| File name: | 2.exe |
| Full analysis: | https://app.any.run/tasks/23f9a9c9-82d4-4f4e-92ae-ee02ee8c3372 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 11:10:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 077DDACC6745D71835B04917F130FC41 |
| SHA1: | DC6A7608F0BA642330DCDF6BB18CCFA9252E1AFD |
| SHA256: | 5169980C90C6C9513D346ABE0B7DB868B5FFFCCEFD48C2AA5815B15FD9607BDB |
| SSDEEP: | 12288:8h11tmcSy/cDYw7J3j4DRUJZdLmiNpaJflZH:8hhmByozyGJPr+JNZH |
MALICIOUS
Loads dropped or rewritten executable
- 2.exe (PID: 2404)
Application was dropped or rewritten from another process
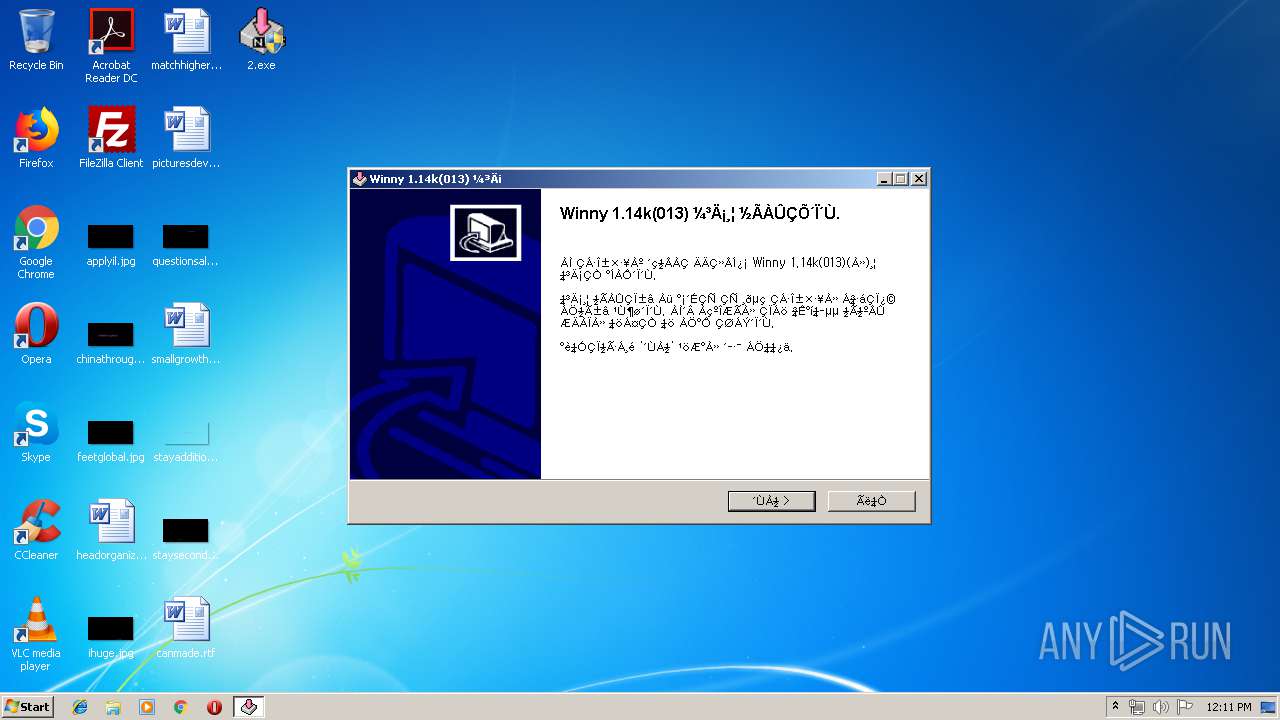
- Winny.exe (PID: 1500)
SUSPICIOUS
Creates files in the program directory
- 2.exe (PID: 2404)
Executable content was dropped or overwritten
- 2.exe (PID: 2404)
Creates a software uninstall entry
- 2.exe (PID: 2404)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (91.9) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.3) |
| .exe | | | Win64 Executable (generic) (3) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:11:17 15:35:37+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30ed |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 17-Nov-2007 14:35:37 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 17-Nov-2007 14:35:37 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005B22 | 0x00005C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.46966 |
.rdata | 0x00007000 | 0x0000129C | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.04904 |
.data | 0x00009000 | 0x00025CB8 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.12345 |
.ndata | 0x0002F000 | 0x00009000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00038000 | 0x00001ED8 | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.49744 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.10609 | 533 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 1.55959 | 1736 | UNKNOWN | English - United States | RT_ICON |
3 | 1.13859 | 1384 | UNKNOWN | English - United States | RT_ICON |
102 | 2.62197 | 160 | UNKNOWN | English - United States | RT_DIALOG |
103 | 2.59109 | 48 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.68176 | 494 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.86295 | 228 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.92694 | 218 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
39
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1500 | "C:\Winny\Winny.exe" | C:\Winny\Winny.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Winny アプリケーション Exit code: 0 Version: 1, 1, 4, 0 Modules
| |||||||||||||||
| 1968 | "C:\Users\admin\Desktop\2.exe" | C:\Users\admin\Desktop\2.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2140 | "C:\Windows\system32\NOTEPAD.EXE" C:\Winny\ReadME(KOR).txt | C:\Windows\system32\NOTEPAD.EXE | — | 2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2404 | "C:\Users\admin\Desktop\2.exe" | C:\Users\admin\Desktop\2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
196
Read events
185
Write events
11
Delete events
0
Modification events
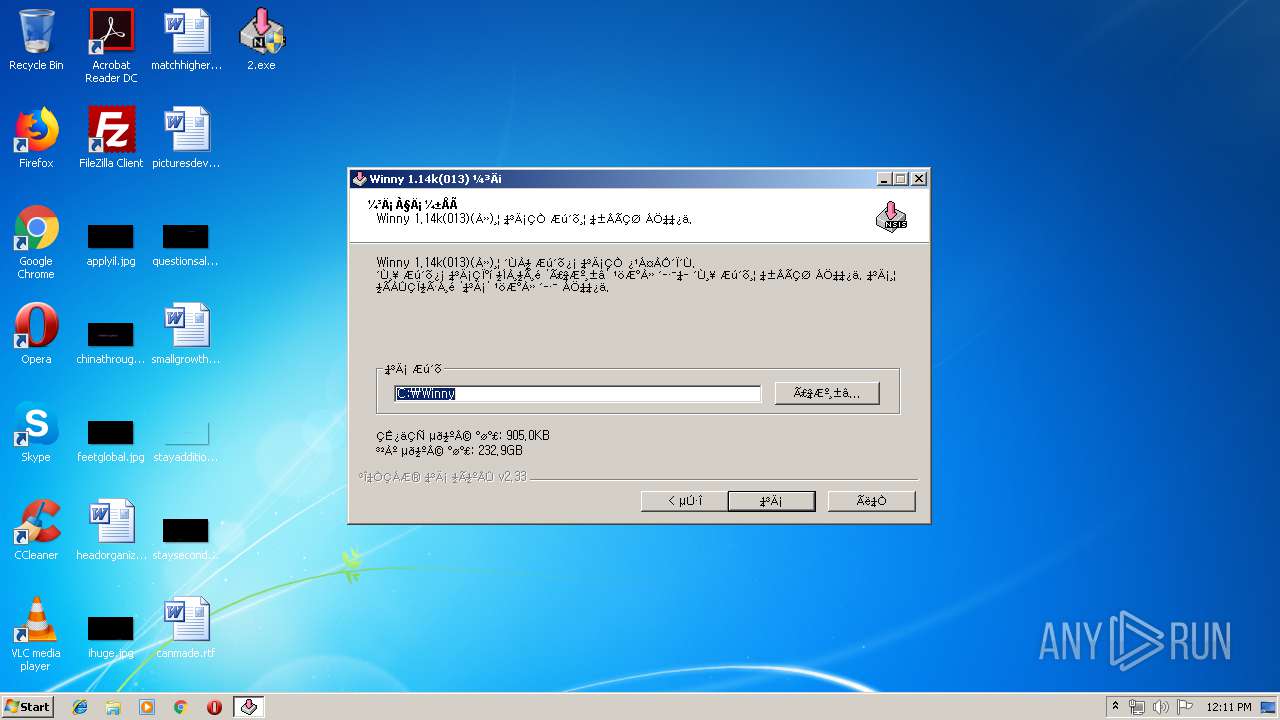
| (PID) Process: | (2404) 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\Winny.exe |
| Operation: | write | Name: | |
Value: C:\Winny\Winny.exe | |||
| (PID) Process: | (2404) 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Winny |
| Operation: | write | Name: | DisplayName |
Value: Winny 1.14k(013) | |||
| (PID) Process: | (2404) 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Winny |
| Operation: | write | Name: | UninstallString |
Value: C:\Winny\uninst.exe | |||
| (PID) Process: | (2404) 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Winny |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Winny\Winny.exe | |||
| (PID) Process: | (2404) 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Winny |
| Operation: | write | Name: | DisplayVersion |
Value: 1.14k(013) | |||
| (PID) Process: | (2404) 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Winny |
| Operation: | write | Name: | URLInfoAbout |
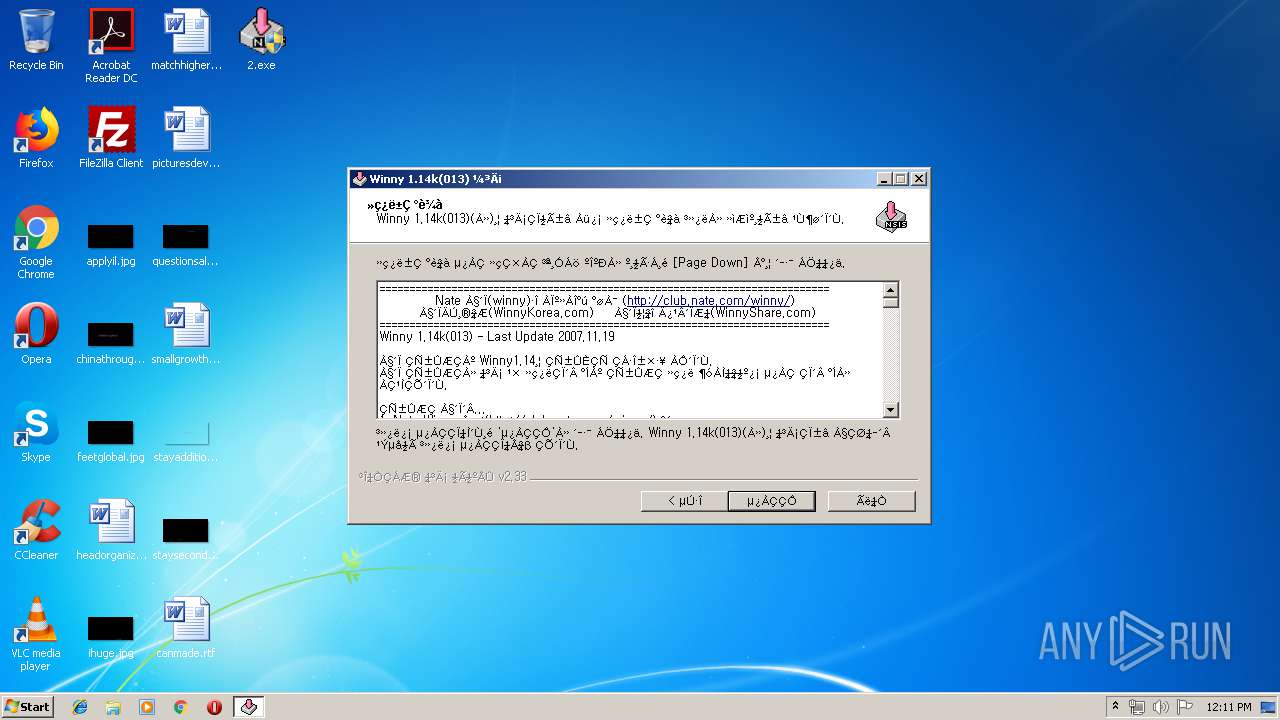
Value: http://winnykorea.com/ | |||
| (PID) Process: | (2404) 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Winny |
| Operation: | write | Name: | Publisher |
Value: À§´ÏÄÚ¸®¾Æ(WinnyKorea.com) | |||
| (PID) Process: | (2140) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 132 | |||
| (PID) Process: | (2140) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 132 | |||
| (PID) Process: | (2140) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
Executable files
5
Suspicious files
0
Text files
119
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2404 | 2.exe | C:\Users\admin\AppData\Local\Temp\nso6861.tmp\ioSpecial.ini | text | |
MD5:— | SHA256:— | |||
| 2404 | 2.exe | C:\Winny\Ignore.txt | text | |
MD5:— | SHA256:— | |||
| 2404 | 2.exe | C:\Winny\BoardList.txt | text | |
MD5:— | SHA256:— | |||
| 2404 | 2.exe | C:\Winny\natewinny.htm | html | |
MD5:— | SHA256:— | |||
| 2404 | 2.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Winny\Noderef.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2404 | 2.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Winny\Nate Winny.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2404 | 2.exe | C:\Winny\Noderef.txt | text | |
MD5:— | SHA256:— | |||
| 2404 | 2.exe | C:\Winny\ReadME(KOR).txt | text | |
MD5:— | SHA256:— | |||
| 2404 | 2.exe | C:\Winny\ReadMe.txt | text | |
MD5:— | SHA256:— | |||
| 2404 | 2.exe | C:\Winny\Readme.html | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1500 | Winny.exe | 61.198.112.179:10853 | — | TOKAI Communications Corporation | JP | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sasak.myhome.cx |
| unknown |