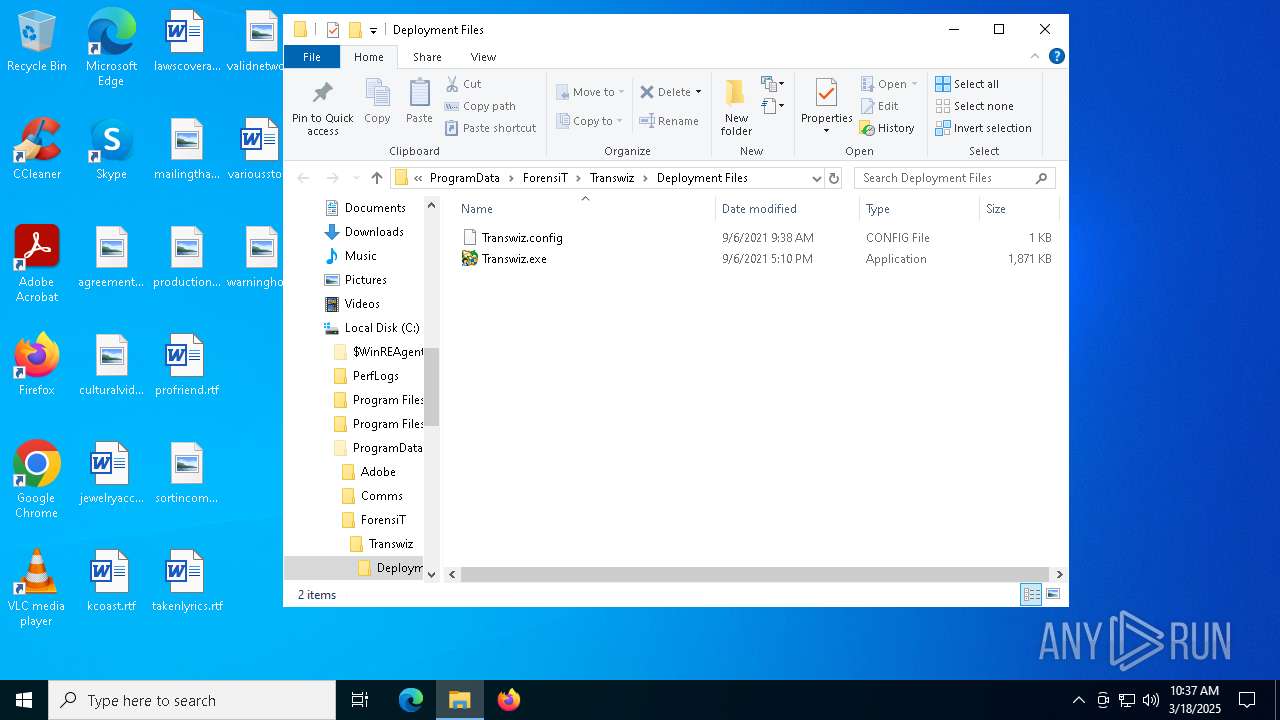
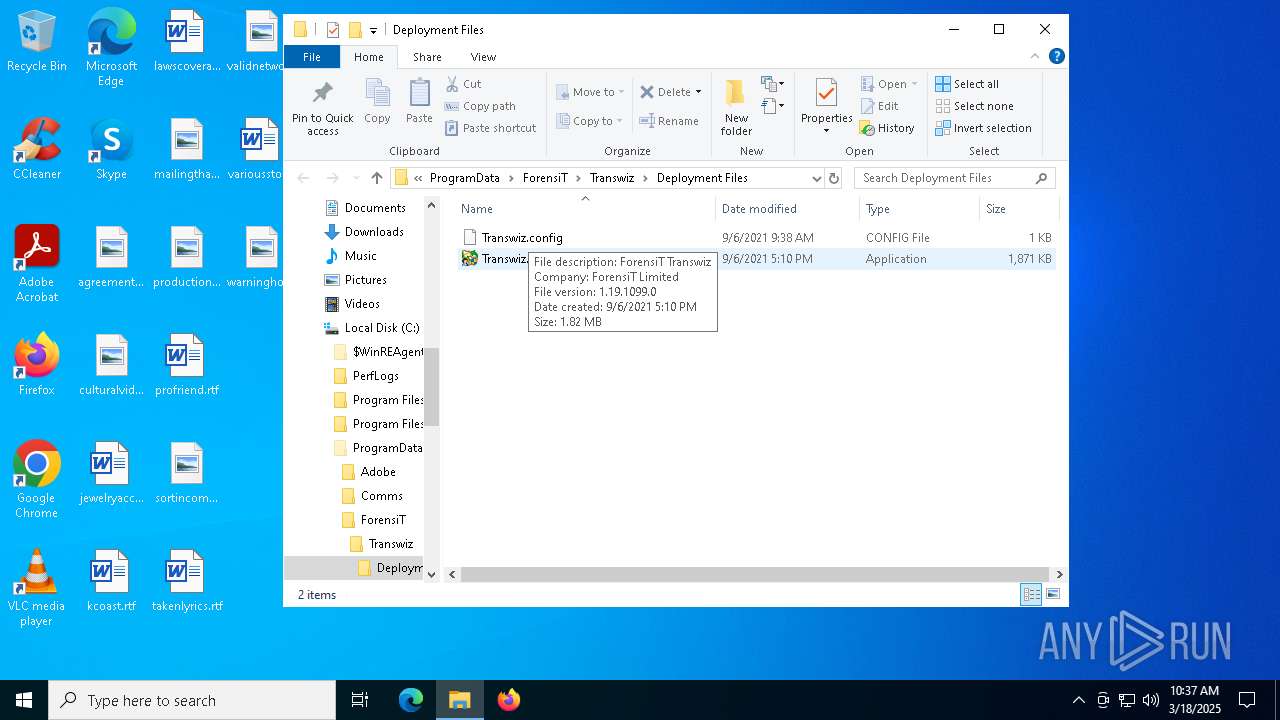
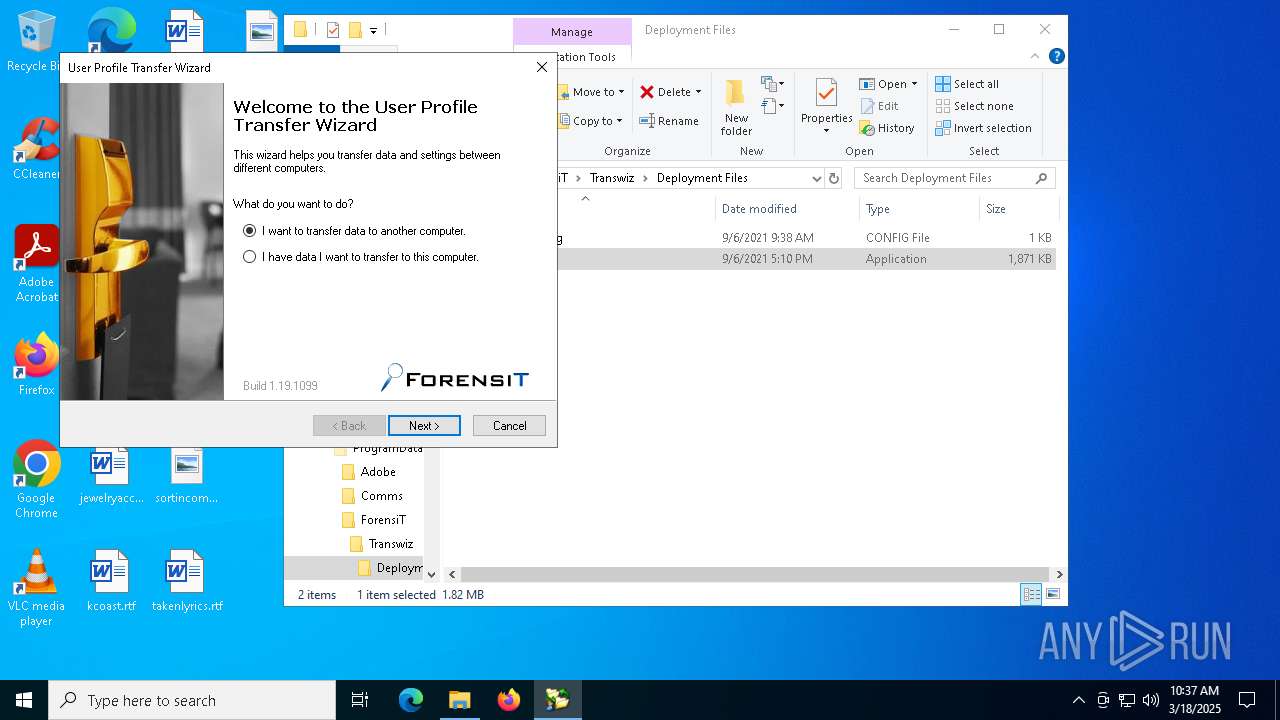
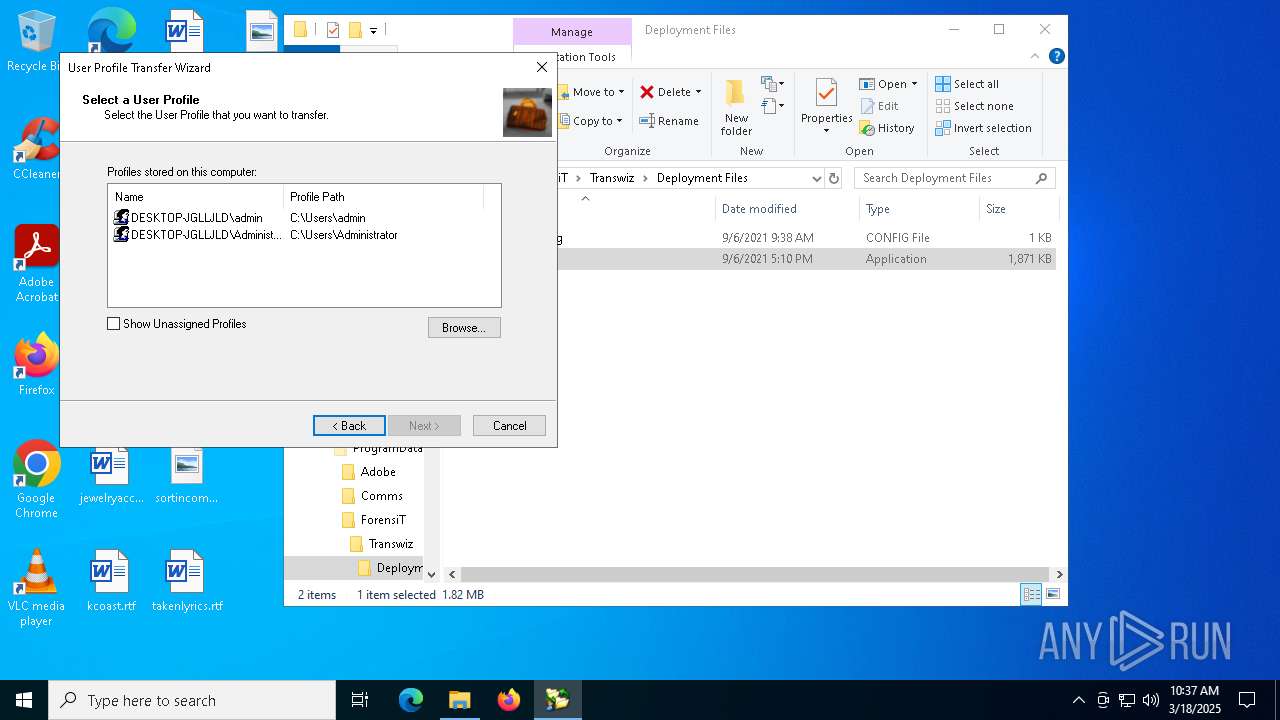
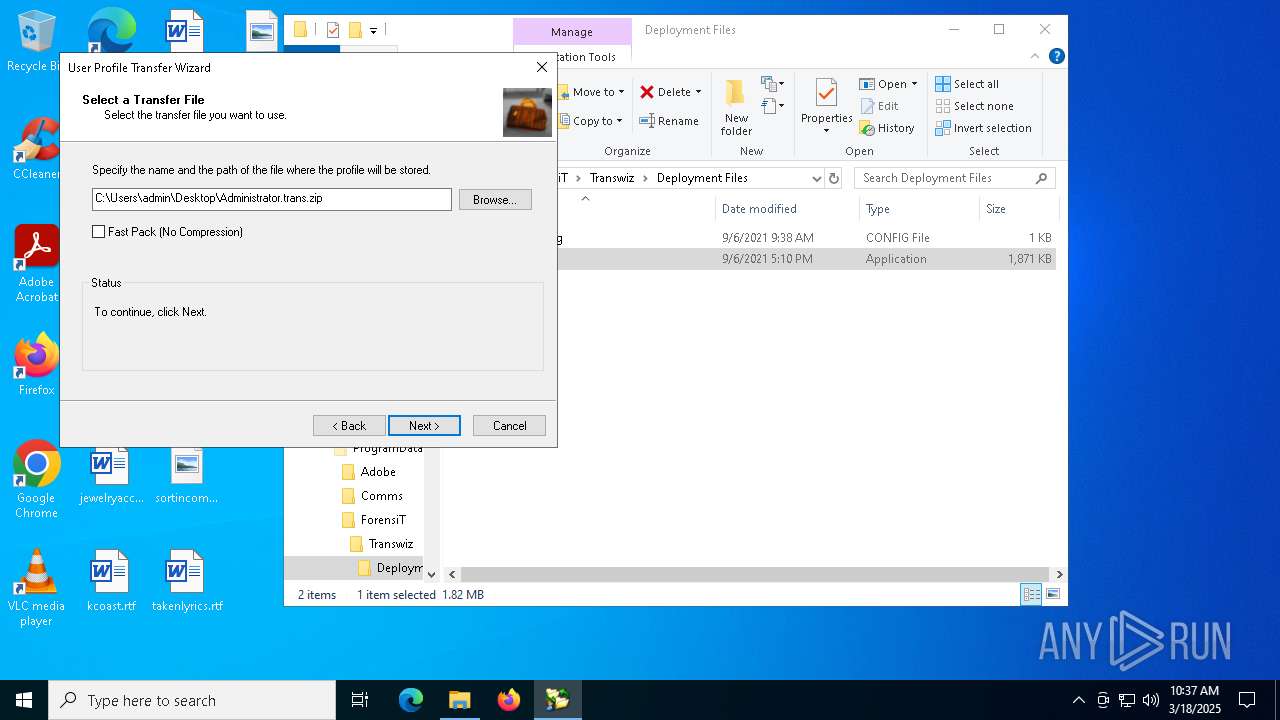
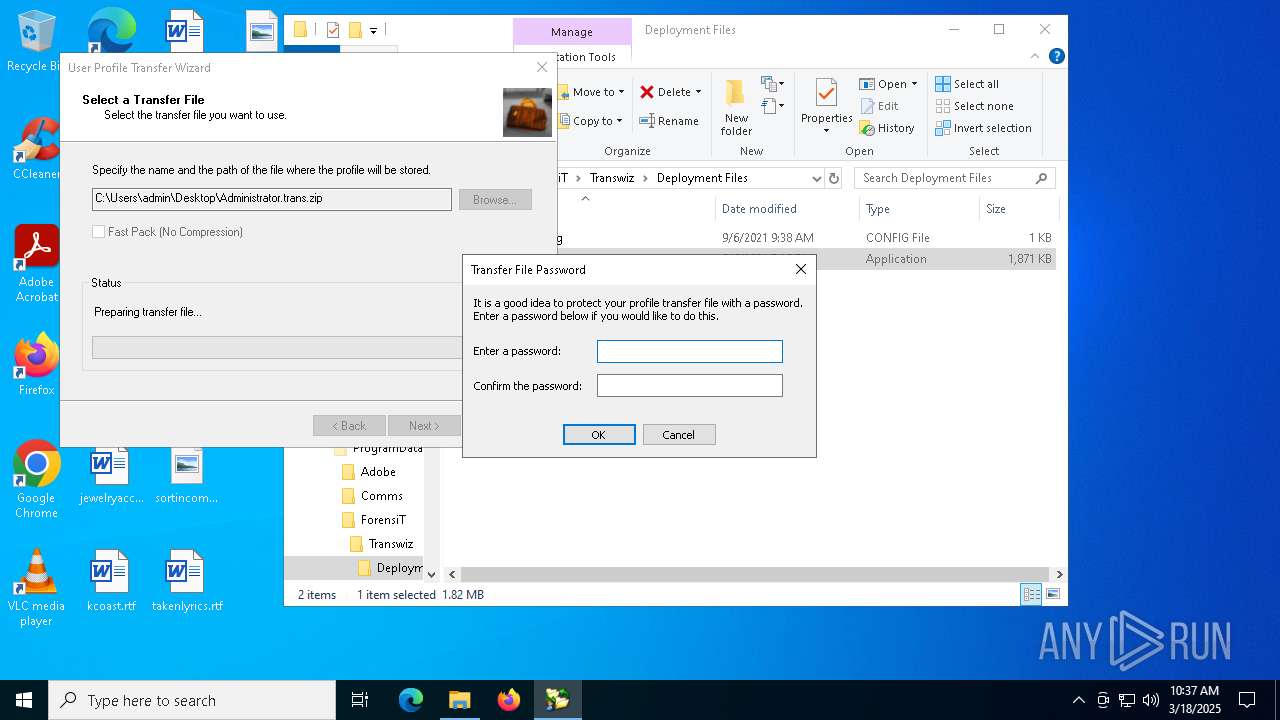
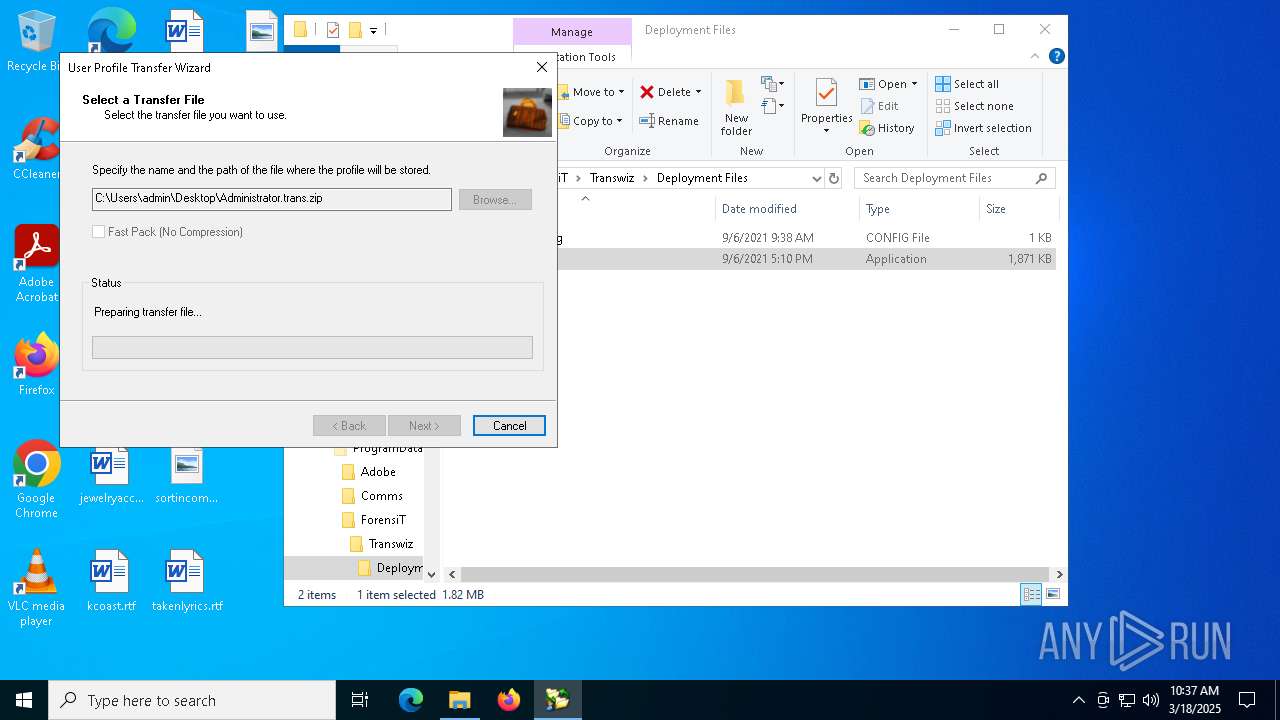
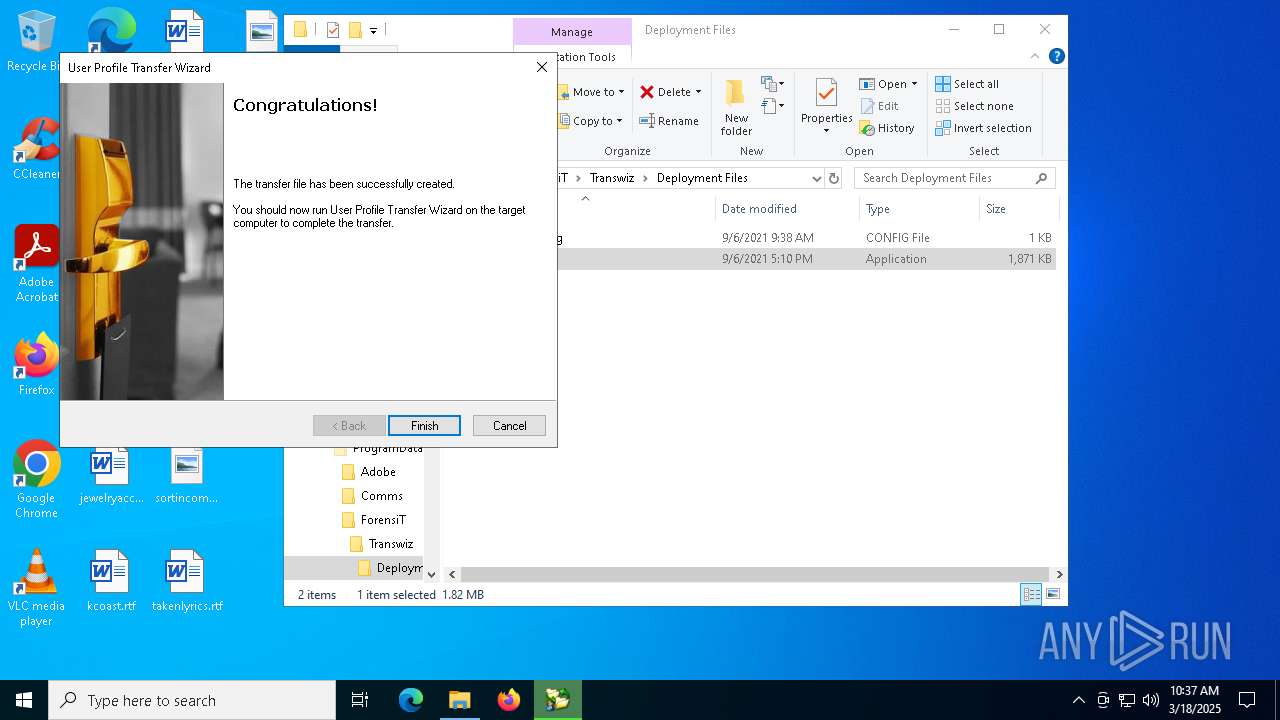
| File name: | Transwiz.msi |
| Full analysis: | https://app.any.run/tasks/27d794f7-fabf-4ef5-ab08-90423cf41ad3 |
| Verdict: | Malicious activity |
| Analysis date: | March 18, 2025, 10:36:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 14:06:51 2020, Security: 0, Code page: 1252, Revision Number: {B034C77C-C017-4926-8EB2-88DF6F1F336B}, Number of Words: 2, Subject: ForensiT Transwiz, Author: ForensiT, Name of Creating Application: Advanced Installer 18.6 build 099b4b9a, Template: ;2057, Comments: This installer database contains the logic and data required to install ForensiT Transwiz., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | CF1DD0006C422C2C85C46A6FE4506406 |
| SHA1: | DA48EC07CEA7407B6B2D38DBB54D2CD472BD7563 |
| SHA256: | 511C2C0908883BC9D05295E5145B767F2633461C93A31D1CB8D765EE09CDD801 |
| SSDEEP: | 49152:fx3AY5aeGDcQ8KmLVR97uAHSvVPcAANEoW7SAmEzkGl7KMGzu7dhlwe50Qe2K:GYTGDP8KmHHSVAvW7SAhxQMG67Zwe6rZ |
MALICIOUS
Executing a file with an untrusted certificate
- licfldr.exe (PID: 7836)
- Transwiz.exe (PID: 7952)
- Transwiz.exe (PID: 7924)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 7368)
- ForensiTAppxService.exe (PID: 8076)
Detects AdvancedInstaller (YARA)
- msiexec.exe (PID: 1300)
- msiexec.exe (PID: 7236)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7236)
Executable content was dropped or overwritten
- Transwiz.exe (PID: 7952)
Reads security settings of Internet Explorer
- Transwiz.exe (PID: 7952)
- licfldr.exe (PID: 7836)
There is functionality for taking screenshot (YARA)
- Transwiz.exe (PID: 7952)
INFO
Reads the software policy settings
- msiexec.exe (PID: 1300)
- BackgroundTransferHost.exe (PID: 7156)
- msiexec.exe (PID: 7236)
- slui.exe (PID: 8176)
Creates files or folders in the user directory
- msiexec.exe (PID: 1300)
- BackgroundTransferHost.exe (PID: 7156)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1300)
- BackgroundTransferHost.exe (PID: 7156)
- BackgroundTransferHost.exe (PID: 7224)
- BackgroundTransferHost.exe (PID: 1628)
- BackgroundTransferHost.exe (PID: 7932)
- BackgroundTransferHost.exe (PID: 7764)
- BackgroundTransferHost.exe (PID: 5400)
Reads the computer name
- msiexec.exe (PID: 7236)
- msiexec.exe (PID: 1676)
- ForensiTAppxService.exe (PID: 8076)
- Transwiz.exe (PID: 7952)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 7156)
Manages system restore points
- SrTasks.exe (PID: 4976)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7236)
- ForensiTAppxService.exe (PID: 8076)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7236)
Checks supported languages
- msiexec.exe (PID: 7236)
- msiexec.exe (PID: 5228)
- msiexec.exe (PID: 1676)
- Transwiz.exe (PID: 7952)
- ForensiTAppxService.exe (PID: 8076)
- licfldr.exe (PID: 7836)
The sample compiled with english language support
- msiexec.exe (PID: 7236)
- Transwiz.exe (PID: 7952)
Reads Environment values
- msiexec.exe (PID: 1676)
Manual execution by a user
- Transwiz.exe (PID: 7924)
- Transwiz.exe (PID: 7952)
Creates a software uninstall entry
- msiexec.exe (PID: 7236)
Creates files in the program directory
- Transwiz.exe (PID: 7952)
Create files in a temporary directory
- Transwiz.exe (PID: 7952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2020:09:18 14:06:51 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {B034C77C-C017-4926-8EB2-88DF6F1F336B} |
| Words: | 2 |
| Subject: | ForensiT Transwiz |
| Author: | ForensiT |
| LastModifiedBy: | - |
| Software: | Advanced Installer 18.6 build 099b4b9a |
| Template: | ;2057 |
| Comments: | This installer database contains the logic and data required to install ForensiT Transwiz. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
165
Monitored processes
23
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1300 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\Transwiz.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | C:\Windows\syswow64\MsiExec.exe -Embedding 52D012BC235AC79AEB5BF07DBC9B755D | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5228 | C:\Windows\syswow64\MsiExec.exe -Embedding 172791EE0D3E8D6FBB549F134480CE7E E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5392 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6480 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6676 | C:\WINDOWS\system32\profhlp.exe /1 | C:\Windows\System32\profhlp.exe | — | Transwiz.exe | |||||||||||
User: admin Company: ForensiT Integrity Level: HIGH Description: User Profile Migration Helper Exit code: 0 Version: 3.0.0.1 Modules
| |||||||||||||||
| 7156 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 192
Read events
17 655
Write events
507
Delete events
30
Modification events
| (PID) Process: | (7368) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000BEDA77A0F197DB01C81C00009C1D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7368) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000BEDA77A0F197DB01C81C0000941D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7368) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000BEDA77A0F197DB01C81C0000E81C0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7368) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000BEDA77A0F197DB01C81C0000E41C0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7368) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7368) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (7368) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7368) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (7368) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7368) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
Executable files
14
Suspicious files
35
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7156 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\ae3481f9-b47e-48d4-a69c-3ab9cb126a53.down_data | — | |
MD5:— | SHA256:— | |||
| 7236 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1300 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\ECF3006D44DA211141391220EE5049F4 | binary | |
MD5:8A217B5124219DD201A733E9BE9EB450 | SHA256:D5689259641845691AB0D283987E29D1D5875A275ACE6B6C2E090DC70A3BAFFA | |||
| 7156 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\2a0e81d9-f5de-4034-847e-a550a6e956ba.820a2a0c-d13c-4063-9b12-955bb7aa8460.down_meta | binary | |
MD5:E7D61AE697E79E0652B5DDB3CE7821B9 | SHA256:FDBA78C6E7100A5B7237C1BFD0ED63BBE71B821E391CA37217A5636C106EBF46 | |||
| 1300 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C46E7B0F942663A1EDC8D9D6D7869173_6043FC604A395E1485AF7AC16D16B7CE | binary | |
MD5:5BFA51F3A417B98E7443ECA90FC94703 | SHA256:BEBE2853A3485D1C2E5C5BE4249183E0DDAFF9F87DE71652371700A89D937128 | |||
| 1300 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EA618097E393409AFA316F0F87E2C202_3449438255B67E4D6417B4BB1457ED70 | binary | |
MD5:98C38EA06D3B6446C273A47379C2301B | SHA256:856BE607A1948D291A3A213AE9F996517D4E9228C538D7E769F36A59B4DF6339 | |||
| 7236 | msiexec.exe | C:\Windows\Installer\MSI2692.tmp | executable | |
MD5:36E2EDBDE4F98A27F31FEF1932D51E95 | SHA256:D9A307D175C72EA0922296F0686AB5A2A72F67E3C8C848E6623CB36AEADDF2EF | |||
| 7236 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{76d791c6-056c-48f6-a69f-3af99878a94e}_OnDiskSnapshotProp | binary | |
MD5:4F565AD348546E2A2FC1A7F8272547E7 | SHA256:5C355E56E41EAFCE700F034852F83253602DB82D0A893D26A2DB478A100D37C7 | |||
| 7236 | msiexec.exe | C:\Windows\Installer\MSI26D1.tmp | executable | |
MD5:36E2EDBDE4F98A27F31FEF1932D51E95 | SHA256:D9A307D175C72EA0922296F0686AB5A2A72F67E3C8C848E6623CB36AEADDF2EF | |||
| 7236 | msiexec.exe | C:\Windows\Installer\MSI2652.tmp | executable | |
MD5:36E2EDBDE4F98A27F31FEF1932D51E95 | SHA256:D9A307D175C72EA0922296F0686AB5A2A72F67E3C8C848E6623CB36AEADDF2EF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
38
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1300 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://sv.symcb.com/sv.crl | unknown | — | — | whitelisted |
7332 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7156 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1348 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1348 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1300 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1300 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | — | — | whitelisted |
1300 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEBfo4xpaWxi9x5juxabCTx8%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1300 | msiexec.exe | 2.23.79.3:80 | s2.symcb.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7332 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
s2.symcb.com |
| whitelisted |
s1.symcb.com |
| whitelisted |
sv.symcd.com |
| whitelisted |
sv.symcb.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |