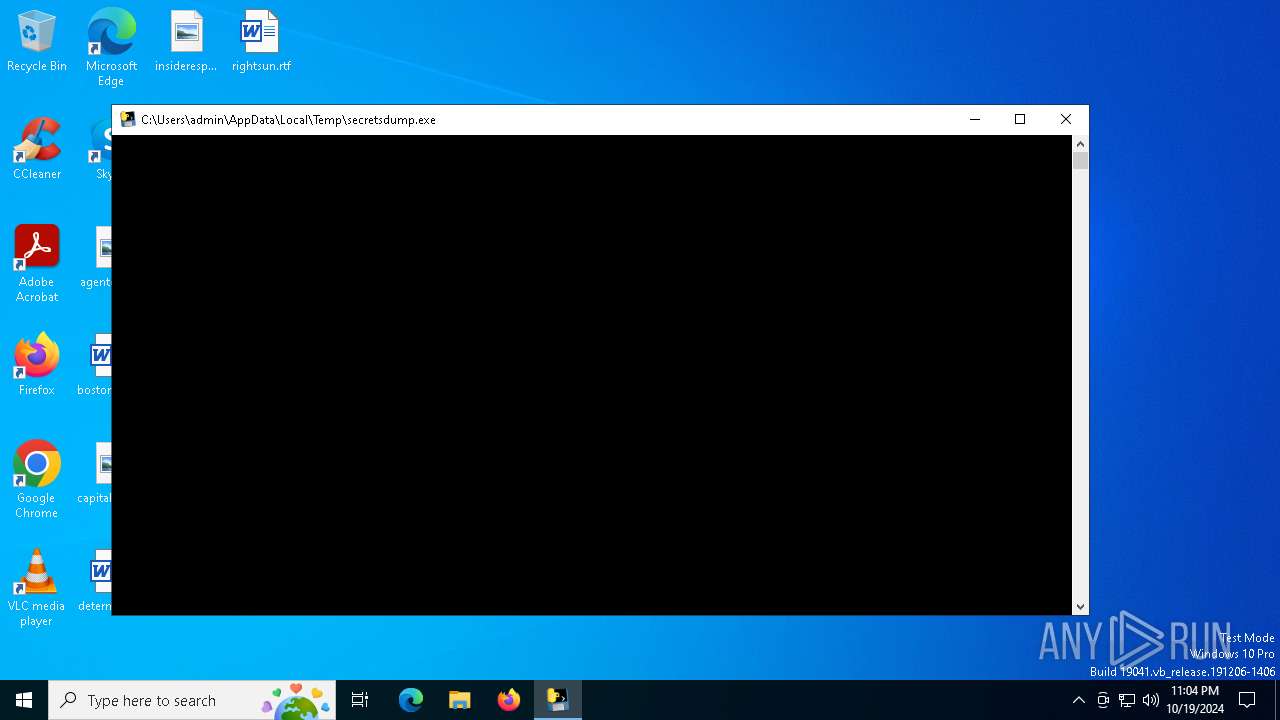
| File name: | secretsdump.exe |
| Full analysis: | https://app.any.run/tasks/9dc25325-54c2-42b4-8bbb-912de7980391 |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2024, 23:04:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 6E05B36151FA4743CCC6FF59C987002C |
| SHA1: | 416B2ED0A1D2A5403383A4F79B6906C5C8ADD691 |
| SHA256: | 50B252867FAB0A37EA53B5F4967EDE4307EDA1E0B4D42B026551C2E226C75F46 |
| SSDEEP: | 98304:zwk6vlH1khsH01WVn/9MfDNiYP9km5VfE6VbHjLmh+qmu3r+mZxUSHEQcdg0iQkG:aqXvsx6mDAbVk1r8t1a7JM9gL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- secretsdump.exe (PID: 6292)
The process drops C-runtime libraries
- secretsdump.exe (PID: 6292)
Process drops python dynamic module
- secretsdump.exe (PID: 6292)
Application launched itself
- secretsdump.exe (PID: 6292)
Loads Python modules
- secretsdump.exe (PID: 6684)
Process drops legitimate windows executable
- secretsdump.exe (PID: 6292)
INFO
Checks supported languages
- secretsdump.exe (PID: 6292)
- secretsdump.exe (PID: 6684)
Reads the computer name
- secretsdump.exe (PID: 6292)
Create files in a temporary directory
- secretsdump.exe (PID: 6292)
Reads the machine GUID from the registry
- secretsdump.exe (PID: 6684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2021:08:01 04:39:37+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.28 |
| CodeSize: | 144896 |
| InitializedDataSize: | 147456 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9d04 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
125
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3772 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | secretsdump.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6292 | "C:\Users\admin\AppData\Local\Temp\secretsdump.exe" | C:\Users\admin\AppData\Local\Temp\secretsdump.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6684 | "C:\Users\admin\AppData\Local\Temp\secretsdump.exe" | C:\Users\admin\AppData\Local\Temp\secretsdump.exe | — | secretsdump.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
215
Read events
215
Write events
0
Delete events
0
Modification events
Executable files
96
Suspicious files
3
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6292 | secretsdump.exe | C:\Users\admin\AppData\Local\Temp\_MEI62922\Cryptodome\Cipher\_Salsa20.pyd | executable | |
MD5:991AA4813AF0ADF95B0DF3F59879E21C | SHA256:5B86D84DA033128000D8BC00A237AB07D5FF75078216654C224854BEC0CD6641 | |||
| 6292 | secretsdump.exe | C:\Users\admin\AppData\Local\Temp\_MEI62922\Cryptodome\Cipher\_ARC4.pyd | executable | |
MD5:BA43C9C79B726F52CD3187231E3A780F | SHA256:7B5E1F955E198278A39B94F6AC18D49CEE21B99C8A951DE722FF99A153162A0B | |||
| 6292 | secretsdump.exe | C:\Users\admin\AppData\Local\Temp\_MEI62922\Cryptodome\Cipher\_raw_blowfish.pyd | executable | |
MD5:9F33973B19B84A288DF7918346CEC5E4 | SHA256:DC86A67CFF9CB3CC763AAAB2D357EC6DBC0616A5DFC16EBE214E8E2C04242737 | |||
| 6292 | secretsdump.exe | C:\Users\admin\AppData\Local\Temp\_MEI62922\Cryptodome\Cipher\_raw_aes.pyd | executable | |
MD5:DACF0299F0ACD196C0B0C35440C9CF78 | SHA256:1199152F31FC5179FD39733B6B7D60B7F4A7269FE28CBC434F87FA53810B305D | |||
| 6292 | secretsdump.exe | C:\Users\admin\AppData\Local\Temp\_MEI62922\Cryptodome\Cipher\_raw_cast.pyd | executable | |
MD5:89D4B1FC3A62B4A739571855F22E0C18 | SHA256:3832F95FE55D1B4DA223DF5438414F03F18D5EF4AAFD285357A81E4ED5AD5DA1 | |||
| 6292 | secretsdump.exe | C:\Users\admin\AppData\Local\Temp\_MEI62922\Cryptodome\Cipher\_raw_cfb.pyd | executable | |
MD5:E87AAC7F2A9BF57D6796E5302626EE2F | SHA256:97BF9E392D6AD9E1EC94237407887EA3D1DEC2D23978891A8174C03AF606FD34 | |||
| 6292 | secretsdump.exe | C:\Users\admin\AppData\Local\Temp\_MEI62922\Cryptodome\Cipher\_raw_des3.pyd | executable | |
MD5:EC55478B5DD99BBE1EBA9D6AD8BDE079 | SHA256:1AF46CBE209E3F1D30CCC0BA9F7E5A455554CAF8B1E3E42F9A93A097D9F435AC | |||
| 6292 | secretsdump.exe | C:\Users\admin\AppData\Local\Temp\_MEI62922\Cryptodome\Cipher\_raw_ctr.pyd | executable | |
MD5:F3F30D72D6D7F4BA94B3C1A9364F1831 | SHA256:7820395C44EAB26DE0312DFC5D08A9A27398F0CAA80D8F9A88DEE804880996FF | |||
| 6292 | secretsdump.exe | C:\Users\admin\AppData\Local\Temp\_MEI62922\Cryptodome\Cipher\_raw_aesni.pyd | executable | |
MD5:5D1CAEEDC9595EC0A30507C049F215D7 | SHA256:A5C4143DDFA6C10216E9467A22B792541096E222EFE71C930A5056B917E531A0 | |||
| 6292 | secretsdump.exe | C:\Users\admin\AppData\Local\Temp\_MEI62922\Cryptodome\Cipher\_raw_des.pyd | executable | |
MD5:020A1E1673A56AF5B93C16B0D312EF50 | SHA256:290B3ED6151B7BF8B7B227EF76879838294F7FF138AF68E083C2FDDC0A50E4FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
52
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5532 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6024 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6024 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5600 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
3952 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5600 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5600 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |