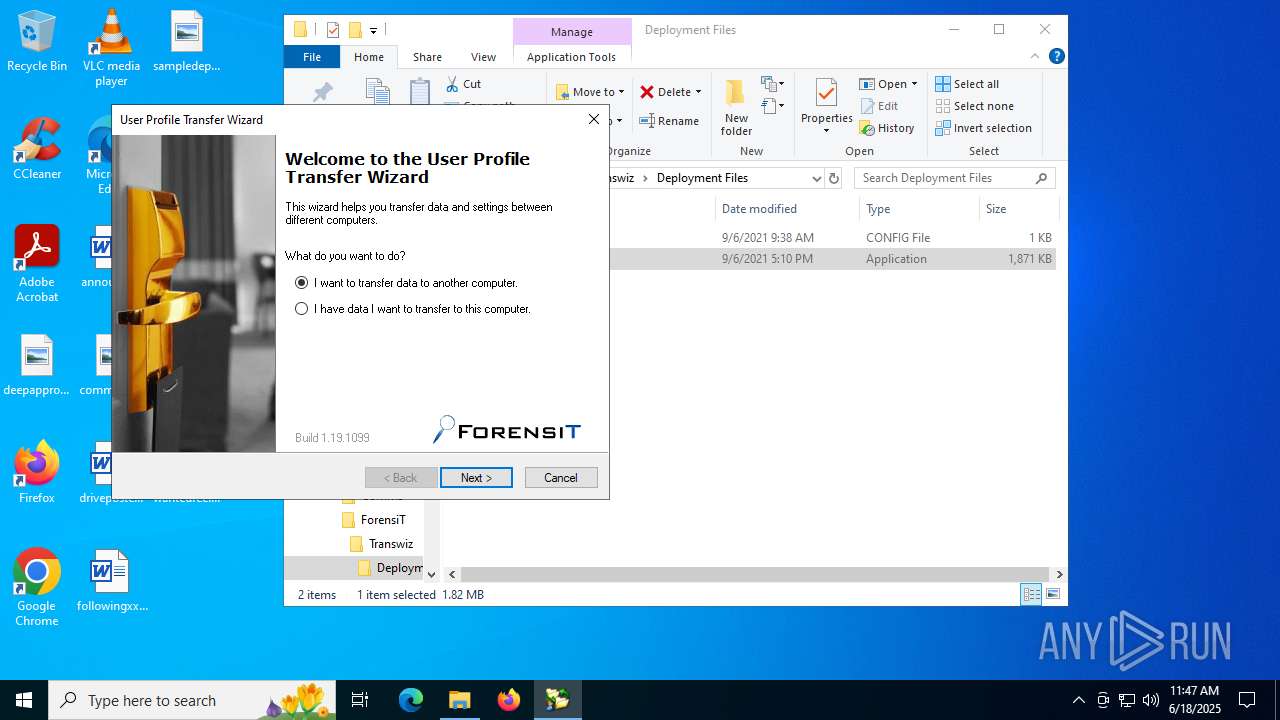
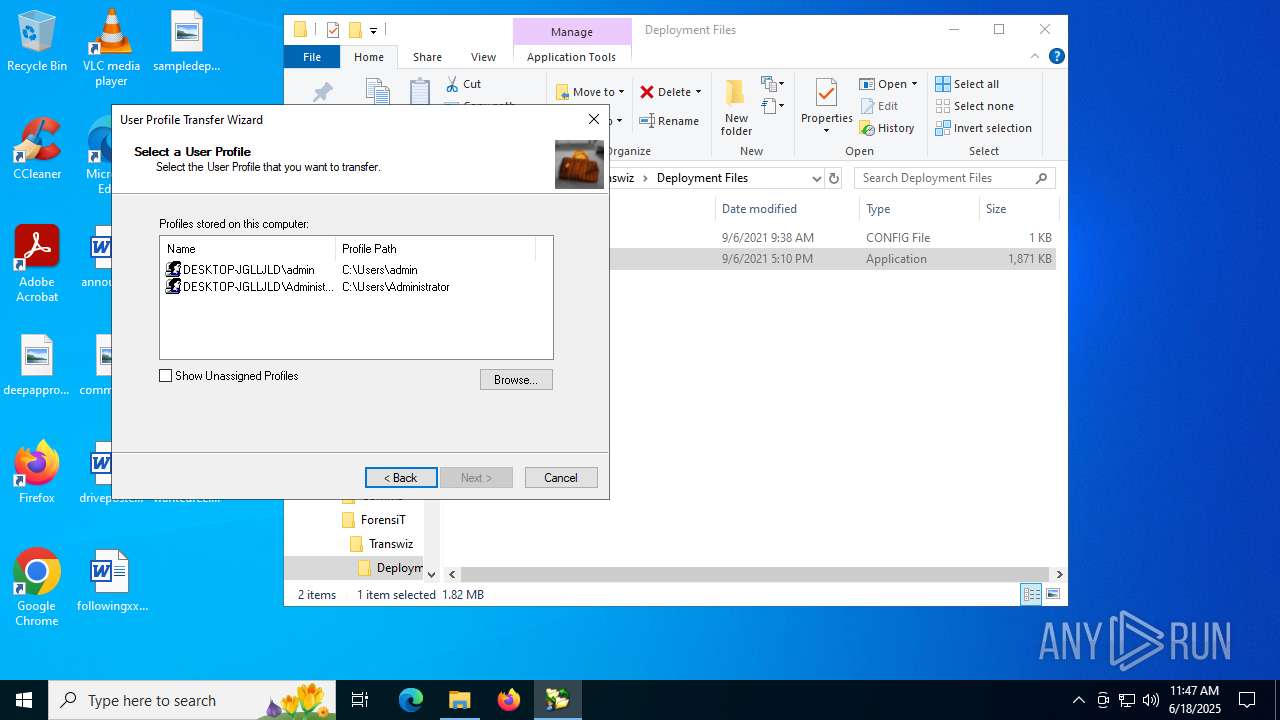
| File name: | Transwiz.msi |
| Full analysis: | https://app.any.run/tasks/119261d5-3489-45ed-a0e1-336ab2ce6dd7 |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2025, 11:46:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 14:06:51 2020, Security: 0, Code page: 1252, Revision Number: {B034C77C-C017-4926-8EB2-88DF6F1F336B}, Number of Words: 2, Subject: ForensiT Transwiz, Author: ForensiT, Name of Creating Application: Advanced Installer 18.6 build 099b4b9a, Template: ;2057, Comments: This installer database contains the logic and data required to install ForensiT Transwiz., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | CF1DD0006C422C2C85C46A6FE4506406 |
| SHA1: | DA48EC07CEA7407B6B2D38DBB54D2CD472BD7563 |
| SHA256: | 511C2C0908883BC9D05295E5145B767F2633461C93A31D1CB8D765EE09CDD801 |
| SSDEEP: | 49152:fx3AY5aeGDcQ8KmLVR97uAHSvVPcAANEoW7SAmEzkGl7KMGzu7dhlwe50Qe2K:GYTGDP8KmHHSVAvW7SAhxQMG67Zwe6rZ |
MALICIOUS
Executing a file with an untrusted certificate
- licfldr.exe (PID: 4920)
- Transwiz.exe (PID: 5528)
- Transwiz.exe (PID: 6704)
Changes the autorun value in the registry
- Transwiz.exe (PID: 6704)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 1944)
- ForensiTAppxService.exe (PID: 7008)
Detects AdvancedInstaller (YARA)
- msiexec.exe (PID: 4192)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6936)
Reads security settings of Internet Explorer
- licfldr.exe (PID: 4920)
There is functionality for taking screenshot (YARA)
- Transwiz.exe (PID: 6704)
Executable content was dropped or overwritten
- Transwiz.exe (PID: 6704)
INFO
Reads the software policy settings
- msiexec.exe (PID: 4192)
- msiexec.exe (PID: 6936)
- slui.exe (PID: 5008)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 4192)
Reads the computer name
- msiexec.exe (PID: 6936)
- msiexec.exe (PID: 6796)
- licfldr.exe (PID: 4920)
- Transwiz.exe (PID: 6704)
- ForensiTAppxService.exe (PID: 7008)
- profhlp.exe (PID: 5340)
- msiexec.exe (PID: 2120)
Checks proxy server information
- msiexec.exe (PID: 4192)
- slui.exe (PID: 5008)
Checks supported languages
- msiexec.exe (PID: 6936)
- msiexec.exe (PID: 6796)
- msiexec.exe (PID: 2120)
- licfldr.exe (PID: 4920)
- Transwiz.exe (PID: 6704)
- ForensiTAppxService.exe (PID: 7008)
- profhlp.exe (PID: 5340)
Manages system restore points
- SrTasks.exe (PID: 2160)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6936)
- ForensiTAppxService.exe (PID: 7008)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6936)
Reads Environment values
- msiexec.exe (PID: 6796)
Creates a software uninstall entry
- msiexec.exe (PID: 6936)
Manual execution by a user
- Transwiz.exe (PID: 6704)
- Transwiz.exe (PID: 5528)
Creates files in the program directory
- Transwiz.exe (PID: 6704)
Launching a file from a Registry key
- Transwiz.exe (PID: 6704)
The sample compiled with english language support
- Transwiz.exe (PID: 6704)
- msiexec.exe (PID: 6936)
Create files in a temporary directory
- Transwiz.exe (PID: 6704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2020:09:18 14:06:51 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {B034C77C-C017-4926-8EB2-88DF6F1F336B} |
| Words: | 2 |
| Subject: | ForensiT Transwiz |
| Author: | ForensiT |
| LastModifiedBy: | - |
| Software: | Advanced Installer 18.6 build 099b4b9a |
| Template: | ;2057 |
| Comments: | This installer database contains the logic and data required to install ForensiT Transwiz. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
164
Monitored processes
14
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2120 | C:\Windows\syswow64\MsiExec.exe -Embedding FDDEA7B20A7FA91F2C46372D7B7FA700 E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2160 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4192 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\Transwiz.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4552 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | "C:\Program Files (x86)\ForensiT\ForensiT Transwiz\licfldr.exe" -tf | C:\Program Files (x86)\ForensiT\ForensiT Transwiz\licfldr.exe | — | msiexec.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5008 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5340 | C:\WINDOWS\system32\profhlp.exe /1 | C:\Windows\System32\profhlp.exe | Transwiz.exe | ||||||||||||
User: admin Company: ForensiT Integrity Level: HIGH Description: User Profile Migration Helper Exit code: 0 Version: 3.0.0.1 Modules
| |||||||||||||||
| 5528 | "C:\ProgramData\ForensiT\Transwiz\Deployment Files\Transwiz.exe" | C:\ProgramData\ForensiT\Transwiz\Deployment Files\Transwiz.exe | — | explorer.exe | |||||||||||
User: admin Company: ForensiT Limited Integrity Level: MEDIUM Description: ForensiT Transwiz Exit code: 3221226540 Version: 1.19.1099.0 Modules
| |||||||||||||||
Total events
11 196
Read events
10 756
Write events
413
Delete events
27
Modification events
| (PID) Process: | (6936) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000138BFFB646E0DB01181B0000D41A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6936) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000F3EE01B746E0DB01181B0000D41A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (1944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (1944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 480000000000000021805CB746E0DB01980700001C130000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (1944) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
14
Suspicious files
28
Text files
4
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6936 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4192 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C46E7B0F942663A1EDC8D9D6D7869173_6043FC604A395E1485AF7AC16D16B7CE | binary | |
MD5:5BFA51F3A417B98E7443ECA90FC94703 | SHA256:BEBE2853A3485D1C2E5C5BE4249183E0DDAFF9F87DE71652371700A89D937128 | |||
| 4192 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C46E7B0F942663A1EDC8D9D6D7869173_6043FC604A395E1485AF7AC16D16B7CE | binary | |
MD5:E1D2A8FA623E6F7F76B1B72324FCFC2F | SHA256:D8C1CA907CB3AF09312C851E403BB79FEA0B8B3266C0D62D170E051CDB67A505 | |||
| 4192 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\40C68D5626484A90937F0752C8B950AB | der | |
MD5:2AB172E9398A3F429D22A89DB10F024D | SHA256:4DFCA5F2F4907EFD537D7DB7D4A8B5D57A14B551EE62A0F4F3EF6B795C438262 | |||
| 4192 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\ECF3006D44DA211141391220EE5049F4 | binary | |
MD5:E08BB3D27D6599521B84183F5AE37818 | SHA256:81CCDB171C25621A366F433EA9C1ECBED60D407119271549FC8B8C5113E6387C | |||
| 4192 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EA618097E393409AFA316F0F87E2C202_3449438255B67E4D6417B4BB1457ED70 | binary | |
MD5:AA49BDF7BCFEE3791AAF8EC491023841 | SHA256:10250455C64319CC883BCBE276A33435E083A643C0A97486A1B18DF87A8E2712 | |||
| 6936 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:3713AD884732E3D4C5713F19CE98E85E | SHA256:48FC79A0755CAD8B61C2DDFF94FFDACB339C6C42174C0AD902D53FC3DEB1166F | |||
| 4192 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EA618097E393409AFA316F0F87E2C202_3449438255B67E4D6417B4BB1457ED70 | binary | |
MD5:5BFA51F3A417B98E7443ECA90FC94703 | SHA256:BEBE2853A3485D1C2E5C5BE4249183E0DDAFF9F87DE71652371700A89D937128 | |||
| 4192 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\40C68D5626484A90937F0752C8B950AB | binary | |
MD5:9E9E72FE66679655916C55EACD626D27 | SHA256:C73B33F7F8E34B9A0ED8E4A0278586E54DDC146CDFDD49FBC9C8B6EE50158894 | |||
| 6936 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{21a96398-1f47-4f85-8195-d4a5126ee3f1}_OnDiskSnapshotProp | binary | |
MD5:3713AD884732E3D4C5713F19CE98E85E | SHA256:48FC79A0755CAD8B61C2DDFF94FFDACB339C6C42174C0AD902D53FC3DEB1166F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
42
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4192 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | — | — | whitelisted |
4192 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | — | — | whitelisted |
4192 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://s1.symcb.com/pca3-g5.crl | unknown | — | — | whitelisted |
4192 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEBfo4xpaWxi9x5juxabCTx8%3D | unknown | — | — | whitelisted |
4192 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEBfo4xpaWxi9x5juxabCTx8%3D | unknown | — | — | whitelisted |
4192 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://sv.symcb.com/sv.crl | unknown | — | — | whitelisted |
2288 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6900 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7052 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4192 | msiexec.exe | 2.23.79.3:80 | s2.symcb.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2288 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2288 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
s2.symcb.com |
| whitelisted |
s1.symcb.com |
| whitelisted |
sv.symcd.com |
| whitelisted |
sv.symcb.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Transwiz.exe | Starting service with SERVICE_ALL_ACCESS |
Transwiz.exe | Service has started |
profhlp.exe | VSS: Waiting on Backup Complete |
Transwiz.exe | The pipe has been ended.
|
profhlp.exe | VSS: Backup Complete. |