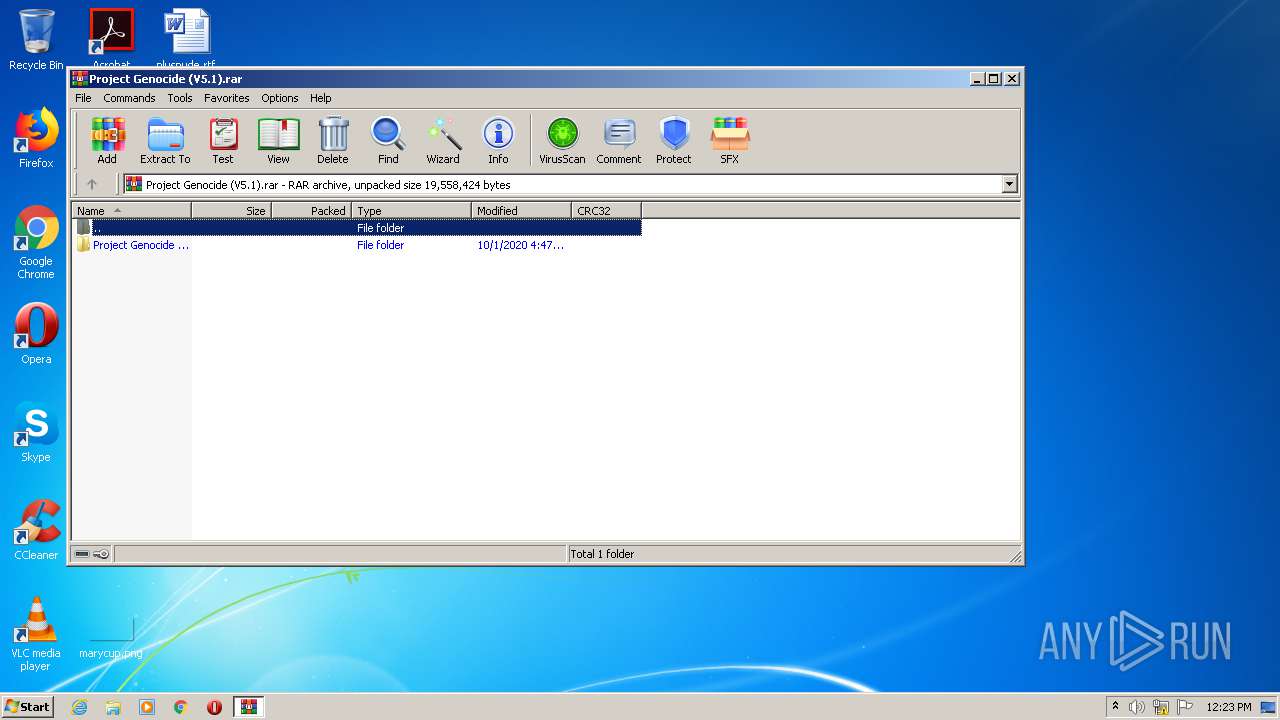
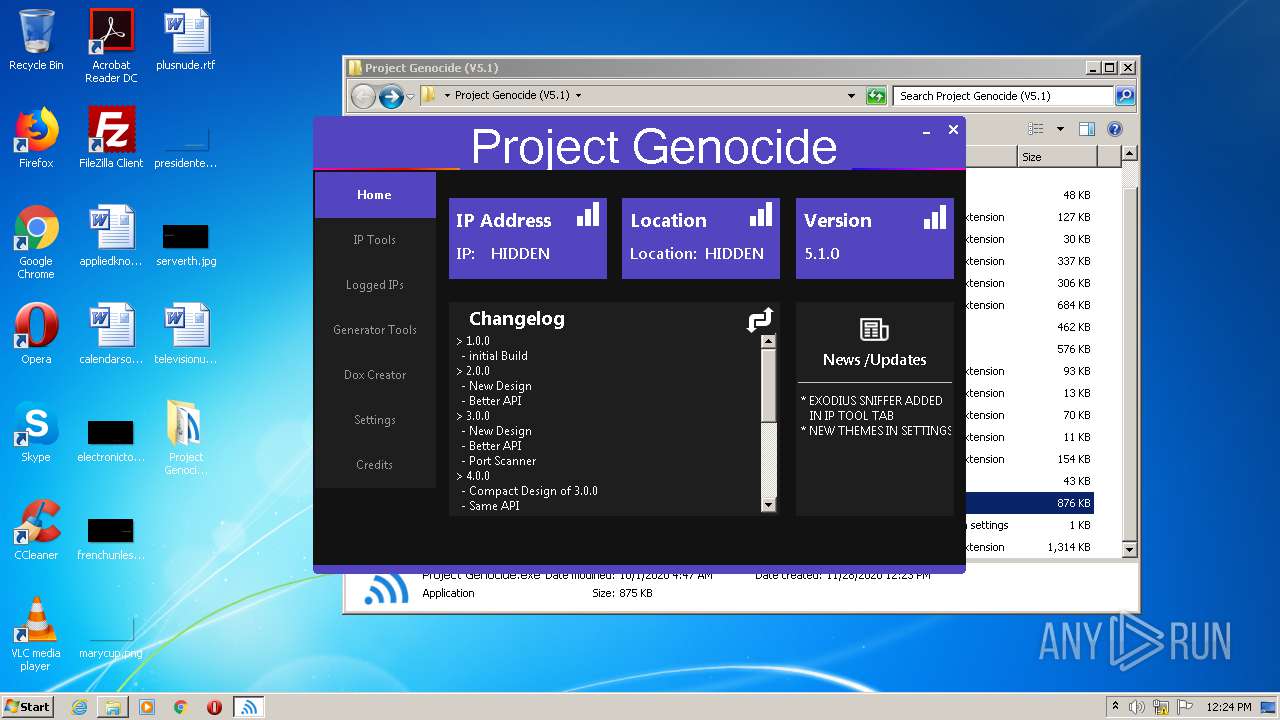
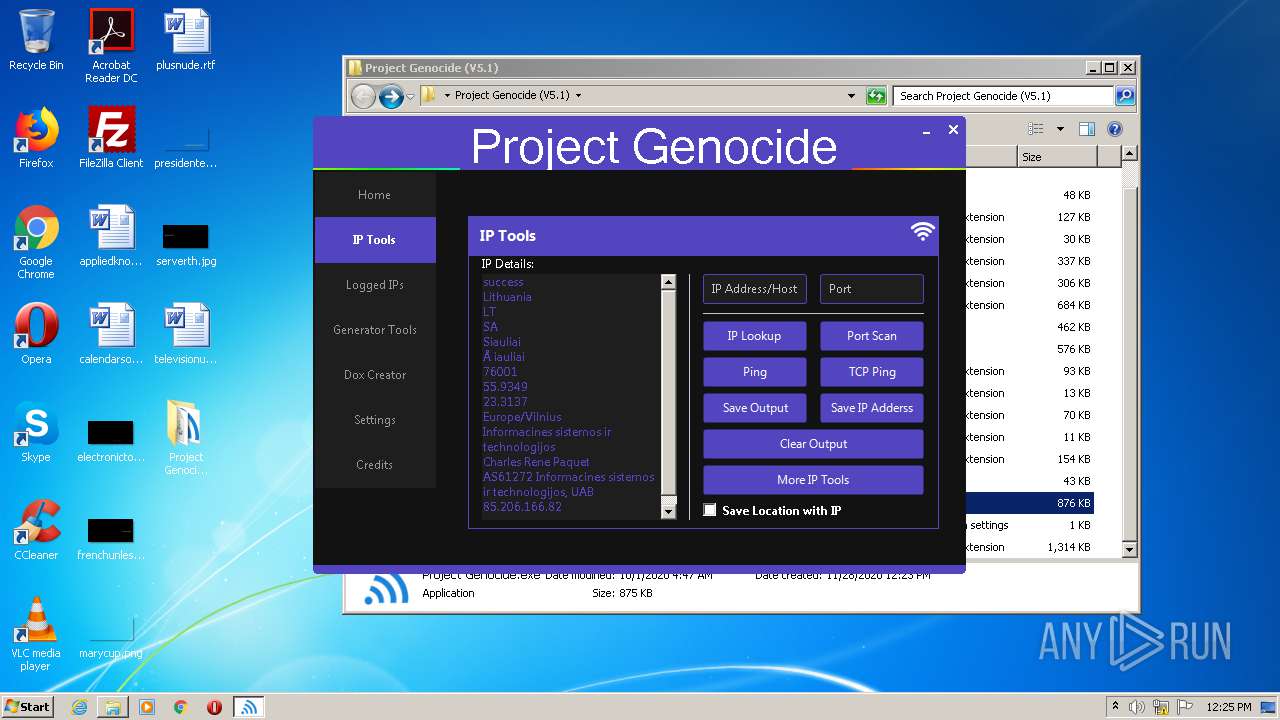
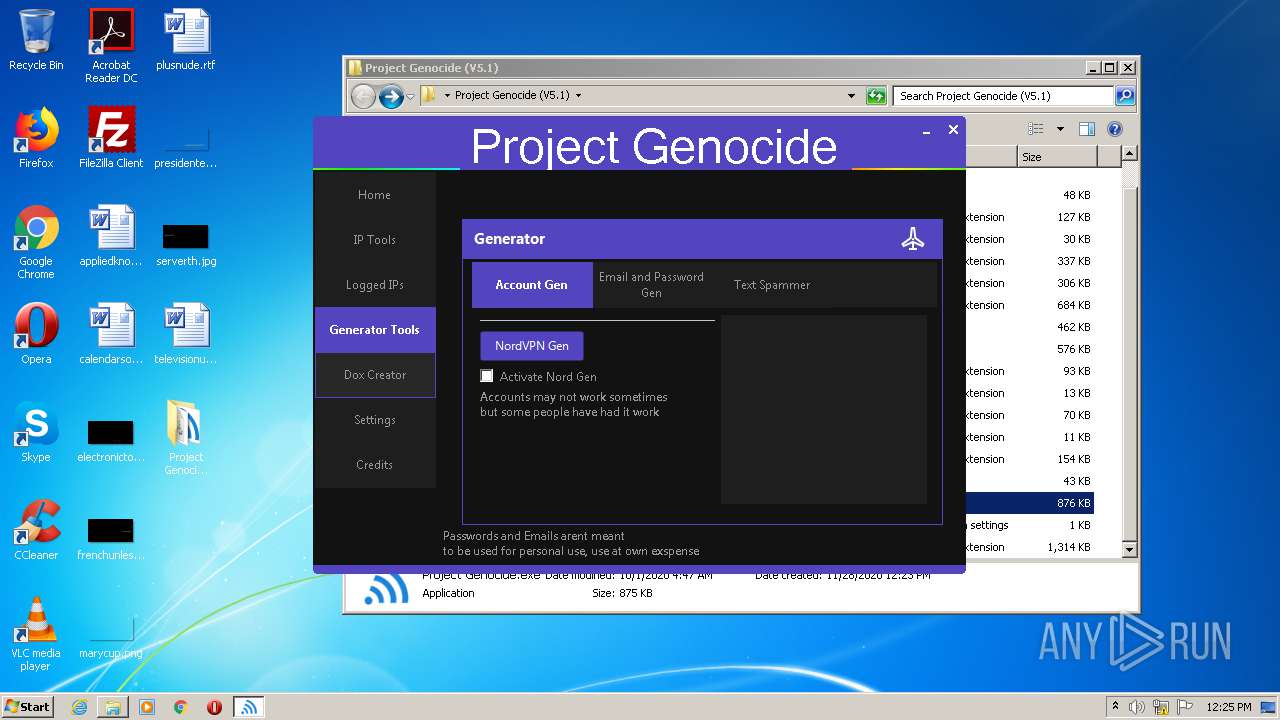
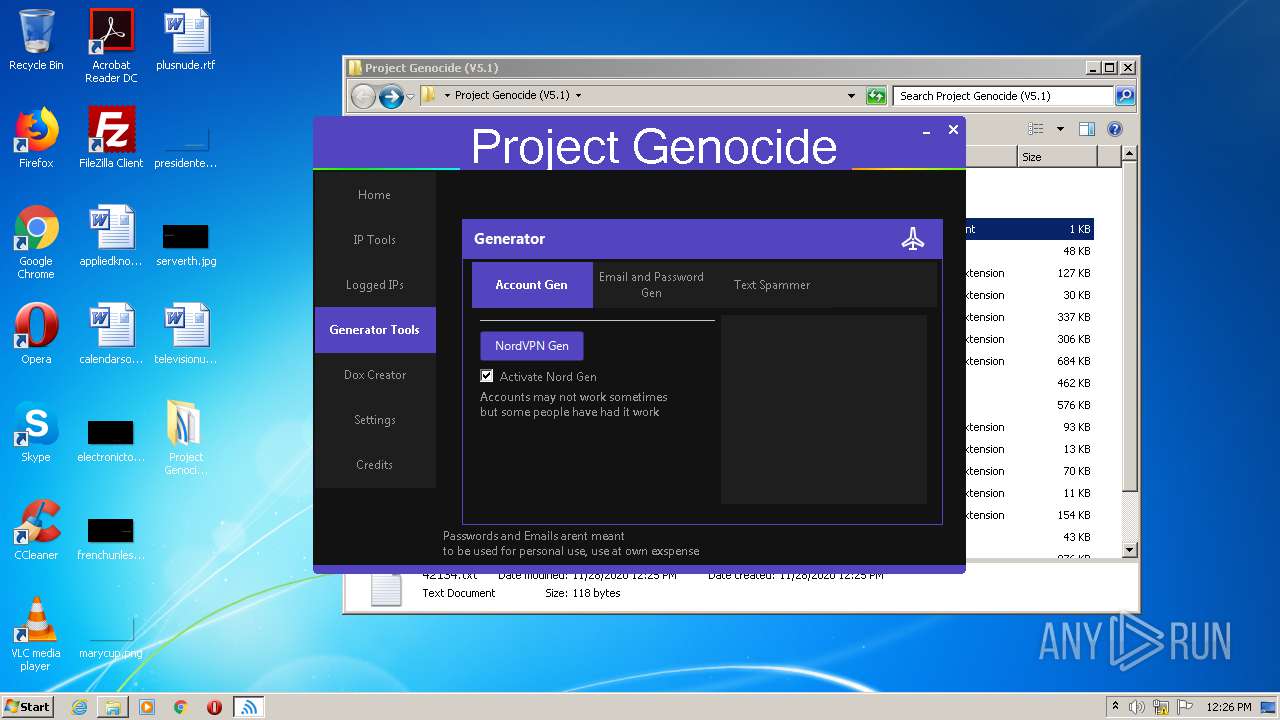
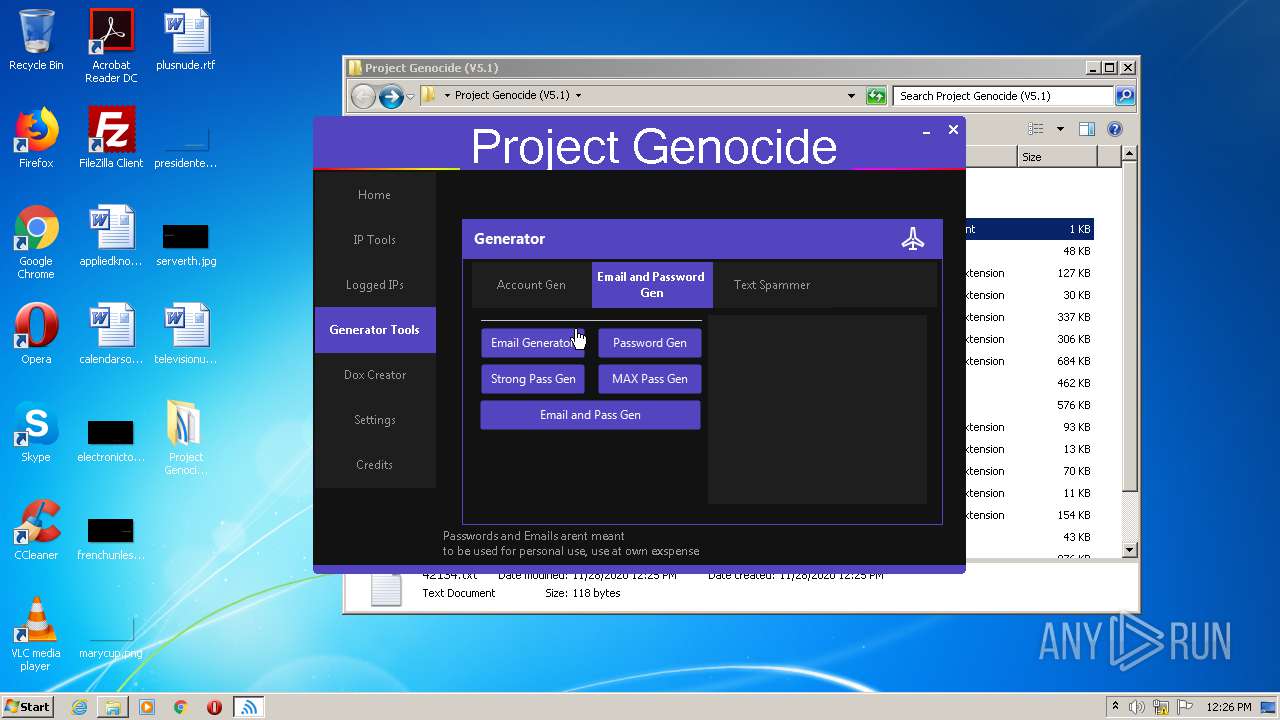
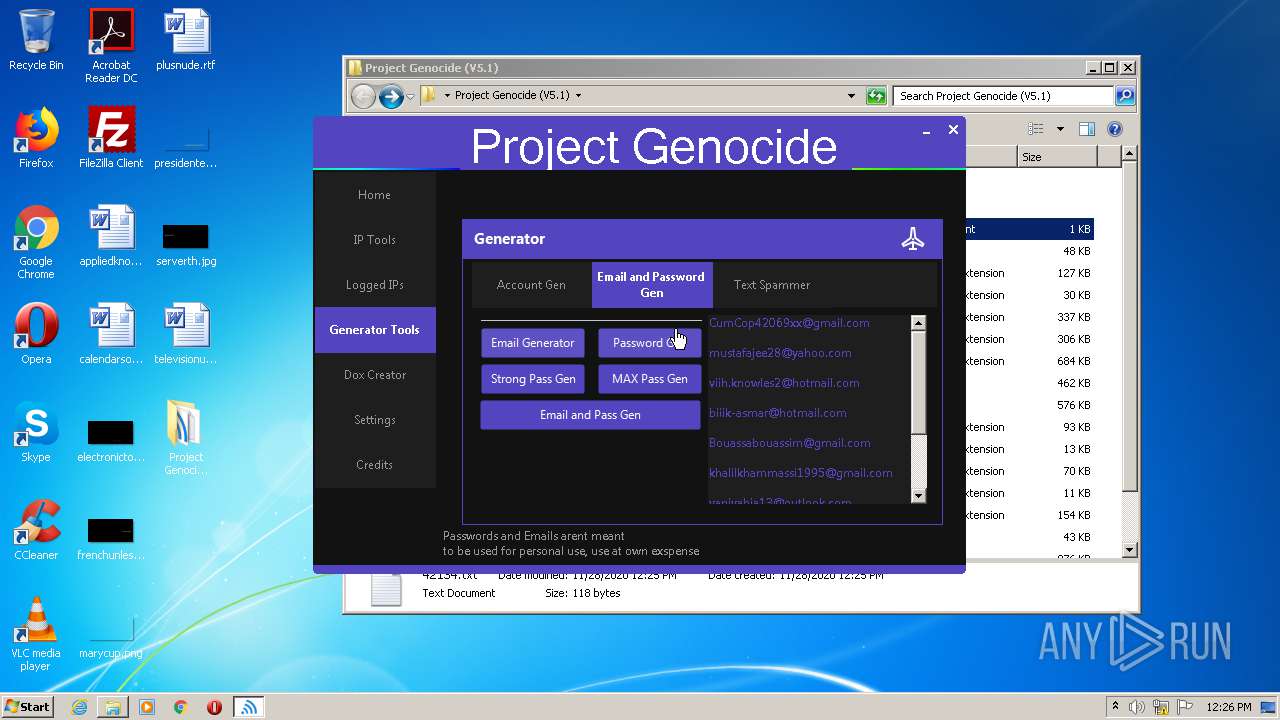
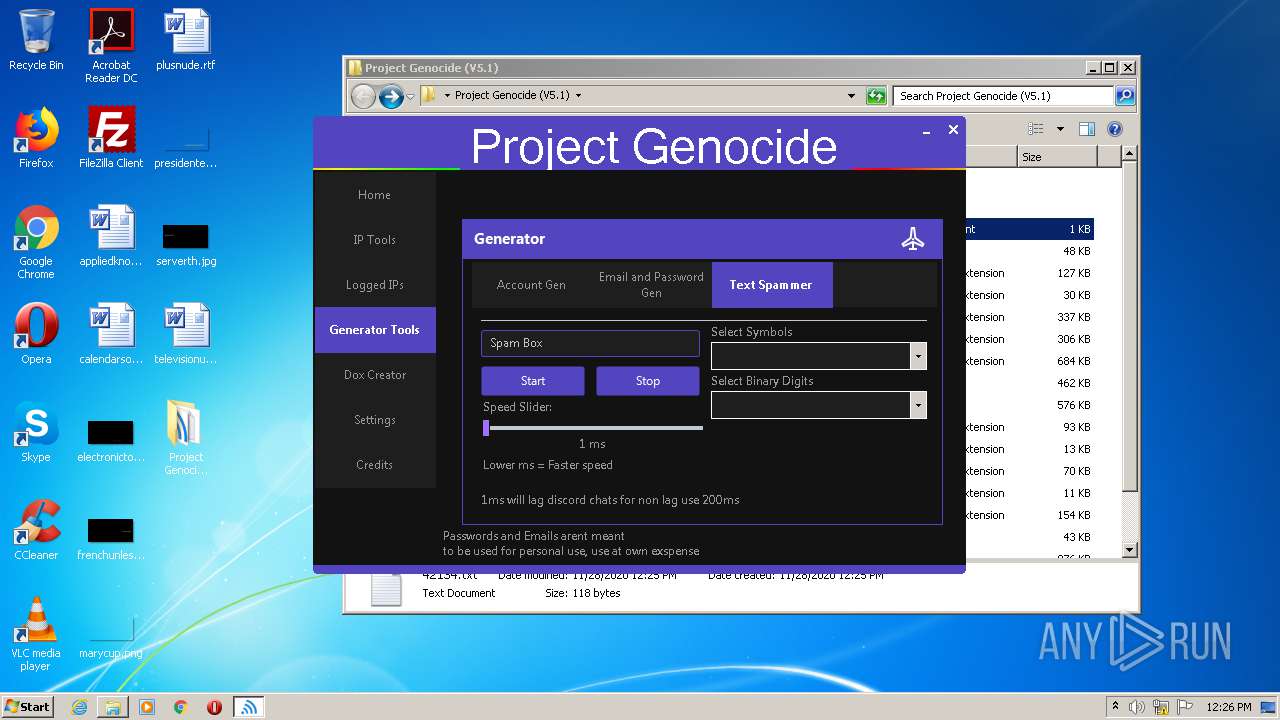
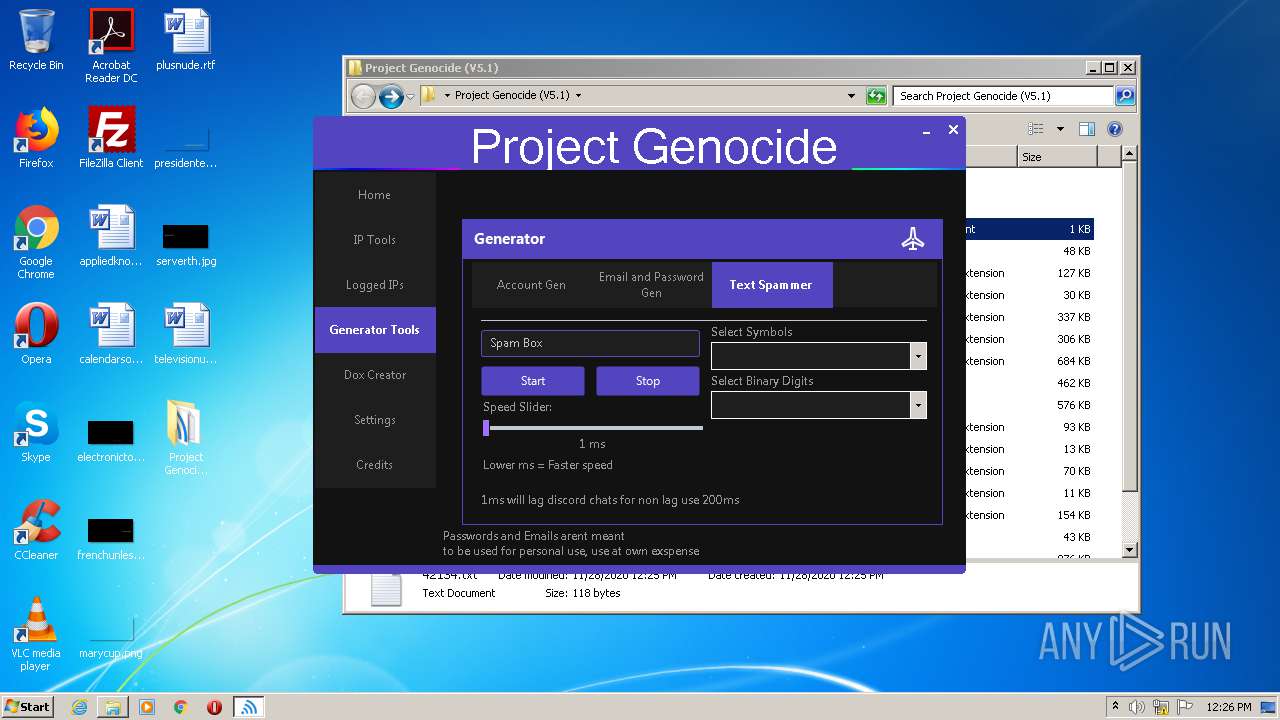
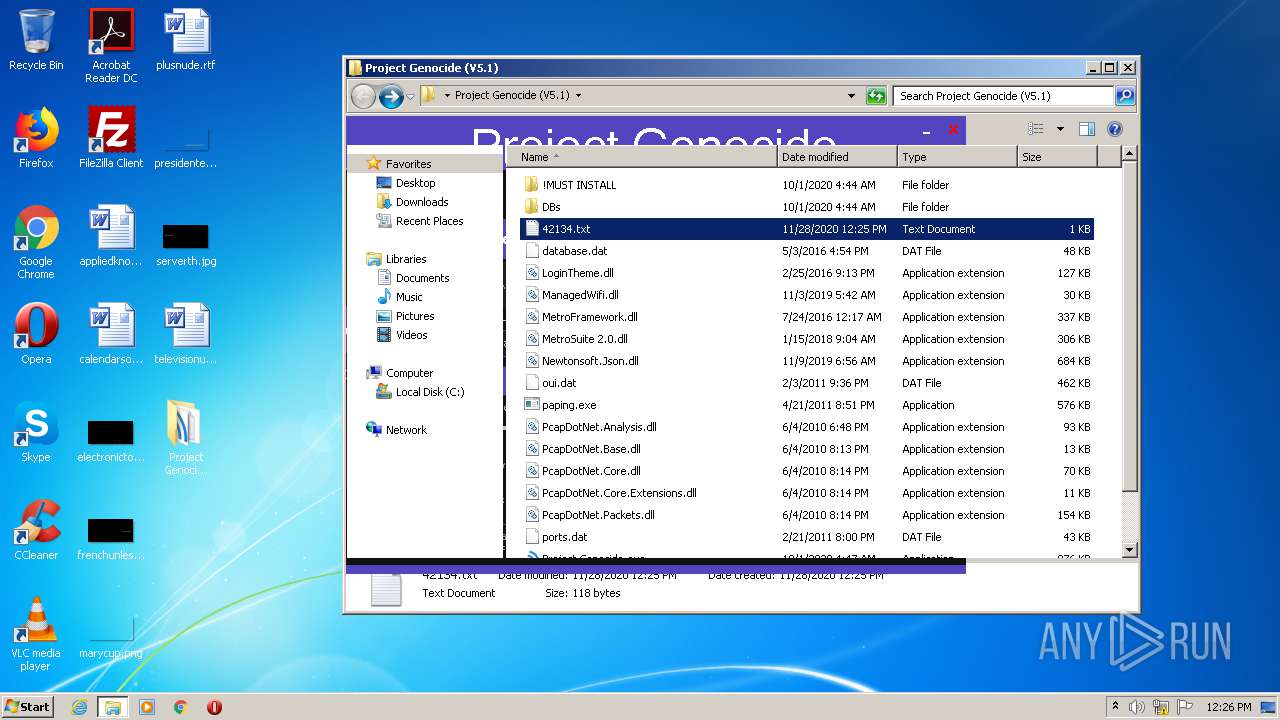
| File name: | Project Genocide (V5.1).rar |
| Full analysis: | https://app.any.run/tasks/8c7c6976-980a-4585-ac11-18bc82468b33 |
| Verdict: | Malicious activity |
| Analysis date: | November 28, 2020, 12:23:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 3215B14DDB5C374B11B9563377C046FD |
| SHA1: | B6F77B063644967778DB5E214623B0FFFB237F7C |
| SHA256: | 51779628BDD48BF85655AFD67B3BB8B17B246CC923BAE9E9732753B86756680C |
| SSDEEP: | 196608:BSXlfFu9c68YD0OEXrHw8l+nQcfR4DKJXhyww8c/UXn/Mh6ep6MpTlSNUi2PUPj7:BWlWZZCHUQuJQMXK6eJSL2Yf |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3352)
- explorer.exe (PID: 356)
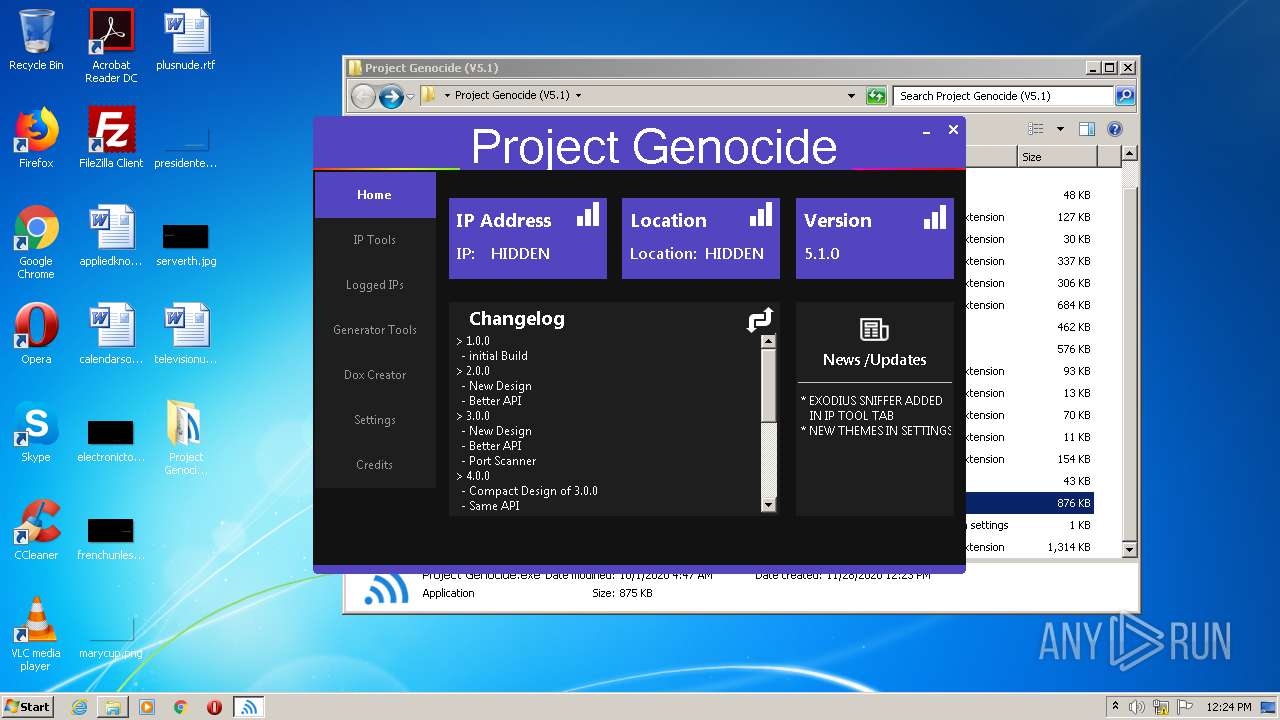
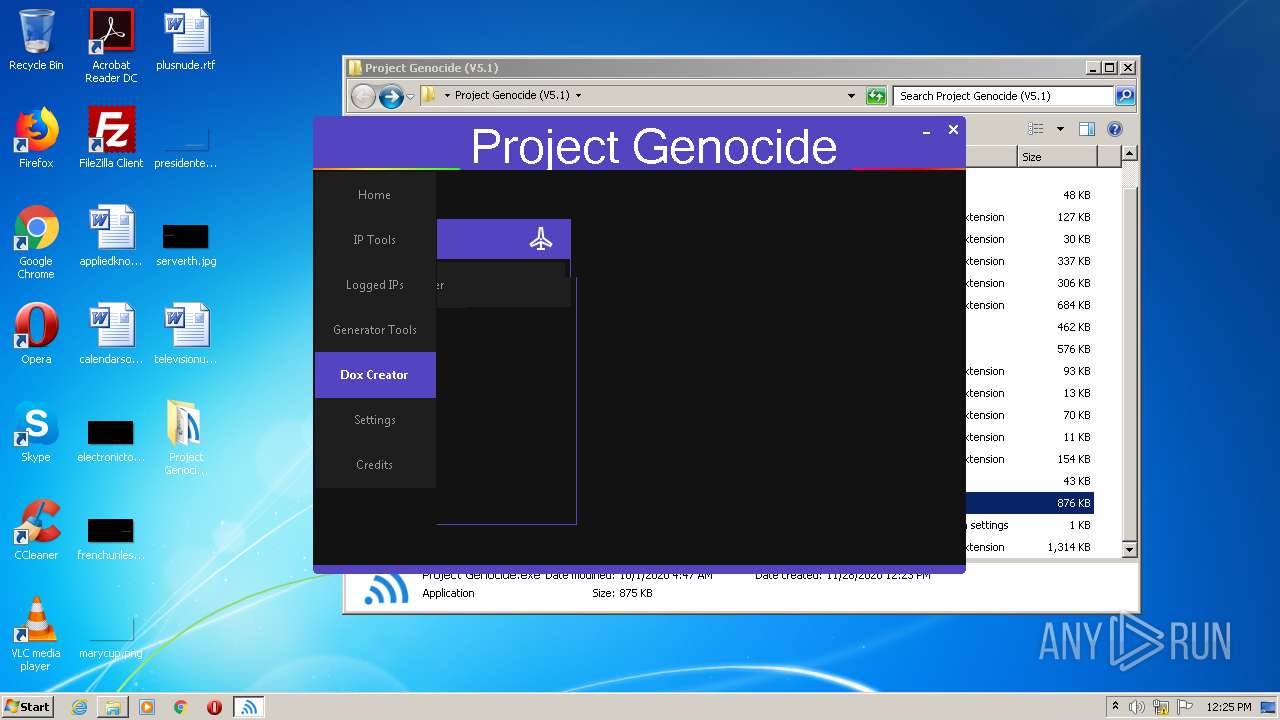
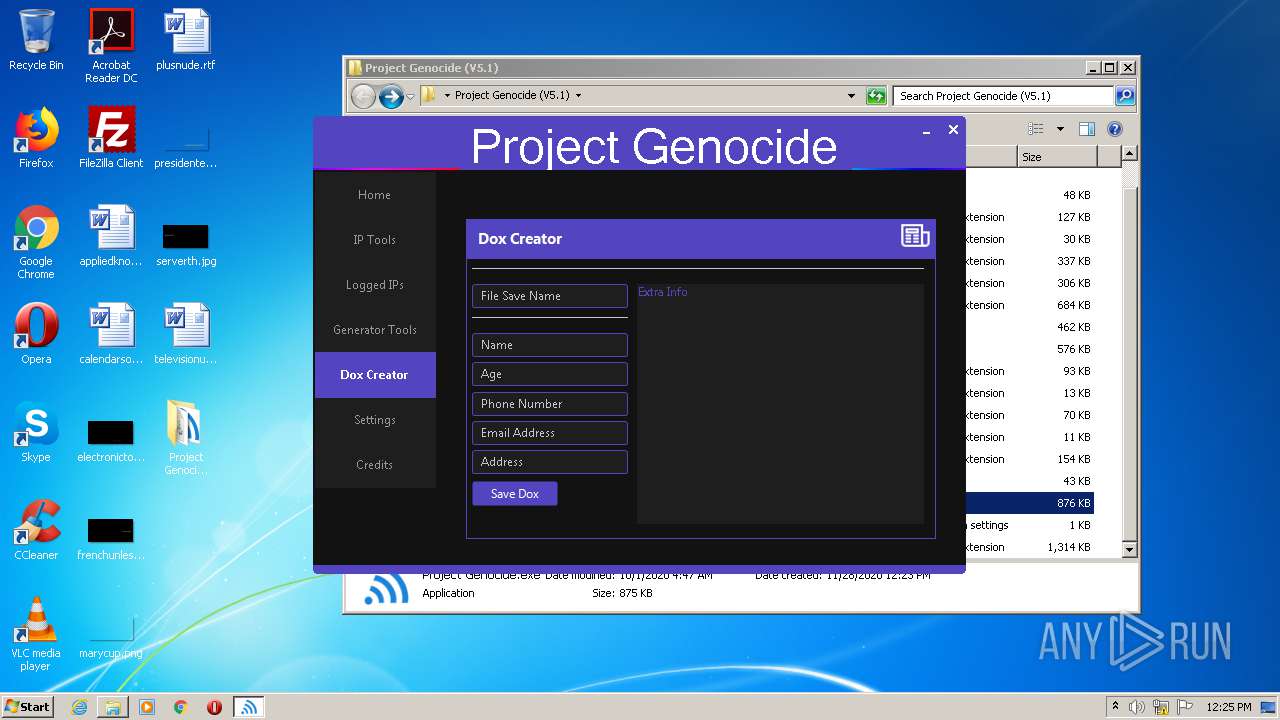
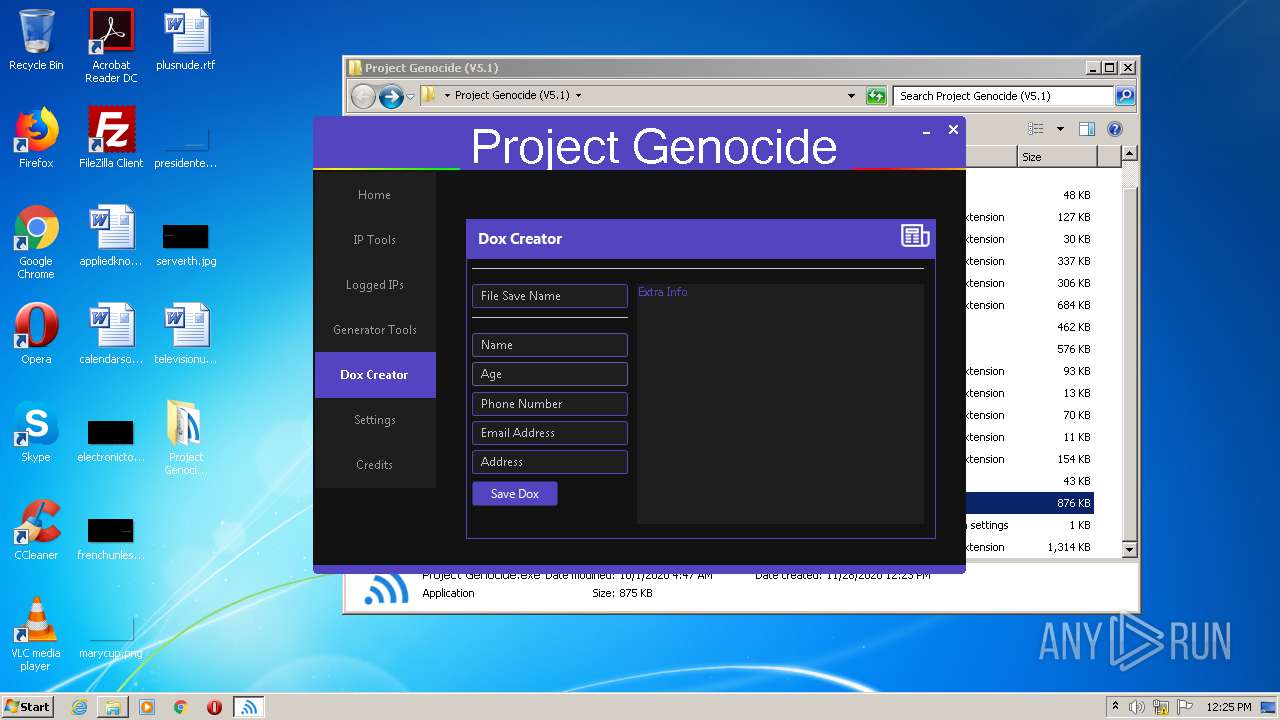
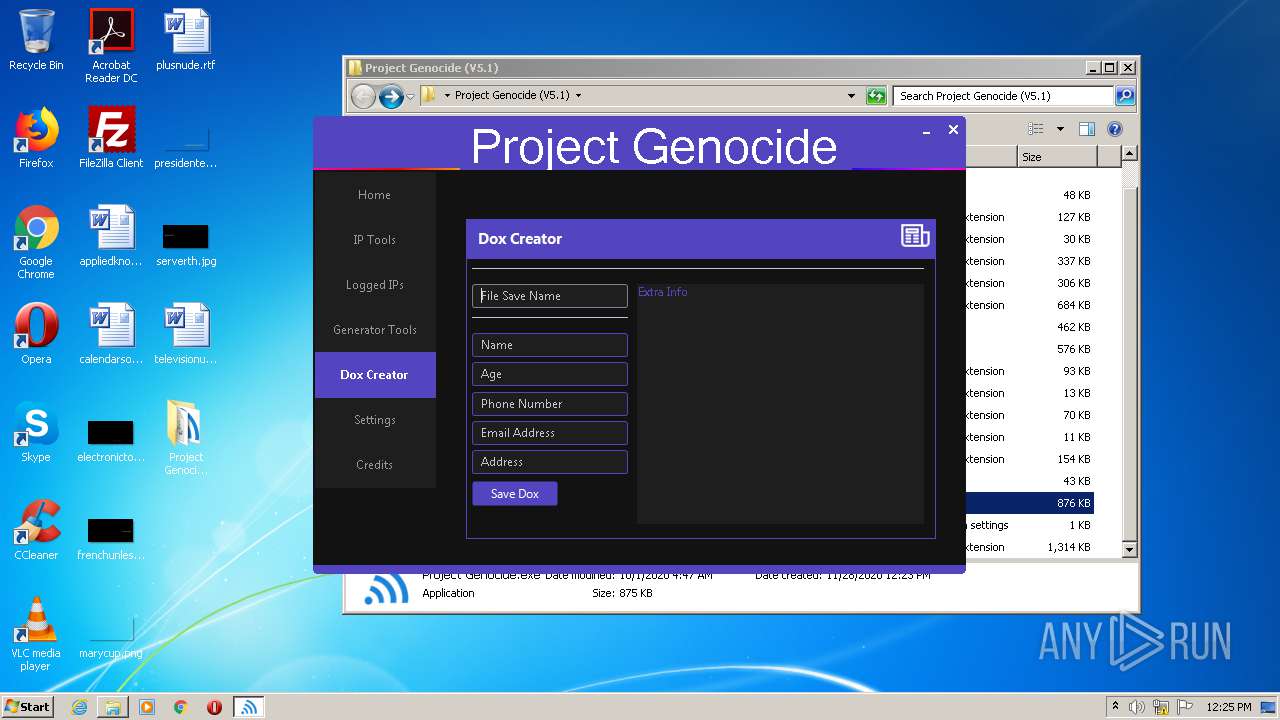
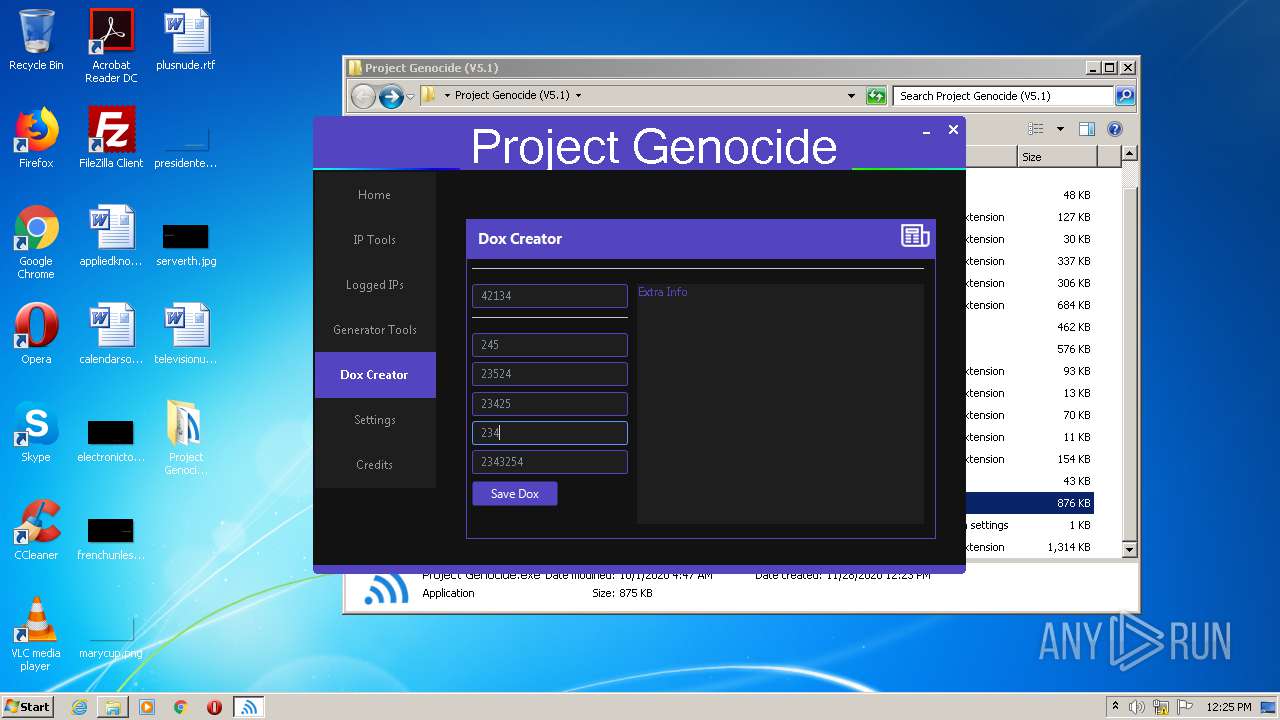
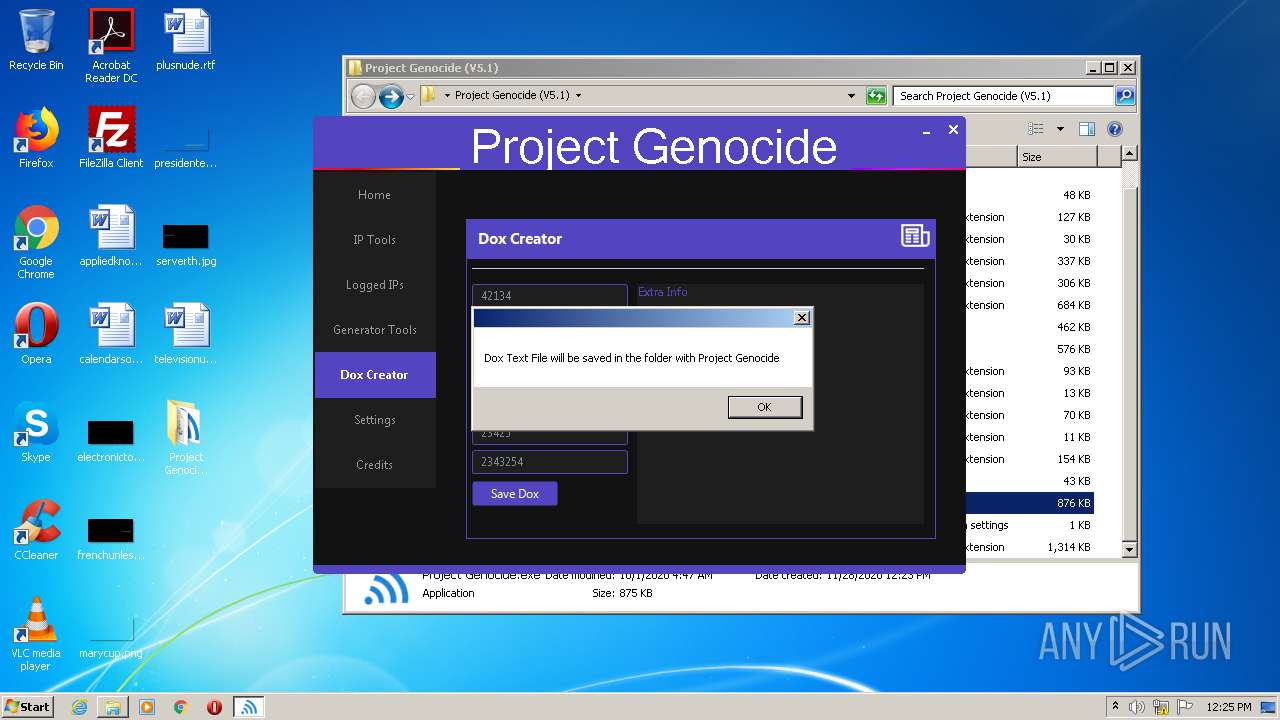
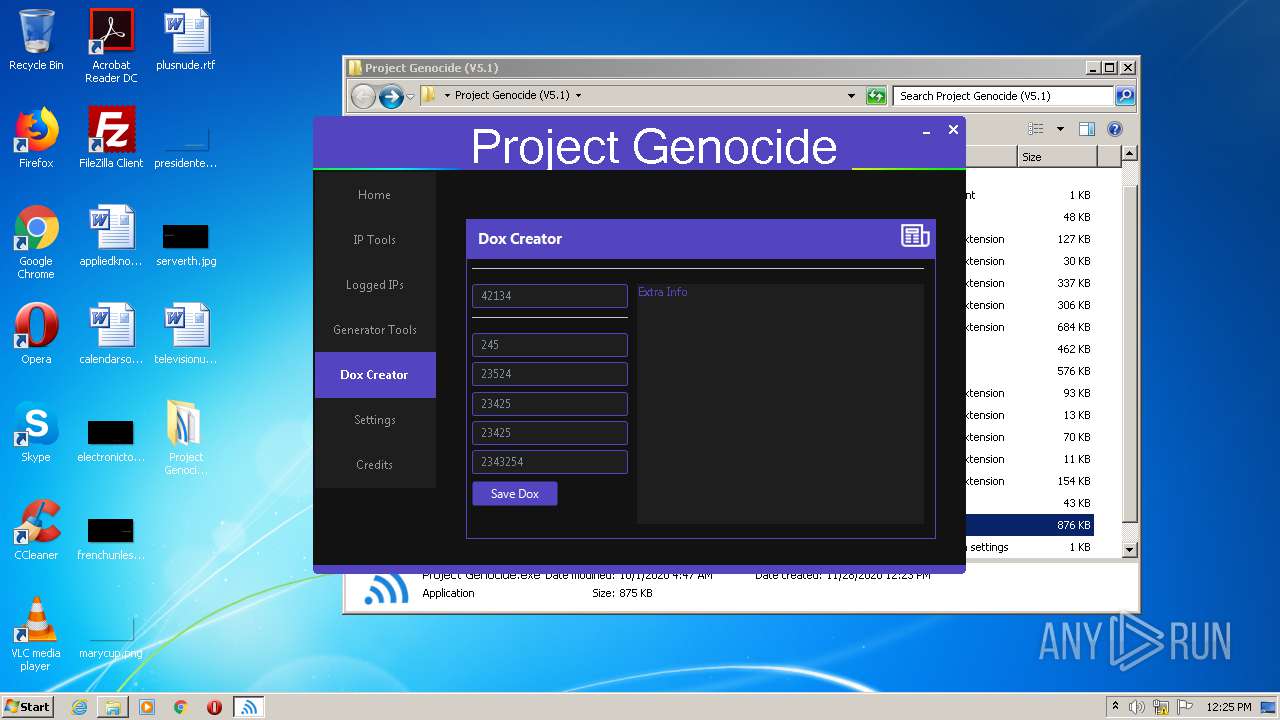
- Project Genocide.exe (PID: 3608)
Application was dropped or rewritten from another process
- Project Genocide.exe (PID: 3608)
SUSPICIOUS
Drops a file with too old compile date
- WinRAR.exe (PID: 2832)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2832)
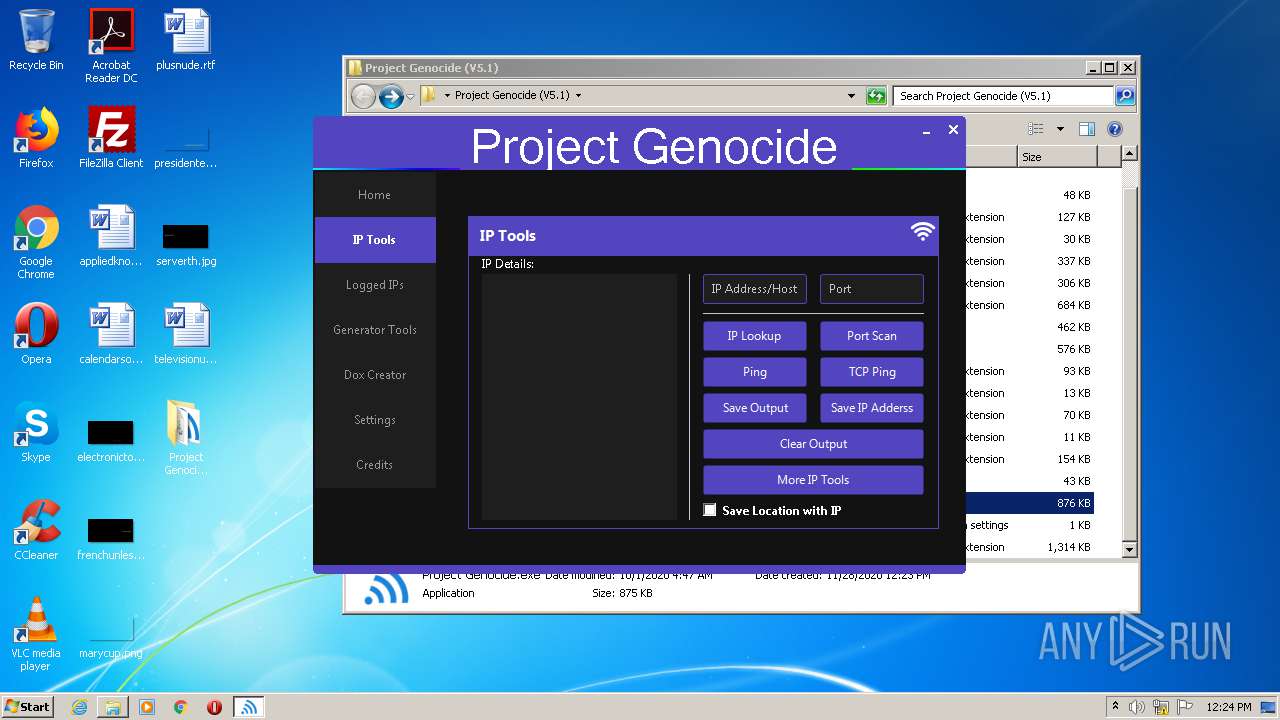
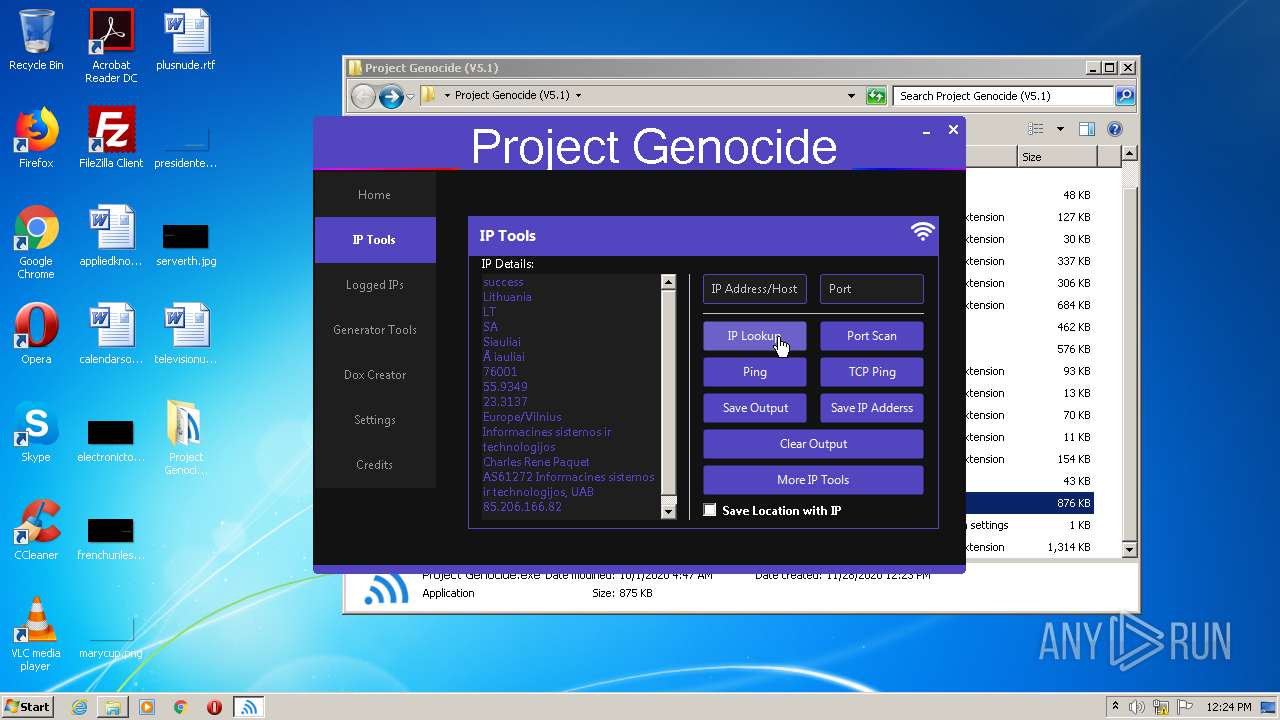
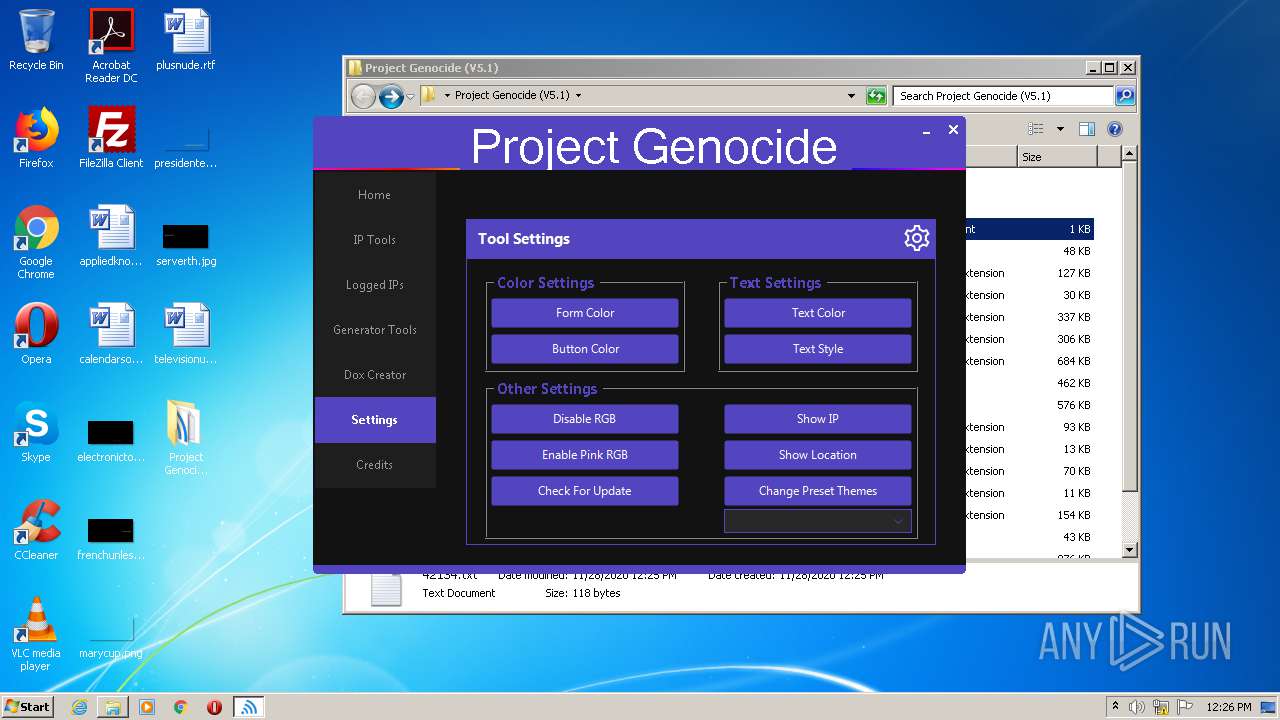
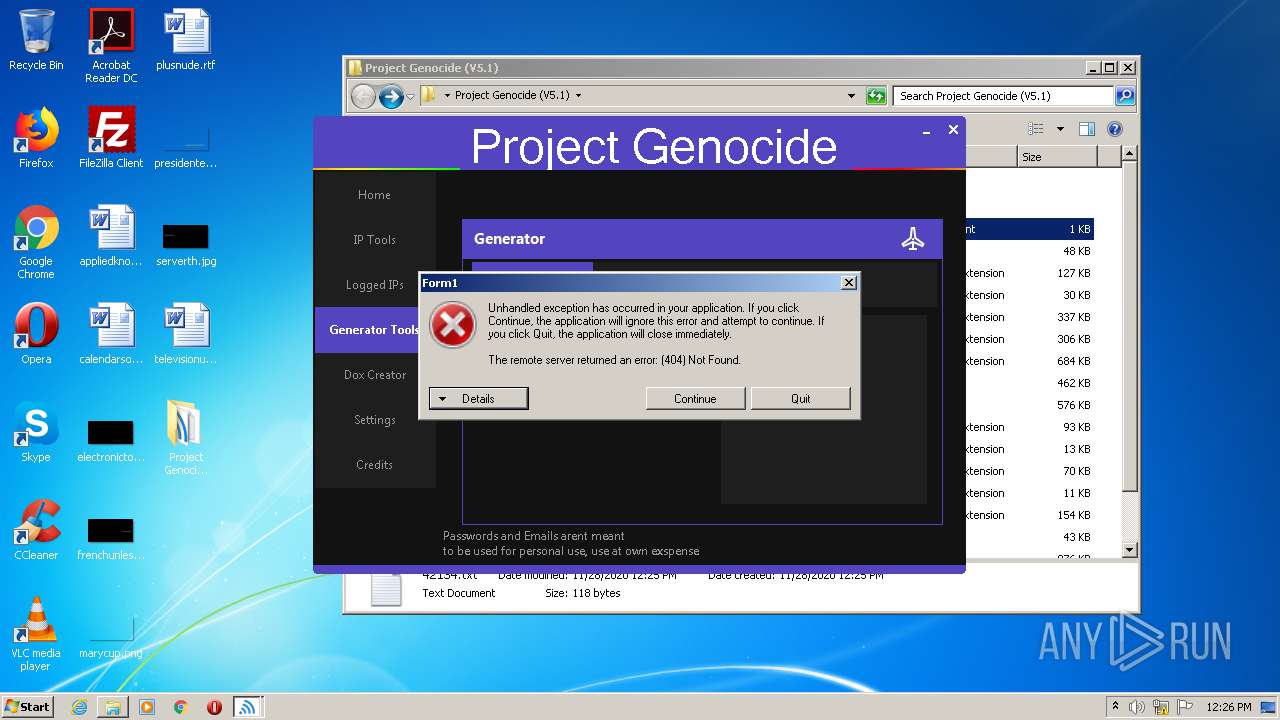
Checks for external IP
- Project Genocide.exe (PID: 3608)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2832)
Creates files in the user directory
- explorer.exe (PID: 356)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
44
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 356 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
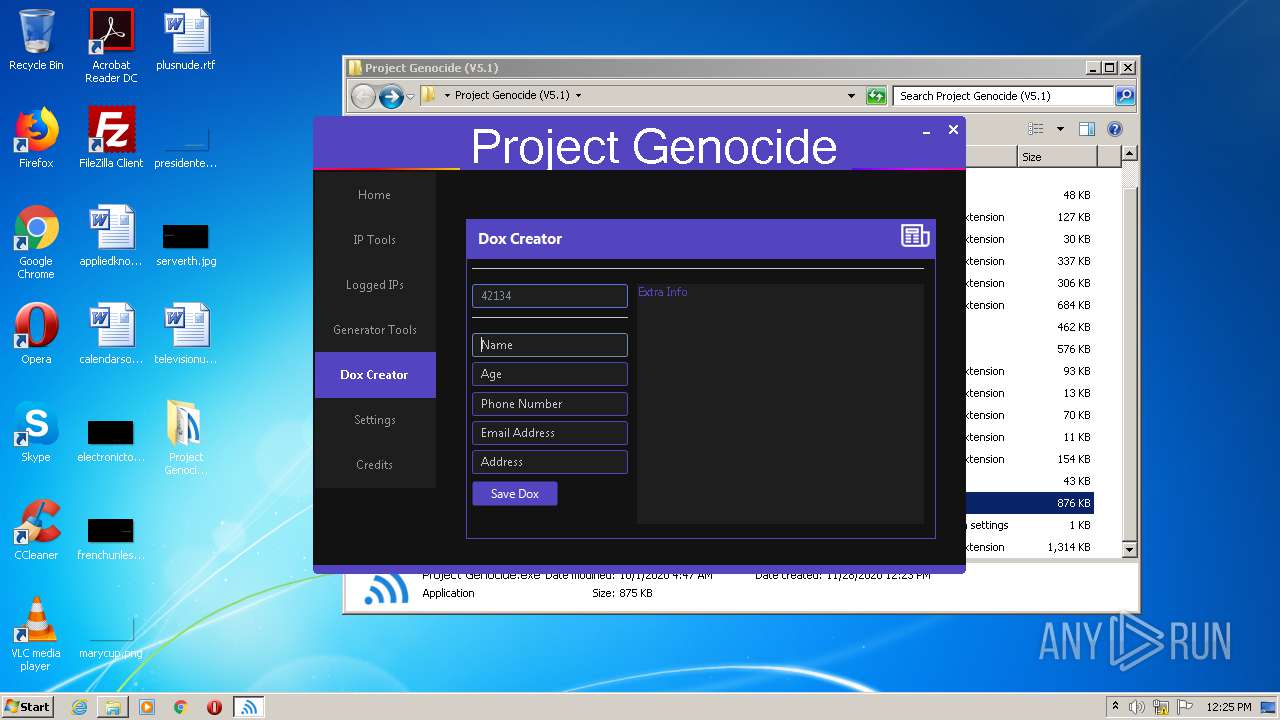
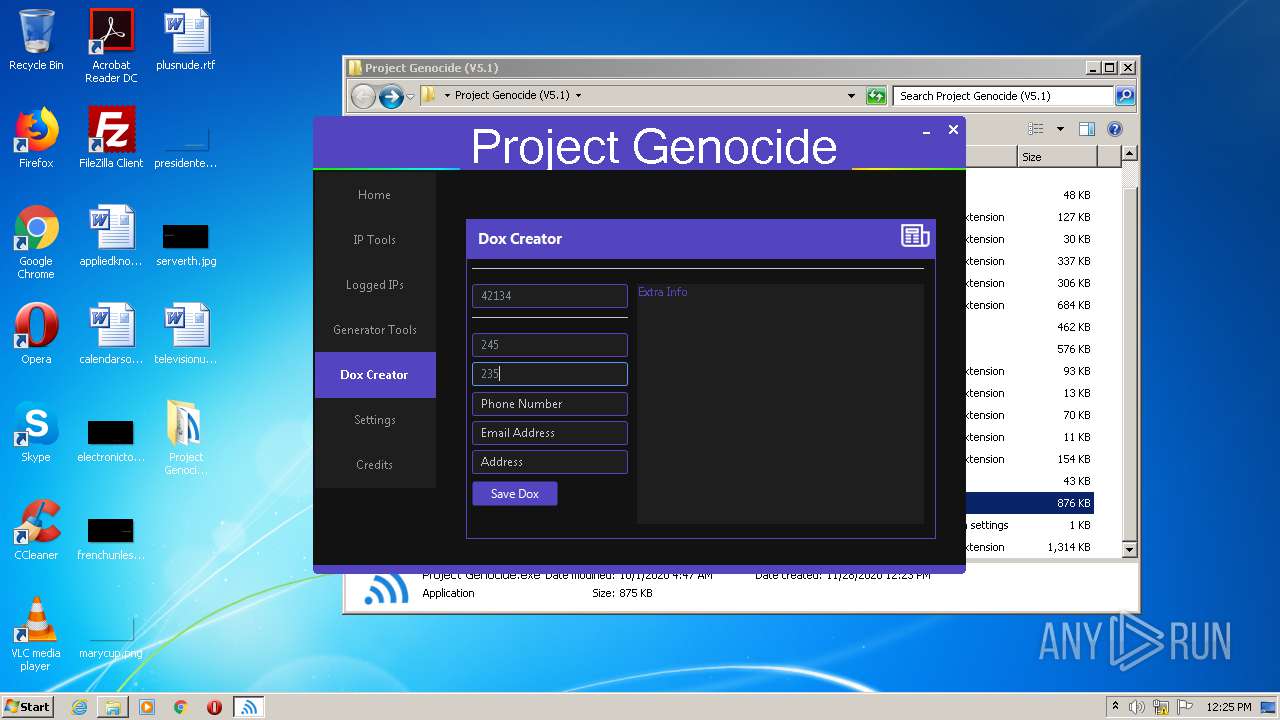
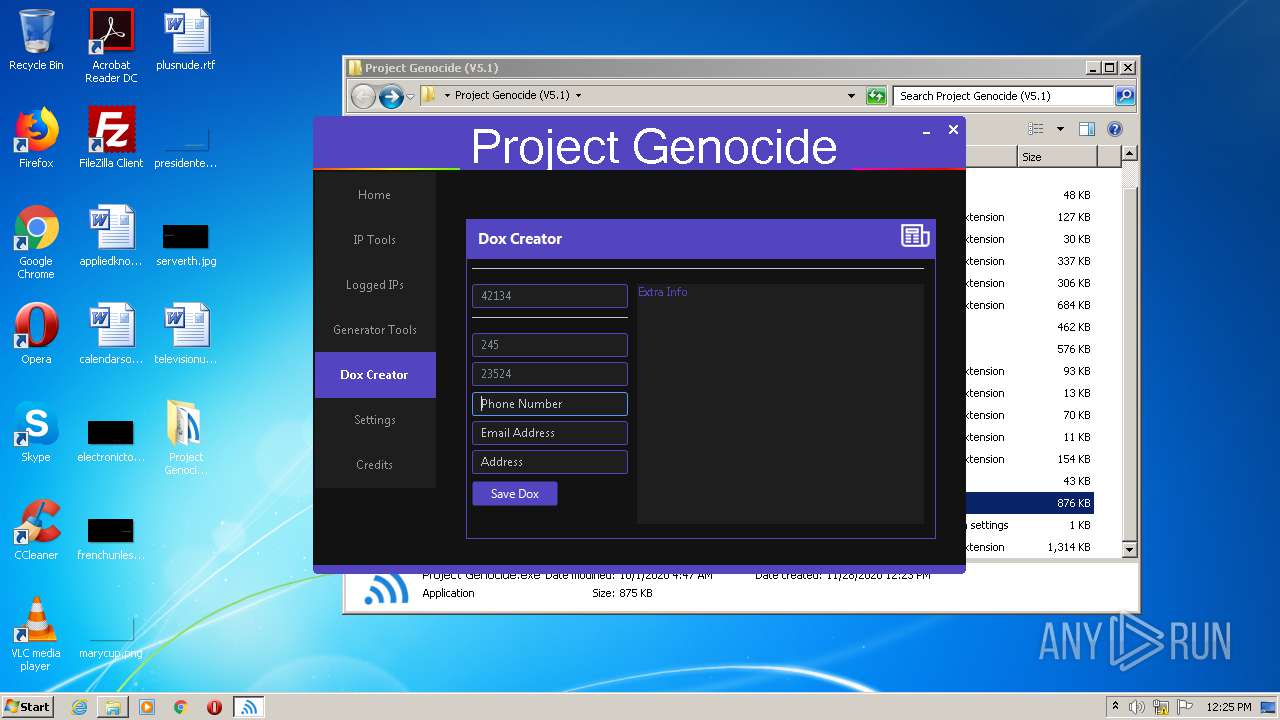
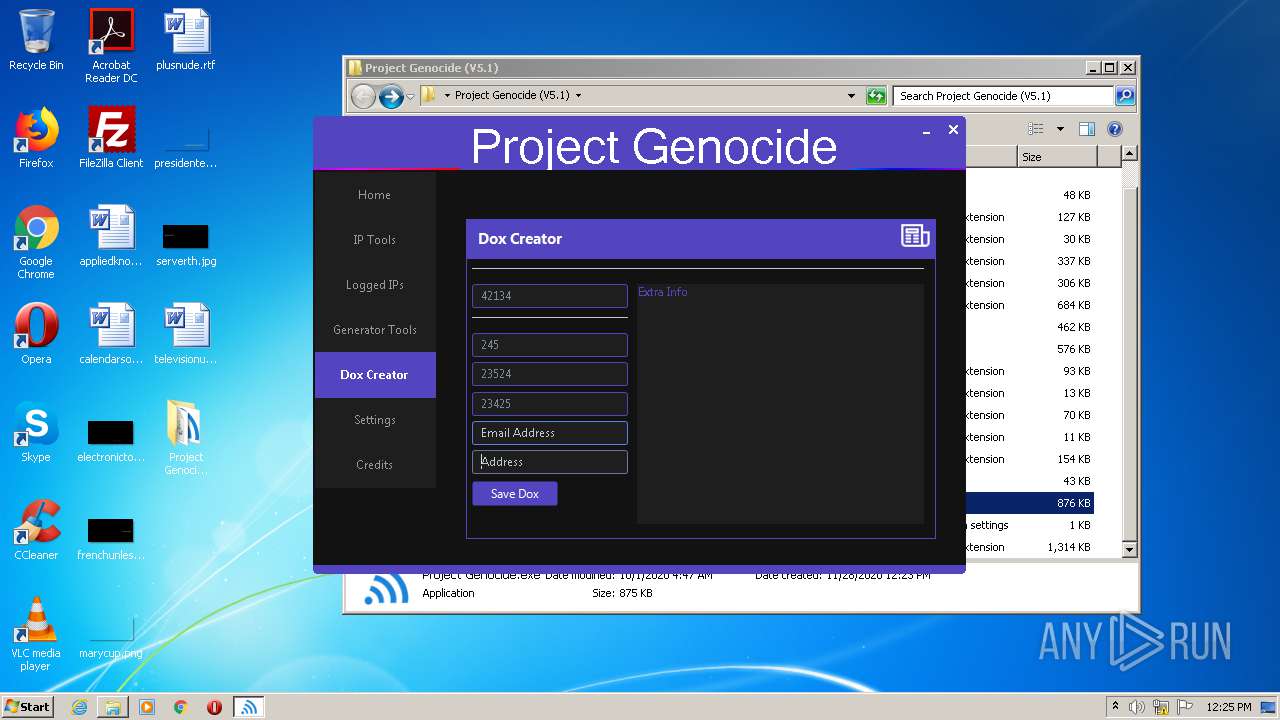
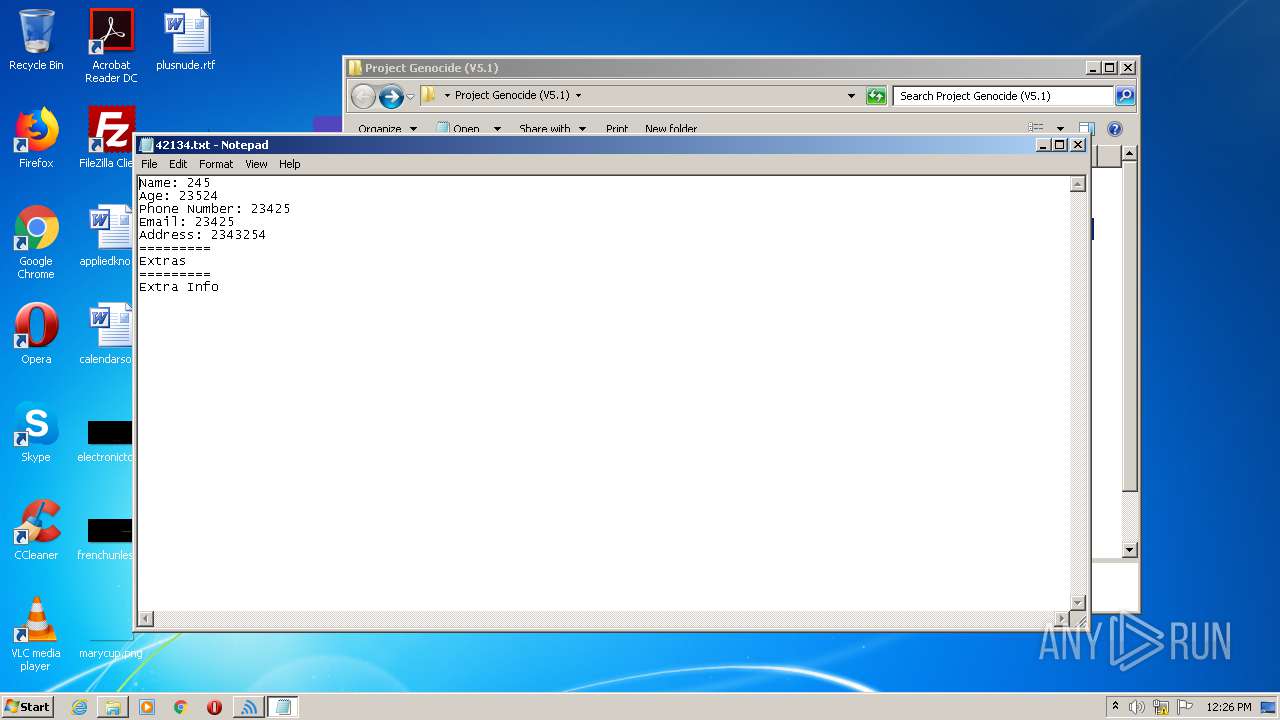
| 2340 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Project Genocide (V5.1)\42134.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2544 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Project Genocide (V5.1)\DBs\OUI.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2832 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Project Genocide (V5.1).rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3352 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
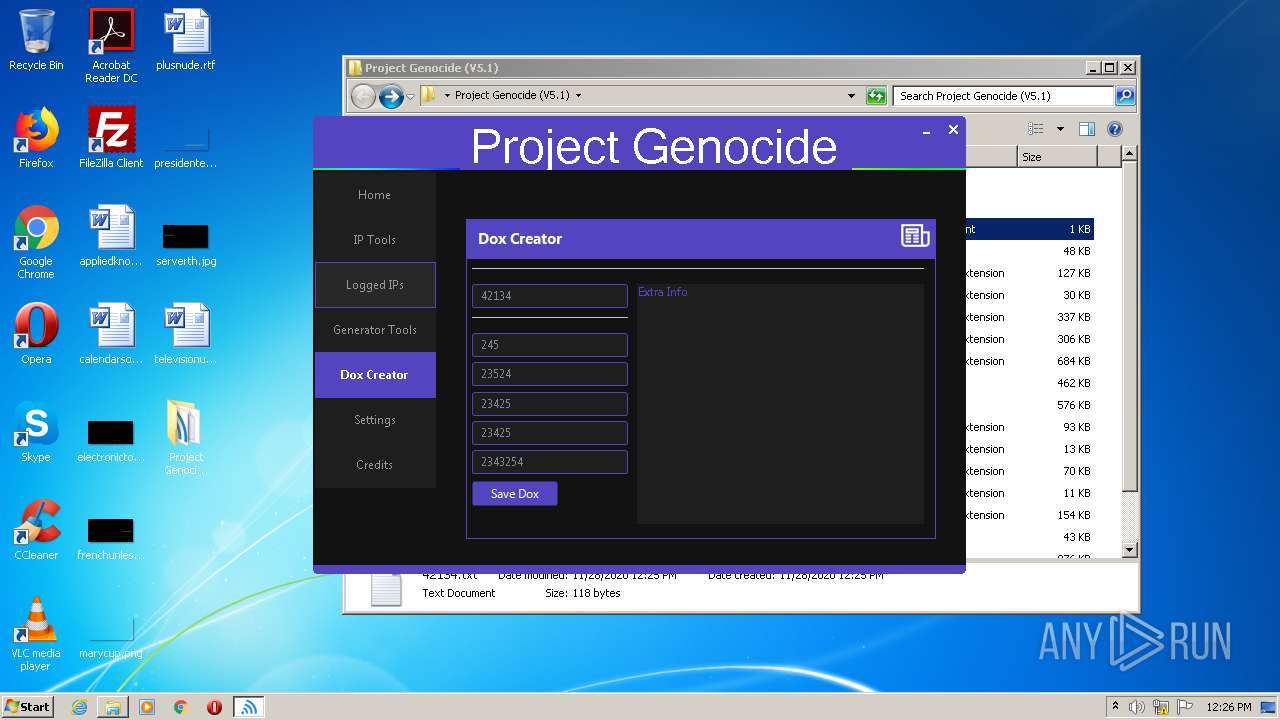
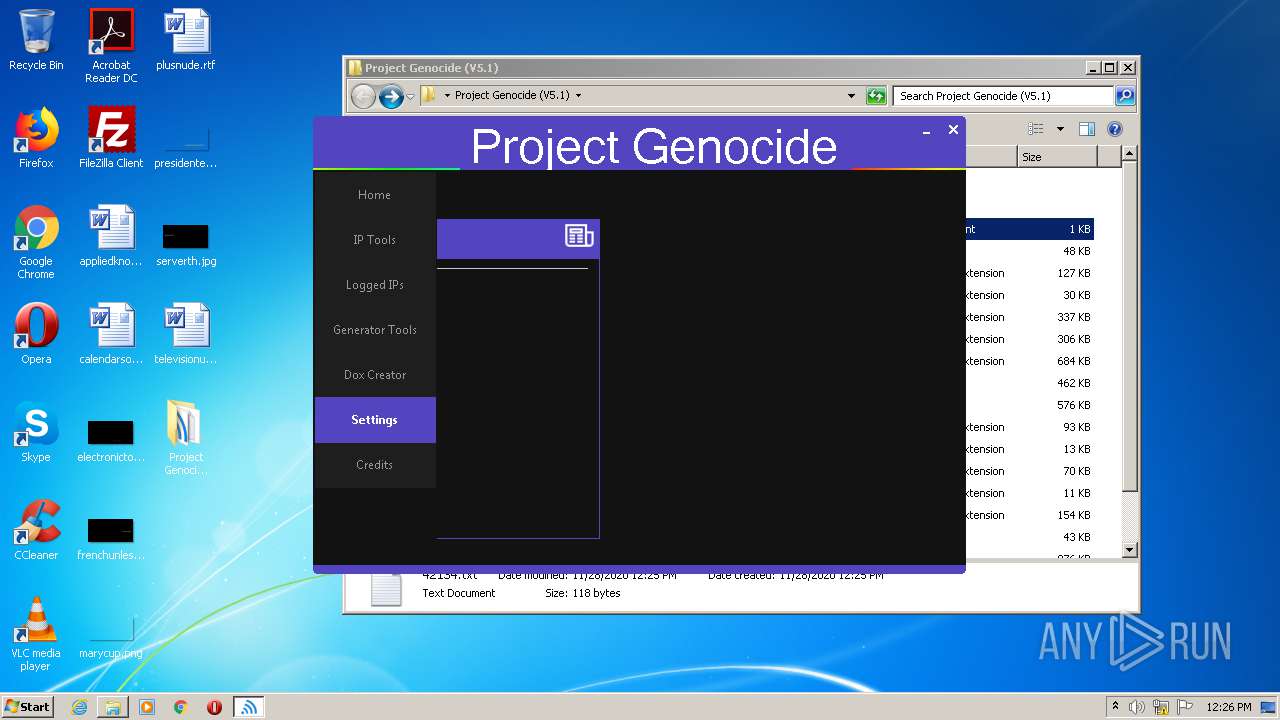
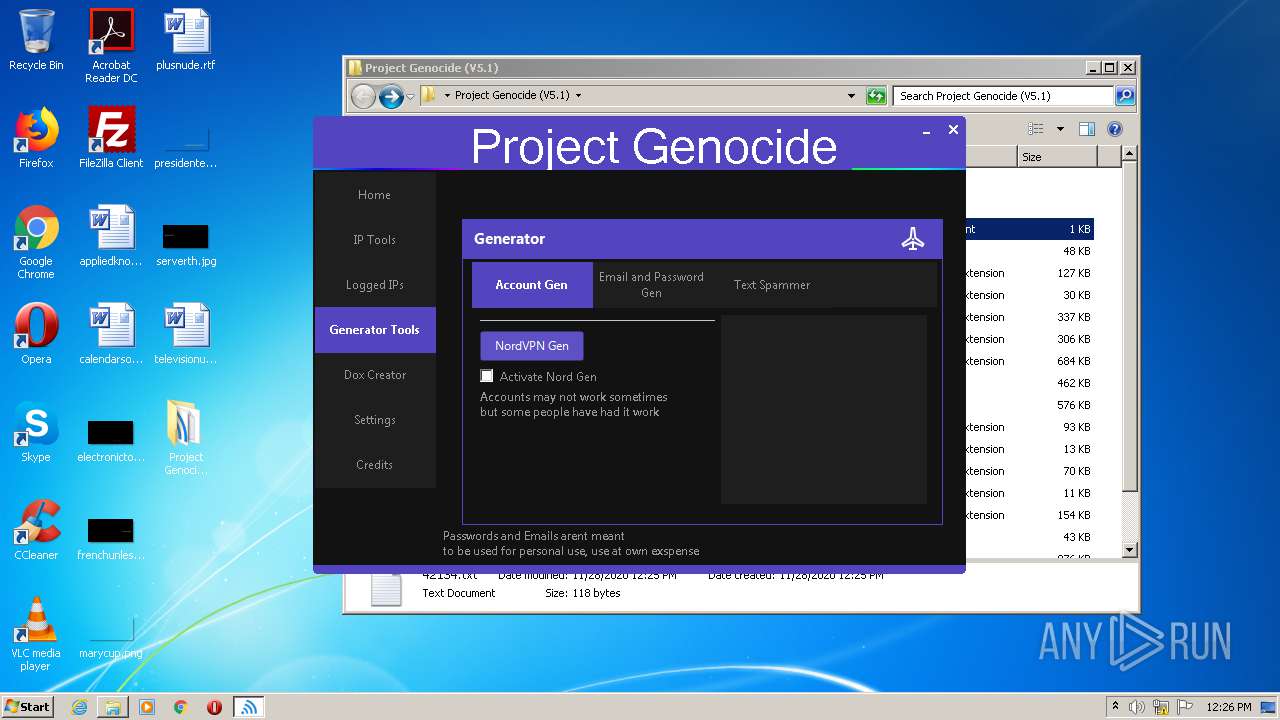
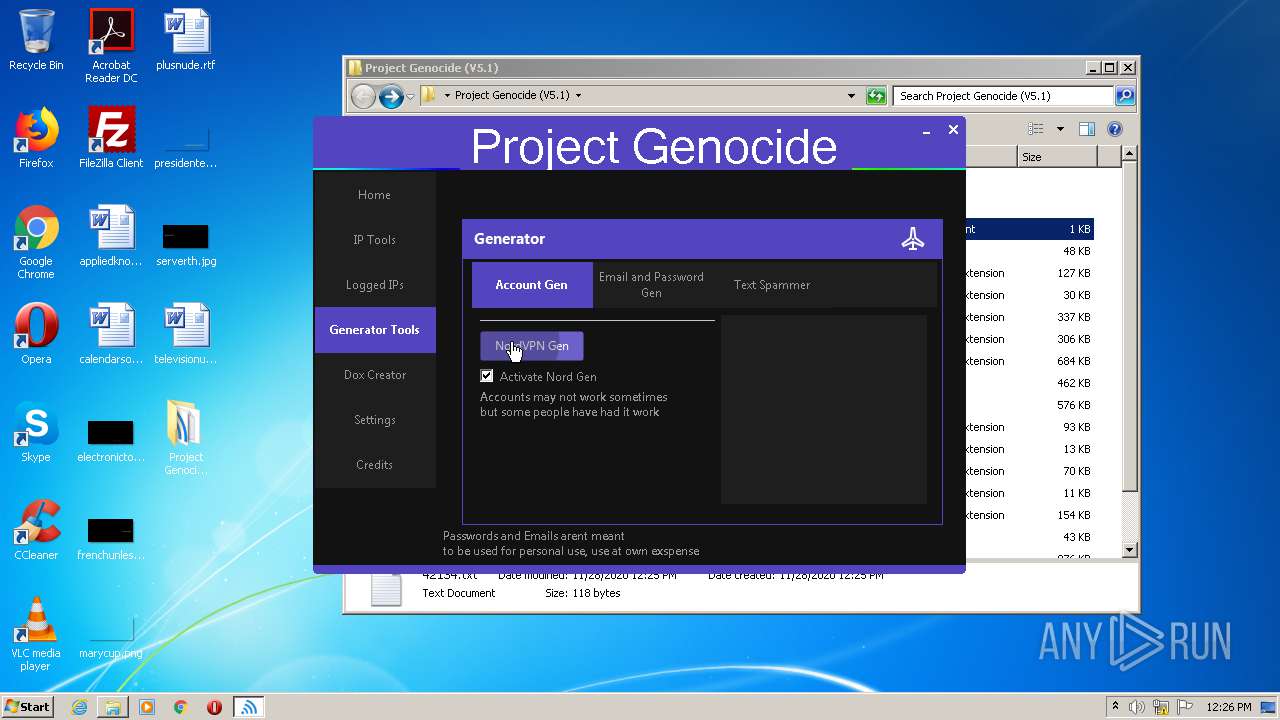
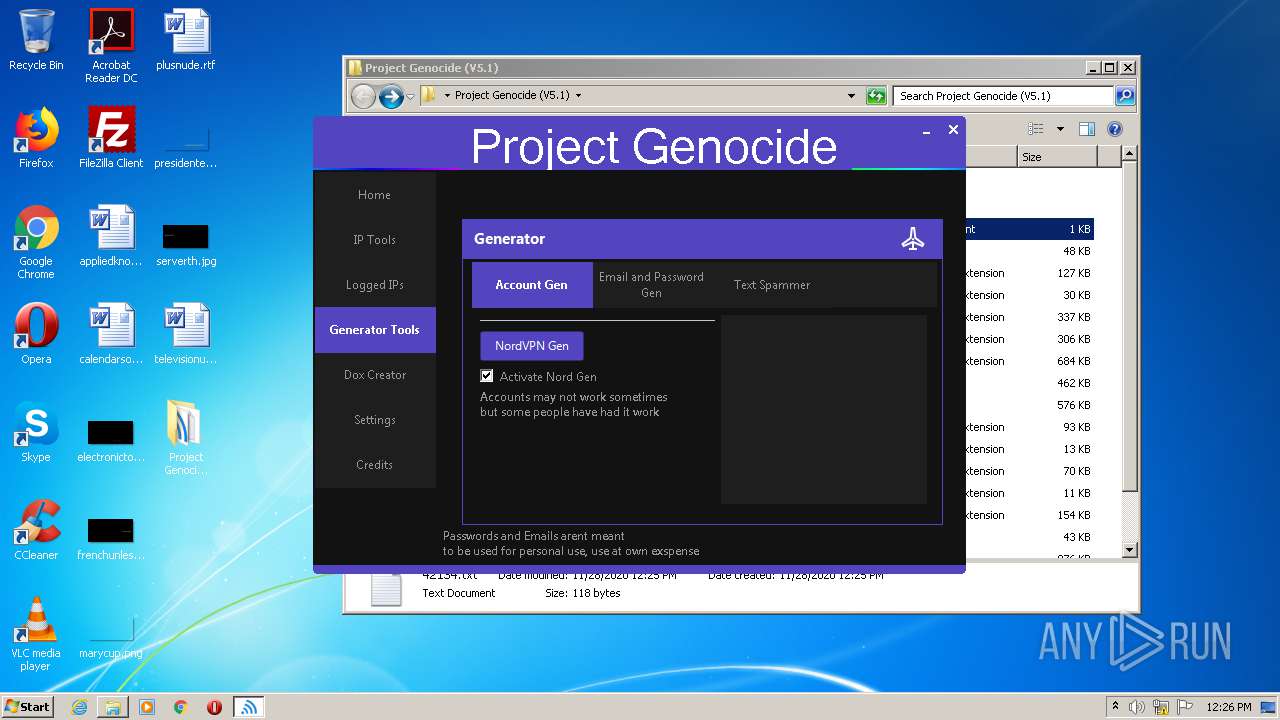
| 3608 | "C:\Users\admin\Desktop\Project Genocide (V5.1)\Project Genocide.exe" | C:\Users\admin\Desktop\Project Genocide (V5.1)\Project Genocide.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: KiekoTool Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
3 428
Read events
3 104
Write events
324
Delete events
0
Modification events
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Project Genocide (V5.1).rar | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (356) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (356) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
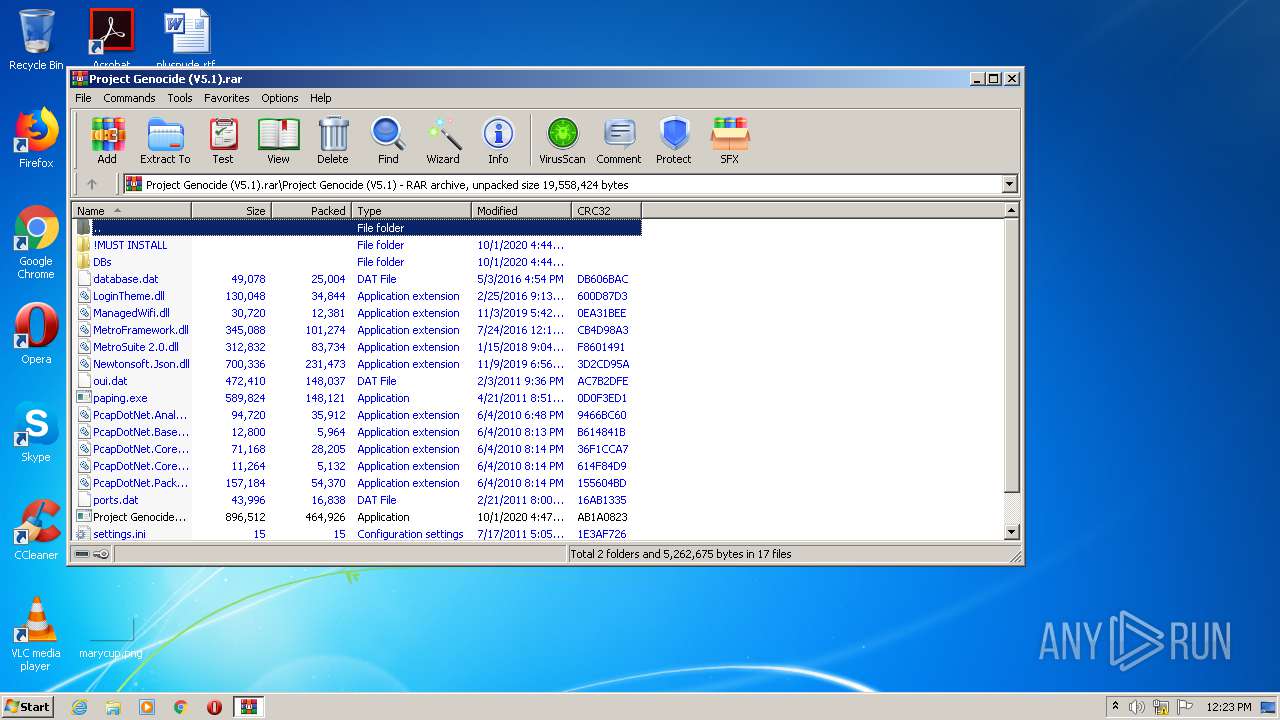
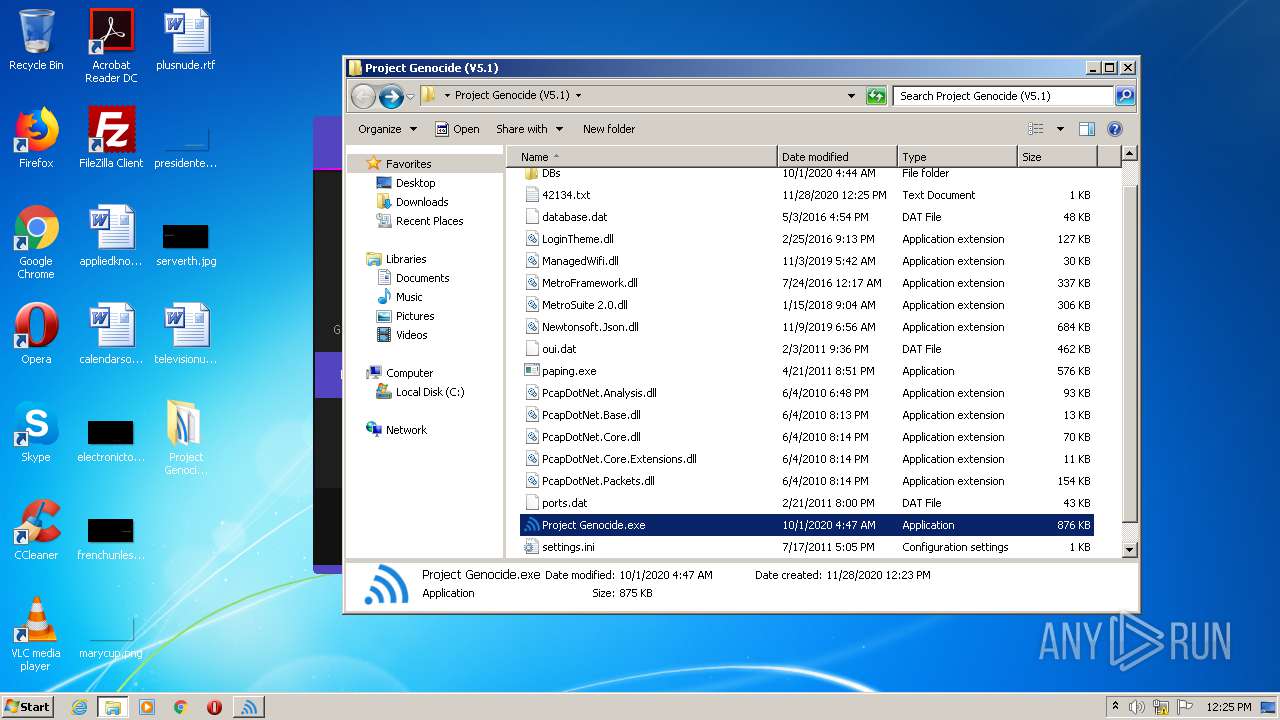
Executable files
13
Suspicious files
1
Text files
7
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Project Genocide (V5.1)\!MUST INSTALL\MUST INSTALL to use Sniffer\Install If Exodius Sniffer wont open.rar | — | |
MD5:— | SHA256:— | |||
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Project Genocide (V5.1)\LoginTheme.dll | executable | |
MD5:78C847DA2E3C7FD889E24F4756CACFA7 | SHA256:1AF039906D73069B2A2D5F09552EB5807FB16121414EFD0989040578806D6609 | |||
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Project Genocide (V5.1)\DBs\OUI.txt | text | |
MD5:04DA9533EFF475D6BF8ED595662D1311 | SHA256:D2331E4FCB141AA9AF169F88C635042D6F1E7FB867F3E01F30948F6F17DB0A99 | |||
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Project Genocide (V5.1)\database.dat | text | |
MD5:C204FD133C3C496D7270A54A5B3E8D89 | SHA256:CF0D342926D25DA2595C49FD34608647032D6E620B39B4005F0CFDC23708FCBF | |||
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Project Genocide (V5.1)\ManagedWifi.dll | executable | |
MD5:E05F0BC5B6CFBCCDB29F22F2A4B57DE9 | SHA256:1F34E970ACB3AE1D7F84B20A2A64C7B8B5F23821DA74370CFB62CFBD99C8EE13 | |||
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Project Genocide (V5.1)\MetroFramework.dll | executable | |
MD5:463D3B29B398E0240B5309A0E05BA3E0 | SHA256:5B1074FC3110E41D9FA5DB4F32A67C6B19693C66B35E84200AEAB3F746E49085 | |||
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Project Genocide (V5.1)\paping.exe | executable | |
MD5:AA32A25FA1FA895F7AB709B88349C933 | SHA256:A54EAA578AF16919B4A582C687DA350038DB018A9748F9A0EE3C4A5C01AF9BD2 | |||
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Project Genocide (V5.1)\Newtonsoft.Json.dll | executable | |
MD5:6815034209687816D8CF401877EC8133 | SHA256:7F912B28A07C226E0BE3ACFB2F57F050538ABA0100FA1F0BF2C39F1A1F1DA814 | |||
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Project Genocide (V5.1)\oui.dat | text | |
MD5:326902D595521AAF2376CEDC4C966B05 | SHA256:0D45A7D5C4E3AF25F054402BCE40866AE37B34C28E545903A7F9DFBEB099043A | |||
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Project Genocide (V5.1)\PcapDotNet.Base.dll | executable | |
MD5:6F2E6B9046E7ED3CE43A34A7B701FBF9 | SHA256:39D850B2412D78580EA842730BB56F59474A8DE4C2D9218D7593CD5B96AC9BAF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
5
DNS requests
7
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3608 | Project Genocide.exe | GET | 200 | 172.67.68.191:80 | http://free.ipwhois.io/json/ | US | text | 788 b | suspicious |
3608 | Project Genocide.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/ | unknown | text | 205 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3608 | Project Genocide.exe | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
3608 | Project Genocide.exe | 54.243.161.145:443 | api.ipify.org | Amazon.com, Inc. | US | suspicious |
3608 | Project Genocide.exe | 172.67.68.191:80 | free.ipwhois.io | — | US | suspicious |
3608 | Project Genocide.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
3608 | Project Genocide.exe | 104.23.99.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
api.ipify.org |
| shared |
free.ipwhois.io |
| suspicious |
ip-api.com |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3608 | Project Genocide.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
3608 | Project Genocide.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
3608 | Project Genocide.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup - free .ipwhois .io |
3608 | Project Genocide.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
3608 | Project Genocide.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
1 ETPRO signatures available at the full report