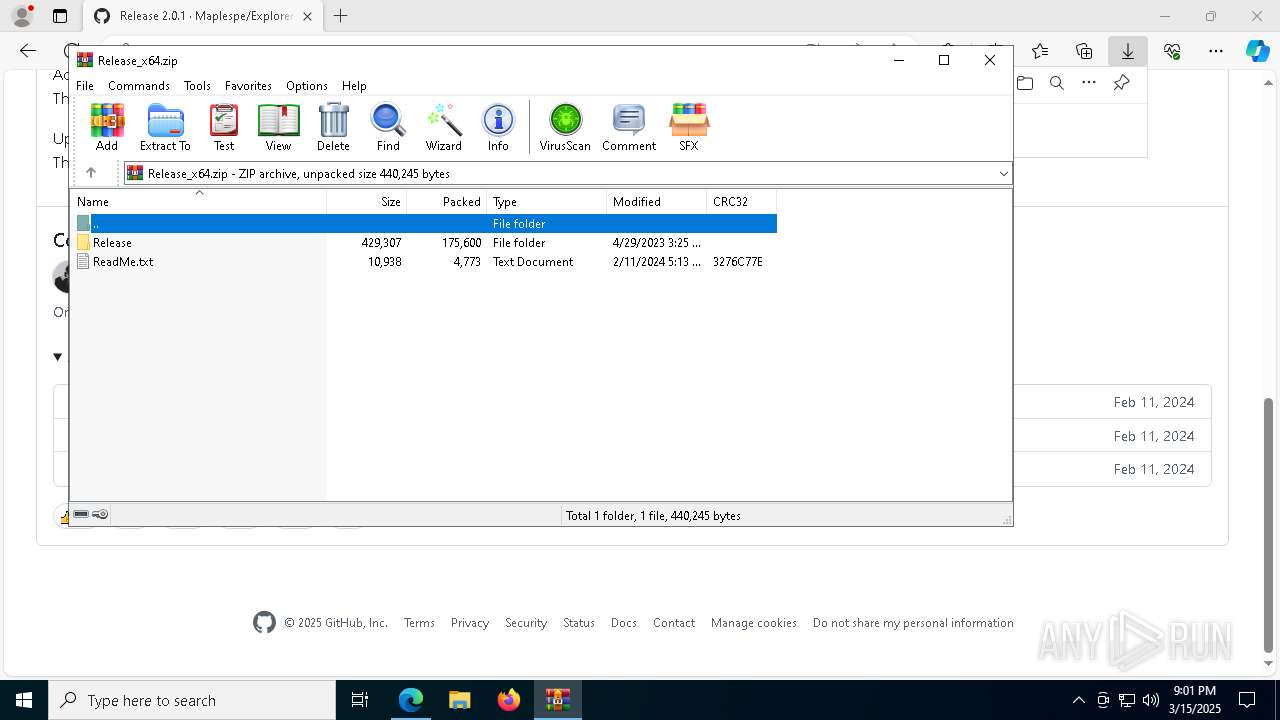
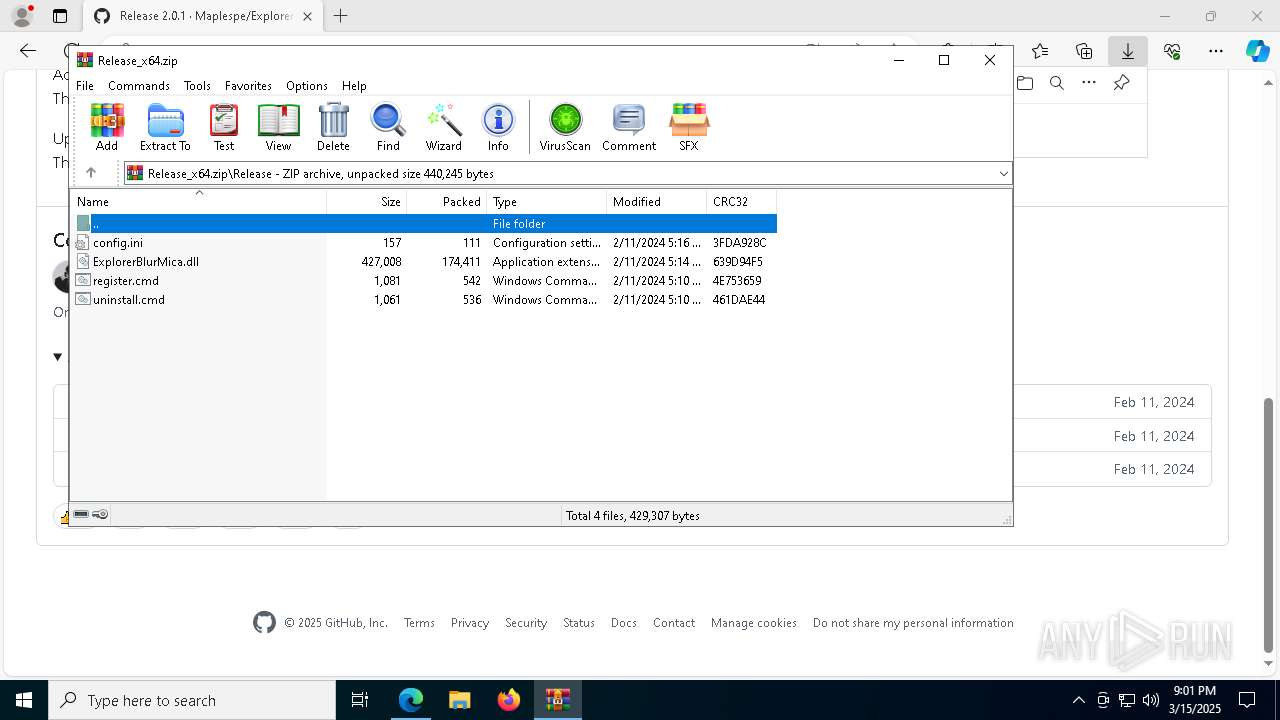
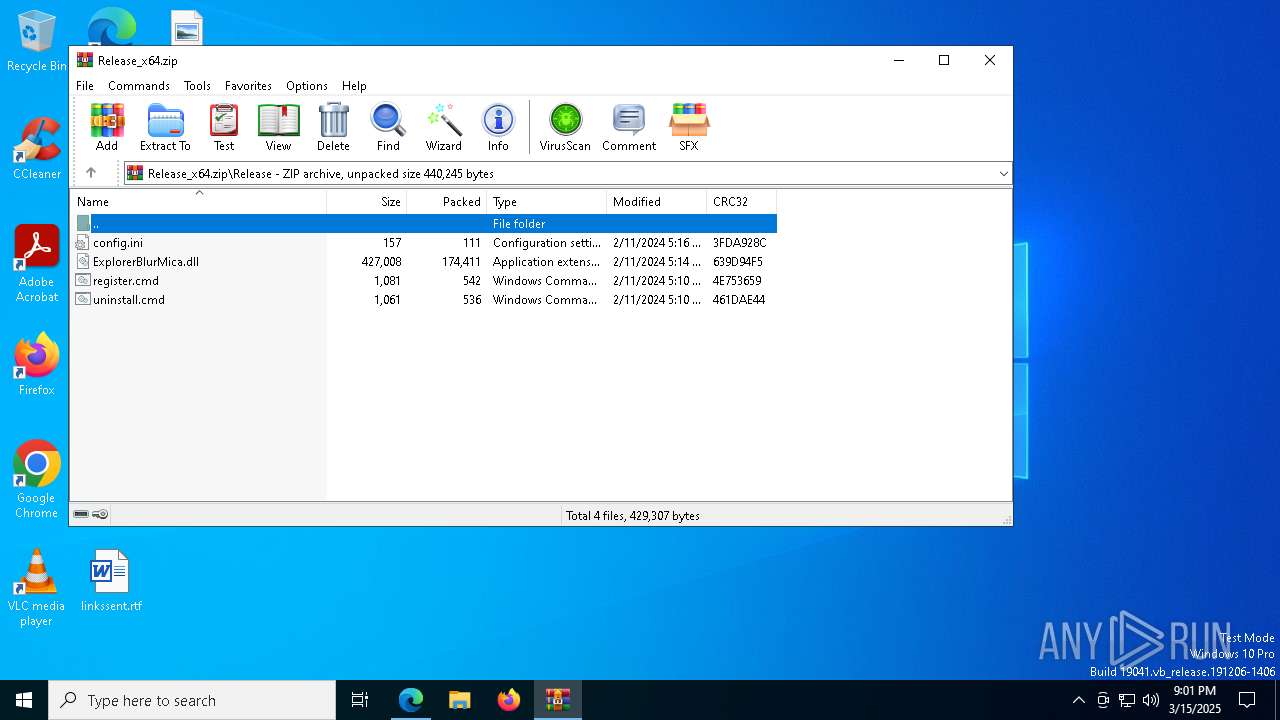
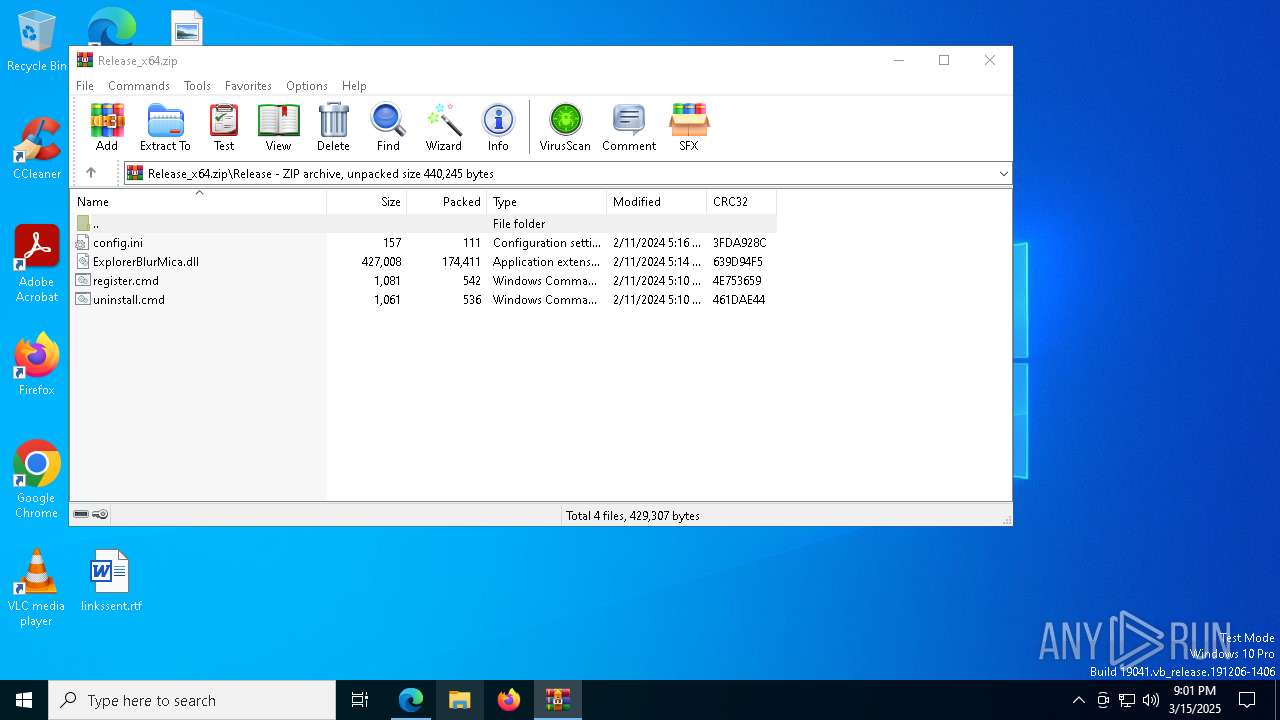
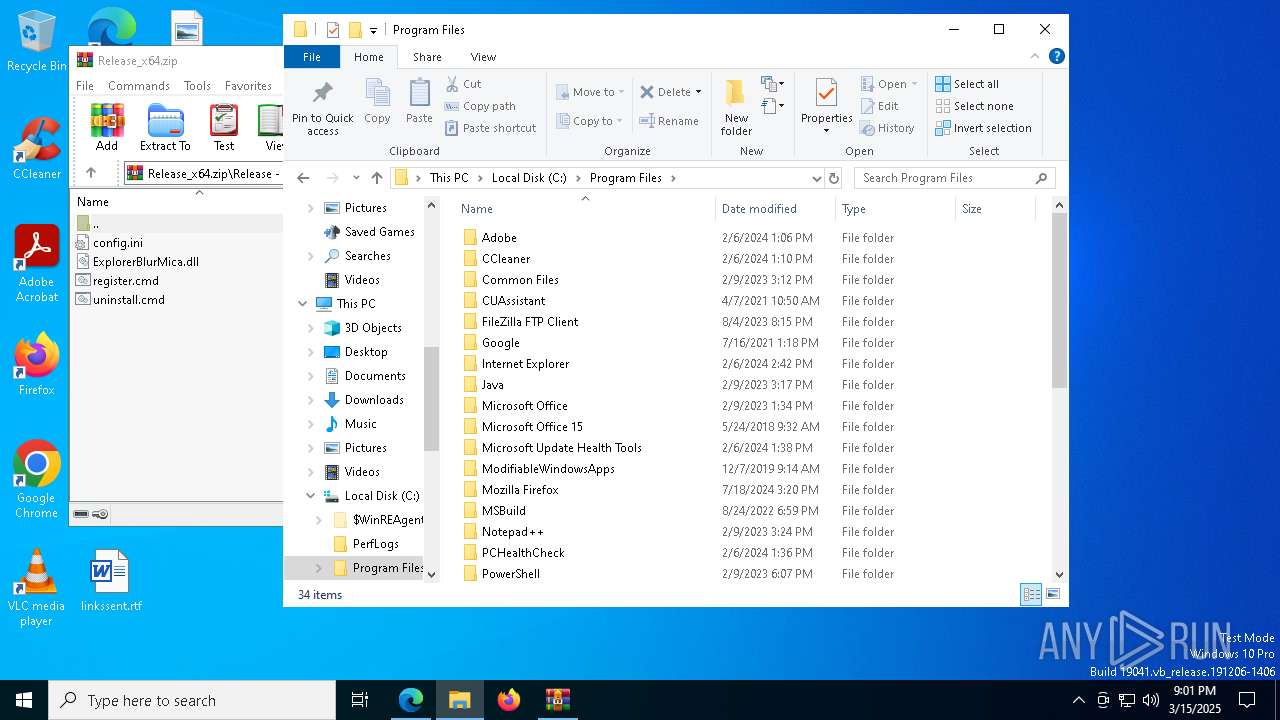
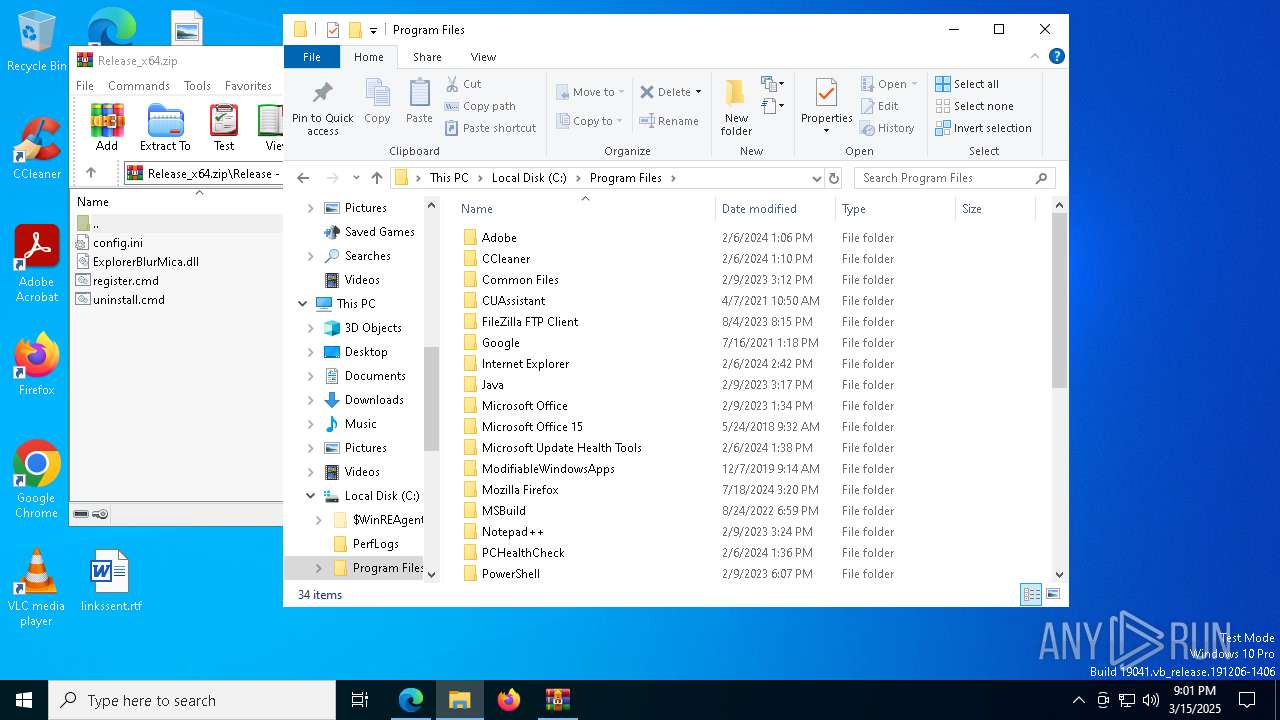
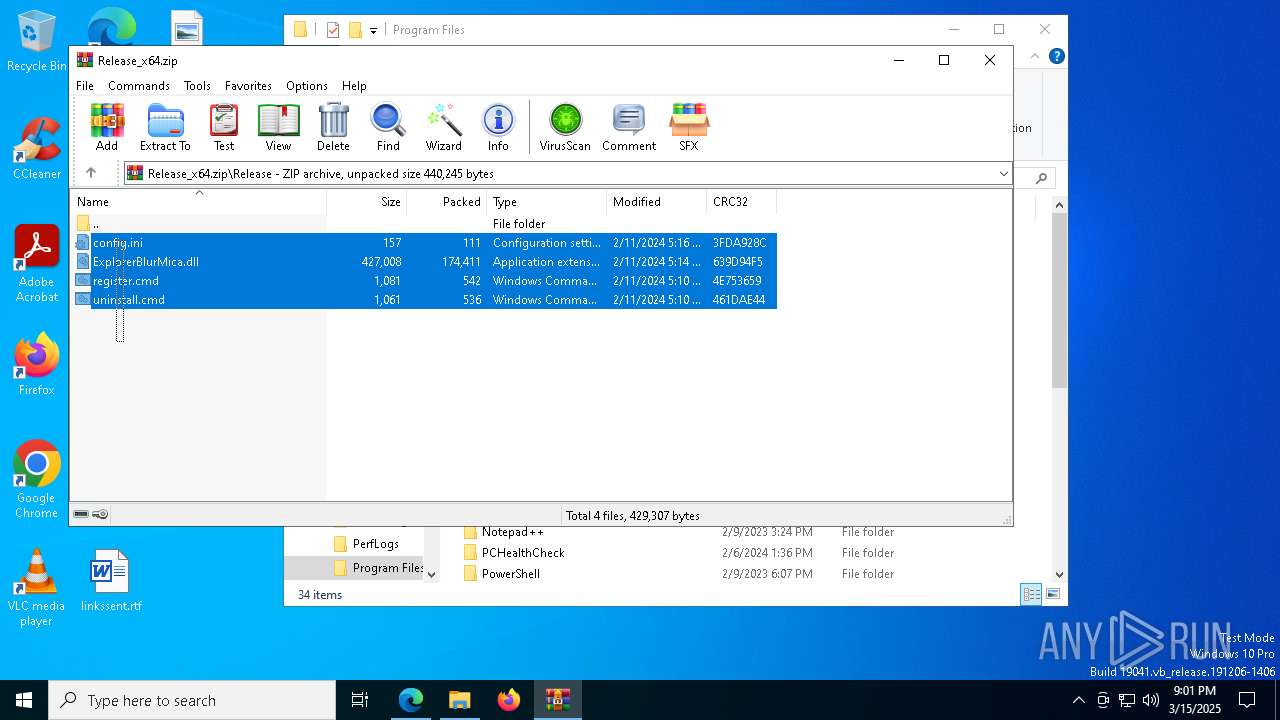
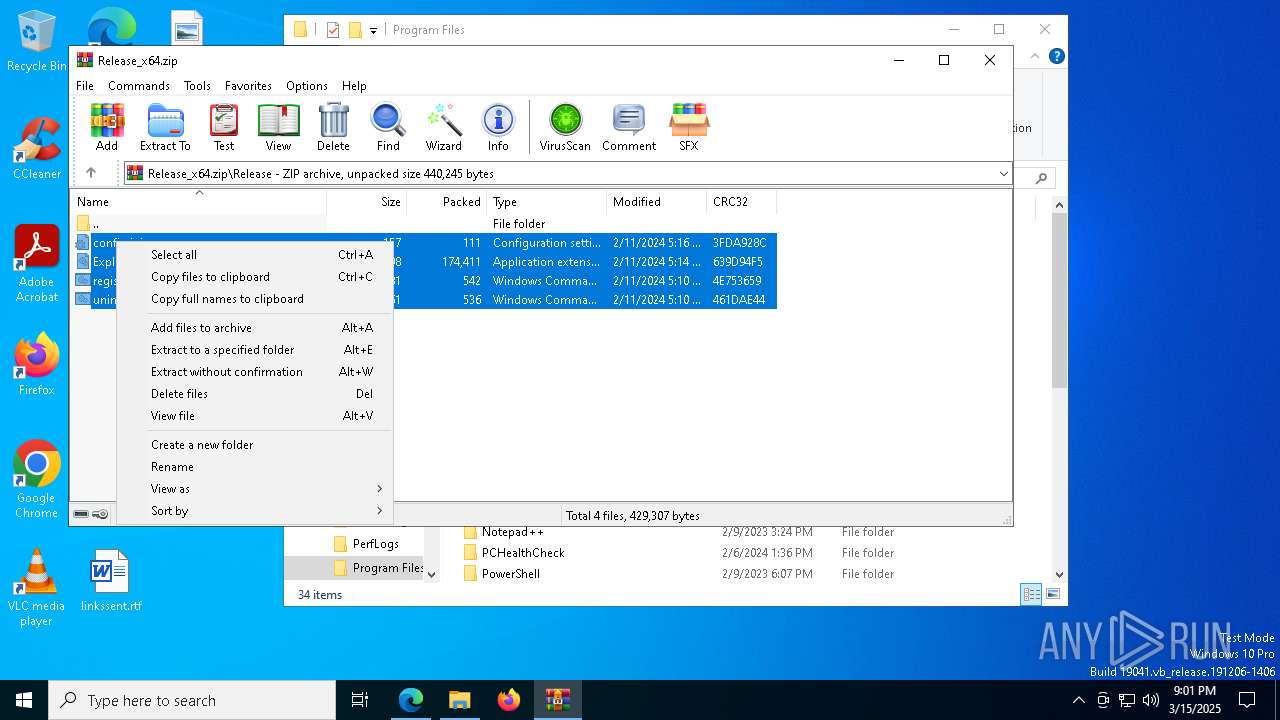
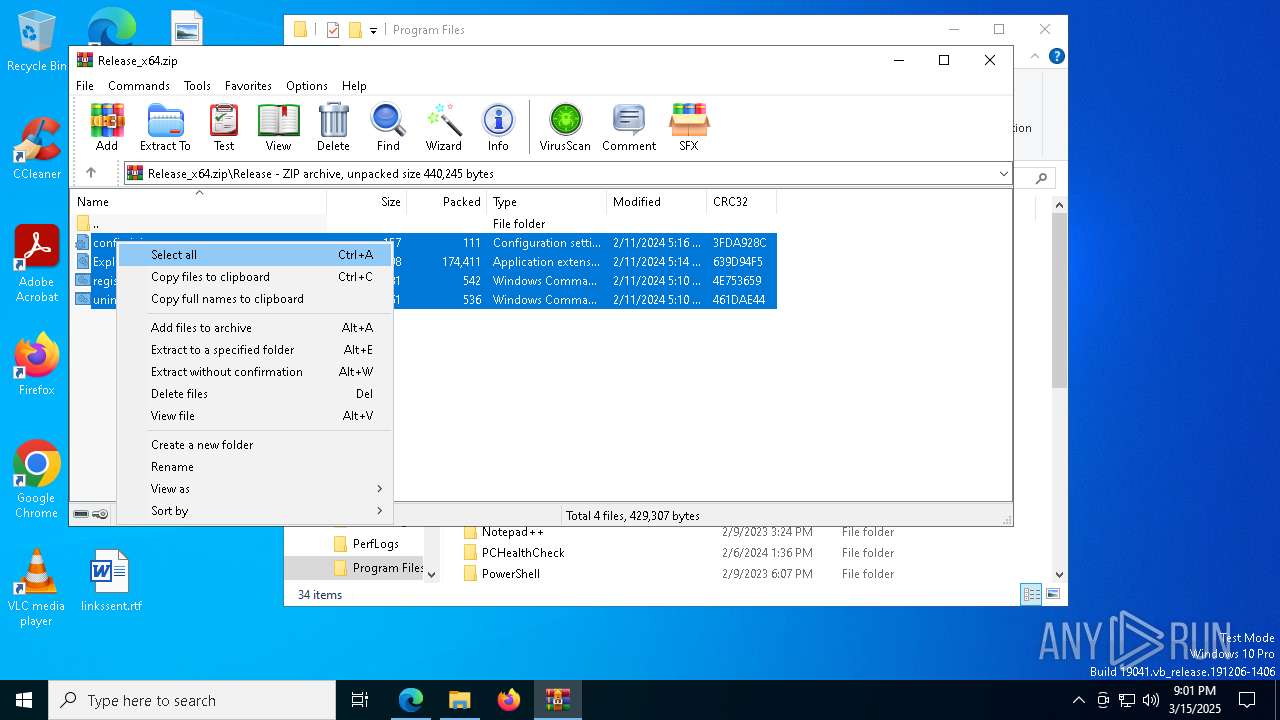
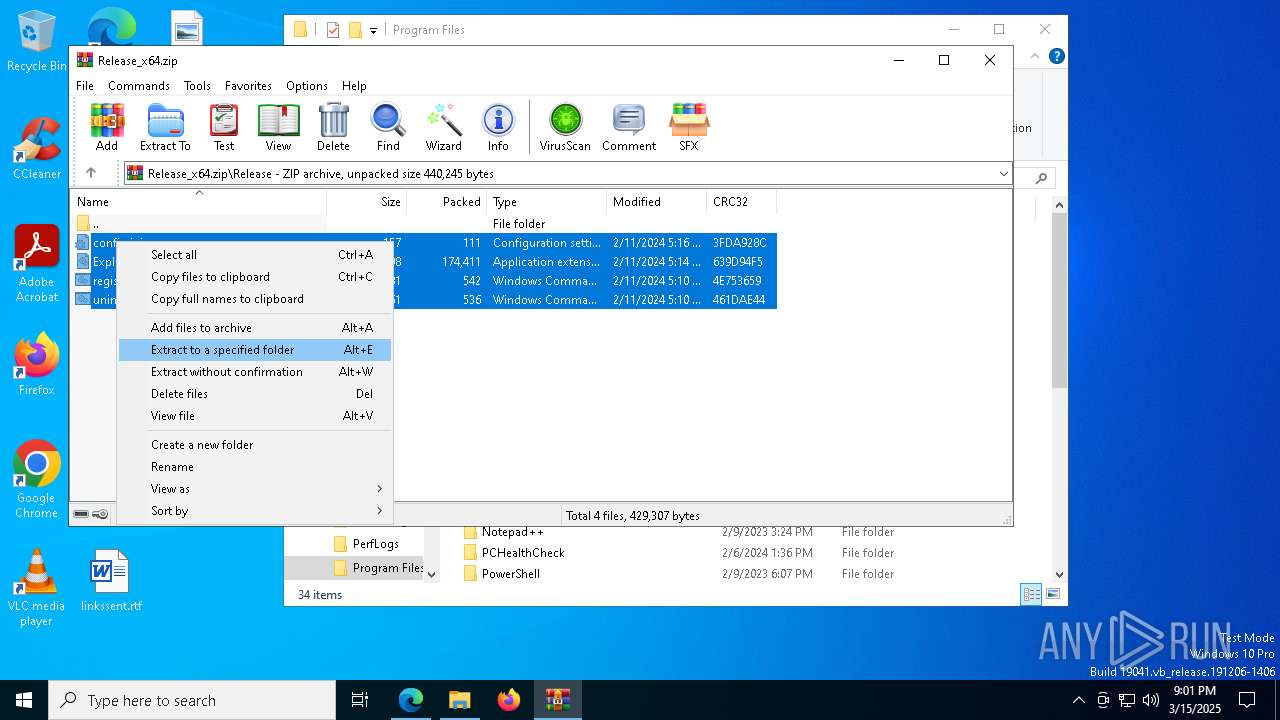
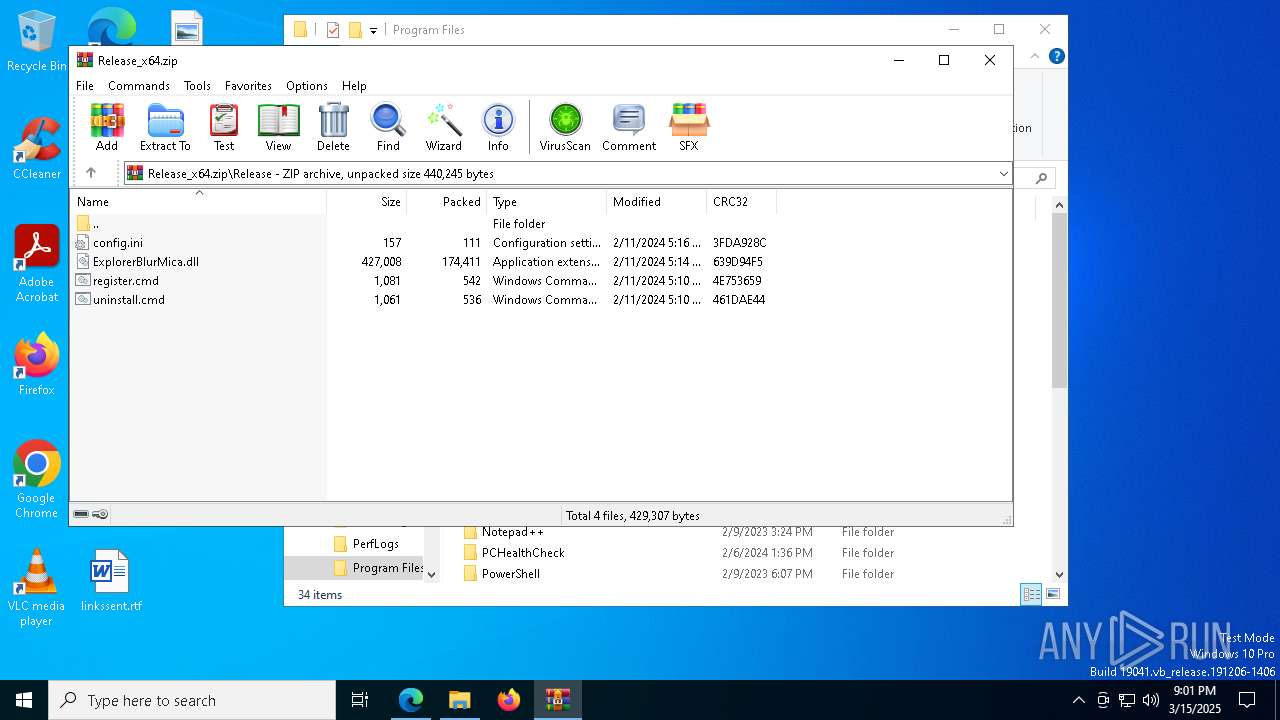
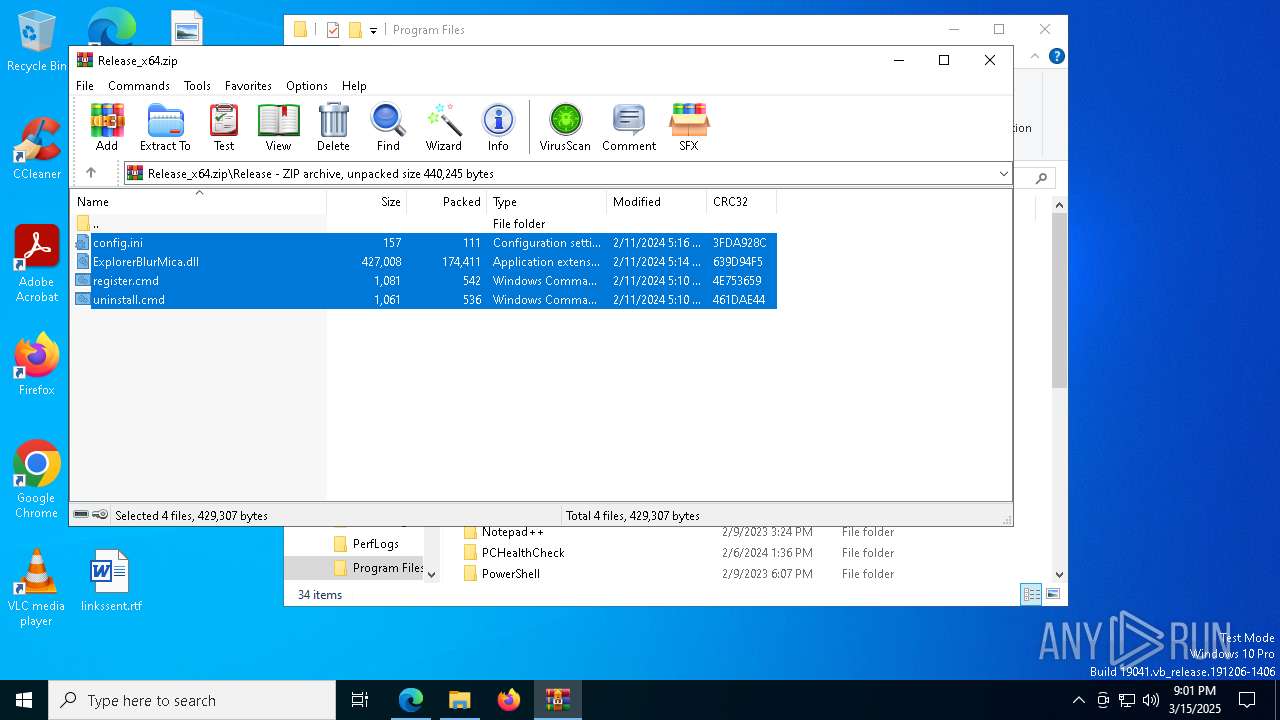
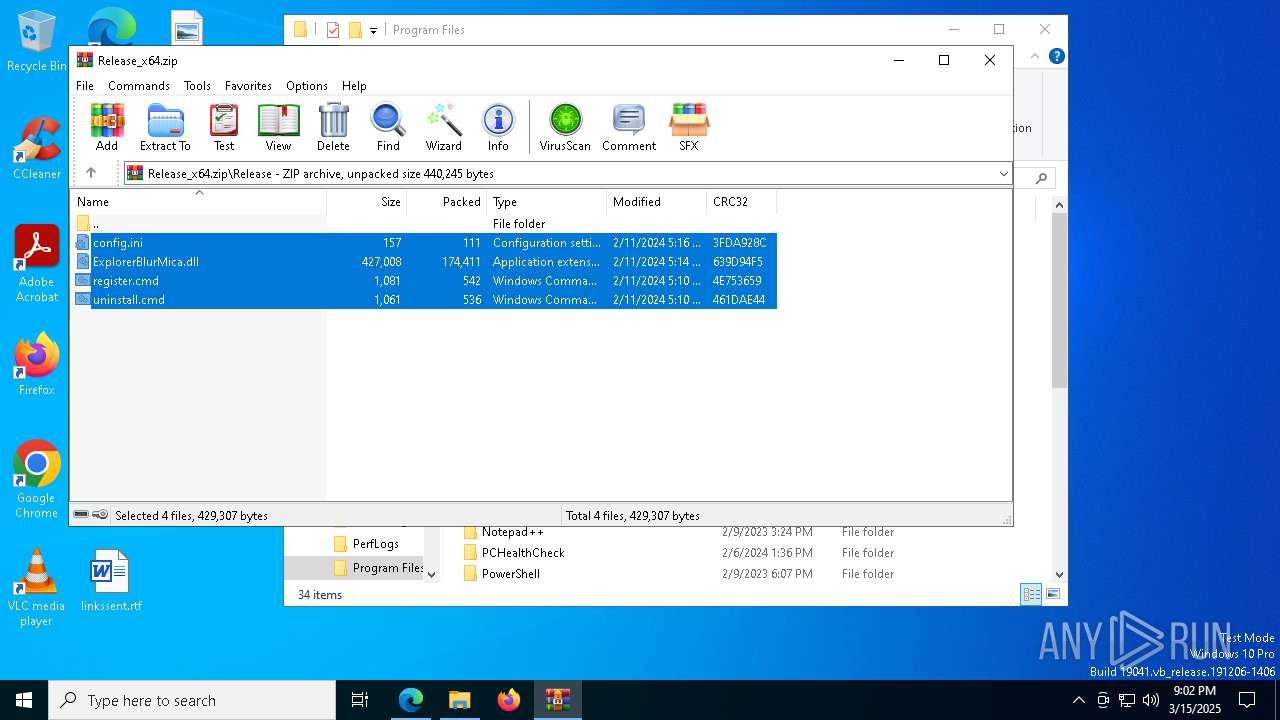
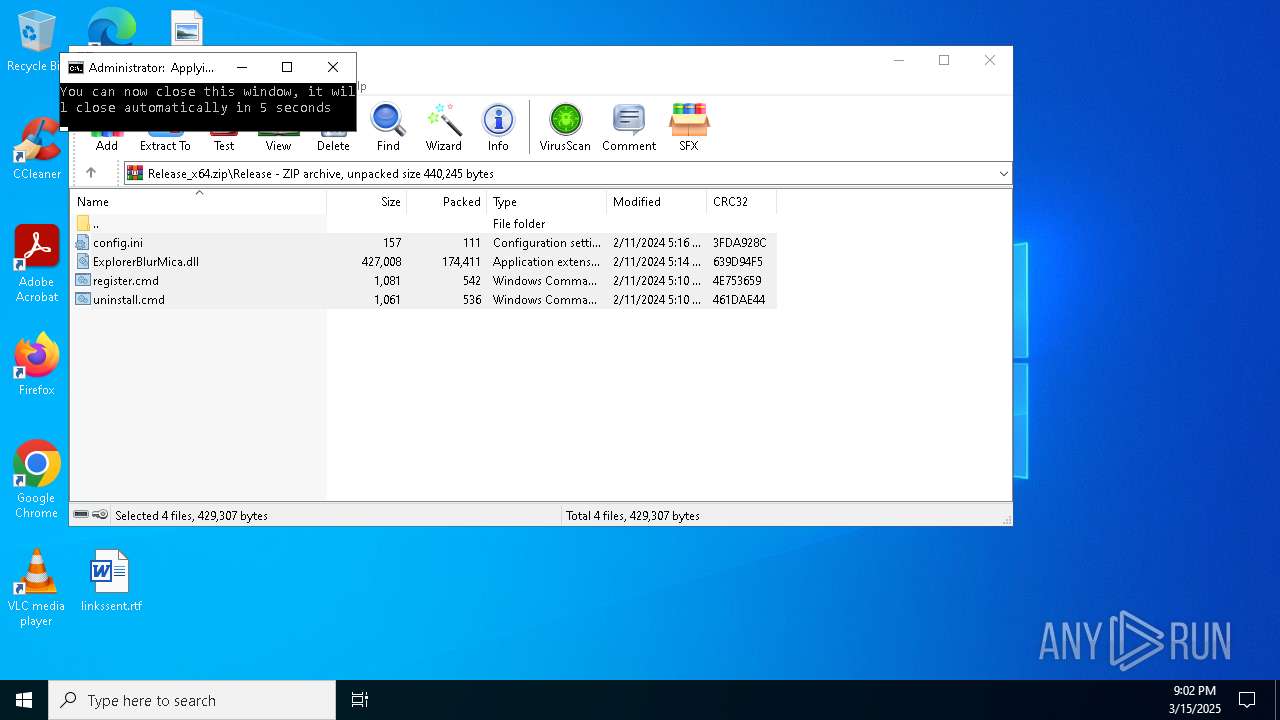
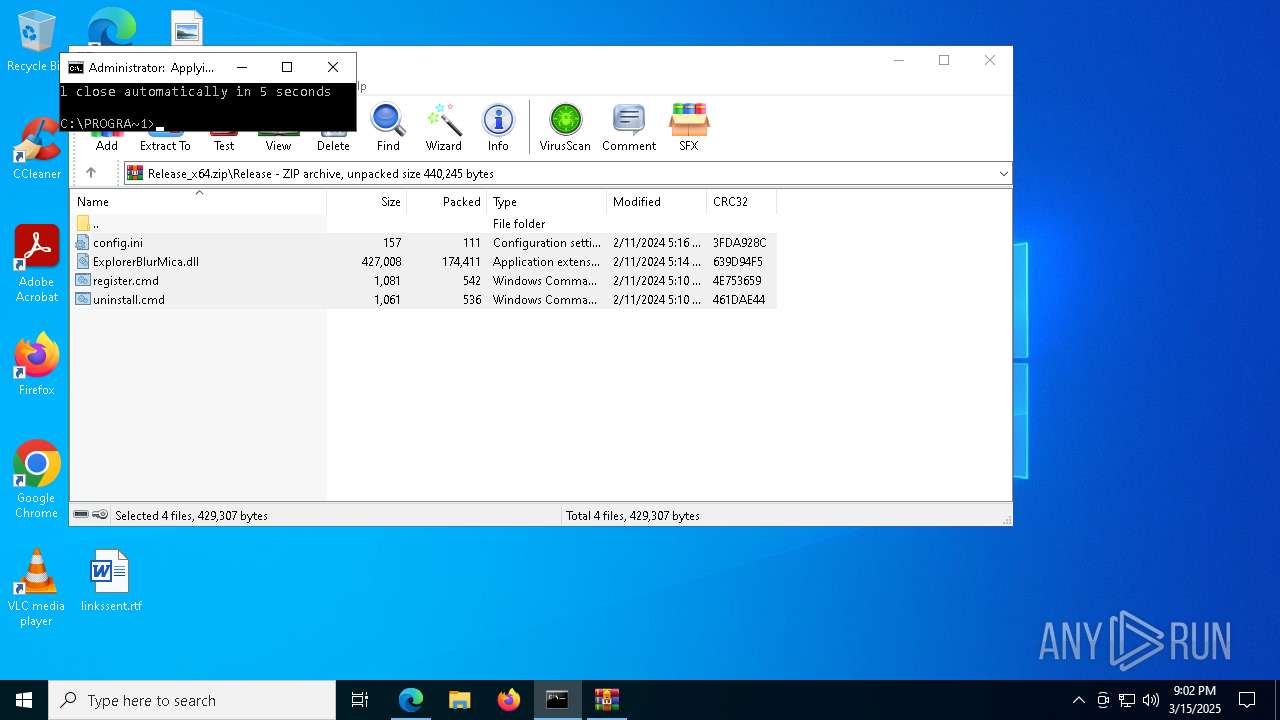
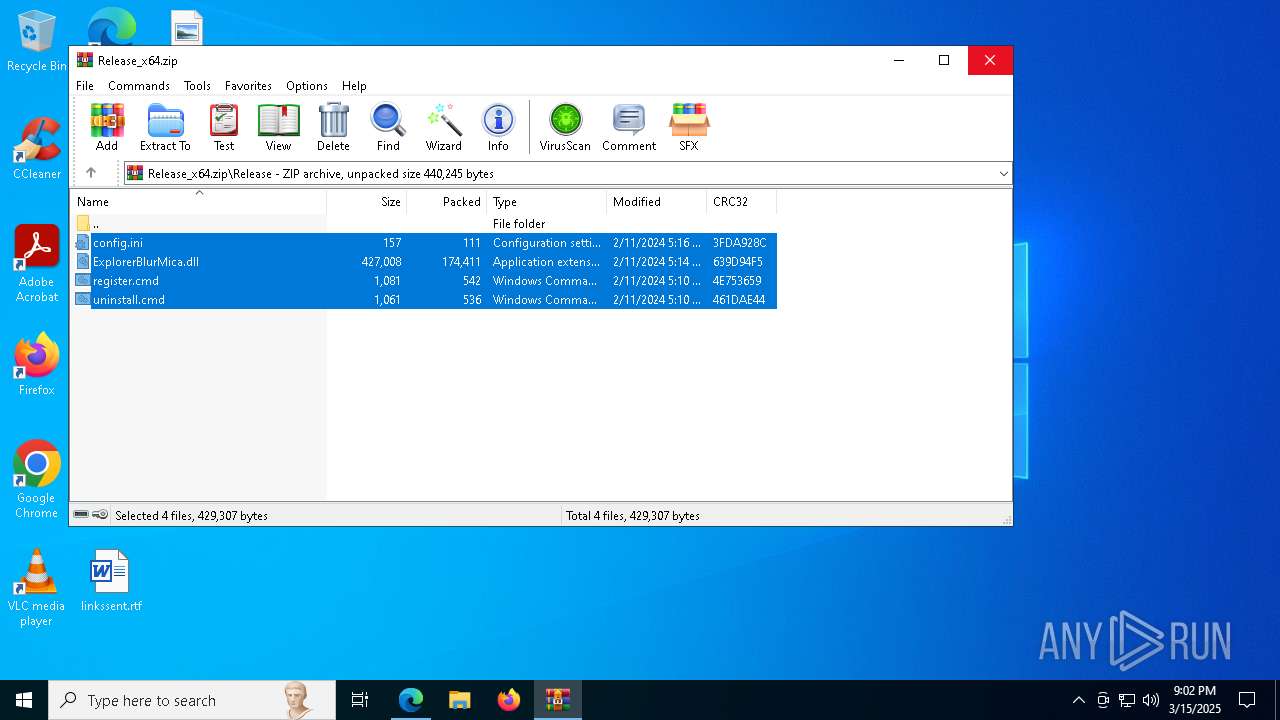
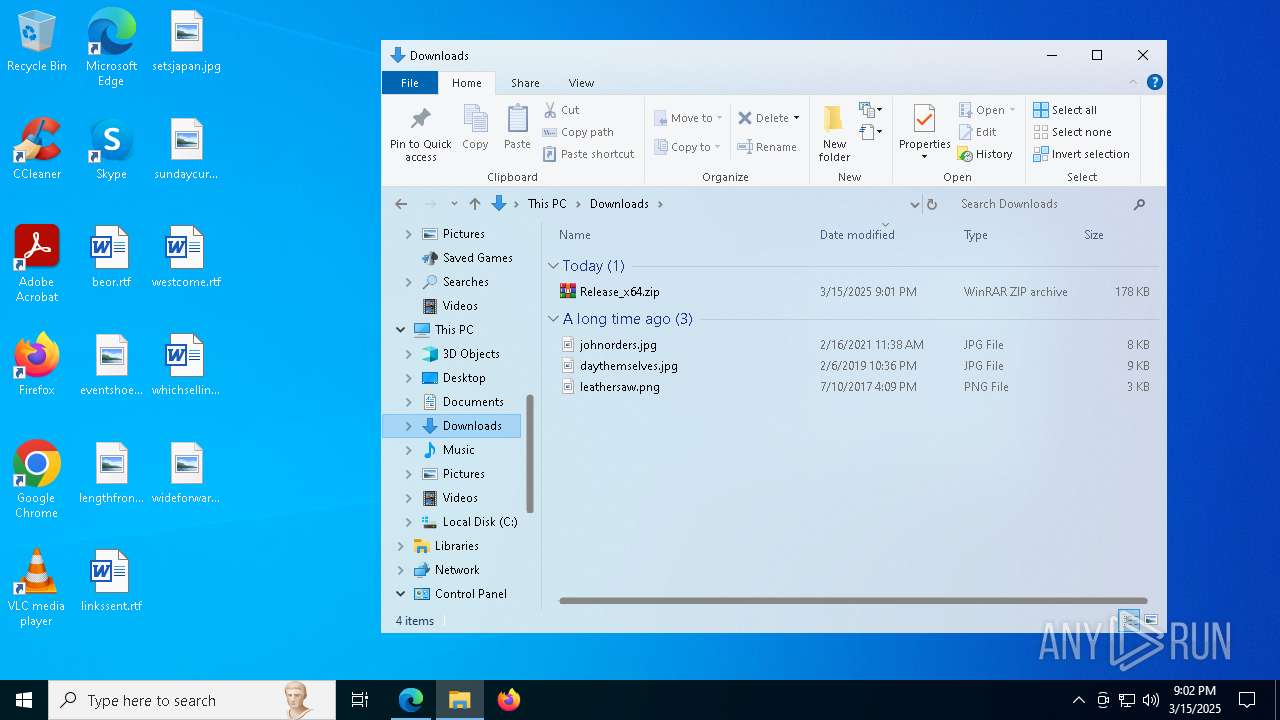
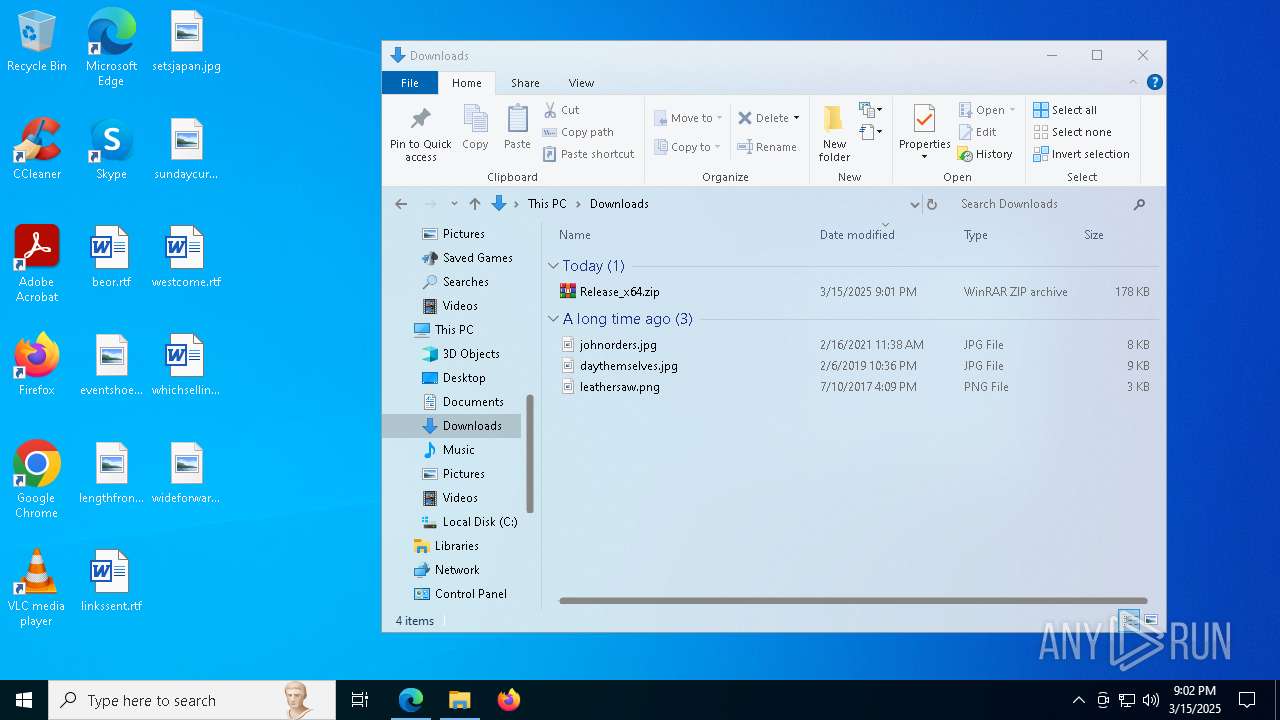
| download: | /Maplespe/ExplorerBlurMica/releases/tag/2.0.1 |
| Full analysis: | https://app.any.run/tasks/e159546e-72ee-4c48-b2ab-67fd2f282683 |
| Verdict: | Malicious activity |
| Analysis date: | March 15, 2025, 21:00:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Unicode text, UTF-8 text, with very long lines (1616) |
| MD5: | 3518C74B84568D7FC58C406D545CEAF9 |
| SHA1: | 26EB2A47DE846AA8EF0EE18BB45D0144573F387C |
| SHA256: | 51675BFEB1CCC38C287B5BFC3A77D1CB01E7A2847B716477392B71B26363866D |
| SSDEEP: | 3072:VkzqzFoSaQhHZnWsMEZbOhj6DjLZIUCp+rtnlexUZSvemMPRis8O0opOL/saqkPN:PvPsswopOL/saqkPV9VHmLqgIDSsqIzn |
MALICIOUS
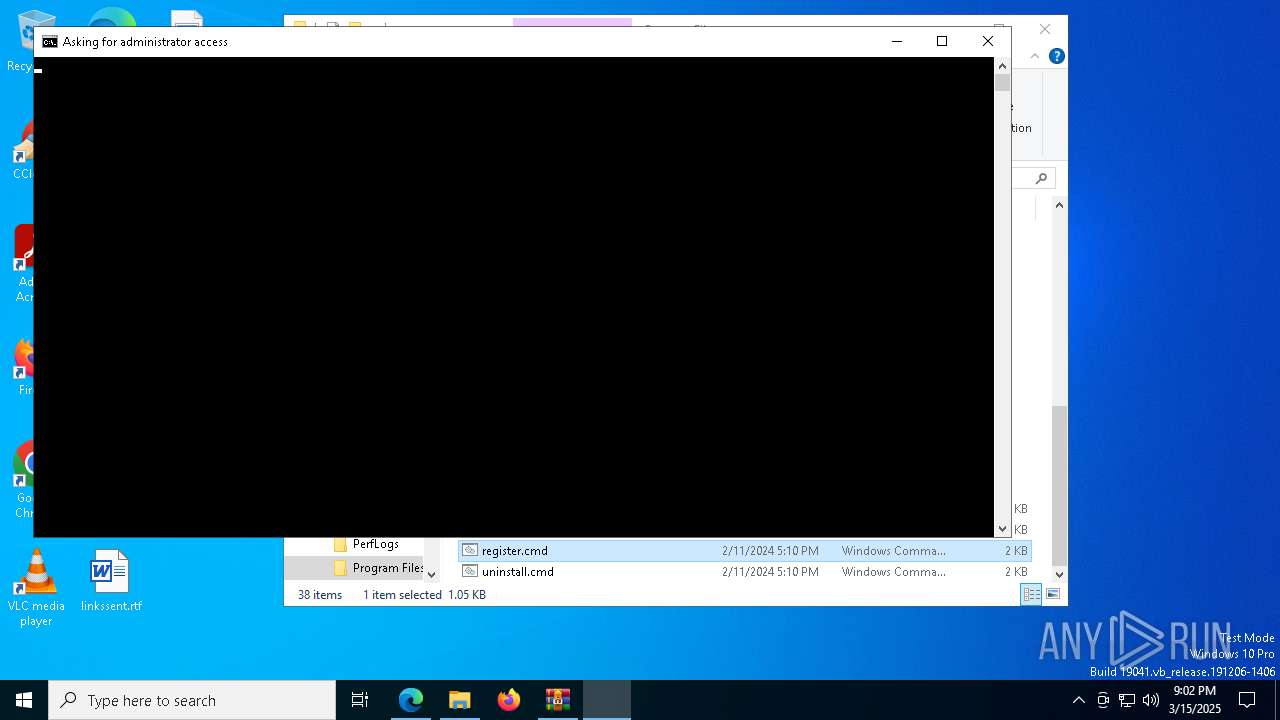
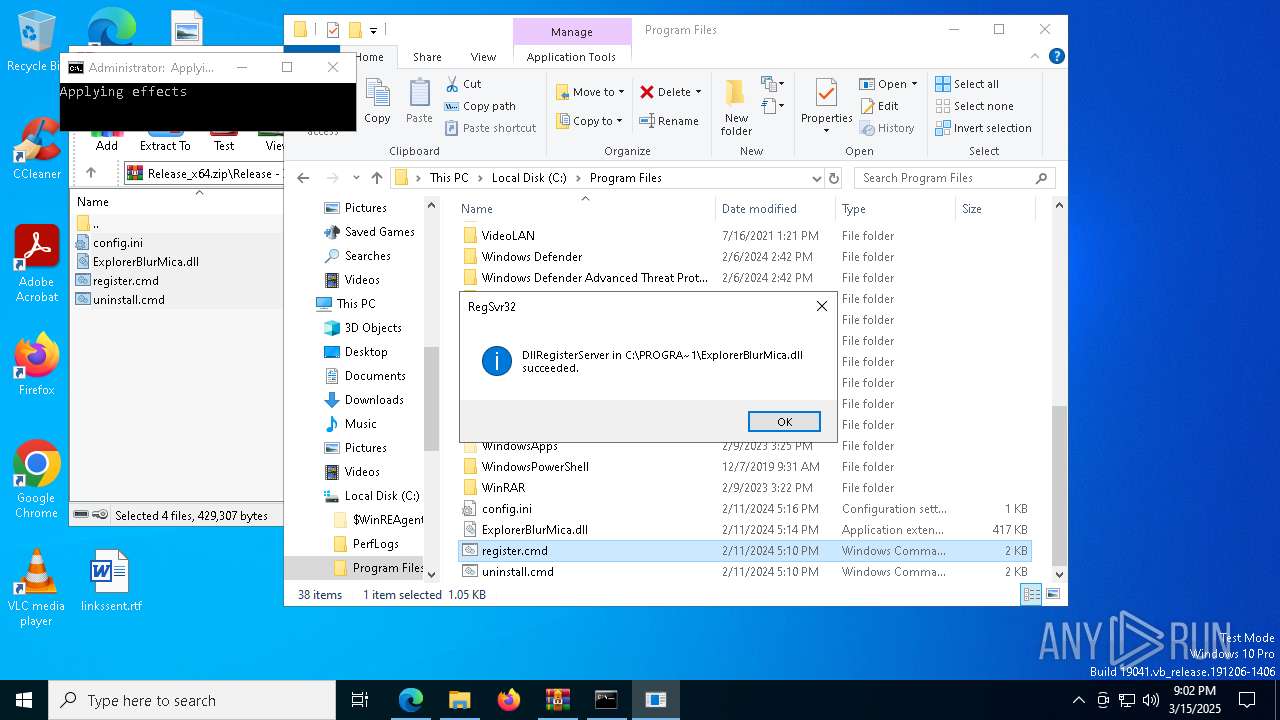
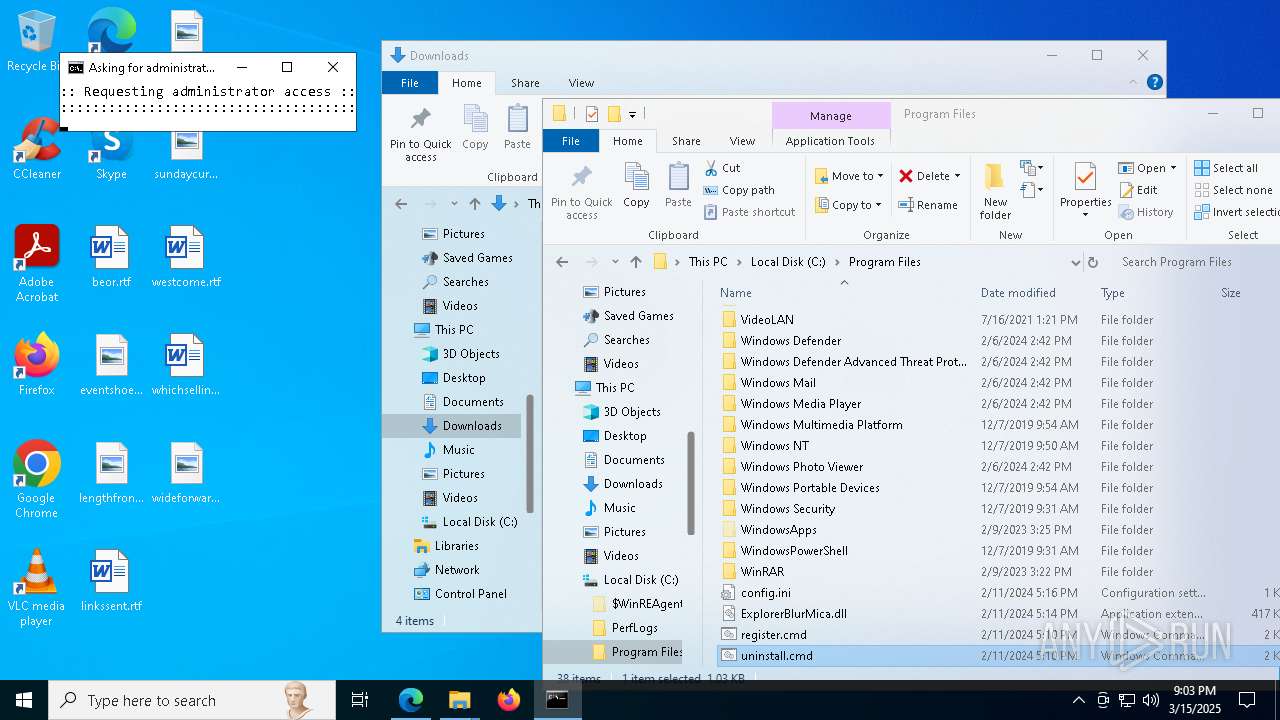
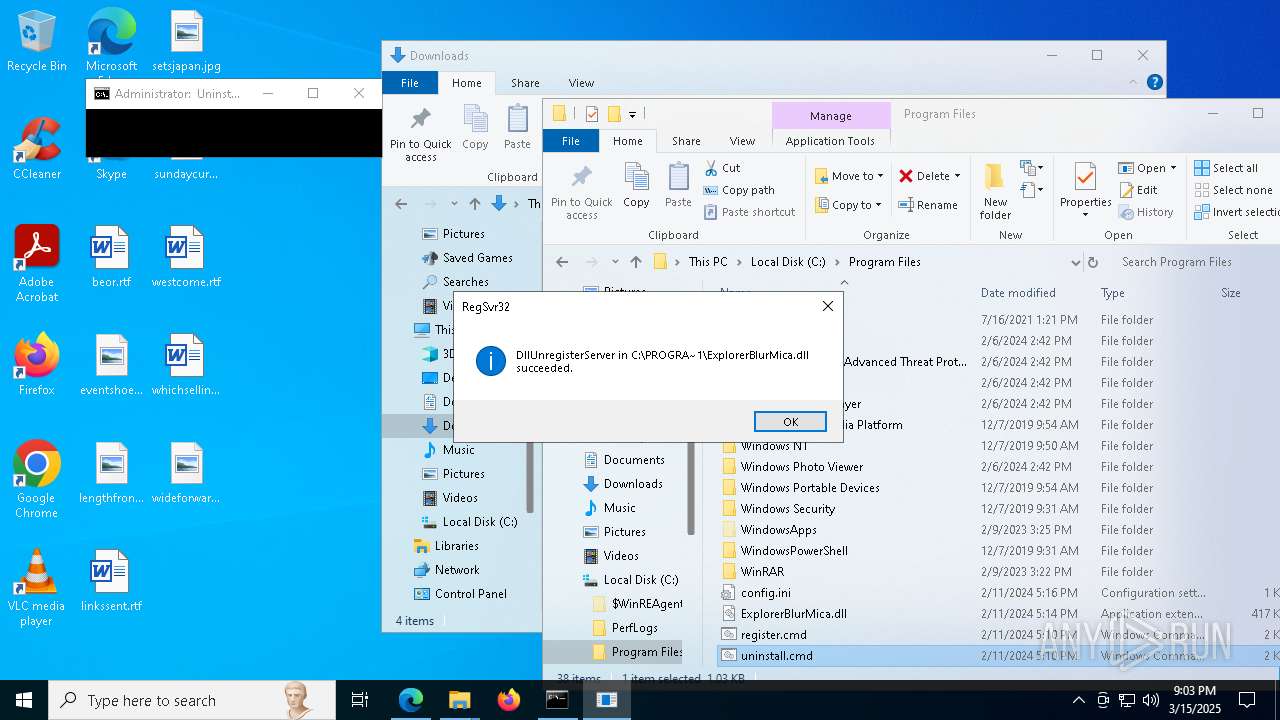
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 7588)
- cmd.exe (PID: 4696)
SUSPICIOUS
Executing commands from ".cmd" file
- wscript.exe (PID: 5968)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 5628)
- wscript.exe (PID: 3888)
- explorer.exe (PID: 7208)
Application launched itself
- cmd.exe (PID: 6712)
- cmd.exe (PID: 5628)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6712)
- wscript.exe (PID: 5968)
- explorer.exe (PID: 7208)
- wscript.exe (PID: 3888)
- cmd.exe (PID: 5628)
The process executes VB scripts
- cmd.exe (PID: 6712)
- cmd.exe (PID: 5628)
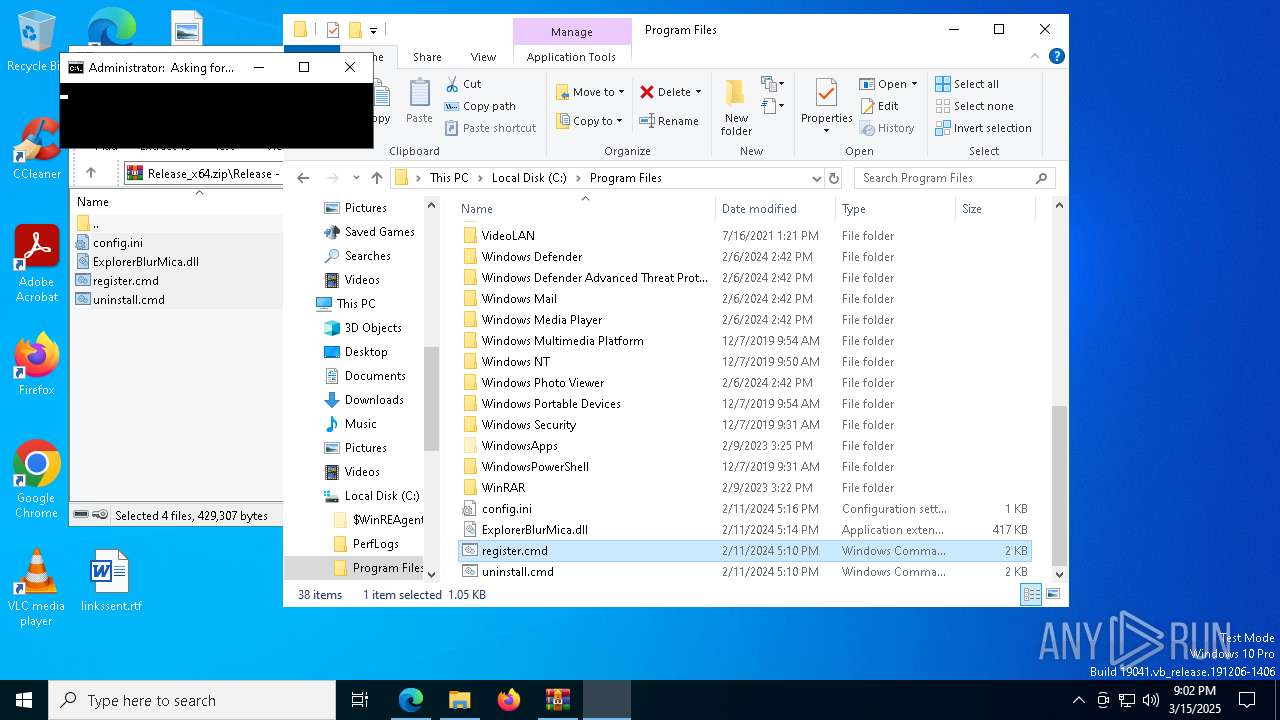
Executable content was dropped or overwritten
- dllhost.exe (PID: 1164)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7588)
- cmd.exe (PID: 4696)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7588)
- cmd.exe (PID: 4696)
The process executes via Task Scheduler
- explorer.exe (PID: 7208)
- explorer.exe (PID: 4112)
Reads security settings of Internet Explorer
- GameBar.exe (PID: 7296)
- StartMenuExperienceHost.exe (PID: 7908)
- StartMenuExperienceHost.exe (PID: 7592)
- ShellExperienceHost.exe (PID: 7336)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5968)
- wscript.exe (PID: 3888)
Reads the date of Windows installation
- SearchApp.exe (PID: 6808)
- StartMenuExperienceHost.exe (PID: 7908)
- StartMenuExperienceHost.exe (PID: 7592)
- SearchApp.exe (PID: 7800)
Creates file in the systems drive root
- explorer.exe (PID: 7208)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 5064)
INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4300)
- msedge.exe (PID: 7988)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 720)
- explorer.exe (PID: 7208)
- explorer.exe (PID: 4112)
Manual execution by a user
- msedge.exe (PID: 7988)
- cmd.exe (PID: 6712)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 720)
- SearchApp.exe (PID: 6808)
- explorer.exe (PID: 7208)
- slui.exe (PID: 7052)
- SearchApp.exe (PID: 7800)
- explorer.exe (PID: 4112)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 720)
- slui.exe (PID: 7424)
- SearchApp.exe (PID: 6808)
- slui.exe (PID: 7052)
- SearchApp.exe (PID: 7800)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 7920)
- dllhost.exe (PID: 1164)
- BackgroundTransferHost.exe (PID: 7528)
- BackgroundTransferHost.exe (PID: 720)
- BackgroundTransferHost.exe (PID: 2100)
- explorer.exe (PID: 7208)
- BackgroundTransferHost.exe (PID: 5728)
- explorer.exe (PID: 4112)
Checks supported languages
- identity_helper.exe (PID: 7604)
- mode.com (PID: 672)
- mode.com (PID: 1672)
- GameBar.exe (PID: 7296)
- TextInputHost.exe (PID: 6620)
- SearchApp.exe (PID: 6808)
- mode.com (PID: 1240)
- mode.com (PID: 6384)
- StartMenuExperienceHost.exe (PID: 7592)
- TextInputHost.exe (PID: 7000)
- SearchApp.exe (PID: 7800)
- ShellExperienceHost.exe (PID: 7336)
- StartMenuExperienceHost.exe (PID: 7908)
Reads Environment values
- identity_helper.exe (PID: 7604)
- SearchApp.exe (PID: 6808)
- SearchApp.exe (PID: 7800)
Starts MODE.COM to configure console settings
- mode.com (PID: 672)
- mode.com (PID: 1672)
- mode.com (PID: 6384)
- mode.com (PID: 1240)
Application launched itself
- msedge.exe (PID: 7988)
Reads the computer name
- GameBar.exe (PID: 7296)
- StartMenuExperienceHost.exe (PID: 7908)
- TextInputHost.exe (PID: 6620)
- identity_helper.exe (PID: 7604)
- SearchApp.exe (PID: 6808)
- TextInputHost.exe (PID: 7000)
- StartMenuExperienceHost.exe (PID: 7592)
- SearchApp.exe (PID: 7800)
- ShellExperienceHost.exe (PID: 7336)
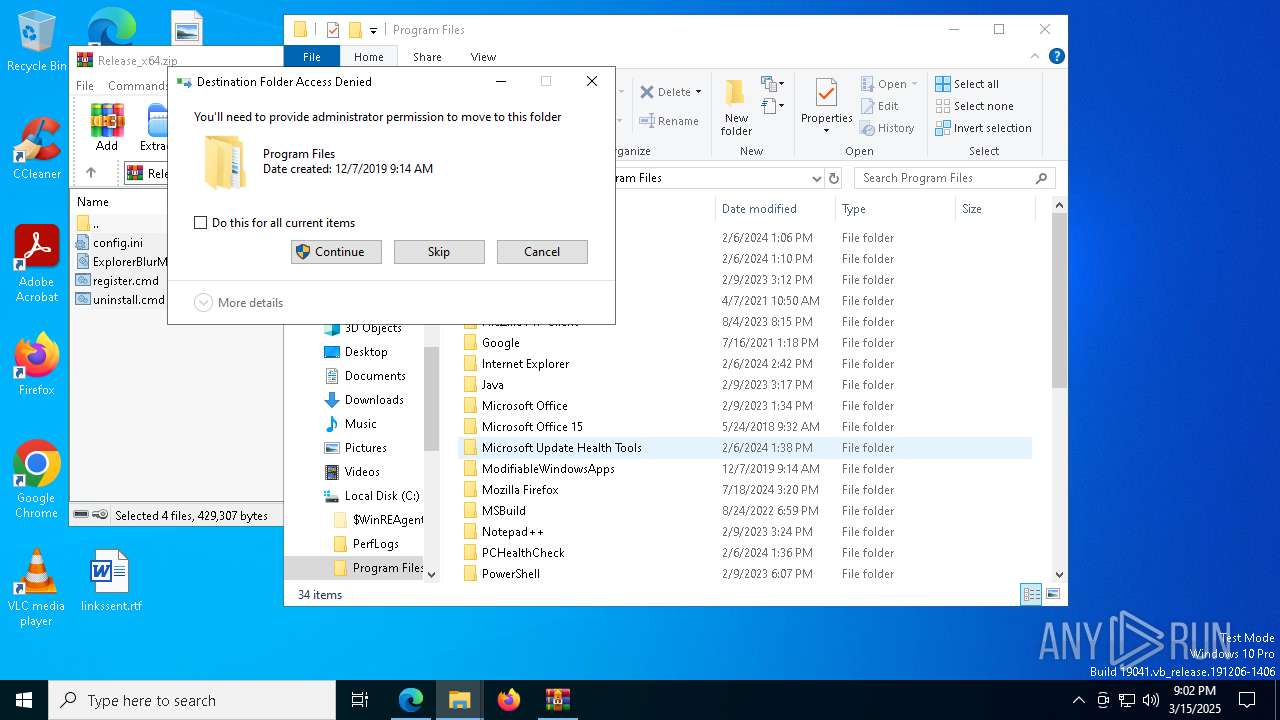
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7836)
- msedge.exe (PID: 660)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 7908)
- SearchApp.exe (PID: 6808)
- StartMenuExperienceHost.exe (PID: 7592)
- SearchApp.exe (PID: 7800)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 6808)
- SearchApp.exe (PID: 7800)
The sample compiled with english language support
- msedge.exe (PID: 660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| Title: | Release 2.0.1 · Maplespe/ExplorerBlurMica · GitHub |
|---|---|
| RoutePattern: | /:user_id/:repository/releases/tag/*name |
| RouteController: | releases |
| RouteAction: | show |
| CurrentCatalogServiceHash: | 6f13f31f798a93a6b08d3be0727120e9af35851fac7b9c620d6cf9a70068c136 |
| RequestId: | E186:158BFA:543659C:572963A:67D5EA76 |
| HtmlSafeNonce: | 8d8c9a92a6bf5e9aee308b1543e621cc50881a1cd269add7874fba2770d61682 |
| VisitorPayload: | eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFMTg2OjE1OEJGQTo1NDM2NTlDOjU3Mjk2M0E6NjdENUVBNzYiLCJ2aXNpdG9yX2lkIjoiMjE5Nzk2MDQ4NDgxNjU0NjQyMiIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9 |
| VisitorHmac: | 99e6c9180efe62e2f4a8afd9764f5e4ce5379c28fd72f4a4b989f397c8066864 |
| HovercardSubjectTag: | repository:529213465 |
| GithubKeyboardShortcuts: | repository,copilot |
| GoogleSiteVerification: | Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I |
| OctolyticsUrl: | https://collector.github.com/github/collect |
| AnalyticsLocation: | /<user-name>/<repo-name>/releases/show |
| UserLogin: | - |
| Viewport: | width=device-width |
| Description: | Add background Blur effect or Acrylic (Mica for win11) effect to explorer for win10 and win11 - Release 2.0.1 · Maplespe/ExplorerBlurMica |
| AppleItunesApp: | app-id=1477376905, app-argument=https://github.com/Maplespe/ExplorerBlurMica/releases/tag/2.0.1 |
| TwitterImage: | https://opengraph.githubassets.com/010c8488a566c785f0ab2c5299177df116998d10ae1f6e25b64768bf81ddb227/Maplespe/ExplorerBlurMica/releases/tag/2.0.1 |
| TwitterSite: | @github |
| TwitterCard: | summary_large_image |
| TwitterTitle: | Release 2.0.1 · Maplespe/ExplorerBlurMica |
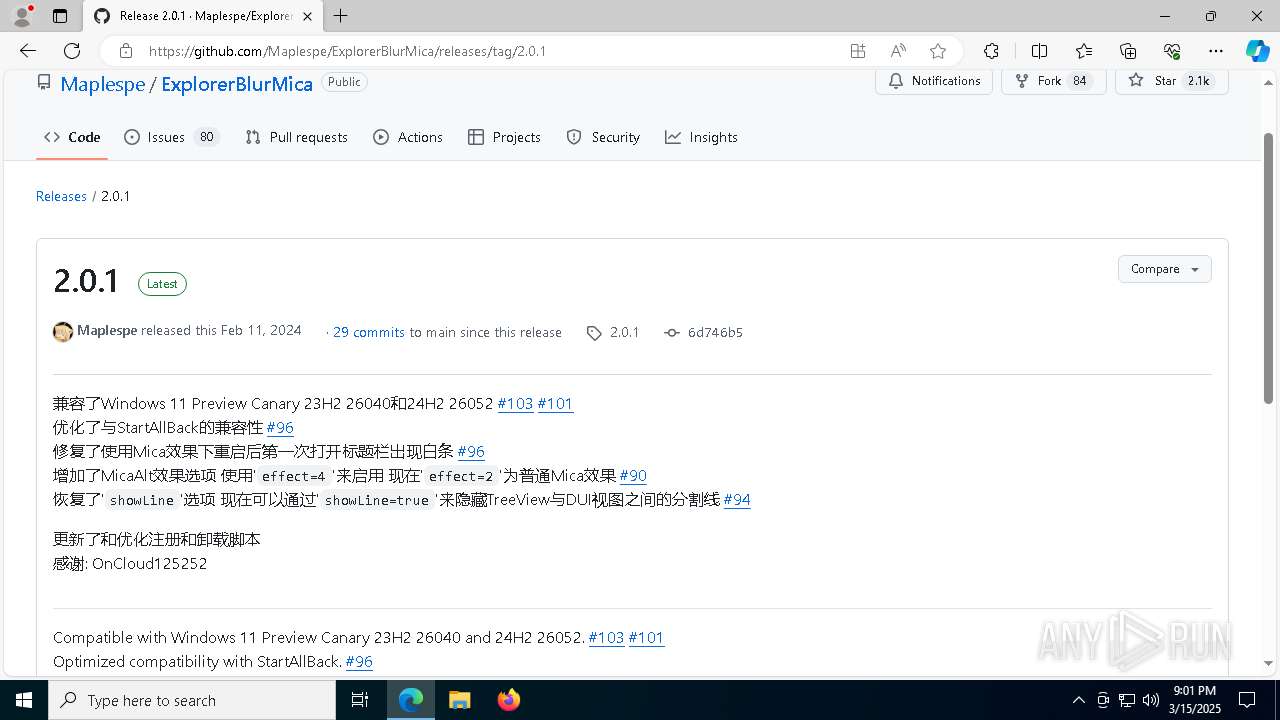
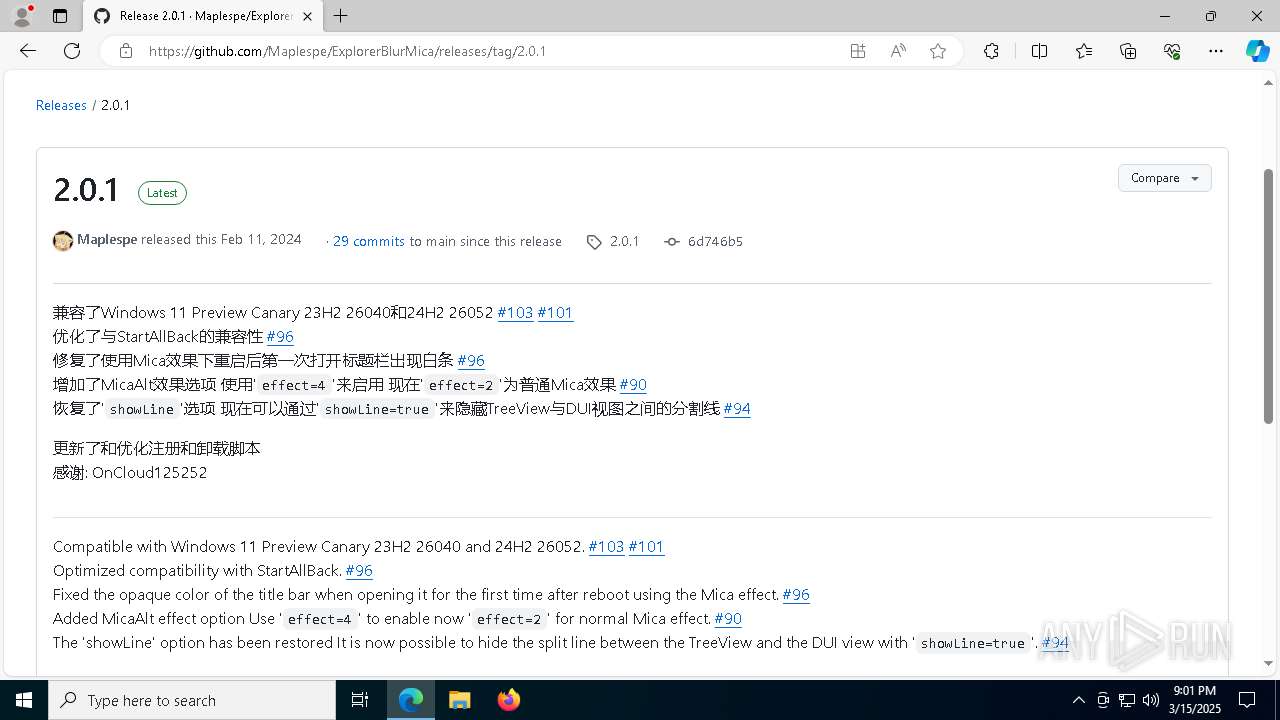
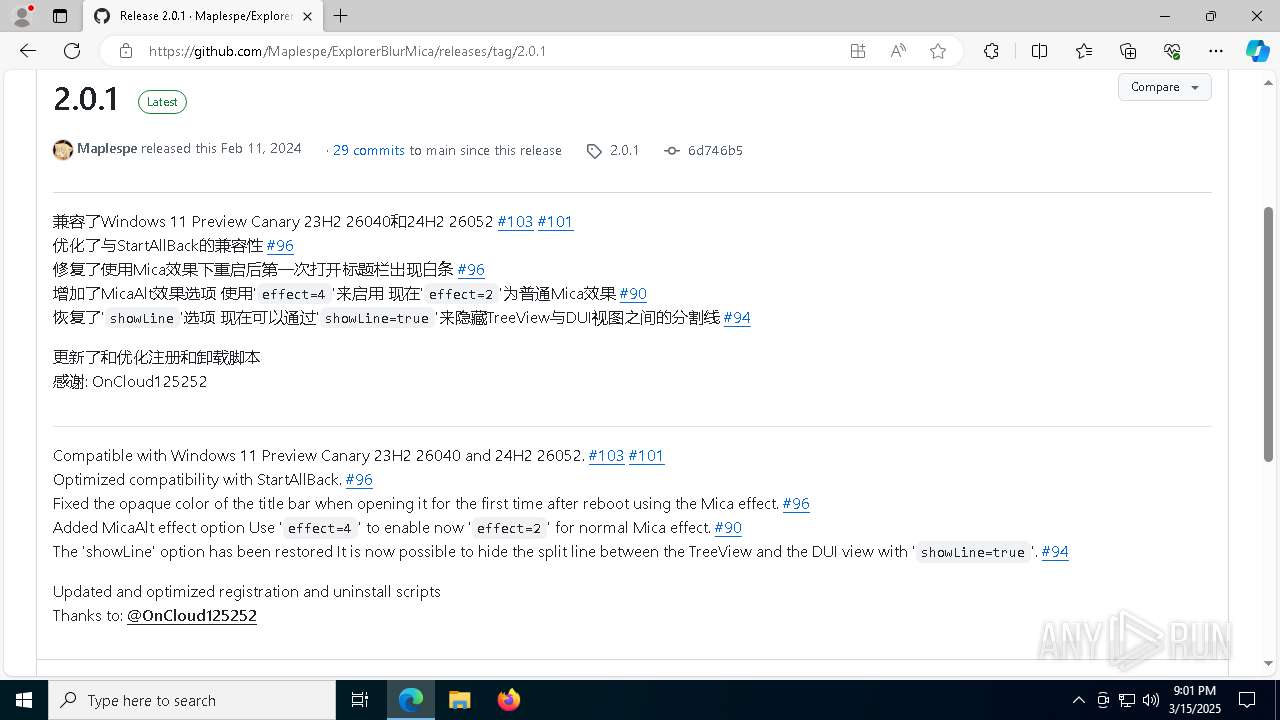
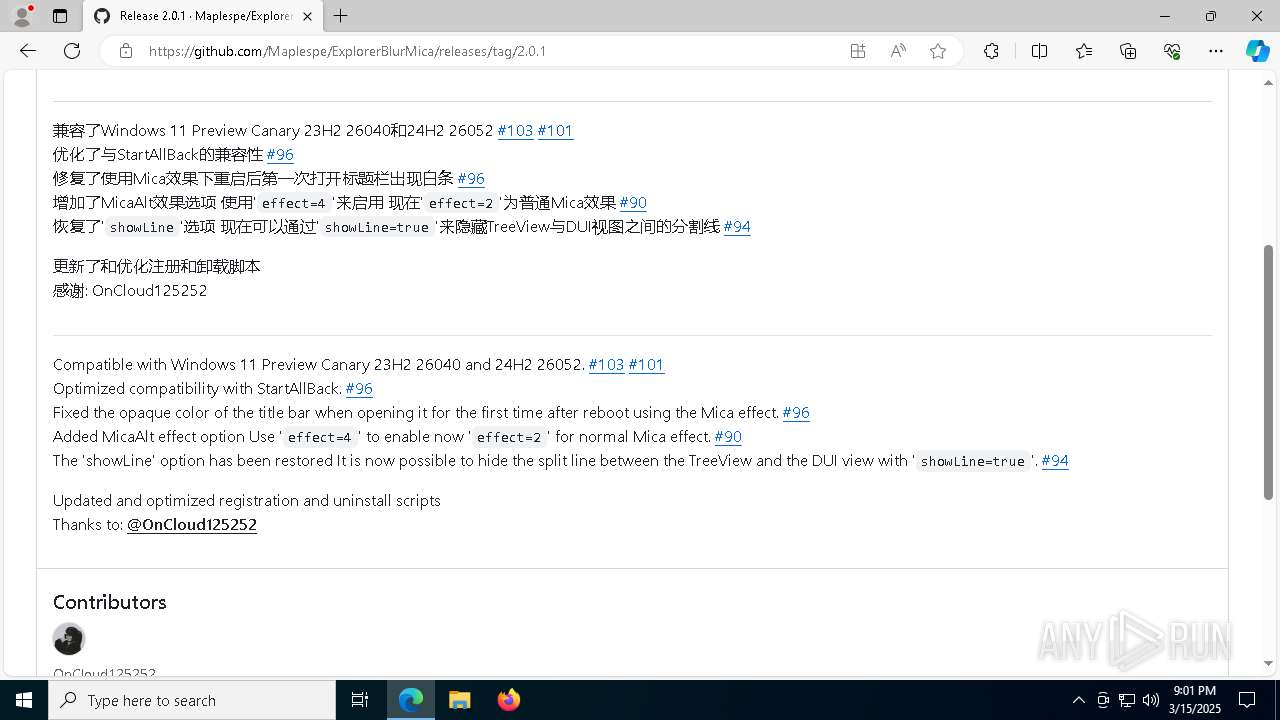
| TwitterDescription: | 兼容了Windows 11 Preview Canary 23H2 26040和24H2 26052 #103 #101 优化了与StartAllBack的兼容性 #96 修复了使用Mica效果下重启后第一次打开标题栏出现白条 #96 增加了MicaAlt效果选项 使用'effect=4'来启用 现在'effect=2'为普通Mica效果 #90 恢复了... |
| Hostname: | github.com |
| ExpectedHostname: | github.com |
| HTTPEquivXPjaxVersion: | e0075927c55fc7d0da57f7affd5f3e3197658df4021089e6ef5c9738212c0576 |
| HTTPEquivXPjaxCspVersion: | 77190eb53eb47fc30bd2fcc17a7eefa2dfd8505869fee9299ba911be3a40a9eb |
| HTTPEquivXPjaxCssVersion: | e9da97be1bcf5aa6bddc7e7ed6c7206dcb5b8d4504a096541c743dc0ebcf6360 |
| HTTPEquivXPjaxJsVersion: | 804ec48a6968b01e58c364191bca12314ca9d25182aedad43999e1d6e4a071a7 |
| TurboCacheControl: | no-preview |
| GoImport: | github.com/Maplespe/ExplorerBlurMica git https://github.com/Maplespe/ExplorerBlurMica.git |
| OctolyticsDimensionUser_id: | 43676879 |
| OctolyticsDimensionUser_login: | Maplespe |
| OctolyticsDimensionRepository_id: | 529213465 |
| OctolyticsDimensionRepository_nwo: | Maplespe/ExplorerBlurMica |
| OctolyticsDimensionRepository_public: | |
| OctolyticsDimensionRepository_is_fork: | - |
| OctolyticsDimensionRepository_network_root_id: | 529213465 |
| OctolyticsDimensionRepository_network_root_nwo: | Maplespe/ExplorerBlurMica |
| TurboBodyClasses: | logged-out env-production page-responsive |
| BrowserStatsUrl: | https://api.github.com/_private/browser/stats |
| BrowserErrorsUrl: | https://api.github.com/_private/browser/errors |
| ThemeColor: | #1e2327 |
| ColorScheme: | light dark |
Total processes
273
Monitored processes
117
Malicious processes
2
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | timeout /t 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1596 --field-trial-handle=2668,i,17272099075646872669,16041997207621475099,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 544 | regsvr32 /u "C:\PROGRA~1\ExplorerBlurMica.dll" | C:\Windows\System32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1940 --field-trial-handle=2668,i,17272099075646872669,16041997207621475099,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 672 | mode CON COLS=37 LINES=3 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=3704 --field-trial-handle=2668,i,17272099075646872669,16041997207621475099,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1008 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7956 --field-trial-handle=2668,i,17272099075646872669,16041997207621475099,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1052 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7816 --field-trial-handle=2668,i,17272099075646872669,16041997207621475099,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
85 331
Read events
84 594
Write events
680
Delete events
57
Modification events
| (PID) Process: | (7988) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7988) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7988) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7988) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: D3BB8822FE8E2F00 | |||
| (PID) Process: | (7988) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7988) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: B8979022FE8E2F00 | |||
| (PID) Process: | (7988) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328402 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {ACA7B651-D336-4608-9C4E-9A3A360FF572} | |||
| (PID) Process: | (7988) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328402 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {FC901E1E-F401-4DBE-8A95-82816C499FD8} | |||
| (PID) Process: | (7988) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328402 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {0B100C0F-6331-4250-9A7A-D21D4B7F634E} | |||
| (PID) Process: | (7988) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328402 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A66FCDBA-4CF4-4545-AE77-A8BFC31F7548} | |||
Executable files
48
Suspicious files
1 041
Text files
353
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10f222.TMP | — | |
MD5:— | SHA256:— | |||
| 7988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10f232.TMP | — | |
MD5:— | SHA256:— | |||
| 7988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10f251.TMP | — | |
MD5:— | SHA256:— | |||
| 7988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10f270.TMP | — | |
MD5:— | SHA256:— | |||
| 7988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF10f29f.TMP | — | |
MD5:— | SHA256:— | |||
| 7988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
57
TCP/UDP connections
156
DNS requests
171
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7296 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7228 | msedge.exe | GET | 304 | 23.209.209.135:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
720 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7916 | svchost.exe | GET | 206 | 2.22.242.122:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1742395360&P2=404&P3=2&P4=Qo0nBElRaN0xi%2bU8rRhzP9M3v%2fFhMoMacyqFTFEY5%2fWg%2bzD0rwAGhPJUZ7sGKCXt6gSJBM6i28e3JONbaRfpZQ%3d%3d | unknown | — | — | whitelisted |
7916 | svchost.exe | GET | 206 | 2.22.242.122:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1742395360&P2=404&P3=2&P4=Qo0nBElRaN0xi%2bU8rRhzP9M3v%2fFhMoMacyqFTFEY5%2fWg%2bzD0rwAGhPJUZ7sGKCXt6gSJBM6i28e3JONbaRfpZQ%3d%3d | unknown | — | — | whitelisted |
7916 | svchost.exe | GET | 206 | 2.22.242.122:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1742395360&P2=404&P3=2&P4=Qo0nBElRaN0xi%2bU8rRhzP9M3v%2fFhMoMacyqFTFEY5%2fWg%2bzD0rwAGhPJUZ7sGKCXt6gSJBM6i28e3JONbaRfpZQ%3d%3d | unknown | — | — | whitelisted |
7916 | svchost.exe | HEAD | 200 | 2.22.242.122:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1742375543&P2=404&P3=2&P4=jnPQItz7PoCZB5B6zPwtbDBeNcHnqiYZAFYhyENvrRhQLV%2b8nQLDqmVUK3KUMUJiaxTD2aHSIJD8KRQtOgHNWw%3d%3d | unknown | — | — | whitelisted |
7916 | svchost.exe | GET | 206 | 2.22.242.122:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1742375543&P2=404&P3=2&P4=jnPQItz7PoCZB5B6zPwtbDBeNcHnqiYZAFYhyENvrRhQLV%2b8nQLDqmVUK3KUMUJiaxTD2aHSIJD8KRQtOgHNWw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4784 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7296 | backgroundTaskHost.exe | 20.103.156.88:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7296 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7228 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
7228 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
7228 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
7228 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
7228 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (bit .ly) |
7228 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (bit .ly) |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7228 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |