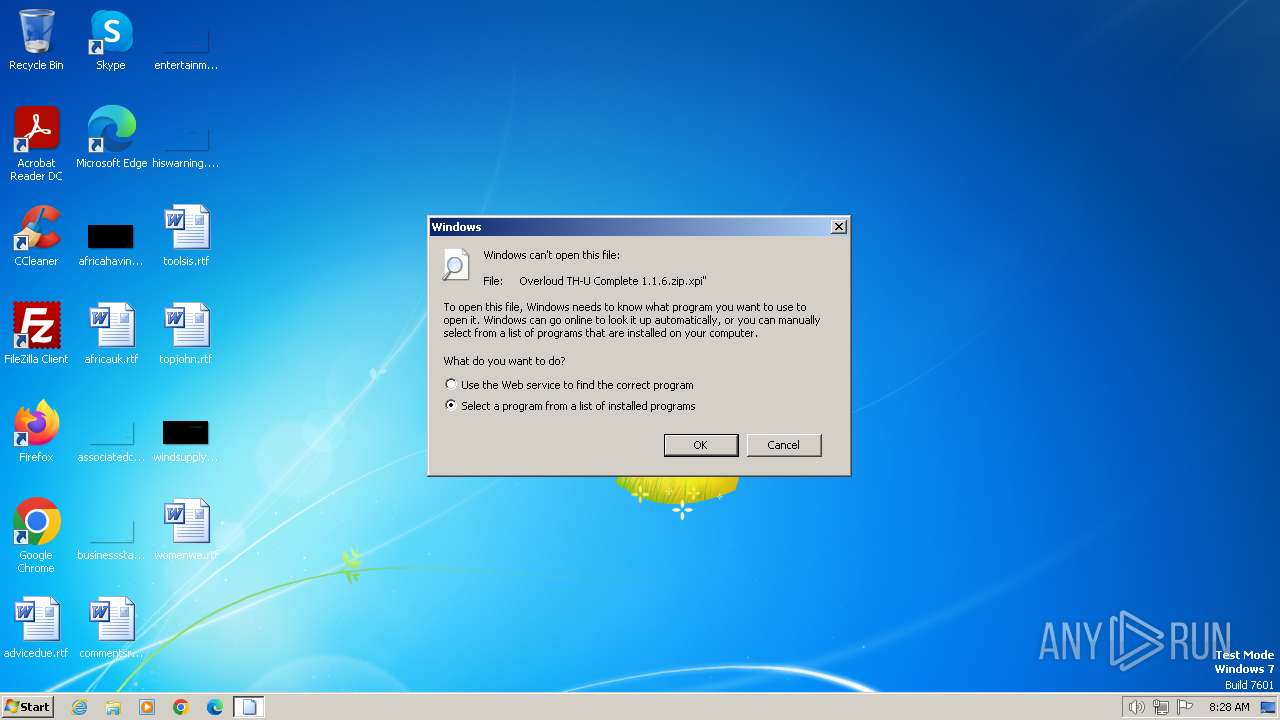
| File name: | Overloud TH-U Complete 1.1.6.zip |
| Full analysis: | https://app.any.run/tasks/97e6e13b-3aba-4d24-b53e-eb9dfe60304d |
| Verdict: | Malicious activity |
| Analysis date: | February 06, 2024, 08:28:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 3BB52D6CC887D5931C0F7FBCF6A1A89D |
| SHA1: | 87EA89234E444DEF004371F2D8D5317775415094 |
| SHA256: | 50AF13C15AAA9931F4C66F8C16CD45E28805A068F7F370EB44DC0958305D845D |
| SSDEEP: | 24576:UfUIzi8wVMwy6bsW9T7SsLhSDk9gPMtxXPtp/gHQJJWaIA+XNKWWSnqTeq24/:UfUIzi8GMwy6bseT7SsLhSDAgPMtNPtd |
MALICIOUS
Drops the executable file immediately after the start
- rundll32.exe (PID: 1392)
- Install.exe (PID: 3440)
- wocualts.exe (PID: 3884)
Creates a writable file in the system directory
- wocualts.exe (PID: 3884)
Registers / Runs the DLL via REGSVR32.EXE
- wocualts.exe (PID: 3884)
Changes the autorun value in the registry
- wocualts.exe (PID: 3884)
SUSPICIOUS
Reads the Internet Settings
- rundll32.exe (PID: 1392)
- Install.exe (PID: 3440)
- wocualts.exe (PID: 3884)
- Install.exe (PID: 3652)
Detected use of alternative data streams (AltDS)
- Install.exe (PID: 3440)
- Install.exe (PID: 3652)
- wocualts.exe (PID: 3716)
- wocualts.exe (PID: 3884)
Reads the BIOS version
- Install.exe (PID: 3440)
- wocualts.exe (PID: 3884)
- Install.exe (PID: 3652)
- wocualts.exe (PID: 3716)
Executable content was dropped or overwritten
- Install.exe (PID: 3440)
- wocualts.exe (PID: 3884)
Starts itself from another location
- Install.exe (PID: 3440)
- Install.exe (PID: 3652)
Reads settings of System Certificates
- wocualts.exe (PID: 3884)
Reads security settings of Internet Explorer
- wocualts.exe (PID: 3884)
Checks Windows Trust Settings
- wocualts.exe (PID: 3884)
INFO
Manual execution by a user
- WinRAR.exe (PID: 2628)
- Install.exe (PID: 3440)
- Install.exe (PID: 2776)
- Install.exe (PID: 3384)
- Install.exe (PID: 3652)
Checks supported languages
- Install.exe (PID: 3440)
- wocualts.exe (PID: 3884)
- Install.exe (PID: 3652)
- wocualts.exe (PID: 3716)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2628)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2628)
Creates files in the program directory
- Install.exe (PID: 3440)
- wocualts.exe (PID: 3884)
Reads the machine GUID from the registry
- Install.exe (PID: 3440)
- wocualts.exe (PID: 3884)
- Install.exe (PID: 3652)
- wocualts.exe (PID: 3716)
Reads the computer name
- Install.exe (PID: 3440)
- wocualts.exe (PID: 3884)
- Install.exe (PID: 3652)
- wocualts.exe (PID: 3716)
Create files in a temporary directory
- Install.exe (PID: 3440)
- wocualts.exe (PID: 3884)
- Install.exe (PID: 3652)
Creates files or folders in the user directory
- wocualts.exe (PID: 3884)
Checks proxy server information
- wocualts.exe (PID: 3884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:01:25 12:02:58 |
| ZipCRC: | 0x8121cd3f |
| ZipCompressedSize: | 861427 |
| ZipUncompressedSize: | 1738007 |
| ZipFileName: | Install.exe |
Total processes
65
Monitored processes
18
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1392 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\AppData\Local\Temp\Overloud TH-U Complete 1.1.6.zip.xpi" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1812 | regsvr32.exe /s "C:\Users\admin\AppData\Local\Temp\vbzip11.dll" | C:\Windows\System32\regsvr32.exe | — | wocualts.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2628 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Overloud TH-U Complete 1.1.6.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2776 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | — | explorer.exe | |||||||||||
User: admin Company: microsoft Integrity Level: MEDIUM Description: dll loader Exit code: 3221226540 Version: 1.02.0057 Modules
| |||||||||||||||
| 2964 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | wocualts.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2980 | regsvr32.exe /s "C:\Users\admin\AppData\Local\Temp\vbzip11.dll" | C:\Windows\System32\regsvr32.exe | — | wocualts.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3384 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | — | explorer.exe | |||||||||||
User: admin Company: microsoft Integrity Level: MEDIUM Description: dll loader Exit code: 3221226540 Version: 1.02.0057 Modules
| |||||||||||||||
| 3440 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | explorer.exe | ||||||||||||
User: admin Company: microsoft Integrity Level: HIGH Description: dll loader Exit code: 0 Version: 1.02.0057 Modules
| |||||||||||||||
| 3456 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Overloud TH-U Complete 1.1.6.zip.xpi | C:\Windows\System32\notepad.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3652 | "C:\Users\admin\Desktop\Install.exe" | C:\Users\admin\Desktop\Install.exe | explorer.exe | ||||||||||||
User: admin Company: microsoft Integrity Level: HIGH Description: dll loader Exit code: 0 Version: 1.02.0057 Modules
| |||||||||||||||
Total events
7 031
Read events
6 856
Write events
175
Delete events
0
Modification events
| (PID) Process: | (1392) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
3
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3440 | Install.exe | C:\Users\admin\AppData\Local\Temp\wocualts.exe | executable | |
MD5:9BDEEB02A9A7B979B6FBBB6386971BC5 | SHA256:AC7AA51E181FE3DD90FE052714C7540351A3D00A0757D37CCB828D227CB86500 | |||
| 3884 | wocualts.exe | C:\Users\admin\AppData\Local\Temp\vbzip11.dll | executable | |
MD5:ABEE1079EA3F3E74C933915BF10A7B9B | SHA256:D13F6334C4CB124052D658E687A0394FB431447E5239A4F8BE576C9C416705CA | |||
| 3884 | wocualts.exe | C:\ProgramData\TEMP:C9C13817 | binary | |
MD5:7C2237BEDCBD9224FE1EF21A7D3CDB0A | SHA256:9573BBD538F6FF57FC578B7E9FC9D70328D5F60939933412FE3C0D002809A9A8 | |||
| 2628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2628.13047\key.txt | text | |
MD5:766BBBC3E44081770671FD2506136EDB | SHA256:A69388FA60696A7397598C2F3B5C8521310AB12E7C7570E31073F0271EACB39E | |||
| 3884 | wocualts.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\7BEVBSS0.txt | text | |
MD5:58147D3A6D9E2B26E9108E6A595D073A | SHA256:DDA49F683D86D5048A22136EC854B6ABEB3214FBEA8C1317ED0ED01DB184B3DA | |||
| 3884 | wocualts.exe | C:\Users\admin\AppData\Local\Temp\instal\readm.txt | text | |
MD5:5ED4E9858AD8D239145EF285B6210A00 | SHA256:85554BB9DD4B57D6E5C850E0840DBAC644CD5568D0E20A2000468B3A01A7532A | |||
| 2964 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF3FA.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2964 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF40A.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 3884 | wocualts.exe | C:\Users\admin\AppData\Local\Temp\micka.exe | abr | |
MD5:F09F35A5637839458E462E6350ECBCE4 | SHA256:38723A2E5E8A17AA7950DC008209944E898F69A7BD10A23C839D341E935FD5CA | |||
| 3884 | wocualts.exe | C:\Users\admin\AppData\Local\Temp\instal\key.txt | text | |
MD5:766BBBC3E44081770671FD2506136EDB | SHA256:A69388FA60696A7397598C2F3B5C8521310AB12E7C7570E31073F0271EACB39E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
9
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3884 | wocualts.exe | GET | 301 | 142.250.185.142:80 | http://google.com/ | unknown | html | 219 b | unknown |
3884 | wocualts.exe | GET | 200 | 216.58.212.164:80 | http://www.google.com/ | unknown | html | 4.34 Kb | unknown |
3884 | wocualts.exe | GET | 200 | 185.53.178.54:80 | http://games.katz.cd/pg/1 | unknown | html | 2.29 Kb | unknown |
3884 | wocualts.exe | GET | 301 | 3.33.130.190:80 | http://btjunkie.org/browse/Software/page1/?o=52&t=0 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3884 | wocualts.exe | 142.250.185.142:80 | google.com | GOOGLE | US | whitelisted |
3884 | wocualts.exe | 216.58.212.164:80 | www.google.com | GOOGLE | US | whitelisted |
3884 | wocualts.exe | 185.53.178.54:80 | games.katz.cd | Team Internet AG | DE | malicious |
3884 | wocualts.exe | 3.33.130.190:80 | btjunkie.org | AMAZON-02 | US | unknown |
3884 | wocualts.exe | 3.33.130.190:443 | btjunkie.org | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.google.com |
| whitelisted |
ns2.thebuisness.com |
| unknown |
games.katz.cd |
| unknown |
btjunkie.org |
| whitelisted |
Threats
Process | Message |
|---|---|
Install.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Install.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
wocualts.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
wocualts.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Install.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Install.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
wocualts.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
wocualts.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |