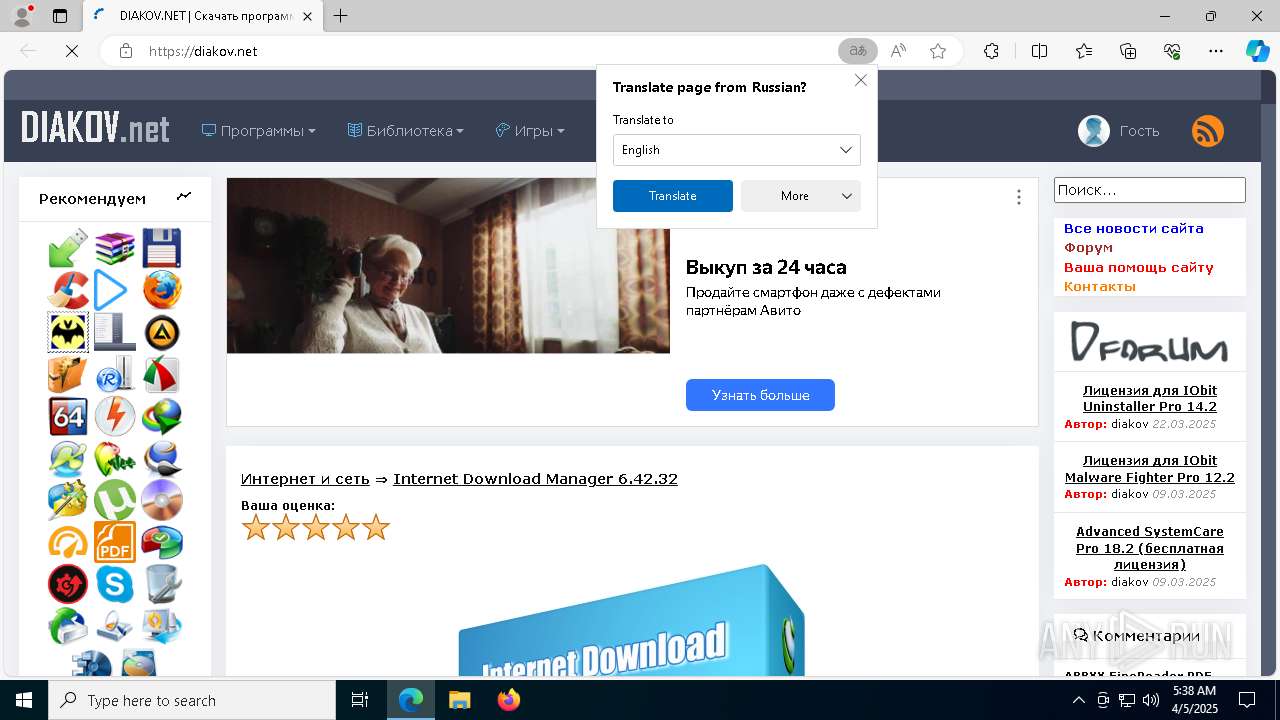
| File name: | StartAllBack-3.9.7.exe |
| Full analysis: | https://app.any.run/tasks/60dfa797-9ba5-4853-831b-cbeb849f7f6d |
| Verdict: | Malicious activity |
| Analysis date: | April 05, 2025, 05:37:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 86063B75B8510FBA54301569B9BC60D8 |
| SHA1: | B98C960E12DA5037B0FF98F23DD1F37663348E63 |
| SHA256: | 514C48EB2F8202B1779F7BF8D471C847A0C682BF93ED8EF6E5576596B79FF8B9 |
| SSDEEP: | 98304:Wj4HoDlWuSDpV7evItRpRv6m3cjsisSW/316YlfeONCxFloooNreIwI6mKLRQ0+q:znXnq |
MALICIOUS
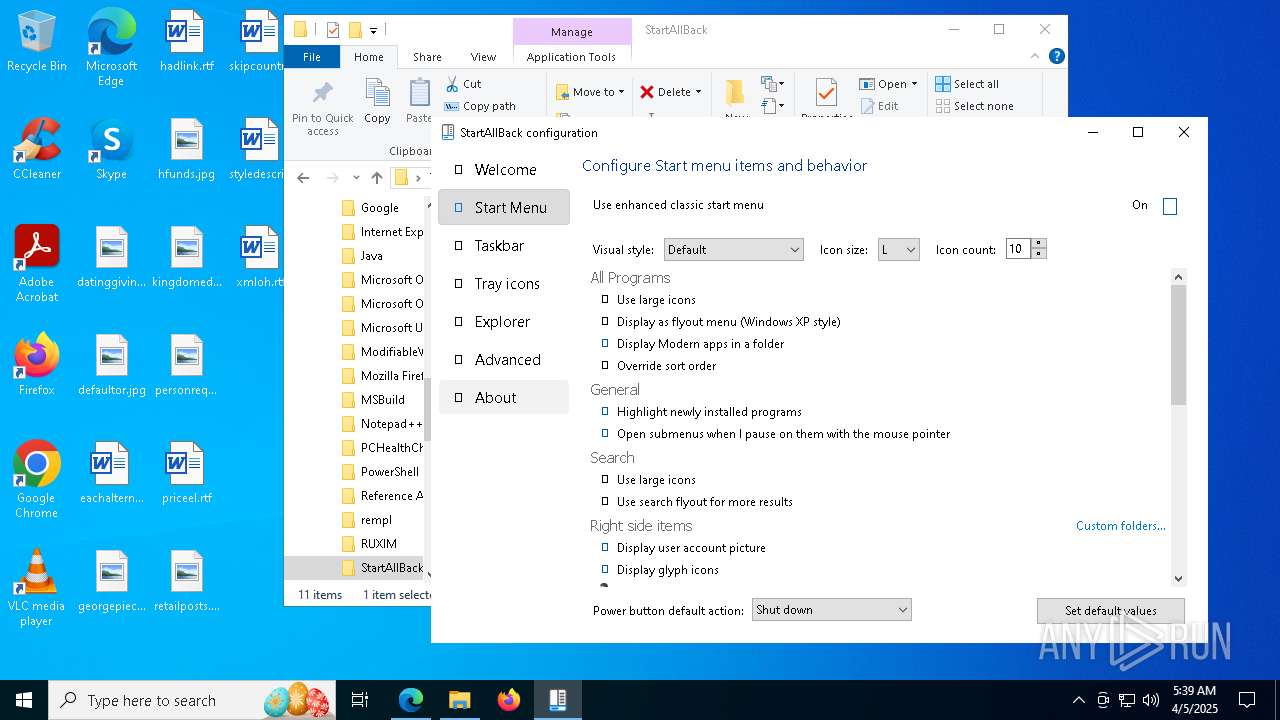
Uses Task Scheduler to run other applications
- StartAllBackCfg.exe (PID: 6372)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- StartAllBack-3.9.7.exe (PID: 3784)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 2140)
Uses TASKKILL.EXE to kill process
- StartAllBackCfg.exe (PID: 6372)
Executable content was dropped or overwritten
- StartAllBackCfg.exe (PID: 6372)
- StartAllBack-3.9.7.exe (PID: 3784)
Creates a software uninstall entry
- StartAllBackCfg.exe (PID: 6372)
Changes default file association
- StartAllBackCfg.exe (PID: 6372)
Reads security settings of Internet Explorer
- StartAllBackCfg.exe (PID: 6372)
- StartAllBack-3.9.7.exe (PID: 3784)
- StartMenuExperienceHost.exe (PID: 1056)
- StartAllBackCfg.exe (PID: 8488)
Creates/Modifies COM task schedule object
- StartAllBackCfg.exe (PID: 6372)
The process executes via Task Scheduler
- explorer.exe (PID: 2564)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 1056)
- SearchApp.exe (PID: 6012)
- StartAllBackCfg.exe (PID: 8488)
Creates file in the systems drive root
- explorer.exe (PID: 2564)
INFO
The sample compiled with russian language support
- StartAllBack-3.9.7.exe (PID: 3784)
Reads the computer name
- StartAllBackCfg.exe (PID: 6372)
- StartAllBack-3.9.7.exe (PID: 3784)
- SearchApp.exe (PID: 6012)
- StartMenuExperienceHost.exe (PID: 1056)
- TextInputHost.exe (PID: 7932)
- UpdateCheck.exe (PID: 7820)
- identity_helper.exe (PID: 9080)
- StartAllBackCfg.exe (PID: 8488)
Checks supported languages
- StartAllBack-3.9.7.exe (PID: 3784)
- StartAllBackCfg.exe (PID: 6372)
- SearchApp.exe (PID: 6012)
- StartMenuExperienceHost.exe (PID: 1056)
- TextInputHost.exe (PID: 7932)
- identity_helper.exe (PID: 9080)
- StartAllBackCfg.exe (PID: 8488)
- DarkMagicLoaderX64.exe (PID: 6876)
- UpdateCheck.exe (PID: 7820)
The sample compiled with english language support
- StartAllBack-3.9.7.exe (PID: 3784)
- StartAllBackCfg.exe (PID: 6372)
- msedge.exe (PID: 6476)
Create files in a temporary directory
- StartAllBack-3.9.7.exe (PID: 3784)
- StartAllBackCfg.exe (PID: 6372)
Creates files in the program directory
- StartAllBackCfg.exe (PID: 6372)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2564)
- mmc.exe (PID: 9004)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 6012)
Process checks computer location settings
- SearchApp.exe (PID: 6012)
- StartMenuExperienceHost.exe (PID: 1056)
- StartAllBackCfg.exe (PID: 8488)
Application launched itself
- msedge.exe (PID: 6380)
- msedge.exe (PID: 812)
Checks proxy server information
- explorer.exe (PID: 2564)
- SearchApp.exe (PID: 6012)
- slui.exe (PID: 8736)
Reads the software policy settings
- SearchApp.exe (PID: 6012)
- slui.exe (PID: 6632)
- slui.exe (PID: 8736)
- UpdateCheck.exe (PID: 7820)
Reads Environment values
- SearchApp.exe (PID: 6012)
- identity_helper.exe (PID: 9080)
Creates files or folders in the user directory
- explorer.exe (PID: 2564)
Executable content was dropped or overwritten
- msedge.exe (PID: 6476)
Reads Microsoft Office registry keys
- explorer.exe (PID: 2564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x323c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.9.7.5266 |
| ProductVersionNumber: | 3.9.7.5266 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Windows, Cyrillic |
| CompanyName: | diakov.net |
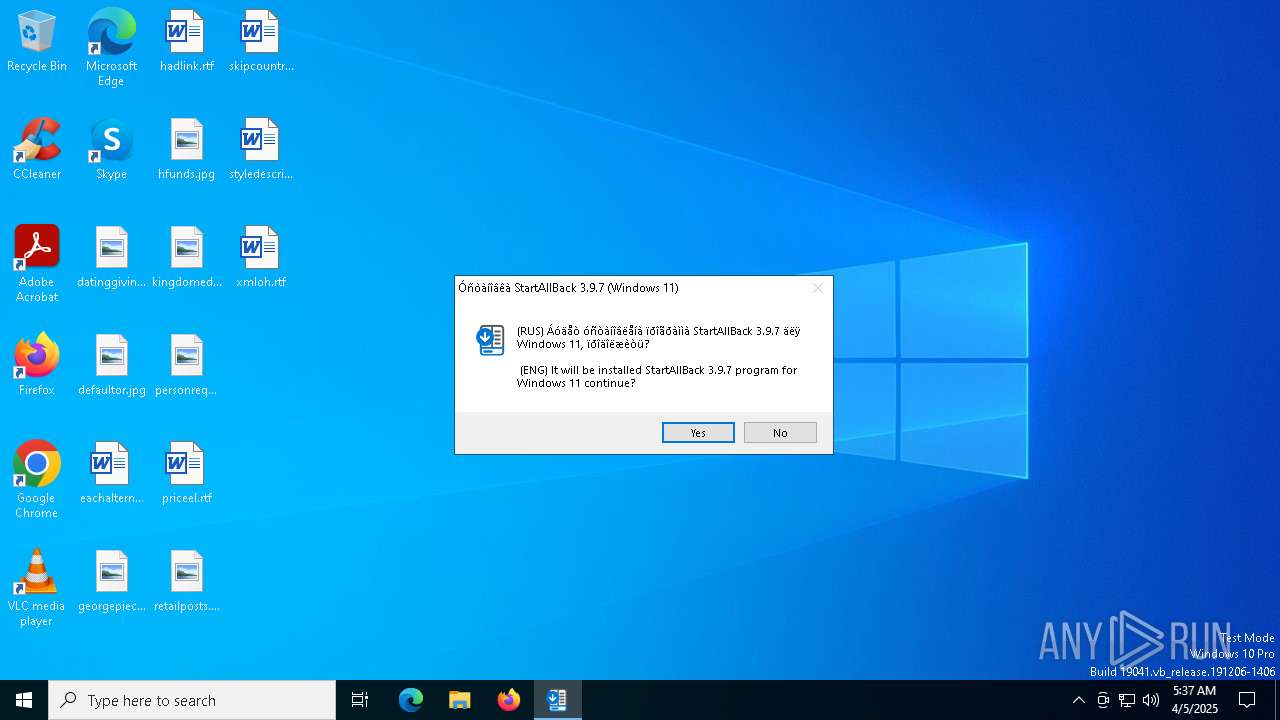
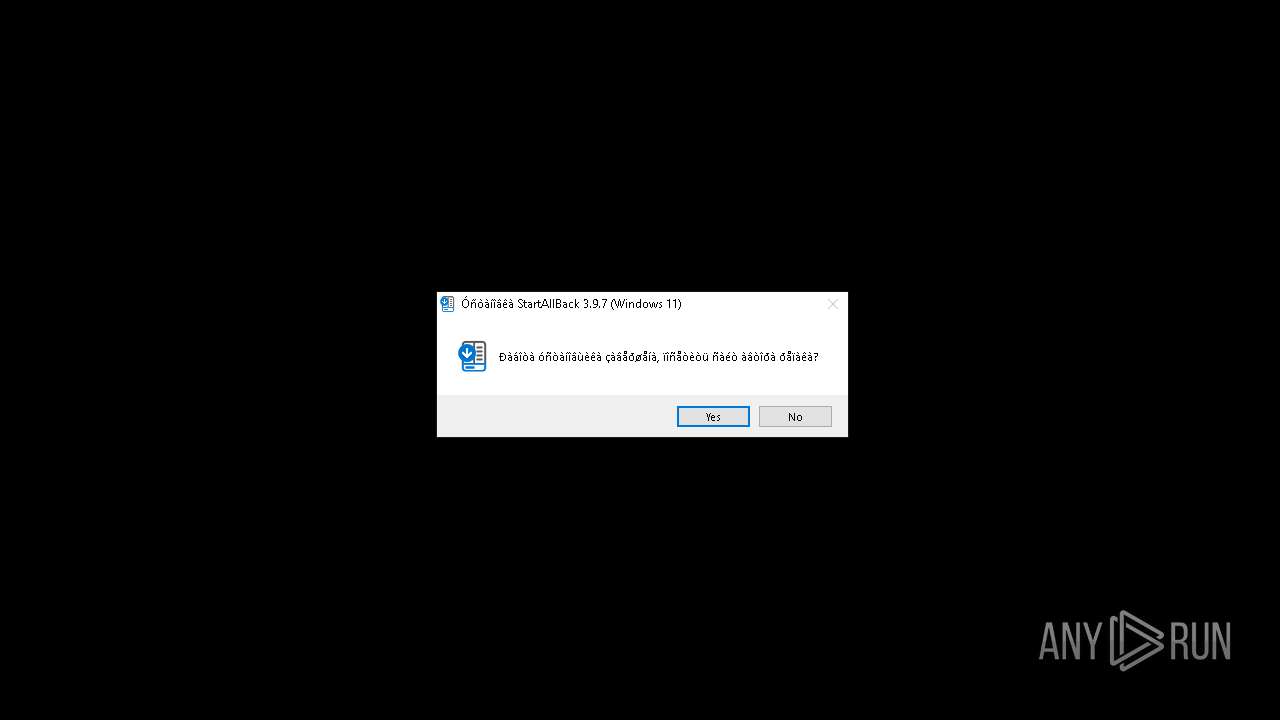
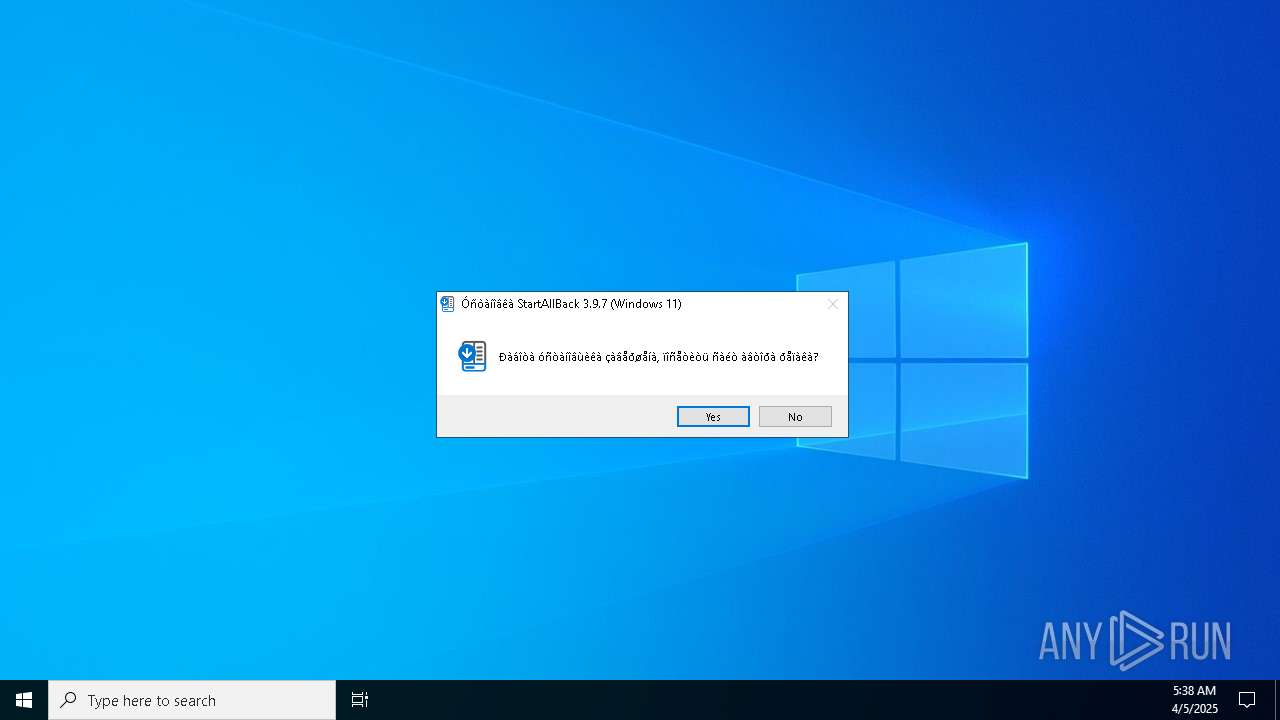
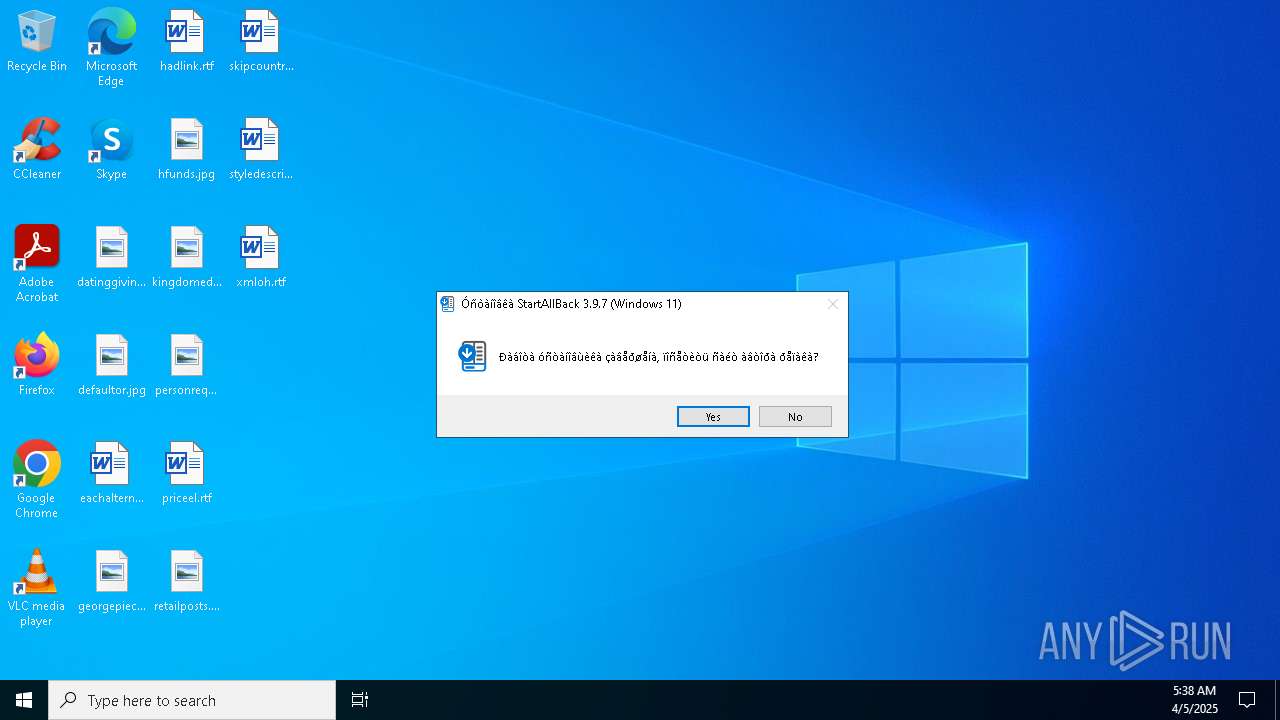
| FileDescription: | StartAllBack 3.9.7 (Windows 11) |
Total processes
245
Monitored processes
99
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --flag-switches-end --do-not-de-elevate --single-argument https://diakov.net/ | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1056 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8140 --field-trial-handle=2348,i,6363927006418573907,9569000646117463617,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tskill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --no-appcompat-clear --mojo-platform-channel-handle=5696 --field-trial-handle=2348,i,6363927006418573907,9569000646117463617,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1272 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7960 --field-trial-handle=2348,i,6363927006418573907,9569000646117463617,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x290,0x294,0x298,0x28c,0x2a0,0x7ffc8add5fd8,0x7ffc8add5fe4,0x7ffc8add5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1300 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7968 --field-trial-handle=2348,i,6363927006418573907,9569000646117463617,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7784 --field-trial-handle=2348,i,6363927006418573907,9569000646117463617,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2140 | schtasks.exe /Delete /TN "\StartIsBack health check" /F | C:\Windows\System32\schtasks.exe | — | StartAllBackCfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
64 435
Read events
63 829
Write events
568
Delete events
38
Modification events
| (PID) Process: | (3784) StartAllBack-3.9.7.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\StartAll |
| Operation: | write | Name: | AutoUpdates |
Value: 0 | |||
| (PID) Process: | (6372) StartAllBackCfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\StartIsBack.AppsFolder\Shell\Delete |
| Operation: | write | Name: | MuiVerb |
Value: @shell32.dll,-33553 | |||
| (PID) Process: | (6372) StartAllBackCfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\StartIsBack.AppsFolder\Shell\Delete |
| Operation: | write | Name: | Position |
Value: Bottom | |||
| (PID) Process: | (6372) StartAllBackCfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\StartIsBack.AppsFolder\Shell\Delete\Command |
| Operation: | write | Name: | DelegateExecute |
Value: {E5C31EC8-C5E6-4E07-957E-944DB4AAD85E} | |||
| (PID) Process: | (6372) StartAllBackCfg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\StartIsBack |
| Operation: | delete value | Name: | CurrentVersion |
Value: | |||
| (PID) Process: | (6372) StartAllBackCfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{ab0b37ec-56f6-4a0e-a8fd-7a8bf7c2da97}\InProcServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (6372) StartAllBackCfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{117E3954-5034-453A-A18B-7B79493646E6}\InProcServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (6372) StartAllBackCfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Drive\shellex\FolderExtensions\{117E3954-5034-453A-A18B-7B79493646E6} |
| Operation: | write | Name: | DriveMask |
Value: 255 | |||
| (PID) Process: | (6372) StartAllBackCfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\StartAllBack |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\StartAllBack\ | |||
| (PID) Process: | (6372) StartAllBackCfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\StartAllBack |
| Operation: | write | Name: | Publisher |
Value: startisback.com | |||
Executable files
48
Suspicious files
710
Text files
351
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
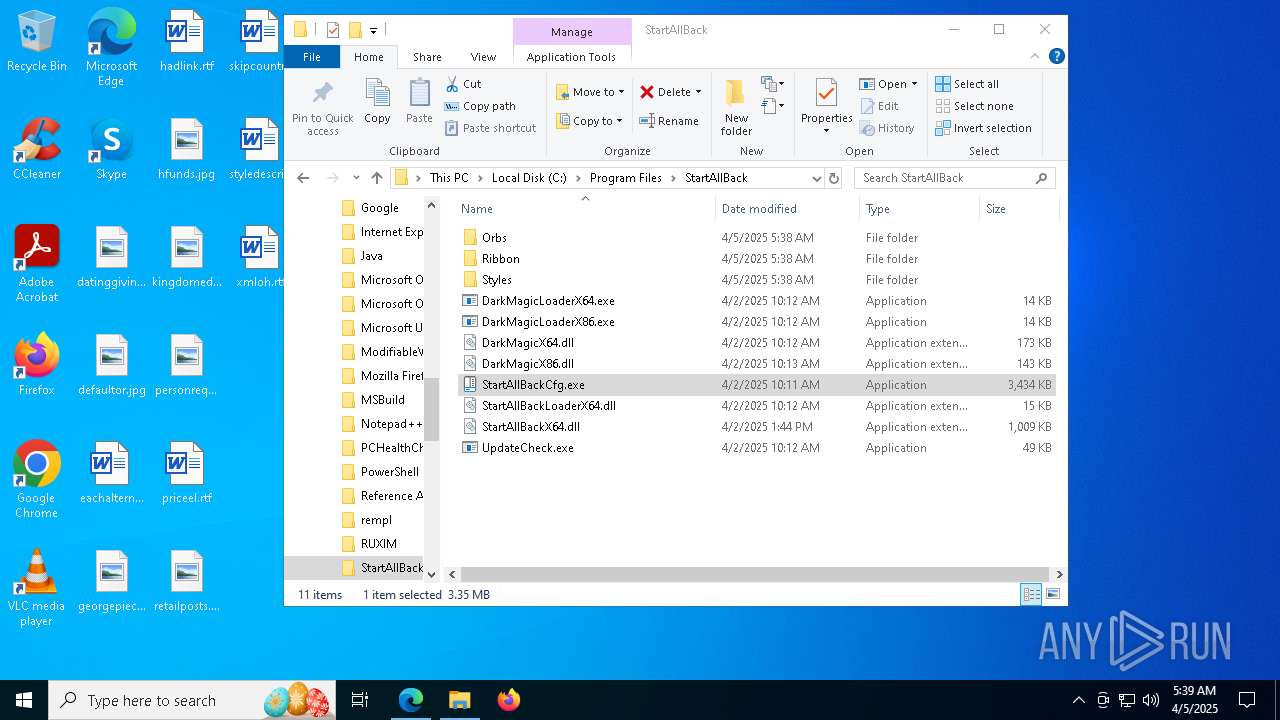
| 3784 | StartAllBack-3.9.7.exe | C:\Users\admin\AppData\Local\Temp\Start\DarkMagicLoaderX64.exe | executable | |
MD5:CBF1F0D8763E72D31375DE938C0FCAC0 | SHA256:FE45E3ED57A947BE938C3EFCE54C79A2EDB81349F6E8A914FC4B7828C9446DFE | |||
| 3784 | StartAllBack-3.9.7.exe | C:\Users\admin\AppData\Local\Temp\Start\DarkMagicX64.dll | executable | |
MD5:D0C44C7F7A0D31C0006C3C626B0075CB | SHA256:626A848CA52795785A979A81991273C282CD7E51AF7921B24EF7BA170030EE32 | |||
| 3784 | StartAllBack-3.9.7.exe | C:\Users\admin\AppData\Local\Temp\Start\Ribbon\theme-dark\Windows.Computer.Manage.svg | image | |
MD5:107FE8D57A6D6821321648484EA41333 | SHA256:11B72939689A479CBDA2BF96A64774D2AC605C7054CF23DEBA0663ED4DC11D6C | |||
| 3784 | StartAllBack-3.9.7.exe | C:\Users\admin\AppData\Local\Temp\Start\Orbs\Windows 7.orb | executable | |
MD5:85328E698E8A74852B4061A683915DC8 | SHA256:E5B74E9E7BD6758A0154B11462AE3328EDD143190865198104D8BD53B9AF7275 | |||
| 3784 | StartAllBack-3.9.7.exe | C:\Users\admin\AppData\Local\Temp\Start\DarkMagicX86.dll | executable | |
MD5:E8B3FA9390B9E237A240822DF3E943AA | SHA256:6B87D591B67DD5C3F36903A4E654A57AE49ADD55D3AEF40D78D055FC2BA40205 | |||
| 3784 | StartAllBack-3.9.7.exe | C:\Users\admin\AppData\Local\Temp\Start\Orbs\w8logo.svg | image | |
MD5:F13738B41B7A2042C53DD228601639E0 | SHA256:C75684410793A98A051A1CF95395709C73E9589037D47BE3F6277B4AC355B7FB | |||
| 3784 | StartAllBack-3.9.7.exe | C:\Users\admin\AppData\Local\Temp\Start\Ribbon\theme-dark\Windows.shareprivate.svg | image | |
MD5:F330543683BD4AE04F346F54507D22E3 | SHA256:EBFCEADFEAC8434C464713EC411E1B9059A743EF0E7B676ADABA78B005BB877E | |||
| 3784 | StartAllBack-3.9.7.exe | C:\Users\admin\AppData\Local\Temp\Start\Ribbon\theme-dark\Windows.MoveToMenu.svg | image | |
MD5:7BEACB39451CA90854D81DC79B25F579 | SHA256:40F70DB8F7814ACF922E25411F82F9D9B9420D30E34F5C6199B8488E260CA13F | |||
| 3784 | StartAllBack-3.9.7.exe | C:\Users\admin\AppData\Local\Temp\Start\StartAllBackCfg.exe | executable | |
MD5:B83F9E9324A52378C93A06F39CA75CD3 | SHA256:C40FB72CAA95F4BC5F8052DD771B972650EC256D9D1DA5CCFBF7B021750AA50F | |||
| 3784 | StartAllBack-3.9.7.exe | C:\Users\admin\AppData\Local\Temp\Start\Ribbon\theme-dark\Windows.RibbonPermissionsDialog.svg | image | |
MD5:F0E4BF42CB74C5DD771F24C743F868E0 | SHA256:2B9A7C378E0160AC8E5843F1CED91021802B677776DCF9FFA71524ADBEFA1800 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
196
DNS requests
210
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7508 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6012 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6012 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6012 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4620 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1744039862&P2=404&P3=2&P4=Zuag1z58QDWnfufcuzeGaytywWj%2bx5rTOVuidNsXWaV1PSEPFZiVLkwNqQ08lvzOgb9iauU6SZRXx%2b%2fUG87gUw%3d%3d | unknown | — | — | whitelisted |
6012 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4620 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1744039862&P2=404&P3=2&P4=Zuag1z58QDWnfufcuzeGaytywWj%2bx5rTOVuidNsXWaV1PSEPFZiVLkwNqQ08lvzOgb9iauU6SZRXx%2b%2fUG87gUw%3d%3d | unknown | — | — | whitelisted |
4620 | svchost.exe | GET | 206 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1744039862&P2=404&P3=2&P4=Zuag1z58QDWnfufcuzeGaytywWj%2bx5rTOVuidNsXWaV1PSEPFZiVLkwNqQ08lvzOgb9iauU6SZRXx%2b%2fUG87gUw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 20.7.2.167:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
diakov.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6012 | SearchApp.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |