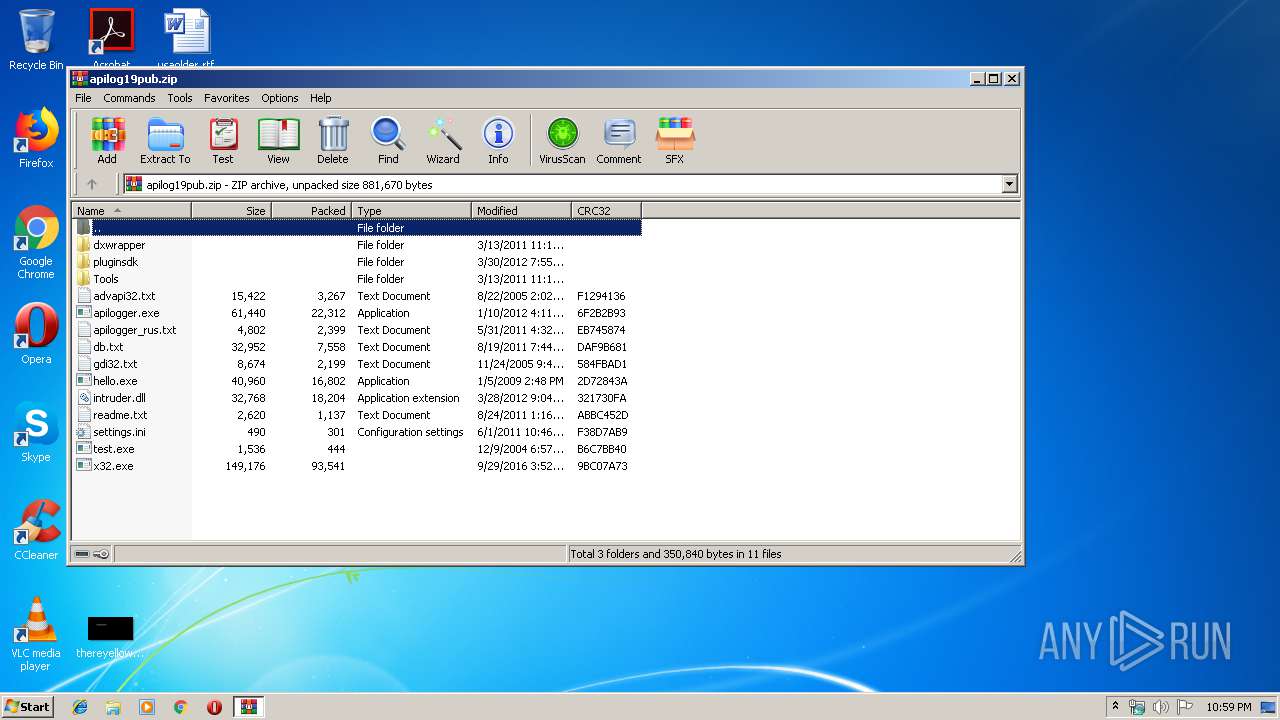
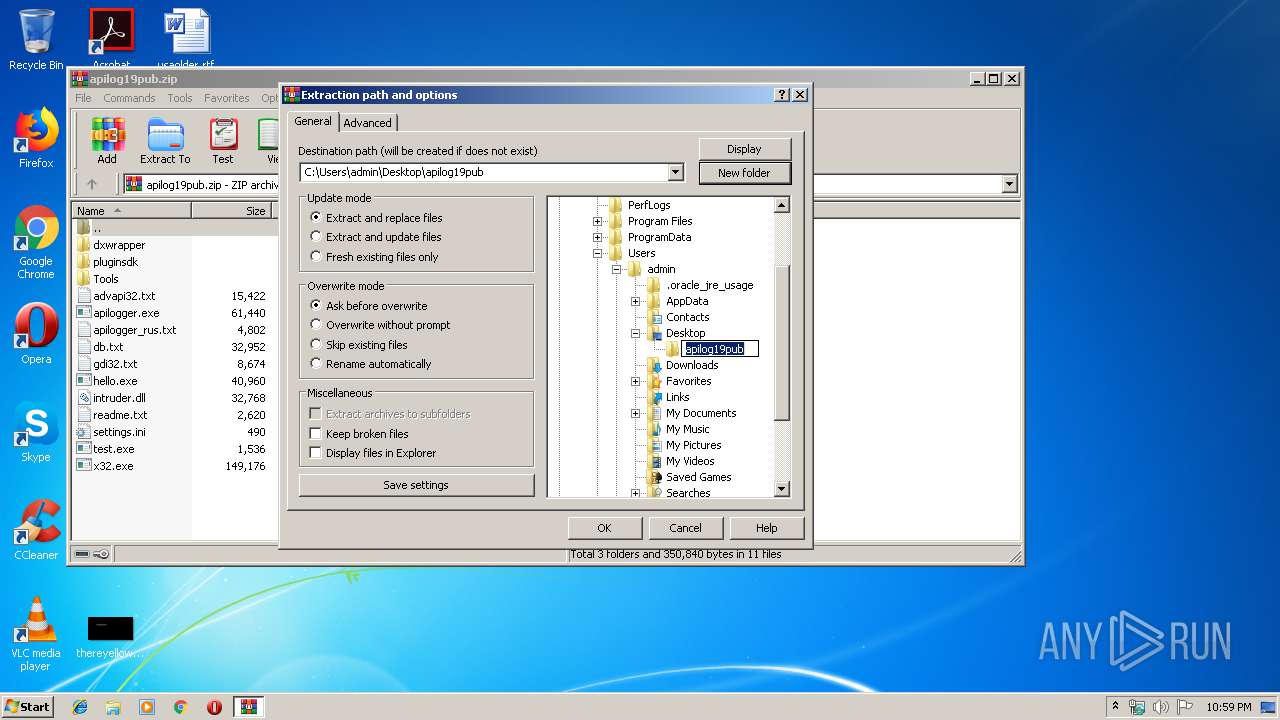
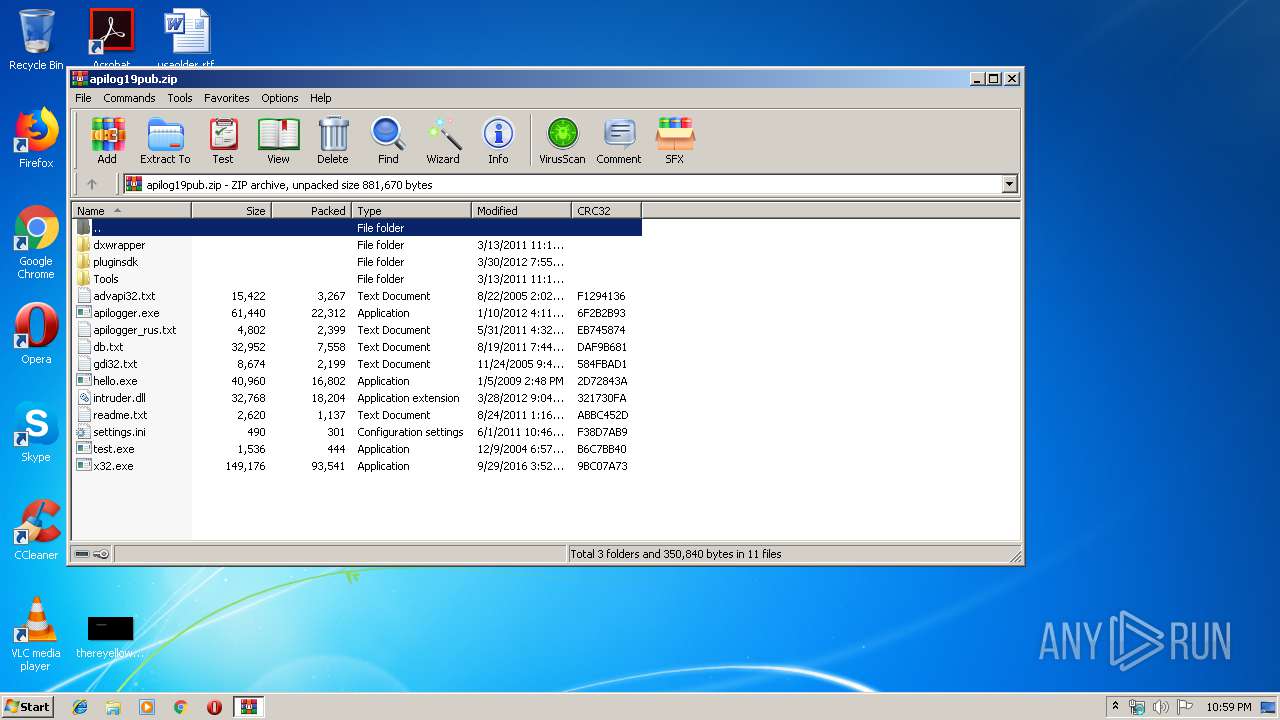
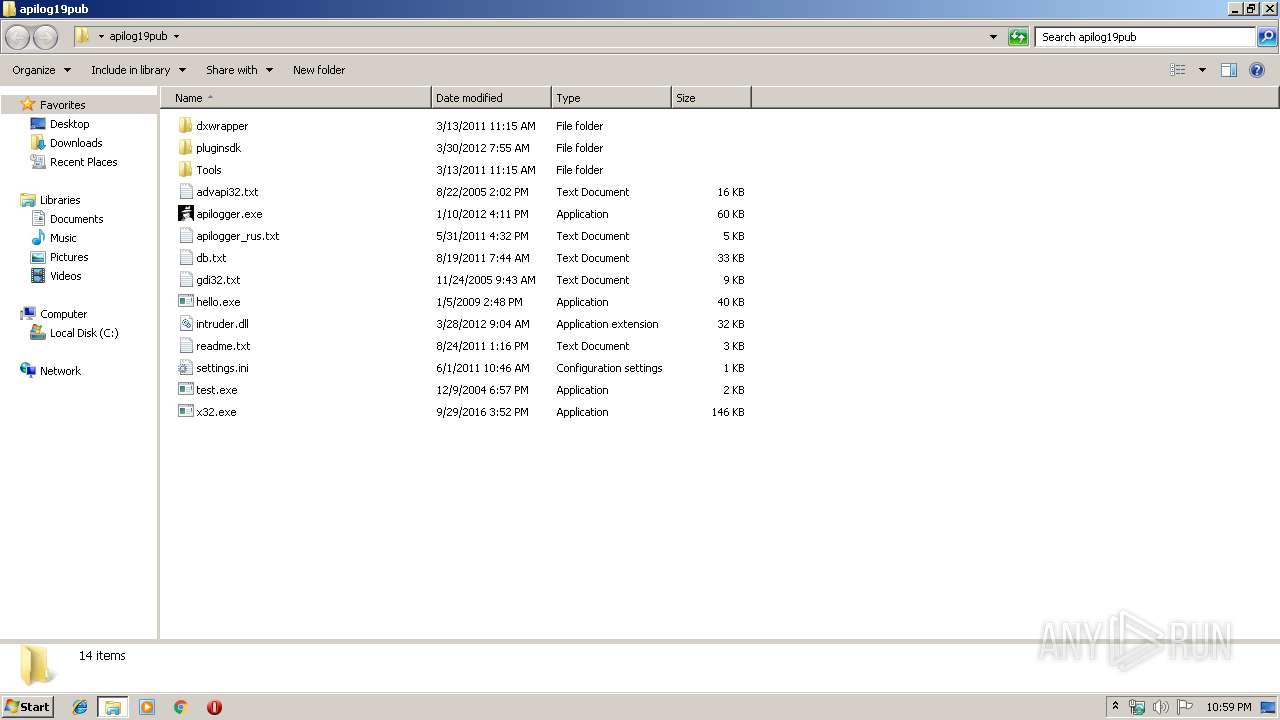
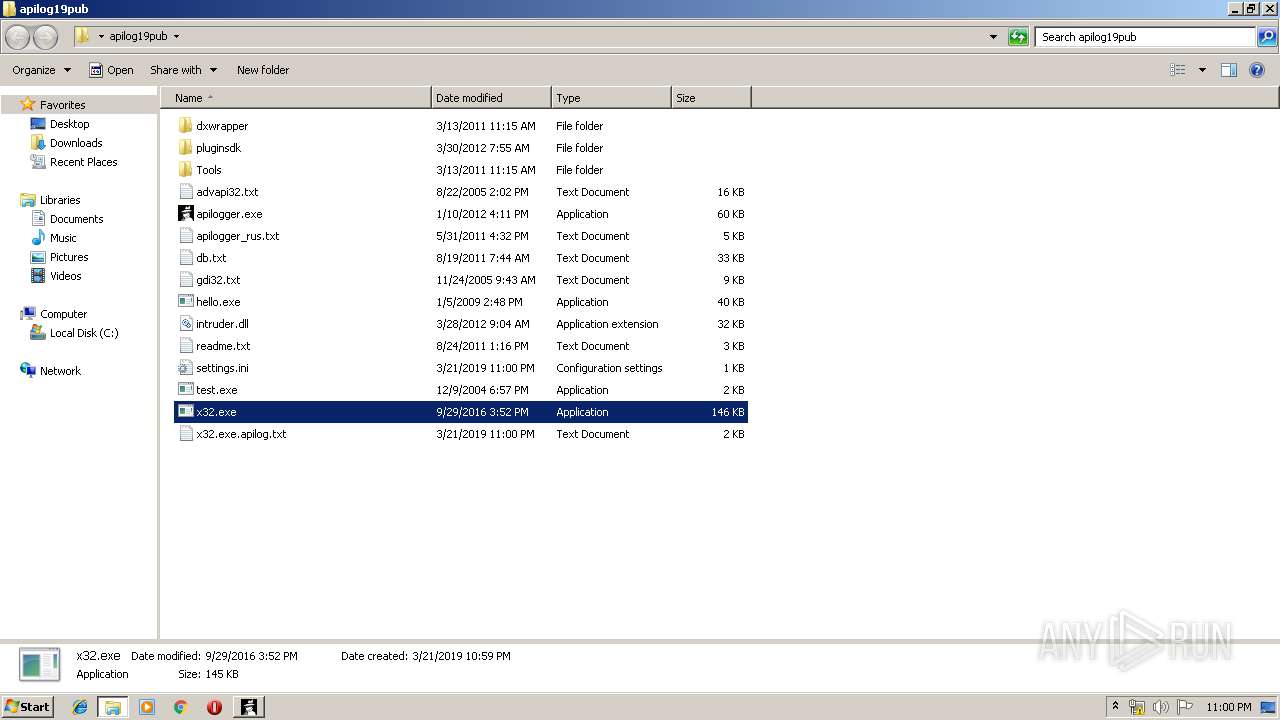
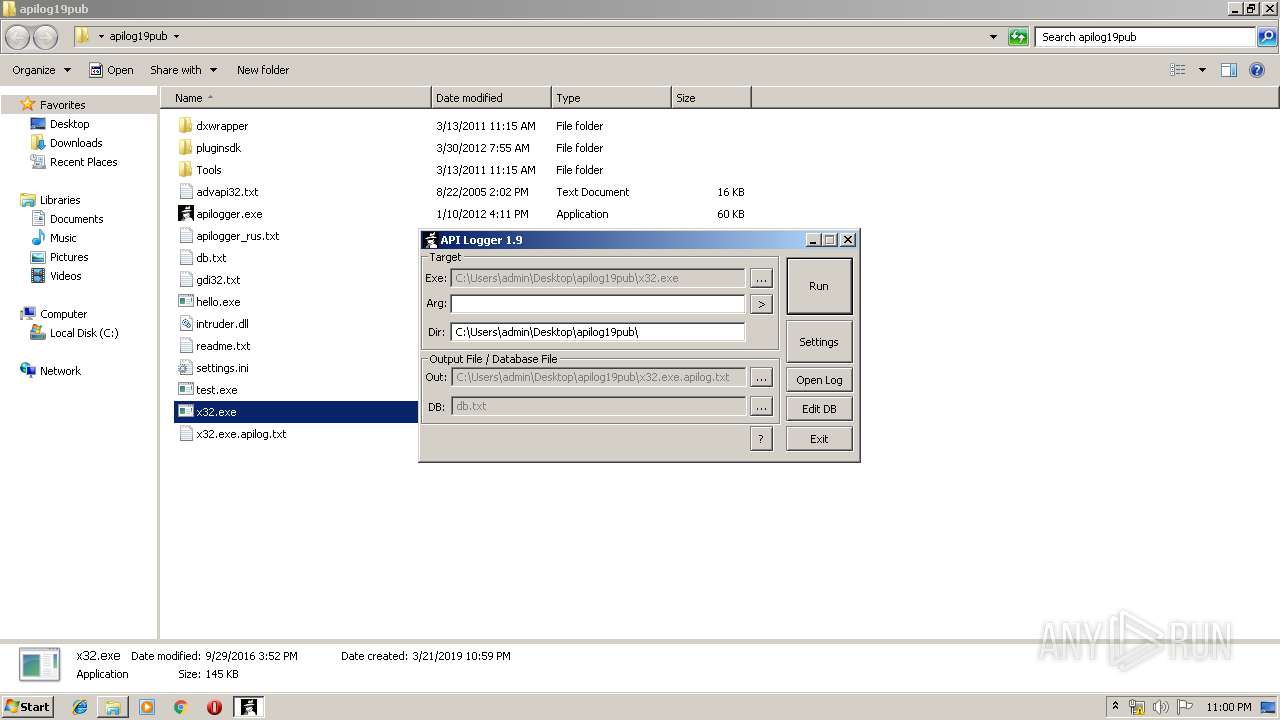
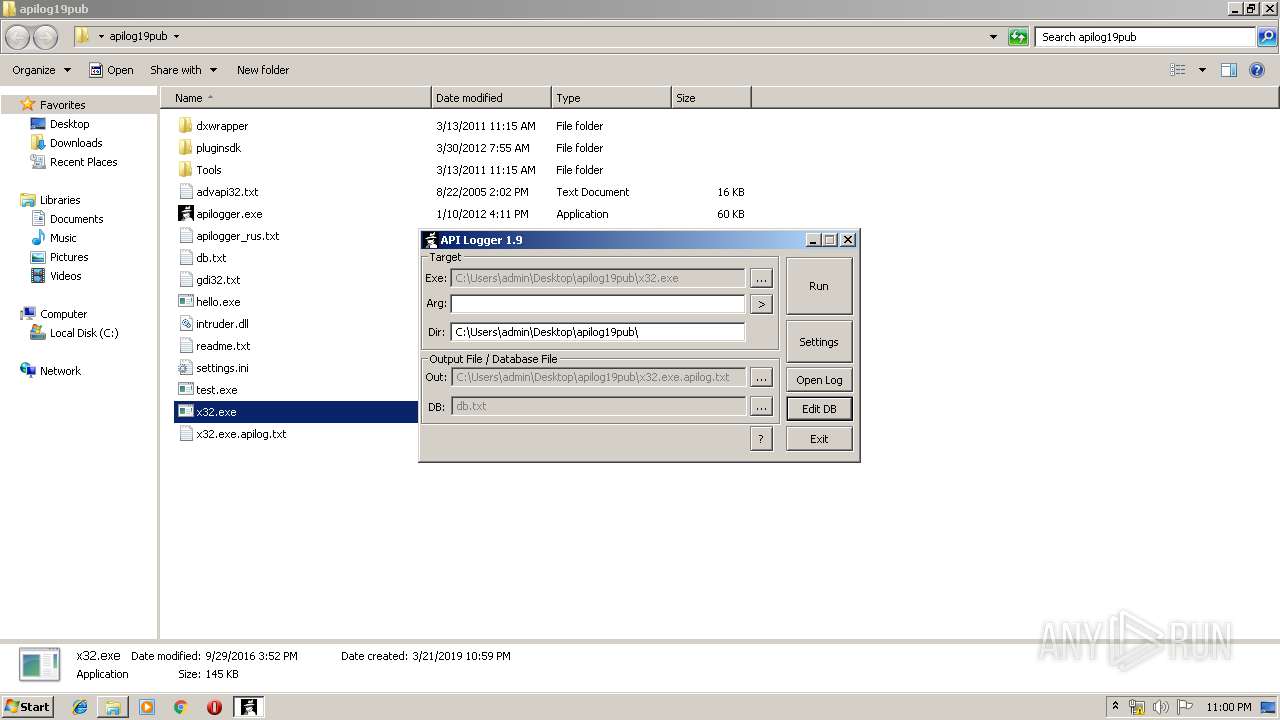
| File name: | apilog19pub.zip |
| Full analysis: | https://app.any.run/tasks/151433d8-7417-48cb-bad1-9fc755c2aad8 |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2019, 22:58:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F015075225FACC7C852251151179793C |
| SHA1: | 6D60C264A212C74CBA064234F1A8A38812FAAC9D |
| SHA256: | 50F45FFD70B8E74213387E75BD124C0BEE87CA8B77B3616A2C3D558239F112AB |
| SSDEEP: | 6144:tmNj4mcp4ZynQPP1KU++nQPP1K8vq/nInDJziMA6h57Cp6JAdO+EVtrEO8NKqV:wNj4mcp7nQPP1KUHnQPP1K8vq+9mMAio |
MALICIOUS
Application was dropped or rewritten from another process
- apilogger.exe (PID: 2480)
- x32.exe (PID: 2676)
- x32.exe (PID: 1276)
- x32.exe (PID: 2016)
- x32.exe (PID: 2348)
- x32.exe (PID: 3780)
Loads dropped or rewritten executable
- x32.exe (PID: 2676)
- WerFault.exe (PID: 3580)
- SearchProtocolHost.exe (PID: 3604)
- x32.exe (PID: 1276)
- WerFault.exe (PID: 3016)
- x32.exe (PID: 2348)
- WerFault.exe (PID: 2780)
- x32.exe (PID: 3780)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1928)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 2848)
- control.exe (PID: 3336)
INFO
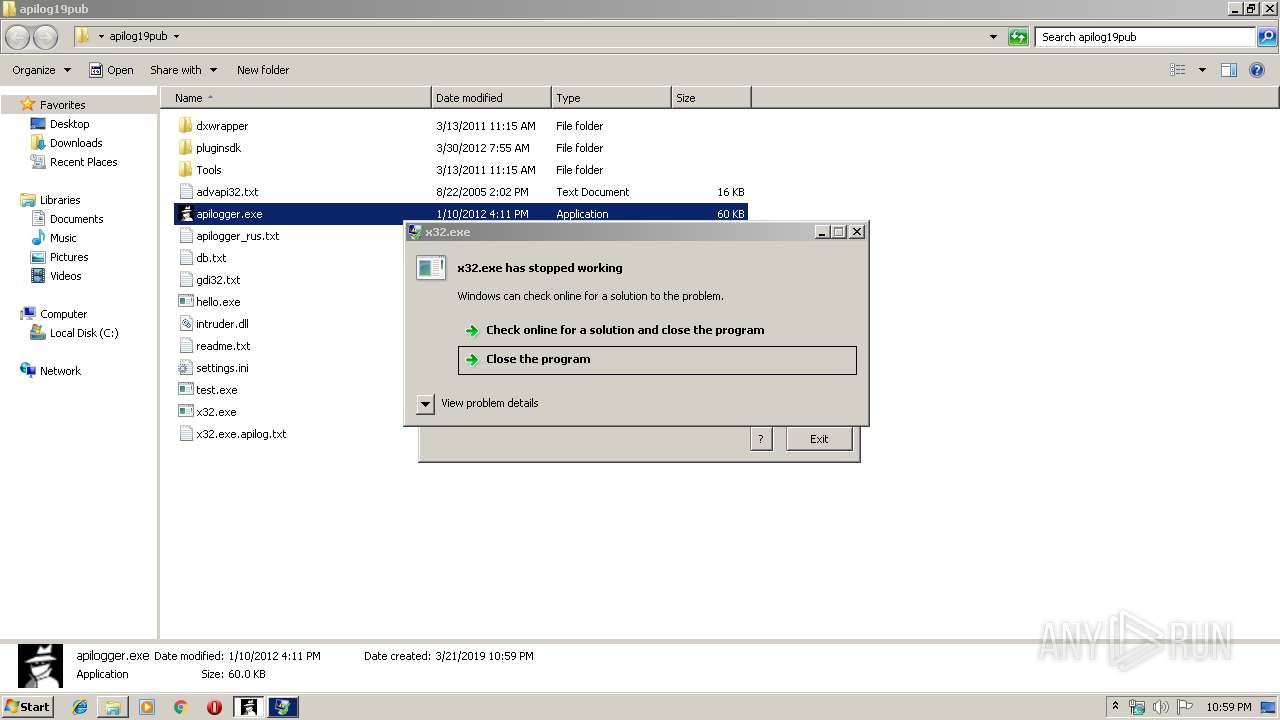
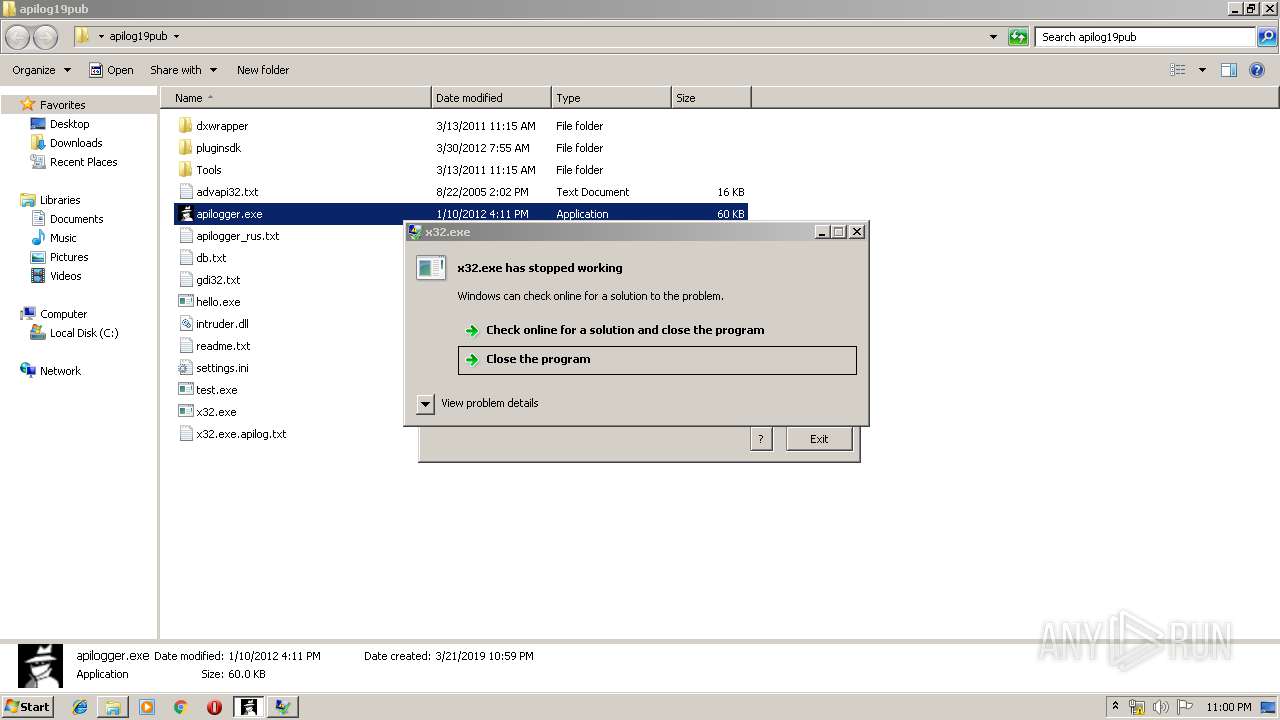
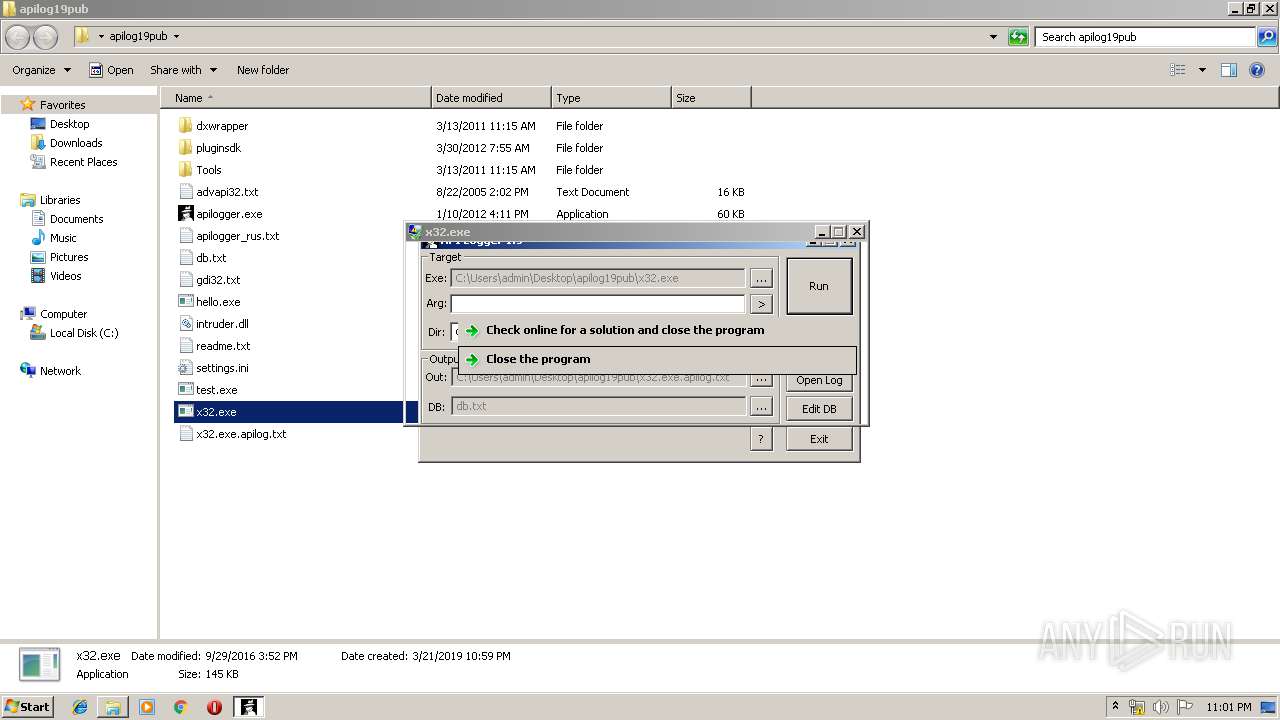
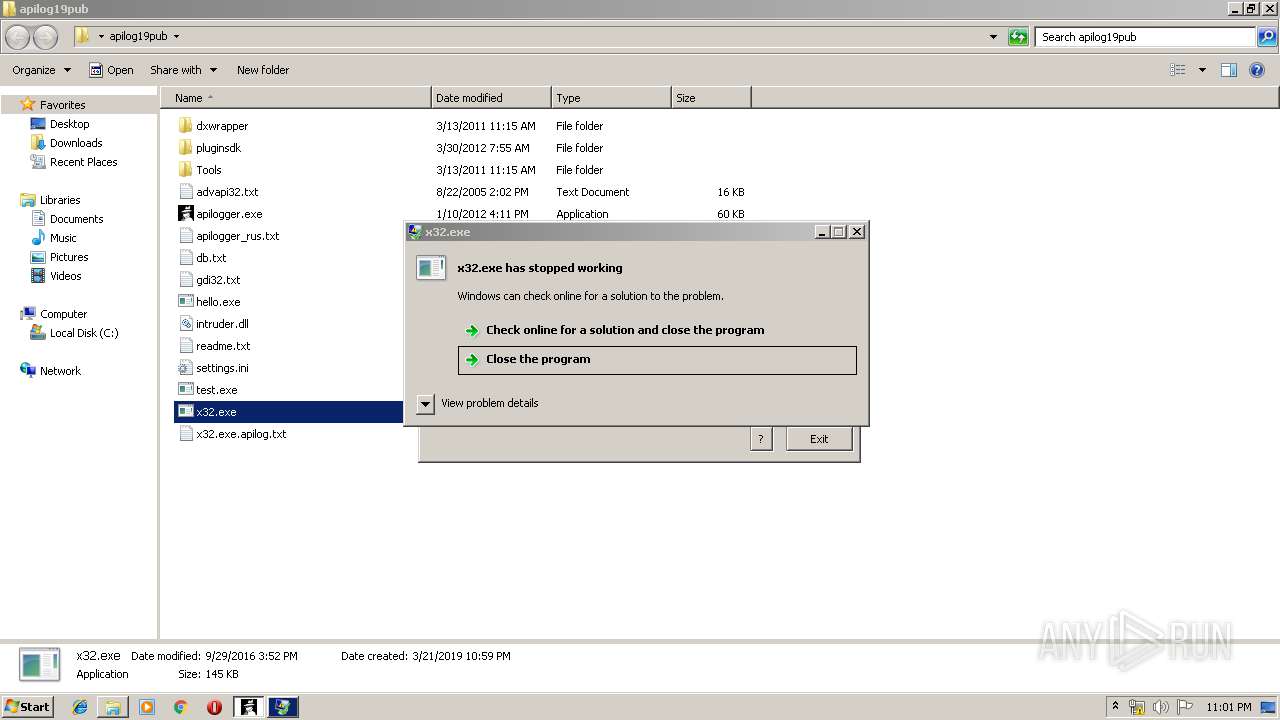
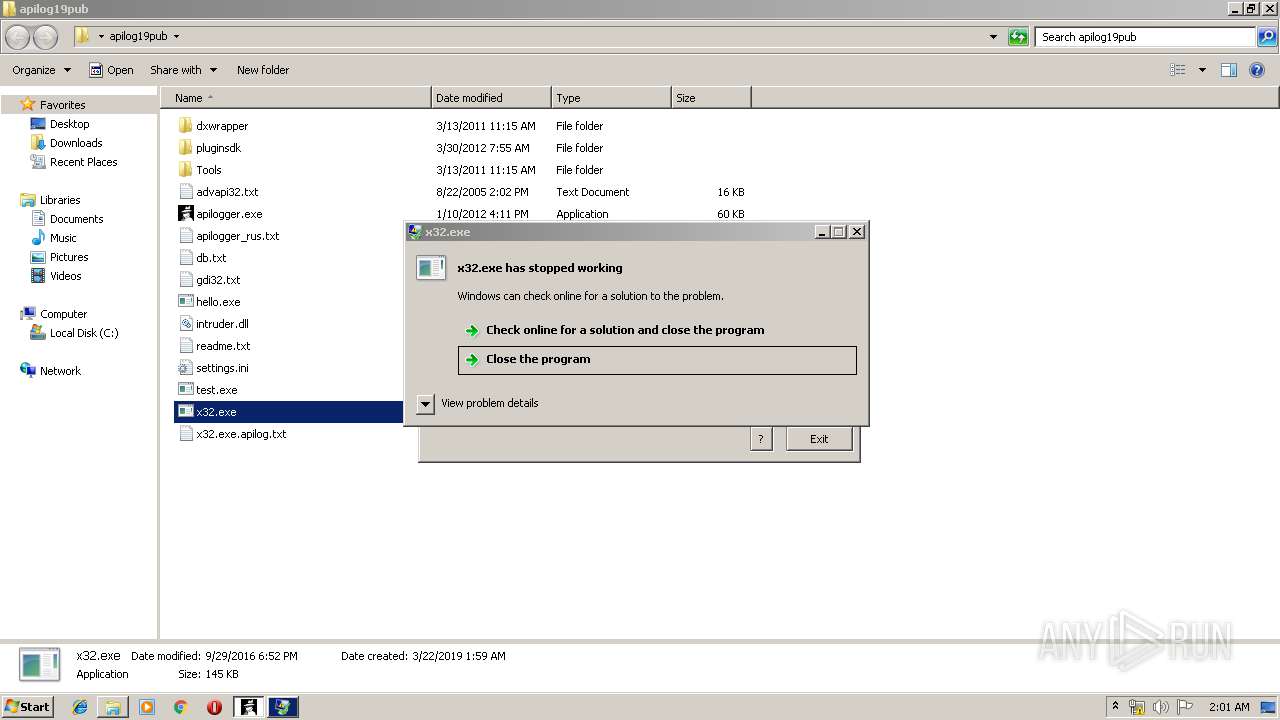
Application was crashed
- x32.exe (PID: 2676)
- x32.exe (PID: 1276)
- x32.exe (PID: 2348)
- x32.exe (PID: 3780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2004:12:09 18:57:09 |
| ZipCRC: | 0xb6c7bb40 |
| ZipCompressedSize: | 444 |
| ZipUncompressedSize: | 1536 |
| ZipFileName: | test.exe |
Total processes
55
Monitored processes
20
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
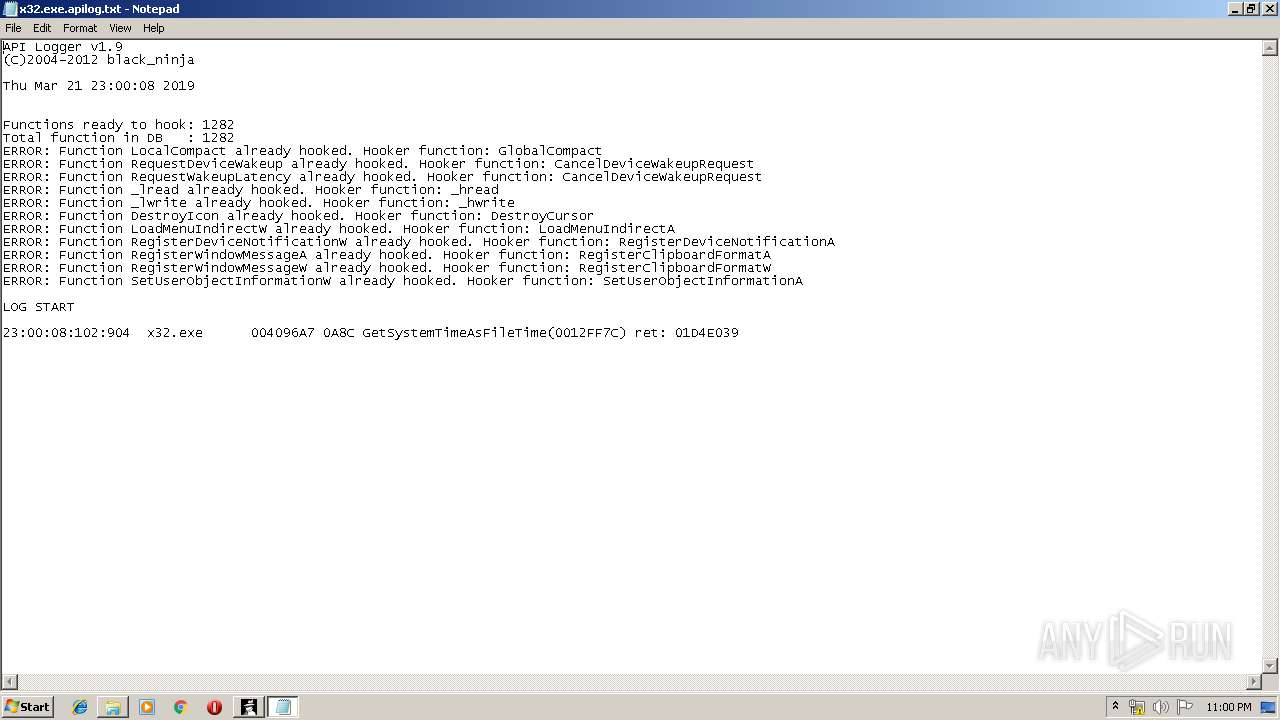
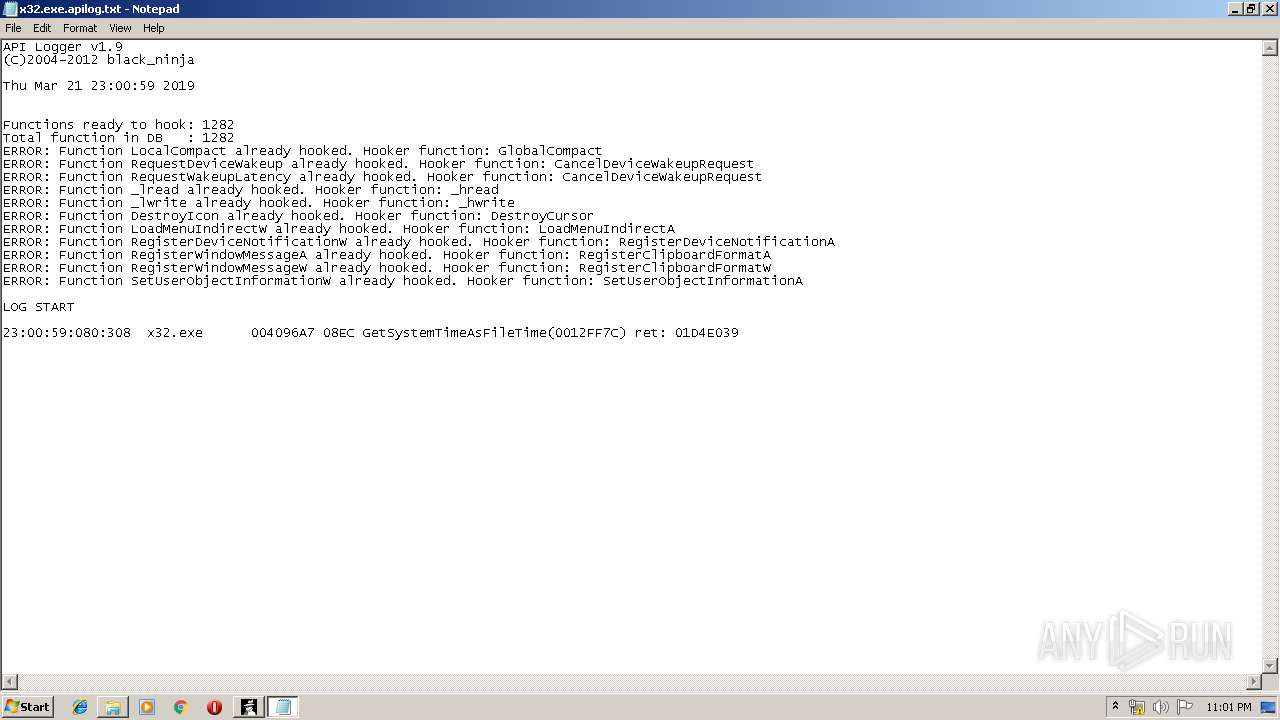
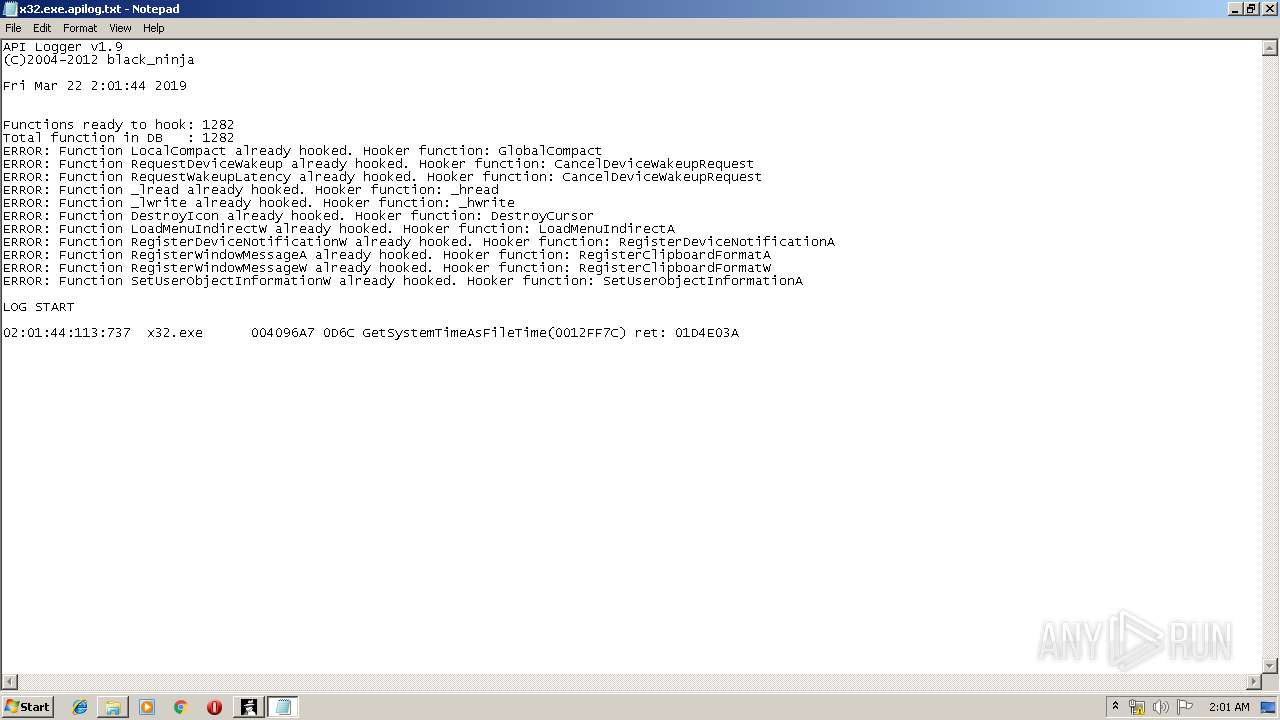
| 1272 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\apilog19pub\x32.exe.apilog.txt | C:\Windows\system32\NOTEPAD.EXE | — | apilogger.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1276 | C:\Users\admin\Desktop\apilog19pub\x32.exe | C:\Users\admin\Desktop\apilog19pub\x32.exe | apilogger.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 1928 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\apilog19pub.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2016 | "C:\Users\admin\Desktop\apilog19pub\x32.exe" | C:\Users\admin\Desktop\apilog19pub\x32.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2084 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\apilog19pub\x32.exe.apilog.txt | C:\Windows\system32\NOTEPAD.EXE | — | apilogger.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | C:\Users\admin\Desktop\apilog19pub\x32.exe | C:\Users\admin\Desktop\apilog19pub\x32.exe | apilogger.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 2420 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\apilog19pub\x32.exe.apilog.txt | C:\Windows\system32\NOTEPAD.EXE | — | apilogger.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
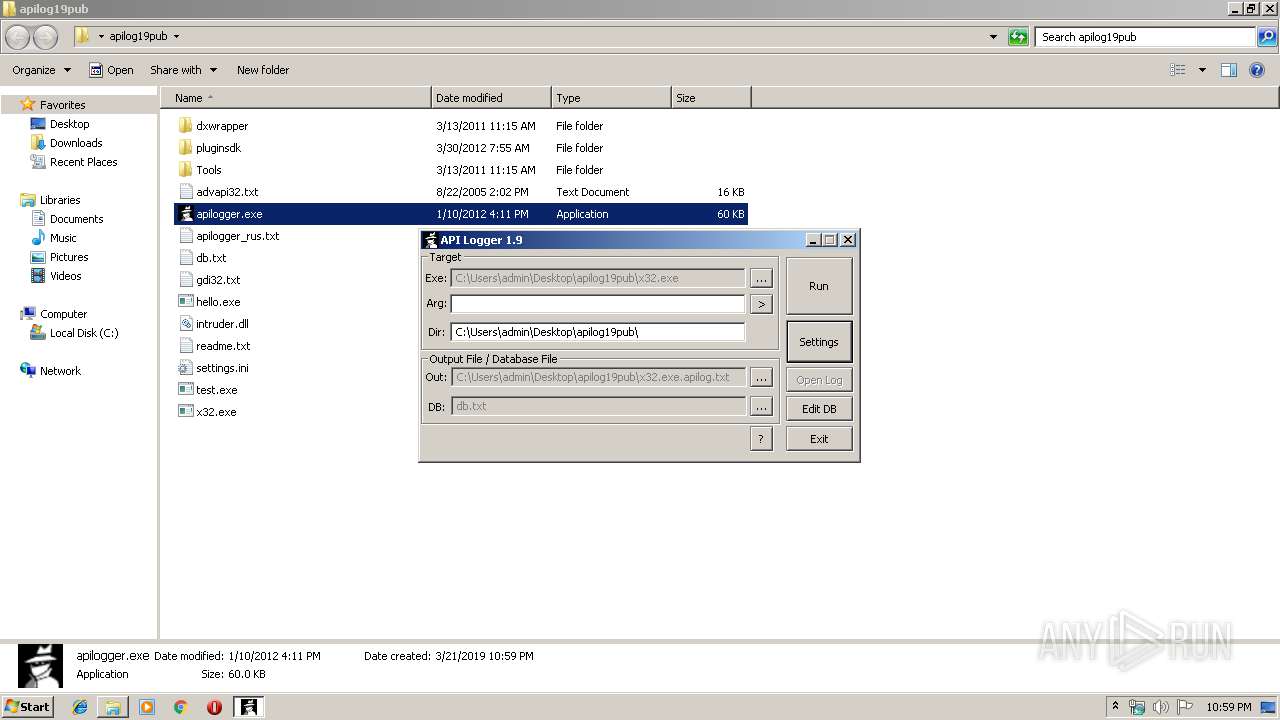
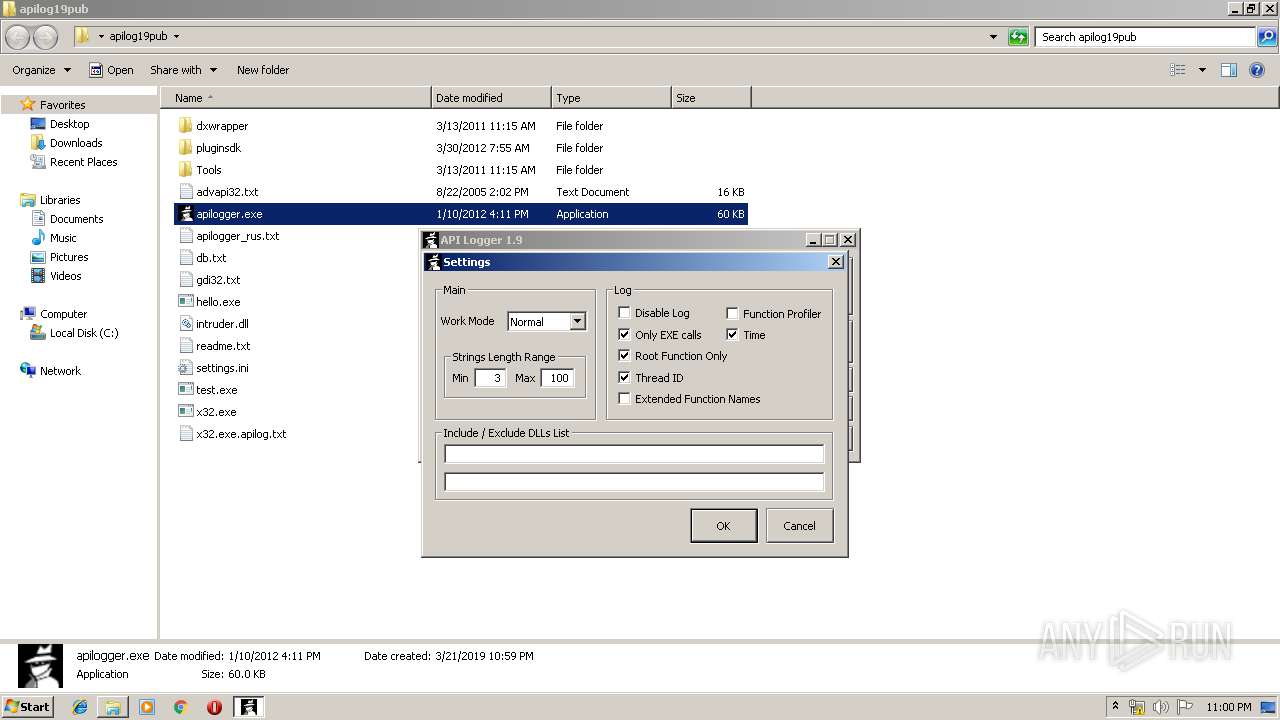
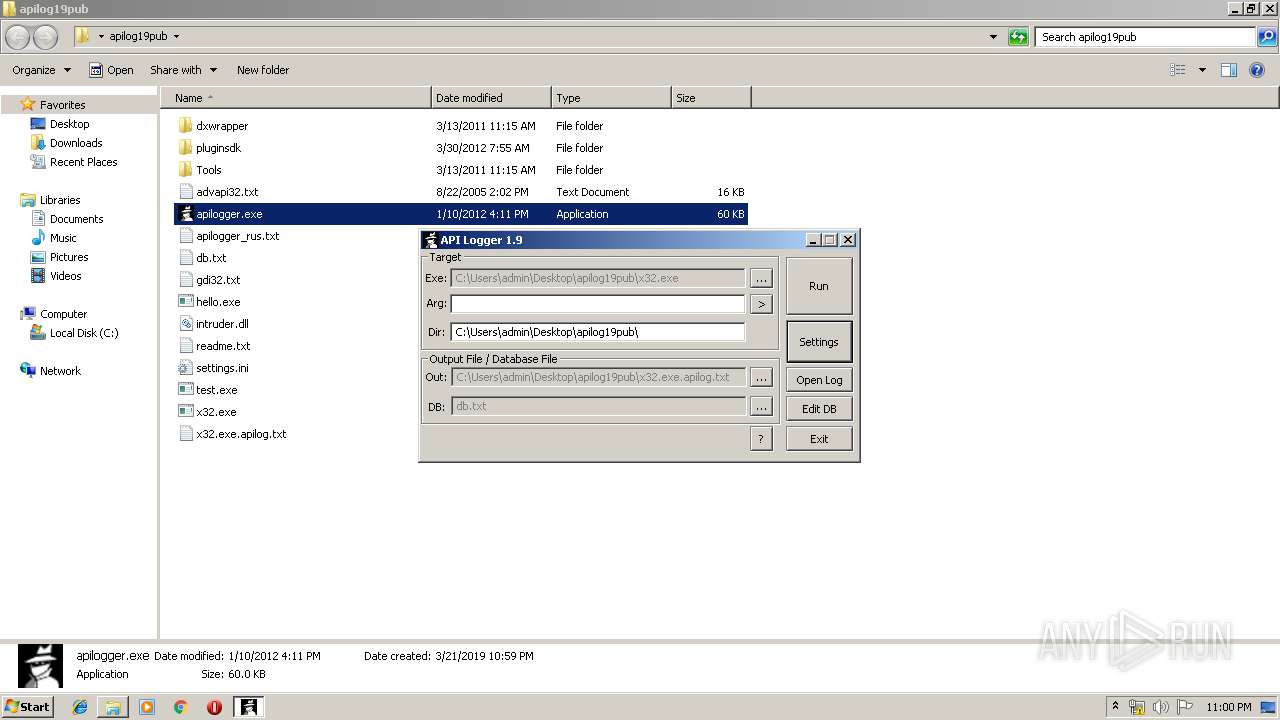
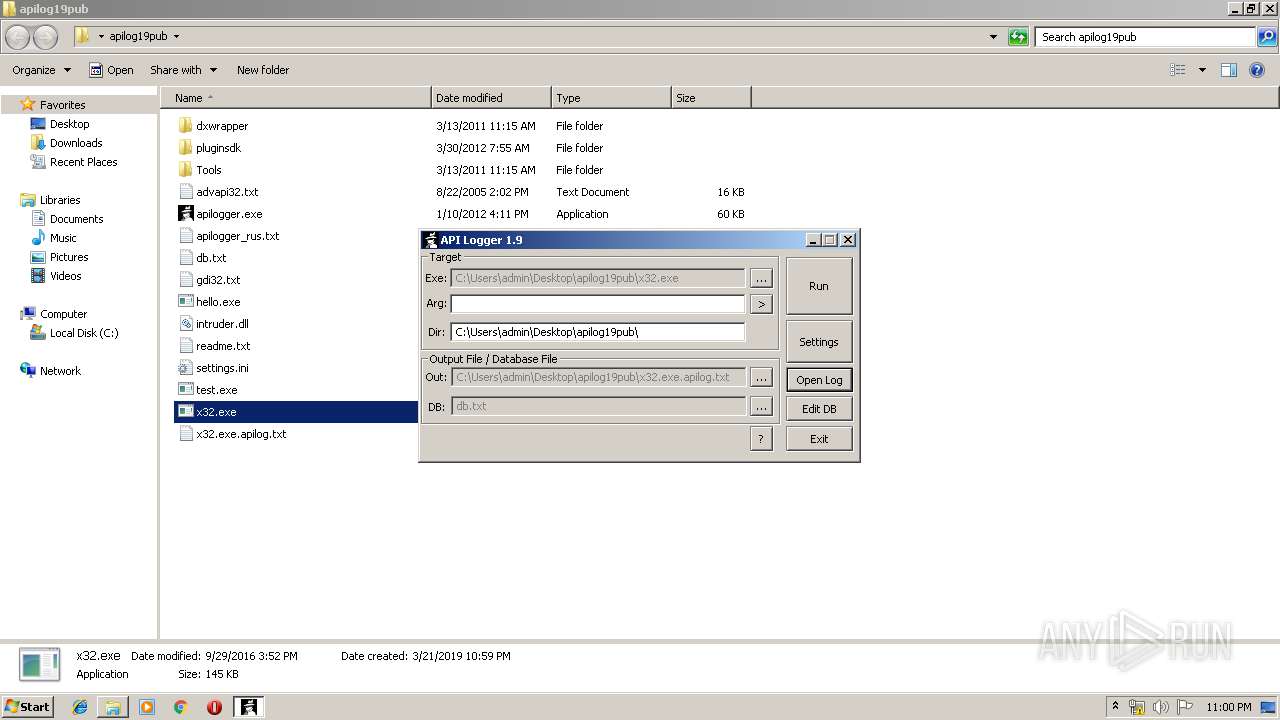
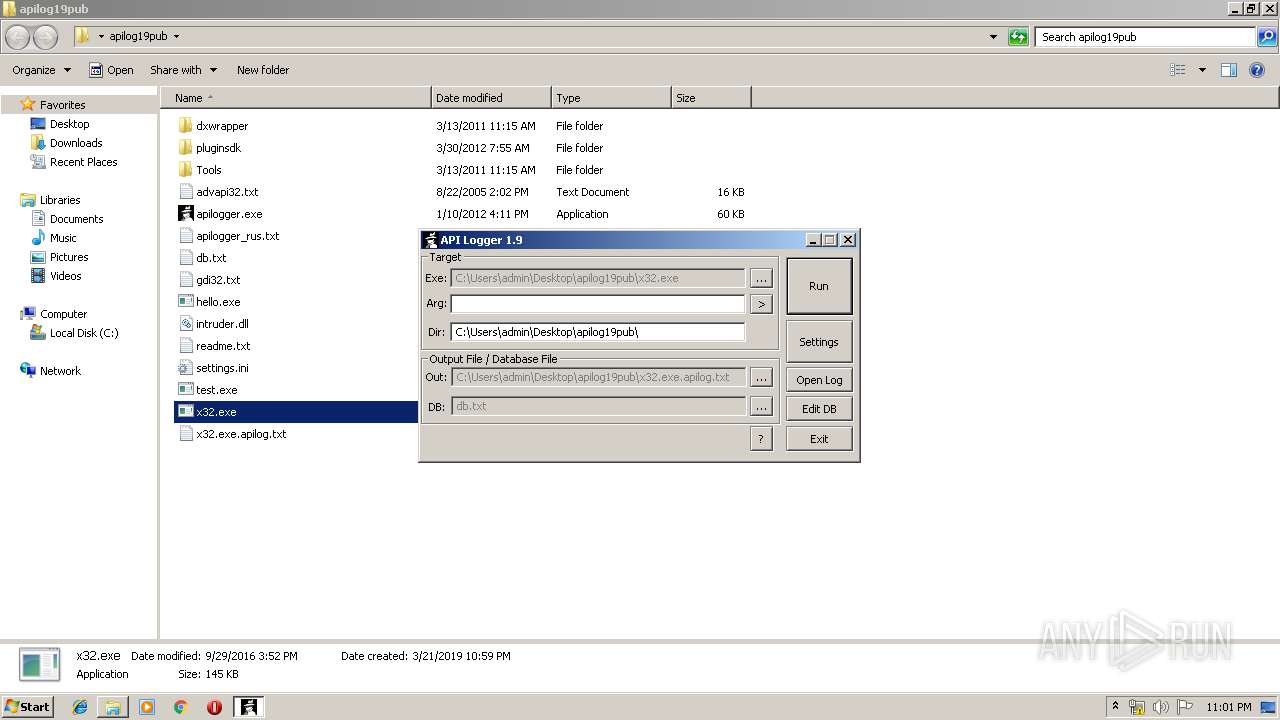
| 2480 | "C:\Users\admin\Desktop\apilog19pub\apilogger.exe" | C:\Users\admin\Desktop\apilog19pub\apilogger.exe | — | explorer.exe | |||||||||||
User: admin Company: http://blackninja2000.narod.ru Integrity Level: MEDIUM Description: API Logger Injector Exit code: 0 Version: 1, 9, 0, 0 Modules
| |||||||||||||||
| 2512 | C:\Windows\system32\DllHost.exe /Processid:{9DF523B0-A6C0-4EA9-B5F1-F4565C3AC8B8} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2624 | "C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL "C:\Windows\system32\timedate.cpl", | C:\Windows\system32\rundll32.exe | — | control.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 516
Read events
1 432
Write events
83
Delete events
1
Modification events
| (PID) Process: | (1928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1928) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\apilog19pub.zip | |||
| (PID) Process: | (1928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1928) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (1928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\apilog19pub | |||
Executable files
9
Suspicious files
3
Text files
78
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1928 | WinRAR.exe | C:\Users\admin\Desktop\apilog19pub\dxwrapper\readme.txt | text | |
MD5:— | SHA256:— | |||
| 1928 | WinRAR.exe | C:\Users\admin\Desktop\apilog19pub\dxwrapper\src\intruder.aps | res | |
MD5:— | SHA256:— | |||
| 1928 | WinRAR.exe | C:\Users\admin\Desktop\apilog19pub\dxwrapper\src\intruder.rc | text | |
MD5:— | SHA256:— | |||
| 1928 | WinRAR.exe | C:\Users\admin\Desktop\apilog19pub\dxwrapper\src\intruder.vcproj | xml | |
MD5:— | SHA256:— | |||
| 1928 | WinRAR.exe | C:\Users\admin\Desktop\apilog19pub\dxwrapper\dxwrap.dll | executable | |
MD5:— | SHA256:— | |||
| 1928 | WinRAR.exe | C:\Users\admin\Desktop\apilog19pub\dxwrapper\src\intruder.h | text | |
MD5:— | SHA256:— | |||
| 1928 | WinRAR.exe | C:\Users\admin\Desktop\apilog19pub\dxwrapper\src\intruder.cpp | text | |
MD5:— | SHA256:— | |||
| 1928 | WinRAR.exe | C:\Users\admin\Desktop\apilog19pub\dxwrapper\src\intruder.suo | suo | |
MD5:— | SHA256:— | |||
| 1928 | WinRAR.exe | C:\Users\admin\Desktop\apilog19pub\dxwrapper\src\stdafx.cpp | text | |
MD5:— | SHA256:— | |||
| 1928 | WinRAR.exe | C:\Users\admin\Desktop\apilog19pub\dxwrapper\src\intruder.def | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report