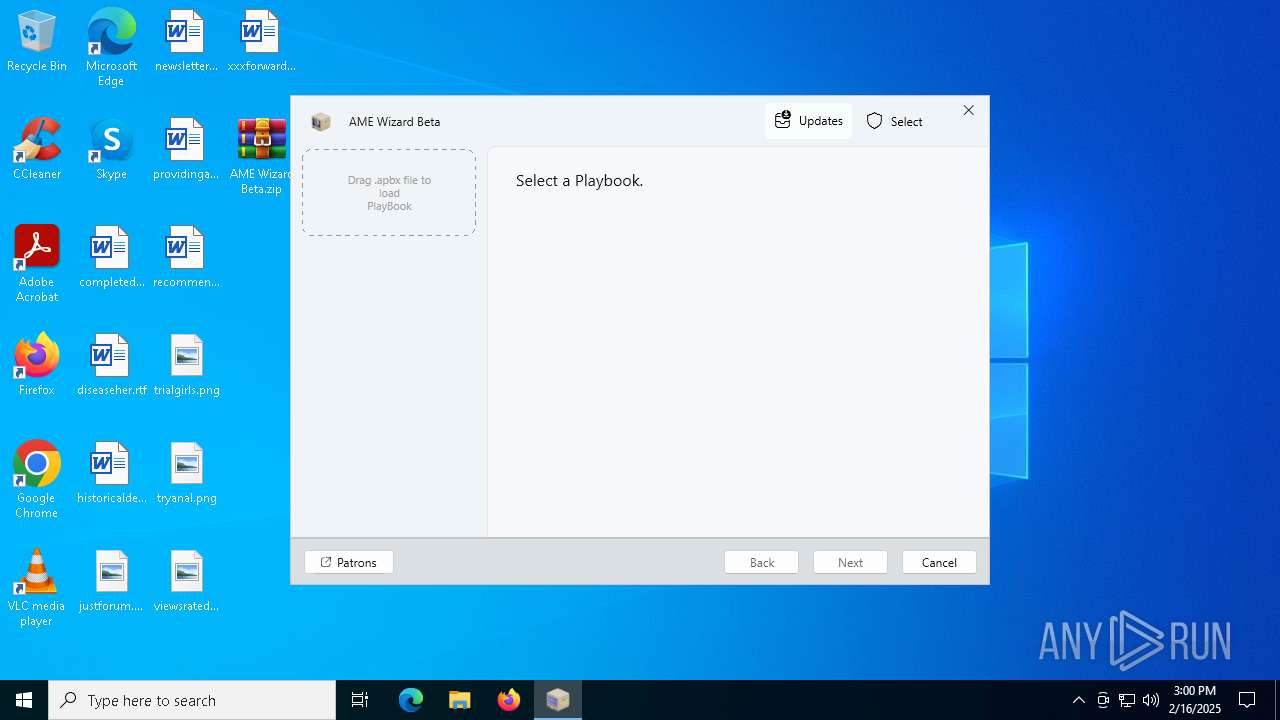
| File name: | AME Wizard Beta.zip |
| Full analysis: | https://app.any.run/tasks/978acc7f-93b0-4486-a4fa-7f10c417e679 |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2025, 15:00:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | FF4D9D30388CFA02551BCA527F764181 |
| SHA1: | E8876F162EEB70FFEC1B3A6EFC457EE394D67738 |
| SHA256: | 5141BB7FB0B9A6B1ECF82D40EE5E53EAF4A772BAC8DE94649323C9F7F206A149 |
| SSDEEP: | 98304:tB7Il/en31llscCp7Eeg6g5hX/TNM38CCAyC+f8NXK/WEqvjXrWCR09cf0kNlvbL:F6hg8GZlgRHRMmFGKY5Ta |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6476)
MIMIKATZ has been detected (YARA)
- AME Wizard Beta.exe (PID: 3640)
- AME Wizard Beta.exe (PID: 5340)
SUSPICIOUS
Executable content was dropped or overwritten
- AME Wizard Beta.exe (PID: 3640)
Drops 7-zip archiver for unpacking
- AME Wizard Beta.exe (PID: 3640)
Process drops legitimate windows executable
- AME Wizard Beta.exe (PID: 3640)
The process creates files with name similar to system file names
- AME Wizard Beta.exe (PID: 3640)
Reads security settings of Internet Explorer
- AME Wizard Beta.exe (PID: 3640)
- AME Wizard Beta.exe (PID: 5340)
The process drops C-runtime libraries
- AME Wizard Beta.exe (PID: 3640)
Reads the date of Windows installation
- AME Wizard Beta.exe (PID: 3640)
Application launched itself
- AME Wizard Beta.exe (PID: 3640)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6476)
Reads the computer name
- AME Wizard Beta.exe (PID: 3640)
- AME Wizard Beta.exe (PID: 5340)
Manual execution by a user
- AME Wizard Beta.exe (PID: 3640)
Checks supported languages
- AME Wizard Beta.exe (PID: 3640)
- AME Wizard Beta.exe (PID: 5340)
Reads the machine GUID from the registry
- AME Wizard Beta.exe (PID: 3640)
- AME Wizard Beta.exe (PID: 5340)
The sample compiled with english language support
- AME Wizard Beta.exe (PID: 3640)
Creates files in the program directory
- AME Wizard Beta.exe (PID: 3640)
- AME Wizard Beta.exe (PID: 5340)
Create files in a temporary directory
- AME Wizard Beta.exe (PID: 3640)
Reads Environment values
- AME Wizard Beta.exe (PID: 3640)
Process checks computer location settings
- AME Wizard Beta.exe (PID: 3640)
Checks proxy server information
- AME Wizard Beta.exe (PID: 3640)
Reads the software policy settings
- AME Wizard Beta.exe (PID: 3640)
Disables trace logs
- AME Wizard Beta.exe (PID: 3640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:05 22:02:50 |
| ZipCRC: | 0x4dd100d7 |
| ZipCompressedSize: | 10738944 |
| ZipUncompressedSize: | 18486784 |
| ZipFileName: | AME Wizard Beta.exe |
Total processes
129
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3640 | "C:\Users\admin\Desktop\AME Wizard Beta.exe" | C:\Users\admin\Desktop\AME Wizard Beta.exe | explorer.exe | ||||||||||||
User: admin Company: Ameliorated LLC Integrity Level: MEDIUM Description: AME Wizard Version: 0.7.7 Modules
| |||||||||||||||
| 5340 | "C:\Users\admin\Desktop\AME Wizard Beta.exe" "C:\Users\admin\AppData\Local\Temp\AME" Interprocess Administrator --Mode TwoWay --Nodes Level=User:ProcessID=3640 --Host 3640 | C:\Users\admin\Desktop\AME Wizard Beta.exe | AME Wizard Beta.exe | ||||||||||||
User: admin Company: Ameliorated LLC Integrity Level: HIGH Description: AME Wizard Version: 0.7.7 Modules
| |||||||||||||||
| 6476 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\AME Wizard Beta.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
4 360
Read events
4 328
Write events
32
Delete events
0
Modification events
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AME Wizard Beta.zip | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
52
Suspicious files
1
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3640 | AME Wizard Beta.exe | C:\Users\admin\AppData\Local\Temp\AME\7zxa.dll | executable | |
MD5:BC3754B7C77DFB6AED1722EF7F53B414 | SHA256:B54CAC90E649EBBF7C27CF1772F5C1644F4600DB88F0D51419A3529A5A5F95FC | |||
| 6476 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6476.34082\AME Wizard Beta.exe | executable | |
MD5:C44B28A9B41F37AAB0898FBC6E128F43 | SHA256:F09105EB7BCF102C8F6D77073D4575F1244EC7CD0B94ACD87C2DC3519BF18B19 | |||
| 3640 | AME Wizard Beta.exe | C:\Users\admin\AppData\Local\Temp\AME\Ben.Demystifier.dll | executable | |
MD5:965D07F46CD56AE2A4F310921230C206 | SHA256:F49EC56E6D8DD1029F990C08DBFC8CA7C5E8EDD353D8D7BA35FAE2C6ADCAA1C9 | |||
| 3640 | AME Wizard Beta.exe | C:\Users\admin\AppData\Local\Temp\AME\DiscUtils.Core.dll | executable | |
MD5:B9EA6C772CFB2B208354E2B9DB9772DB | SHA256:C338A2FC6B0879F326237B32B1D15EF617F41A12356FF289E8A09CDDCEBF67A0 | |||
| 3640 | AME Wizard Beta.exe | C:\Users\admin\AppData\Local\Temp\AME\DiscUtils.Iso9660.dll | executable | |
MD5:C7340CDF1E4AF72C007FE68694B7ECB5 | SHA256:4AA30F253343F3E130F4FF8DF0E955232134F339FFCB279CB8FE22A05ACC727D | |||
| 3640 | AME Wizard Beta.exe | C:\Users\admin\AppData\Local\Temp\AME\DiscUtils.Streams.dll | executable | |
MD5:E4229054374707ACECE62079A0037610 | SHA256:4275A6241646141419D97E30ACAB3B2D7F4CDA51B5ADC9BB12F9C8B385022D51 | |||
| 3640 | AME Wizard Beta.exe | C:\Users\admin\AppData\Local\Temp\AME\FluentIcons.Common.dll | executable | |
MD5:93B2FC669F12BBFE5D7F95DE850B5AE0 | SHA256:006B593E445FA07F9C717C9FC4A4928A133E59ED0B5EBA7C1F07BFBF3E7D430E | |||
| 3640 | AME Wizard Beta.exe | C:\Users\admin\AppData\Local\Temp\AME\7za.dll | executable | |
MD5:58FDBF10D3DCE4D2E270C03E8311D9DB | SHA256:0BBCC7BFC688A512911FBE679BBD279928F1B463431139685EBE39A98798134E | |||
| 3640 | AME Wizard Beta.exe | C:\Users\admin\AppData\Local\Temp\AME\client-helper.dll | executable | |
MD5:37FAF38D69284BDA23E383C000D946A3 | SHA256:0C84C4F52A981B57DA3C639D7F96DE0BD3E366C241B14972BA8A5F6D396DBD54 | |||
| 3640 | AME Wizard Beta.exe | C:\Users\admin\AppData\Local\Temp\AME\System.Buffers.dll | executable | |
MD5:ECDFE8EDE869D2CCC6BF99981EA96400 | SHA256:ACCCCFBE45D9F08FFEED9916E37B33E98C65BE012CFFF6E7FA7B67210CE1FEFB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
30
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6440 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6440 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6748 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
440 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 2.19.106.8:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6440 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
api.github.com |
| whitelisted |