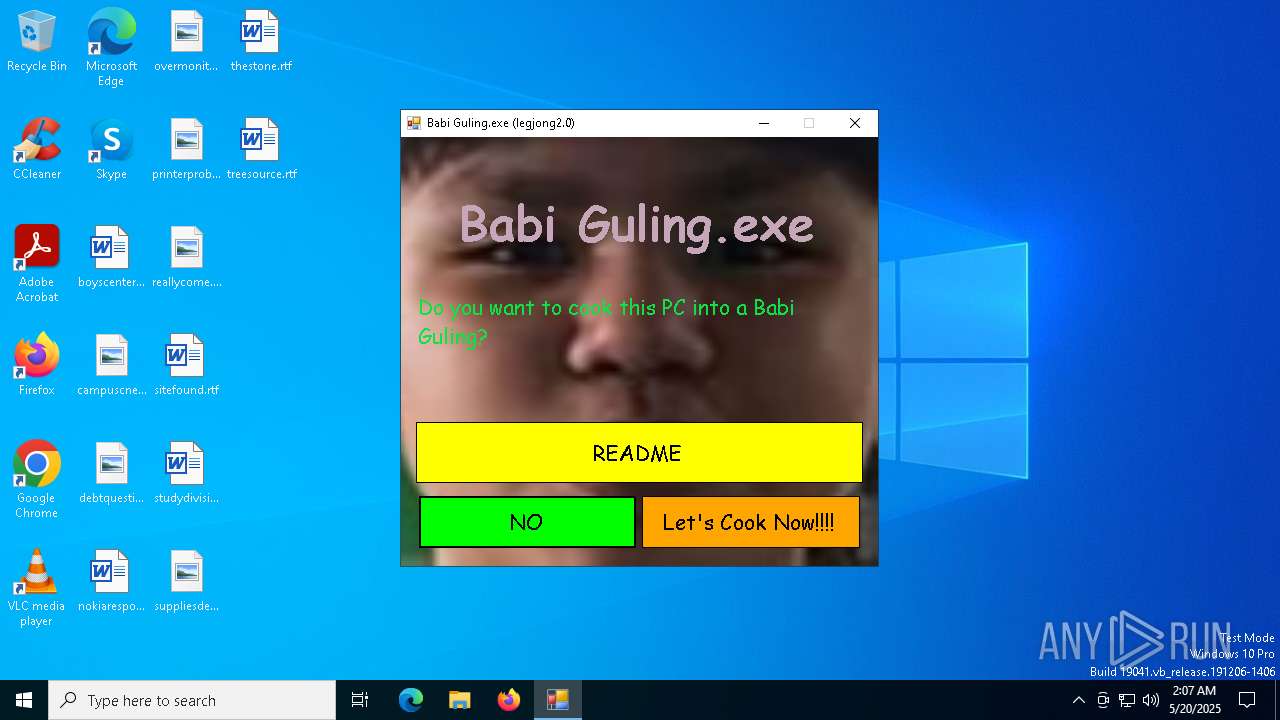
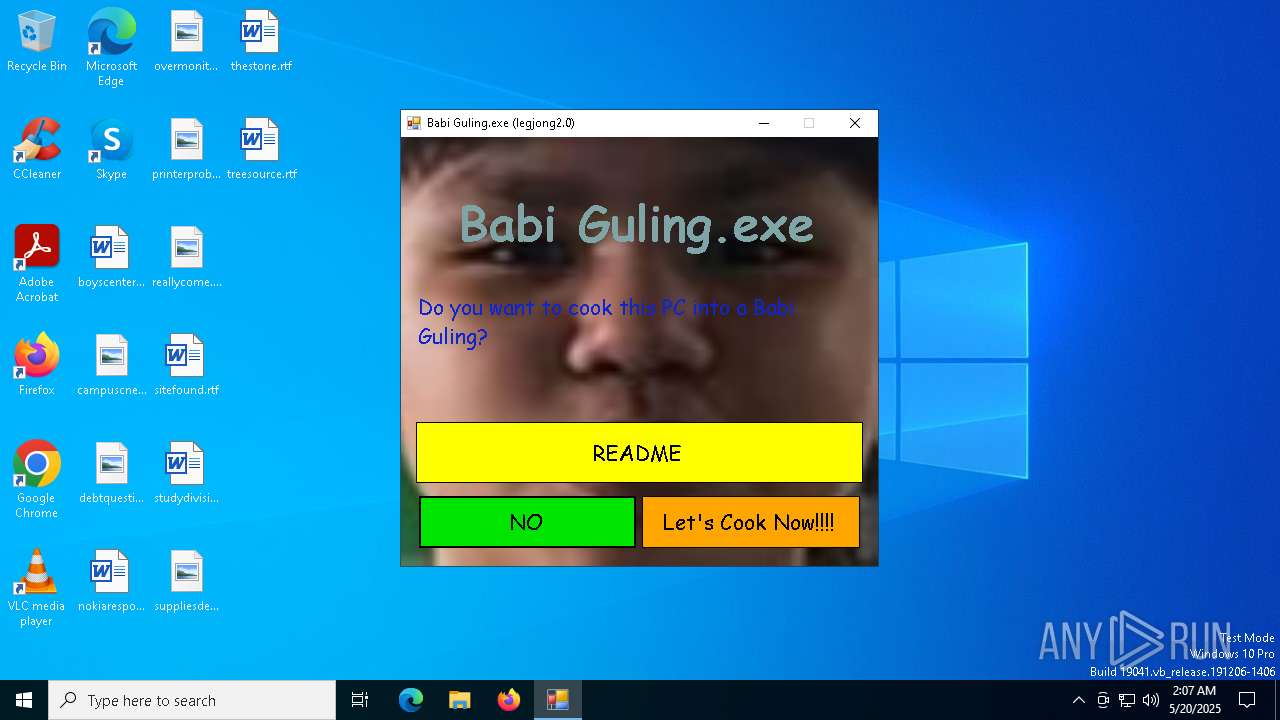
| File name: | Babi Guling(Legjong 2).exe |
| Full analysis: | https://app.any.run/tasks/5ae7c0d1-165c-41cb-a0b1-c5397bbc860c |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2025, 02:07:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 5 sections |
| MD5: | D4ED2CE974DE54D4B7A42A098F478AB0 |
| SHA1: | 3F0044E35C265B73FBA8317563F28CEB4FBA586A |
| SHA256: | 50B09C2D13250AA54090A2A38BE495BE8E3D6AFA888D29876B07CD726508BF2F |
| SSDEEP: | 12288:Jx1M7VP9EOuIrrG205FUXcqfRT0TuN4l+7wFt6:JPM7XEOuI9 |
MALICIOUS
DISKWRITER has been found (auto)
- Babi Guling(Legjong 2).exe (PID: 4892)
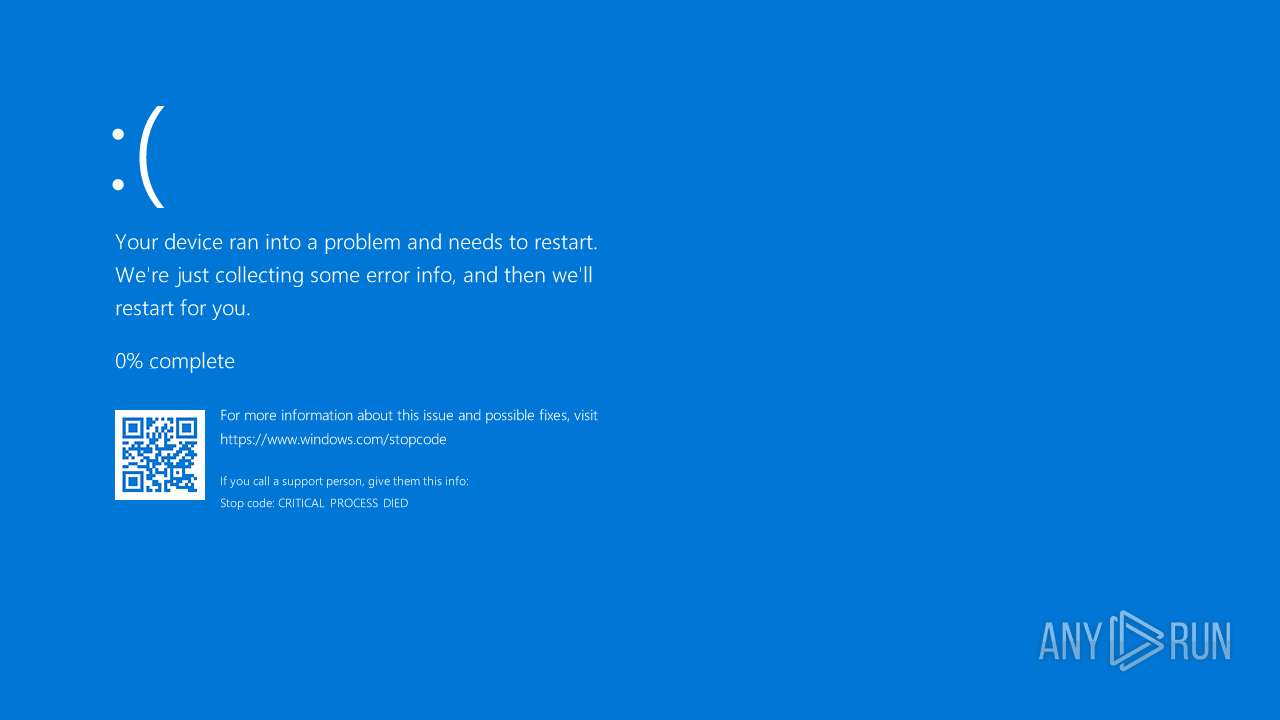
Disables task manager
- Babi Guling(Legjong 2).exe (PID: 4892)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Babi Guling(Legjong 2).exe (PID: 4892)
Starts CMD.EXE for commands execution
- Babi Guling(Legjong 2).exe (PID: 4892)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6436)
- cmd.exe (PID: 6068)
Process drops legitimate windows executable
- Babi Guling(Legjong 2).exe (PID: 4892)
Executable content was dropped or overwritten
- Babi Guling(Legjong 2).exe (PID: 4892)
Reads security settings of Internet Explorer
- Babi Guling(Legjong 2).exe (PID: 4892)
Reads the date of Windows installation
- Babi Guling(Legjong 2).exe (PID: 4892)
The process executes VB scripts
- Babi Guling(Legjong 2).exe (PID: 4892)
The process drops C-runtime libraries
- Babi Guling(Legjong 2).exe (PID: 4892)
Process copies executable file
- Babi Guling(Legjong 2).exe (PID: 4892)
INFO
Confuser has been detected (YARA)
- Babi Guling(Legjong 2).exe (PID: 4892)
Checks supported languages
- Babi Guling(Legjong 2).exe (PID: 4892)
Reads the machine GUID from the registry
- Babi Guling(Legjong 2).exe (PID: 4892)
Reads the computer name
- Babi Guling(Legjong 2).exe (PID: 4892)
The sample compiled with english language support
- Babi Guling(Legjong 2).exe (PID: 4892)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4756)
Process checks computer location settings
- Babi Guling(Legjong 2).exe (PID: 4892)
The sample compiled with french language support
- Babi Guling(Legjong 2).exe (PID: 4892)
Manual execution by a user
- notepad++.exe (PID: 5744)
The sample compiled with chinese language support
- Babi Guling(Legjong 2).exe (PID: 4892)
The sample compiled with korean language support
- Babi Guling(Legjong 2).exe (PID: 4892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2073:01:03 16:54:47+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 122880 |
| InitializedDataSize: | 176128 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5000a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | legjong2.0 |
| CompanyName: | CriticForInterpreting |
| FileDescription: | Babi Guling |
| FileVersion: | 1.0.0.0 |
| InternalName: | Babi Guling.exe |
| LegalCopyright: | Public Domain |
| LegalTrademarks: | - |
| OriginalFileName: | Babi Guling.exe |
| ProductName: | Babi Guling |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
200
Monitored processes
52
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\WINDOWS\system32\dialer.exe" | C:\Windows\System32\dialer.exe | — | Babi Guling(Legjong 2).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Phone Dialer Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | %systemroot%\system32\MusNotifyIcon.exe NotifyTrayIcon 13 | C:\Windows\System32\MusNotifyIcon.exe | — | MusNotification.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MusNotifyIcon.exe Exit code: 2149884437 Version: 10.0.19041.3693 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | reg delete HKCC /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "C:\WINDOWS\system32\DevicePairingWizard.exe" | C:\Windows\System32\DevicePairingWizard.exe | — | Babi Guling(Legjong 2).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Device Pairing Application Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | comp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\WINDOWS\system32\comp.exe" | C:\Windows\System32\comp.exe | — | Babi Guling(Legjong 2).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: File Compare Utility Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | reg delete HKCC /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\WINDOWS\system32\vdsldr.exe" | C:\Windows\System32\vdsldr.exe | — | Babi Guling(Legjong 2).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 1073807364 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 244
Read events
14 218
Write events
15
Delete events
11
Modification events
| (PID) Process: | (632) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\System\CurrentControlSet\SERVICES\TSDDD\DEVICE0 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (632) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\System\CurrentControlSet\SERVICES\TSDDD |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (632) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\System\CurrentControlSet\SERVICES |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1128) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\Software\Fonts |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1128) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\Software |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1128) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\System\CurrentControlSet\Control\Print\Printers |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1128) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\System\CurrentControlSet\Control\Print |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1128) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\System\CurrentControlSet\Control |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1128) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Hardware Profiles\0001\System\CurrentControlSet\SERVICES\TSDDD\DEVICE0 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4892) Babi Guling(Legjong 2).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
Executable files
38
Suspicious files
13
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4892 | Babi Guling(Legjong 2).exe | C:\Windows\System32\OEMDefaultAssociations.xml | xml | |
MD5:57765E99F5B5892C1F283A033E631CE2 | SHA256:2E2A2C9A1E2B3CE125C413846E2DAFDA4D474B1EB65F7137401267652CD140E3 | |||
| 4892 | Babi Guling(Legjong 2).exe | C:\Windows\System32\RtkCfg64.dll | executable | |
MD5:FF2B83521D3192952E7AF4BA3841014D | SHA256:35E80D9E79DA752A88971EF3EE7F281B4B8AB1C3DD8CD638F878FF707C7CF784 | |||
| 4892 | Babi Guling(Legjong 2).exe | C:\Windows\System32\mfc140jpn.dll | executable | |
MD5:1C266385CB23418380A9B07013EAE0C5 | SHA256:B0ACB5E4021EF6D0EE6AFF884D10520CA9881BB734F2CC73C166FA7251367F71 | |||
| 4892 | Babi Guling(Legjong 2).exe | C:\Windows\System32\mfc140u.dll | executable | |
MD5:B7D8B3F9D0D62FA30B7D29A736D2720D | SHA256:4545EABA650AF037B76B3F6029101BDE46CEFA3E40F43BDF9B9447B36A7C65B3 | |||
| 4892 | Babi Guling(Legjong 2).exe | C:\Windows\System32\MRT-KB890830.exe | — | |
MD5:— | SHA256:— | |||
| 4892 | Babi Guling(Legjong 2).exe | C:\Windows\System32\mmc.exe.config | xml | |
MD5:19D44DDFF72FCA799BA56013AC688B2B | SHA256:11A784EFAEBD8F3981AE61A2B98591C95EEF205247ABE2836750E2A6A37E0F0A | |||
| 4892 | Babi Guling(Legjong 2).exe | C:\Windows\System32\mfc140esn.dll | executable | |
MD5:B8FA6AEE8D3537F9F3CC0F466711B175 | SHA256:03538E72F7A3A28DB98A40F7BA48289A072807070CEACD574F367D36CEB65155 | |||
| 4892 | Babi Guling(Legjong 2).exe | C:\Windows\System32\msclmd.dll | executable | |
MD5:33D65CB2A7F71AA0ED57CC411BCC716B | SHA256:ED9B1D64A416C20153F4FE5B64AA759760FAFFEFCCA66EB093B7DABF5AFD8EFD | |||
| 4892 | Babi Guling(Legjong 2).exe | C:\Windows\System32\NetSetupMig.log | binary | |
MD5:662F4565D5900CF8EAF93585E7F0AEFE | SHA256:0E6D8F2D00A205FAAD08388DC00D718B0231C63BCD6FD21F6B5BBC436AFB05CD | |||
| 4892 | Babi Guling(Legjong 2).exe | C:\Windows\System32\emptyregdb.dat | binary | |
MD5:48B8F5E4E1555CEC9C6C720D386D8685 | SHA256:9479651FDB32BB0702F4E96890D0691143C77C044D6A02F664B1DBCE25A1E098 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2040 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5344 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5344 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2040 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |