| File name: | Gameplay tool_3_2_5_Jenkey1002.rar |
| Full analysis: | https://app.any.run/tasks/92d87e48-ab25-4cd4-a676-901284702ccf |
| Verdict: | Malicious activity |
| Analysis date: | August 24, 2024, 19:06:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 84C22692C9FB948B7F14E3A173DF4051 |
| SHA1: | 0A6EE31A234E6952398B773536E5B9DE48FC1058 |
| SHA256: | 50DFC4B46BA73B44A3D05B145AEEB4BEE466E9464A279267BEBB1B2D6D0ECAF1 |
| SSDEEP: | 98304:NzQzKGXUMZ2ReHh5e17GpDl1Kr3jL+2i+VK+LA0Omix8FA0dhnHMUhJpdh3zvauC:sjU9sfO9edvyLgw5GXgCgo |
MALICIOUS
No malicious indicators.SUSPICIOUS
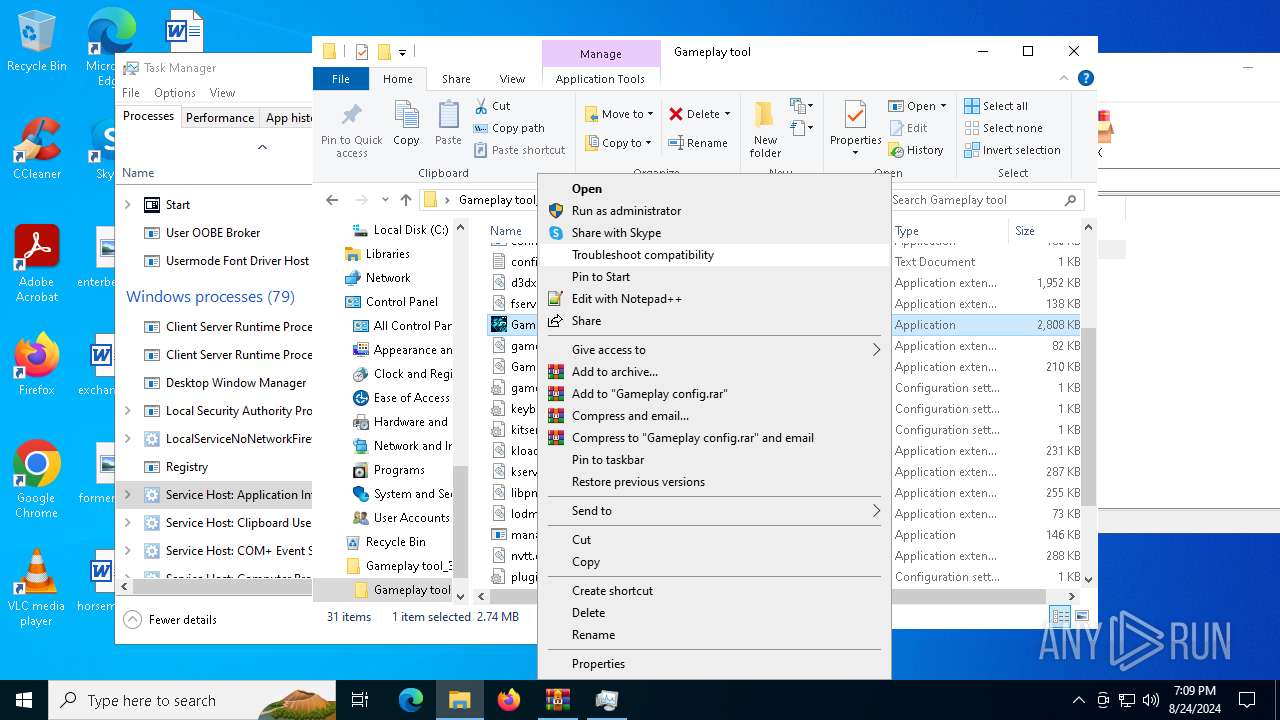
Probably uses Microsoft diagnostics tool to execute malicious payload
- pcwrun.exe (PID: 6528)
Executable content was dropped or overwritten
- csc.exe (PID: 4064)
- csc.exe (PID: 5900)
- csc.exe (PID: 208)
Drops the executable file immediately after the start
- csc.exe (PID: 5900)
- csc.exe (PID: 4064)
- csc.exe (PID: 208)
Gets file extension (POWERSHELL)
- sdiagnhost.exe (PID: 6352)
Uses RUNDLL32.EXE to load library
- msdt.exe (PID: 6520)
Converts a string into array of characters (POWERSHELL)
- sdiagnhost.exe (PID: 6352)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6772)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6772)
Manual execution by a user
- Taskmgr.exe (PID: 6580)
- Gameplay config.exe (PID: 2580)
- Gameplay config.exe (PID: 2868)
- Taskmgr.exe (PID: 3032)
- manager.exe (PID: 2252)
- Gameplay config.exe (PID: 4288)
- Gameplay config.exe (PID: 1044)
- pcwrun.exe (PID: 6528)
- config.exe (PID: 3412)
- config.exe (PID: 232)
- Gameplay config.exe (PID: 7104)
Reads mouse settings
- Gameplay config.exe (PID: 7104)
- Gameplay config.exe (PID: 2580)
- Gameplay config.exe (PID: 2868)
- Gameplay config.exe (PID: 4288)
- Gameplay config.exe (PID: 1044)
- Gameplay config.exe (PID: 6668)
Reads the computer name
- Gameplay config.exe (PID: 7104)
- Gameplay config.exe (PID: 2580)
- manager.exe (PID: 2252)
- Gameplay config.exe (PID: 2868)
- Gameplay config.exe (PID: 1044)
- Gameplay config.exe (PID: 4288)
- Gameplay config.exe (PID: 6668)
- config.exe (PID: 3412)
- config.exe (PID: 232)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6580)
- sdiagnhost.exe (PID: 6352)
- msdt.exe (PID: 6520)
- rundll32.exe (PID: 3684)
Checks supported languages
- Gameplay config.exe (PID: 2868)
- Gameplay config.exe (PID: 4288)
- manager.exe (PID: 2252)
- Gameplay config.exe (PID: 1044)
- csc.exe (PID: 5900)
- cvtres.exe (PID: 4308)
- csc.exe (PID: 4064)
- cvtres.exe (PID: 1432)
- csc.exe (PID: 208)
- cvtres.exe (PID: 1108)
- Gameplay config.exe (PID: 6668)
- config.exe (PID: 3412)
- config.exe (PID: 232)
- Gameplay config.exe (PID: 7104)
- Gameplay config.exe (PID: 2580)
Create files in a temporary directory
- pcwrun.exe (PID: 6528)
- msdt.exe (PID: 6520)
- sdiagnhost.exe (PID: 6352)
- csc.exe (PID: 5900)
- csc.exe (PID: 4064)
- cvtres.exe (PID: 4308)
- cvtres.exe (PID: 1432)
- csc.exe (PID: 208)
- cvtres.exe (PID: 1108)
Reads the software policy settings
- msdt.exe (PID: 6520)
- sdiagnhost.exe (PID: 6352)
Reads the machine GUID from the registry
- csc.exe (PID: 5900)
- csc.exe (PID: 4064)
- csc.exe (PID: 208)
Uses string replace method (POWERSHELL)
- sdiagnhost.exe (PID: 6352)
Checks proxy server information
- sdiagnhost.exe (PID: 6352)
Uses string split method (POWERSHELL)
- sdiagnhost.exe (PID: 6352)
Creates files or folders in the user directory
- msdt.exe (PID: 6520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 57672 |
|---|---|
| UncompressedSize: | 142336 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2013:02:03 10:55:16 |
| PackingMethod: | Normal |
| ArchivedFileName: | Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\afs2fs.dll |
Total processes
155
Monitored processes
24
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\gmex45am.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 232 | "C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\config.exe" | C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\config.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: KitServer 13 Configuration Tool Exit code: 0 Version: 13.0.0.0 Modules
| |||||||||||||||
| 1044 | "C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\Gameplay config.exe" | C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\Gameplay config.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Gameplay tool configuration Exit code: 0 Version: 3.2.4.0 Modules
| |||||||||||||||
| 1108 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES393.tmp" "c:\Users\admin\AppData\Local\Temp\CSC57A228801AF54DF88A21099B187E2.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 1432 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES77.tmp" "c:\Users\admin\AppData\Local\Temp\CSCE7F4FE1E30C24FF68AB36424F2B726BB.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
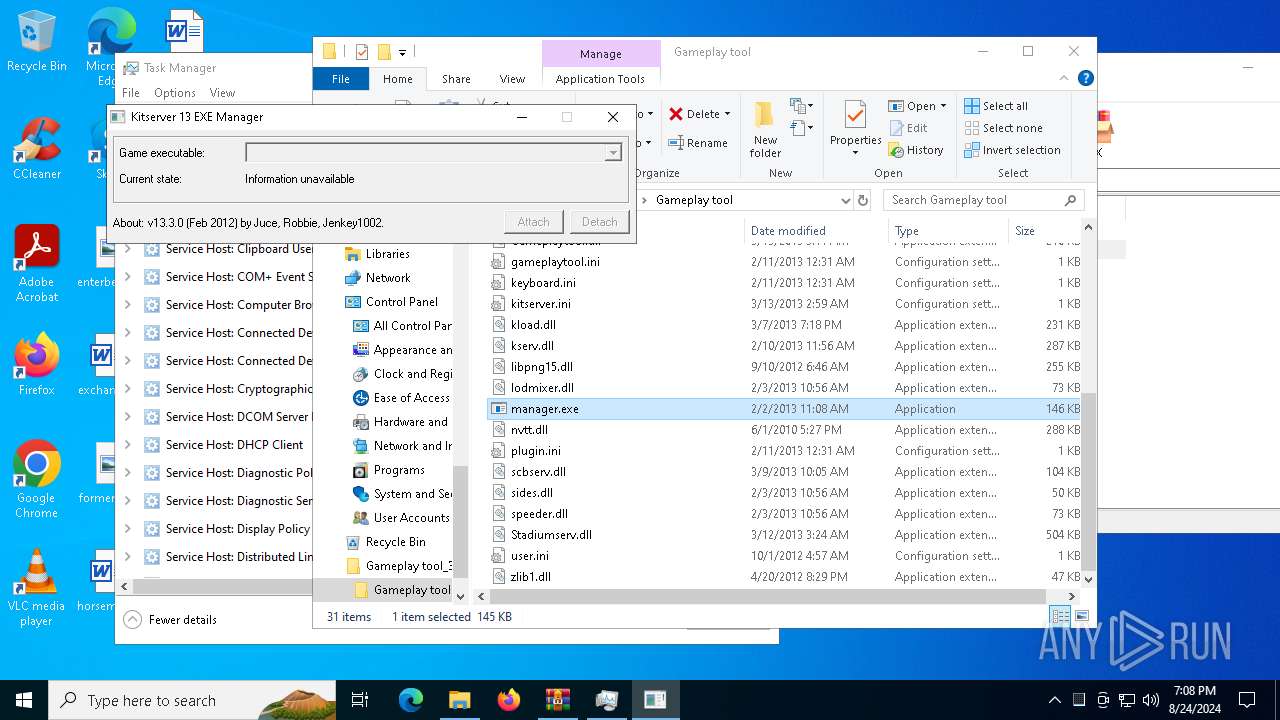
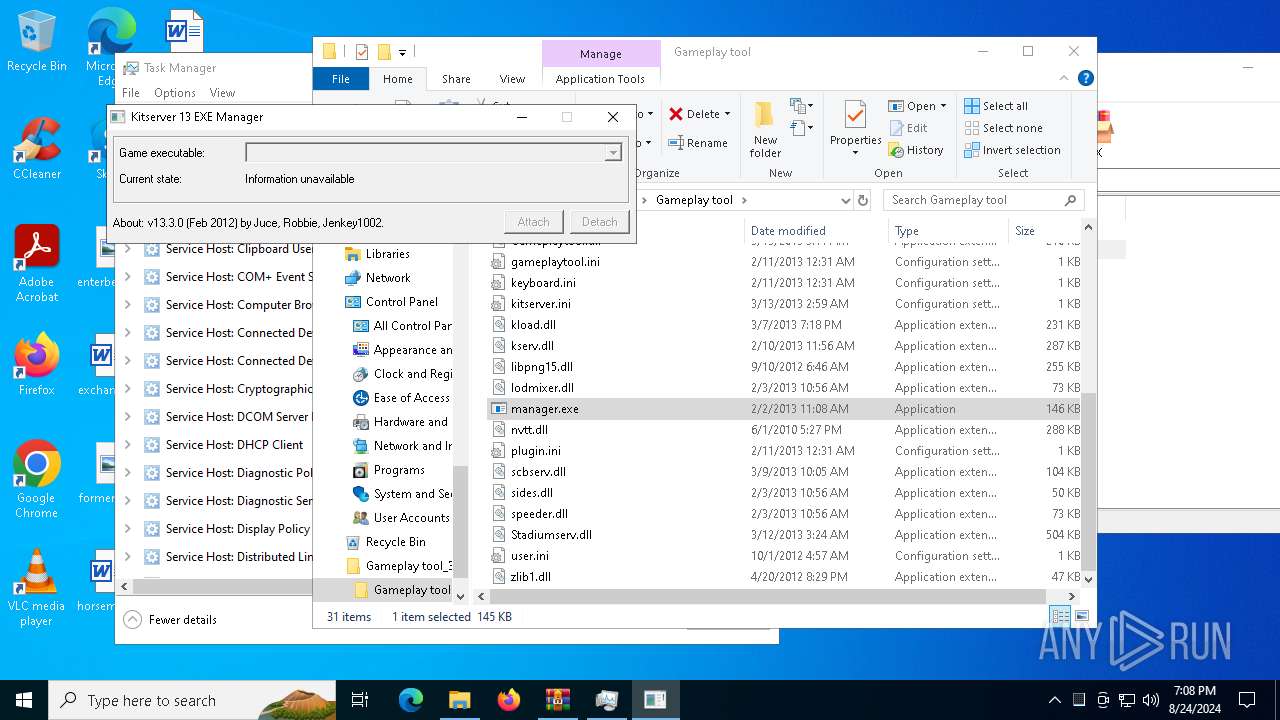
| 2252 | "C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\manager.exe" | C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\manager.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Kitserver 13 EXE Manager Exit code: 0 Version: 13.3.0.0 Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\Gameplay config.exe" | C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\Gameplay config.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Gameplay tool configuration Exit code: 0 Version: 3.2.4.0 Modules
| |||||||||||||||
| 2868 | "C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\Gameplay config.exe" | C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\Gameplay config.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Gameplay tool configuration Exit code: 0 Version: 3.2.4.0 Modules
| |||||||||||||||
| 3032 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3412 | "C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\config.exe" | C:\Users\admin\Desktop\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\config.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: KitServer 13 Configuration Tool Exit code: 0 Version: 13.0.0.0 Modules
| |||||||||||||||
Total events
21 355
Read events
21 302
Write events
51
Delete events
2
Modification events
| (PID) Process: | (6772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Gameplay tool_3_2_5_Jenkey1002.rar | |||
| (PID) Process: | (6772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6772) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6580) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (6580) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AAC14FF77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AAC14FF77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AAC14FF77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AAC14FF77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AAC14FF77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000ABC14FF77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028ABC14FF77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050ABC14FF77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AAC14FF77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070ABC14FF77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088ABC14FF77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8ABC14FF77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8ABC14FF77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0ABC14FF77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010ACC14FF77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AAC14FF77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AAC14FF77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AAC14FF77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040ACC14FF77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068ACC14FF77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090ACC14FF77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8ACC14FF77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8ACC14FF77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8ACC14FF77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028ABC14FF77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AAC14FF77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020ADC14FF77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040ADC14FF77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068ADC14FF77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AAC14FF77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050ABC14FF77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AAC14FF77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070ABC14FF77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088ABC14FF77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8ABC14FF77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8ABC14FF77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AAC14FF77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088ADC14FF77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8ADC14FF77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0ADC14FF77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AEC14FF77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AEC14FF77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AEC14FF77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AEC14FF77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
Executable files
28
Suspicious files
18
Text files
189
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6772.18474\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\docs\arsenal.png | image | |
MD5:B208B7A5E22013E08CD4015BD0528E8B | SHA256:ADD5211C9850D8303486F25C9F19C828586B36BC620F29A1402FBEA439815D9F | |||
| 6772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6772.18474\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\docs\config-sides.png | image | |
MD5:F96C144E6BC062DD012331610DE1B59E | SHA256:D5F7DF6F237E67169A7632280490B4CE4A1DE1E3F7316C2C334D3223A88D5664 | |||
| 6772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6772.18474\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\ballserv.dll | executable | |
MD5:17F8EC750F9EB66E84A1726B95854635 | SHA256:E999905333E71C14FD088711E2B394C976F5E26D6A92B8F7370C7E79BBA33A0A | |||
| 6772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6772.18474\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\docs\layout1.png | image | |
MD5:3B53F4758C23CF87E54DB35154F91922 | SHA256:E925946170E93F63F79B72A6D8D04BAD5F96C61B8FC2A82F273CB4E0EBD20D8D | |||
| 6772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6772.18474\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\d3dx9_43.dll | executable | |
MD5:86E39E9161C3D930D93822F1563C280D | SHA256:0B28546BE22C71834501F7D7185EDE5D79742457331C7EE09EFC14490DD64F5F | |||
| 6772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6772.18474\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\docs\manager.png | image | |
MD5:8863F77A8B5291534A926FC4F9A5F728 | SHA256:26079D126680286A742914E2FFEEBBADCD9D1D985972D37B9CA805BC0B67D345 | |||
| 6772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6772.18474\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\docs\afs2fs.png | image | |
MD5:3B53F4758C23CF87E54DB35154F91922 | SHA256:E925946170E93F63F79B72A6D8D04BAD5F96C61B8FC2A82F273CB4E0EBD20D8D | |||
| 6772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6772.18474\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\docs\manual.html | html | |
MD5:772743EF4A4A564876E136A3F758A587 | SHA256:CFC3858DBA06193B7531ED4BB94EC2F99BD7161A4DF7CEA4B02C8DF772976AEC | |||
| 6772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6772.18474\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\afs2fs.dll | executable | |
MD5:0E0F8051D2DD4D8D7B2AE55B1F442EFC | SHA256:6C7CC8A10E6DD02D63763E144863D49C1E4DCBBFD885FD12EEF390DC8CF4A6F8 | |||
| 6772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6772.18474\Gameplay tool_3_2_5_Jenkey1002\Gameplay tool\afsio.dll | executable | |
MD5:17EAADE1837ECF1940D8E8B7111085E9 | SHA256:602D4F25FBB1AD07CF3BEE0F5FC312092592CCB2462EC016C3977BF46658FE07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
42
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5044 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6628 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3308 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1172 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3308 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5044 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5044 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Gameplay config.exe | FTH: (6668): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|