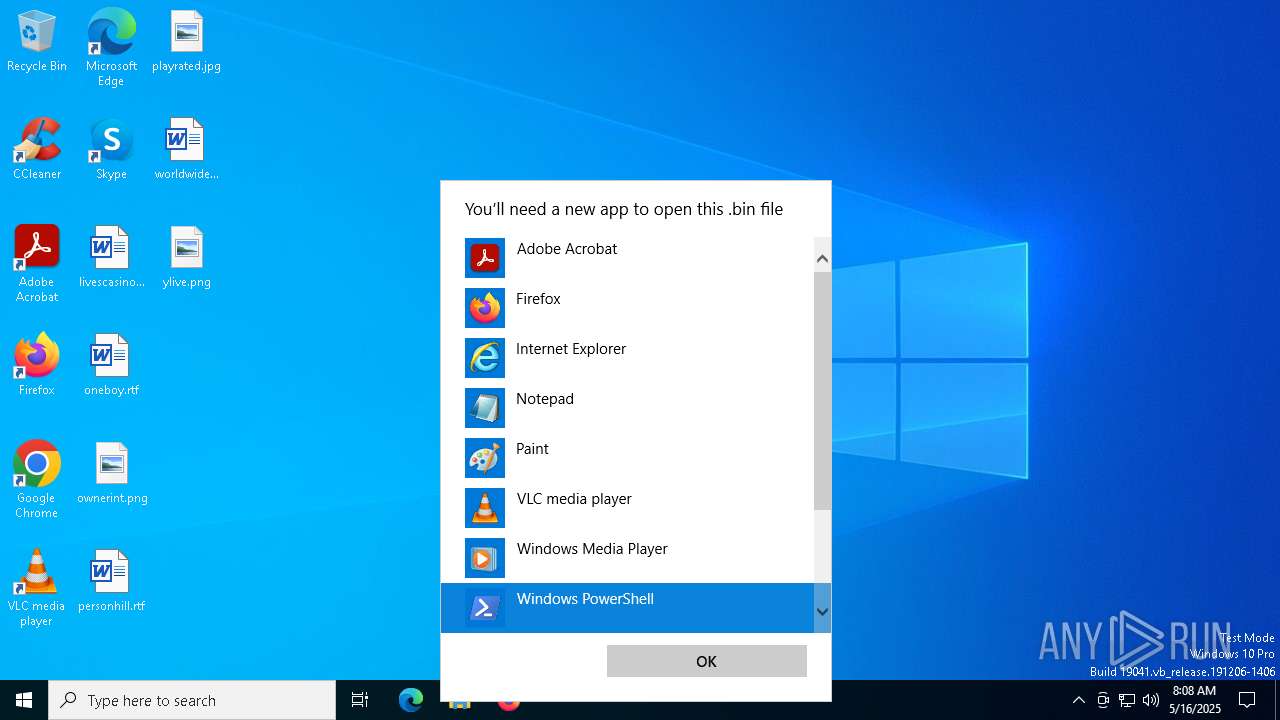
| File name: | 2020-06-09-soub4.cab-from-a4zy33hbmhxx70w9q.com.bin |
| Full analysis: | https://app.any.run/tasks/0408592d-875d-402b-9ca6-1313dbe16d90 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 08:07:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 12079931286AD2D1D2C0D23FC5B4AB8C |
| SHA1: | 514B161DE55ED7070D16CF4034F6797F710F9547 |
| SHA256: | 518B5D5CF0BED2777FDB52121688F929759DA1071C6B6FFED1CEE6DD30618C48 |
| SSDEEP: | 12288:OlCi5MOPvlIcfq3cgVzQwdXXnIaUnM+bu:OEi1vR8dlQw9XIaUnM+bu |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- powershell.exe (PID: 1764)
- powershell.exe (PID: 3304)
- powershell.exe (PID: 7712)
- powershell.exe (PID: 6068)
- powershell.exe (PID: 4408)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 7964)
- powershell.exe (PID: 7860)
- powershell.exe (PID: 1020)
- powershell.exe (PID: 5668)
- powershell.exe (PID: 4452)
- powershell.exe (PID: 7936)
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 3024)
- powershell.exe (PID: 5740)
- powershell.exe (PID: 7680)
- powershell.exe (PID: 7824)
- powershell.exe (PID: 7780)
- powershell.exe (PID: 6572)
- powershell.exe (PID: 8092)
- powershell.exe (PID: 7184)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 8172)
- powershell.exe (PID: 5008)
- powershell.exe (PID: 8124)
- powershell.exe (PID: 3192)
- powershell.exe (PID: 5360)
- powershell.exe (PID: 7736)
- powershell.exe (PID: 4932)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 6108)
- powershell.exe (PID: 2316)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 8092)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 444)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 5008)
- powershell.exe (PID: 1452)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 7000)
- powershell.exe (PID: 7856)
- powershell.exe (PID: 5400)
- powershell.exe (PID: 5596)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 616)
- powershell.exe (PID: 2344)
- powershell.exe (PID: 1188)
- powershell.exe (PID: 7172)
- powershell.exe (PID: 3676)
- powershell.exe (PID: 1452)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 736)
- powershell.exe (PID: 8076)
- powershell.exe (PID: 7864)
- powershell.exe (PID: 7304)
- powershell.exe (PID: 7976)
- powershell.exe (PID: 2656)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 664)
- powershell.exe (PID: 5204)
- powershell.exe (PID: 2104)
- powershell.exe (PID: 7648)
- powershell.exe (PID: 8060)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 7284)
- powershell.exe (PID: 5512)
- powershell.exe (PID: 5556)
- powershell.exe (PID: 7308)
- powershell.exe (PID: 7756)
- powershell.exe (PID: 5364)
- powershell.exe (PID: 5972)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 7572)
- powershell.exe (PID: 6476)
- powershell.exe (PID: 7396)
- powershell.exe (PID: 7264)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 6676)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 1096)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 7636)
- powershell.exe (PID: 7856)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7764)
- powershell.exe (PID: 4944)
- powershell.exe (PID: 6712)
- powershell.exe (PID: 4528)
- powershell.exe (PID: 3888)
- powershell.exe (PID: 7208)
- powershell.exe (PID: 7184)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 3240)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 976)
- powershell.exe (PID: 5508)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 7852)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 7756)
- powershell.exe (PID: 8076)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 7584)
- powershell.exe (PID: 1004)
- powershell.exe (PID: 8092)
- powershell.exe (PID: 5744)
- powershell.exe (PID: 6168)
- powershell.exe (PID: 7184)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 5064)
- powershell.exe (PID: 2504)
- powershell.exe (PID: 856)
- powershell.exe (PID: 2104)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 616)
- powershell.exe (PID: 4728)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 6564)
- powershell.exe (PID: 6156)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 1176)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 4244)
- powershell.exe (PID: 5740)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 4688)
- powershell.exe (PID: 4276)
- powershell.exe (PID: 3268)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 6192)
- powershell.exe (PID: 7608)
- powershell.exe (PID: 8060)
- powershell.exe (PID: 8052)
- powershell.exe (PID: 7320)
- powershell.exe (PID: 3176)
- powershell.exe (PID: 6652)
- powershell.exe (PID: 7748)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 2560)
- powershell.exe (PID: 5512)
- powershell.exe (PID: 7348)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 7624)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 7712)
- powershell.exe (PID: 7860)
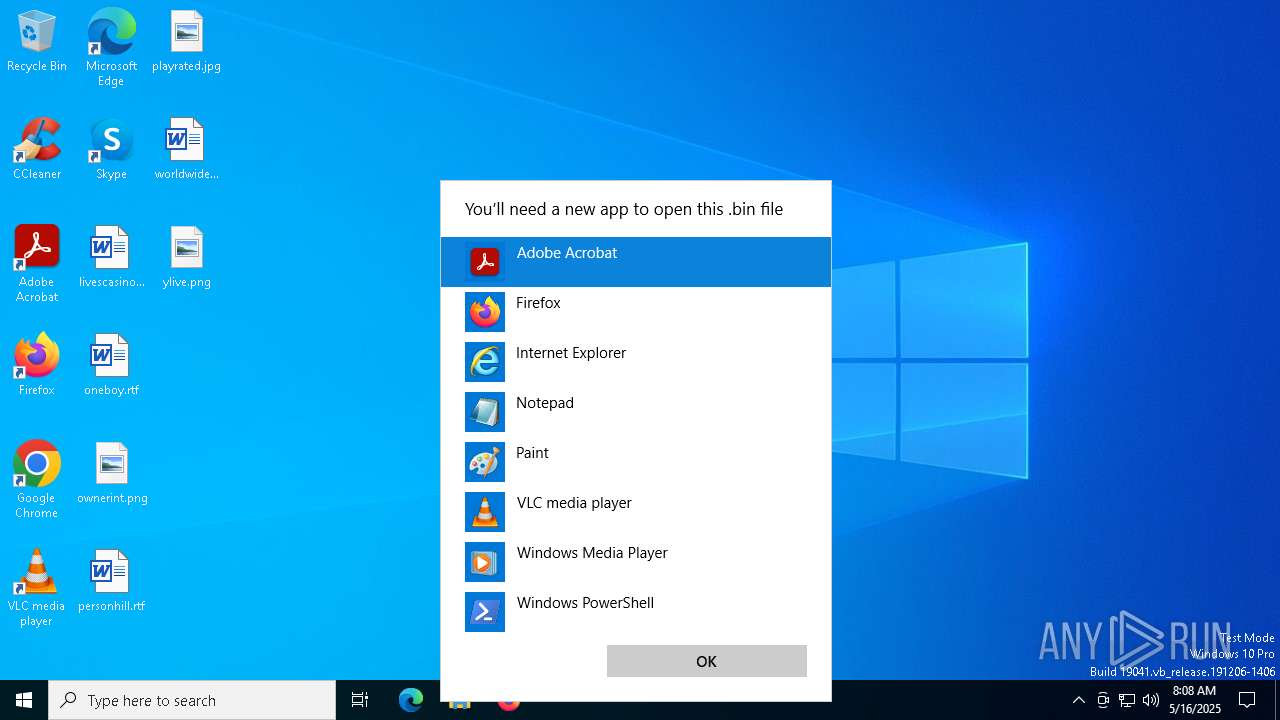
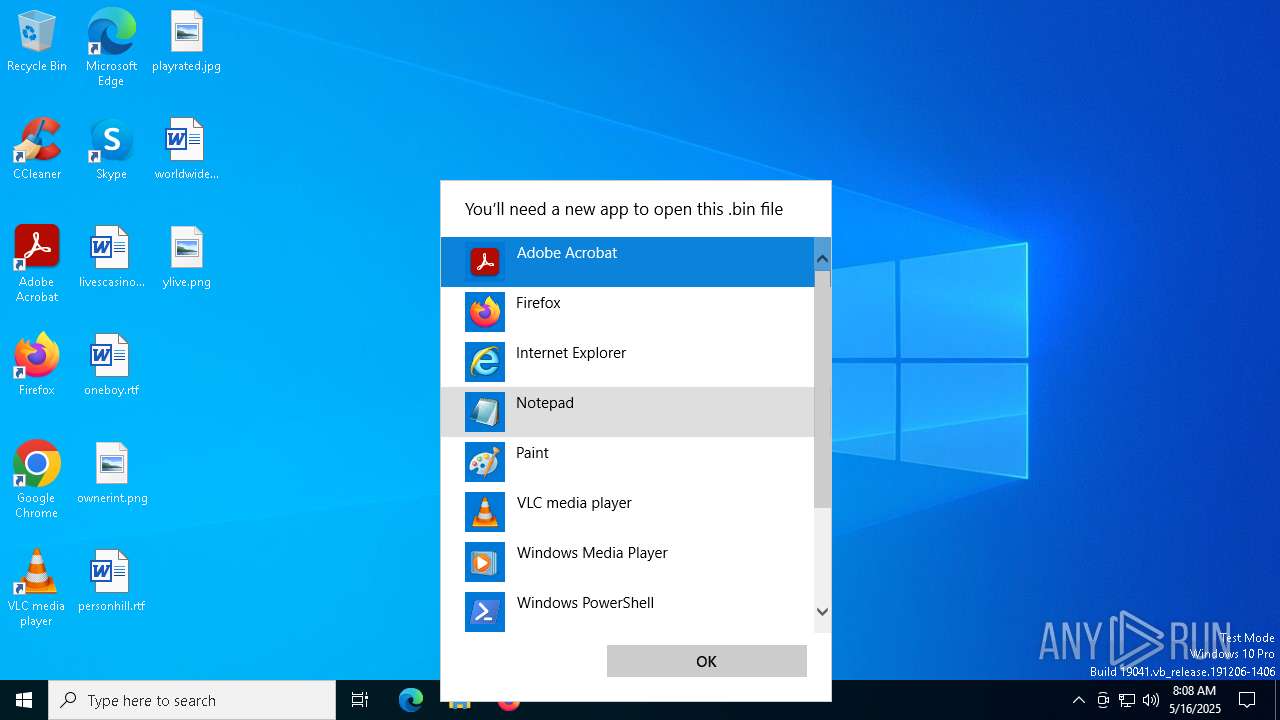
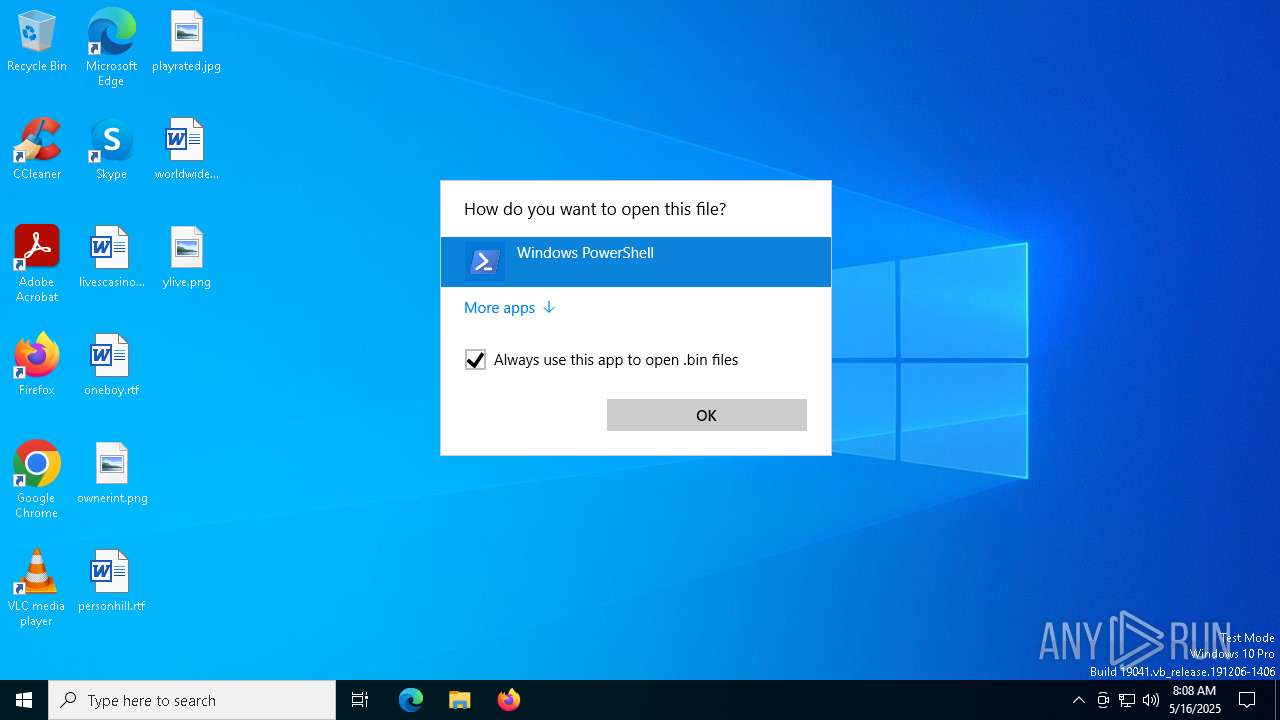
- OpenWith.exe (PID: 8172)
- powershell.exe (PID: 6068)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 1764)
- OpenWith.exe (PID: 7456)
- powershell.exe (PID: 3304)
- powershell.exe (PID: 4408)
- powershell.exe (PID: 1020)
- powershell.exe (PID: 7936)
- powershell.exe (PID: 7964)
- powershell.exe (PID: 3024)
- powershell.exe (PID: 4452)
- powershell.exe (PID: 5668)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 1348)
- powershell.exe (PID: 5740)
- powershell.exe (PID: 7680)
- powershell.exe (PID: 7824)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 6572)
- powershell.exe (PID: 7780)
- powershell.exe (PID: 8092)
- powershell.exe (PID: 8172)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 2316)
- powershell.exe (PID: 5008)
- powershell.exe (PID: 5360)
- powershell.exe (PID: 3192)
- powershell.exe (PID: 7736)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 7184)
- powershell.exe (PID: 6108)
- powershell.exe (PID: 4932)
- powershell.exe (PID: 444)
- powershell.exe (PID: 8092)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 1452)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 5008)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 7000)
- powershell.exe (PID: 5400)
- powershell.exe (PID: 7856)
- powershell.exe (PID: 5596)
- powershell.exe (PID: 2344)
- powershell.exe (PID: 616)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 1188)
- powershell.exe (PID: 3676)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 7172)
- powershell.exe (PID: 1452)
- powershell.exe (PID: 7976)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 7864)
- powershell.exe (PID: 7304)
- powershell.exe (PID: 8076)
- powershell.exe (PID: 8060)
- powershell.exe (PID: 5508)
- powershell.exe (PID: 7284)
- powershell.exe (PID: 2656)
- powershell.exe (PID: 2104)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 664)
- powershell.exe (PID: 5204)
- powershell.exe (PID: 7648)
- powershell.exe (PID: 5512)
- powershell.exe (PID: 5364)
- powershell.exe (PID: 7308)
- powershell.exe (PID: 7756)
- powershell.exe (PID: 5556)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 5972)
- powershell.exe (PID: 8124)
- powershell.exe (PID: 6476)
- powershell.exe (PID: 7264)
- powershell.exe (PID: 7396)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 6676)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 1096)
- powershell.exe (PID: 7572)
- powershell.exe (PID: 5952)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7764)
- powershell.exe (PID: 7856)
- powershell.exe (PID: 7636)
- powershell.exe (PID: 4944)
- powershell.exe (PID: 7632)
- powershell.exe (PID: 4528)
- powershell.exe (PID: 3888)
- powershell.exe (PID: 7184)
- powershell.exe (PID: 7208)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 3240)
- powershell.exe (PID: 736)
- powershell.exe (PID: 976)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 6712)
- powershell.exe (PID: 7852)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 7584)
- powershell.exe (PID: 8076)
- powershell.exe (PID: 1004)
- powershell.exe (PID: 8092)
- powershell.exe (PID: 7756)
- powershell.exe (PID: 5744)
- powershell.exe (PID: 6168)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7184)
- powershell.exe (PID: 5064)
- powershell.exe (PID: 856)
- powershell.exe (PID: 2104)
- powershell.exe (PID: 3016)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 4728)
- powershell.exe (PID: 6564)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 616)
- powershell.exe (PID: 6156)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 2504)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 4688)
- powershell.exe (PID: 4244)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 4276)
- powershell.exe (PID: 3744)
- powershell.exe (PID: 1176)
- powershell.exe (PID: 5740)
- powershell.exe (PID: 3268)
- powershell.exe (PID: 6192)
- powershell.exe (PID: 7608)
- powershell.exe (PID: 8052)
- powershell.exe (PID: 7320)
- powershell.exe (PID: 8060)
- powershell.exe (PID: 3176)
- powershell.exe (PID: 6652)
- powershell.exe (PID: 7748)
- powershell.exe (PID: 5176)
- powershell.exe (PID: 2560)
- powershell.exe (PID: 7348)
- powershell.exe (PID: 5512)
- powershell.exe (PID: 7624)
INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7456)
- OpenWith.exe (PID: 8172)
The sample compiled with english language support
- OpenWith.exe (PID: 7456)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 7456)
- OpenWith.exe (PID: 8172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:06:09 09:05:31+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, DLL |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 112640 |
| InitializedDataSize: | 194048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11390 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.5.3.576 |
| ProductVersionNumber: | 7.5.3.576 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Separate ThinkFeed Corporation |
| FileVersion: | 7.5.3.576 Occ-4048579 |
| InternalName: | Iron corner |
| LegalCopyright: | © Separate ThinkFeed Corporation. All rights reserved. |
| OriginalFileName: | Iron corner.DLL |
| ProductName: | Separate ThinkFeed® ClassDesert® join busy |
| ProductVersion: | 7.5.3.576 |
Total processes
443
Monitored processes
311
Malicious processes
0
Suspicious processes
91
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\2020-06-09-soub4.cab-from-a4zy33hbmhxx70w9q.com.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\2020-06-09-soub4.cab-from-a4zy33hbmhxx70w9q.com.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\2020-06-09-soub4.cab-from-a4zy33hbmhxx70w9q.com.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "C:\Users\admin\AppData\Local\Temp\2020-06-09-soub4.cab-from-a4zy33hbmhxx70w9q.com.bin" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
718 458
Read events
718 299
Write events
159
Delete events
0
Modification events
| (PID) Process: | (8172) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (8172) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (8172) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
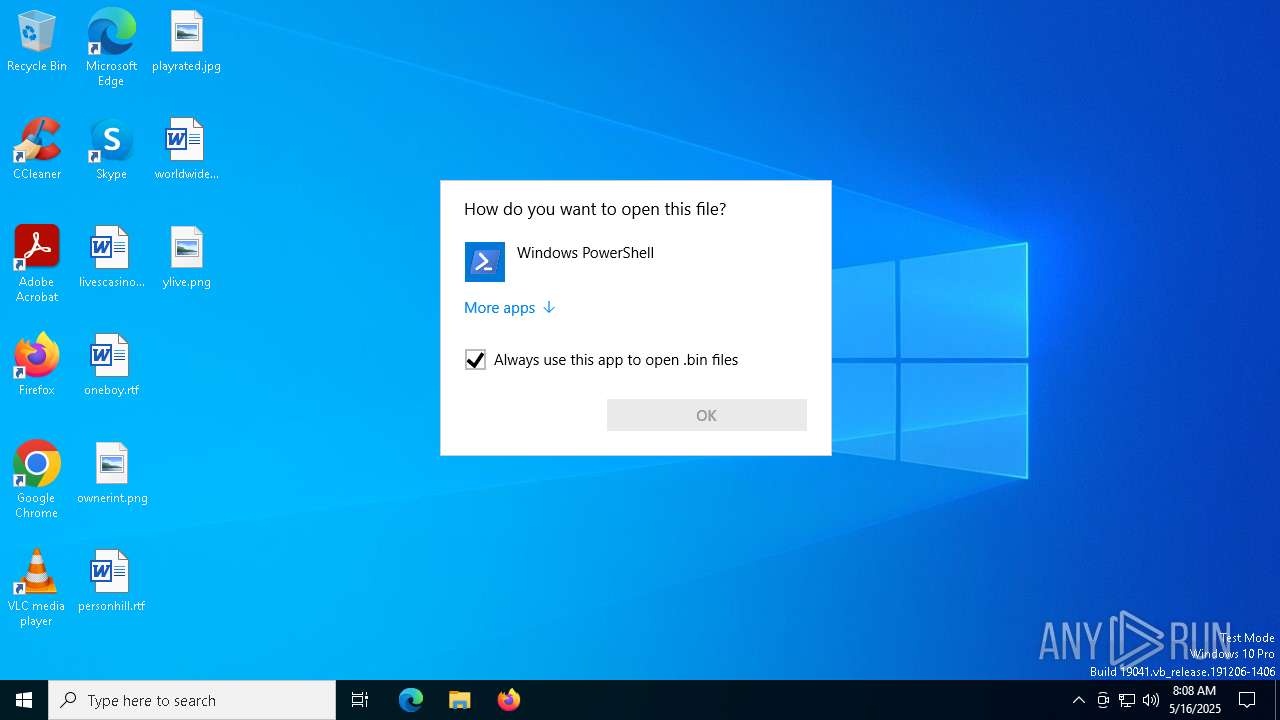
| (PID) Process: | (8172) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\UserChoice |
| Operation: | write | Name: | ProgId |
Value: Applications\powershell.exe | |||
| (PID) Process: | (8172) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\UserChoice |
| Operation: | write | Name: | Hash |
Value: cQyn0chkbCU= | |||
| (PID) Process: | (6068) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (4408) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (3304) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (6512) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
| (PID) Process: | (7712) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bin\OpenWithProgids |
| Operation: | write | Name: | bin_auto_file |
Value: | |||
Executable files
0
Suspicious files
463
Text files
306
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\051UIDYPI98F7I4Z61JL.temp | binary | |
MD5:4F41739A6C430FA280621F0127B6BE20 | SHA256:F0CF138918E7B126889E4422FB5E6D4D1D13549551AD3161F3BA69CB58962480 | |||
| 7956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kpxpb204.r3a.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3304 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tnv5s5pv.0mm.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6068 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:D337BC291B576D3CE04558645FB2584E | SHA256:848B794262482890188C6F7964FBD4AC71C9580328695D4A5AC08944748BCAA1 | |||
| 7956 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:7BB55D92B4A693719F6EB98457A57509 | SHA256:CF18A122C2AB32839733CBA5F13C7EA3C367216ED1EB499F750CF8985796DAA7 | |||
| 7956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:4F41739A6C430FA280621F0127B6BE20 | SHA256:F0CF138918E7B126889E4422FB5E6D4D1D13549551AD3161F3BA69CB58962480 | |||
| 6068 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\6RX7AEYQ597LSZV3PQUO.temp | binary | |
MD5:D337BC291B576D3CE04558645FB2584E | SHA256:848B794262482890188C6F7964FBD4AC71C9580328695D4A5AC08944748BCAA1 | |||
| 4408 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\DD8D90QY9SHOJEOZ17ZA.temp | binary | |
MD5:7060163A9092BB03FB288F225EE45C08 | SHA256:BFF2483EC46E487637B9B7D29495F128892FF0C9D91F04BC704368D96BB729E4 | |||
| 3304 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:60626332574546EB8AFDD3C90CEBB4F9 | SHA256:BA1B445879DCA45DA62DE1FBDD3AD8DDD1B9DA9972E2156EDE61943AAE6FCA41 | |||
| 3304 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF11784a.TMP | binary | |
MD5:7060163A9092BB03FB288F225EE45C08 | SHA256:BFF2483EC46E487637B9B7D29495F128892FF0C9D91F04BC704368D96BB729E4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
50
DNS requests
16
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7284 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7284 | SIHClient.exe | 20.3.187.198:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
198.187.3.20.in-addr.arpa |
| unknown |
4.8.2.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.0.0.2.0.c.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
nexusrules.officeapps.live.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |