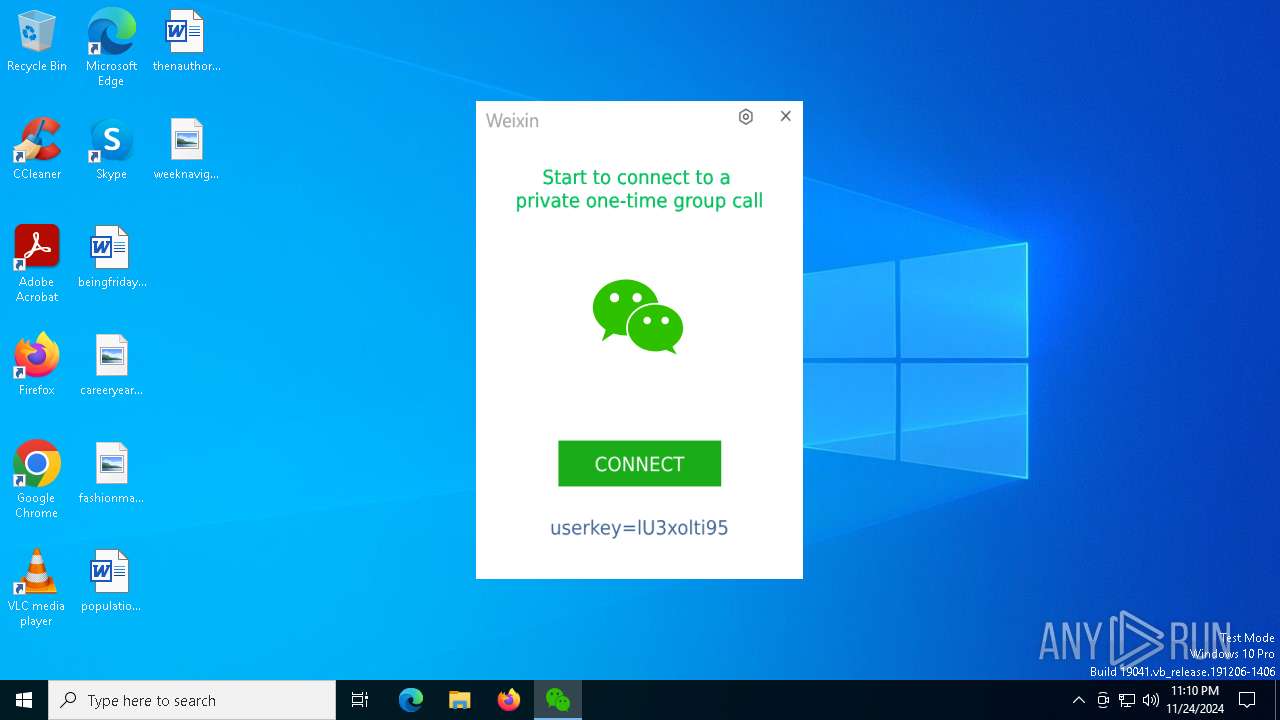
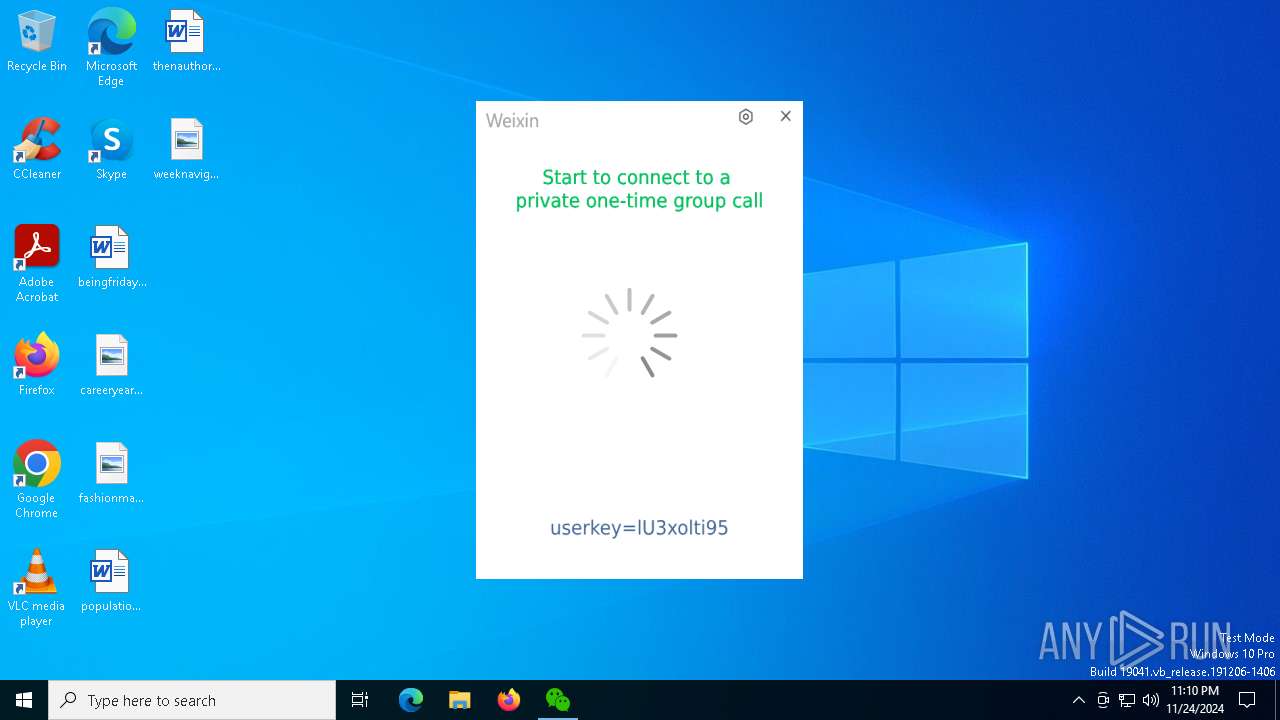
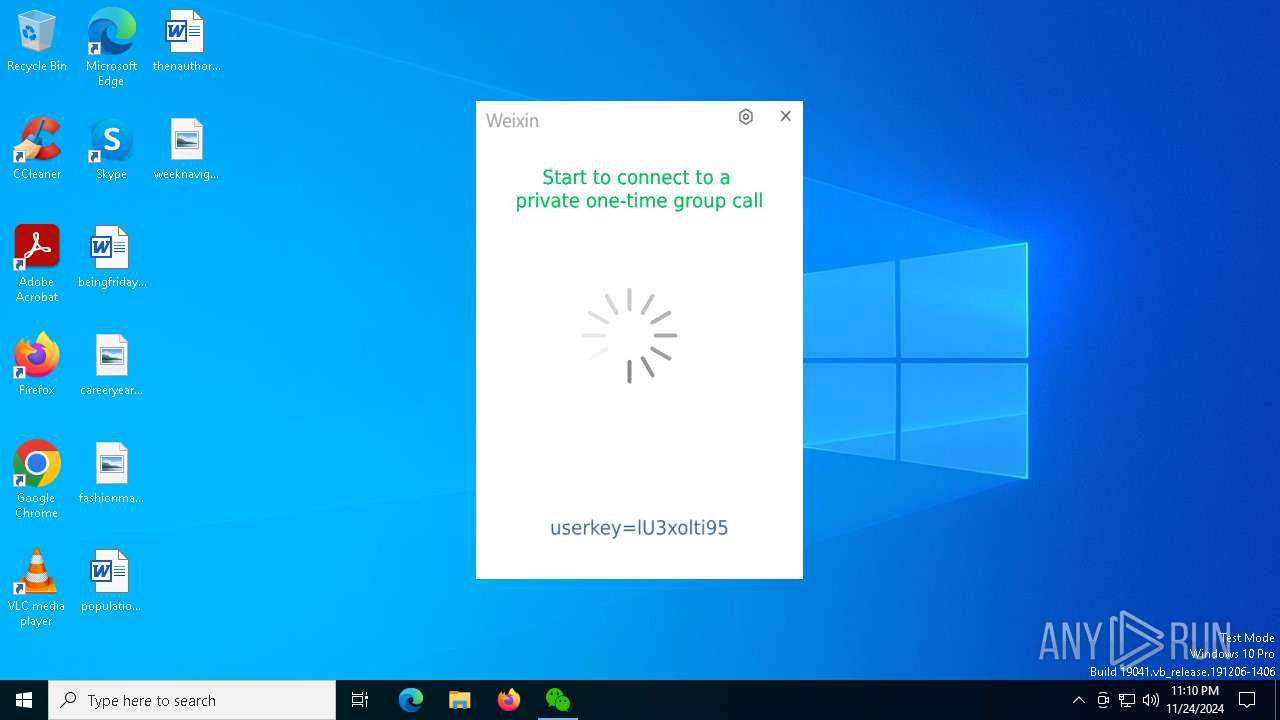
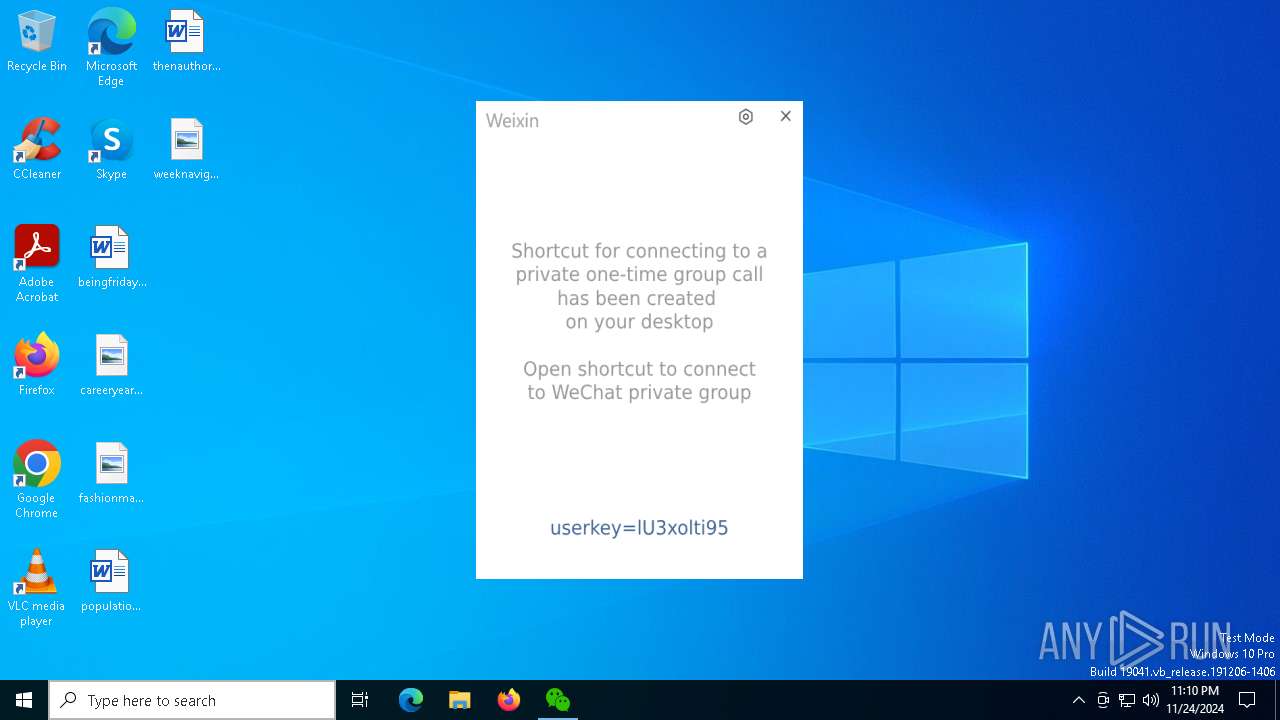
| File name: | Weixin.exe |
| Full analysis: | https://app.any.run/tasks/42b43146-4532-42a4-bd96-fd7e781b8499 |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2024, 23:09:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2261DEC5F4D72906BCFE361188B2A549 |
| SHA1: | CBE47647DC22213C053A813808DDB099269A4EB9 |
| SHA256: | 50CF2DA7225C5E1FBDB44DEE6B8106B4B9A79DDE48B5C62D3E086856FDC473E4 |
| SSDEEP: | 98304:9vflLNAnM/Qf2osA7LE7dVgzZdY3flN+mYZFmvy1hJ7DE9N7TmnETlE+Wd6YH2BA:hv0fzJ |
MALICIOUS
Changes the autorun value in the registry
- Wallet.exe (PID: 2164)
SUSPICIOUS
Reads security settings of Internet Explorer
- Weixin.exe (PID: 4624)
Executable content was dropped or overwritten
- Weixin.exe (PID: 4624)
- ScreenShot.exe (PID: 4976)
- SendBugReportNew.exe (PID: 6188)
Starts itself from another location
- ScreenShot.exe (PID: 4976)
- SendBugReportNew.exe (PID: 6188)
Starts CMD.EXE for commands execution
- ScreenShot.exe (PID: 2160)
- SendBugReportNew.exe (PID: 6208)
Connects to unusual port
- Wallet.exe (PID: 2164)
- OpenWith.exe (PID: 6612)
The process checks if it is being run in the virtual environment
- OpenWith.exe (PID: 6612)
INFO
Checks supported languages
- Weixin.exe (PID: 4624)
- Ledger.exe (PID: 5160)
- ScreenShot.exe (PID: 4976)
- ScreenShot.exe (PID: 2160)
- SendBugReportNew.exe (PID: 6188)
- SendBugReportNew.exe (PID: 6208)
- Wallet.exe (PID: 2164)
Reads the machine GUID from the registry
- Weixin.exe (PID: 4624)
- Ledger.exe (PID: 5160)
- Wallet.exe (PID: 2164)
Reads the computer name
- Weixin.exe (PID: 4624)
- Ledger.exe (PID: 5160)
- ScreenShot.exe (PID: 4976)
- ScreenShot.exe (PID: 2160)
- Wallet.exe (PID: 2164)
- SendBugReportNew.exe (PID: 6188)
- SendBugReportNew.exe (PID: 6208)
Process checks computer location settings
- Weixin.exe (PID: 4624)
Create files in a temporary directory
- Weixin.exe (PID: 4624)
- ScreenShot.exe (PID: 2160)
- SendBugReportNew.exe (PID: 6208)
The process uses the downloaded file
- Weixin.exe (PID: 4624)
Creates files or folders in the user directory
- ScreenShot.exe (PID: 4976)
- SendBugReportNew.exe (PID: 6188)
Disables trace logs
- Wallet.exe (PID: 2164)
Checks proxy server information
- Wallet.exe (PID: 2164)
Manual execution by a user
- OpenWith.exe (PID: 6612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2068:03:20 08:31:23+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 6864896 |
| InitializedDataSize: | 17408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x68de5a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Weixin |
| FileVersion: | 1.0.0.0 |
| InternalName: | Weixin.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | Weixin.exe |
| ProductName: | Weixin |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
136
Monitored processes
14
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1140 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | ScreenShot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2160 | C:\Users\admin\AppData\Roaming\cloudValid\ScreenShot.exe | C:\Users\admin\AppData\Roaming\cloudValid\ScreenShot.exe | — | ScreenShot.exe | |||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: ScreenShot Exit code: 1 Version: 1.0.0.57 Modules
| |||||||||||||||
| 2164 | "C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm\Wallet.exe" | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm\Wallet.exe | Weixin.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Wallet Version: 1.0.0.0 Modules
| |||||||||||||||
| 4624 | "C:\Users\admin\AppData\Local\Temp\Weixin.exe" | C:\Users\admin\AppData\Local\Temp\Weixin.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Weixin Version: 1.0.0.0 Modules
| |||||||||||||||
| 4976 | "C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm\ScreenShot.exe" | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm\ScreenShot.exe | Weixin.exe | ||||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: ScreenShot Exit code: 0 Version: 1.0.0.57 Modules
| |||||||||||||||
| 5160 | "C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\Ledger.exe" | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\Ledger.exe | — | Weixin.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Ledger Version: 1.0.0.0 Modules
| |||||||||||||||
| 6188 | "C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm2\SendBugReportNew.exe" | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm2\SendBugReportNew.exe | Weixin.exe | ||||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: Send Bug Report Exit code: 0 Version: 10.0.10.101 Modules
| |||||||||||||||
| 6208 | C:\Users\admin\AppData\Roaming\DYFUpload_beta\SendBugReportNew.exe | C:\Users\admin\AppData\Roaming\DYFUpload_beta\SendBugReportNew.exe | — | SendBugReportNew.exe | |||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: Send Bug Report Exit code: 1 Version: 10.0.10.101 Modules
| |||||||||||||||
| 6232 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | SendBugReportNew.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 713
Read events
1 697
Write events
16
Delete events
0
Modification events
| (PID) Process: | (2164) Wallet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Wallet_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2164) Wallet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Wallet_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2164) Wallet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Wallet_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2164) Wallet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Wallet_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2164) Wallet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Wallet_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2164) Wallet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Wallet_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2164) Wallet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Wallet_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2164) Wallet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Wallet_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2164) Wallet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Wallet_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2164) Wallet.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Wallet_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
20
Suspicious files
16
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4624 | Weixin.exe | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\Ledger.exe | executable | |
MD5:9C1F8C62751CAA79FA028172335F3DE4 | SHA256:34577A531DE5E6DD14EE9BE8088AB313FC20CA2C2756F219E89A1AFC355AB7E2 | |||
| 4624 | Weixin.exe | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm2\imgmc | binary | |
MD5:A2A3A9321F48E30B5BF35E05E1DDEC59 | SHA256:48406E16D210599BCBBA894A8FE87D00CC024448FA4D1F8D0E738C65599207E2 | |||
| 4624 | Weixin.exe | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm2\mmpryv | binary | |
MD5:8D408479D9E62FFF58F46D6D9789210E | SHA256:82CD2319511238615293F1E60941D16C6AC69BF683045B79BCD712FFE6CC3C34 | |||
| 4624 | Weixin.exe | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm\madbasic_.bpl | executable | |
MD5:A734F2428443030C46DB9CE3AB2E68A6 | SHA256:038511FC64801BE03D8472A2F7A6BA8A27E0398CF876BE1427C1463CF9190C80 | |||
| 4624 | Weixin.exe | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm.zip | compressed | |
MD5:60BBFB264A104B3E336DDF92B7EF9127 | SHA256:5FA11A24E71F0C5020D72B68E6AB555C6FF30A10B13AF0A9BC748542B4955280 | |||
| 4624 | Weixin.exe | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm2\vcl120.bpl | binary | |
MD5:1B6A18A0E44E1CFE1D879EE51FB43A1E | SHA256:0EFF72741529CD583D33B9FD7F7F3869537E9E4A4687448DAFF3720576BECECA | |||
| 4624 | Weixin.exe | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm\madexcept_.bpl | executable | |
MD5:562EC96D0F65B0309AD7508D0E0CED11 | SHA256:FB64A5954B726D2D0F0BC26113A36DC8A86C469AF994CEEAF2E2609743A0A557 | |||
| 4624 | Weixin.exe | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm\aolnxqs | binary | |
MD5:2508BAC99E582FF36AFBF4824892189C | SHA256:77CCED323FF30515230A88DC6E3473793FF2EDFD28C06C40DE0F7787E50F8E59 | |||
| 4624 | Weixin.exe | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm\cgul | binary | |
MD5:7EDE6EF0BA61BF801AB8F17AA7F862F3 | SHA256:516035C29604F783BE1BB8101EC04400F1C8A8E707F3B2DE975D0650F14CC25D | |||
| 4624 | Weixin.exe | C:\Users\admin\AppData\Local\Temp\WeixinTemp\e7f6099a-a9d7-4ed8-aceb-2a6af175bc1f\XForm2\rtl120.bpl | executable | |
MD5:E71E48E31AC728A6DE7C020645F0C32F | SHA256:40A1D1A2F276738F568700DDCCAC99CDCD35B973FC8BE86AB826C0D1ABC9D6FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
39
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5572 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6364 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6364 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5776 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1176 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |