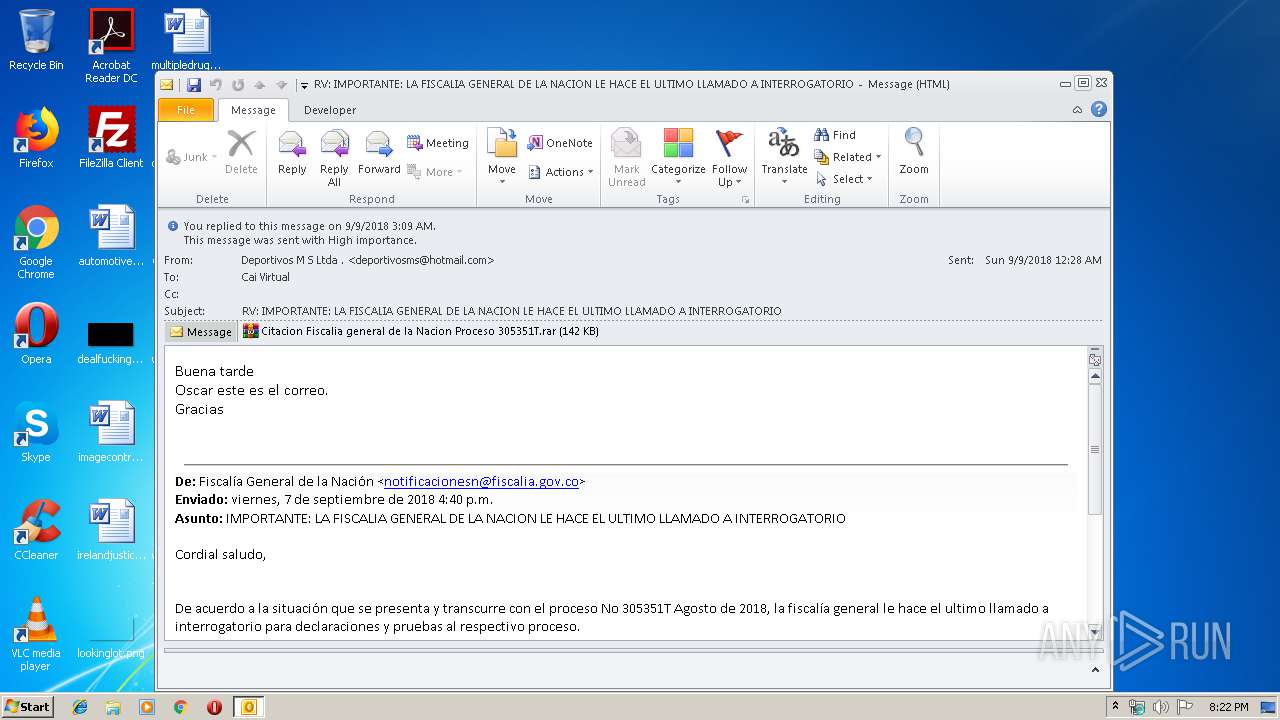
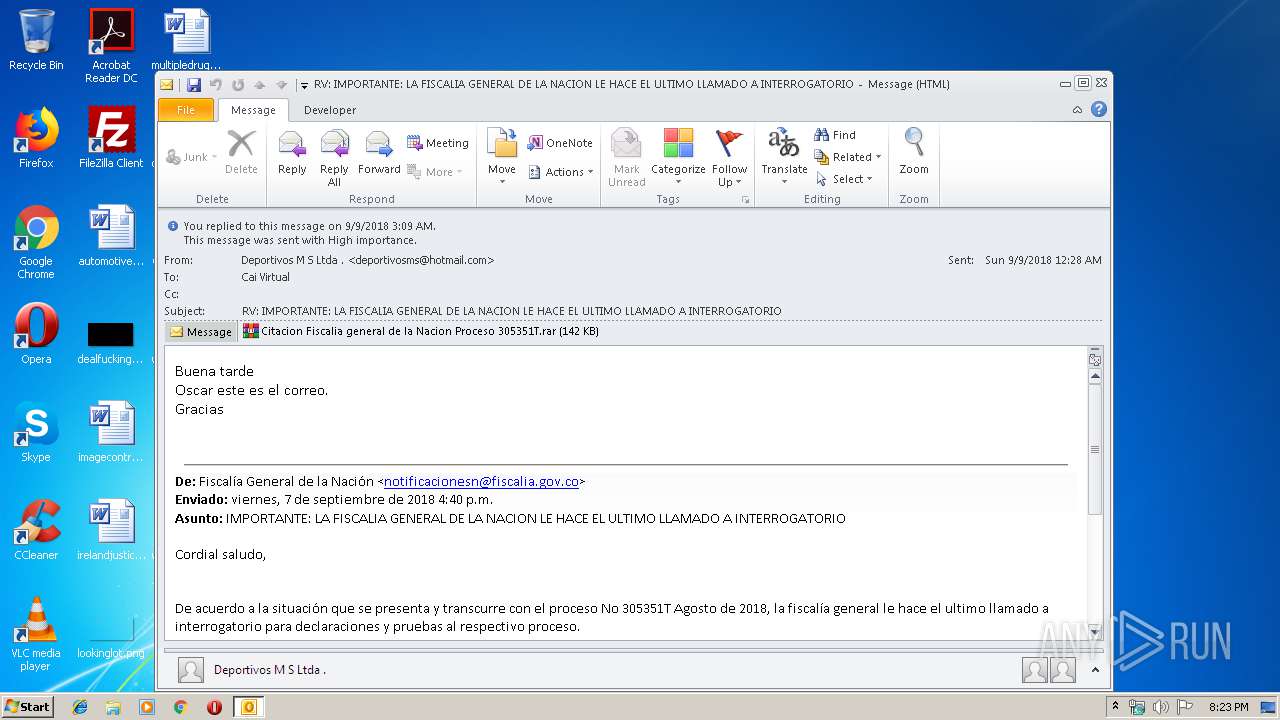
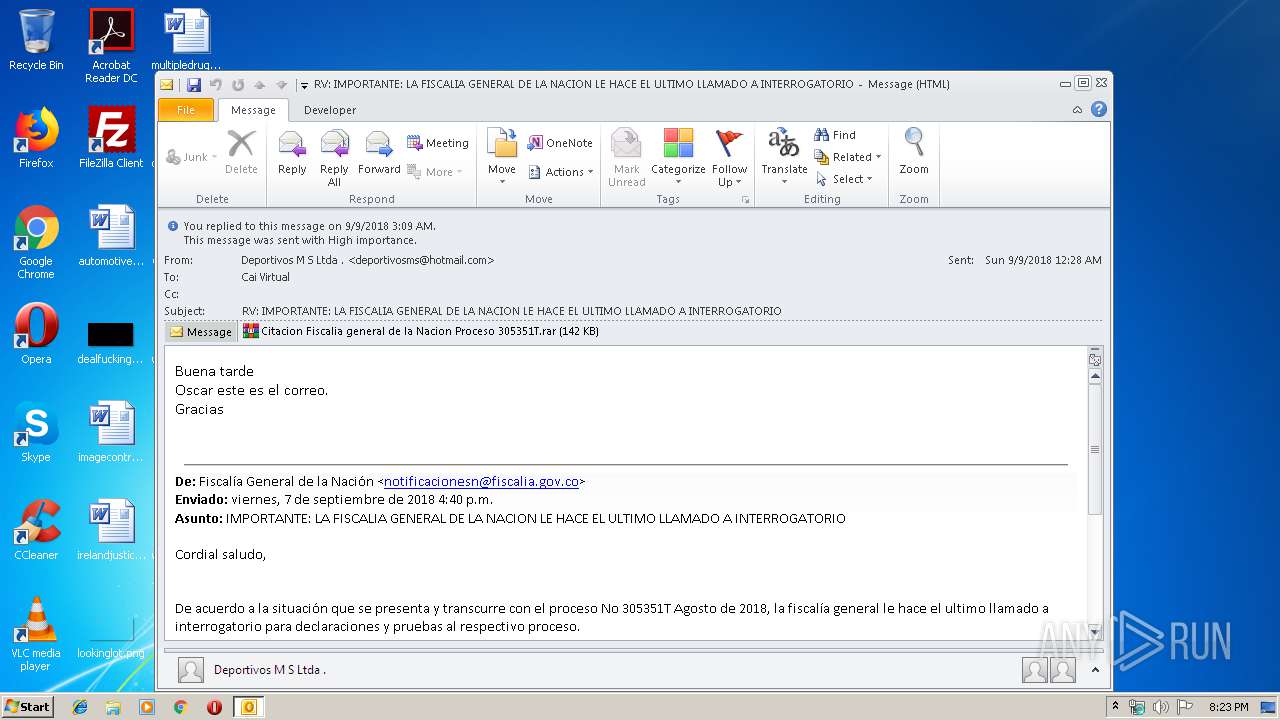
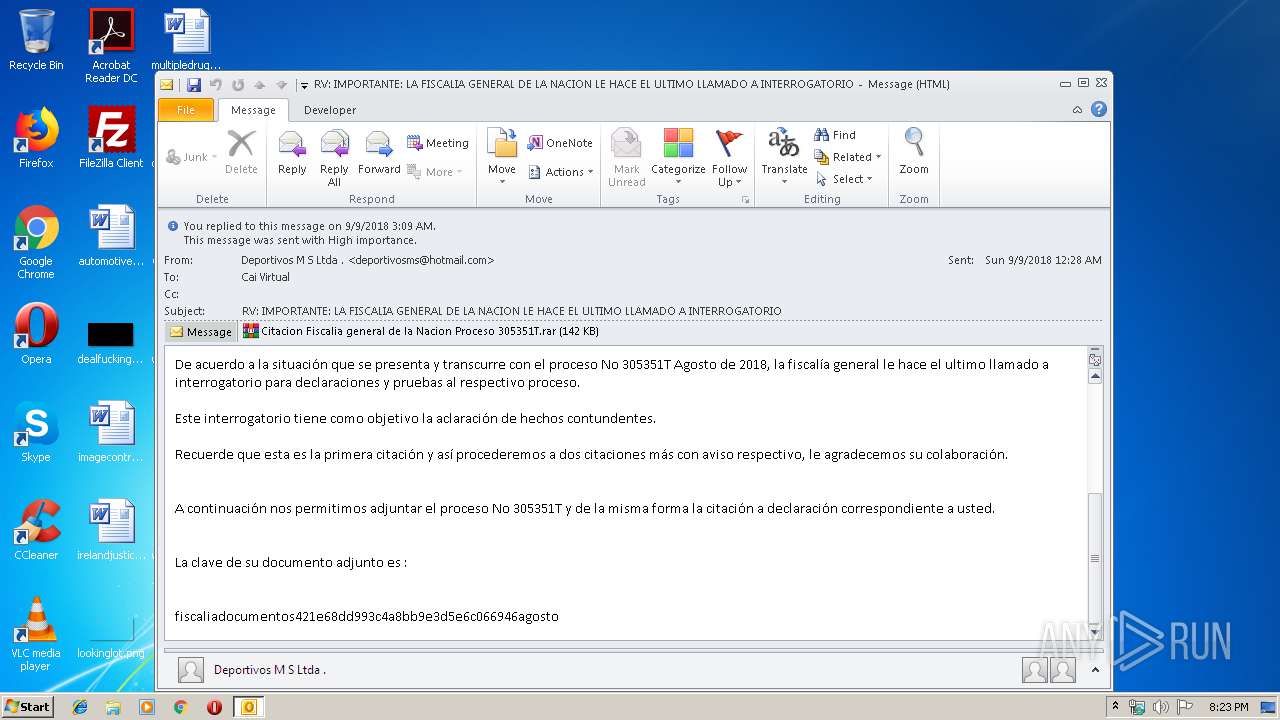
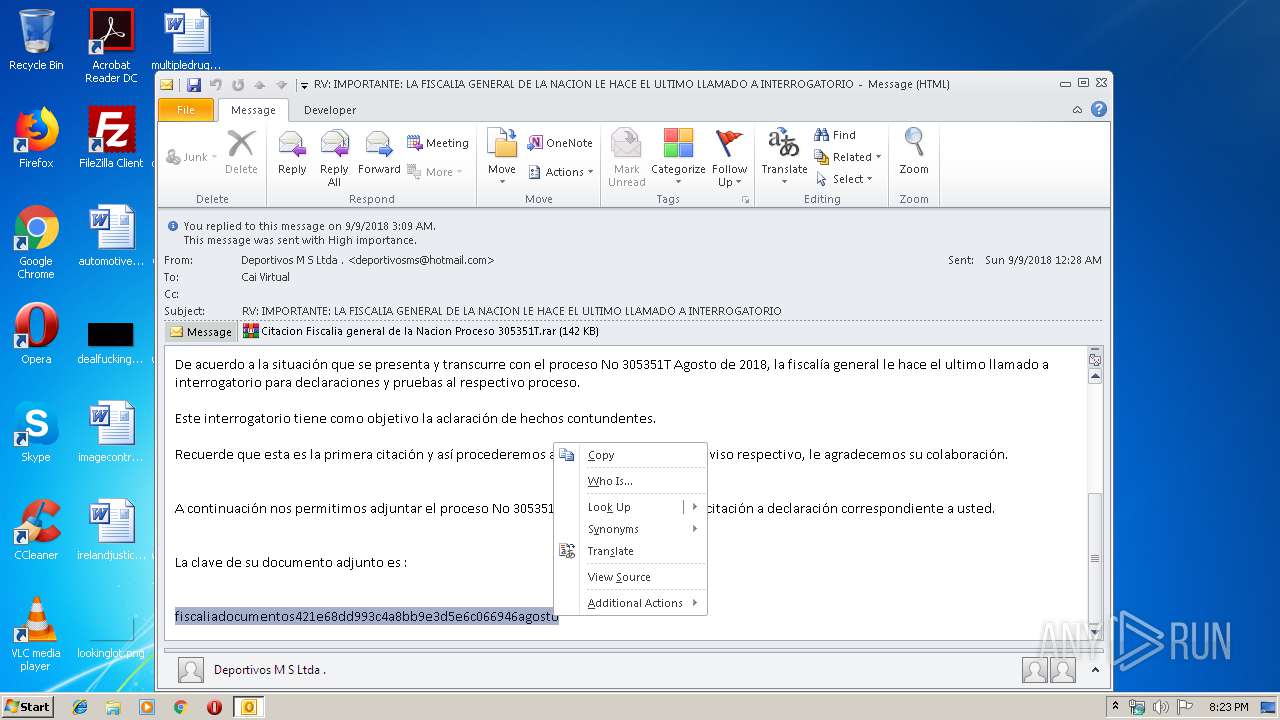
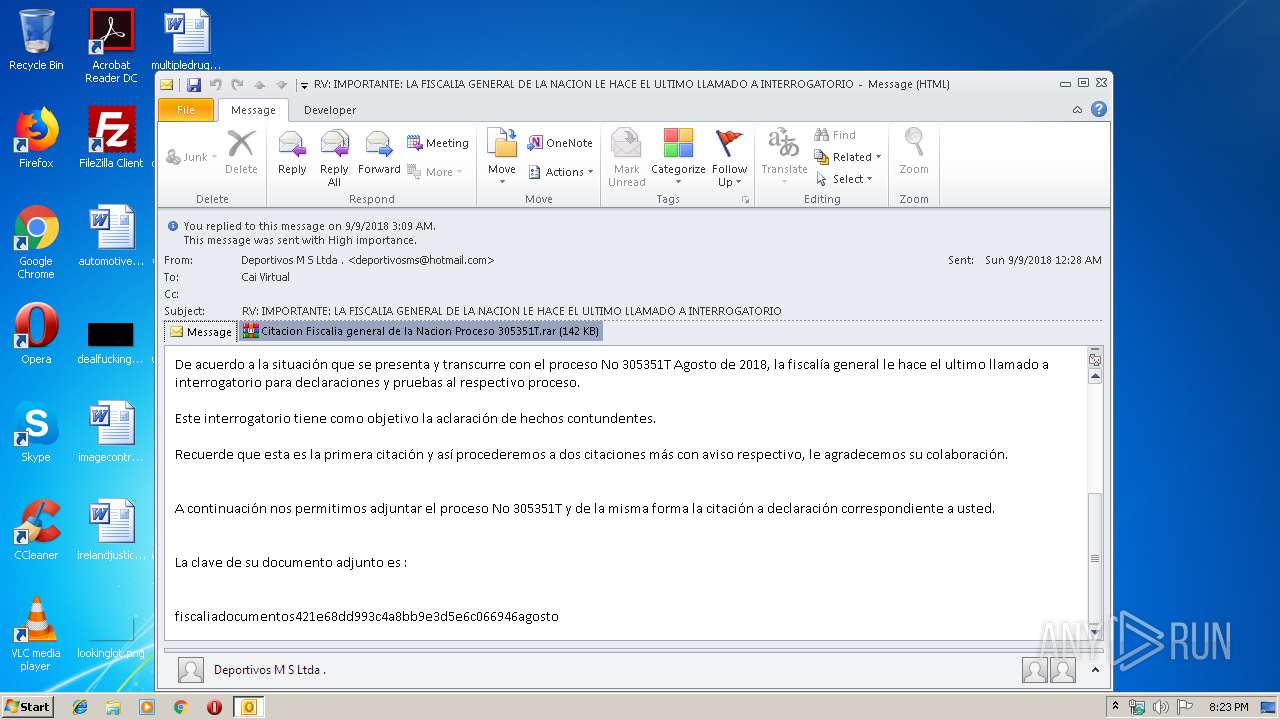
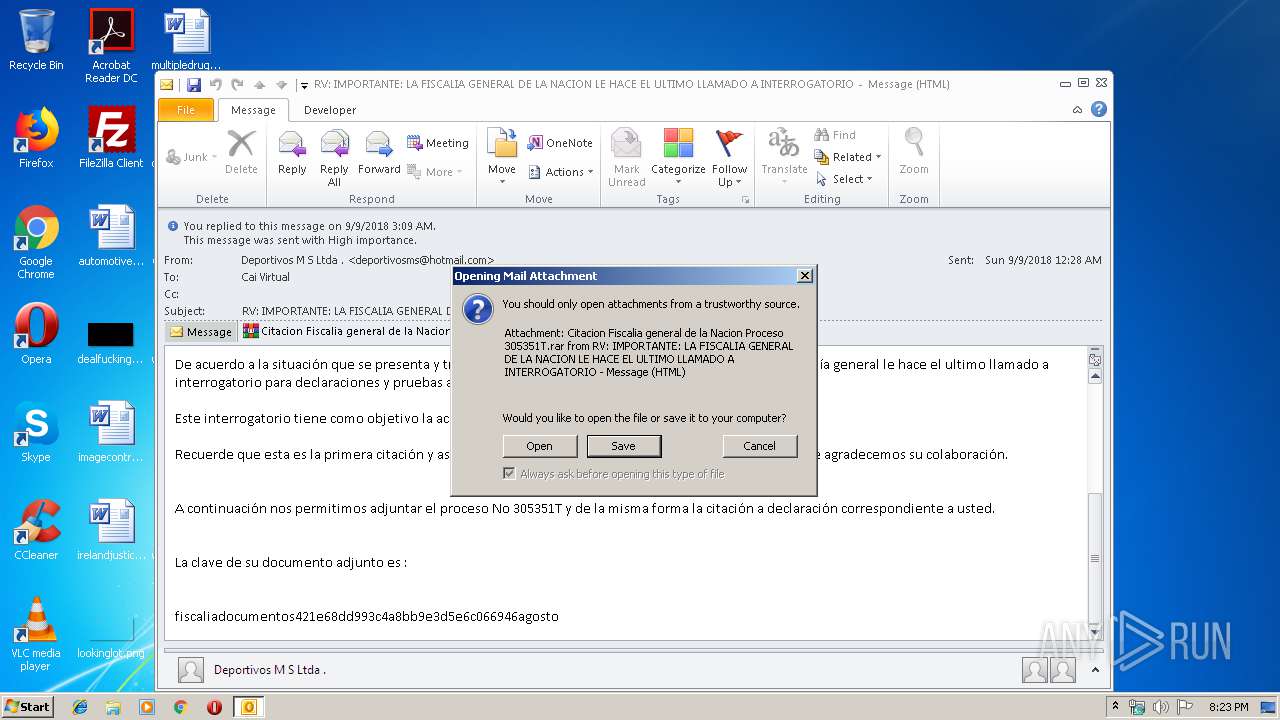
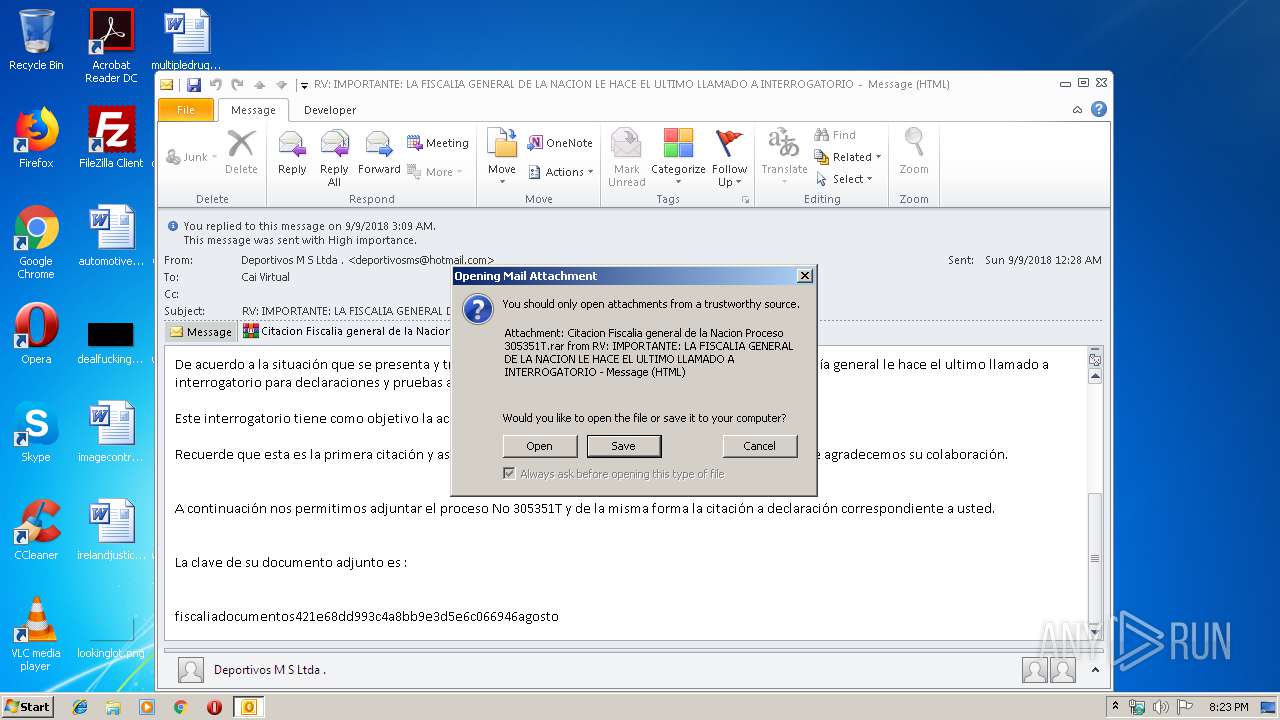
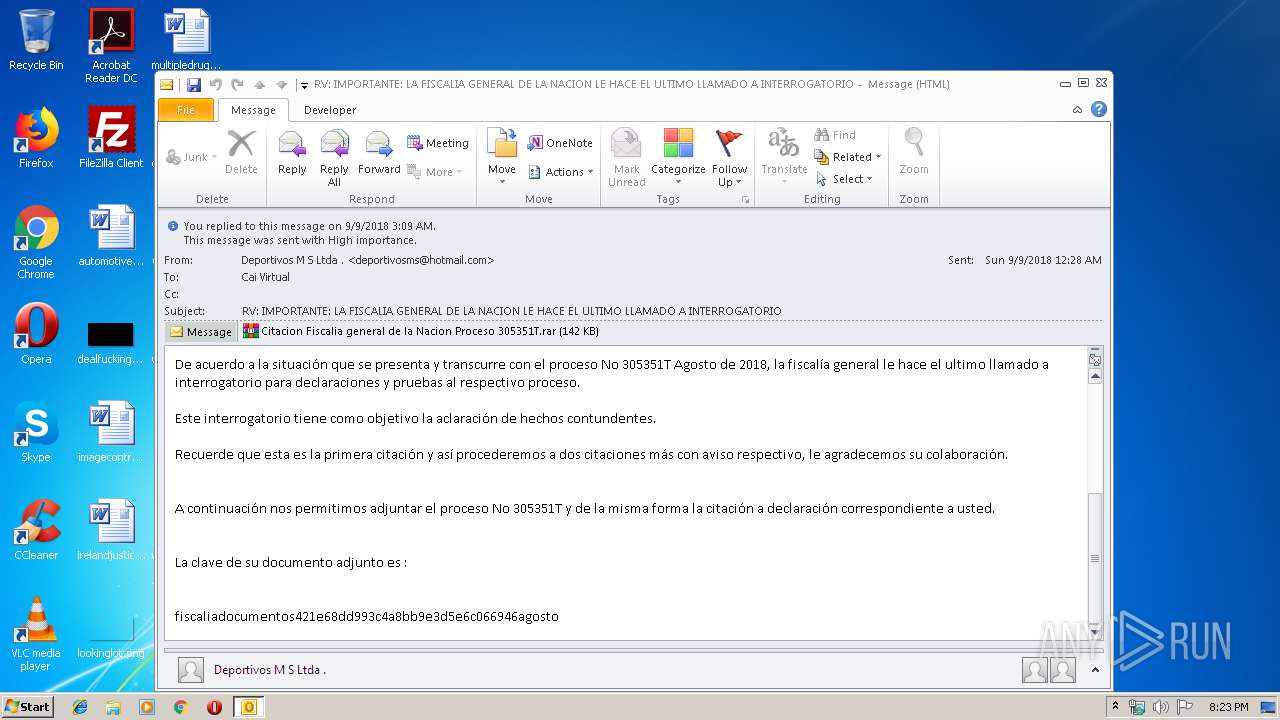
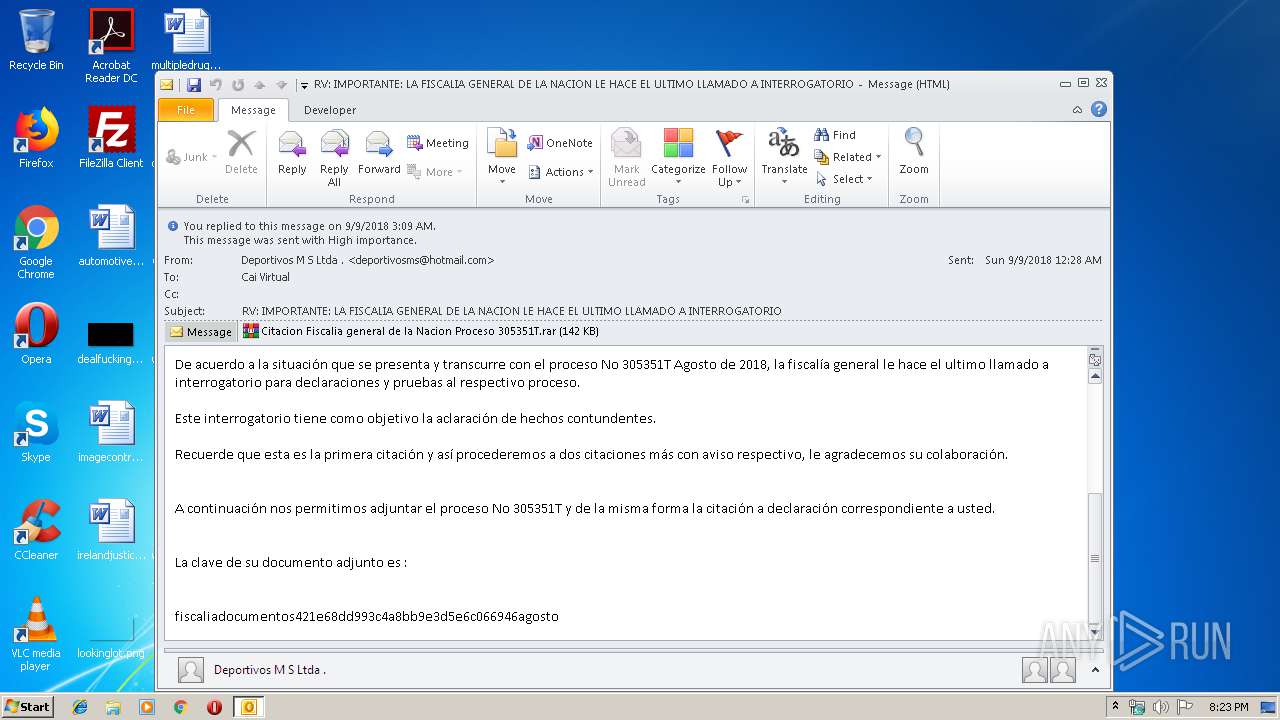
| File name: | RV IMPORTANTE LA FISCALIA GENERAL DE LA NACION LE HACE EL ULTIMO LLAMADO A INTERROGATORIO.msg |
| Full analysis: | https://app.any.run/tasks/36d451aa-d7d3-40e4-8124-d41e88e7f87e |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 19:22:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 0A454452DCBD5E58AC5C33A2106693DC |
| SHA1: | E0D9A916EAE66CD750E74EF0343C8EB2F228BB2C |
| SHA256: | 511ED8C5EAF4E7567827D3994FA4B194E34EF4B7BAA4E6CEF524D95BF8786D03 |
| SSDEEP: | 3072:wIOdNVMZnybfkb4Xaa46W7p2mtxqoHmjwtEytYOvKgy7BT12F:ienp4X5462dBGjwtDYelAM |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2360)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2360)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2360)
Starts Microsoft Office Application
- WinRAR.exe (PID: 1732)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2384)
- OUTLOOK.EXE (PID: 2360)
Creates files in the user directory
- WINWORD.EXE (PID: 2384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
36
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
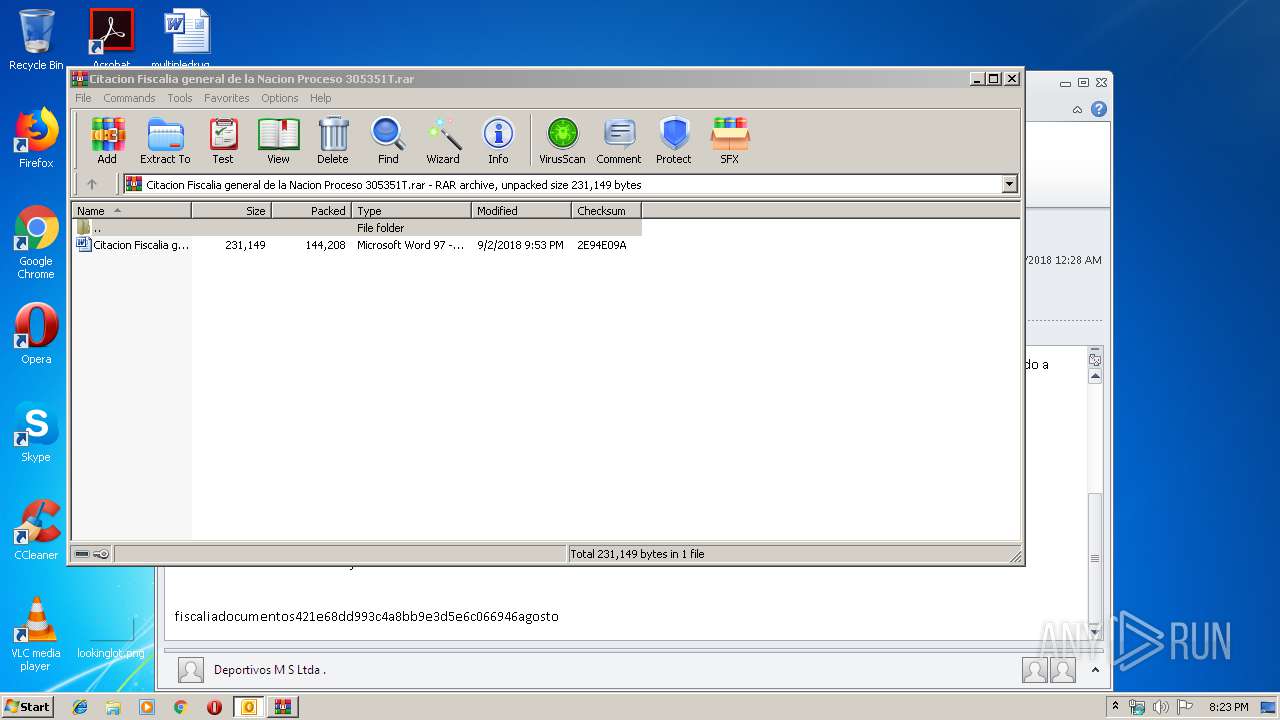
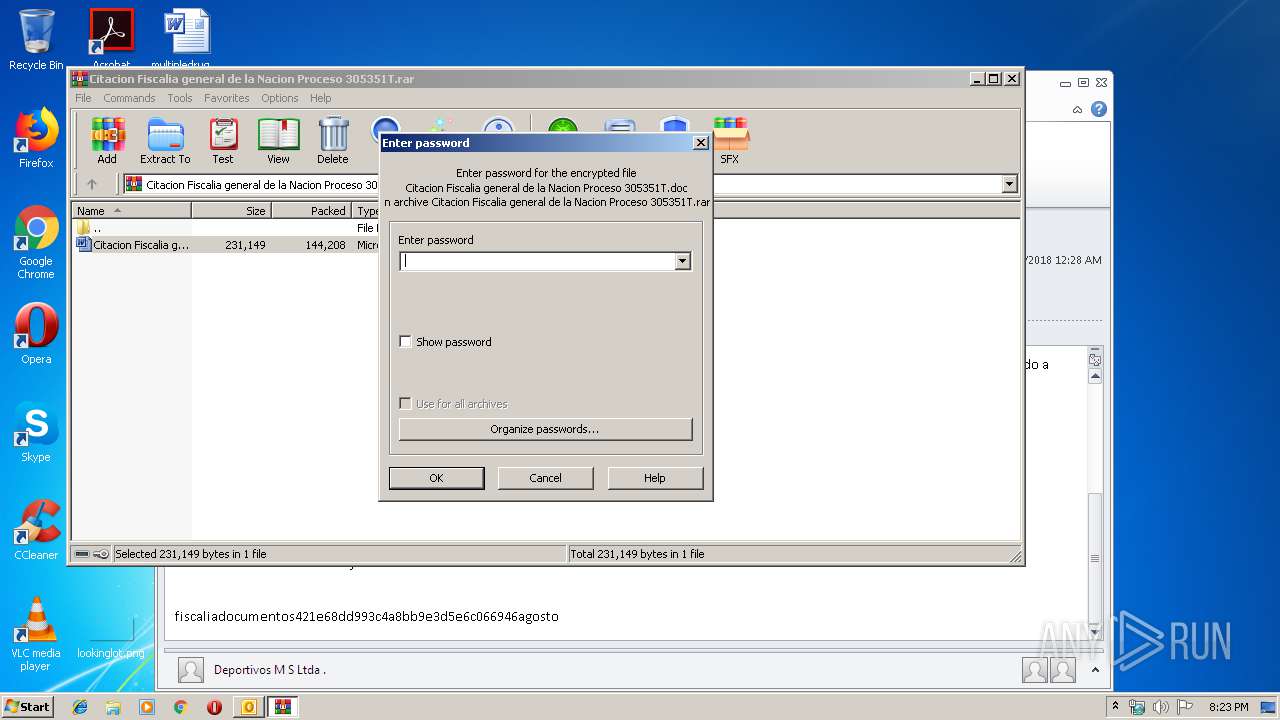
| 1732 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\QJAOCL81\Citacion Fiscalia general de la Nacion Proceso 305351T.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2360 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\RV IMPORTANTE LA FISCALIA GENERAL DE LA NACION LE HACE EL ULTIMO LLAMADO A INTERROGATORIO.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
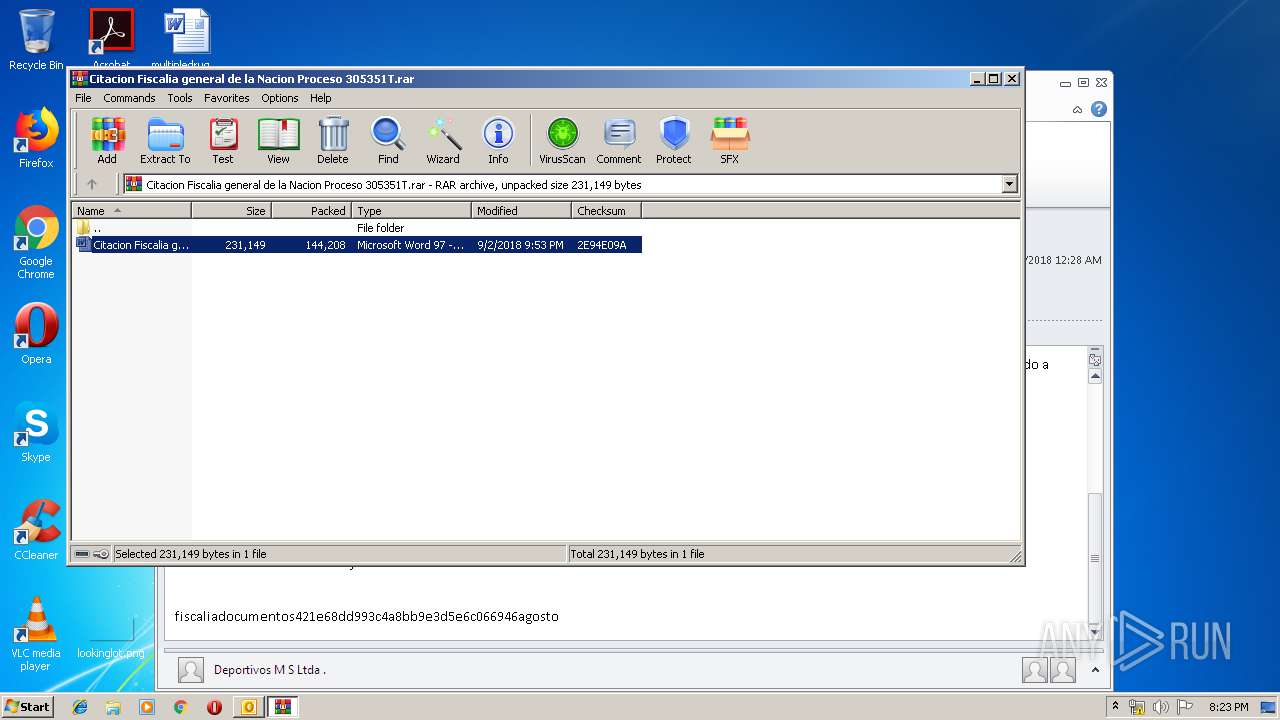
| 2384 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb1732.2496\Citacion Fiscalia general de la Nacion Proceso 305351T.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 178
Read events
1 744
Write events
414
Delete events
20
Modification events
| (PID) Process: | (2360) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2360) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2360) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | +b9 |
Value: 2B62390038090000010000000000000000000000 | |||
| (PID) Process: | (2360) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 380900003E1430F1D67ED50100000000 | |||
| (PID) Process: | (2360) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (2360) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220250880 | |||
| (PID) Process: | (2360) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (2360) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2360) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (2360) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1330184213 | |||
Executable files
0
Suspicious files
2
Text files
27
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2360 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRDFC.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2360 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\QJAOCL81\Citacion Fiscalia general de la Nacion Proceso 305351T (2).rar\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2384 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVREDDC.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2360 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\QJAOCL81\Citacion Fiscalia general de la Nacion Proceso 305351T.rar | compressed | |
MD5:— | SHA256:— | |||
| 2360 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 2360 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_ConversationPrefs_2_D468568D25EDD047BBBDB4B3C9472983.dat | xml | |
MD5:57F30B1BCA811C2FCB81F4C13F6A927B | SHA256:612BAD93621991CB09C347FF01EC600B46617247D5C041311FF459E247D8C2D3 | |||
| 1732 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb1732.2496\Citacion Fiscalia general de la Nacion Proceso 305351T.doc | text | |
MD5:— | SHA256:— | |||
| 2360 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 2360 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_ContactPrefs_2_6DE20B284DC2F64AB06224BE255CF3C6.dat | xml | |
MD5:BBCF400BD7AE536EB03054021D6A6398 | SHA256:383020065C1F31F4FB09F448599A6D5E532C390AF4E5B8AF0771FE17A23222AD | |||
| 2360 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\QJAOCL81\Citacion Fiscalia general de la Nacion Proceso 305351T (2).rar | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2360 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2360 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |