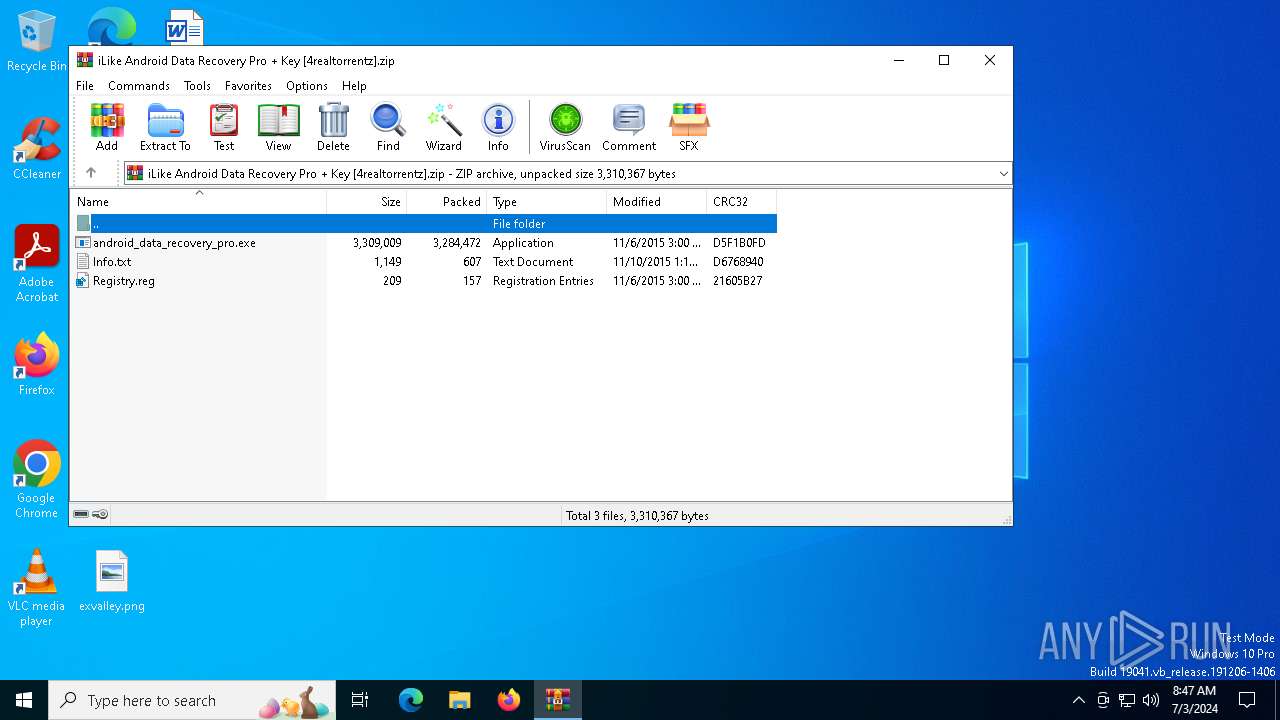
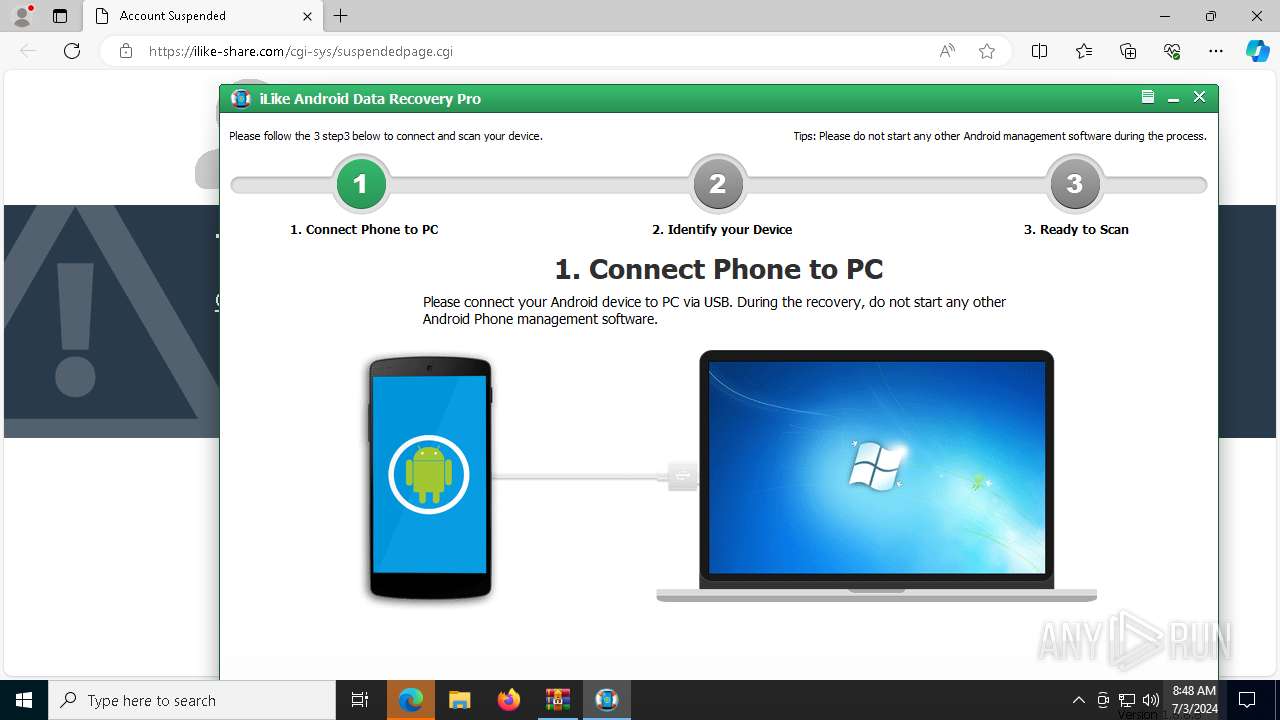
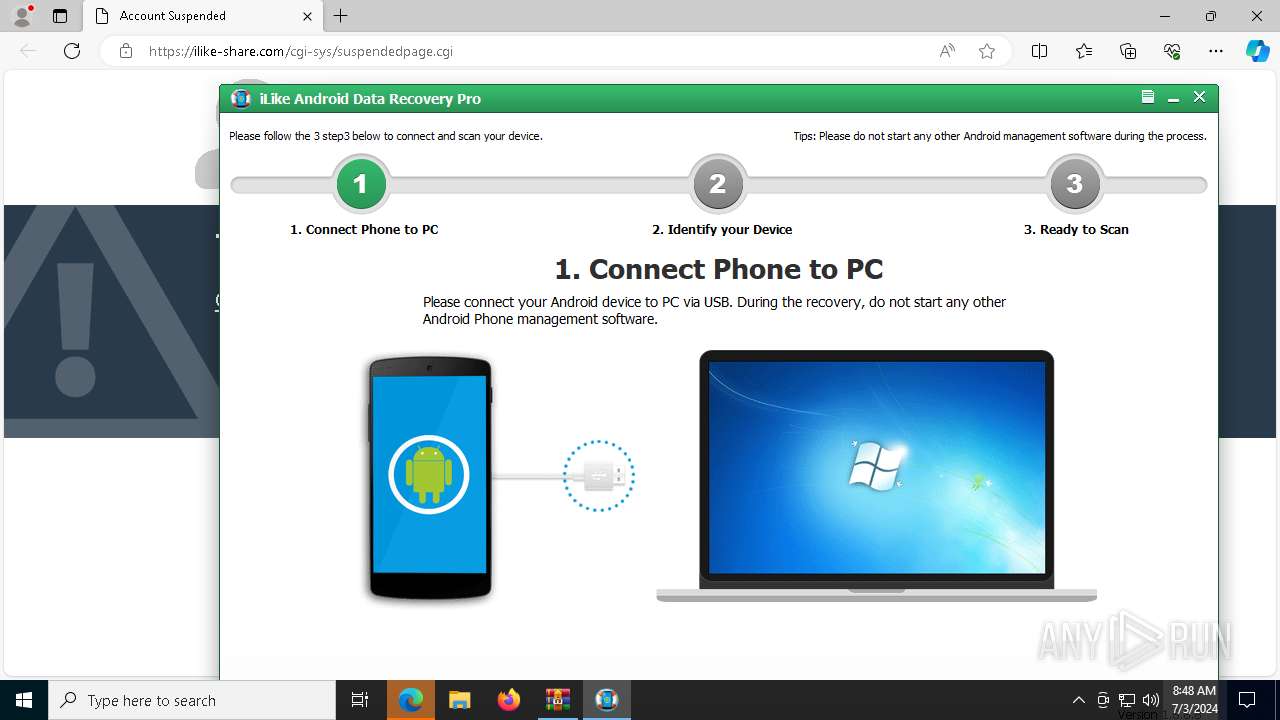
| File name: | iLike Android Data Recovery Pro + Key [4realtorrentz].zip |
| Full analysis: | https://app.any.run/tasks/f7ef0724-68c8-49fc-903d-712109600b5a |
| Verdict: | Malicious activity |
| Analysis date: | July 03, 2024, 08:47:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | FAEF981B52A3AC4F7EAE3D8B18FE9EEE |
| SHA1: | B09681E0D4768484B4F48E9275D25437B95F4D5A |
| SHA256: | 5118D864A91390CFD579AE7D3AAB17B59BFCE6511425A461589F24AF47DA5B0F |
| SSDEEP: | 98304:7qSnfYc/vQCJHwi68l4WoaLLOKXp1VjBqAl7YZakISWFvlSxmxFK0wfi2PCzc8PK:PyV88iSacrCm |
MALICIOUS
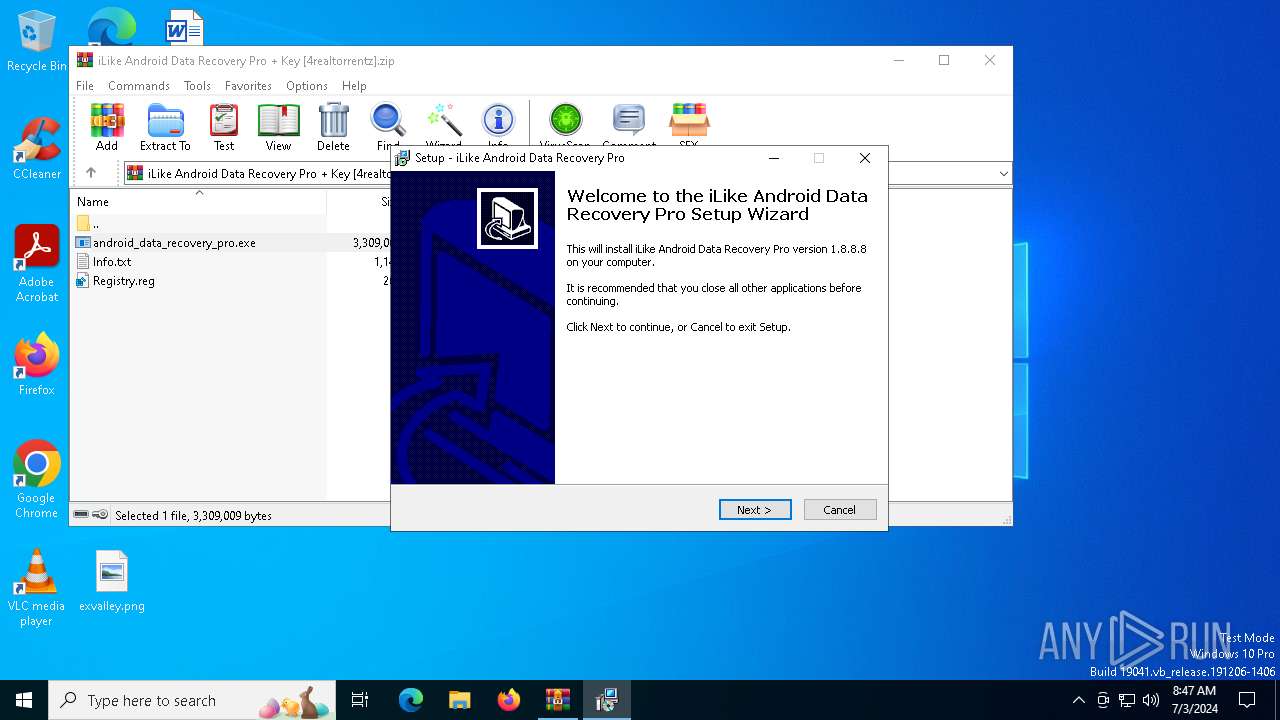
Drops the executable file immediately after the start
- android_data_recovery_pro.exe (PID: 5524)
- android_data_recovery_pro.tmp (PID: 4220)
- WinRAR.exe (PID: 1332)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1332)
- android_data_recovery_pro.tmp (PID: 4220)
Reads the Windows owner or organization settings
- android_data_recovery_pro.tmp (PID: 4220)
The process drops C-runtime libraries
- android_data_recovery_pro.tmp (PID: 4220)
Executable content was dropped or overwritten
- android_data_recovery_pro.tmp (PID: 4220)
- android_data_recovery_pro.exe (PID: 5524)
Creates/Modifies COM task schedule object
- iLike Android Data Recovery Pro.exe (PID: 3688)
Process drops legitimate windows executable
- android_data_recovery_pro.tmp (PID: 4220)
Application launched itself
- adb.exe (PID: 6260)
INFO
Checks supported languages
- android_data_recovery_pro.exe (PID: 5524)
- android_data_recovery_pro.tmp (PID: 4220)
- iLike Android Data Recovery Pro.exe (PID: 3688)
- adb.exe (PID: 6260)
- adb.exe (PID: 6968)
- identity_helper.exe (PID: 6388)
- adb.exe (PID: 4220)
- adb.exe (PID: 6904)
- adb.exe (PID: 6284)
- adb.exe (PID: 6436)
- adb.exe (PID: 6156)
- adb.exe (PID: 6284)
- adb.exe (PID: 4220)
- adb.exe (PID: 4220)
- adb.exe (PID: 6436)
- adb.exe (PID: 6352)
- adb.exe (PID: 4796)
- adb.exe (PID: 6436)
- adb.exe (PID: 6320)
- adb.exe (PID: 6336)
- adb.exe (PID: 6352)
- adb.exe (PID: 6352)
- adb.exe (PID: 6352)
- adb.exe (PID: 6400)
- adb.exe (PID: 6400)
- adb.exe (PID: 5480)
- adb.exe (PID: 4684)
- adb.exe (PID: 6760)
- adb.exe (PID: 4684)
- adb.exe (PID: 5524)
- adb.exe (PID: 6316)
- adb.exe (PID: 6764)
- adb.exe (PID: 5480)
- adb.exe (PID: 4164)
- adb.exe (PID: 1292)
- adb.exe (PID: 6772)
- adb.exe (PID: 4164)
- adb.exe (PID: 6352)
- adb.exe (PID: 6764)
- adb.exe (PID: 6384)
- adb.exe (PID: 1824)
- adb.exe (PID: 6400)
- adb.exe (PID: 5456)
- adb.exe (PID: 1320)
- adb.exe (PID: 6156)
- adb.exe (PID: 5184)
- adb.exe (PID: 3680)
- adb.exe (PID: 3516)
- adb.exe (PID: 6120)
- adb.exe (PID: 1828)
- adb.exe (PID: 916)
- adb.exe (PID: 1964)
- adb.exe (PID: 4116)
- adb.exe (PID: 4264)
- adb.exe (PID: 5652)
- adb.exe (PID: 6904)
- adb.exe (PID: 936)
- adb.exe (PID: 7136)
- adb.exe (PID: 3848)
- adb.exe (PID: 1320)
- adb.exe (PID: 6436)
- adb.exe (PID: 3596)
- adb.exe (PID: 6332)
- adb.exe (PID: 5288)
- adb.exe (PID: 6152)
- adb.exe (PID: 6284)
- adb.exe (PID: 3828)
- adb.exe (PID: 1660)
- adb.exe (PID: 1092)
- adb.exe (PID: 2520)
- adb.exe (PID: 6320)
- adb.exe (PID: 544)
- adb.exe (PID: 6156)
- adb.exe (PID: 7136)
- adb.exe (PID: 2896)
- adb.exe (PID: 3188)
- adb.exe (PID: 4488)
- adb.exe (PID: 4000)
- adb.exe (PID: 5316)
- adb.exe (PID: 5816)
- adb.exe (PID: 5456)
- adb.exe (PID: 4796)
- adb.exe (PID: 6152)
- adb.exe (PID: 4796)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1332)
Create files in a temporary directory
- android_data_recovery_pro.exe (PID: 5524)
- android_data_recovery_pro.tmp (PID: 4220)
- adb.exe (PID: 6968)
Creates a software uninstall entry
- android_data_recovery_pro.tmp (PID: 4220)
Reads the computer name
- android_data_recovery_pro.tmp (PID: 4220)
- iLike Android Data Recovery Pro.exe (PID: 3688)
- adb.exe (PID: 6968)
- identity_helper.exe (PID: 6388)
Creates files in the program directory
- android_data_recovery_pro.tmp (PID: 4220)
Reads Microsoft Office registry keys
- android_data_recovery_pro.tmp (PID: 4220)
- msedge.exe (PID: 1276)
- msedge.exe (PID: 6408)
Application launched itself
- msedge.exe (PID: 1276)
- msedge.exe (PID: 6408)
Manual execution by a user
- msedge.exe (PID: 6408)
Reads the machine GUID from the registry
- adb.exe (PID: 6968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2015:11:06 11:00:24 |
| ZipCRC: | 0xd5f1b0fd |
| ZipCompressedSize: | 3284472 |
| ZipUncompressedSize: | 3309009 |
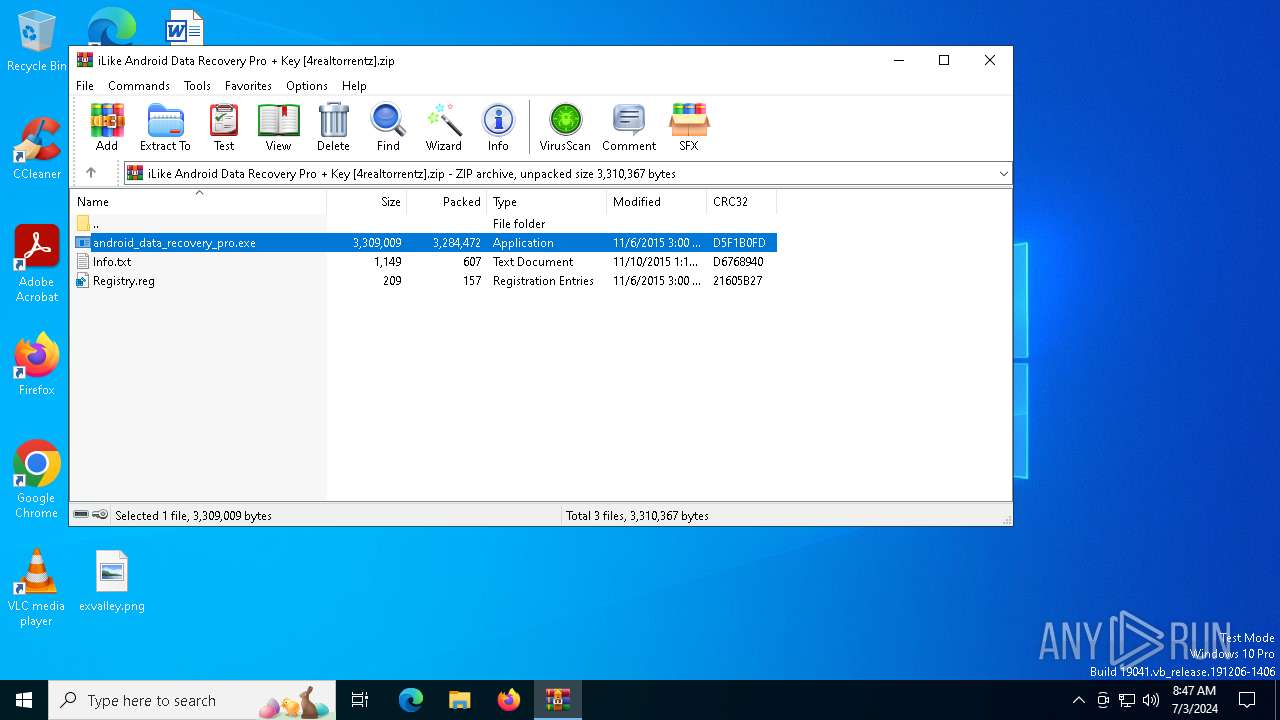
| ZipFileName: | android_data_recovery_pro.exe |
Total processes
398
Monitored processes
258
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 476 | "C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\Adb.exe" shell | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\adb.exe | — | iLike Android Data Recovery Pro.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 | |||||||||||||||
| 524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 544 | "C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\Adb.exe" shell | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\adb.exe | — | iLike Android Data Recovery Pro.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 544 | "C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\Adb.exe" shell | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\adb.exe | — | iLike Android Data Recovery Pro.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 | |||||||||||||||
| 916 | "C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\Adb.exe" shell | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\adb.exe | — | iLike Android Data Recovery Pro.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 936 | "C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\Adb.exe" shell | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\adb.exe | — | iLike Android Data Recovery Pro.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1016 | "C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\Adb.exe" shell | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\adb.exe | — | iLike Android Data Recovery Pro.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 | |||||||||||||||
| 1092 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 956
Read events
36 806
Write events
141
Delete events
9
Modification events
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\iLike Android Data Recovery Pro + Key [4realtorrentz].zip | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\regedit.exe,-309 |
Value: Registration Entries | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
23
Suspicious files
56
Text files
63
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4220 | android_data_recovery_pro.tmp | C:\Users\admin\AppData\Local\Temp\is-508A3.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 4220 | android_data_recovery_pro.tmp | C:\Program Files (x86)\iLike Android Data Recovery Pro\is-DM0AL.tmp | executable | |
MD5:CB07A77EAB6BA27940381A5AF34BF032 | SHA256:3A93F454757226751FEBE459015FD762C8E085EE79014E093E6F723DD80D7488 | |||
| 4220 | android_data_recovery_pro.tmp | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\is-VLVMN.tmp | executable | |
MD5:5EEE0CAD50404BFC8F9DB899EEDB144A | SHA256:3113F3F431EA76D78ABC5867A0214822C1C3445F23B57030F233BB6FF3DB1AB9 | |||
| 4220 | android_data_recovery_pro.tmp | C:\Users\admin\AppData\Local\Temp\is-508A3.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 4220 | android_data_recovery_pro.tmp | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\is-V791A.tmp | executable | |
MD5:47A6EE3F186B2C2F5057028906BAC0C6 | SHA256:14A51482AA003DB79A400F4B15C158397FE6D57EE6606B3D633FA431A7BFDF4B | |||
| 4220 | android_data_recovery_pro.tmp | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\AdbWinApi.dll | executable | |
MD5:47A6EE3F186B2C2F5057028906BAC0C6 | SHA256:14A51482AA003DB79A400F4B15C158397FE6D57EE6606B3D633FA431A7BFDF4B | |||
| 4220 | android_data_recovery_pro.tmp | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\AndroidDR | binary | |
MD5:88538D3AAD710DEE40BD28ABEEF18FF5 | SHA256:0A37D8D11AEE3B0B59B3516C703357D7823FB8089AF1A418553DA1306D52CF13 | |||
| 4220 | android_data_recovery_pro.tmp | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\is-NATTH.tmp | executable | |
MD5:5F23F2F936BDFAC90BB0A4970AD365CF | SHA256:041C6859BB4FC78D3A903DD901298CD1ECFB75B6BE0646B74954CD722280A407 | |||
| 4220 | android_data_recovery_pro.tmp | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\adb.exe | executable | |
MD5:5EEE0CAD50404BFC8F9DB899EEDB144A | SHA256:3113F3F431EA76D78ABC5867A0214822C1C3445F23B57030F233BB6FF3DB1AB9 | |||
| 4220 | android_data_recovery_pro.tmp | C:\Program Files (x86)\iLike Android Data Recovery Pro\bin\AdbWinUsbApi.dll | executable | |
MD5:5F23F2F936BDFAC90BB0A4970AD365CF | SHA256:041C6859BB4FC78D3A903DD901298CD1ECFB75B6BE0646B74954CD722280A407 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
71
DNS requests
48
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2536 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
6332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
6332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
5832 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2536 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2536 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3172 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1436 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2536 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2536 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2536 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
2536 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
r.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |