| File name: | test99 |
| Full analysis: | https://app.any.run/tasks/173886ce-3bcd-488c-8bc0-6570bfef9b68 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2024, 00:37:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 2513EB59C3DB32A2D5EFBEDE6136A75D |
| SHA1: | 1D8DBFC96C391091BE3CABCB7F437DAF069AD943 |
| SHA256: | 50D1B32CF53FE1B0822D2606AA397743D6069785BA0B03A3CAD52E63F84C90A8 |
| SSDEEP: | 192:1D3nTjp5JdQUP5YttDOtMXmgntgO8ljTcQ4en:1DXPpvxYyC/nmnjOen |
MALICIOUS
Creates internet connection object (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Gets path to any of the special folders (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Sends HTTP request (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Opens an HTTP connection (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Opens a text file (SCRIPT)
- scrcons.exe (PID: 3408)
Accesses user account's information(Win32_UserAccount) via WMI (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Deletes a file (SCRIPT)
- scrcons.exe (PID: 3408)
Accesses Processor(Win32_Processor, may evade sandboxes) via WMI (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Uses base64 encoding (SCRIPT)
- cscript.exe (PID: 2888)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 2888)
Accesses the network adapter (Win32_NetworkAdapter) via WMI (SCRIPT)
- cscript.exe (PID: 2888)
Creates a writable file in the system directory
- powershell.exe (PID: 3516)
Accesses to a group account data(Win32_Group) via WMI (SCRIPT)
- cscript.exe (PID: 2888)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 3516)
May hide the program window using WMI (SCRIPT)
- cscript.exe (PID: 2888)
Uses sleep, probably for evasion detection (SCRIPT)
- cscript.exe (PID: 2888)
Accesses system services(Win32_Service) via WMI (SCRIPT)
- cscript.exe (PID: 2888)
SUSPICIOUS
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Accesses current user name via WMI (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Checks whether a specific file exists (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Checks Windows Trust Settings
- drvinst.exe (PID: 1168)
Writes binary data to a Stream object (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Starts POWERSHELL.EXE for commands execution
- scrcons.exe (PID: 3408)
Executes WMI query (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Creates FileSystem object to access computer's file system (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Adds/modifies Windows certificates
- scrcons.exe (PID: 3408)
Checks for external IP
- scrcons.exe (PID: 3408)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Saves data to a binary file (SCRIPT)
- scrcons.exe (PID: 3408)
- cscript.exe (PID: 2888)
Changes charset (SCRIPT)
- cscript.exe (PID: 2888)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 2888)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 2888)
Creates XML DOM element (SCRIPT)
- cscript.exe (PID: 2888)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 2888)
Possibly malicious use of IEX has been detected
- scrcons.exe (PID: 3408)
Runs shell command (SCRIPT)
- scrcons.exe (PID: 3408)
Starts CMD.EXE for commands execution
- scrcons.exe (PID: 3408)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 3516)
Gets information about processes (POWERSHELL)
- powershell.exe (PID: 3516)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 3516)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- cscript.exe (PID: 2888)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 2888)
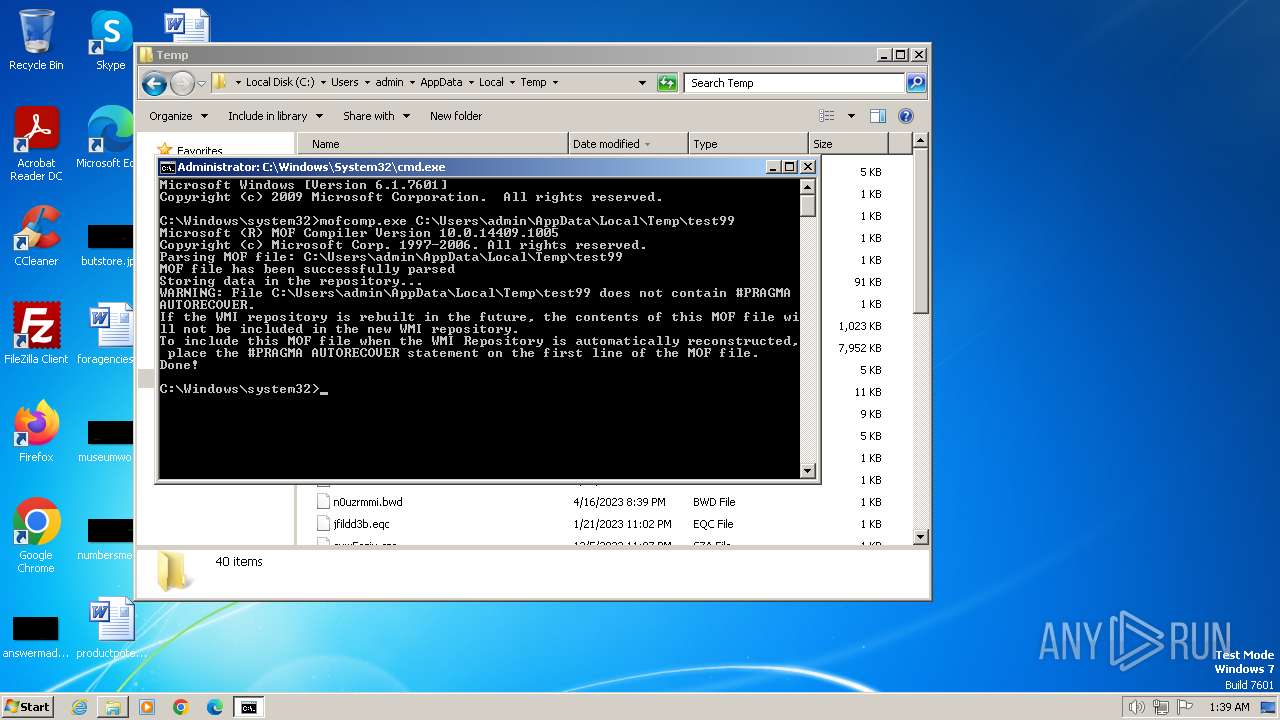
Executed via WMI
- mofcomp.exe (PID: 2772)
Adds, changes, or deletes HTTP request header (SCRIPT)
- cscript.exe (PID: 2888)
Accesses ComputerSystem(Win32_ComputerSystem) via WMI (SCRIPT)
- cscript.exe (PID: 2888)
INFO
Manual execution by a user
- explorer.exe (PID: 1980)
- cmd.exe (PID: 2092)
Reads the software policy settings
- drvinst.exe (PID: 1168)
- scrcons.exe (PID: 3408)
Checks supported languages
- drvinst.exe (PID: 1168)
Reads the computer name
- drvinst.exe (PID: 1168)
Reads the machine GUID from the registry
- drvinst.exe (PID: 1168)
Reads security settings of Internet Explorer
- scrcons.exe (PID: 3408)
Disables trace logs
- powershell.exe (PID: 3516)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
58
Monitored processes
11
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1168 | DrvInst.exe "1" "200" "UMB\UMB\1&841921d&0&TERMINPUT_BUS" "" "" "6e3bed883" "00000000" "0000030C" "00000060" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1980 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2092 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2724 | mofcomp.exe C:\Users\admin\AppData\Local\Temp\test99 | C:\Windows\System32\wbem\mofcomp.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: The Managed Object Format (MOF) Compiler Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2772 | mofcomp C:\Windows\TEMP\mf | C:\Windows\System32\wbem\mofcomp.exe | — | WmiPrvSE.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: The Managed Object Format (MOF) Compiler Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2868 | "C:\Windows\System32\cmd.exe" /c cscript.exe /b /e:VBScript.Encode C:\Windows\TEMP\xw2.tmp 579562847 & del /f/q C:\Windows\TEMP\xw2.tmp | C:\Windows\System32\cmd.exe | — | scrcons.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2888 | cscript.exe /b /e:VBScript.Encode C:\Windows\TEMP\xw2.tmp 579562847 | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3380 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3408 | C:\Windows\system32\wbem\scrcons.exe -Embedding | C:\Windows\System32\wbem\scrcons.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Standard Event Consumer - scripting Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3516 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" iex $env:EXVAR | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | scrcons.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
11 669
Read events
11 598
Write events
56
Delete events
15
Modification events
| (PID) Process: | (3700) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3700) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: Firefox | |||
| (PID) Process: | (3700) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
| (PID) Process: | (3700) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (3700) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3700) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3700) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (3700) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
| (PID) Process: | (3700) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (3700) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
8
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2888 | cscript.exe | C:\Windows\TEMP\onlyonceaddu240427.txt | text | |
MD5:6F8DB599DE986FAB7A21625B7916589C | SHA256:D5579C46DFCC7F18207013E65B44E4CB4E2C2298F4AC457BA8F82743F31E930B | |||
| 3516 | powershell.exe | C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 1168 | drvinst.exe | C:\Windows\INF\setupapi.ev3 | binary | |
MD5:9EBC654990CE1A767CA8B0FEC40AA488 | SHA256:9238AE2D3B756EB9BA37056F7F2869B460C7EA3AEAB6FE5831D2E00A51FBBC4F | |||
| 3408 | scrcons.exe | C:\Windows\temp\dfvt.log | text | |
MD5:1B6666BAA37AAE6ACA0AA1F481F3F2DB | SHA256:4CED55FC0F30E15033A9D620E9F9071A1448FF34792CE5ADBCD38A4BC53DA1B1 | |||
| 3408 | scrcons.exe | C:\Windows\TEMP\xw2.tmp | vbe | |
MD5:A1BFE3D65C10A7C736DE9CFB09490077 | SHA256:85B9FD2750571831FD1DCD22B11DA9C935F03DF98B9B854A91C3541D7EAE104A | |||
| 2888 | cscript.exe | C:\Windows\TEMP\onlyonceupmf0805.txt | text | |
MD5:6F8DB599DE986FAB7A21625B7916589C | SHA256:D5579C46DFCC7F18207013E65B44E4CB4E2C2298F4AC457BA8F82743F31E930B | |||
| 1168 | drvinst.exe | C:\Windows\INF\setupapi.ev2 | binary | |
MD5:2FE52592F516CEC700CDA4E84FC29CAA | SHA256:3B345047D3FDAF504E9AB049DC67240910B4BBA5087DE72992CFFE0244185B0F | |||
| 1168 | drvinst.exe | C:\Windows\INF\setupapi.ev1 | binary | |
MD5:60132FBCD9D75F3D5B5BE24655EF6561 | SHA256:83945B0EB90B2E7D6053429476130725EC3E4738DBC8F8452EBAEDEC7A34655A | |||
| 3516 | powershell.exe | C:\Windows\TEMP\utxa1hhp.vbl.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2888 | cscript.exe | C:\Windows\TEMP\mf | binary | |
MD5:2513EB59C3DB32A2D5EFBEDE6136A75D | SHA256:50D1B32CF53FE1B0822D2606AA397743D6069785BA0B03A3CAD52E63F84C90A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
17
DNS requests
10
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 2.19.126.137:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3408 | scrcons.exe | GET | 200 | 188.114.97.3:80 | http://d.mymst.top/ver | unknown | — | — | whitelisted |
3408 | scrcons.exe | GET | 200 | 188.114.96.3:80 | http://m.mymst.top/jl?info=53_53_58_59_47_47_47_58_54_48_51_57_48_54_59_48_59_55_60_53_53_58_59_47_47_47_73_119_103_117_118_47_47_47_56_48_51_47_47_47_54_101_114_119_47_47_47_75_112_118_103_110_42_84_43_34_69_113_116_103_42_86_79_43_34_107_55_47_56_54_50_50_34_69_82_87_34_66_34_52_48_57_50_73_74_124_74_113_119_116_117_47_47_47_112_113_110_113_105 | unknown | — | — | whitelisted |
3408 | scrcons.exe | GET | 200 | 172.67.178.106:80 | http://d.mymst007.info/s/h64endl2?e=1 | unknown | — | — | unknown |
3516 | powershell.exe | GET | 200 | 172.67.178.106:80 | http://d.mymst007.info/s/ps/istH64 | unknown | — | — | unknown |
2888 | cscript.exe | GET | 200 | 172.67.178.106:80 | http://d.mymst007.info/f/w/mf | unknown | — | — | unknown |
2888 | cscript.exe | GET | 200 | 172.67.178.106:80 | http://d.mymst007.info/pc?info=3389---4---0409---Guest | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1372 | svchost.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
1060 | svchost.exe | 2.19.126.137:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
d.mymst.top |
| malicious |
ifconfig.me |
| shared |
m.mymst.top |
| malicious |
d.mymst007.info |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
1060 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Lookup Domain (ifconfig .me) |
3408 | scrcons.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
3408 | scrcons.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL/TLS Certificate (ifconfig .me) |
3516 | powershell.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Get-CimInstance Cmdlet has been detected |
3516 | powershell.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Get-WmiObject Cmdlet has been detected |
3408 | scrcons.exe | Misc activity | ET INFO Microsoft Script Encoder Encoded File |