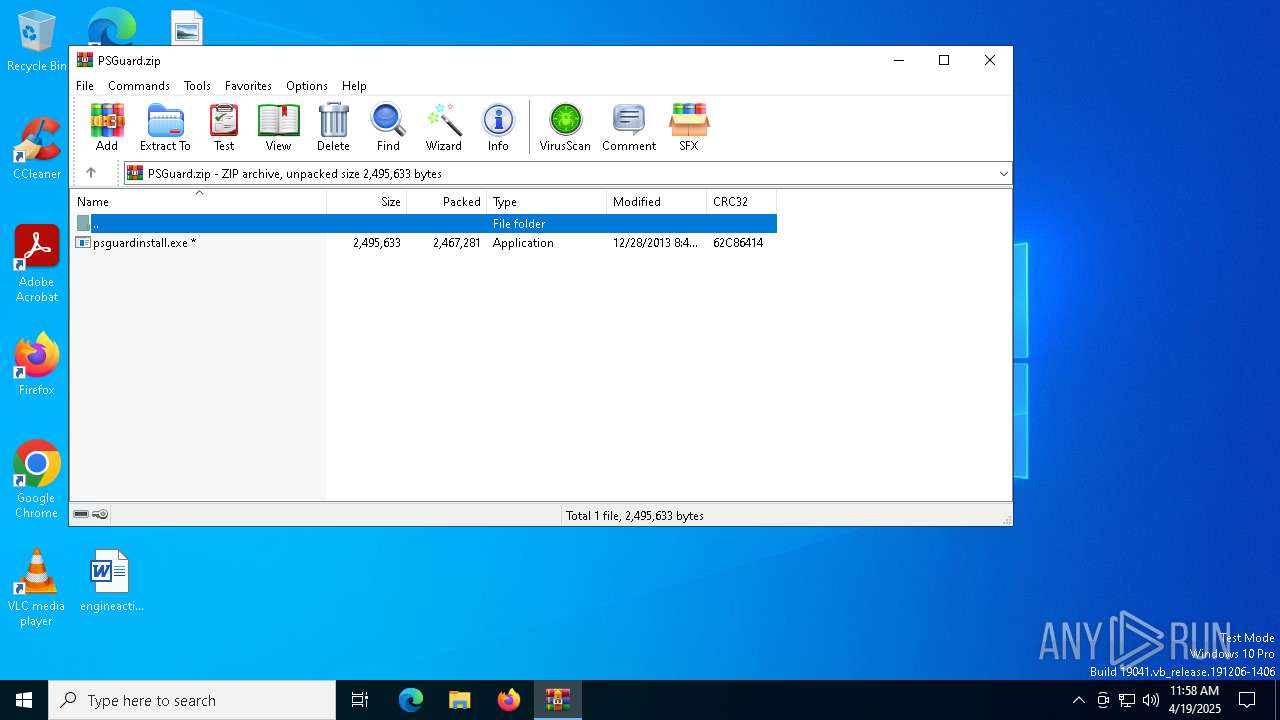
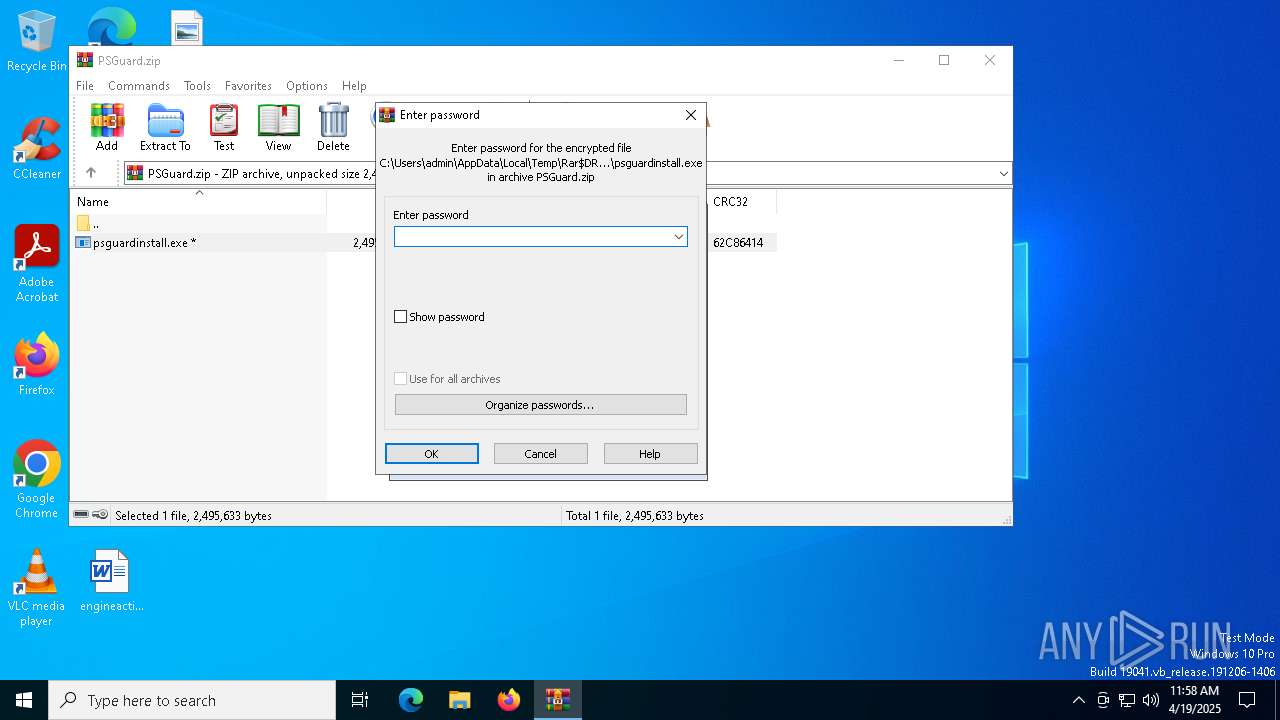
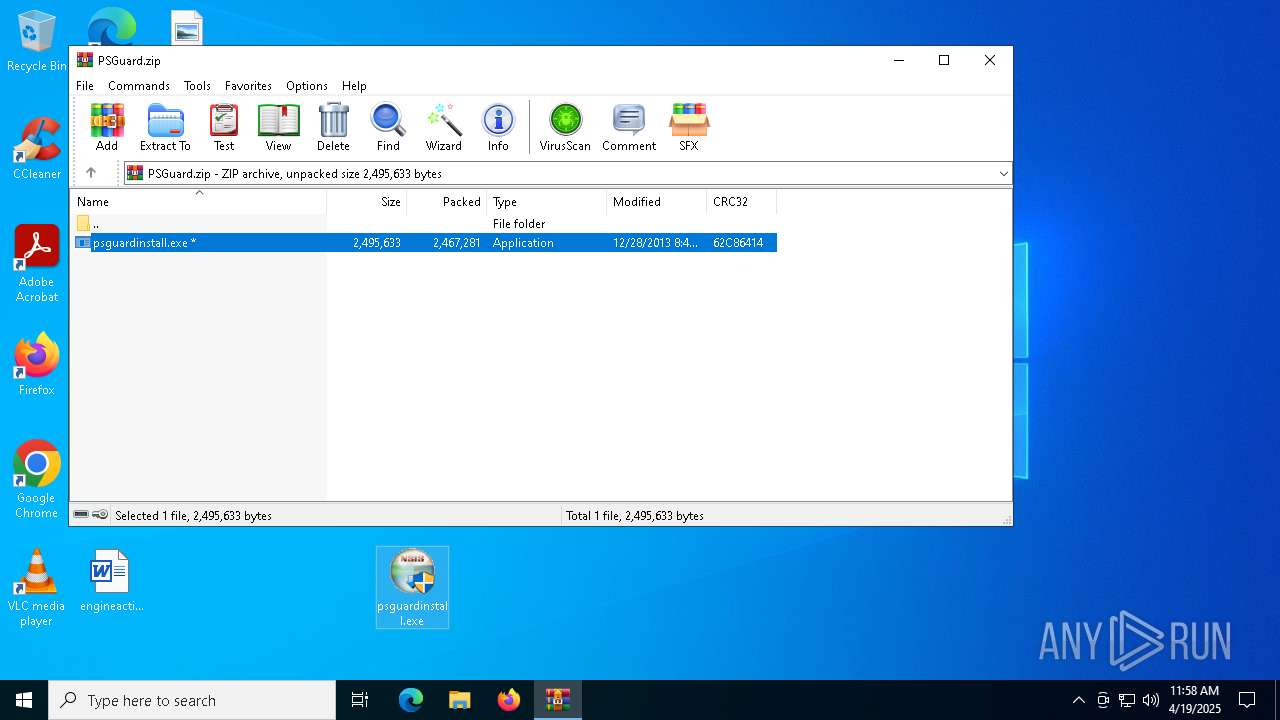
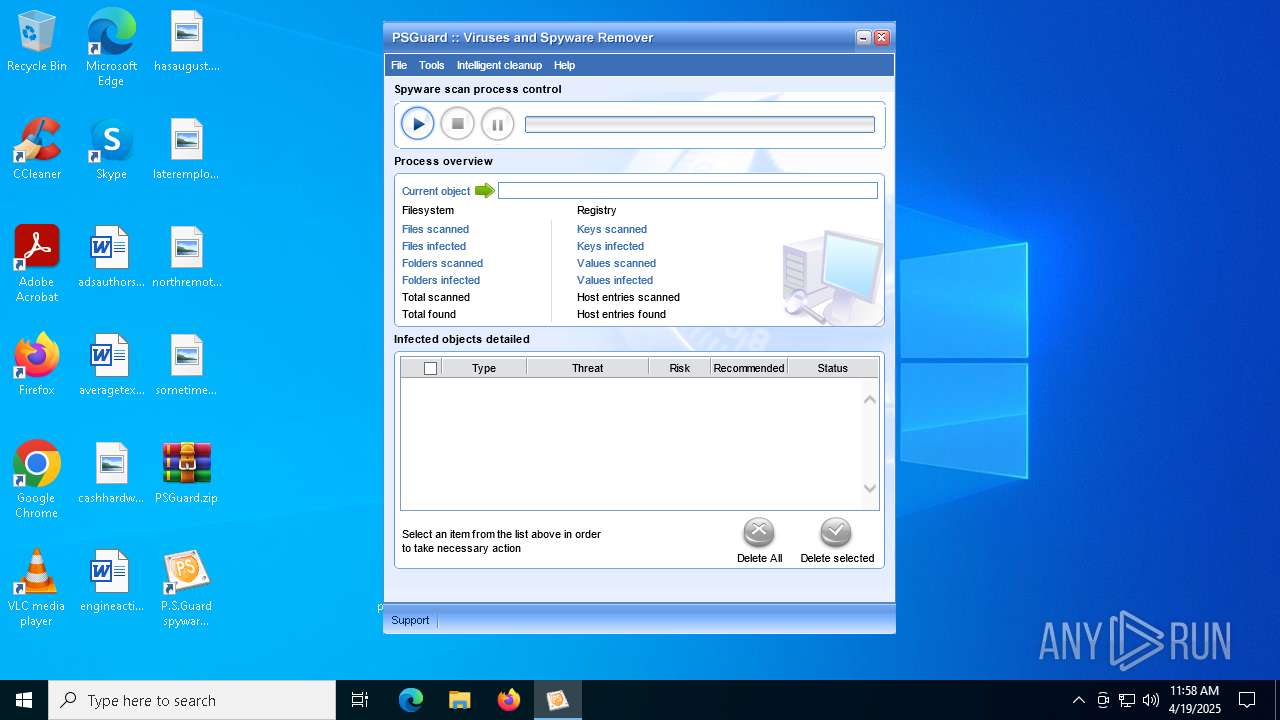
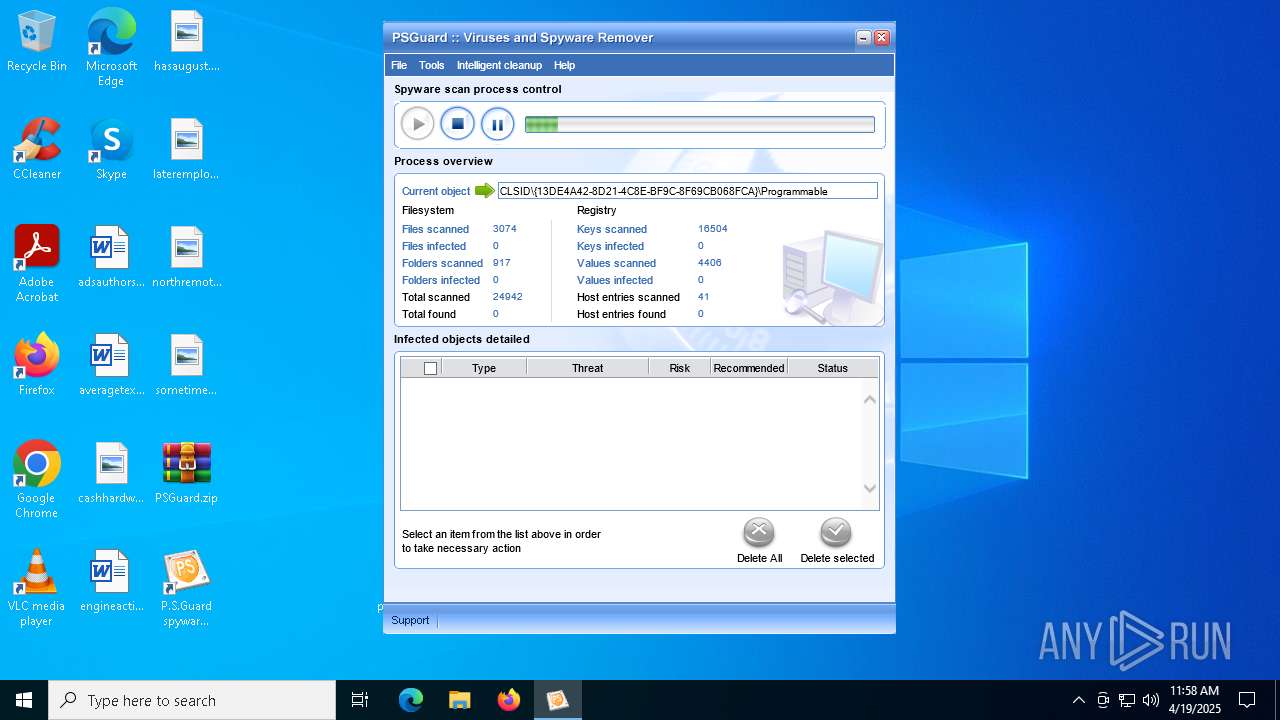
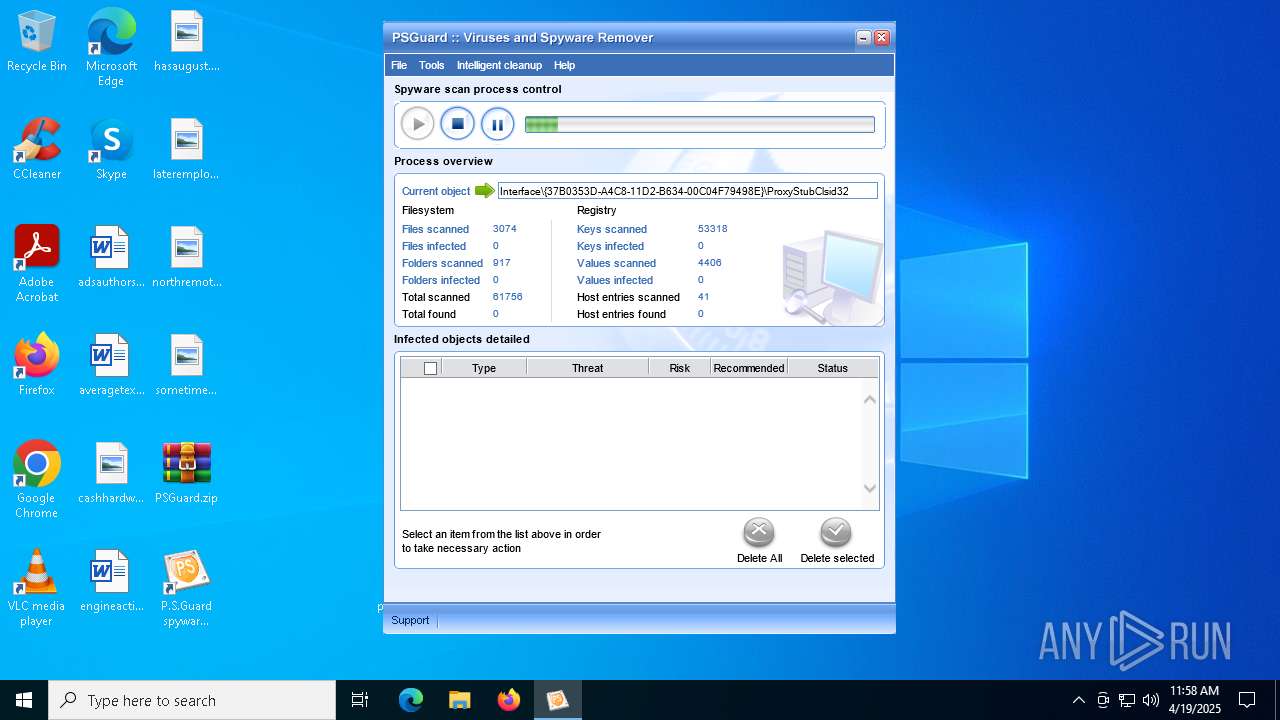
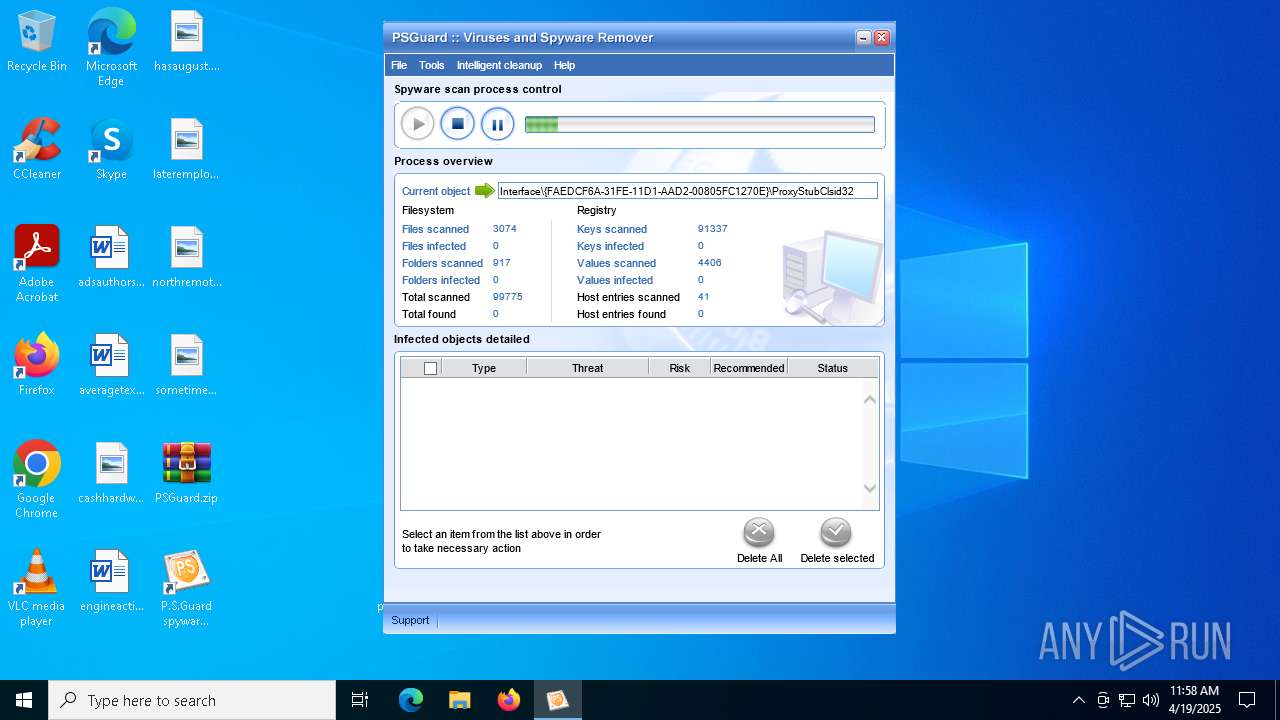
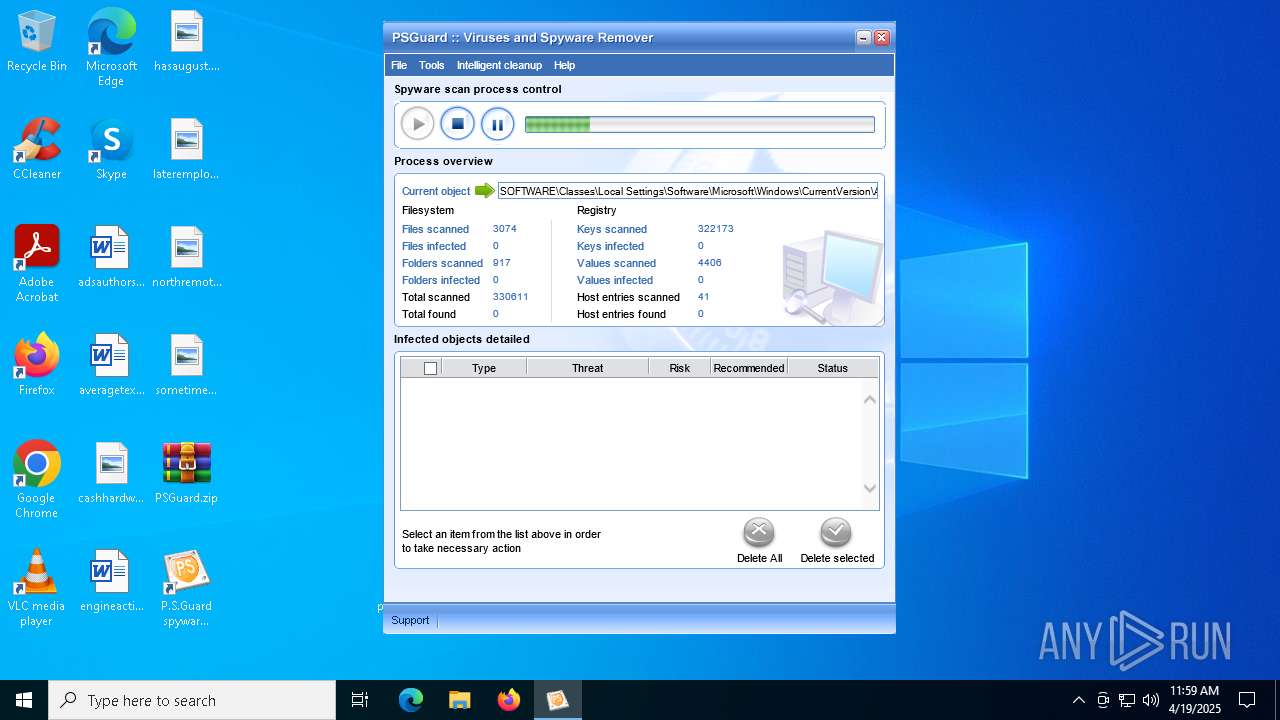
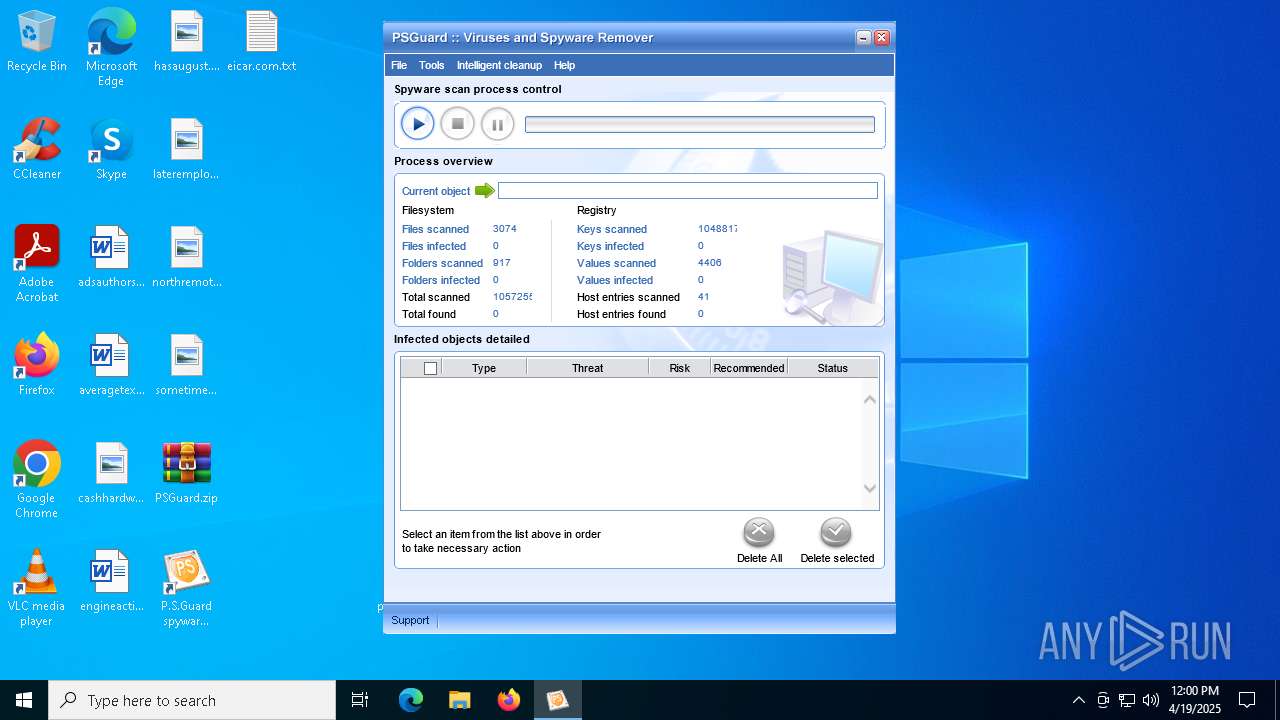
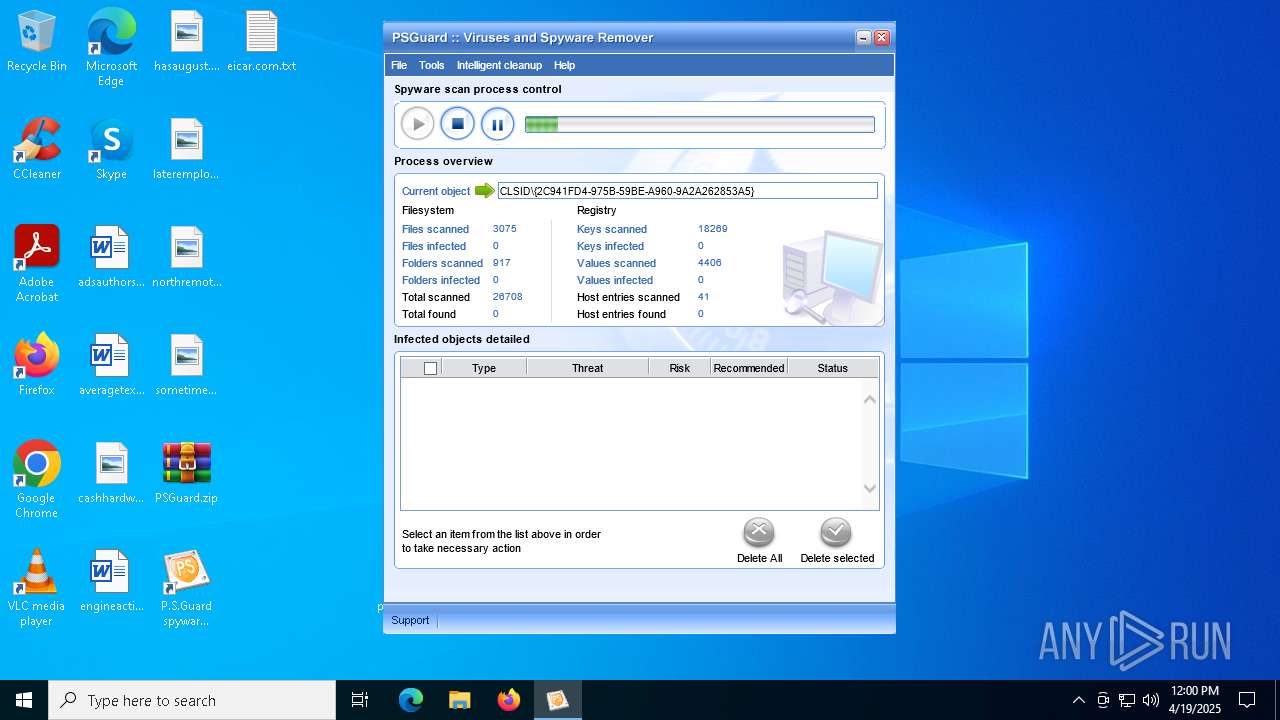
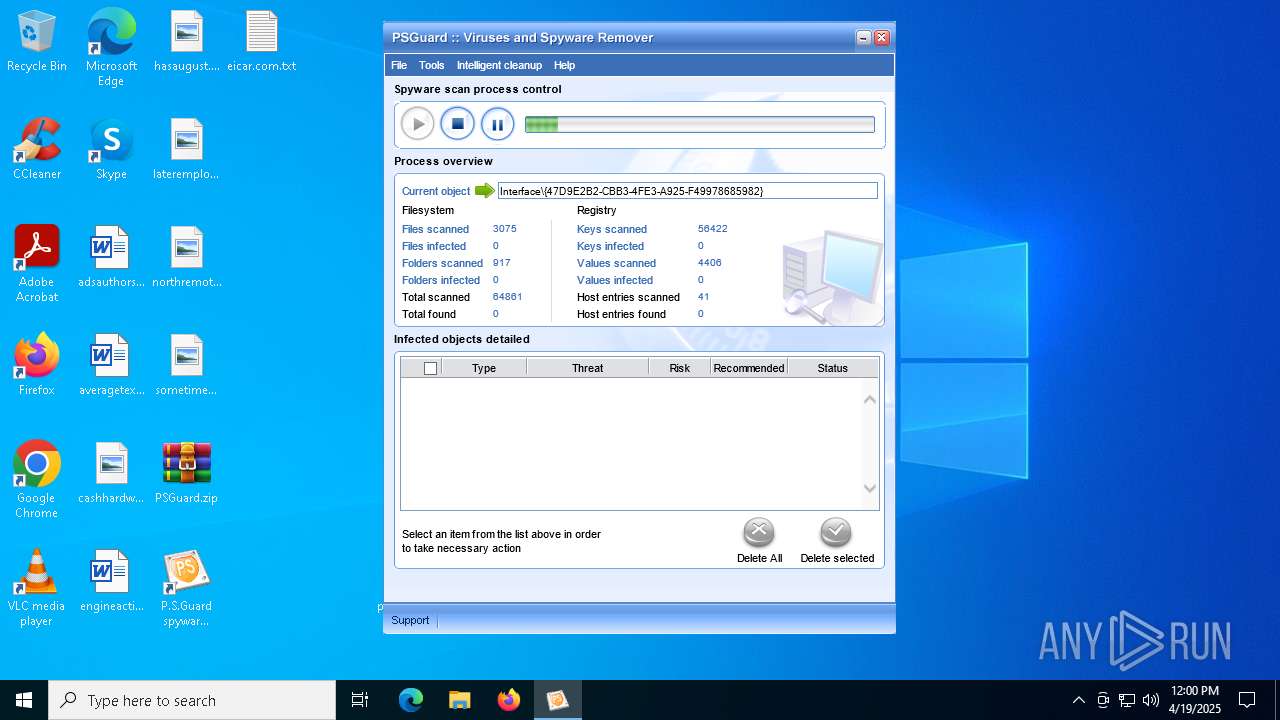
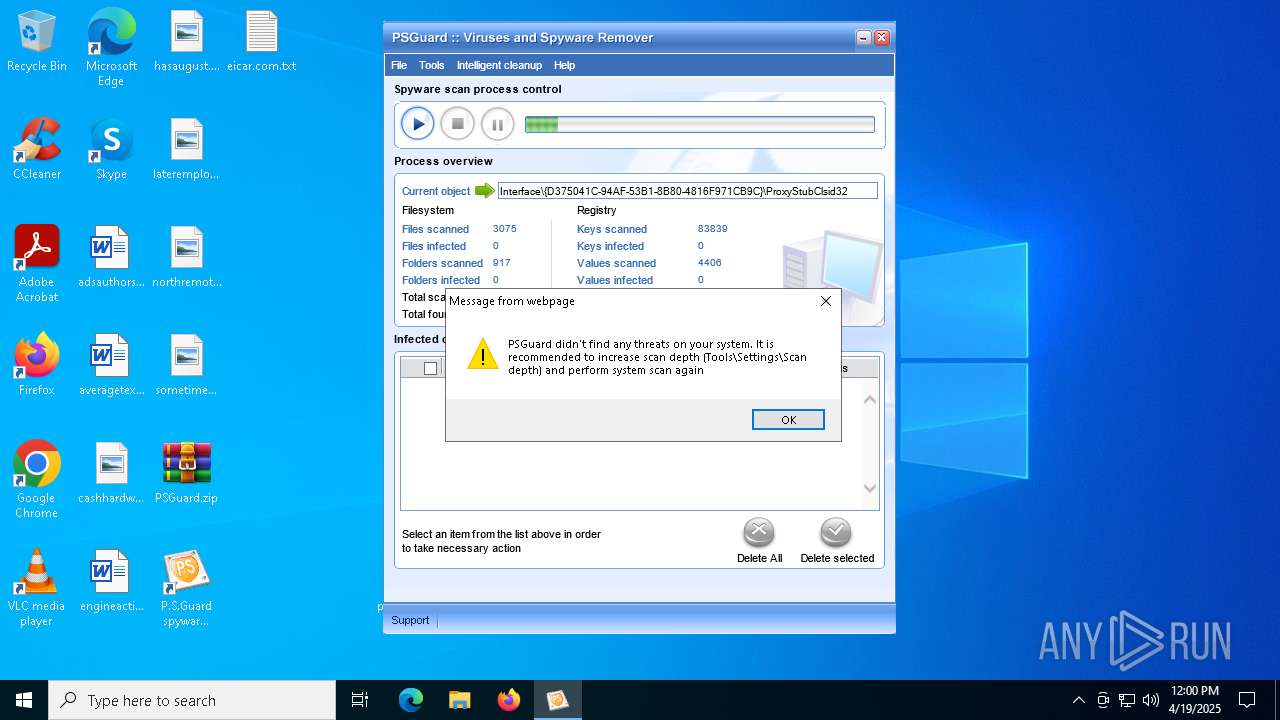
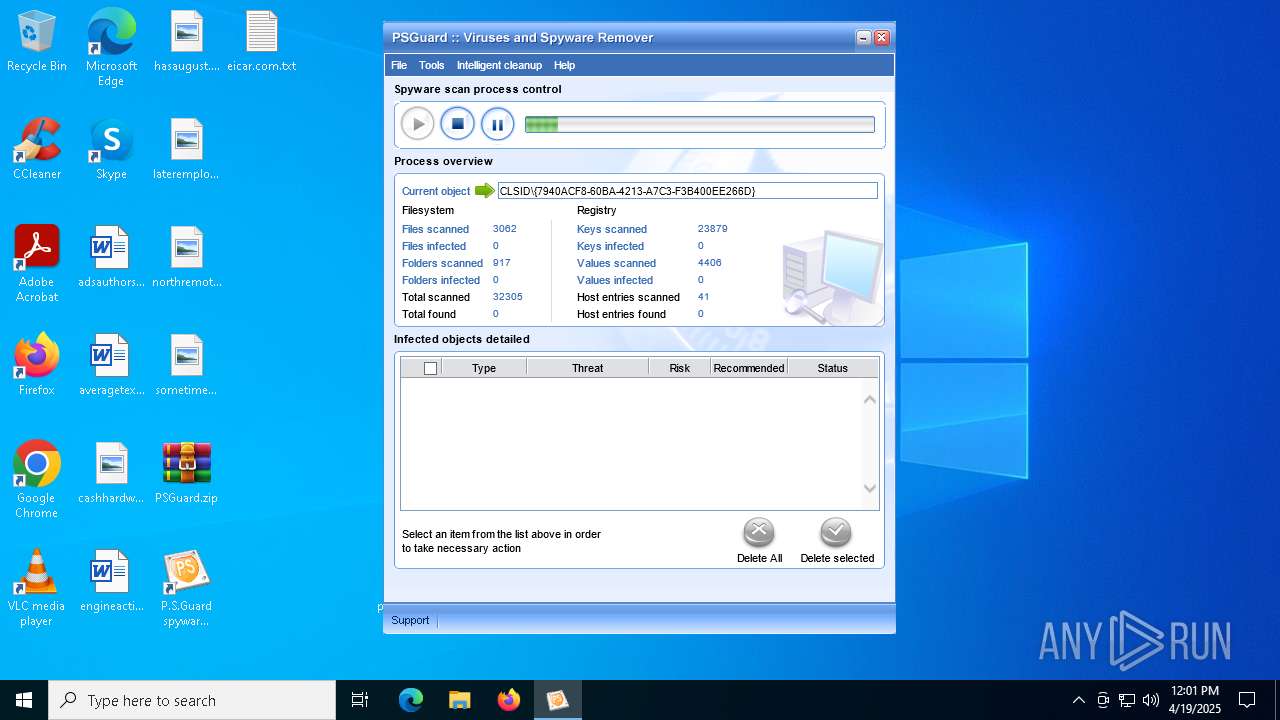
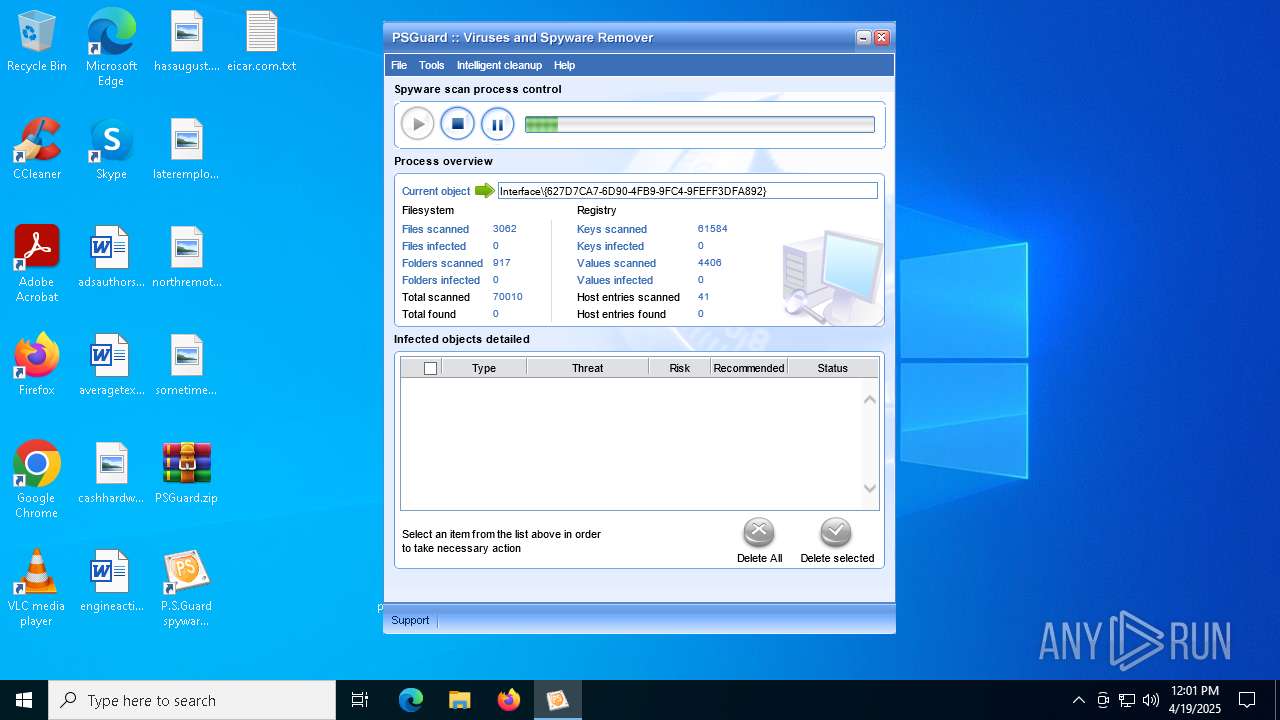
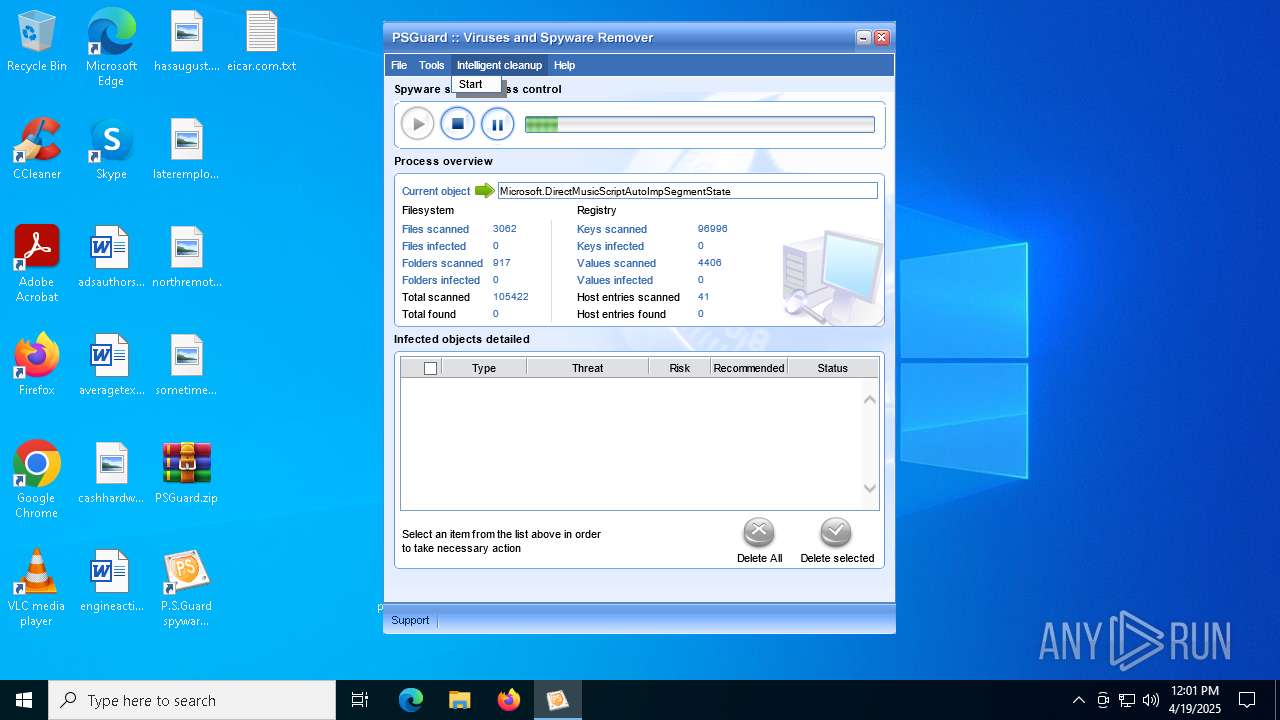
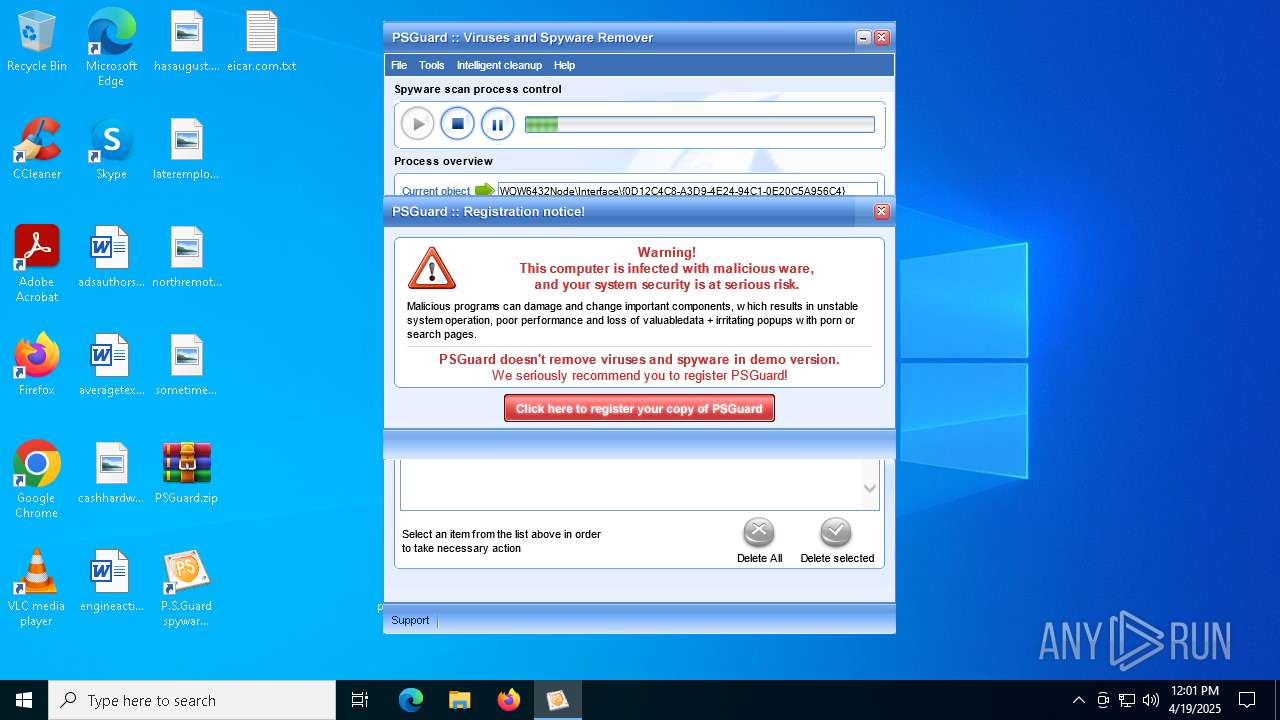
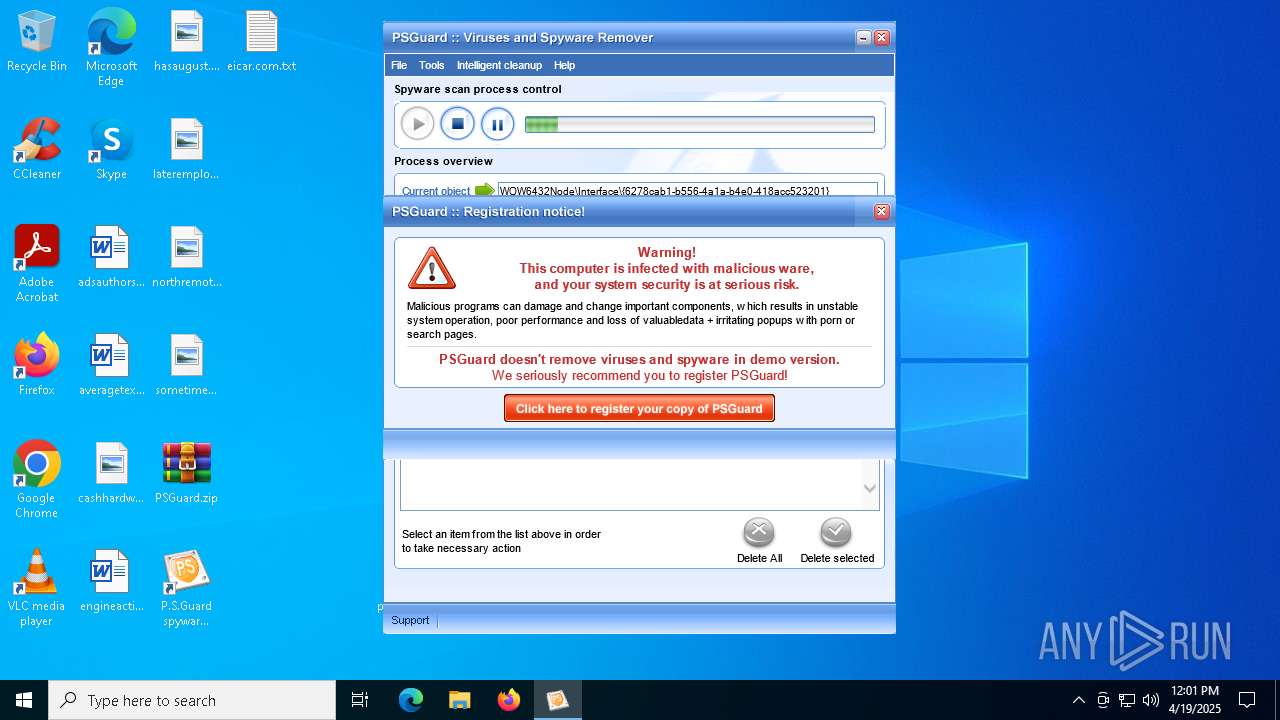
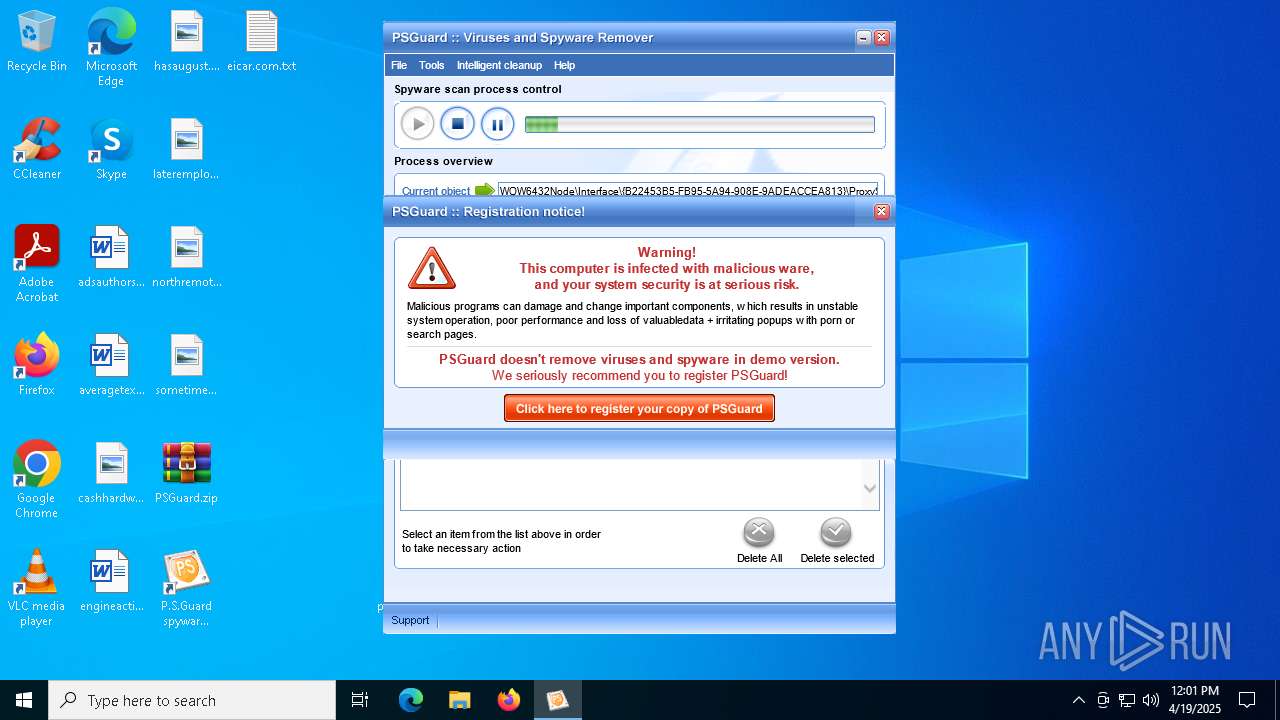
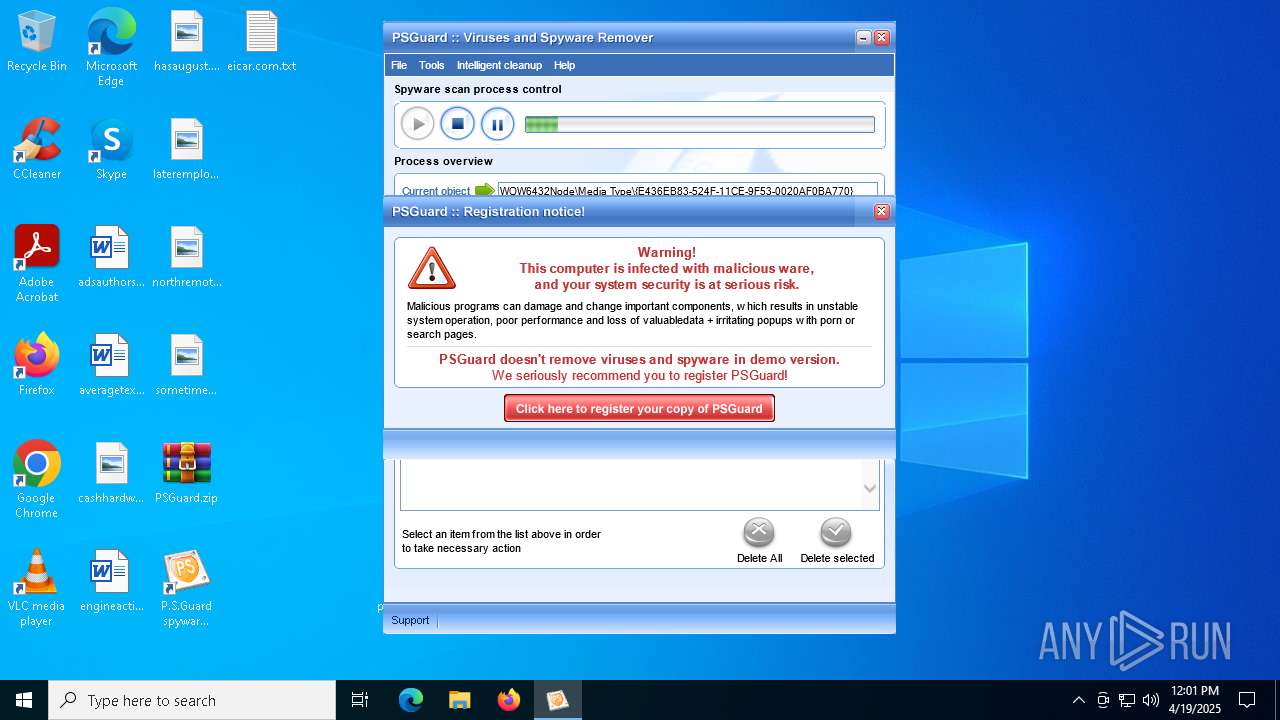
| File name: | PSGuard.zip |
| Full analysis: | https://app.any.run/tasks/d613a6dd-27fb-4dd5-a31e-76787d9218b3 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 11:58:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | C9952C335F0A39A91CAC7BFFE3312552 |
| SHA1: | DD013D9007048254CE198DB99956900272844628 |
| SHA256: | 50B9BF0FF90F9AD61DF3913AECBDA95B53032789F65C495BD4B6F93D707BB383 |
| SSDEEP: | 98304:nPZPZ91W4JtQFOrGcrdJVXZBl05w4rpORhwNaliMDlZSLhwCllBdPnVfIwBTCLbD:d/xh |
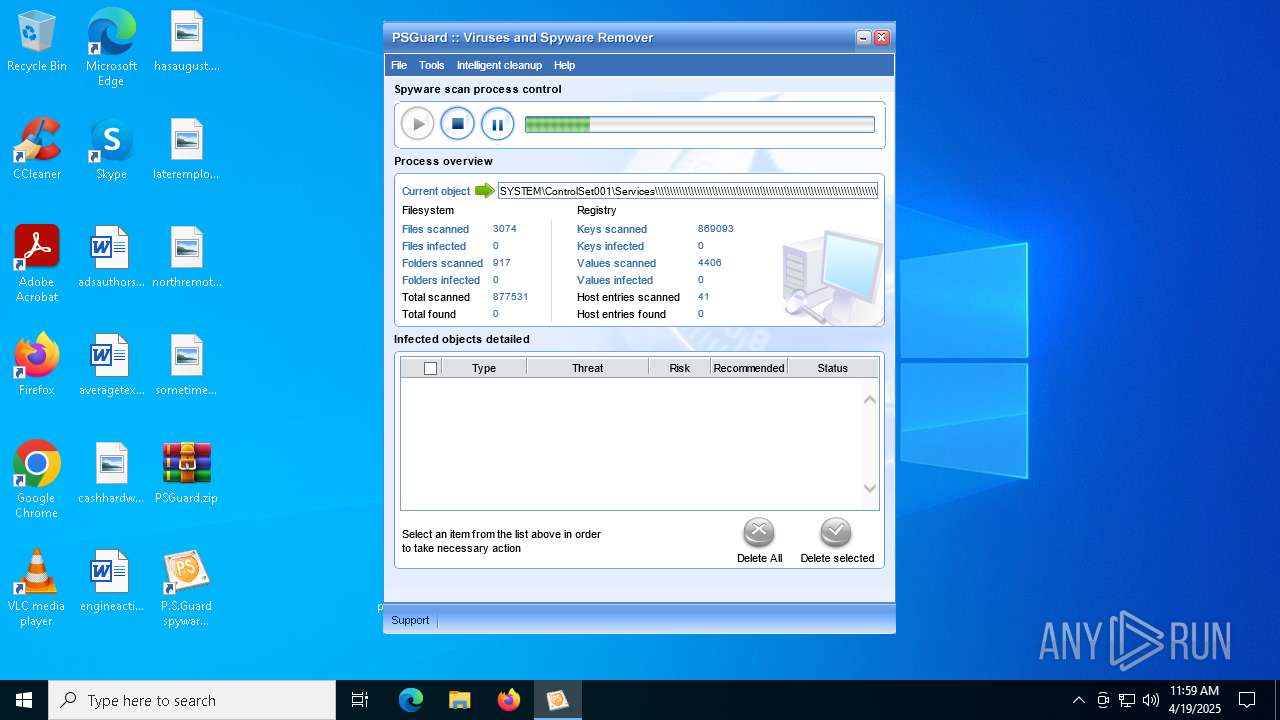
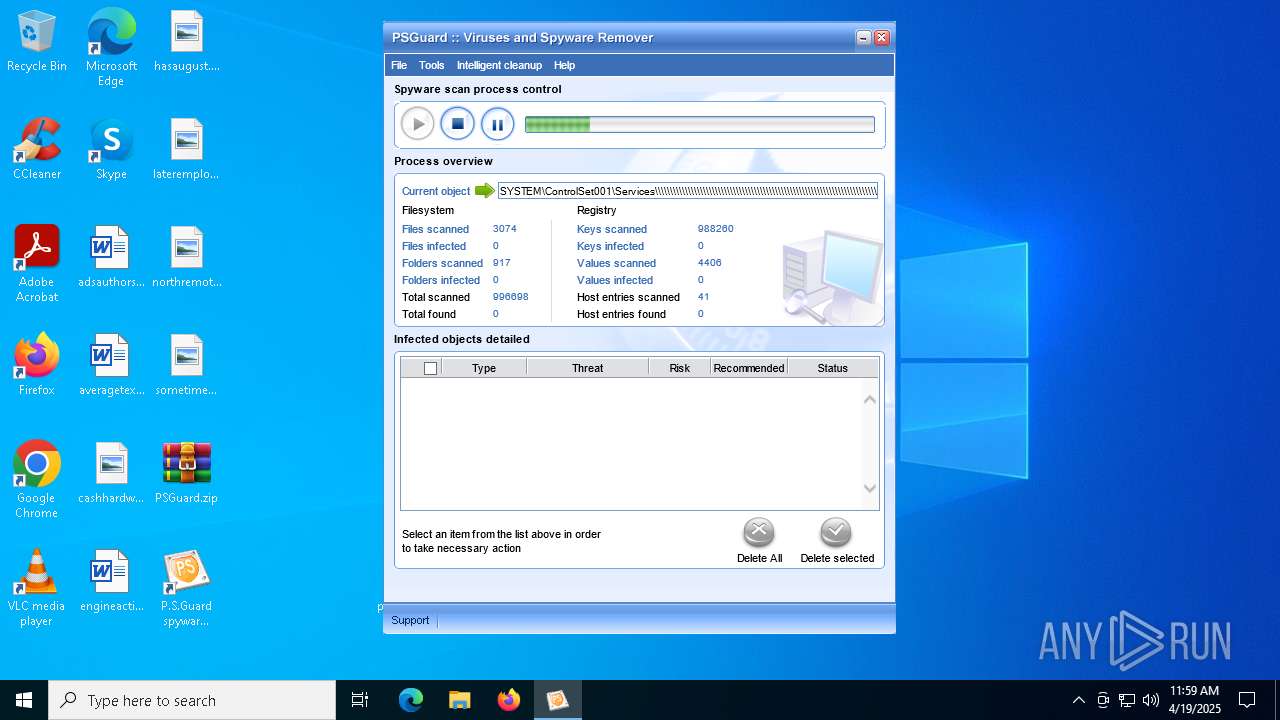
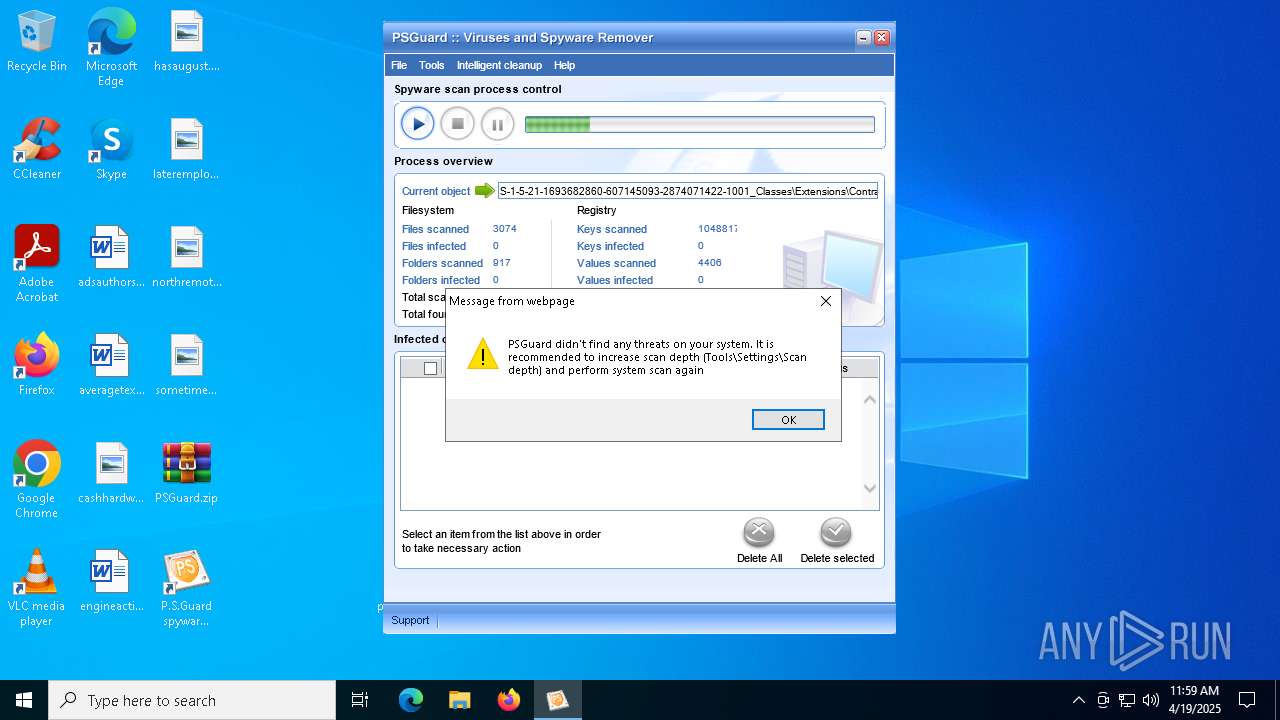
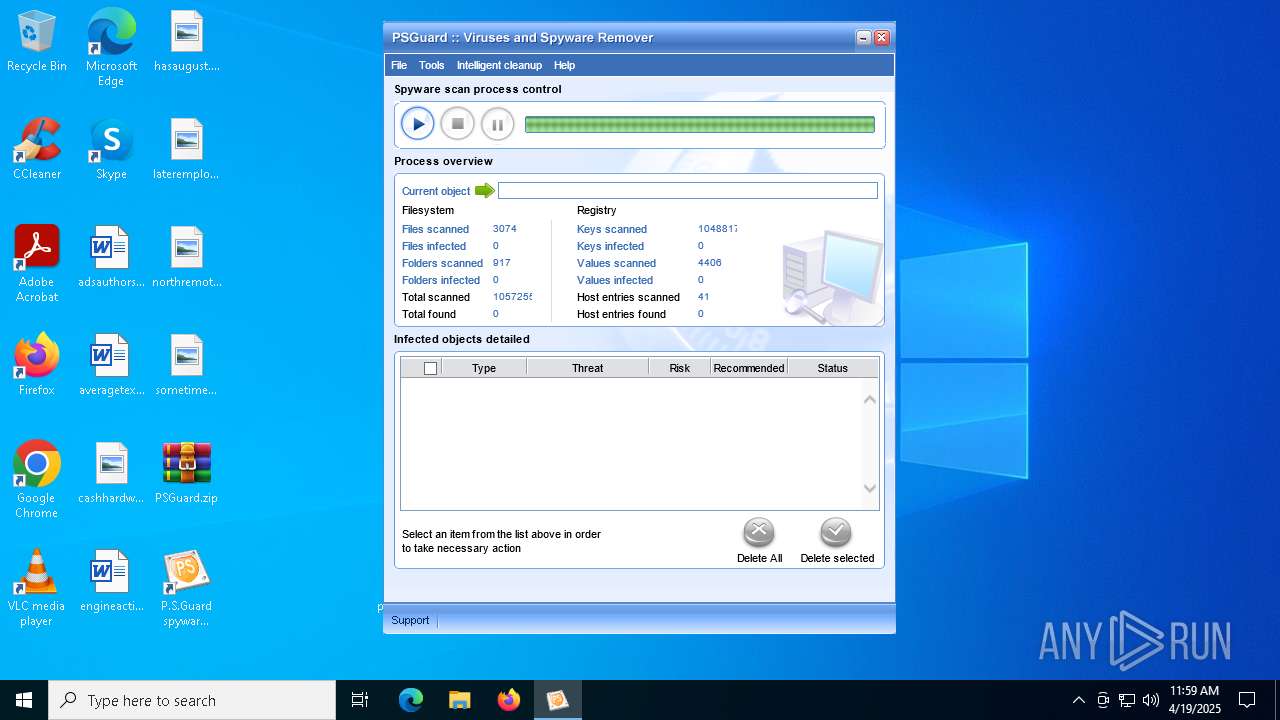
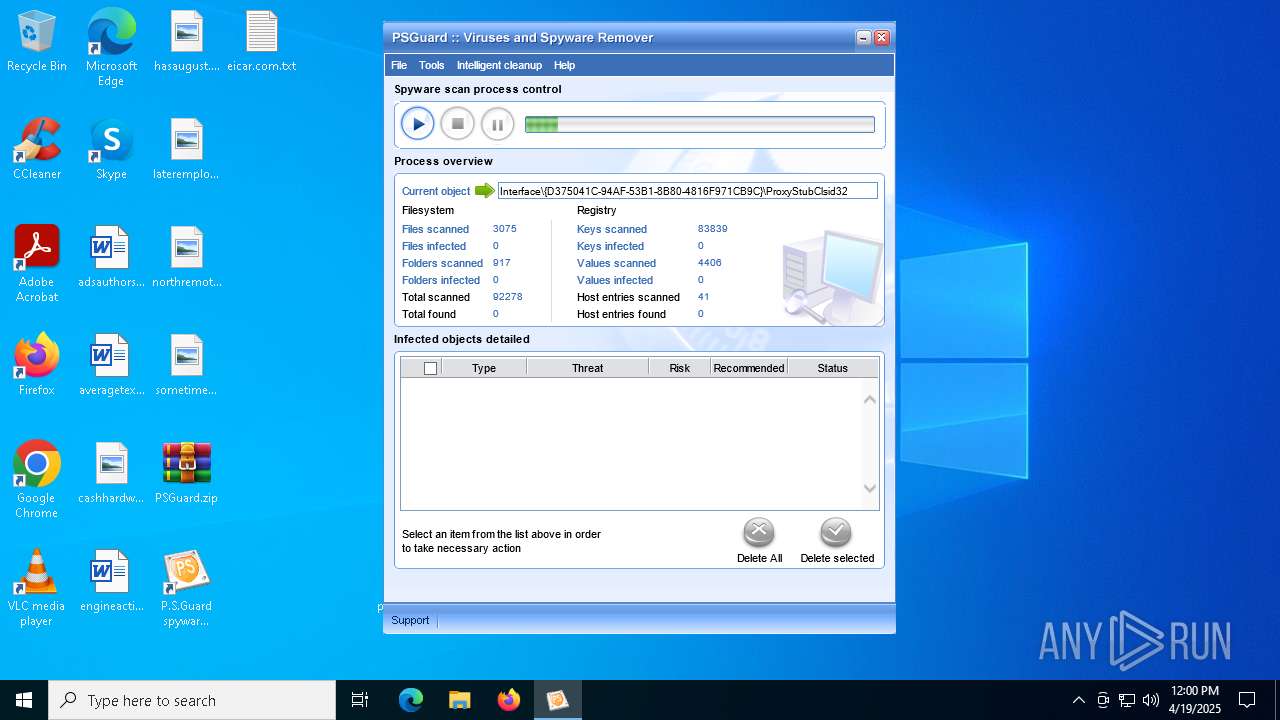
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7408)
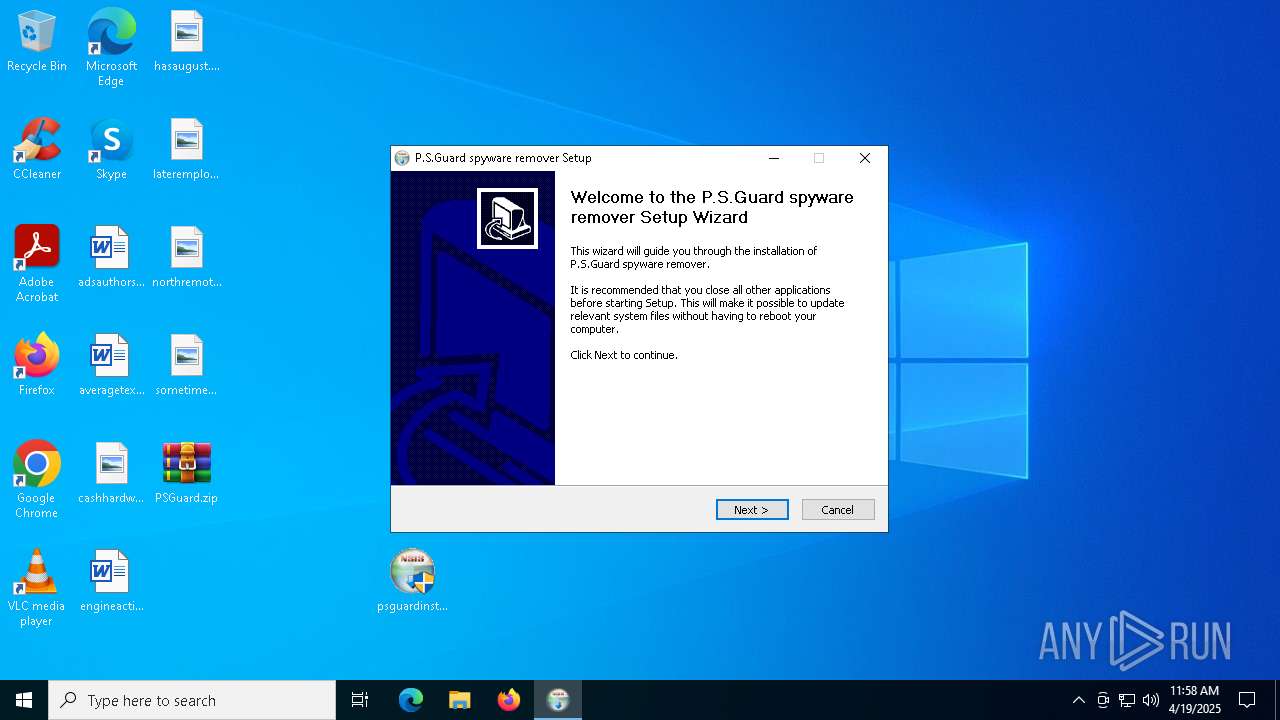
Changes the autorun value in the registry
- psguardinstall.exe (PID: 8064)
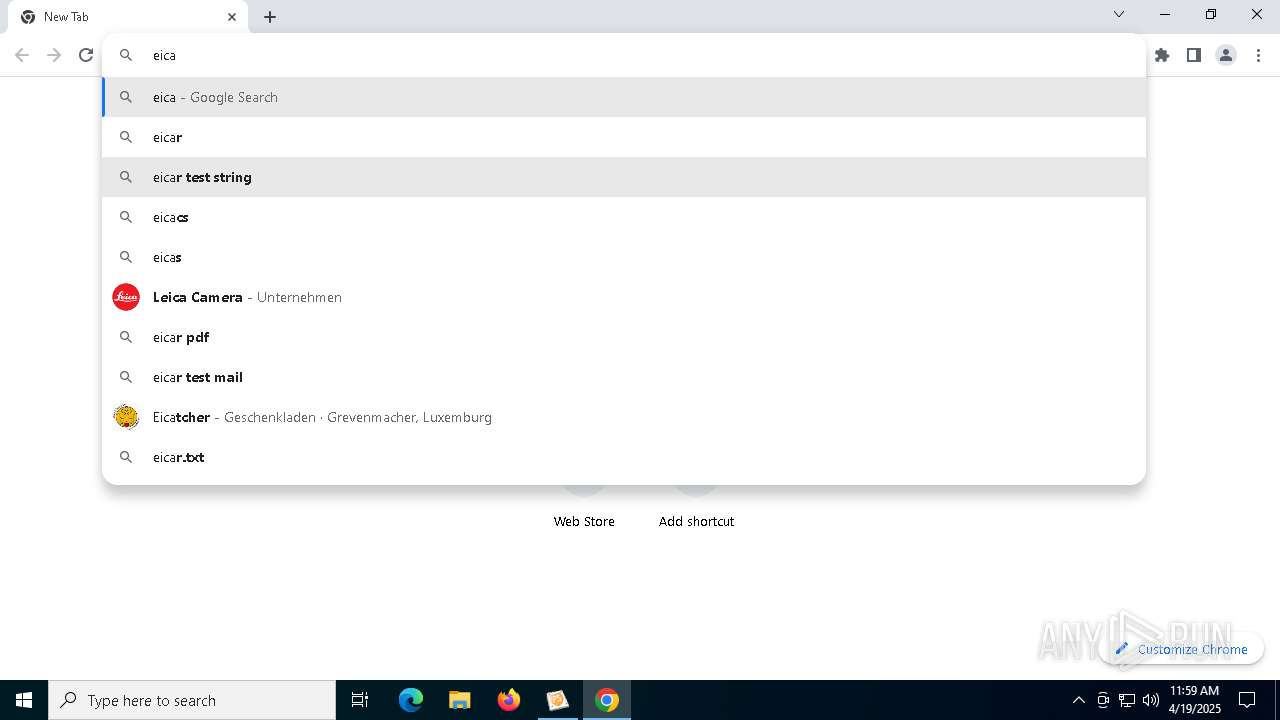
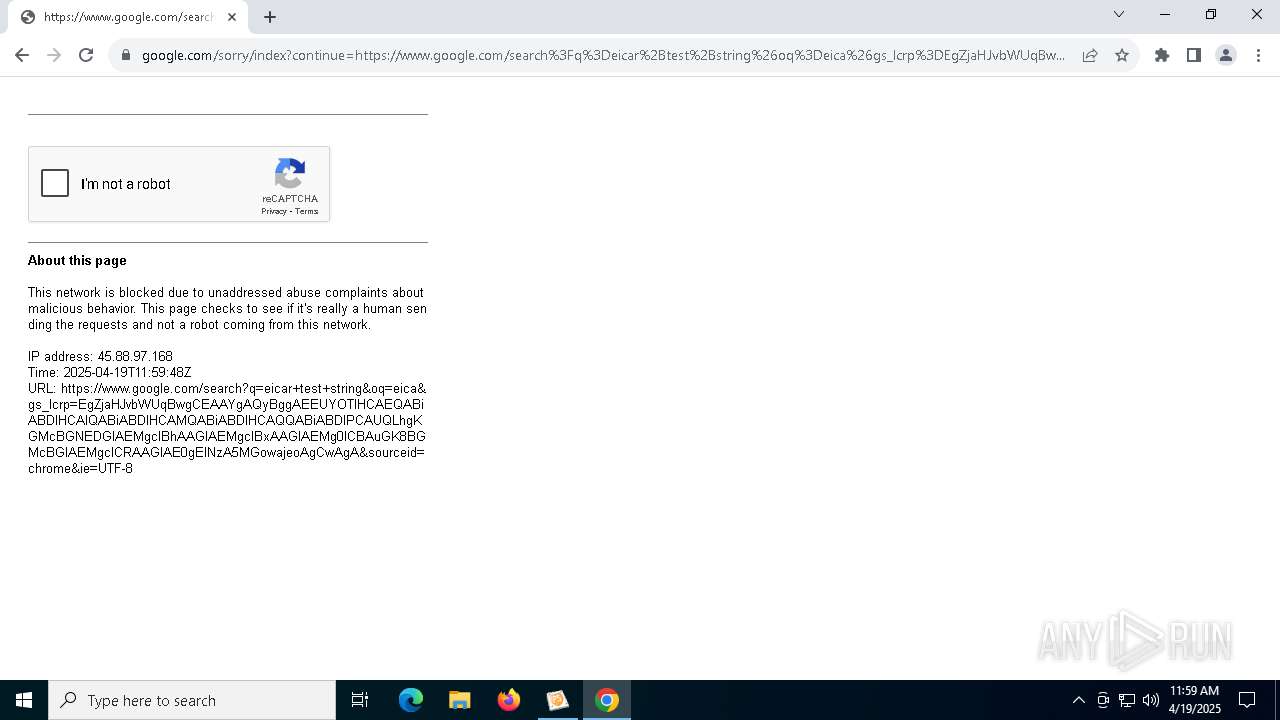
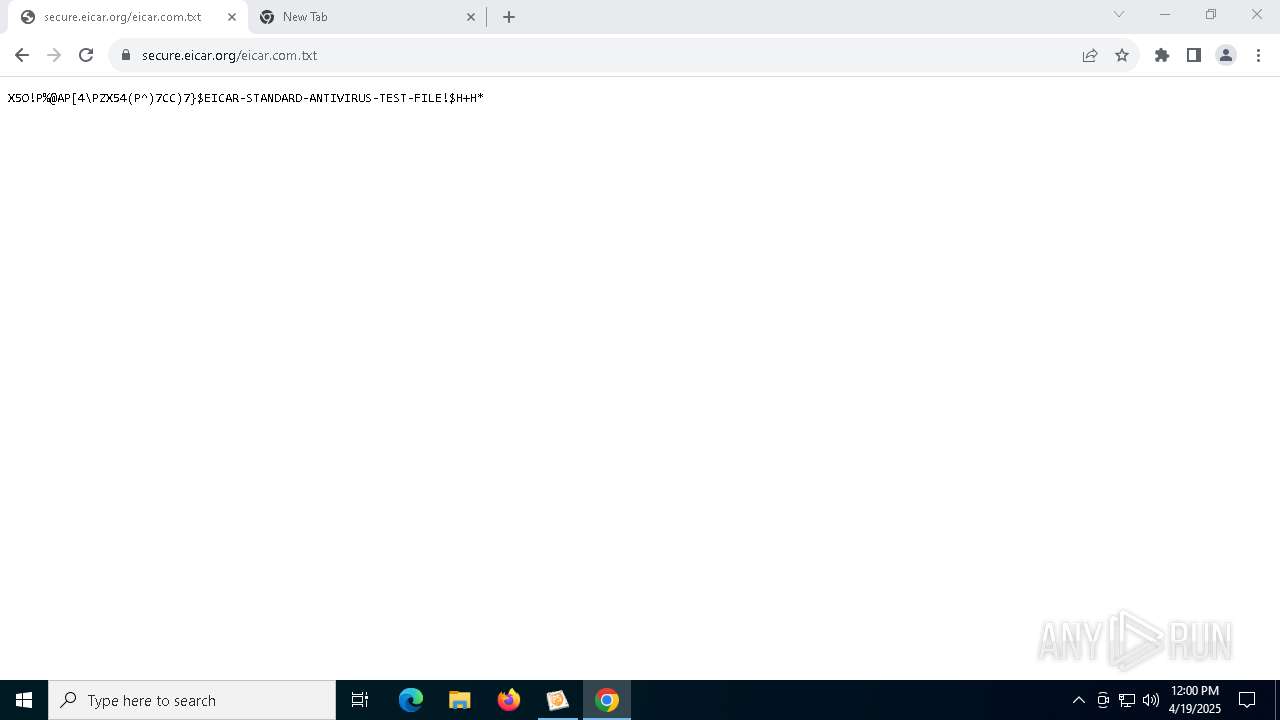
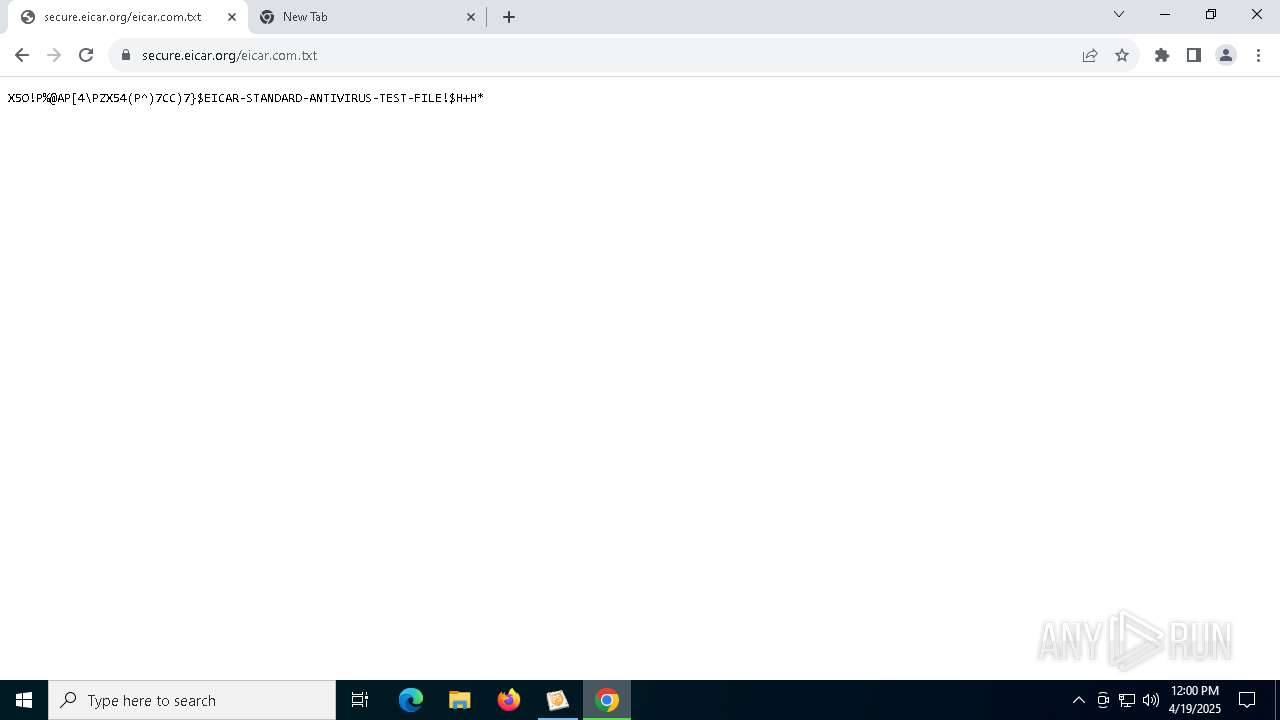
The EICAR Standard Anti-Virus Test File is detected
- chrome.exe (PID: 7636)
- chrome.exe (PID: 4300)
SUSPICIOUS
Process drops legitimate windows executable
- psguardinstall.exe (PID: 8064)
The process drops C-runtime libraries
- psguardinstall.exe (PID: 8064)
Executable content was dropped or overwritten
- psguardinstall.exe (PID: 8064)
The process creates files with name similar to system file names
- psguardinstall.exe (PID: 8064)
Creates/Modifies COM task schedule object
- psguardinstall.exe (PID: 8064)
Creates a software uninstall entry
- psguardinstall.exe (PID: 8064)
Reads security settings of Internet Explorer
- psguardinstall.exe (PID: 8064)
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
Reads the BIOS version
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
Reads Microsoft Outlook installation path
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
The process checks if it is being run in the virtual environment
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
Reads Internet Explorer settings
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
Starts application from unusual location
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
There is functionality for taking screenshot (YARA)
- PSGuard.exe (PID: 7516)
Executes application which crashes
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 7408)
- psguardinstall.exe (PID: 8064)
Create files in a temporary directory
- psguardinstall.exe (PID: 8064)
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
Checks supported languages
- psguardinstall.exe (PID: 8064)
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7408)
Manual execution by a user
- psguardinstall.exe (PID: 8016)
- psguardinstall.exe (PID: 8064)
- chrome.exe (PID: 4300)
- PSGuard.exe (PID: 7828)
Reads the computer name
- psguardinstall.exe (PID: 8064)
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
Creates files in the program directory
- psguardinstall.exe (PID: 8064)
Creates files or folders in the user directory
- psguardinstall.exe (PID: 8064)
- PSGuard.exe (PID: 7516)
- PSGuard.exe (PID: 7828)
- WerFault.exe (PID: 7980)
- WerFault.exe (PID: 5576)
Process checks computer location settings
- psguardinstall.exe (PID: 8064)
Checks proxy server information
- PSGuard.exe (PID: 7516)
- slui.exe (PID: 7192)
- PSGuard.exe (PID: 7828)
Reads the software policy settings
- slui.exe (PID: 7576)
- slui.exe (PID: 7192)
Reads security settings of Internet Explorer
- WerFault.exe (PID: 7980)
- WerFault.exe (PID: 5576)
Application launched itself
- chrome.exe (PID: 4300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2013:12:28 10:46:56 |
| ZipCRC: | 0x62c86414 |
| ZipCompressedSize: | 2467281 |
| ZipUncompressedSize: | 2495633 |
| ZipFileName: | psguardinstall.exe |
Total processes
169
Monitored processes
29
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5304 --field-trial-handle=1968,i,14925061575269940058,16912217844901249142,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=3184 --field-trial-handle=1968,i,14925061575269940058,16912217844901249142,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4756 --field-trial-handle=1968,i,14925061575269940058,16912217844901249142,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=4588 --field-trial-handle=1968,i,14925061575269940058,16912217844901249142,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=856 --field-trial-handle=1968,i,14925061575269940058,16912217844901249142,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 5376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3724 --field-trial-handle=1968,i,14925061575269940058,16912217844901249142,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 5576 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7828 -s 2840 | C:\Windows\SysWOW64\WerFault.exe | — | PSGuard.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=3252 --field-trial-handle=1968,i,14925061575269940058,16912217844901249142,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc896bdc40,0x7ffc896bdc4c,0x7ffc896bdc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
17 750
Read events
17 508
Write events
230
Delete events
12
Modification events
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\PSGuard.zip | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
47
Suspicious files
313
Text files
89
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8064 | psguardinstall.exe | C:\Users\admin\AppData\Local\Temp\nszF9.tmp\update.ini | text | |
MD5:E10C4DD06932498A042363359D8A3F0E | SHA256:25406130B3F04C2A04F675A8C8CE221564AAB09AF95E8AC9043ED3DDFD4E1D5B | |||
| 8064 | psguardinstall.exe | C:\Users\admin\AppData\Local\Temp\nszF8.tmp | — | |
MD5:— | SHA256:— | |||
| 8064 | psguardinstall.exe | C:\Users\admin\AppData\Local\Temp\nszF9.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 8064 | psguardinstall.exe | C:\Users\admin\AppData\Local\Temp\nszF9.tmp\ioSpecial.ini | text | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 7408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7408.22178\psguardinstall.exe | executable | |
MD5:A36E719F884A1D1F0BF3ECE901305888 | SHA256:5FE734AA86DB44189E889E670D40D0C697EC9C13C2FF4D9D77E7096F5C1E52F2 | |||
| 8064 | psguardinstall.exe | C:\Program Files (x86)\P.S.Guard\WndSystem.dll | executable | |
MD5:6FE5F810E013F4B5C9925B1EA309D7A2 | SHA256:D912A2CB63E10A571263B317FC2A6101A6ED813F5F1F79B7313524E8B98DD453 | |||
| 8064 | psguardinstall.exe | C:\Program Files (x86)\P.S.Guard\msvcr71.dll | executable | |
MD5:86F1895AE8C5E8B17D99ECE768A70732 | SHA256:8094AF5EE310714CAEBCCAEEE7769FFB08048503BA478B879EDFEF5F1A24FEFE | |||
| 8064 | psguardinstall.exe | C:\Program Files (x86)\P.S.Guard\msvcp71.dll | executable | |
MD5:561FA2ABB31DFA8FAB762145F81667C2 | SHA256:DF96156F6A548FD6FE5672918DE5AE4509D3C810A57BFFD2A91DE45A3ED5B23B | |||
| 8064 | psguardinstall.exe | C:\Program Files (x86)\P.S.Guard\PSGuard.exe | executable | |
MD5:9F6E298F867908A396D07ACBD9F927C2 | SHA256:93497725AF39978806C34CF02936ABA3022716A36451921BEFDC4B01B15DC561 | |||
| 4300 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF11e22f.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
99
DNS requests
101
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2284 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2284 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrovrpquemobbwthbstjwffhima_2025.1.17.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2025.01.17.01_all_dd5w5blqtgwb4xkyhfpmehllye.crx3 | unknown | — | — | whitelisted |
4868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrovrpquemobbwthbstjwffhima_2025.1.17.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2025.01.17.01_all_dd5w5blqtgwb4xkyhfpmehllye.crx3 | unknown | — | — | whitelisted |
4868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrovrpquemobbwthbstjwffhima_2025.1.17.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2025.01.17.01_all_dd5w5blqtgwb4xkyhfpmehllye.crx3 | unknown | — | — | whitelisted |
4868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrovrpquemobbwthbstjwffhima_2025.1.17.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2025.01.17.01_all_dd5w5blqtgwb4xkyhfpmehllye.crx3 | unknown | — | — | whitelisted |
4868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrovrpquemobbwthbstjwffhima_2025.1.17.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2025.01.17.01_all_dd5w5blqtgwb4xkyhfpmehllye.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2284 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2284 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |